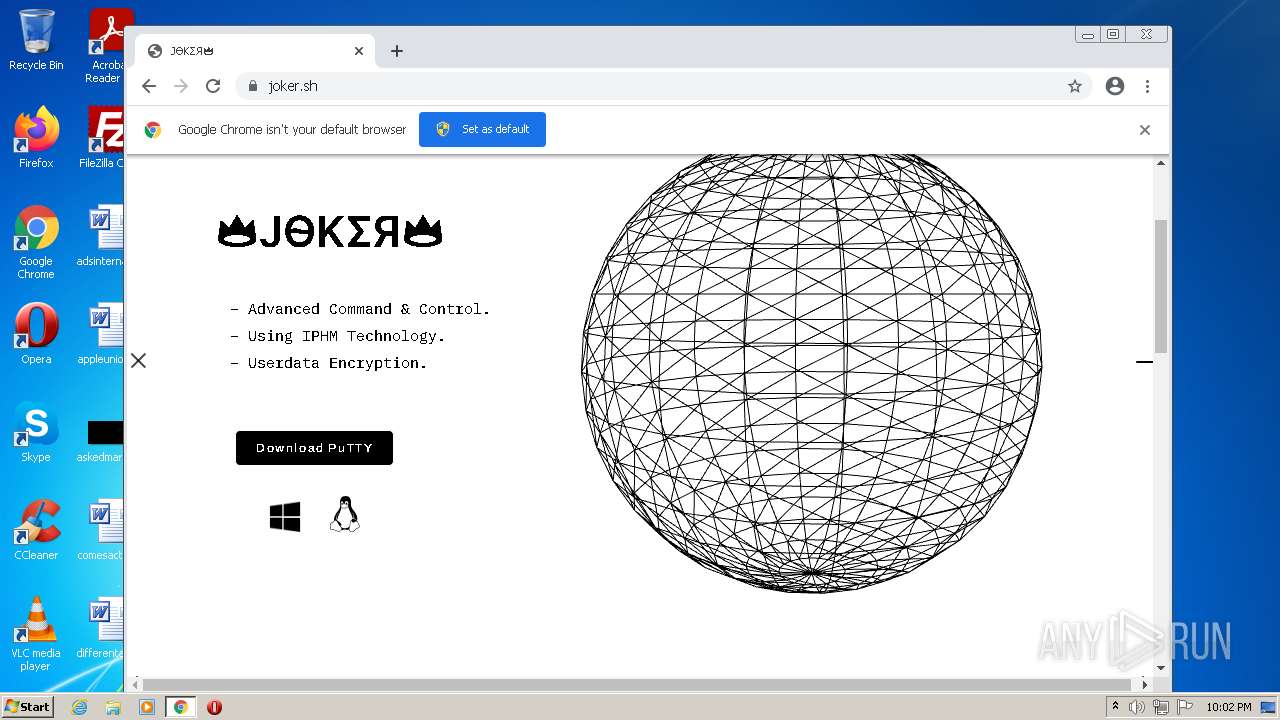
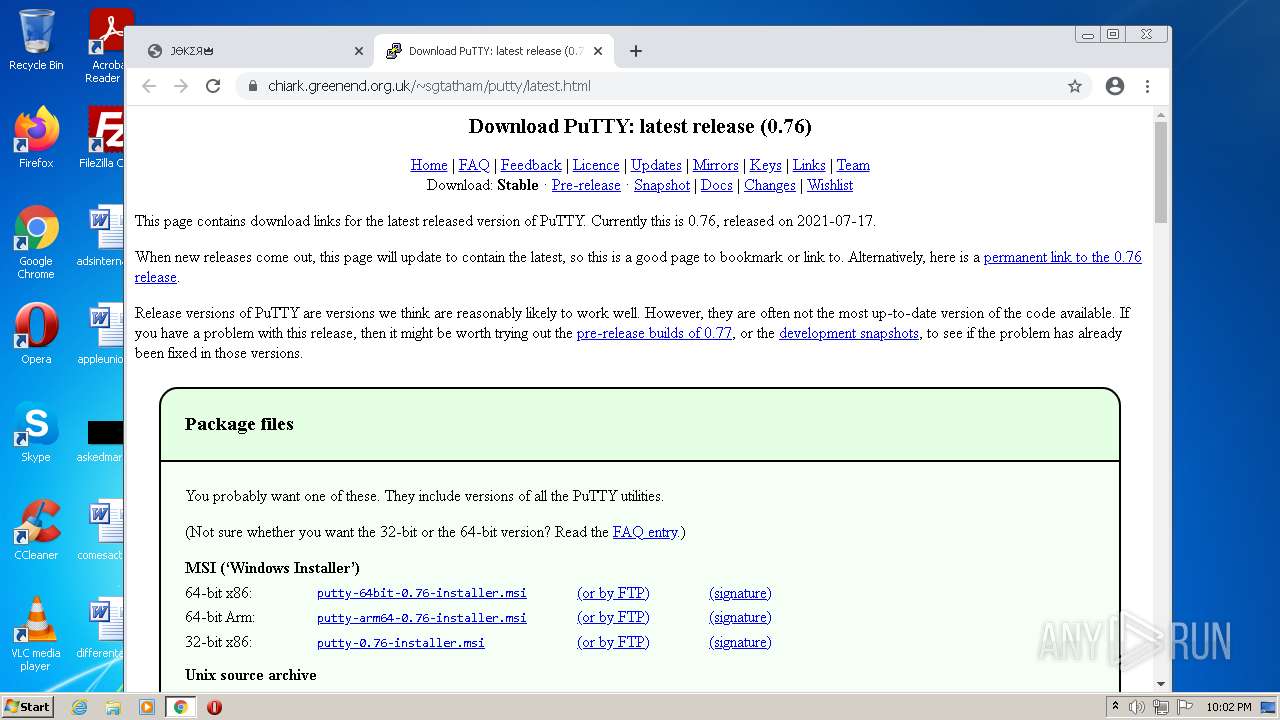
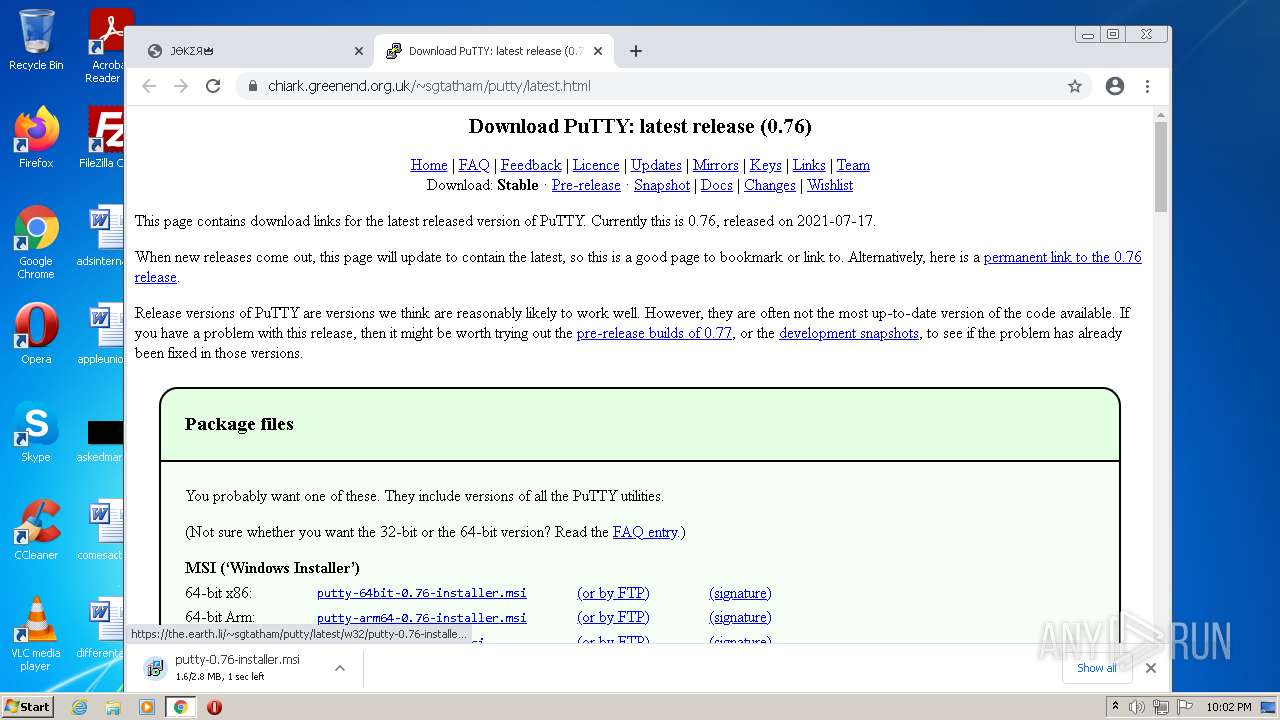
| URL: | https://joker.sh/ |
| Full analysis: | https://app.any.run/tasks/f2f1ffde-300a-4e50-b721-8b258bd164e2 |
| Verdict: | Malicious activity |
| Analysis date: | May 20, 2022, 21:02:24 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 4AFF4824DDF05952630C0640DF9BF5B0 |
| SHA1: | 33C185F703CF390446AC7C64C976B6603C0C3BA9 |
| SHA256: | F4E620D5C5E954C56013EFD68AA2AC93D715EA3D9D94E06F3A068D5E537884ED |
| SSDEEP: | 3:N8qF:2qF |
MALICIOUS
Drops executable file immediately after starts
- msiexec.exe (PID: 1004)
- msiexec.exe (PID: 1984)
Application was dropped or rewritten from another process
- putty.exe (PID: 2264)
SUSPICIOUS
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 1040)
Modifies files in Chrome extension folder
- chrome.exe (PID: 3192)
Executable content was dropped or overwritten
- chrome.exe (PID: 1372)
- chrome.exe (PID: 3192)
- msiexec.exe (PID: 1004)
- msiexec.exe (PID: 1984)
Starts Microsoft Installer
- chrome.exe (PID: 3192)
Reads the computer name
- msiexec.exe (PID: 1984)
- MsiExec.exe (PID: 1432)
- putty.exe (PID: 2264)
Reads the Windows organization settings
- msiexec.exe (PID: 1004)
- msiexec.exe (PID: 1984)
Drops a file with a compile date too recent
- msiexec.exe (PID: 1004)
- msiexec.exe (PID: 1984)
Checks supported languages
- msiexec.exe (PID: 1984)
- MsiExec.exe (PID: 1432)
- putty.exe (PID: 2264)
Executed as Windows Service
