| File name: | pf.zip |
| Full analysis: | https://app.any.run/tasks/8536e90d-a922-4a96-b924-8e833ae9af50 |
| Verdict: | Malicious activity |
| Analysis date: | December 05, 2022, 20:06:33 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 90B901191FB837ECD03B591D2CEEFD9A |
| SHA1: | BF200150DD3F4F61898B44F53F6756C804821094 |
| SHA256: | F4C1D831719DEFF3F583396038B9181B316E509AC410132BFA4EE2334C3121F6 |
| SSDEEP: | 49152:TmPNJDnvx4+Zf95vAH3W0l79GFmZS0bn3VLIPLS0Le:6Fr4+Zfh0t9RZS0bn3BSB6 |
MALICIOUS
Disables Windows Defender
- msiexec.exe (PID: 4068)
Writes to the Start menu file
- regsvr32.exe (PID: 2100)
Changes the autorun value in the registry
- regsvr32.exe (PID: 2100)
- unregmp2.exe (PID: 2328)
Changes the Startup folder
- regsvr32.exe (PID: 2100)
SUSPICIOUS
Application launched itself
- msiexec.exe (PID: 4068)
- ie4uinit.exe (PID: 3884)
- rundll32.exe (PID: 1400)
Creates or modifies Windows services
- netsh.exe (PID: 2460)
Executes as Windows Service
- taskhost.exe (PID: 3540)
- EOSNotify.exe (PID: 308)
Executes via Task Scheduler
- sipnotify.exe (PID: 3240)
Start notepad (likely ransomware note)
- WinRAR.exe (PID: 3528)
Uses RUNDLL32.EXE to load library
- ie4uinit.exe (PID: 3884)
- rundll32.exe (PID: 1400)
Reads Microsoft Outlook installation path
- ie4uinit.exe (PID: 3884)
Write to the desktop.ini file (may be used to cloak folders)
- ie4uinit.exe (PID: 3884)
- unregmp2.exe (PID: 2328)
- regsvr32.exe (PID: 2100)
Reads Internet Explorer settings
- ie4uinit.exe (PID: 3884)
Changes default file association
- unregmp2.exe (PID: 2328)
Reads settings of System Certificates
- sipnotify.exe (PID: 3240)
Changes internet zones settings
