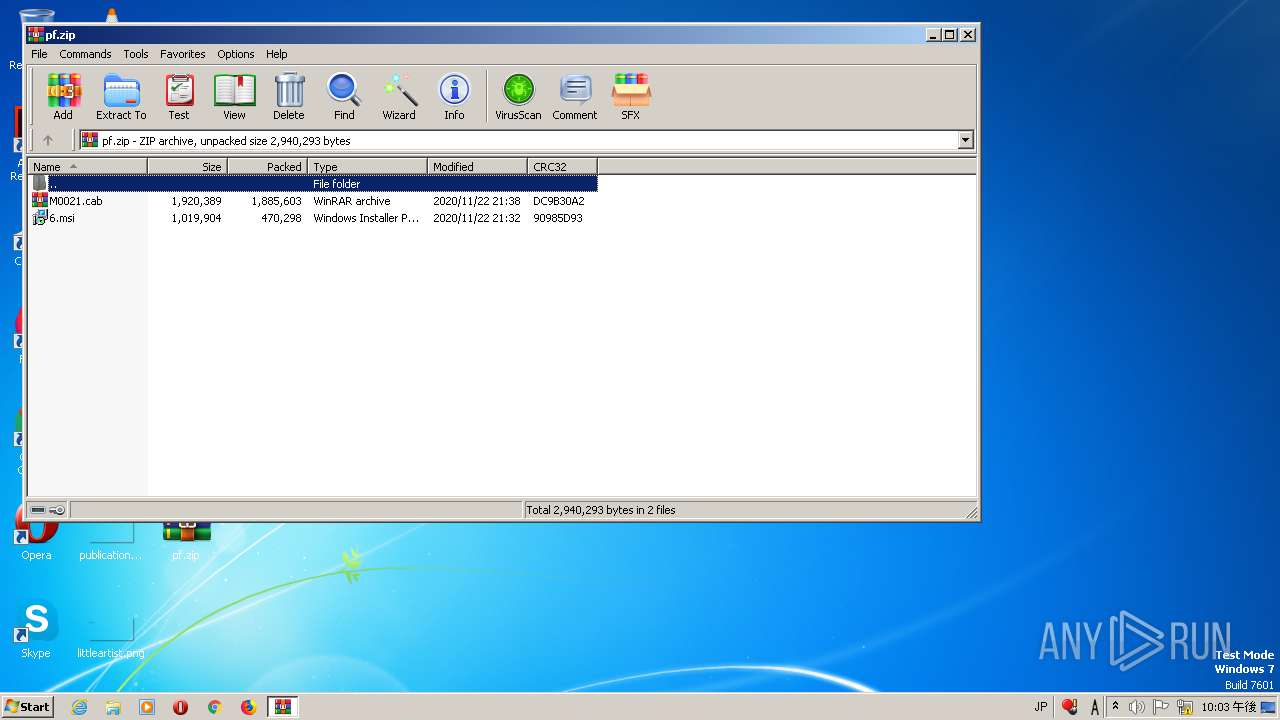
| File name: | pf.zip |
| Full analysis: | https://app.any.run/tasks/48756484-1224-43e5-b094-537761ec1942 |
| Verdict: | Malicious activity |
| Analysis date: | November 22, 2020, 13:03:08 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 90B901191FB837ECD03B591D2CEEFD9A |
| SHA1: | BF200150DD3F4F61898B44F53F6756C804821094 |
| SHA256: | F4C1D831719DEFF3F583396038B9181B316E509AC410132BFA4EE2334C3121F6 |
| SSDEEP: | 49152:TmPNJDnvx4+Zf95vAH3W0l79GFmZS0bn3VLIPLS0Le:6Fr4+Zfh0t9RZS0bn3BSB6 |
MALICIOUS
Disables Windows Defender
- msiexec.exe (PID: 2964)
Loads dropped or rewritten executable
- services.exe (PID: 644)
- svchost.exe (PID: 456)
Runs injected code in another process
- svchost.exe (PID: 460)
- services.exe (PID: 644)
- svchost.exe (PID: 456)
Application was injected by another process
- svchost.exe (PID: 1028)
- svchost.exe (PID: 424)
- svchost.exe (PID: 456)
- winlogon.exe (PID: 372)
Loads the Task Scheduler COM API
- sppsvc.exe (PID: 1104)
Uses SVCHOST.EXE for hidden code execution
- svchost.exe (PID: 1028)
SUSPICIOUS
Uses NETSH.EXE for network configuration
- MsiExec.exe (PID: 1736)
Executes PowerShell scripts
- MsiExec.exe (PID: 1736)
Creates or modifies windows services
- netsh.exe (PID: 2056)
- svchost.exe (PID: 456)
Creates files in the user directory
- powershell.exe (PID: 3000)
Creates files in the Windows directory
- svchost.exe (PID: 456)
- svchost.exe (PID: 424)
- mscorsvw.exe (PID: 2824)
- mscorsvw.exe (PID: 1944)
- svchost.exe (PID: 1028)
- WMIADAP.EXE (PID: 2004)
- msiexec.exe (PID: 2964)
Creates files in the driver directory
- svchost.exe (PID: 456)
Removes files from Windows directory
- svchost.exe (PID: 456)
- svchost.exe (PID: 424)
- svchost.exe (PID: 1028)
- WMIADAP.EXE (PID: 2004)
Drops a file that was compiled in debug mode
- svchost.exe (PID: 456)
- msiexec.exe (PID: 2964)
Drops a file with too old compile date
- svchost.exe (PID: 456)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2696)
- msiexec.exe (PID: 2964)
Creates a directory in Program Files
- msiexec.exe (PID: 2964)
Low-level read access rights to disk partition
- svchost.exe (PID: 424)
Starts SC.EXE for service management
- services.exe (PID: 644)
Reads Environment values
- MsiExec.exe (PID: 1352)
INFO
Loads dropped or rewritten executable
- MsiExec.exe (PID: 1352)
Manual execution by user
- msiexec.exe (PID: 2176)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2020:11:22 21:38:19 |
| ZipCRC: | 0xdc9b30a2 |
| ZipCompressedSize: | 1885603 |
| ZipUncompressedSize: | 1920389 |
| ZipFileName: | M0021.cab |
Total processes
165
Monitored processes
53
Malicious processes
8
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | "C:\Windows\SysWOW64\netsh.exe" ipsec static add filteraction name=FilteraAtion1 action=block | C:\Windows\SysWOW64\netsh.exe | — | MsiExec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 372 | winlogon.exe | C:\Windows\System32\winlogon.exe | — | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Logon Application Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 424 | "C:\Windows\SysWOW64\svchost.exe" -k LocalService | C:\Windows\SysWOW64\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 456 | C:\Windows\system32\svchost.exe -k netsvcs | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 460 | "C:\Windows\SysWOW64\svchost.exe" -k NetworkService | C:\Windows\SysWOW64\svchost.