| URL: | https://d48ehdag0go01.cloudfront.net/P2mk/lAeoCEkXj/KhLylBl/robloxplayer-1.6.0.5520592-installer.exe |
| Full analysis: | https://app.any.run/tasks/0d9df2f7-595d-4944-9b90-2a6793caf4d7 |
| Verdict: | Malicious activity |
| Analysis date: | September 21, 2024, 10:53:22 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 9D3189D96D171173B82493528ED05F63 |
| SHA1: | 6245DB72DA5115A359D33908033D2591BAFED99C |
| SHA256: | F4D163F96003543C47307C421CCACD565AFB2F91E4998444A3423B5EF585A313 |
| SSDEEP: | 3:N8JLFiIl/0u2JLtHaEM0jJgLVnwXLNn:2MTbtjsVnwXLN |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- robloxplayer-1.6.0.5520592-installer_fQqpd-1.exe (PID: 5000)
- component0.exe (PID: 1640)
- RobloxPlayerLauncher.exe (PID: 6008)
- robloxplayer-1.6.0.5520592-installer.exe (PID: 3768)
- rsEngineSvc.exe (PID: 7416)
- MicrosoftEdgeWebview2Setup.exe (PID: 3696)
- RobloxPlayerBeta.exe (PID: 8072)
- robloxplayer-1.6.0.5520592-installer_fQqpd-1.exe (PID: 3924)
- 43hc2twb.exe (PID: 7548)
- UnifiedStub-installer.exe (PID: 7592)
- robloxplayer-1.6.0.5520592-installer_fQqpd-1.tmp (PID: 5388)
Application launched itself
- robloxplayer-1.6.0.5520592-installer.exe (PID: 3768)
- RobloxPlayerLauncher.exe (PID: 6008)
- rsAppUI.exe (PID: 7216)
Executes as Windows Service
- rsSyncSvc.exe (PID: 7876)
- rsClientSvc.exe (PID: 7284)
- rsEDRSvc.exe (PID: 2016)
- rsEngineSvc.exe (PID: 7416)
- WmiApSrv.exe (PID: 4104)
- rsWSC.exe (PID: 7636)
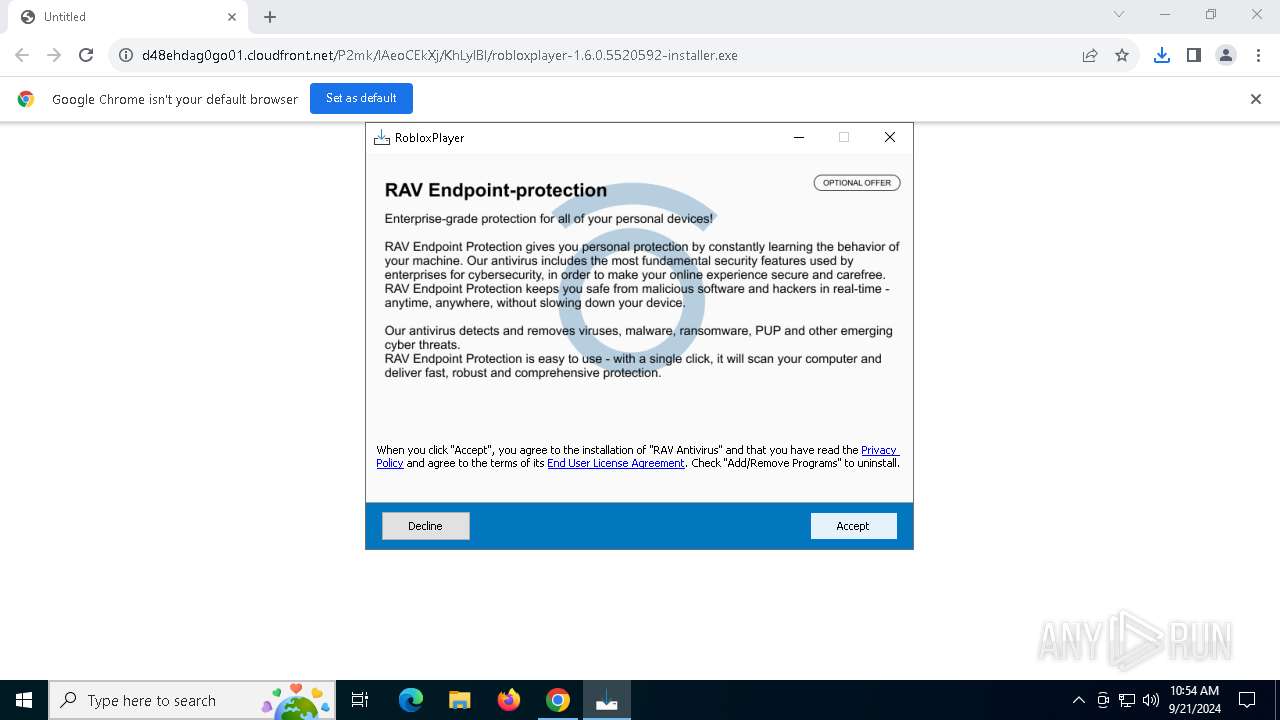
Process drops legitimate windows executable
- UnifiedStub-installer.exe (PID: 7592)
- RobloxPlayerLauncher.exe (PID: 6008)
- rsEngineSvc.exe (PID: 7416)
- MicrosoftEdgeUpdate.exe (PID: 6584)
- MicrosoftEdgeWebview2Setup.exe (PID: 3696)
- 43hc2twb.exe (PID: 7548)
Drops 7-zip archiver for unpacking
- UnifiedStub-installer.exe (PID: 7592)
Drops a system driver (possible attempt to evade defenses)
- UnifiedStub-installer.exe (PID: 7592)
The process drops C-runtime libraries
- UnifiedStub-installer.exe (PID: 7592)
Uses RUNDLL32.EXE to load library
- UnifiedStub-installer.exe (PID: 7592)
Uses WEVTUTIL.EXE to install publishers and event logs from the manifest
- UnifiedStub-installer.exe (PID: 7592)
Starts a Microsoft application from unusual location
- MicrosoftEdgeUpdate.exe (PID: 6584)
There is functionality for taking screenshot (YARA)
- rsHelper.exe (PID: 8084)
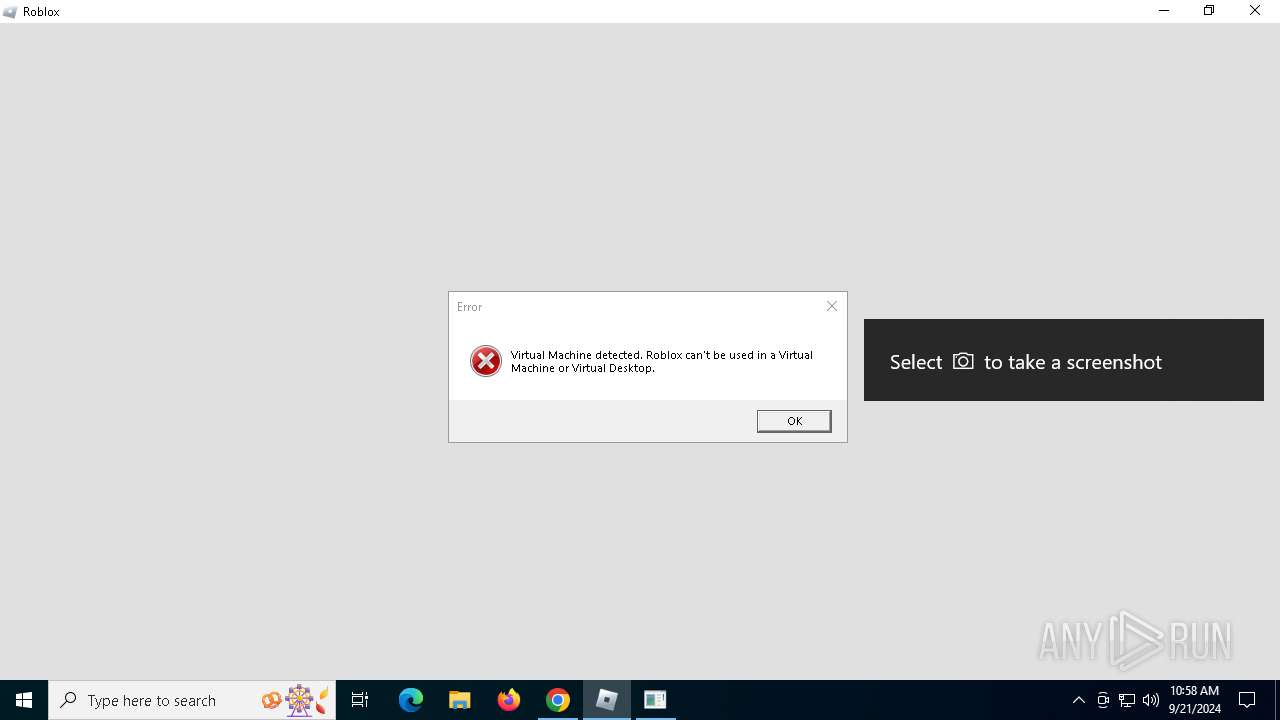
Executes application which crashes
- robloxplayer-1.6.0.5520592-installer_fQqpd-1.tmp (PID: 5388)
INFO
Executable content was dropped or overwritten
- chrome.exe (PID: 4060)
- chrome.exe (PID: 6528)
The process uses the downloaded file
- chrome.exe (PID: 7184)
Application launched itself
- chrome.exe (PID: 4060)
.NET Reactor protector has been detected
- UnifiedStub-installer.exe (PID: 7592)
- rsWSC.exe (PID: 7636)
- rsEngineSvc.exe (PID: 7416)
- rsEDRSvc.exe (PID: 2016)
- rsHelper.exe (PID: 8084)
Found Base64 encoded access to Windows Defender via PowerShell (YARA)
- rsEngineSvc.exe (PID: 7416)
Found Base64 encoded text manipulation via PowerShell (YARA)