- vssvc.exe (PID: 2876)
Reads Windows owner or organization settings
- msiexec.exe (PID: 1004)
- msiexec.exe (PID: 1984)
Reads Environment values
- vssvc.exe (PID: 2876)
Creates a directory in Program Files
- msiexec.exe (PID: 1984)
Changes default file association
- msiexec.exe (PID: 1984)
INFO
Changes internet zones settings
- iexplore.exe (PID: 2692)
Checks supported languages
- iexplore.exe (PID: 2692)
- iexplore.exe (PID: 1040)
- chrome.exe (PID: 3192)
- chrome.exe (PID: 1396)
- chrome.exe (PID: 1372)
- chrome.exe (PID: 508)
- chrome.exe (PID: 4016)
- chrome.exe (PID: 2760)
- chrome.exe (PID: 1988)
- chrome.exe (PID: 2328)
- chrome.exe (PID: 1436)
- chrome.exe (PID: 2740)
- chrome.exe (PID: 2772)
- chrome.exe (PID: 2144)
- chrome.exe (PID: 2136)
- chrome.exe (PID: 3028)
- chrome.exe (PID: 2368)
- msiexec.exe (PID: 1004)
- vssvc.exe (PID: 2876)
- chrome.exe (PID: 2928)
- chrome.exe (PID: 3196)
- chrome.exe (PID: 2484)
- NOTEPAD.EXE (PID: 412)
- chrome.exe (PID: 1360)
- chrome.exe (PID: 4012)
- chrome.exe (PID: 1496)
- chrome.exe (PID: 2980)
- chrome.exe (PID: 3868)
- chrome.exe (PID: 2468)
Reads the computer name
- iexplore.exe (PID: 2692)
- iexplore.exe (PID: 1040)
- chrome.exe (PID: 3192)
- chrome.exe (PID: 1372)
- chrome.exe (PID: 508)
- chrome.exe (PID: 1988)
- chrome.exe (PID: 2144)
- msiexec.exe (PID: 1004)
- chrome.exe (PID: 2368)
- vssvc.exe (PID: 2876)
- chrome.exe (PID: 1360)
- chrome.exe (PID: 4012)
- chrome.exe (PID: 1496)
Application launched itself