- ie4uinit.exe (PID: 3884)
Checks for Java to be installed
- jusched.exe (PID: 4016)
INFO
Executable content was dropped or overwritten
- msiexec.exe (PID: 4068)
Drops a file that was compiled in debug mode
- msiexec.exe (PID: 4068)
Manual execution by a user
- WinRAR.exe (PID: 3528)
- chrome.exe (PID: 3168)
- ie4uinit.exe (PID: 3884)
- ie4uinit.exe (PID: 2992)
- chrmstp.exe (PID: 3304)
- unregmp2.exe (PID: 2328)
- ie4uinit.exe (PID: 3984)
- regsvr32.exe (PID: 2100)
- IMEKLMG.EXE (PID: 936)
- jusched.exe (PID: 4016)
- IMEKLMG.EXE (PID: 3336)
- msiexec.exe (PID: 3752)
Application launched itself
- chrmstp.exe (PID: 3304)
- chrome.exe (PID: 3168)
Reads security settings of Internet Explorer
- sipnotify.exe (PID: 3240)
- ie4uinit.exe (PID: 3884)
Checks supported languages
- IMEKLMG.EXE (PID: 3336)
- IMEKLMG.EXE (PID: 936)
- jusched.exe (PID: 4016)
- imkrmig.exe (PID: 3912)
Reads the computer name
- IMEKLMG.EXE (PID: 3336)
- IMEKLMG.EXE (PID: 936)
Process checks are UAC notifies on
- IMEKLMG.EXE (PID: 3336)
- IMEKLMG.EXE (PID: 936)
Drops the executable file immediately after the start
- msiexec.exe (PID: 4068)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
Total processes
159
Monitored processes
74
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 308 | C:\Windows\system32\EOSNotify.exe | C:\Windows\system32\EOSNotify.exe | — | services.exe | |||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: EOS Notification Exit code: 0 Version: 6.1.7601.24544 (win7sp1_ldr_escrow.191230-1647) Modules
| |||||||||||||||
