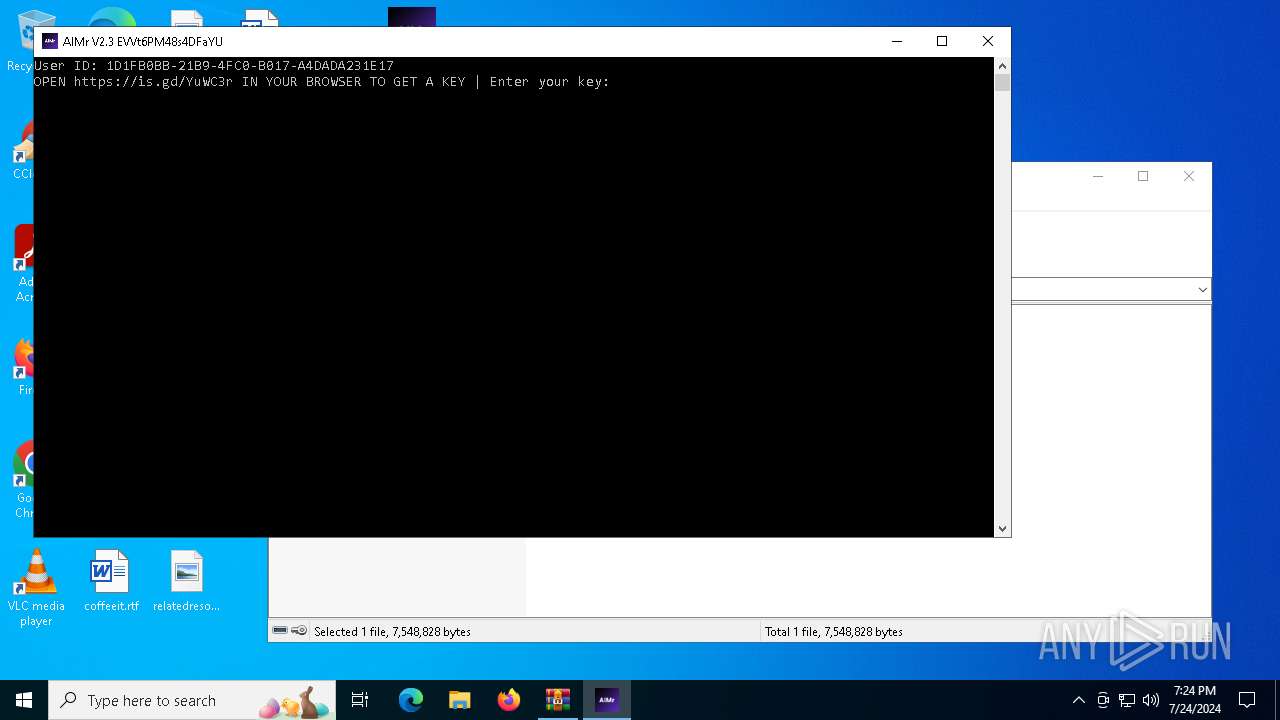
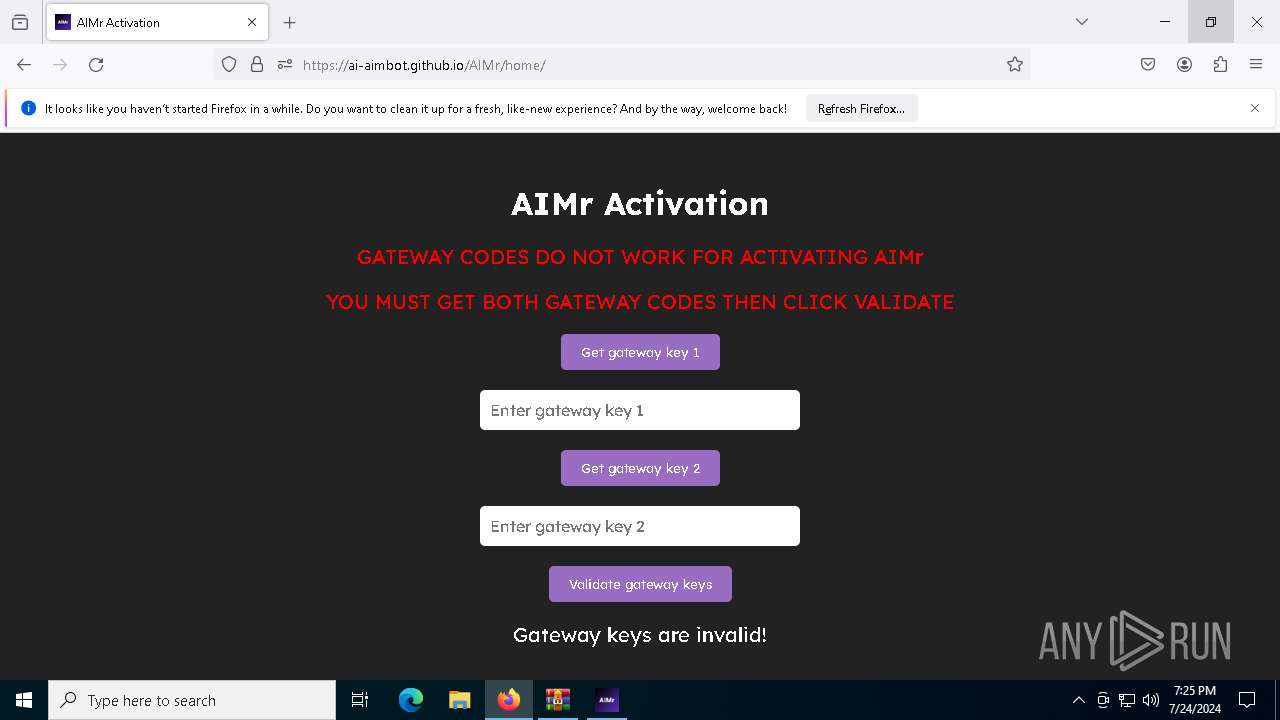
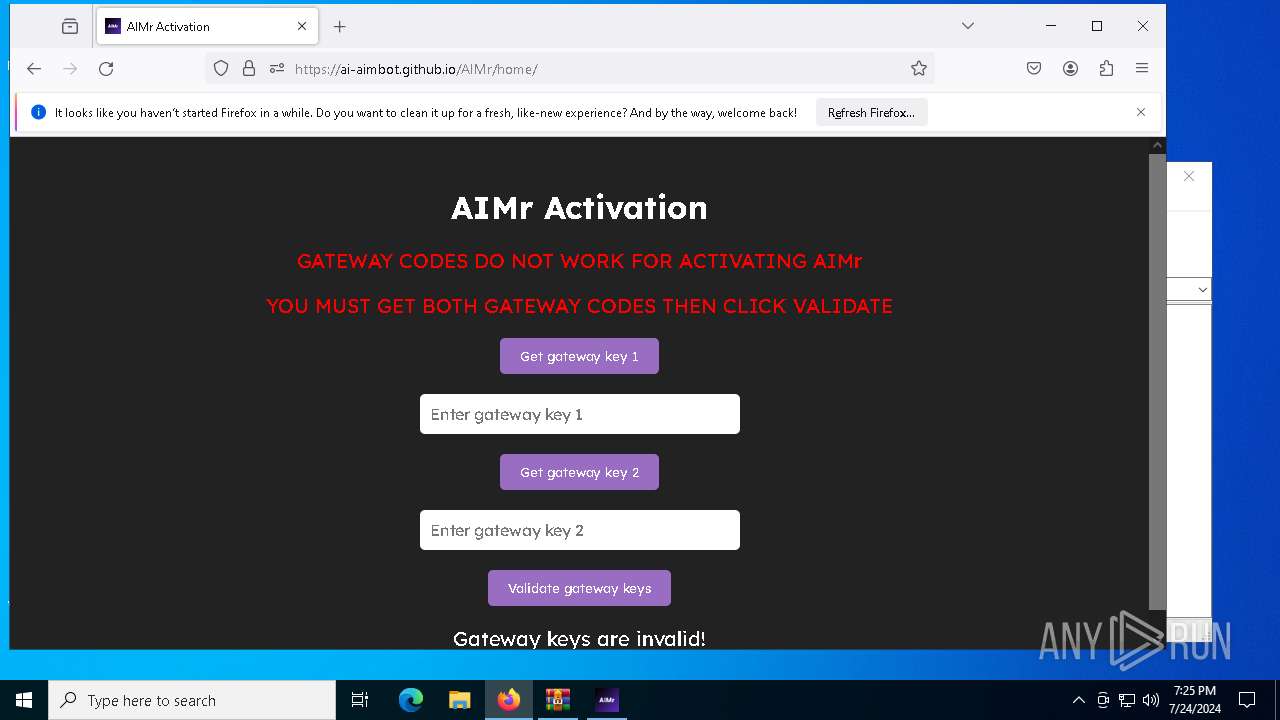
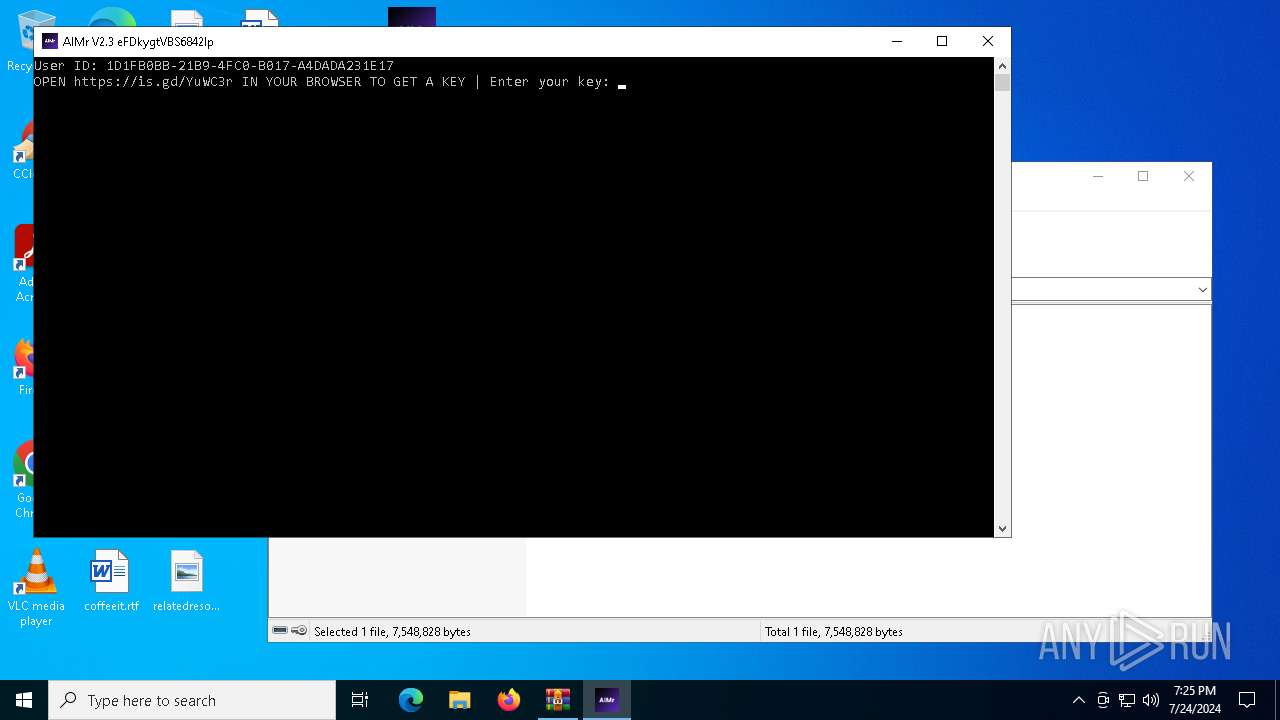
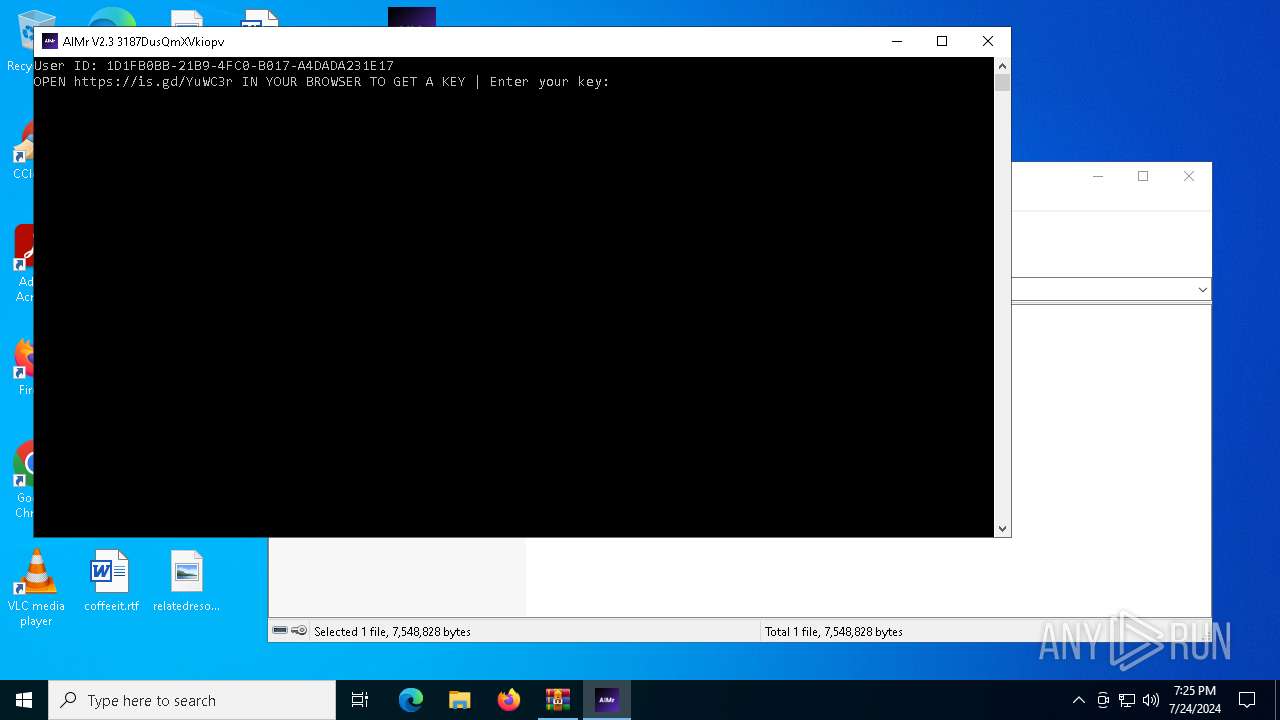
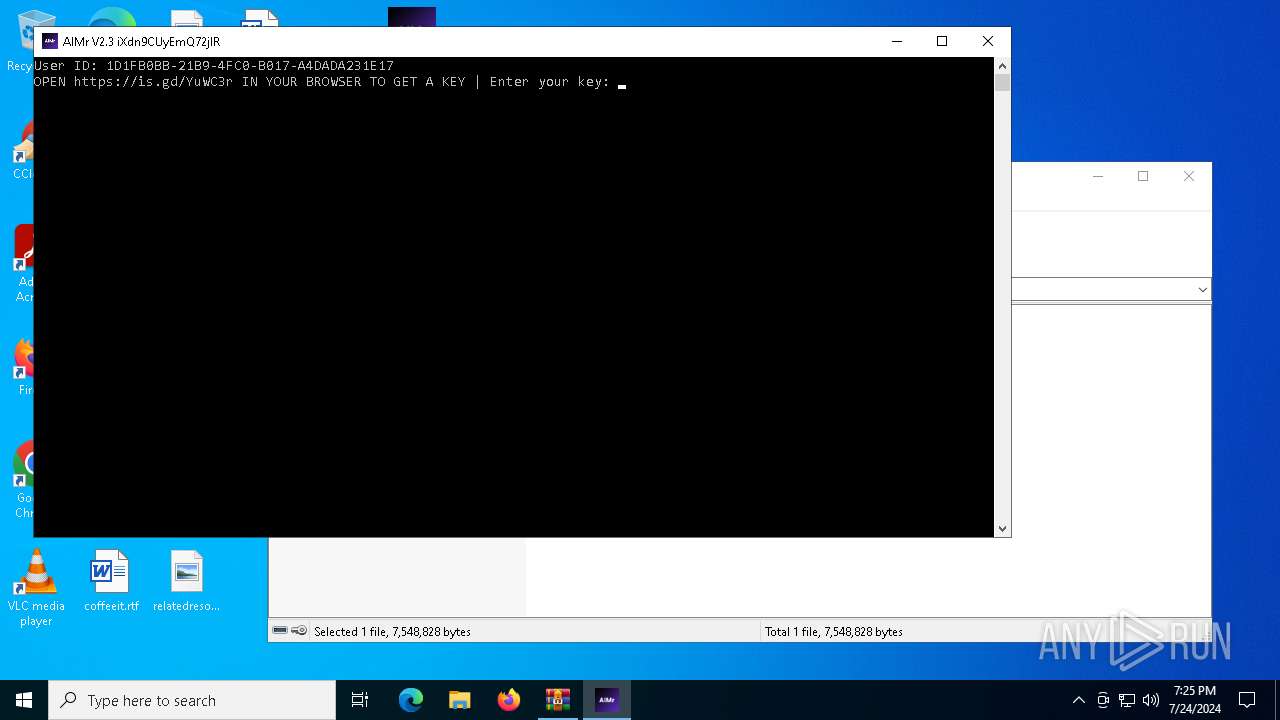
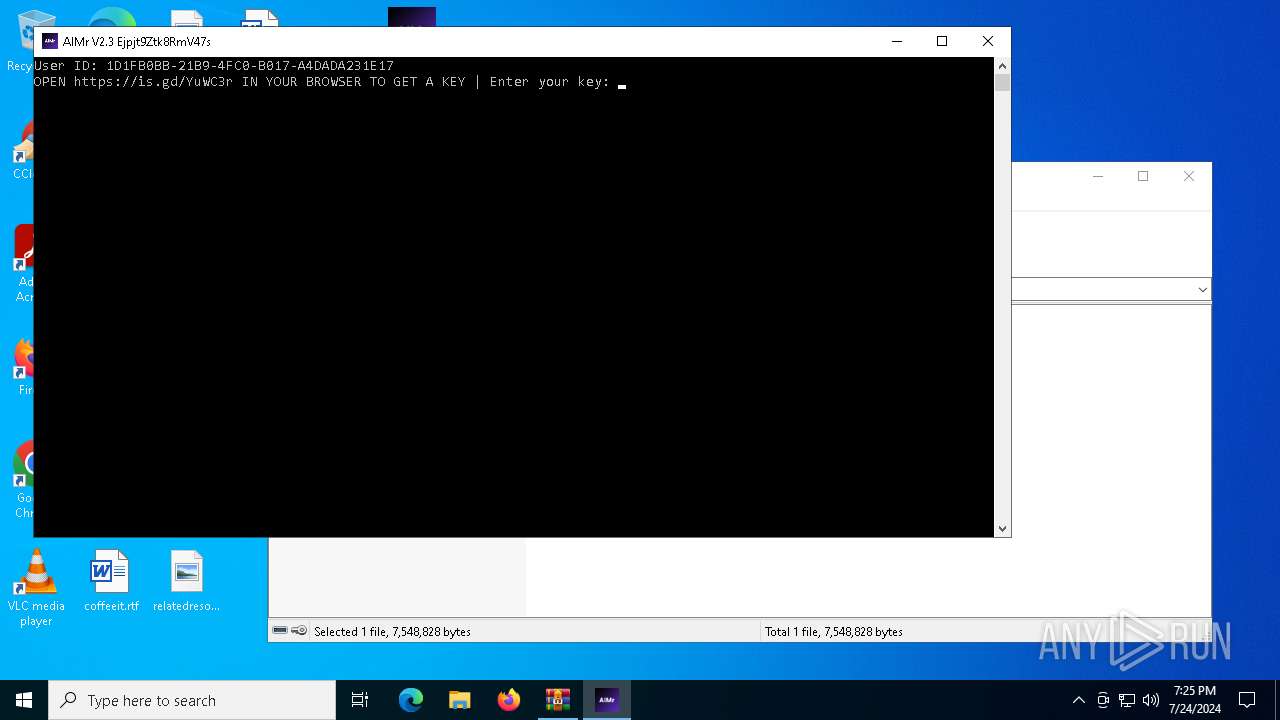
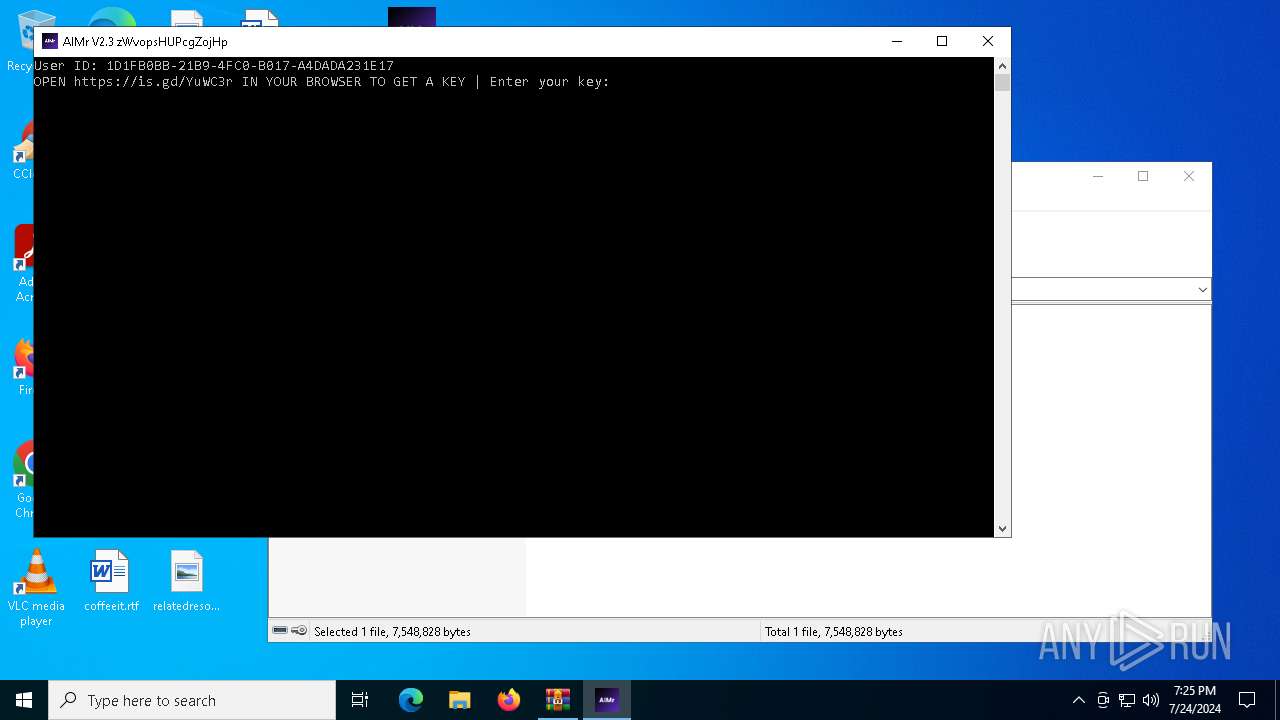
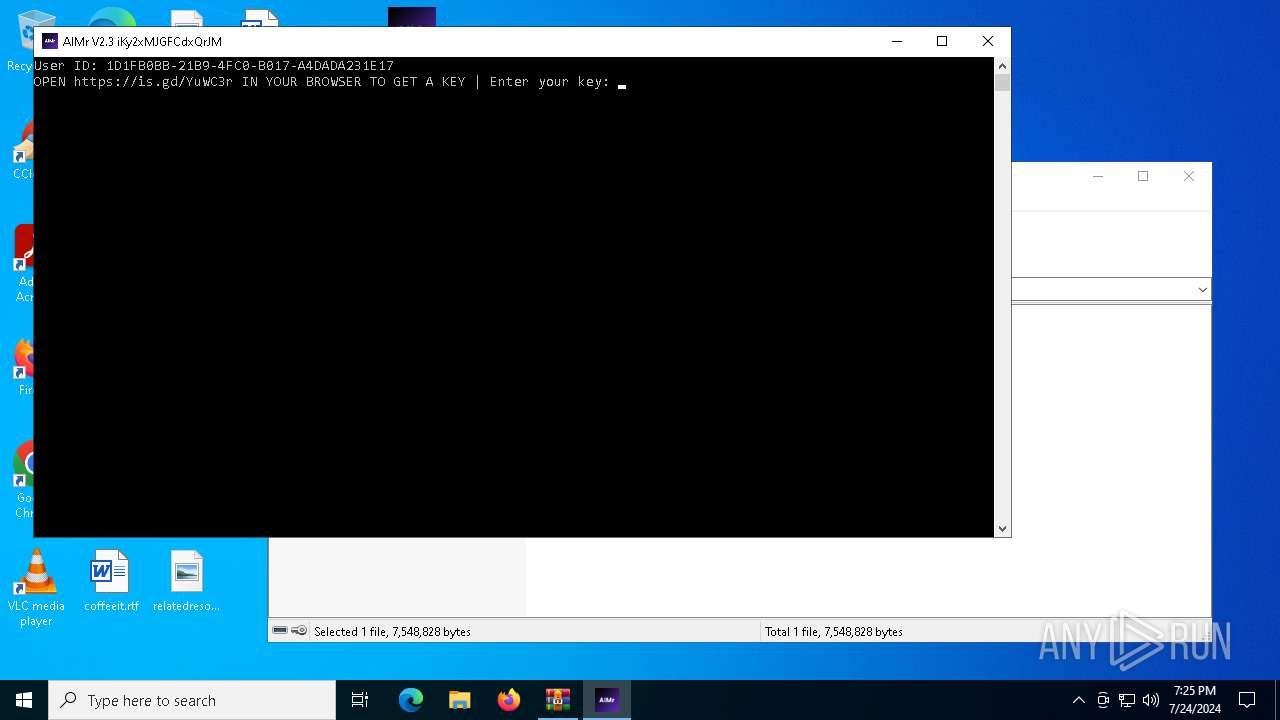
| download: | /ai-aimbot/AIMr/files/15284124/AIMr.zip |
| Full analysis: | https://app.any.run/tasks/b158c984-9eeb-43f7-84d7-6e2e2961581e |
| Verdict: | Malicious activity |
| Analysis date: | July 24, 2024, 19:24:23 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | DBC2DE4B885B9626D6CF8323B080C60F |
| SHA1: | 3D48A93873DCD8B61ECF166EC12C8CBE6A9A52E4 |
| SHA256: | F534F51BFB6136975B3CD469EEF6285043D47466AA103FD2F2996FBF9CE3868E |
| SSDEEP: | 98304:hKBBgVhsrFFD4Aw6DFM65Es07jZKmH/krpzj1ELj9hpU/1c0J/7dY21l3vs+YXGc:37D82JbtaZL9q2diCmkPNk |
MALICIOUS
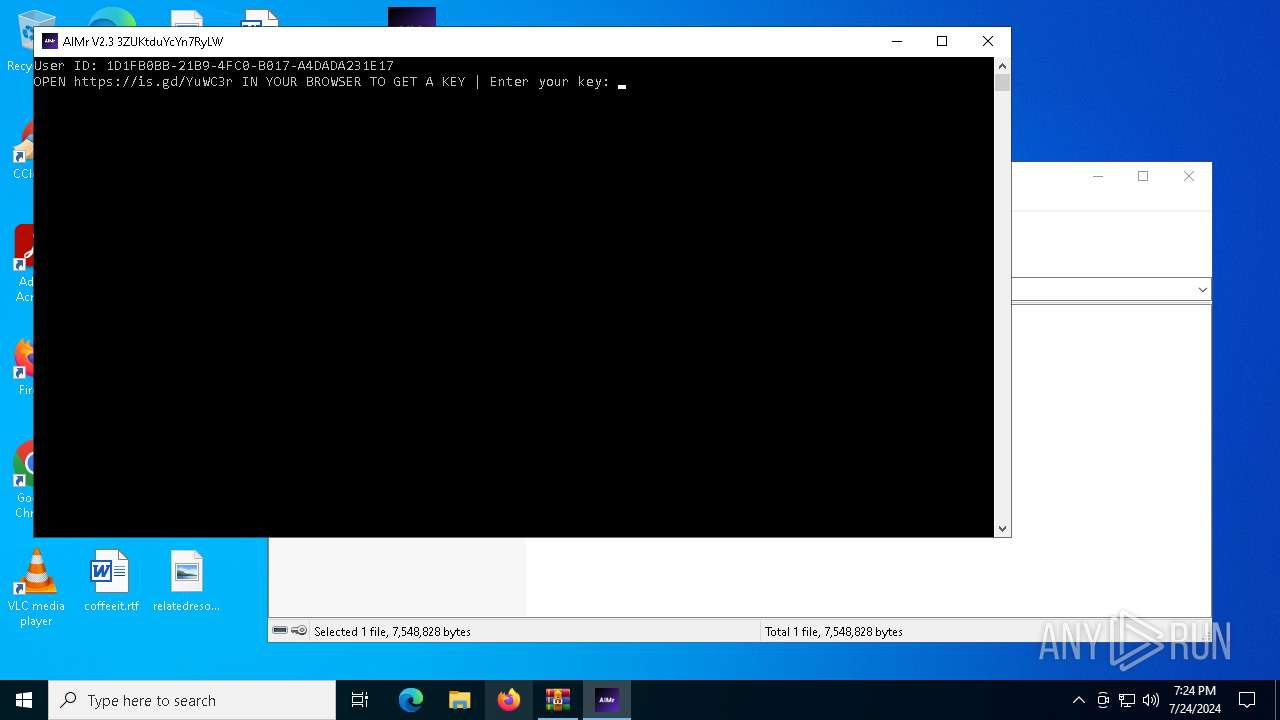
Drops the executable file immediately after the start
- WinRAR.exe (PID: 116)
- AIMr.exe (PID: 5032)
SUSPICIOUS
Process drops legitimate windows executable
- AIMr.exe (PID: 5032)
Process drops python dynamic module
- AIMr.exe (PID: 5032)
Application launched itself
- AIMr.exe (PID: 5032)
The process drops C-runtime libraries
- AIMr.exe (PID: 5032)