- iexplore.exe (PID: 2692)
- chrome.exe (PID: 3192)
- msiexec.exe (PID: 1984)
Checks Windows Trust Settings
- iexplore.exe (PID: 1040)
- iexplore.exe (PID: 2692)
- chrome.exe (PID: 3192)
- msiexec.exe (PID: 1004)
- msiexec.exe (PID: 1984)
Reads settings of System Certificates
- iexplore.exe (PID: 1040)
- iexplore.exe (PID: 2692)
- chrome.exe (PID: 1372)
- chrome.exe (PID: 3192)
- msiexec.exe (PID: 1004)
- msiexec.exe (PID: 1984)
Reads the date of Windows installation
- iexplore.exe (PID: 2692)
- chrome.exe (PID: 4012)
Manual execution by user
- chrome.exe (PID: 3192)
- putty.exe (PID: 2264)
Reads the hosts file
- chrome.exe (PID: 3192)
- chrome.exe (PID: 1372)
Creates files in the program directory
- msiexec.exe (PID: 1984)
Creates a software uninstall entry
- msiexec.exe (PID: 1984)
Searches for installed software
- msiexec.exe (PID: 1984)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
70
Monitored processes
32
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
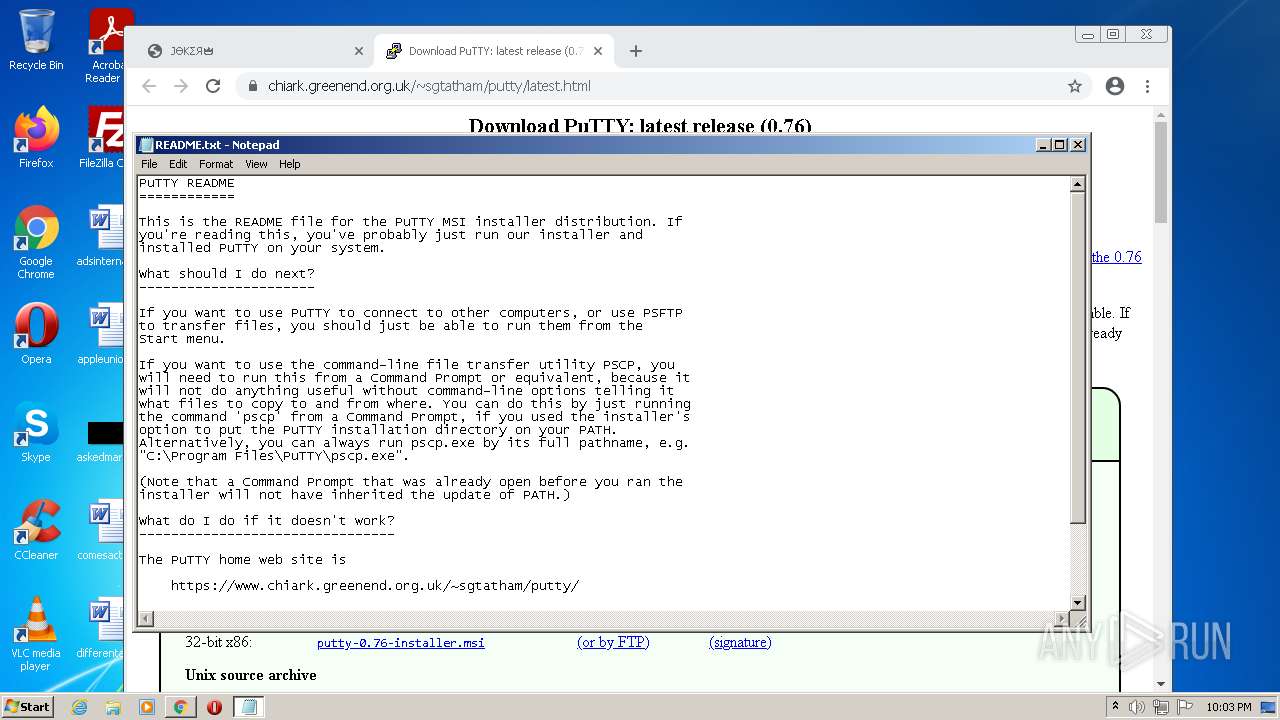
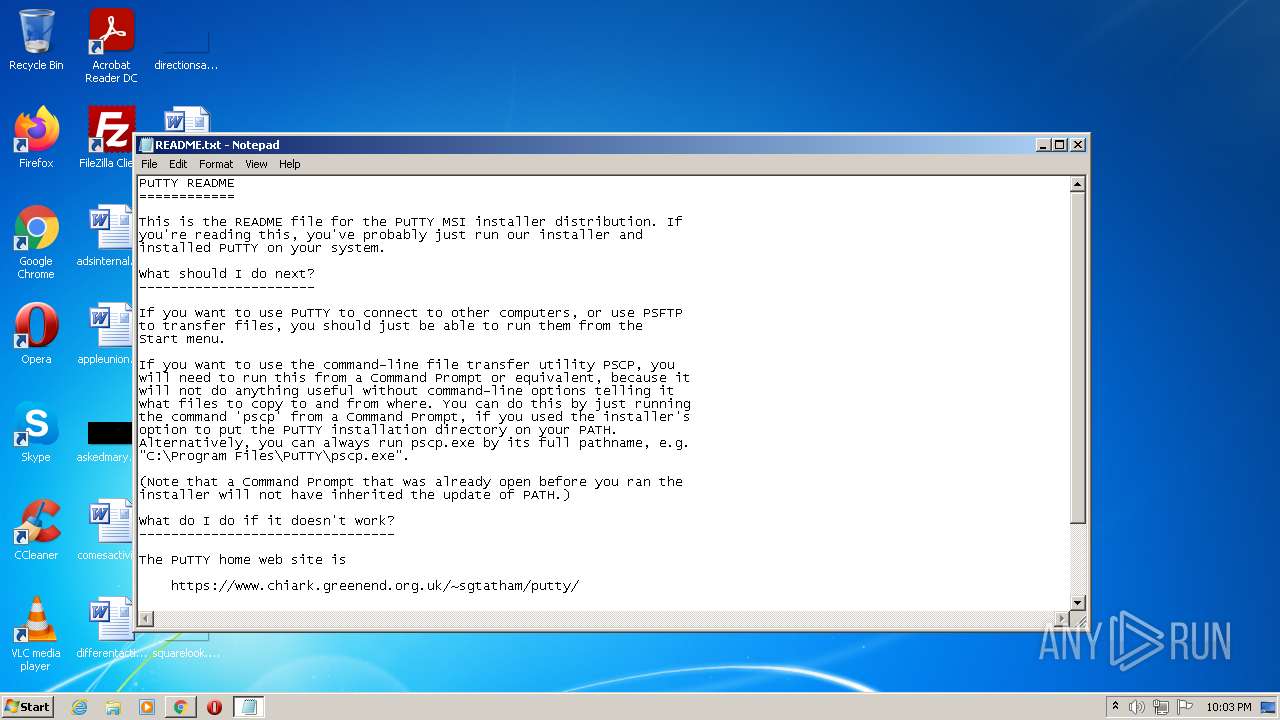
| 412 | "C:\Windows\system32\NOTEPAD.EXE" C:\Program Files\PuTTY\README.txt | C:\Windows\system32\NOTEPAD.EXE | — | MsiExec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 508 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1048,17722713018229338308,12365962866017576924,131072 --enable-features=PasswordImport --gpu-preferences=MAAAAAAAAADgAAAwAAAAAAAAAAAAAAAAAABgAAAAAAAQAAAAAAAAAAAAAAAAAAAAKAAAAAQAAAAgAAAAAAAAACgAAAAAAAAAMAAAAAAAAAA4AAAAAAAAABAAAAAAAAAAAAAAAAUAAAAQAAAAAAAAAAAAAAAGAAAAEAAAAAAAAAABAAAABQAAABAAAAAAAAAAAQAAAAYAAAA= --mojo-platform-channel-handle=1060 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