| 372 | "C:\Windows\System32\takeown.exe" /f C:\Windows\system32\cscript.exe | C:\Windows\System32\takeown.exe | — | MsiExec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Takes ownership of a file Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 452 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1028,6473511869097434887,9092192445100589692,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3164 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 488 | "C:\Windows\System32\netsh.exe" ipsec static add filter filterlist=Filter1 srcaddr=Me dstaddr=any dstport=7777 protocol=TCP | C:\Windows\System32\netsh.exe | — | MsiExec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 788 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1028,6473511869097434887,9092192445100589692,131072 --enable-features=PasswordImport --lang=en-US --instant-process --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1948 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
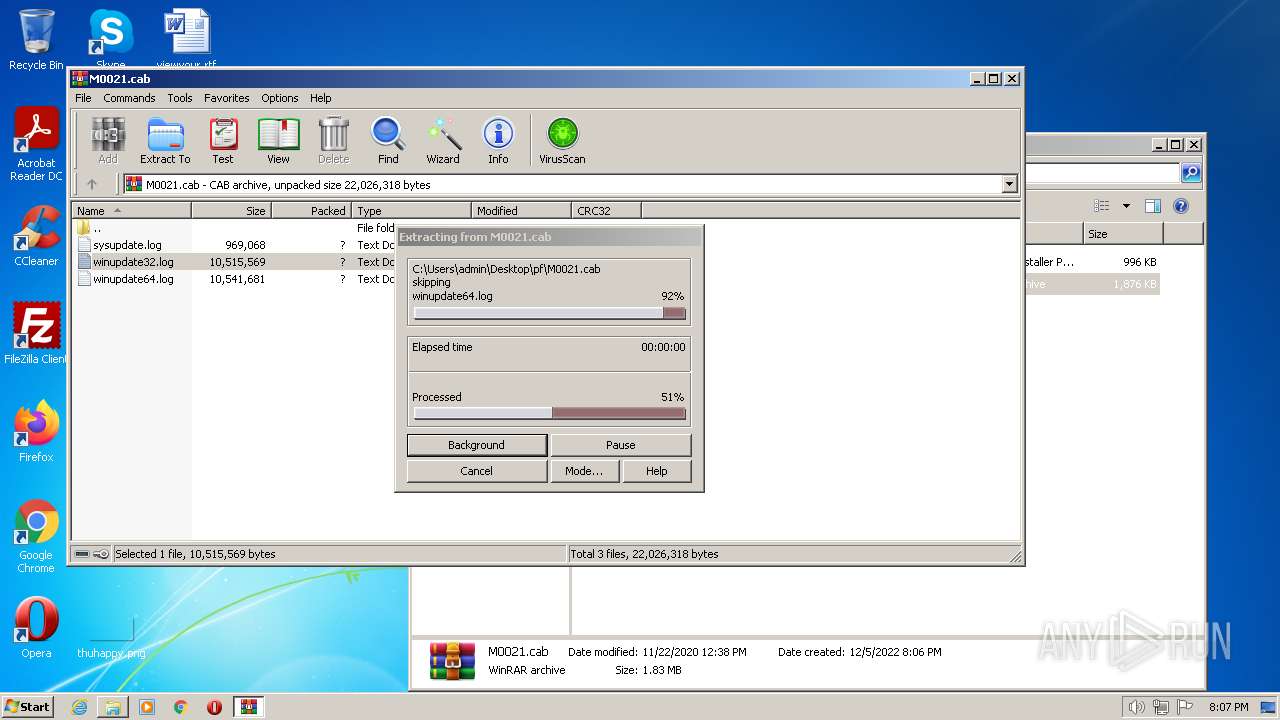
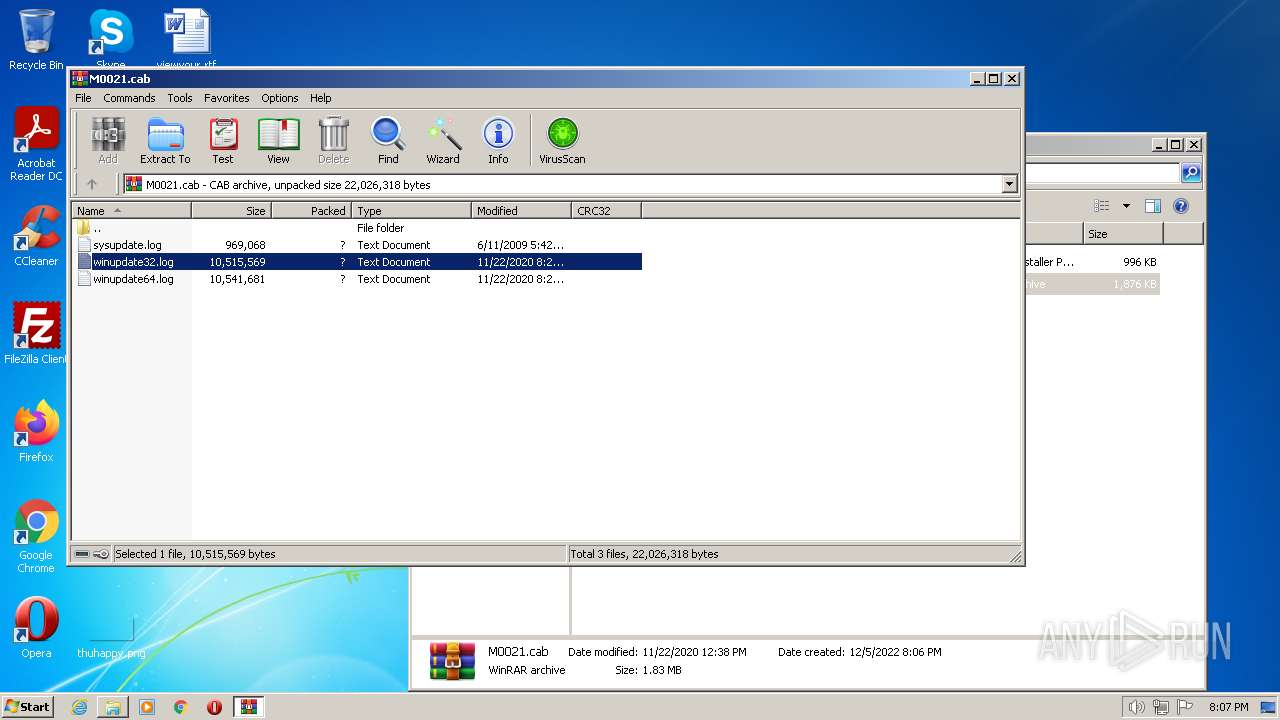
| 912 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\Rar$DIa3528.32122\winupdate32.log | C:\Windows\system32\NOTEPAD.EXE | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 936 | "C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE" /SetPreload /KOR /Log | C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE | — | Explorer.EXE | |||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Office IME 2010 Exit code: 1 Version: 14.0.4734.1000 Modules
| |||||||||||||||
| 1172 | "C:\Windows\System32\netsh.exe" ipsec static add filter filterlist=Filter1 srcaddr=Me dstaddr=any dstport=14443 protocol=TCP | C:\Windows\System32\netsh.exe | — | MsiExec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1220 | "C:\Windows\System32\netsh.exe" ipsec