- rsEngineSvc.exe (PID: 7416)
Manual execution by a user
- RobloxPlayerBeta.exe (PID: 8072)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
219
Monitored processes
74
Malicious processes
9
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 360 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | fltMC.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 736 | "C:\Program Files (x86)\Roblox\Versions\version-43ad1853ad91427d\\RobloxCrashHandler.exe" --no-rate-limit --crashCounter Win-ROBLOXPlayer-Crash --baseUrl http://www.roblox.com/ --attachment=attachment_0.642.0.6420636_20240921T105813Z_Player_2AC57_last.log=C:\Users\admin\AppData\Local\Roblox\logs\0.642.0.6420636_20240921T105813Z_Player_2AC57_last.log --database=C:\Users\admin\AppData\Local\Roblox\logs\crashes --metrics-dir=C:\Users\admin\AppData\Local\Roblox\logs\crashes --url=https://upload.crashes.rbxinfra.com/post?format=minidump --annotation=AppVersion=0.642.0.6420636 --annotation=BaseUrl=http://www.roblox.com/ "--annotation=CPUMake=Intel(R) Core(TM) i5-6400 CPU @ 2.70GHz" --annotation=Format=minidump --annotation=OSPlatform=Win32 "--annotation=OSVersion=Windows 10 - PlatformId 2, Version 10.0, Build 19045" --annotation=PlatformId=2 --annotation=RobloxChannel=production --annotation=RobloxGitHash=fb5071aa25c087808982b03a639e8c461b22c7f7 --annotation=RobloxProduct=RobloxPlayer --annotation=TotalMemory=4289146880 --annotation=UniqueId=9049497548589805762 --annotation=UploadAttachmentKiloByteLimit=1000 --annotation=UseCrashpad=True --initial-client-data=0x924,0x908,0x974,0x89c,0x9d8,0x7ff619972408,0x7ff619972420,0x7ff619972438 | C:\Program Files (x86)\Roblox\Versions\version-43ad1853ad91427d\RobloxCrashHandler.exe | — | RobloxPlayerBeta.exe | |||||||||||
User: admin Integrity Level: MEDIUM | |||||||||||||||
| 788 | "C:\program files\reasonlabs\epp\rsLitmus.A.exe" | C:\Program Files\ReasonLabs\EPP\rsLitmus.A.exe | — | rsEngineSvc.exe | |||||||||||
User: SYSTEM Integrity Level: SYSTEM Exit code: 54321 | |||||||||||||||
| 892 | "C:\Program Files\ReasonLabs\Common\rsSyncSvc.exe" -i -bn:ReasonLabs -pn:EPP -lpn:rav_antivirus -url:https://update.reasonsecurity.com/v2/live -dt:10 | C:\Program Files\ReasonLabs\Common\rsSyncSvc.exe | — | UnifiedStub-installer.exe | |||||||||||
User: admin Company: Reason Software Company Inc. Integrity Level: HIGH Description: Reason Security Synchronize Service Exit code: 0 Version: 1.8.5.0 Modules
| |||||||||||||||
| 1108 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --no-appcompat-clear --gpu-preferences=WAAAAAAAAADgABAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=1980 --field-trial-handle=1984,i,558187569772804331,6309693715902873500,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1236 | "C:\WINDOWS\system32\wevtutil.exe" im C:\Program Files\ReasonLabs\EPP\x64\elam\evntdrv.xml | C:\Windows\System32\wevtutil.exe | — | UnifiedStub-installer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Eventing Command Line Utility Exit code: 87 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1640 | "C:\Users\admin\AppData\Local\Temp\is-7A9T9.tmp\component0.exe" -ip:"dui=bb926e54-e3ca-40fd-ae90-2764341e7792&dit=20240921105446&is_silent=true&oc=ZB_RAV_Cross_Solo_Soft&p=fa70&a=100&b=&se=true" -i | C:\Users\admin\AppData\Local\Temp\is-7A9T9.tmp\component0.exe | robloxplayer-1.6.0.5520592-installer_fQqpd-1.tmp | ||||||||||||