Executable content was dropped or overwritten
- AIMr.exe (PID: 5032)
Uses WMIC.EXE to obtain Windows Installer data
- AIMr.exe (PID: 6956)
Loads Python modules
- AIMr.exe (PID: 6956)
Accesses product unique identifier via WMI (SCRIPT)
- WMIC.exe (PID: 3480)
INFO
Manual execution by a user
- AIMr.exe (PID: 5032)
- firefox.exe (PID: 6288)
Reads the computer name
- AIMr.exe (PID: 5032)
- AIMr.exe (PID: 6956)
- TextInputHost.exe (PID: 7232)
Create files in a temporary directory
- AIMr.exe (PID: 5032)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 116)
Checks supported languages
- AIMr.exe (PID: 6956)
- AIMr.exe (PID: 5032)
- TextInputHost.exe (PID: 7232)
Checks proxy server information
- AIMr.exe (PID: 6956)
- slui.exe (PID: 6364)
Reads the machine GUID from the registry
- AIMr.exe (PID: 6956)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 3480)
Application launched itself
- firefox.exe (PID: 6288)
- firefox.exe (PID: 7132)
Reads Microsoft Office registry keys
- firefox.exe (PID: 7132)
Reads the software policy settings
- slui.exe (PID: 6364)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:05:11 12:45:10 |
| ZipCRC: | 0xf4d6834f |
| ZipCompressedSize: | 7363385 |
| ZipUncompressedSize: | 7548828 |
| ZipFileName: | AIMr.exe |
Total processes
156
Monitored processes
22
