| File name: | CyanideRaider.7z |
| Full analysis: | https://app.any.run/tasks/8cd66971-7b15-434d-8419-cde5f91b0144 |
| Verdict: | Malicious activity |
| Analysis date: | May 20, 2022, 23:51:26 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 3B08B9628547AB447E02D9A85E02071C |
| SHA1: | CFC9303EEB5724DDC51F5BAB5DF32601EAA7E153 |
| SHA256: | F50C5DCE7AB0765E2DA42245544D1D59B2DC4C4D42CDB6F30197CEB6016EE716 |
| SSDEEP: | 49152:+Ru7GtlbErvgqHc/f8rqPUfOkus3STHV3y2JXTV5FD:P7u2j88CCW5yWXzh |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 2932)
Application was dropped or rewritten from another process
- CyanideRaider.exe (PID: 3860)
Drops executable file immediately after starts
- CyanideRaider.exe (PID: 3860)
- WinRAR.exe (PID: 568)
Changes the autorun value in the registry
- CyanideRaider.exe (PID: 3860)
SUSPICIOUS
Checks supported languages
- CyanideRaider.exe (PID: 3860)
- WinRAR.exe (PID: 568)
Reads the computer name
- WinRAR.exe (PID: 568)
- CyanideRaider.exe (PID: 3860)
Executable content was dropped or overwritten
- CyanideRaider.exe (PID: 3860)
- WinRAR.exe (PID: 568)
Drops a file with a compile date too recent
- CyanideRaider.exe (PID: 3860)
- WinRAR.exe (PID: 568)
INFO
Manual execution by user
- CyanideRaider.exe (PID: 3860)
- taskmgr.exe (PID: 2628)
Checks supported languages
- taskmgr.exe (PID: 2628)
Reads the computer name
- taskmgr.exe (PID: 2628)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
37
Monitored processes
4