User: admin Company: Reason Software Company Inc. Integrity Level: HIGH Description: rsStubActivator Exit code: 0 Version: 1.6.1.0 Modules
| |||||||||||||||
| 1744 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=6024 --field-trial-handle=1984,i,558187569772804331,6309693715902873500,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1848 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 5388 -s 2324 | C:\Windows\SysWOW64\WerFault.exe | robloxplayer-1.6.0.5520592-installer_fQqpd-1.tmp | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2016 | "C:\Program Files\ReasonLabs\EDR\rsEDRSvc.exe" | C:\Program Files\ReasonLabs\EDR\rsEDRSvc.exe | services.exe | ||||||||||||
User: SYSTEM Company: Reason Cybersecurity Ltd. Integrity Level: SYSTEM Description: Reason EDR Service Version: 2.2.1 | |||||||||||||||
Total events
33 585
Read events
33 406
Write events
127
Delete events
52
Modification events
| (PID) Process: | (4060) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (4060) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (4060) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (4060) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (4060) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (7184) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {2781761E-28E0-4109-99FE-B9D127C57AFE} {56FFCC30-D398-11D0-B2AE-00A0C908FA49} 0xFFFF |
Value: 0100000000000000BC022181140CDB01 | |||
| (PID) Process: | (1640) component0.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\component0_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (1640) component0.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\component0_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (1640) component0.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\component0_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (1640) component0.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\component0_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
Executable files
743
Suspicious files
507
Text files
93
Unknown types
17
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4060 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF1fbfce.TMP | — | |
MD5:— | SHA256:— | |||
| 4060 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4060 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4060 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4060 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4060 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF1fbffd.TMP | — | |
MD5:— | SHA256:— | |||