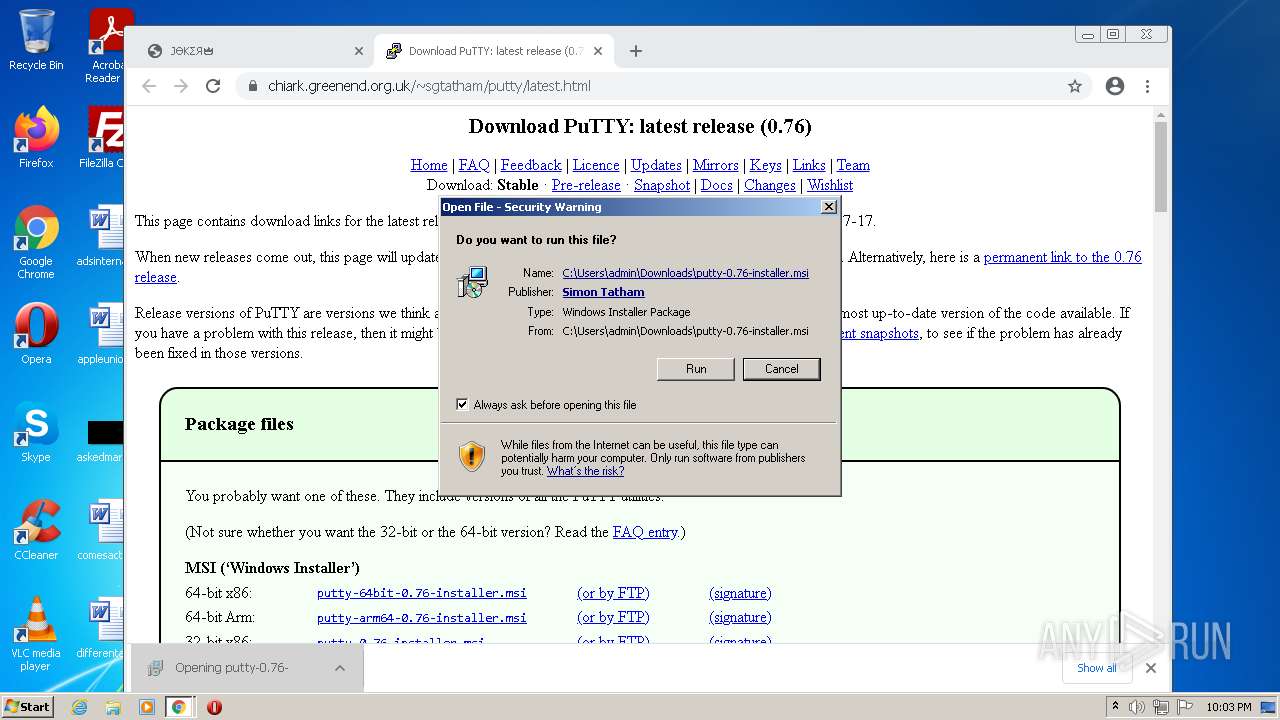
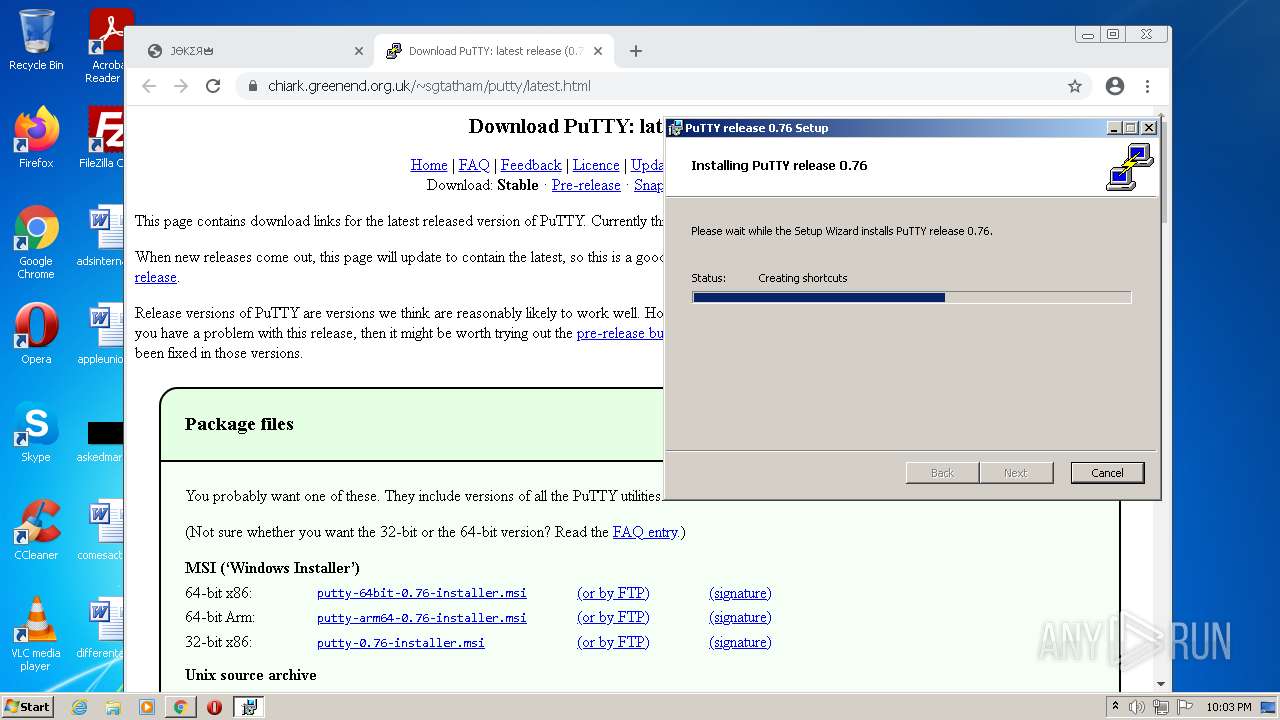
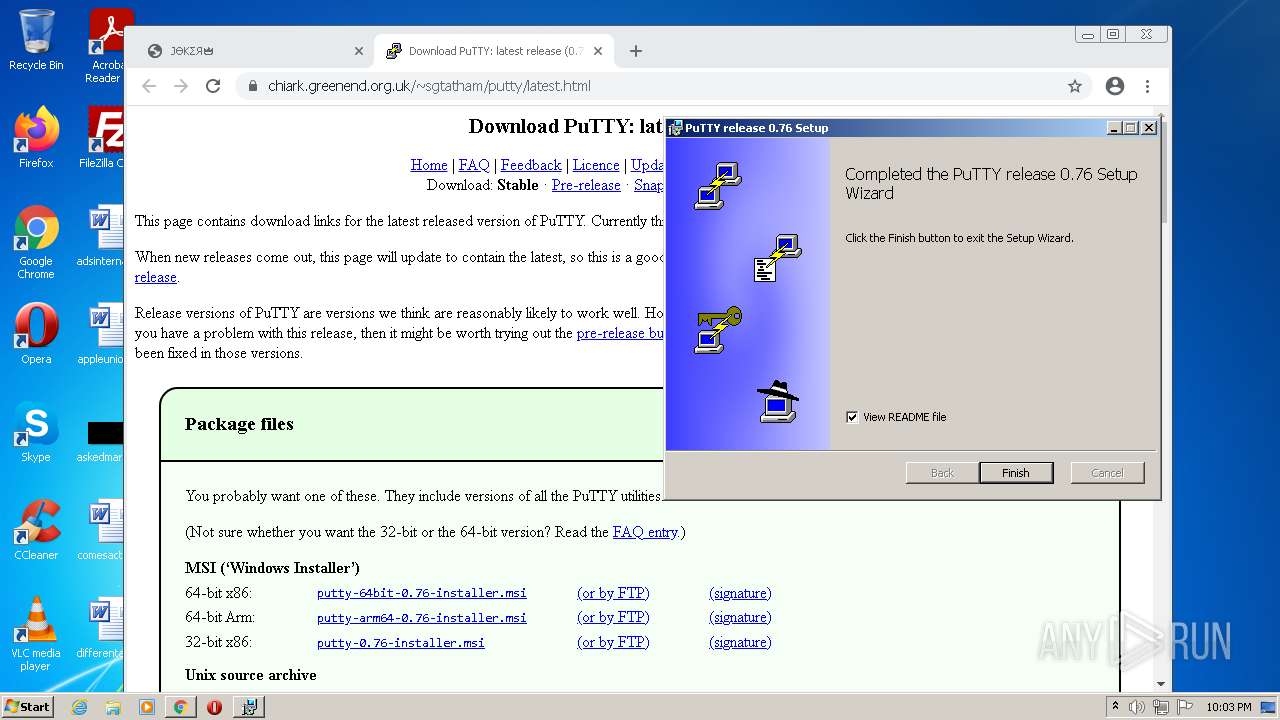
| 1004 | "C:\Windows\System32\msiexec.exe" /i "C:\Users\admin\Downloads\putty-0.76-installer.msi" | C:\Windows\System32\msiexec.exe | chrome.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1040 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2692 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1360 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1048,17722713018229338308,12365962866017576924,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=4344 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1372 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --field-trial-handle=1048,17722713018229338308,12365962866017576924,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=network --mojo-platform-channel-handle=1316 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1396 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=86.0.4240.198 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd4,0x6e95d988,0x6e95d998,0x6e95d9a4 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1432 | C:\Windows\system32\MsiExec.exe -Embedding 81D4A863FC4ED07D7F24C78E0FB25F15 C | C:\Windows\system32\MsiExec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1436 