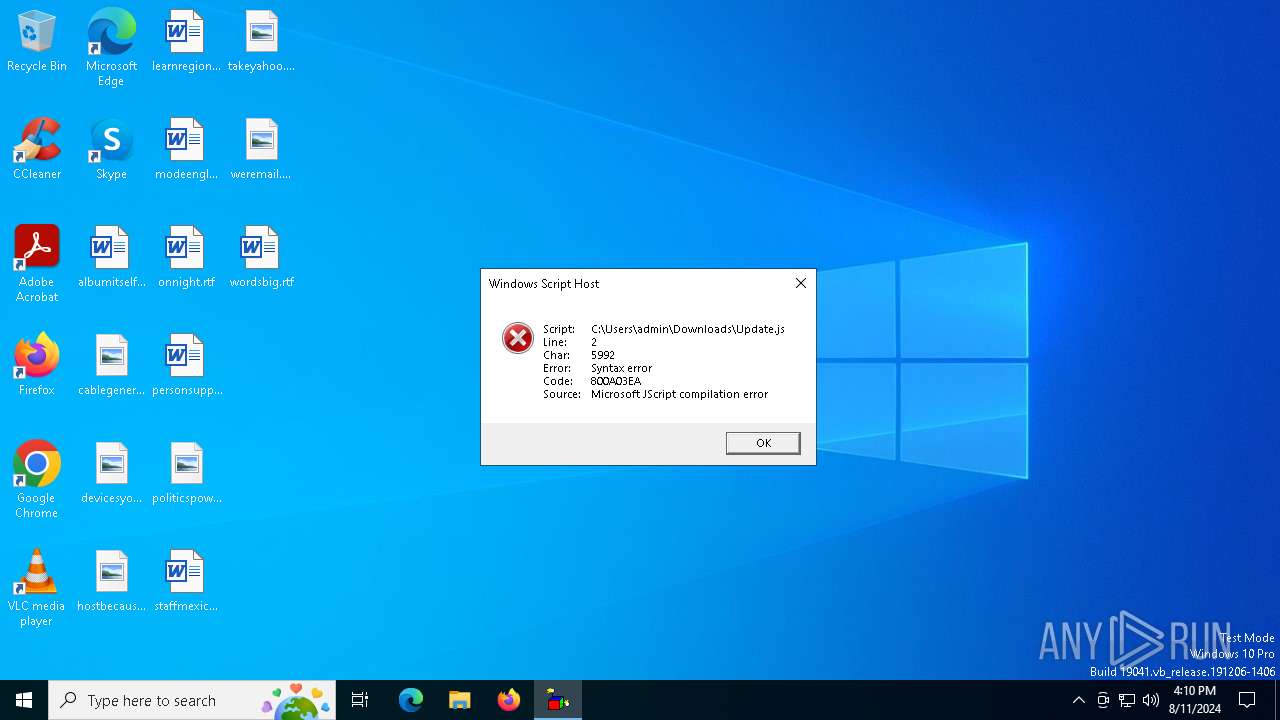
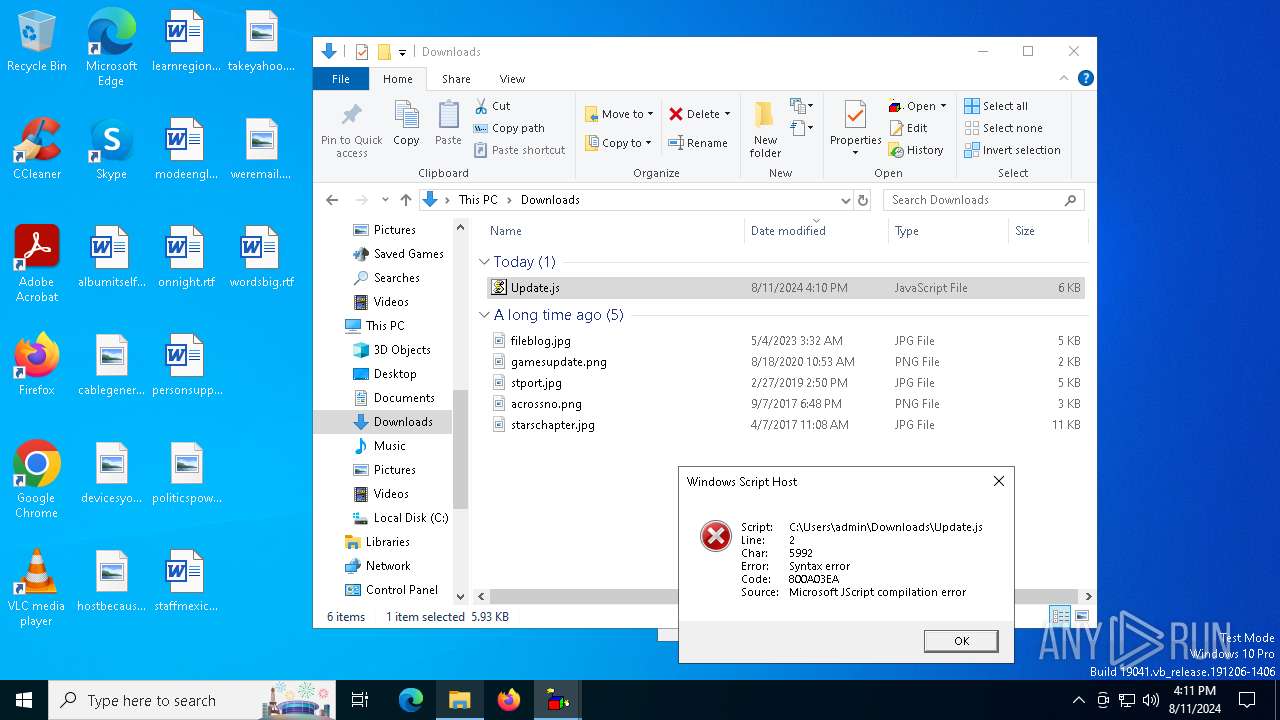
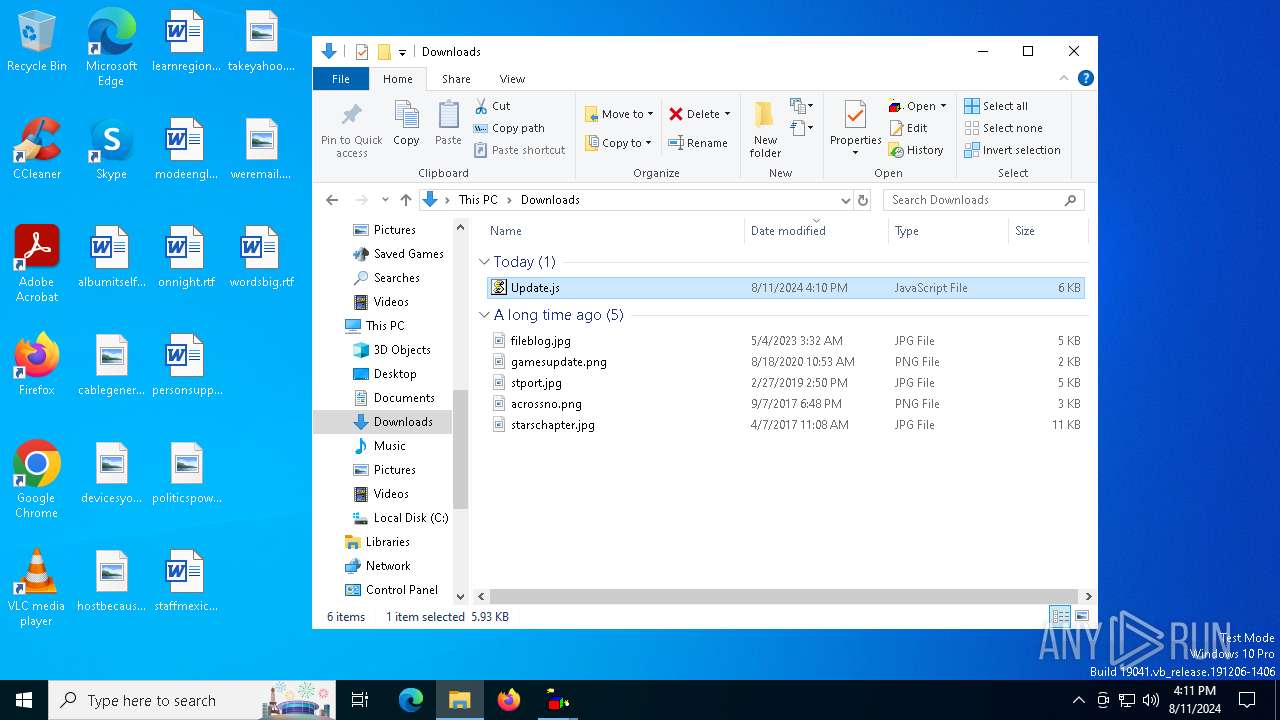
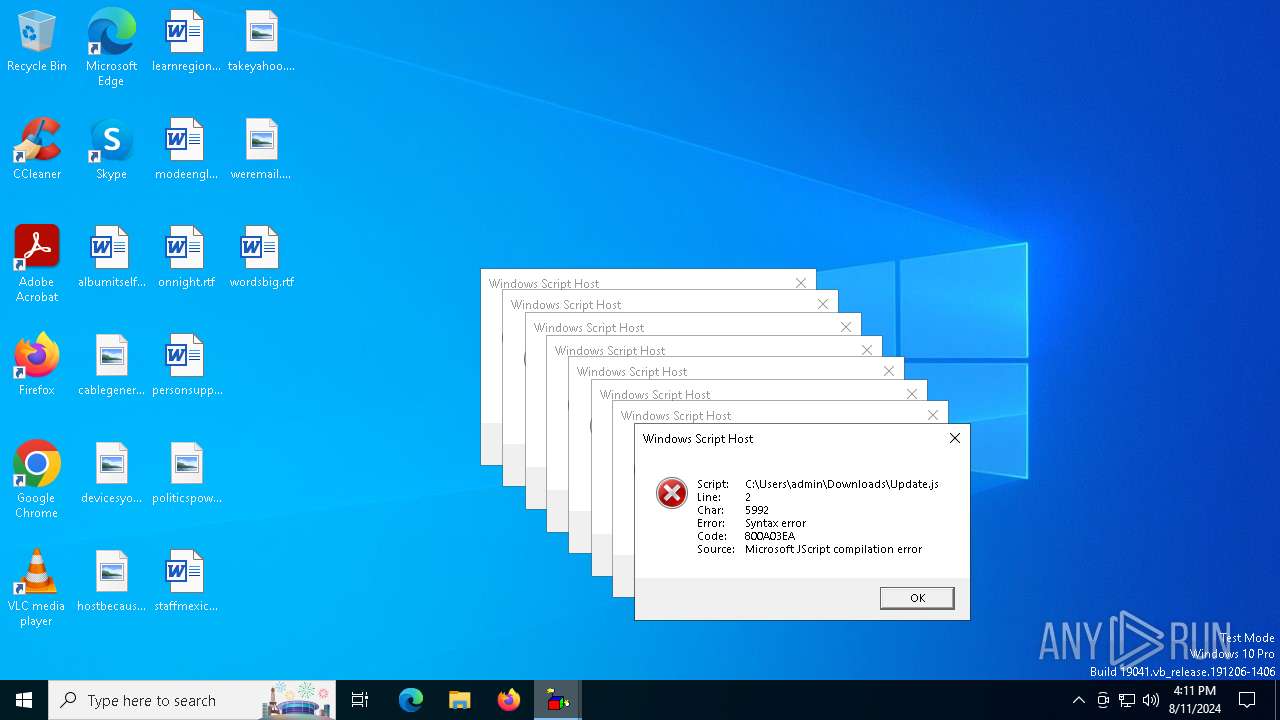
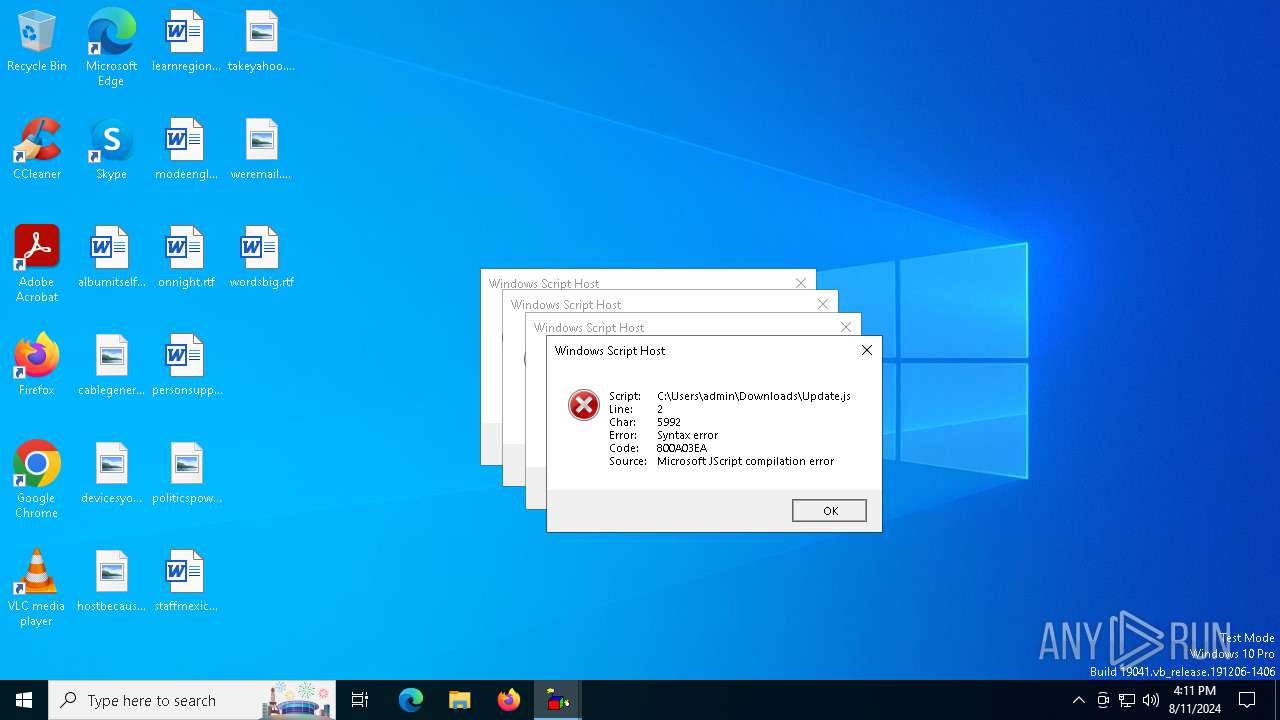
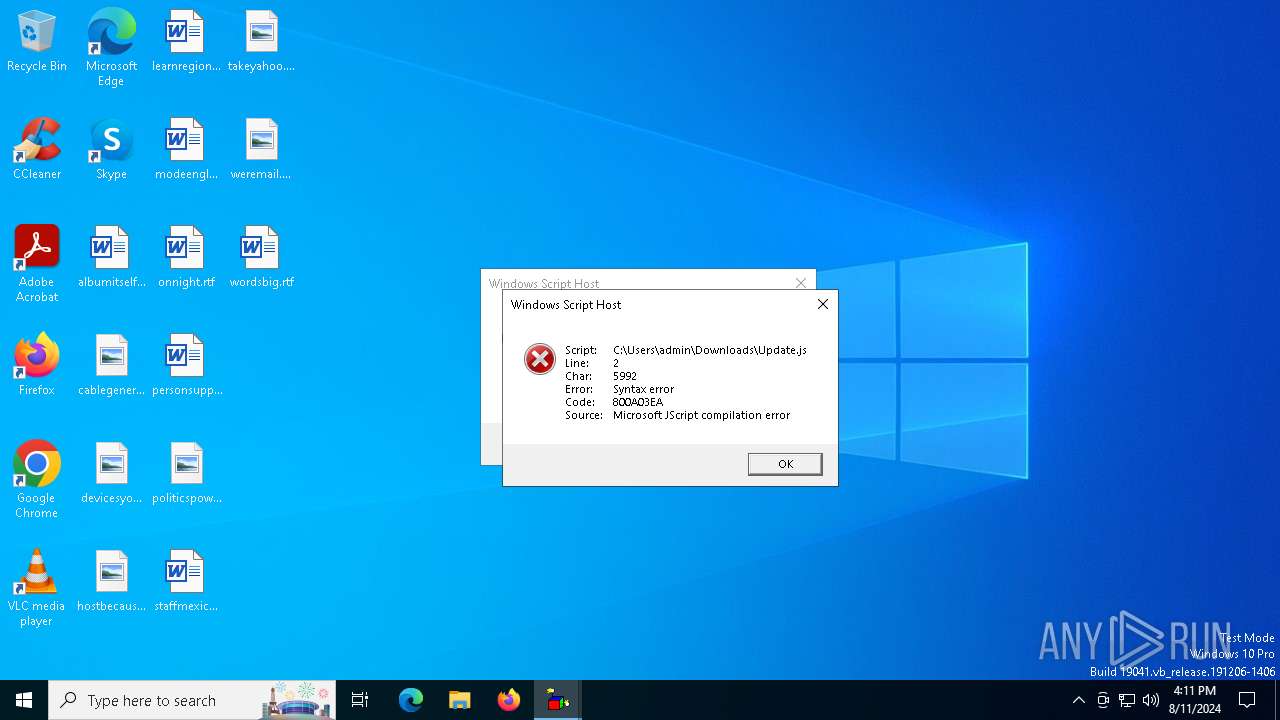
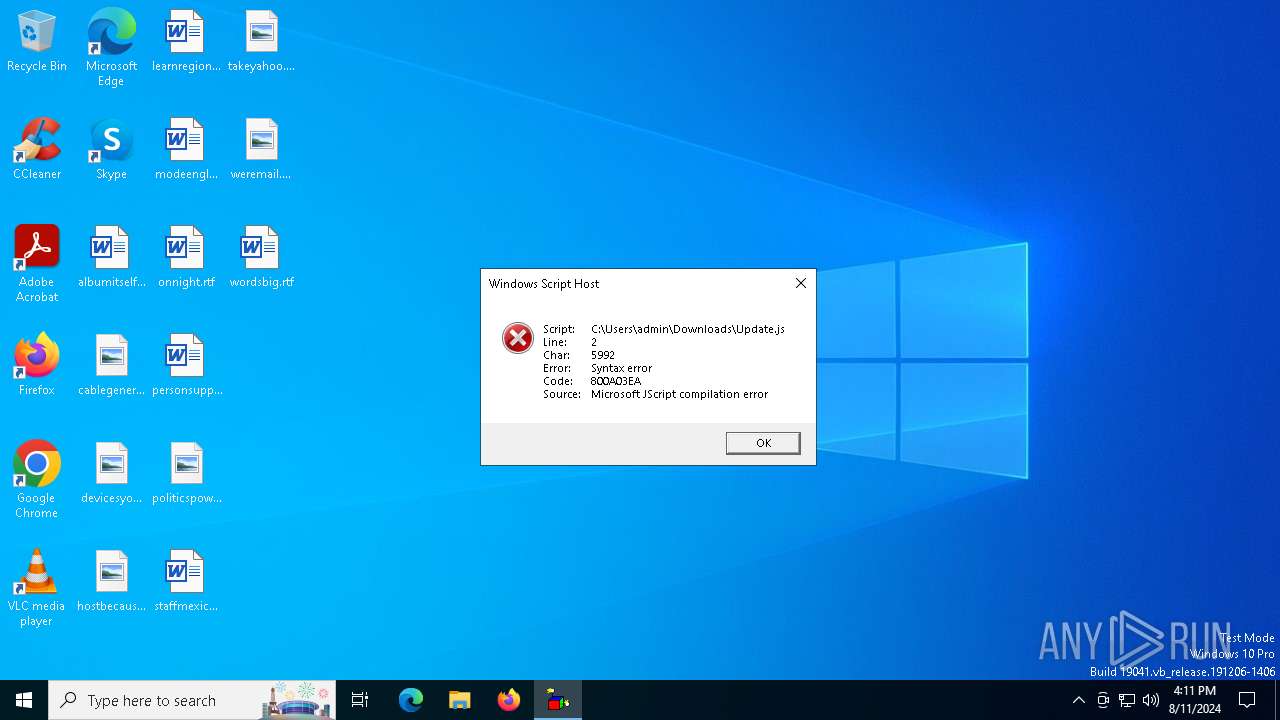
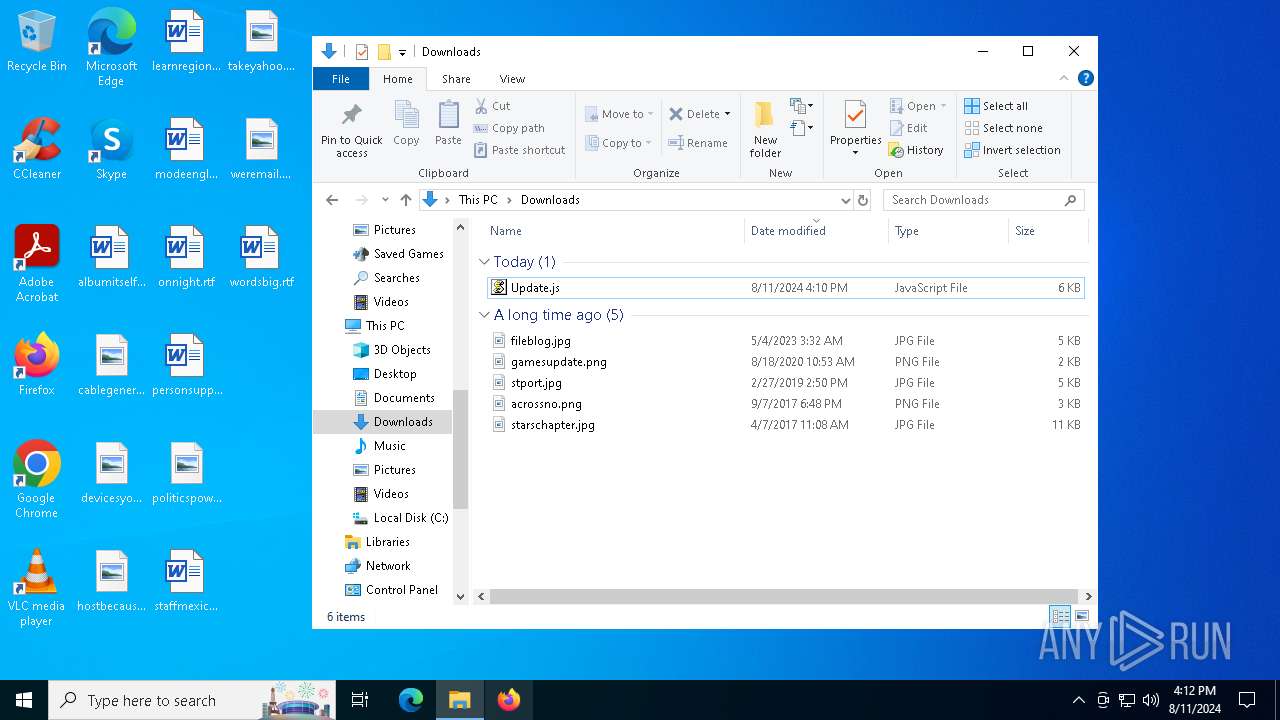
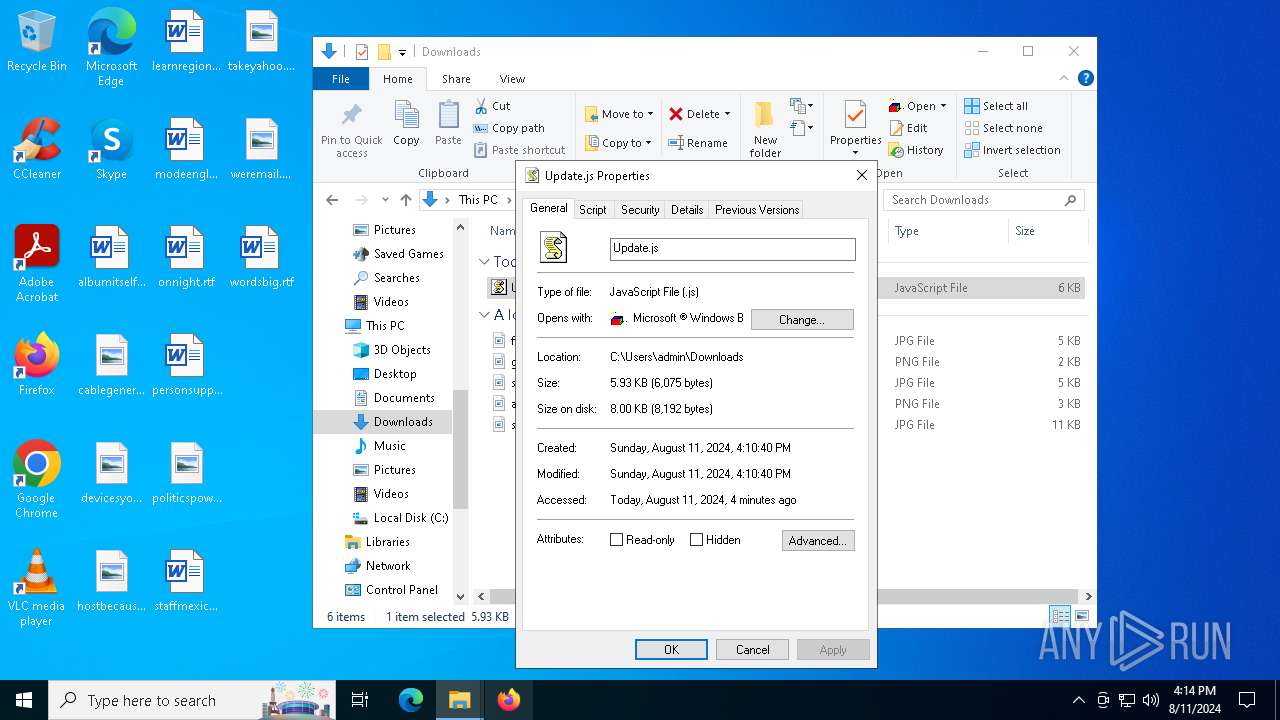
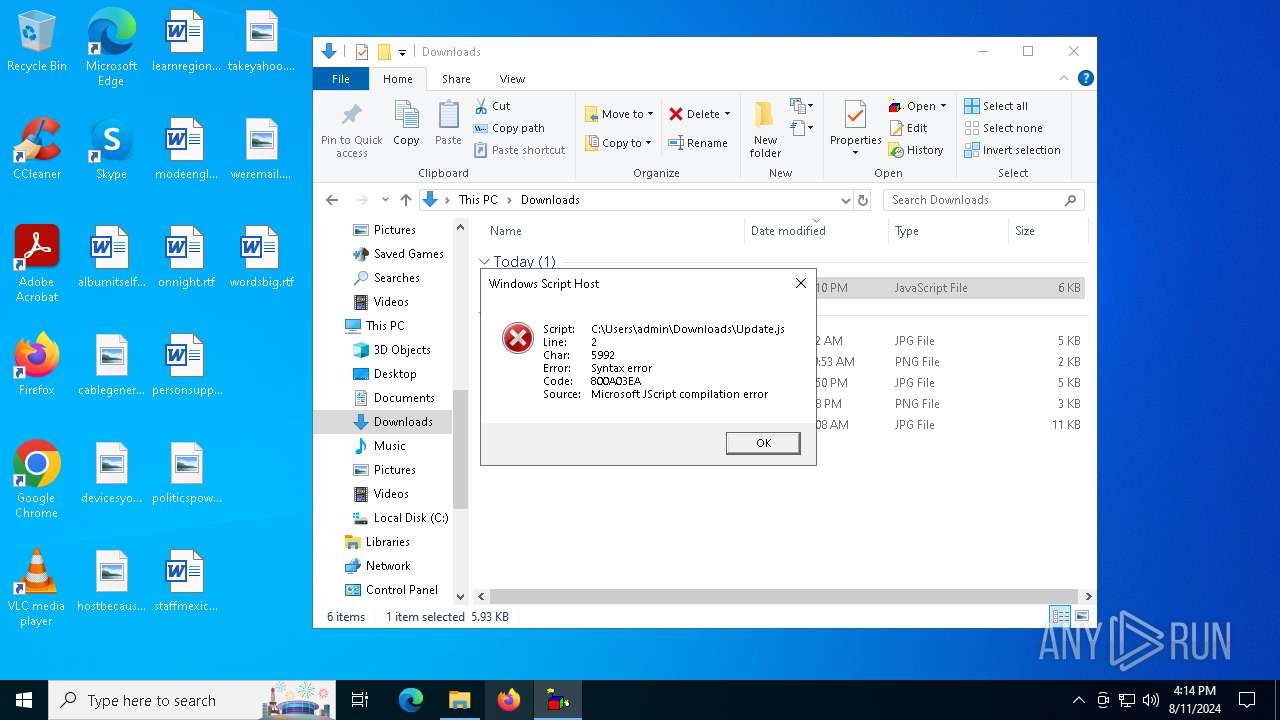
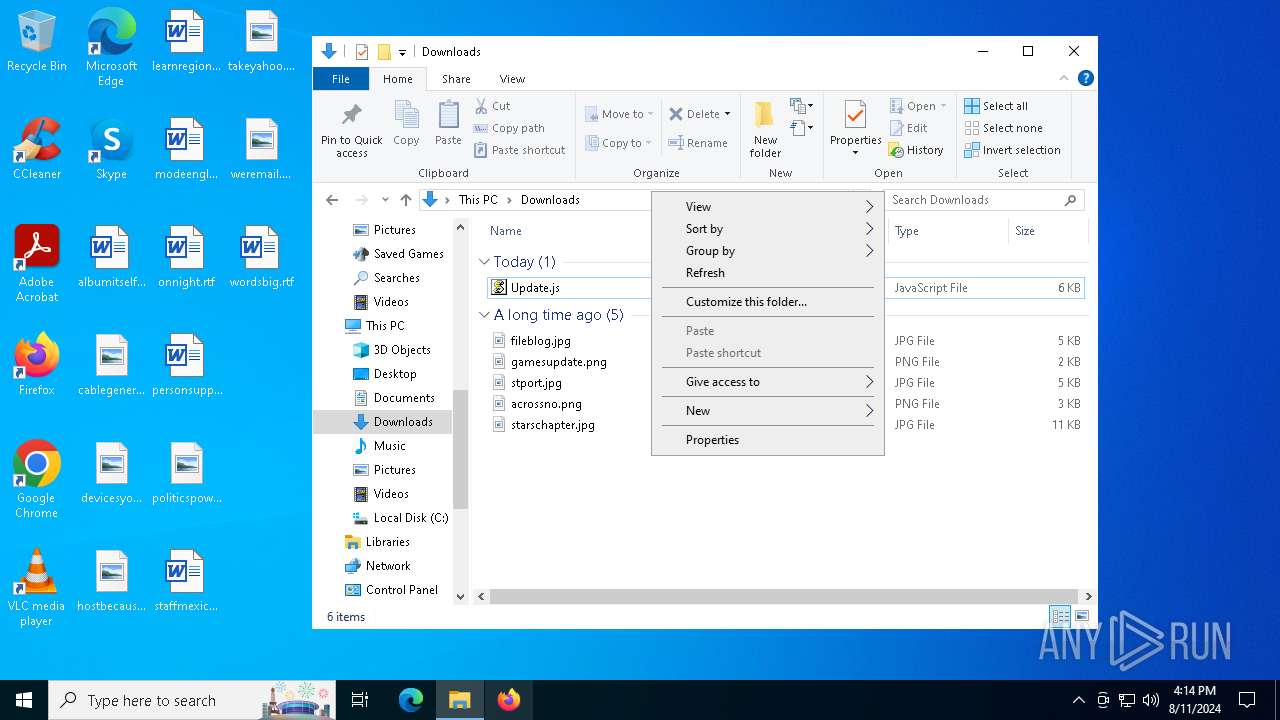
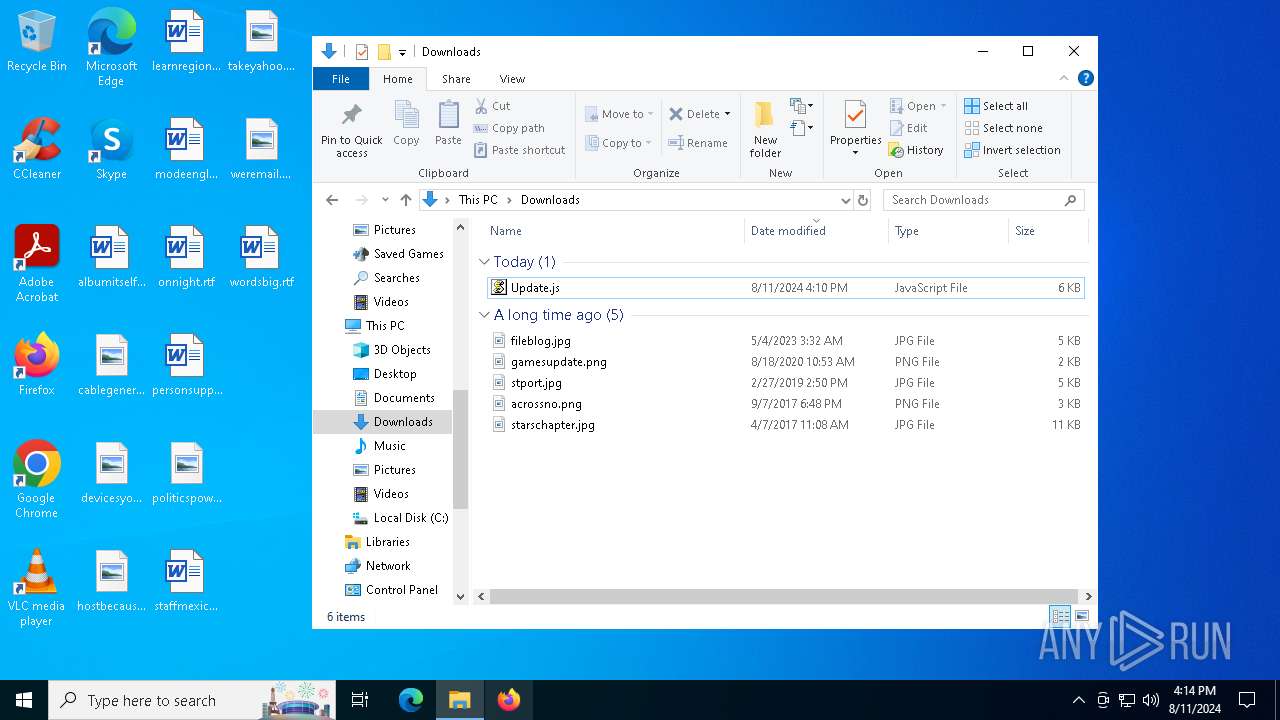
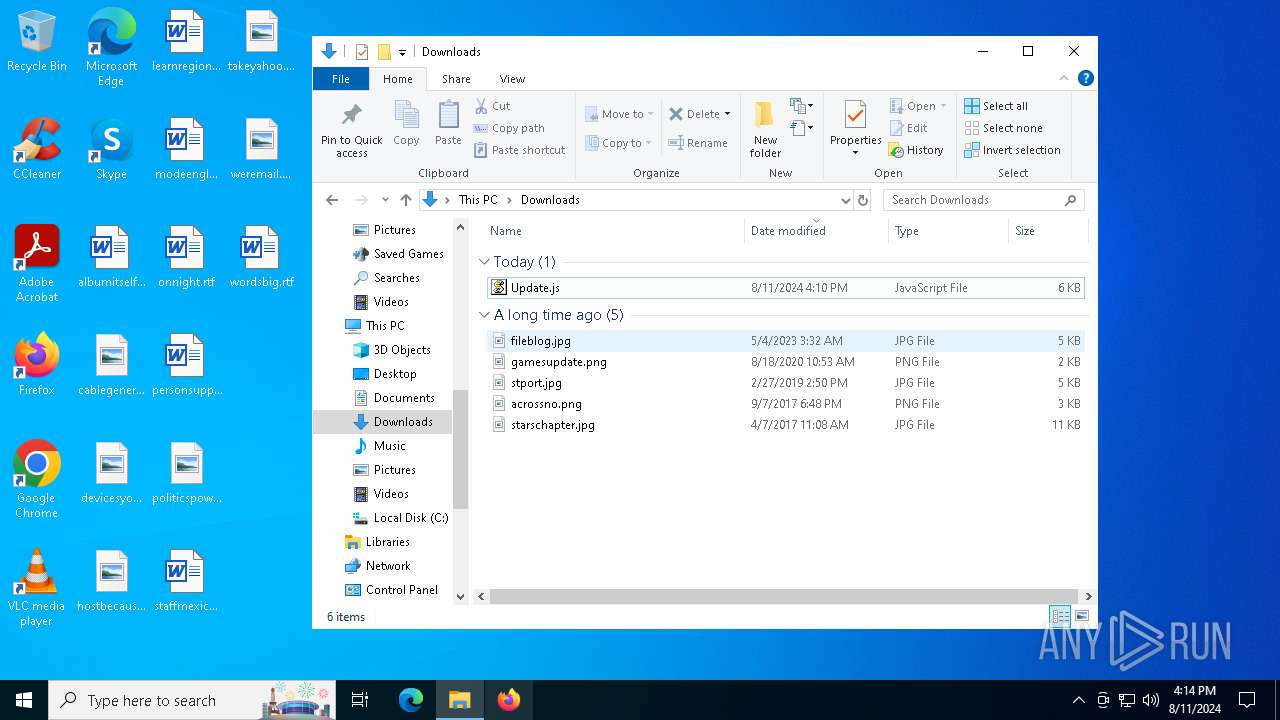
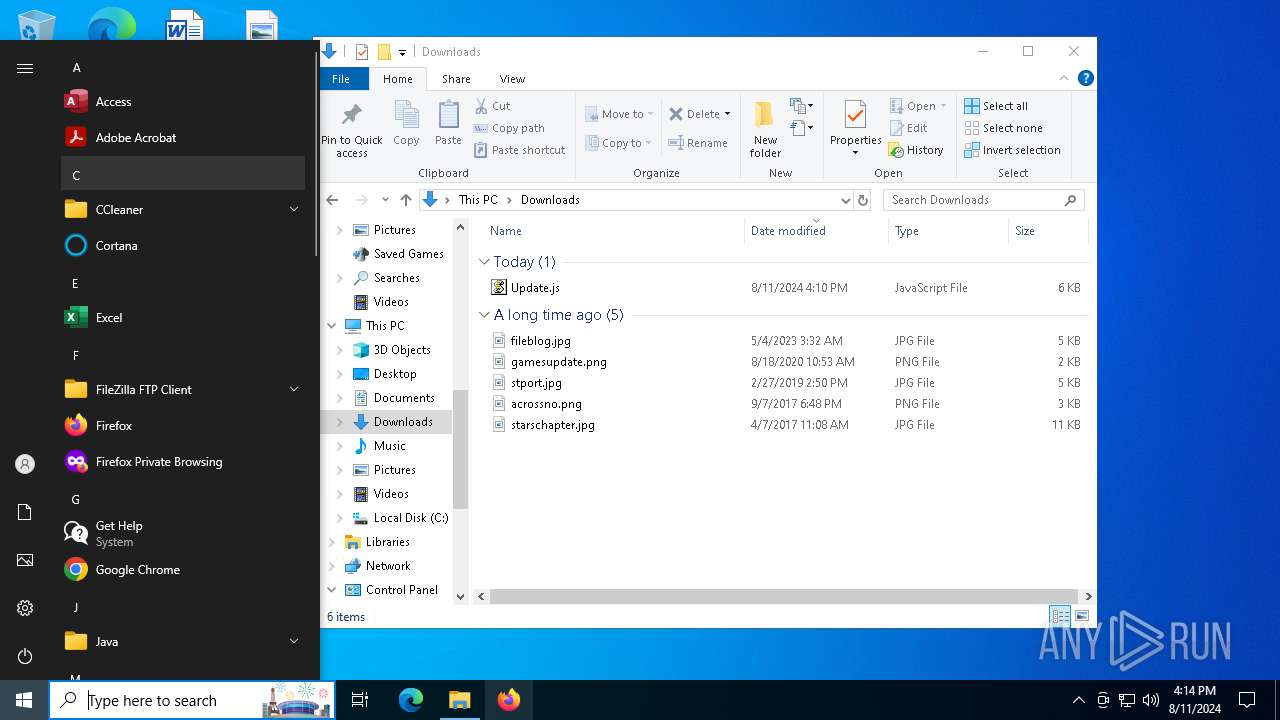
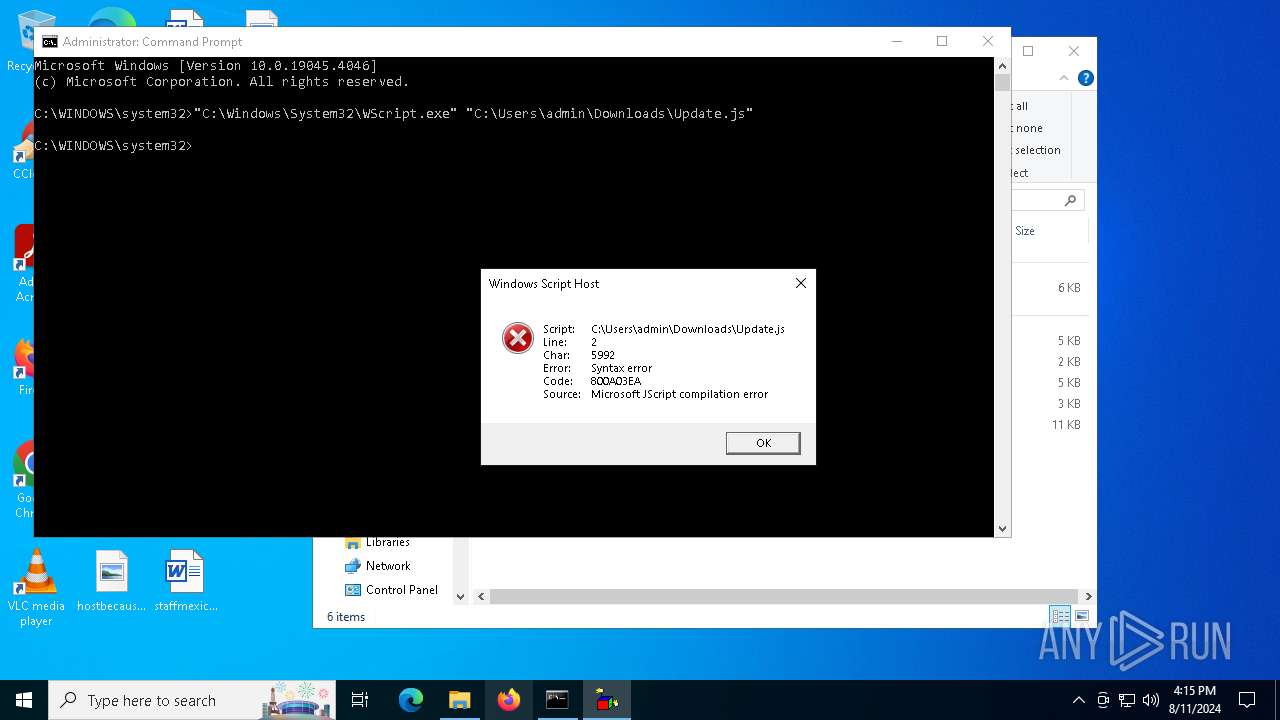
| File name: | Update.js |
| Full analysis: | https://app.any.run/tasks/5dfcae3d-158d-440b-817e-af80556c2625 |
| Verdict: | Malicious activity |
| Analysis date: | August 11, 2024, 16:10:37 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with very long lines (6058) |
| MD5: | E24B63AE3E47BB02DB243229184E407D |
| SHA1: | 38DAA823CC78E44EA63BE37FF2A536E35C1DCED9 |
| SHA256: | F4E54C508DCC022E550C8F570FD22CE14B38E81C4E906084789F855134EBCD20 |
| SSDEEP: | 96:6X13CPjTCm74r7kGDPGYNQ+wgl8mAT3UG3WzfAk+K3AqW//V62uCLQVlyHGaYGwH:813CPjTCKyLDPMT3UG3SZ+K3fId6f50q |
MALICIOUS
Creates internet connection object (SCRIPT)
- wscript.exe (PID: 6428)
- wscript.exe (PID: 6272)
- wscript.exe (PID: 7104)
- wscript.exe (PID: 7124)
- wscript.exe (PID: 240)
- wscript.exe (PID: 6348)
- wscript.exe (PID: 6176)
- wscript.exe (PID: 840)
- wscript.exe (PID: 1860)
- wscript.exe (PID: 6620)
- wscript.exe (PID: 6468)
- wscript.exe (PID: 6248)