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 568 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\CyanideRaider.7z" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2628 | "C:\Windows\system32\taskmgr.exe" /4 | C:\Windows\system32\taskmgr.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Task Manager Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2932 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe2_ Global\UsGthrCtrlFltPipeMssGthrPipe2 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\system32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7601.24542 (win7sp1_ldr_escrow.191209-2211) Modules
| |||||||||||||||
| 3860 | "C:\Users\admin\Desktop\CyanideRaider\CyanideRaider.exe" | C:\Users\admin\Desktop\CyanideRaider\CyanideRaider.exe | Explorer.EXE | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
2 184
Read events
2 106
Write events
78
Delete events
0
Modification events
| (PID) Process: | (568) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (568) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (568) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (568) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (568) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (568) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\CyanideRaider.7z | |||
| (PID) Process: | (568) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (568) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (568) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (568) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
4
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3860 | CyanideRaider.exe | C:\Users\admin\AppData\Local\Minecraft\Gravity.exe | executable | |
MD5:— | SHA256:— | |||
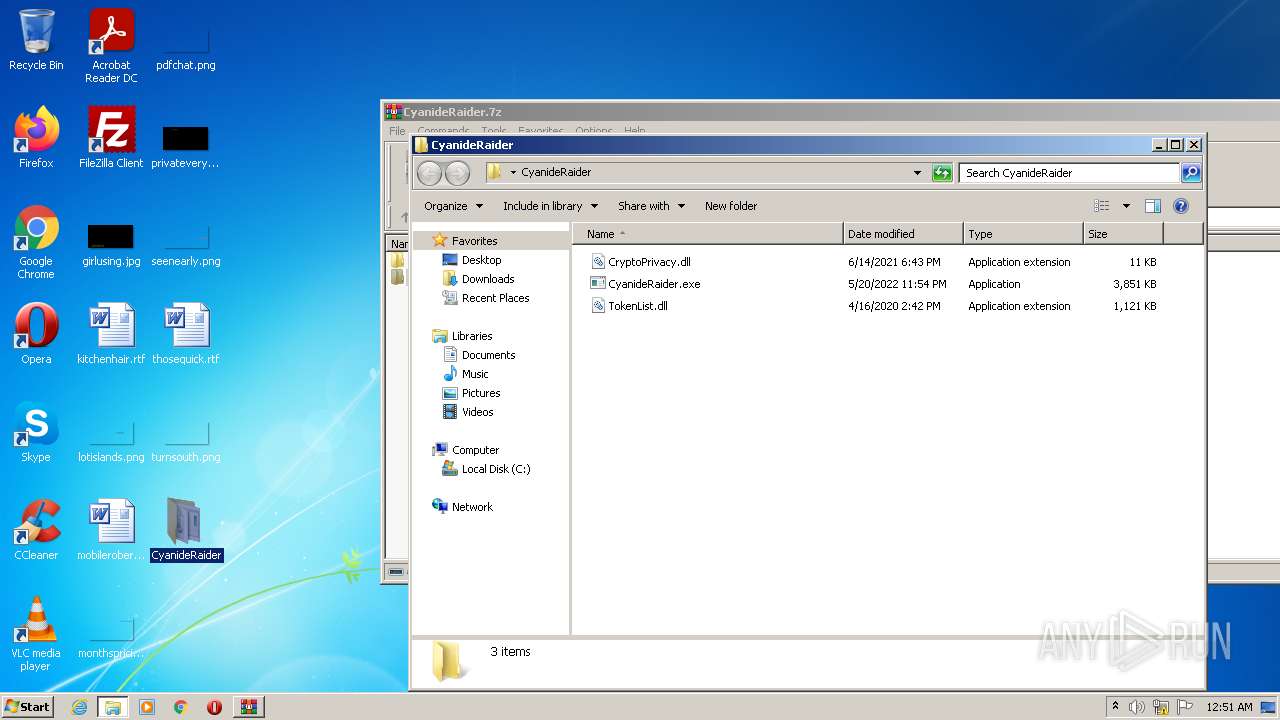
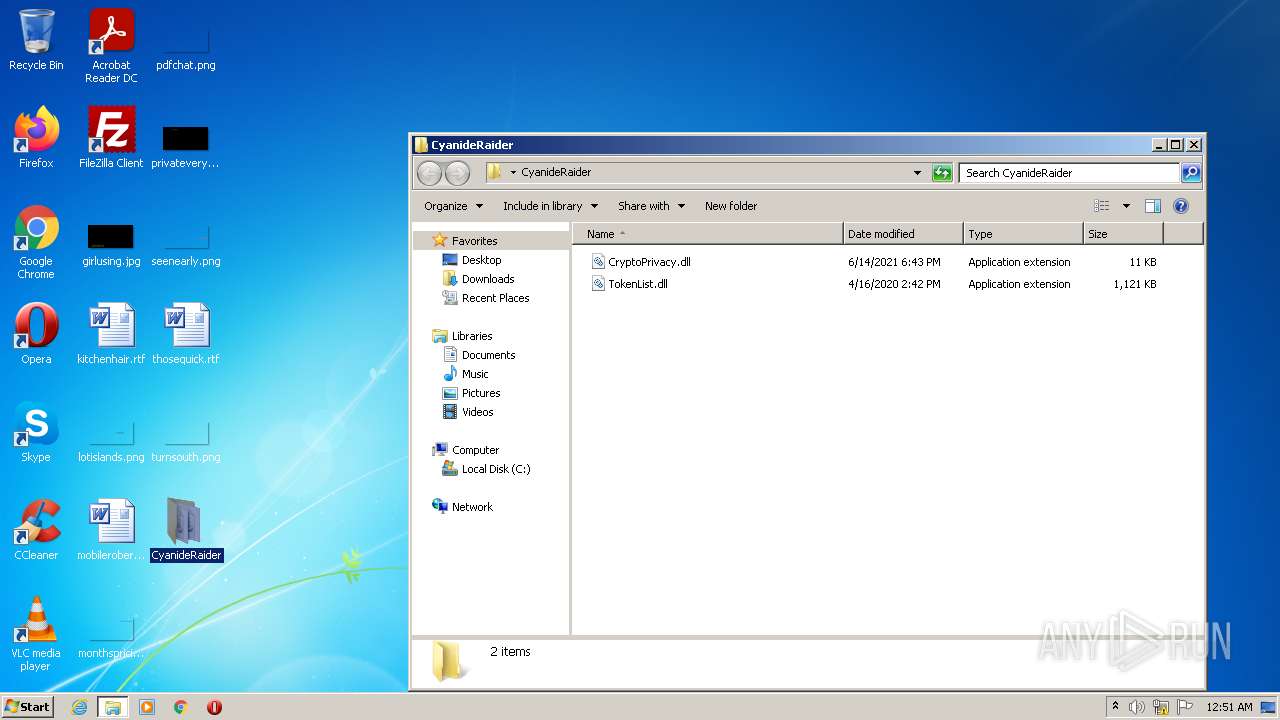
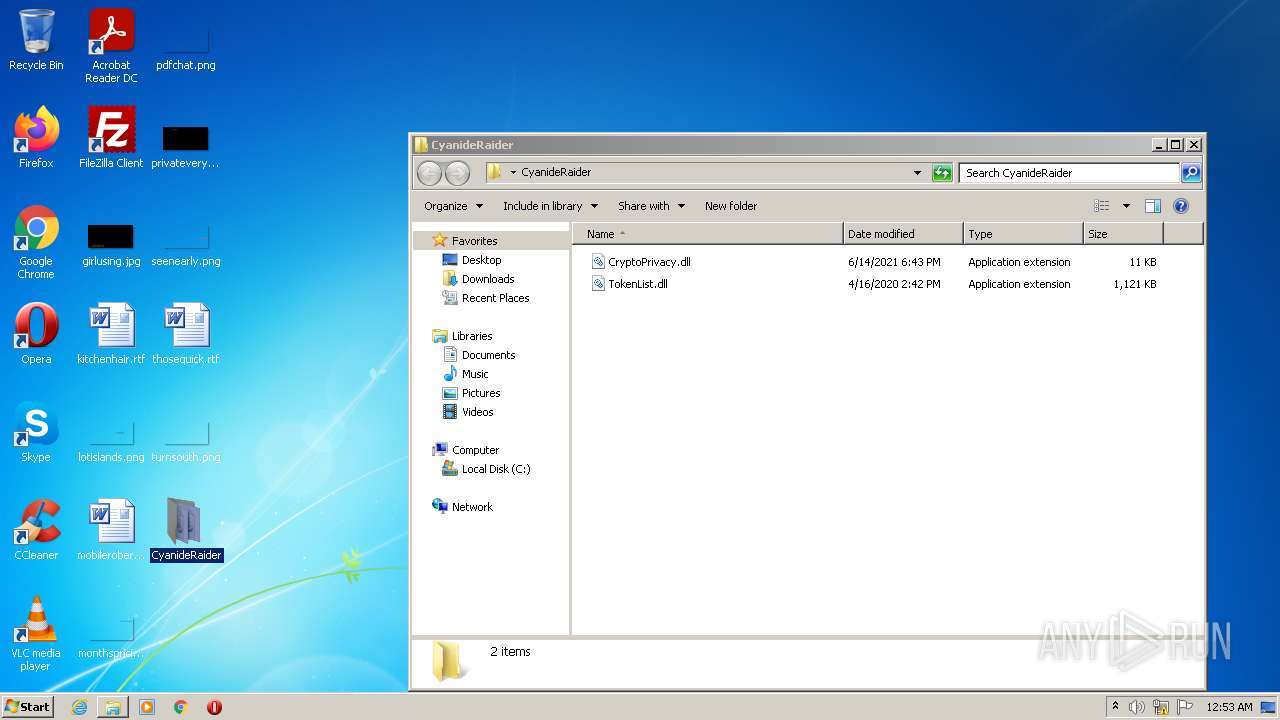
| 568 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa568.35663\CyanideRaider\CryptoPrivacy.dll | executable | |
MD5:— | SHA256:— | |||
| 568 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa568.35663\CyanideRaider\CyanideRaider.exe | executable | |
MD5:— | SHA256:— | |||
| 568 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa568.35663\CyanideRaider\TokenList.dll | executable | |
MD5:DE0069C4097C987BD30EBE8155A8AF35 | SHA256:83445595D38A8E33513B33DFC201983AF4746E5327C9BED470A6282D91D539B6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
8
DNS requests
6
Threats
5
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3860 | CyanideRaider.exe | 67.6.43.147:88 | zero-gravity.ddns.net | Qwest Communications Company, LLC | US | unknown |
— | — | 67.6.43.147:88 | zero-gravity.ddns.net | Qwest Communications Company, LLC | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
zero-gravity.ddns.net |
| unknown |
dns.msftncsi.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.ddns .net |
— | — | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.ddns .net |
— | — | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.ddns .net |
— | — | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.ddns .net |
— | — | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.ddns .net |