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1048,17722713018229338308,12365962866017576924,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=2940 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1496 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1048,17722713018229338308,12365962866017576924,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=3880 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
Total events
37 395
Read events
36 812
Write events
561
Delete events
22
Modification events
| (PID) Process: | (2692) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (2692) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (2692) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30960780 | |||
| (PID) Process: | (2692) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (2692) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30960780 | |||
| (PID) Process: | (2692) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2692) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2692) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2692) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2692) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
12
Suspicious files
194
Text files
138
Unknown types
26
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3192 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-628801F2-C78.pma | — | |
MD5:— | SHA256:— | |||
| 2692 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Last Active\RecoveryStore.{42C873D0-1D90-11EB-BA2C-12A9866C77DE}.dat | binary | |
MD5:— | SHA256:— | |||
| 2692 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFEE4A5D97C7E0B2AC.TMP | gmc | |
MD5:— | SHA256:— | |||
| 2692 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFC1FD42CD3891E20B.TMP | gmc | |
MD5:— | SHA256:— | |||
| 2692 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF3EF51ADA9902172A.TMP | gmc | |
MD5:— | SHA256:— | |||
| 2692 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Last Active\{2E944E0C-D880-11EC-BF60-12A9866C77DE}.dat | binary | |
MD5:— | SHA256:— | |||
| 2692 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{2795C809-D880-11EC-BF60-12A9866C77DE}.dat | binary | |
MD5:— | SHA256:— | |||
| 1372 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Cache\index | binary | |
MD5:— | SHA256:— | |||
| 3192 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RF107dbd.TMP | text | |
MD5:64AD8ED3E666540337BA541C549F72F7 | SHA256:BECBDB08B5B37D203A85F2E974407334053BB1D2270F0B3C9A4DB963896F2206 | |||
| 1396 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\CrashpadMetrics.pma | binary | |
MD5:03C4F648043A88675A920425D824E1B3 | SHA256:F91DBB7C64B4582F529C968C480D2DCE1C8727390482F31E4355A27BB3D9B450 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
18
TCP/UDP connections
47
DNS requests
33
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
416 | svchost.exe | GET | 304 | 67.27.157.126:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?9b1f1ce816b98402 | US | — | — | whitelisted |