- wscript.exe (PID: 6216)
Opens an HTTP connection (SCRIPT)
- wscript.exe (PID: 6428)
- wscript.exe (PID: 6272)
- wscript.exe (PID: 7124)
- wscript.exe (PID: 7104)
- wscript.exe (PID: 240)
- wscript.exe (PID: 840)
- wscript.exe (PID: 6176)
- wscript.exe (PID: 6348)
- wscript.exe (PID: 6620)
- wscript.exe (PID: 6468)
- wscript.exe (PID: 6248)
- wscript.exe (PID: 6216)
- wscript.exe (PID: 1860)
Scans artifacts that could help determine the target
- wscript.exe (PID: 6428)
- wscript.exe (PID: 6272)
- wscript.exe (PID: 7124)
- wscript.exe (PID: 7104)
- wscript.exe (PID: 240)
- wscript.exe (PID: 6348)
- wscript.exe (PID: 840)
- wscript.exe (PID: 6176)
- wscript.exe (PID: 1860)
- wscript.exe (PID: 6620)
- wscript.exe (PID: 6468)
- wscript.exe (PID: 6248)
- wscript.exe (PID: 6216)
SOCGHOLISH has been detected (SURICATA)
- svchost.exe (PID: 2256)
- wscript.exe (PID: 6428)
- wscript.exe (PID: 6272)
- wscript.exe (PID: 7124)
- wscript.exe (PID: 240)
- wscript.exe (PID: 6176)
- wscript.exe (PID: 1860)
- wscript.exe (PID: 6348)
- wscript.exe (PID: 840)
- wscript.exe (PID: 6468)
- wscript.exe (PID: 6620)
- wscript.exe (PID: 6216)
- wscript.exe (PID: 7104)
Sends HTTP request (SCRIPT)
- wscript.exe (PID: 6428)
- wscript.exe (PID: 6272)
- wscript.exe (PID: 7124)
- wscript.exe (PID: 7104)
- wscript.exe (PID: 6348)
- wscript.exe (PID: 240)
- wscript.exe (PID: 6176)
- wscript.exe (PID: 840)
- wscript.exe (PID: 1860)
- wscript.exe (PID: 6620)
- wscript.exe (PID: 6468)
- wscript.exe (PID: 6248)
- wscript.exe (PID: 6216)
Connects to the CnC server