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Downloads\AIMr.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 132 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=2952 -childID 1 -isForBrowser -prefsHandle 2944 -prefMapHandle 1516 -prefsLen 30953 -prefMapSize 244343 -jsInitHandle 1440 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {a8843d45-ab69-49bf-8a22-fb0e9510d305} 7132 "\\.\pipe\gecko-crash-server-pipe.7132" 1d47f76c150 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 1132 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | AIMr.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3480 | wmic csproduct get uuid | C:\Windows\System32\wbem\WMIC.exe | — | AIMr.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5032 | "C:\Users\admin\Desktop\AIMr.exe" | C:\Users\admin\Desktop\AIMr.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 5664 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=2292 -parentBuildID 20240213221259 -prefsHandle 2284 -prefMapHandle 2252 -prefsLen 30537 -prefMapSize 244343 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {e9b9194c-04a2-4901-8d91-e88b525a489e} 7132 "\\.\pipe\gecko-crash-server-pipe.7132" 1d46d380d10 socket | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 5776 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=1916 -parentBuildID 20240213221259 -prefsHandle 1856 -prefMapHandle 1848 -prefsLen 30537 -prefMapSize 244343 -appDir "C:\Program Files\Mozilla Firefox\browser" - {2d0d9581-21e7-46b3-b4bb-3397f691464d} 7132 "\\.