880 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ac6uhcfbxlex6uvq35lxbiuo4pua_9.35.0/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.35.0_all_ou4l2poiq7vz5pxjtnyxcnyqx4.crx3 | US | — | — | whitelisted |
880 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ac6uhcfbxlex6uvq35lxbiuo4pua_9.35.0/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.35.0_all_ou4l2poiq7vz5pxjtnyxcnyqx4.crx3 | US | binary | 9.74 Kb | whitelisted |
2692 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
880 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ac6uhcfbxlex6uvq35lxbiuo4pua_9.35.0/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.35.0_all_ou4l2poiq7vz5pxjtnyxcnyqx4.crx3 | US | binary | 5.65 Kb | whitelisted |
2692 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://crl3.digicert.com/Omniroot2025.crl | US | der | 7.78 Kb | whitelisted |
880 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ac6uhcfbxlex6uvq35lxbiuo4pua_9.35.0/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.35.0_all_ou4l2poiq7vz5pxjtnyxcnyqx4.crx3 | US | binary | 9.73 Kb | whitelisted |
880 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ac6uhcfbxlex6uvq35lxbiuo4pua_9.35.0/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.35.0_all_ou4l2poiq7vz5pxjtnyxcnyqx4.crx3 | US | binary | 9.73 Kb | whitelisted |
880 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/APhHMzuprJvS7ixvnAk_gdI_1/anGnv31dmOJhheXBnYQ3gw | US | binary | 3.69 Kb | whitelisted |