- svchost.exe (PID: 2256)
- wscript.exe (PID: 6428)
- wscript.exe (PID: 6272)
- wscript.exe (PID: 7104)
- wscript.exe (PID: 6348)
- wscript.exe (PID: 7124)
- wscript.exe (PID: 1860)
- wscript.exe (PID: 240)
- wscript.exe (PID: 840)
- wscript.exe (PID: 6176)
- wscript.exe (PID: 6620)
- wscript.exe (PID: 6468)
- wscript.exe (PID: 6216)
Uses sleep, probably for evasion detection (SCRIPT)
- wscript.exe (PID: 6272)
- wscript.exe (PID: 6428)
- wscript.exe (PID: 7124)
- wscript.exe (PID: 7104)
- wscript.exe (PID: 6348)
- wscript.exe (PID: 240)
- wscript.exe (PID: 840)
- wscript.exe (PID: 6176)
- wscript.exe (PID: 1860)
- wscript.exe (PID: 6620)
- wscript.exe (PID: 6468)
- wscript.exe (PID: 6248)
- wscript.exe (PID: 6216)
SUSPICIOUS
Adds, changes, or deletes HTTP request header (SCRIPT)
- wscript.exe (PID: 6428)
- wscript.exe (PID: 6272)
- wscript.exe (PID: 7124)
- wscript.exe (PID: 7104)
- wscript.exe (PID: 240)
- wscript.exe (PID: 6348)
- wscript.exe (PID: 6176)
- wscript.exe (PID: 840)
- wscript.exe (PID: 6620)
- wscript.exe (PID: 6468)
- wscript.exe (PID: 6248)
- wscript.exe (PID: 6216)
- wscript.exe (PID: 1860)
Contacting a server suspected of hosting an CnC
- svchost.exe (PID: 2256)
- wscript.exe (PID: 6428)
- wscript.exe (PID: 6272)
- wscript.exe (PID: 7124)
- wscript.exe (PID: 6348)
- wscript.exe (PID: 1860)
- wscript.exe (PID: 240)
- wscript.exe (PID: 840)
- wscript.exe (PID: 6176)
- wscript.exe (PID: 6468)
- wscript.exe (PID: 6620)
- wscript.exe (PID: 6216)
- wscript.exe (PID: 7104)
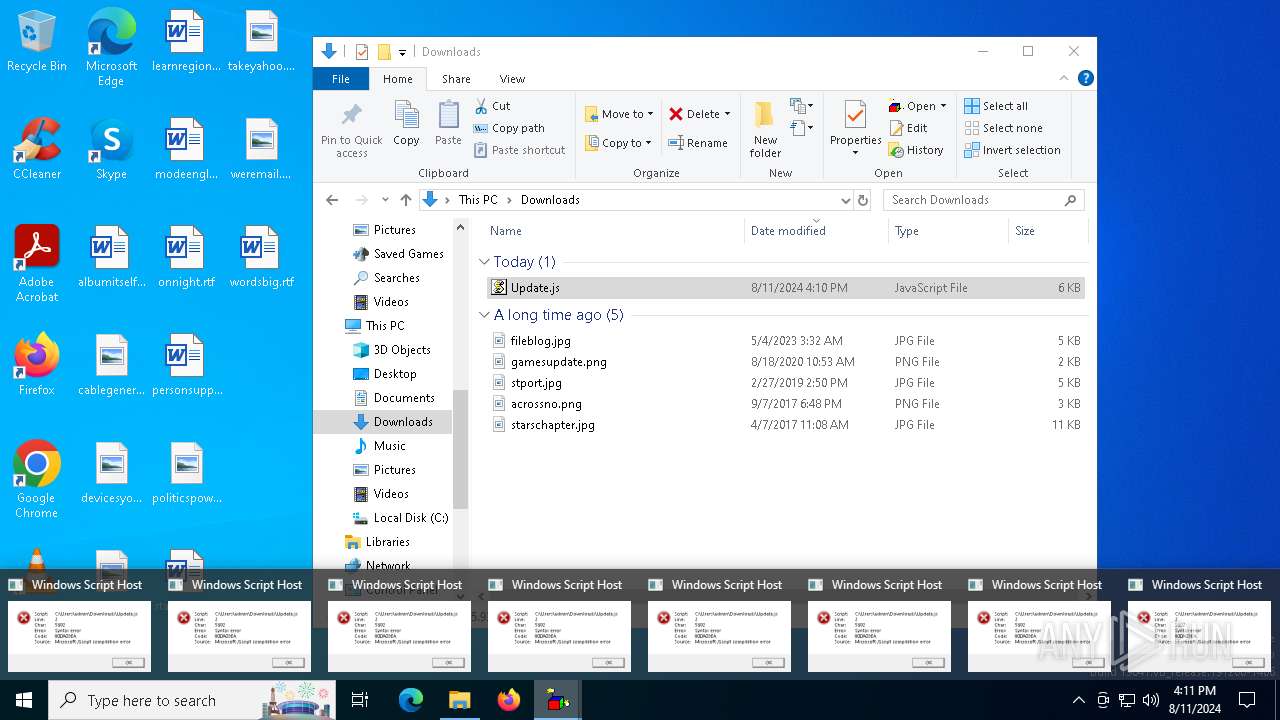