\pipe\gecko-crash-server-pipe.7132" 1d479eea210 gpu | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 1 Version: 123.0 Modules
| |||||||||||||||
| 6288 | "C:\Program Files\Mozilla Firefox\firefox.exe" | C:\Program Files\Mozilla Firefox\firefox.exe | — | explorer.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 6364 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6956 | "C:\Users\admin\Desktop\AIMr.exe" | C:\Users\admin\Desktop\AIMr.exe | AIMr.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
Total events
30 494
Read events
30 454
Write events
39
Delete events
1
Modification events
| (PID) Process: | (116) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (116) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (116) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (116) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Downloads\AIMr.zip | |||
| (PID) Process: | (116) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (116) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (116) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (116) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6288) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Launcher |
Value: 7DA101C900000000 | |||
| (PID) Process: | (7132) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Browser |
Value: AA5902C900000000 | |||
Executable files
53
Suspicious files
201
Text files
61
Unknown types
28
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 116 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa116.38759\AIMr.exe | executable | |
MD5:ADCD61646DD9EE3238279FF36DC0E88E | SHA256:481865D699E7B4DC3C160E33181F4D2A82067D2D03DD661E0C8FBE047E9F283C | |||
| 5032 | AIMr.exe | C:\Users\admin\AppData\Local\Temp\_MEI50322\api-ms-win-core-file-l2-1-0.dll | executable | |
MD5:BFFFA7117FD9B1622C66D949BAC3F1D7 | SHA256:1EA267A2E6284F17DD548C6F2285E19F7EDB15D6E737A55391140CE5CB95225E | |||
| 5032 | AIMr.exe | C:\Users\admin\AppData\Local\Temp\_MEI50322\api-ms-win-core-interlocked-l1-1-0.dll | executable | |
MD5:39809CC5DABF769DA8871A91A8ED9E69 | SHA256:5CD00FF4731691F81FF528C4B5A2E408548107EFC22CC6576048B0FDCE3DFBC9 | |||
| 5032 | AIMr.exe | C:\Users\admin\AppData\Local\Temp\_MEI50322\_socket.pyd | executable | |
MD5:6DF98284426330435E5AA6B8434CF461 | SHA256:153F1D66C0FD99A6FBC77496F8A91591D8850A122CC57B99A2AF95FA58951401 | |||
| 5032 | AIMr.exe | C:\Users\admin\AppData\Local\Temp\_MEI50322\_hashlib.pyd | executable | |