static add filter filterlist=Filter1 srcaddr=Me dstaddr=any dstport=4444 protocol=TCP | C:\Windows\System32\netsh.exe | — | MsiExec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1232 | C:\Windows\system32\MsiExec.exe -Embedding DC85B2E1F3AF71BB631842C1153117BA E Global\MSI0000 | C:\Windows\system32\MsiExec.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
36 370
Read events
33 716
Write events
2 633
Delete events
21
Modification events
| (PID) Process: | (1772) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1772) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1772) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1772) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (1772) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (1772) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\pf.zip | |||
| (PID) Process: | (1772) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1772) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1772) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1772) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
9
Suspicious files
148
Text files
172
Unknown types
20
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4068 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\~DFAC9A5AB76408D9BD.TMP | gmc | |
MD5:— | SHA256:— | |||
| 1772 | WinRAR.exe | C:\Users\admin\Desktop\pf\6.msi | executable | |
MD5:— | SHA256:— | |||
| 4068 | msiexec.exe | C:\Windows\Installer\1073681.msi | executable | |
MD5:— | SHA256:— | |||
| 4068 | msiexec.exe | C:\Windows\.ini | binary | |
MD5:— | SHA256:— | |||
| 4068 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\~DF8C6F74876A5782E9.TMP | gmc | |