The process executes JS scripts
- cmd.exe (PID: 4064)
INFO
Checks proxy server information
- wscript.exe (PID: 6428)
- wscript.exe (PID: 6272)
- wscript.exe (PID: 7124)
- wscript.exe (PID: 7104)
- wscript.exe (PID: 240)
- wscript.exe (PID: 6348)
- wscript.exe (PID: 840)
- wscript.exe (PID: 6176)
- wscript.exe (PID: 6620)
- wscript.exe (PID: 1860)
- wscript.exe (PID: 6468)
- wscript.exe (PID: 6248)
- wscript.exe (PID: 6216)
Manual execution by a user
- wscript.exe (PID: 6272)
- wscript.exe (PID: 7104)
- wscript.exe (PID: 7124)
- wscript.exe (PID: 240)
- wscript.exe (PID: 6348)
- wscript.exe (PID: 840)
- wscript.exe (PID: 6176)
- wscript.exe (PID: 1860)
- wscript.exe (PID: 6620)
- wscript.exe (PID: 6468)
- wscript.exe (PID: 6248)
- cmd.exe (PID: 6192)
- cmd.exe (PID: 4064)
Checks supported languages
- TextInputHost.exe (PID: 6880)
Reads the computer name
- TextInputHost.exe (PID: 6880)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
204
Monitored processes
20
Malicious processes
15
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
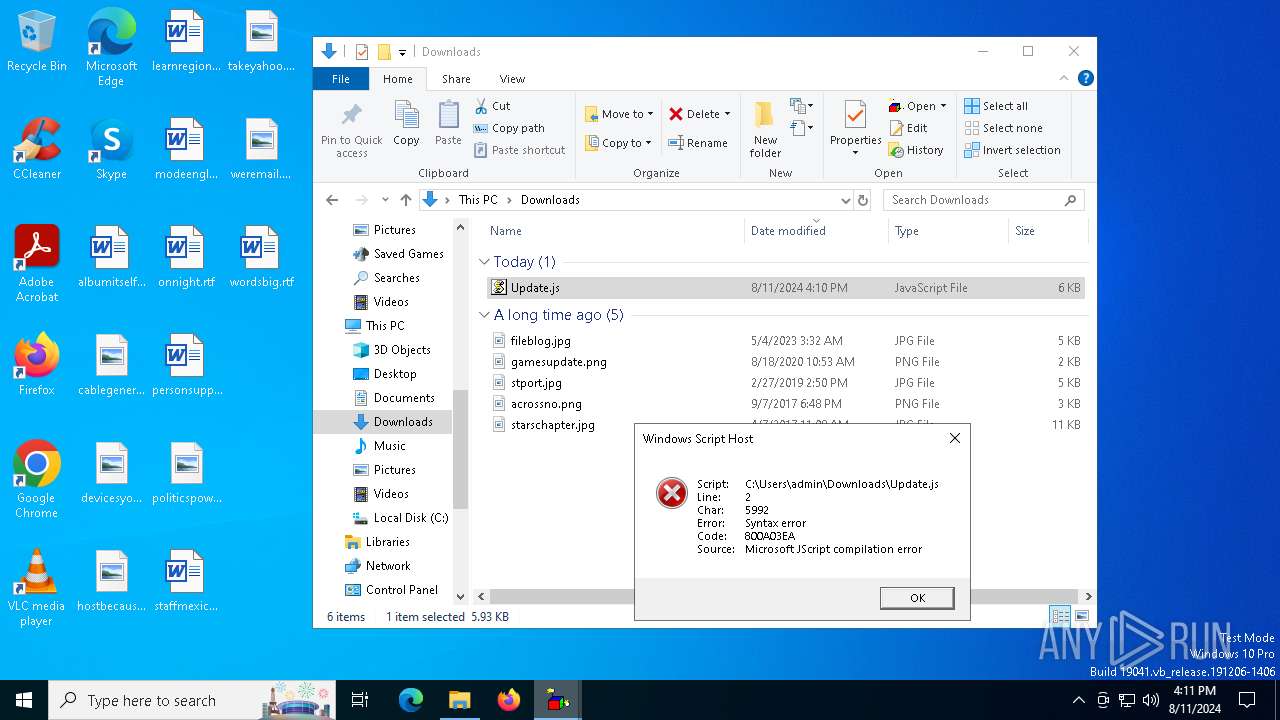
| 240 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\Downloads\Update.js" | C:\Windows\System32\wscript.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 840 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\Downloads\Update.js" | C:\Windows\System32\wscript.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 1860 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\Downloads\Update.js" | C:\Windows\System32\wscript.