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 644 | C:\Windows\system32\services.exe | C:\Windows\System32\services.exe | — | wininit.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Services and Controller app Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 684 | "C:\Windows\SysWOW64\netsh.exe" ipsec static add filter filterlist=Filter1 srcaddr=Me dstaddr=any dstport=6666 protocol=TCP | C:\Windows\SysWOW64\netsh.exe | — | MsiExec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 684 | "C:\Windows\SysWOW64\takeown.exe" /f C:\Windows\syswow64\cscript.exe | C:\Windows\SysWOW64\takeown.exe | — | MsiExec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Takes ownership of a file Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 912 | "taskhost.exe" | C:\Windows\system32\taskhost.exe | — | services.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 996 | "C:\Windows\SysWOW64\cacls.exe" C:\Windows\syswow64\jscript.dll /E /P everyone:N | C:\Windows\SysWOW64\cacls.exe | — | MsiExec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Control ACLs Program Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
18 306
Read events
16 649
Write events
1 631
Delete events
26
Modification events
| (PID) Process: | (2696) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2696) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2696) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2696) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\pf.zip | |||
| (PID) Process: | (2696) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2696) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2696) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2696) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2696) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | @C:\Windows\System32\msimsg.dll,-34 |
Value: Windows Installer Package | |||
| (PID) Process: | (2696) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF1600000016000000D60300000B020000 | |||
Executable files
6
Suspicious files
31
Text files
4
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2964 | msiexec.exe | C:\Windows\Installer\MSI6CDF.tmp | — | |
MD5:— | SHA256:— | |||
| 2964 | msiexec.exe | C:\Windows\Installer\MSI6D0F.tmp | — | |
MD5:— | SHA256:— | |||
| 2964 | msiexec.exe | C:\Windows\Installer\MSI6D2F.tmp | — | |
MD5:— | SHA256:— | |||
| 2964 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\~DFFA96E4BA66BDF2A8.TMP | — | |
MD5:— | SHA256:— | |||
| 2964 | msiexec.exe | C:\Config.Msi\186540.rbs | — | |
MD5:— | SHA256:— | |||
| 2964 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\~DFC2A6D4A18E956473.TMP | — | |
MD5:— | SHA256:— | |||
| 2964 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\~DF163B0130CD53AACE.TMP | — | |
MD5:— | SHA256:— | |||
| 3000 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\UNIRVML18TXRDXAGXLCU.temp | — | |
MD5:— | SHA256:— | |||
| 456 | svchost.exe | C:\Windows\System32\drivers\dump_VMBUS.sys | — | |
MD5:— | SHA256:— | |||
| 456 | svchost.exe | C:\Windows\system32\MsE6E0D97CApp.dll | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
96
TCP/UDP connections
17 456
DNS requests
5
Threats
82
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2352 | svchost.exe | HEAD | 200 | 58.229.194.122:11627 | http://58.229.194.122:11627/0BC8EC41.moe | KR | — | — | unknown |
2352 | svchost.exe | HEAD | 200 | 45.76.155.140:13317 | http://45.76.155.140:13317/0BC8EC41.moe | SG | — | — | suspicious |