880 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/APhHMzuprJvS7ixvnAk_gdI_1/anGnv31dmOJhheXBnYQ3gw | US | binary | 45.0 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1040 | iexplore.exe | 188.114.97.10:443 | joker.sh | Cloudflare Inc | US | malicious |
1040 | iexplore.exe | 67.27.234.126:80 | ctldl.windowsupdate.com | Level 3 Communications, Inc. | US | suspicious |
2692 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
2692 | iexplore.exe | 67.27.234.126:80 | ctldl.windowsupdate.com | Level 3 Communications, Inc. | US | suspicious |
1372 | chrome.exe | 142.250.186.46:443 | clients2.google.com | Google Inc. | US | whitelisted |
1372 | chrome.exe | 142.250.185.131:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
1372 | chrome.exe | 142.250.184.237:443 | accounts.google.com | Google Inc. | US | suspicious |
1372 | chrome.exe | 142.250.184.196:443 | www.google.com | Google Inc. | US | whitelisted |
1372 | chrome.exe | 142.250.181.225:443 | clients2.googleusercontent.com | Google Inc. | US | whitelisted |
2692 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
joker.sh |
| malicious |
ctldl.windowsupdate.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
clients2.google.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com |
| malicious |
clients2.googleusercontent.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2264 | putty.exe | Attempted Information Leak | ET SCAN Potential SSH Scan OUTBOUND |