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 2256 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4064 | "C:\WINDOWS\system32\cmd.exe" | C:\Windows\System32\cmd.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6016 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6176 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\Downloads\Update.js" | C:\Windows\System32\wscript.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 6192 | "C:\WINDOWS\system32\cmd.exe" | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 3221225786 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6216 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\Downloads\Update.js" | C:\Windows\System32\wscript.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 6248 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\Downloads\Update.js" | C:\Windows\System32\wscript.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
Total events
23 798
Read events
23 654
Write events
144
Delete events
0
Modification events
| (PID) Process: | (6428) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6428) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (6428) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (6428) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (6428) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6428) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6428) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (6428) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows Script\Settings\Telemetry\wscript.exe |
| Operation: | write | Name: | JScriptSetScriptStateStarted |
Value: 3C7A0E0000000000 | |||
| (PID) Process: | (6272) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6272) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
0
Suspicious files
6
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6428 | wscript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\D0E1C4B6144E7ECAB3F020E4A19EFC29_03D1B482EE3032A122274428715A4E19 | binary | |
MD5:D27A779BF64DB6F563E1545E121528E7 | SHA256:28F47DA140ADF74F003A76C22B488C49BCC53A53ABAA16C500548B82AC313C59 | |||
| 6428 | wscript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\3B148F74BFBE9B5F77B450DFFBC4E16D | binary | |
MD5:5A80C128409996E5B6CB1161BDFB3797 | SHA256:1C472AEAB6D4D0A58B92F058656123C9A8536CB18F4350C8D61CB21650E18BBD | |||
| 6428 | wscript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B2FAF7692FD9FFBD64EDE317E42334BA_89854CA6A0F0936A4D2ECA78845CEA25 | binary | |
MD5:BE360344E32BE81F6D8C49C84BF4385E | SHA256:A8481E7E7455B858B218284A8480E8C957F55714571FA47538804CCBACA1C7E5 | |||
| 6428 | wscript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B2FAF7692FD9FFBD64EDE317E42334BA_89854CA6A0F0936A4D2ECA78845CEA25 | binary | |
MD5:27B4AC4D33EA87EA34C6BF4463E9F5FE | SHA256:95999C081AD63D5303FCE13B5F586F6A82D9C795EA7FCC76D3B3E9F45C34C023 | |||
| 6428 | wscript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\D0E1C4B6144E7ECAB3F020E4A19EFC29_03D1B482EE3032A122274428715A4E19 | binary | |
MD5:3DB4B05C4268C7FA15BFAA1F633F4C47 | SHA256:10C147310C2772FA655D165EE2BA7BDEB501ED3F6D8E4DB72825120764895370 | |||