MD5:917CD9D31245F587CB36E92650B05952 | SHA256:68B478F11FE94F4C325B0239DC3F2BBB4B81ED1A7D40F0109A98990351D89967 | |||
| 5032 | AIMr.exe | C:\Users\admin\AppData\Local\Temp\_MEI50322\api-ms-win-core-file-l1-1-0.dll | executable | |
MD5:241338AEF5E2C18C80FB1DB07AA8BCDF | SHA256:56DE091EFE467FE23CC989C1EE21F3249A1BDB2178B51511E3BD514DF12C5CCB | |||
| 5032 | AIMr.exe | C:\Users\admin\AppData\Local\Temp\_MEI50322\_ssl.pyd | executable | |
MD5:B2EC752BF3928BF6C8A8F1EE36CA5607 | SHA256:E65568773DB94E6F2DD33B5973DEEAD718ADC8BC47E99ABDF314C7629C359E5B | |||
| 5032 | AIMr.exe | C:\Users\admin\AppData\Local\Temp\_MEI50322\_lzma.pyd | executable | |
MD5:012D4FF37E52E0D258BDBBE4C17FC012 | SHA256:D6297ABB919F3F69E94C035FCA327E56841E5ABEBBFF29FF95FE0A68BE46432D | |||
| 5032 | AIMr.exe | C:\Users\admin\AppData\Local\Temp\_MEI50322\api-ms-win-core-debug-l1-1-0.dll | executable | |
MD5:9476AFFAAC53E6E34405C4001F141805 | SHA256:55574F9E80D313048C245ACEFD21801D0D6C908A8A5049B4C46253EFAF420F89 | |||
| 5032 | AIMr.exe | C:\Users\admin\AppData\Local\Temp\_MEI50322\VCRUNTIME140.dll | executable | |
MD5:8697C106593E93C11ADC34FAA483C4A0 | SHA256:FF43E813785EE948A937B642B03050BB4B1C6A5E23049646B891A66F65D4C833 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
28
TCP/UDP connections
154
DNS requests
219
Threats
12