MD5:— | SHA256:— | |||
| 3168 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-638E4F85-C60.pma | — | |
MD5:— | SHA256:— | |||
| 4068 | msiexec.exe | C:\Windows\Installer\MSI3906.tmp | binary | |
MD5:— | SHA256:— | |||
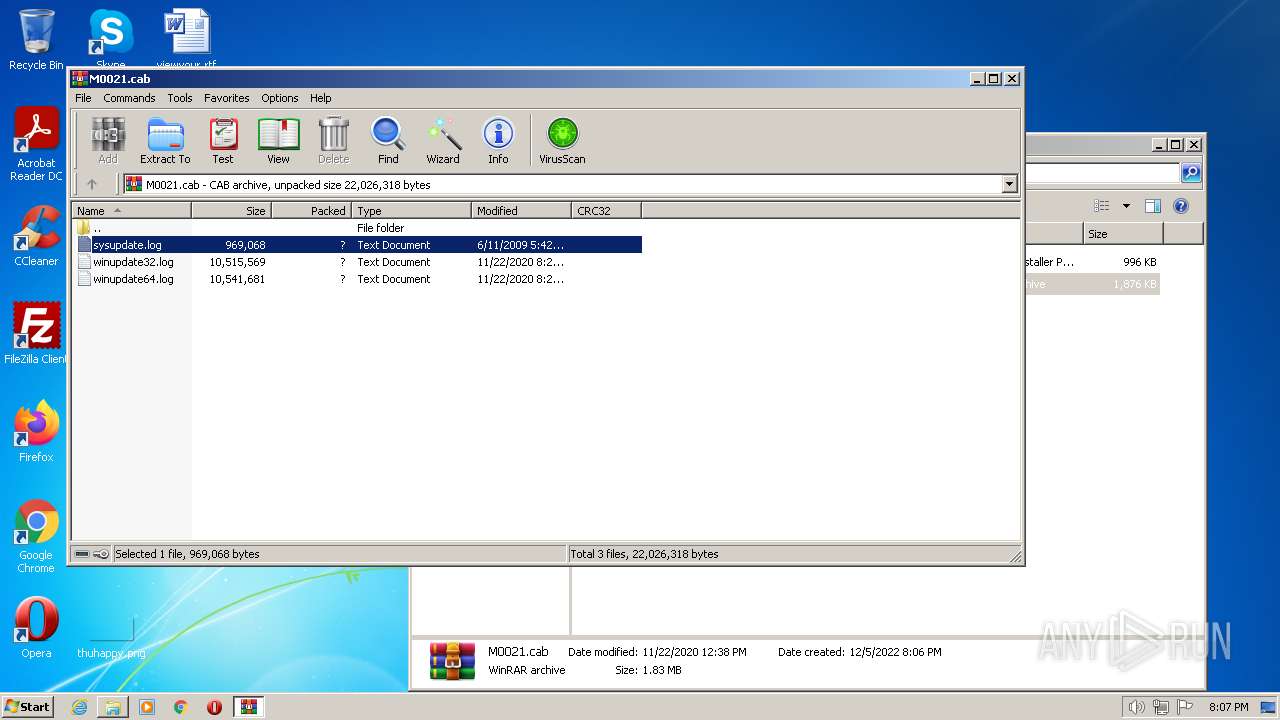
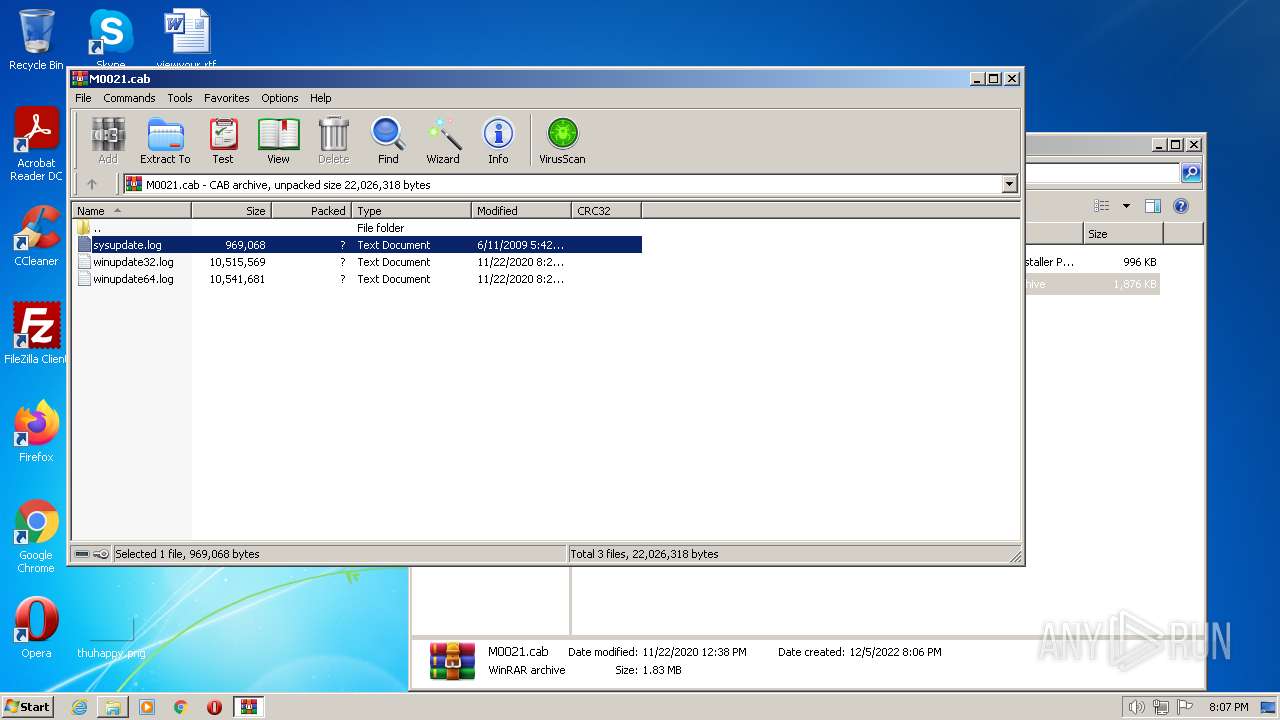
| 3528 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa3528.31134\sysupdate.log | binary | |
MD5:— | SHA256:— | |||
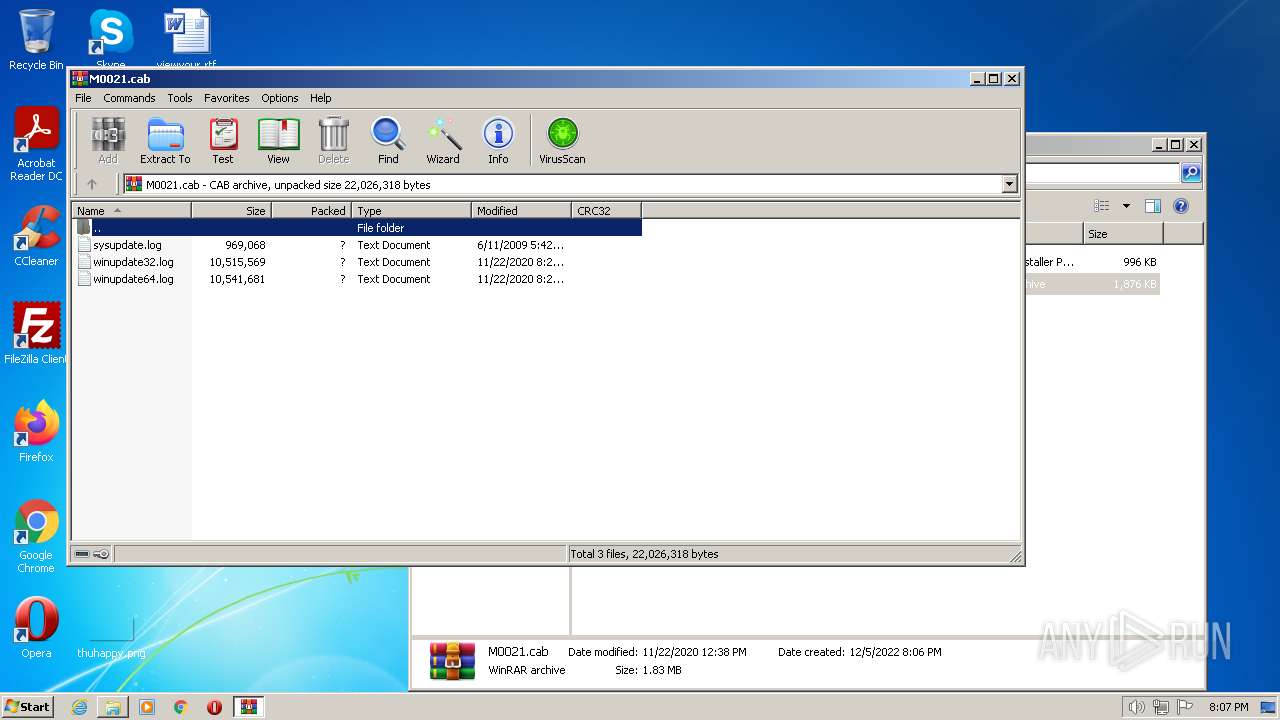
| 1772 | WinRAR.exe | C:\Users\admin\Desktop\pf\M0021.cab | compressed | |
MD5:— | SHA256:— | |||
| 4068 | msiexec.exe | C:\Windows\Installer\1073683.ipi | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
27
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | HEAD | 200 | 104.109.59.136:80 | http://query.prod.cms.rt.microsoft.com/cms/api/am/binary/RE2JgkA?v=133147445309530000 | NL | — | — | whitelisted |
— | — | HEAD | 200 | 23.203.90.83:80 | http://query.prod.cms.rt.microsoft.com/cms/api/am/binary/RE2JgkA?v=133147446004680000 | US | — | — | whitelisted |
3240 | sipnotify.exe | HEAD | 200 | 23.205.225.13:80 | http://query.prod.cms.rt.microsoft.com/cms/api/am/binary/RE2JgkA?v=133147444704350000 | NL | — | — | whitelisted |
3240 | sipnotify.exe | GET | 200 | 23.205.225.13:80 | http://query.prod.cms.rt.microsoft.com/cms/api/am/binary/RE2JgkA?v=133147444704350000 | NL | compressed | 78.4 Kb | whitelisted |
— | — | HEAD | 200 | 23.203.90.83:80 | http://query.prod.cms.rt.microsoft.com/cms/api/am/binary/RE2JgkA?v=133147445655780000 | US | — | — | whitelisted |