| 6428 | wscript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\3B148F74BFBE9B5F77B450DFFBC4E16D | binary | |
MD5:BD8689B4805C07E276A9B02A5DC2F28D | SHA256:DB4A3E45DCE10EC575EAA3BB8CC3BE758B923F055505639B1B988FDF97475396 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
84
DNS requests
35
Threats
28
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6428 | wscript.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEFZnHQTqT5lMbxCBR1nSdZQ%3D | unknown | — | — | whitelisted |
6428 | wscript.exe | GET | 200 | 104.18.38.233:80 | http://zerossl.ocsp.sectigo.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQzH%2F4%2F%2FQuEFihPlI1WwH4Dktj2TQQUD2vmS845R672fpAeefAwkZLIX6MCEC4wg36ZoTyFtmhaNg14CKs%3D | unknown | — | — | whitelisted |
6428 | wscript.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSr83eyJy3njhjVpn5bEpfc6MXawQQUOuEJhtTPGcKWdnRJdtzgNcZjY5oCECO3bePBuysaUZYeCOq3ZOg%3D | unknown | — | — | whitelisted |
2608 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 163.181.92.229:80 | http://ocsp.digicert.cn/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEA%2FgMquETQMxBsUMjhPIsGg%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6800 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6836 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
876 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5056 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6428 | wscript.exe | 50.114.37.59:443 | tuxwe.donors.eucharisticjesus.net | Des Capital B.V. | US | malicious |