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6856 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
7132 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
5272 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7132 | firefox.exe | POST | 200 | 2.16.241.15:80 | http://r10.o.lencr.org/ | unknown | — | — | unknown |
7132 | firefox.exe | POST | 200 | 2.16.241.12:80 | http://r3.o.lencr.org/ | unknown | — | — | unknown |
7132 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
7132 | firefox.exe | POST | 200 | 2.16.241.15:80 | http://r10.o.lencr.org/ | unknown | — | — | unknown |
7132 | firefox.exe | POST | 200 | 2.16.241.15:80 | http://r10.o.lencr.org/ | unknown | — | — | unknown |
7132 | firefox.exe | POST | 200 | 2.16.241.15:80 | http://r11.o.lencr.org/ | unknown | — | — | unknown |
7132 | firefox.exe | POST | 200 | 142.250.186.35:80 | http://o.pki.goog/wr2 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6012 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4360 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
3380 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
— | — | 2.23.209.182:443 | www.bing.com | Akamai International B.V. | GB | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4204 | svchost.exe | 4.209.32.67:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
3952 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6956 | AIMr.exe | 185.199.111.133:443 | raw.githubusercontent.com | FASTLY | US | unknown |
1952 | slui.exe | 20.83.72.98:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
raw.githubusercontent.com |
| shared |
activation-v2.sls.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.bing.com |
| whitelisted |
arc.msn.com |
| whitelisted |
detectportal.firefox.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
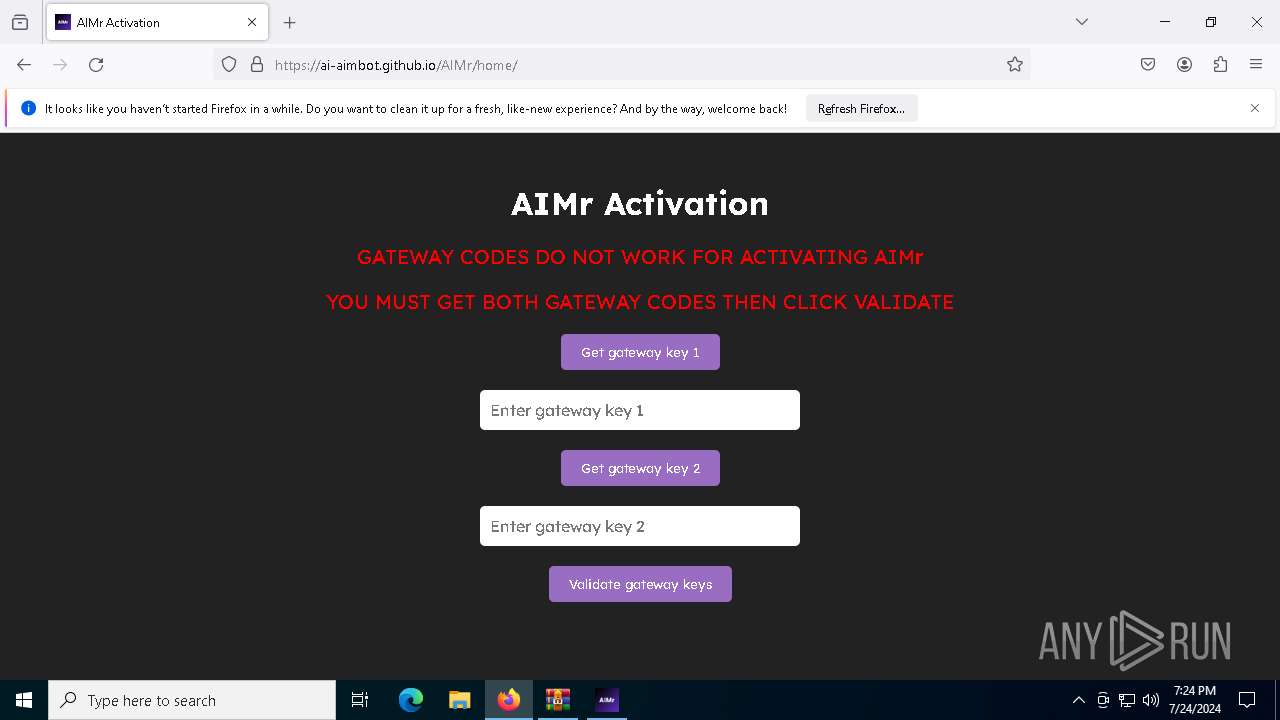
2284 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
2284 | svchost.exe | Misc activity | ET INFO URL Shortener Service Domain in DNS Lookup (is .gd) |
2284 | svchost.exe | Misc activity | ET INFO URL Shortener Service Domain in DNS Lookup (is .gd) |
2284 | svchost.exe | Misc activity | ET INFO URL Shortener Service Domain in DNS Lookup (is .gd) |
2284 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
2284 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
2284 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
7132 | firefox.exe | Misc activity | ET INFO External IP Address Lookup Domain (ipify .org) in TLS SNI |
2284 | svchost.exe | Misc activity | ET INFO External IP Lookup Domain (ipify .org) in DNS Lookup |
2284 | svchost.exe | Misc activity | ET INFO External IP Lookup Domain (ipify .org) in DNS Lookup |