2352 | svchost.exe | HEAD | 200 | 172.106.32.32:19232 | http://172.106.32.32:19232/0BC8EC41.moe | US | — | — | unknown |
2352 | svchost.exe | HEAD | 200 | 1.248.75.9:18035 | http://1.248.75.9:18035/0BC8EC41.moe | KR | — | — | malicious |
2352 | svchost.exe | HEAD | 200 | 63.209.0.101:19667 | http://63.209.0.101:19667/0BC8EC41.moe | US | — | — | suspicious |
2352 | svchost.exe | HEAD | 200 | 58.229.194.122:11627 | http://58.229.194.122:11627/0BC8EC41.moe | KR | — | — | unknown |
2352 | svchost.exe | HEAD | 200 | 45.32.155.0:14217 | http://45.32.155.0:14217/0BC8EC41.moe | DE | — | — | suspicious |
2352 | svchost.exe | HEAD | 200 | 63.209.0.101:19667 | http://63.209.0.101:19667/0BC8EC41.moe | US | — | — | suspicious |
2352 | svchost.exe | HEAD | 200 | 149.28.193.205:19487 | http://149.28.193.205:19487/0BC8EC41.moe | US | — | — | malicious |
2352 | svchost.exe | HEAD | 200 | 58.229.194.121:11532 | http://58.229.194.121:11532/0BC8EC41.moe | KR | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
424 | svchost.exe | 51.105.208.173:80 | time.windows.com | Microsoft Corporation | GB | unknown |
424 | svchost.exe | 175.188.188.205:19486 | — | China Networks Inter-Exchange | CN | suspicious |
1028 | svchost.exe | 45.76.204.9:25739 | — | Choopa, LLC | JP | unknown |
424 | svchost.exe | 210.212.235.51:14755 | — | National Internet Backbone | IN | suspicious |
1028 | svchost.exe | 210.16.120.35:32139 | — | SoftLayer Technologies Inc. | SG | unknown |
2316 | svchost.exe | 108.61.216.239:443 | — | Choopa, LLC | US | unknown |
2352 | svchost.exe | 45.124.193.230:445 | — | National Internet Backbone | IN | unknown |
1028 | svchost.exe | 1.248.75.8:17182 | — | SK Broadband Co Ltd | KR | malicious |
2352 | svchost.exe | 45.124.25.52:445 | — | Cloudie Limited | HK | unknown |
424 | svchost.exe | 45.32.155.0:10121 | — | Choopa, LLC | DE | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
teredo.ipv6.microsoft.com |
| whitelisted |
time.windows.com |
| whitelisted |
Rpc.1qw.us |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
424 | svchost.exe | A Network Trojan was detected | LOADER [PTsecurity] PhantomNugget |
424 | svchost.exe | A Network Trojan was detected | LOADER [PTsecurity] PhantomNugget |
1028 | svchost.exe | A Network Trojan was detected | LOADER [PTsecurity] PhantomNugget |
2352 | svchost.exe | Misc activity | ET SCAN Behavioral Unusual Port 445 traffic Potential Scan or Infection |
2352 | svchost.exe | Generic Protocol Command Decode | SURICATA HTTP unable to match response to request |
2352 | svchost.exe | Misc Attack | ET CINS Active Threat Intelligence Poor Reputation IP group 1 |
2352 | svchost.exe | Generic Protocol Command Decode | SURICATA HTTP unable to match response to request |
2352 | svchost.exe | Generic Protocol Command Decode | SURICATA HTTP unable to match response to request |
2352 | svchost.exe | Generic Protocol Command Decode | SURICATA HTTP unable to match response to request |
2352 | svchost.exe | Generic Protocol Command Decode | SURICATA HTTP unable to match response to request |
Process | Message |
|---|---|
MsiExec.exe | [AVX_CRT_Fix][C:\Windows\Installer\MSI6934.tmp] CPU: __isa_available = 5
|
MsiExec.exe | [AVX_CRT_Fix][C:\Windows\Installer\MSI6CDF.tmp] CPU: __isa_available = 5
|
MsiExec.exe | [AVX_CRT_Fix][C:\Windows\Installer\MSI6D0F.tmp] CPU: __isa_available = 5
|
MsiExec.exe | [AVX_CRT_Fix][C:\Windows\Installer\MSI6D2F.tmp] CPU: __isa_available = 5
|