6428 | wscript.exe | 104.18.38.233:80 | ocsp.comodoca.com | CLOUDFLARENET | — | shared |
6428 | wscript.exe | 172.64.149.23:80 | ocsp.comodoca.com | CLOUDFLARENET | US | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
876 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
tuxwe.donors.eucharisticjesus.net |
| malicious |
ocsp.comodoca.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
zerossl.ocsp.sectigo.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE SocGholish CnC Domain in DNS (* .donors .eucharisticjesus .net) |
6428 | wscript.exe | Domain Observed Used for C2 Detected | ET MALWARE SocGholish CnC Domain in TLS SNI (* .donors .eucharisticjesus .net) |
6428 | wscript.exe | Misc activity | ET INFO Observed ZeroSSL SSL/TLS Certificate |
6272 | wscript.exe | Domain Observed Used for C2 Detected | ET MALWARE SocGholish CnC Domain in TLS SNI (* .donors .eucharisticjesus .net) |
6272 | wscript.exe | Misc activity | ET INFO Observed ZeroSSL SSL/TLS Certificate |
7124 | wscript.exe | Misc activity | ET INFO Observed ZeroSSL SSL/TLS Certificate |
7124 | wscript.exe | Domain Observed Used for C2 Detected | ET MALWARE SocGholish CnC Domain in TLS SNI (* .donors .eucharisticjesus .net) |
7104 | wscript.exe | Misc activity | ET INFO Observed ZeroSSL SSL/TLS Certificate |
7104 | wscript.exe | Domain Observed Used for C2 Detected | ET MALWARE SocGholish CnC Domain in TLS SNI (* .donors .eucharisticjesus .net) |
240 | wscript.exe | Misc activity | ET INFO Observed ZeroSSL SSL/TLS Certificate |