3260 | chrome.exe | GET | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvNzI0QUFXNV9zT2RvdUwyMERESEZGVmJnQQ/1.0.0.6_nmmhkkegccagdldgiimedpiccmgmieda.crx | US | crx | 242 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3260 | chrome.exe | 142.250.185.68:443 | www.google.com | GOOGLE | US | whitelisted |
3260 | chrome.exe | 142.250.184.227:443 | clientservices.googleapis.com | GOOGLE | US | whitelisted |
3260 | chrome.exe | 142.250.186.46:443 | clients2.google.com | GOOGLE | US | whitelisted |
3260 | chrome.exe | 216.58.212.161:443 | clients2.googleusercontent.com | GOOGLE | US | whitelisted |
3260 | chrome.exe | 142.250.185.202:443 | fonts.googleapis.com | GOOGLE | US | whitelisted |
3260 | chrome.exe | 142.250.186.131:443 | www.gstatic.com | GOOGLE | US | whitelisted |
3260 | chrome.exe | 172.217.18.3:443 | fonts.gstatic.com | GOOGLE | US | whitelisted |
3260 | chrome.exe | 172.217.16.206:443 | apis.google.com | GOOGLE | US | whitelisted |
3240 | sipnotify.exe | 23.205.225.13:80 | query.prod.cms.rt.microsoft.com | AKAMAI-AS | DE | unknown |
3260 | chrome.exe | 142.250.185.227:443 | ssl.gstatic.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
clients2.google.com |
| whitelisted |
www.google.com |
| malicious |
accounts.google.com |
| shared |
clients2.googleusercontent.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
ssl.gstatic.com |
| whitelisted |
Threats
Process | Message |
|---|---|
MsiExec.exe | [AVX_CRT_Fix][C:\Windows\Installer\MSI376C.tmp] CPU: __isa_available = 5
|
MsiExec.exe | [AVX_CRT_Fix][C:\Windows\Installer\MSI37CB.tmp] CPU: __isa_available = 5
|
MsiExec.exe | [AVX_CRT_Fix][C:\Windows\Installer\MSI37DB.tmp] CPU: __isa_available = 5
|
MsiExec.exe | [AVX_CRT_Fix][C:\Windows\Installer\MSI37FB.tmp] CPU: __isa_available = 5
|