| 4060 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4060 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4060 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad\settings.dat | binary | |
MD5:FC81892AC822DCBB09441D3B58B47125 | SHA256:FB077C966296D02D50CCBF7F761D2A3311A206A784A7496F331C2B0D6AD205C8 | |||
| 4060 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\metadata\LOG.old~RF1fc116.TMP | text | |
MD5:602C51DB8380F8CD0A961D9A46AF1186 | SHA256:84F716E38017F52138A76222524A3152DB8D3A7FBE30E94067458568B14DC36D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
89
TCP/UDP connections
152
DNS requests
92
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3880 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acaldksiunzh56452py2db5mnbpa_120.0.6050.0/jamhcnnkihinmdlkakkaopbjbbcngflc_120.0.6050.0_all_dgzfpknn7v3zslsbhrwu6bt44e.crx3 | unknown | — | — | whitelisted |
3880 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acaldksiunzh56452py2db5mnbpa_120.0.6050.0/jamhcnnkihinmdlkakkaopbjbbcngflc_120.0.6050.0_all_dgzfpknn7v3zslsbhrwu6bt44e.crx3 | unknown | — | — | whitelisted |
4060 | chrome.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA6bGI750C3n79tQ4ghAGFo%3D | unknown | — | — | whitelisted |
3880 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acaldksiunzh56452py2db5mnbpa_120.0.6050.0/jamhcnnkihinmdlkakkaopbjbbcngflc_120.0.6050.0_all_dgzfpknn7v3zslsbhrwu6bt44e.crx3 | unknown | — | — | whitelisted |
4060 | chrome.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | — | — | whitelisted |
4060 | chrome.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEApJaqM%2Bmgz234UUEUR6Zyc%3D | unknown | — | — | whitelisted |
2120 | MoUsoCoreWorker.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3812 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3880 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acaldksiunzh56452py2db5mnbpa_120.0.6050.0/jamhcnnkihinmdlkakkaopbjbbcngflc_120.0.6050.0_all_dgzfpknn7v3zslsbhrwu6bt44e.crx3 | unknown | — | — | whitelisted |
8168 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5900 | svchost.exe | 52.137.106.217:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
— | — | 52.168.117.168:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
— | — | 2.16.110.171:443 | — | Akamai International B.V. | DE | unknown |
2452 | RUXIMICS.exe | 52.137.106.217:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
— | — | 52.137.106.217:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2120 | MoUsoCoreWorker.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2120 | MoUsoCoreWorker.exe | 52.137.106.217:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7136 | chrome.exe | 18.172.111.76:443 | d48ehdag0go01.cloudfront.net | — | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
d48ehdag0go01.cloudfront.net |
| whitelisted |
accounts.google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
sb-ssl.google.com |
| whitelisted |
www.google.com |
| whitelisted |
browser.pipe.aria.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
RobloxPlayerLauncher.exe | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|