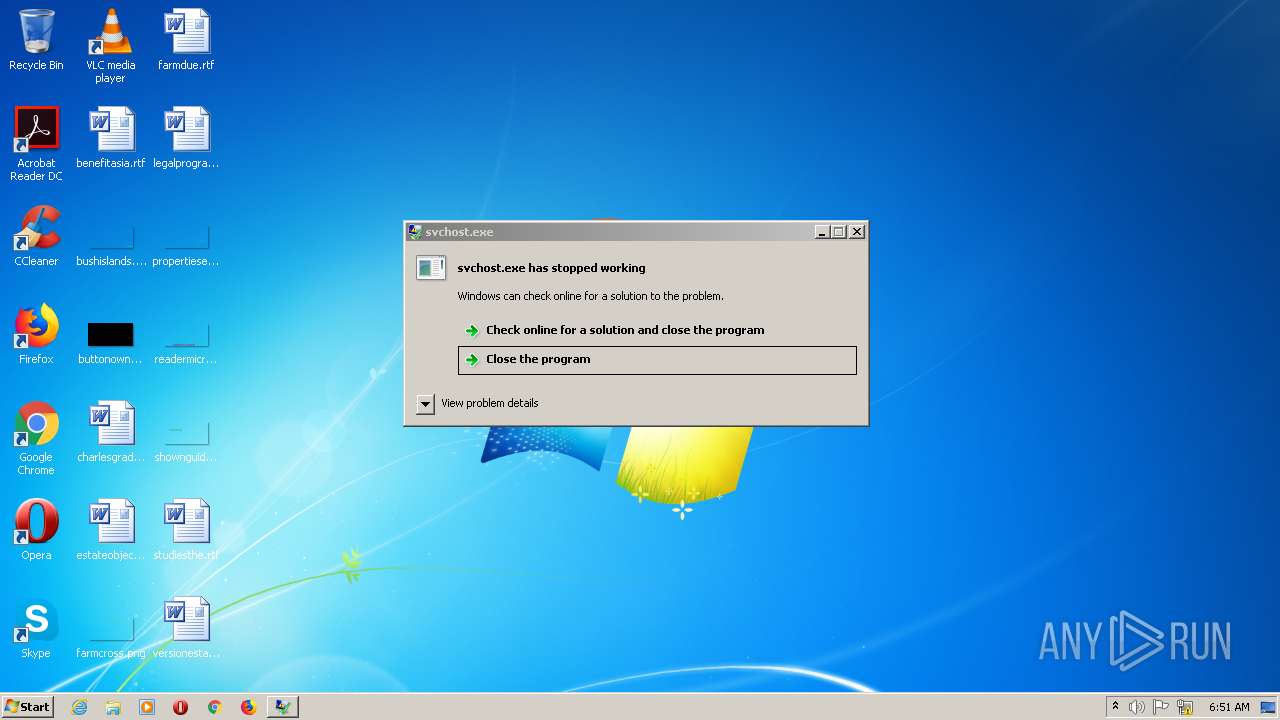
| download: | svchost.exe |
| Full analysis: | https://app.any.run/tasks/7cb3ae3c-f426-4e37-b183-1c19dafac8ba |
| Verdict: | Malicious activity |
| Analysis date: | February 10, 2022, 06:51:31 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 86B94F253E62C80A9BD7CF6D9CBAB71B |
| SHA1: | 6A6E680EEBFBEDCA9C079E2FC3EBB88AE8A4BA72 |
| SHA256: | F4B1ADDE20BD198A03E68758D147BE76756FD99156EC6774FE0EF7AA41EF0EB1 |
| SSDEEP: | 98304:ZCOLmFpKYiLajmnLkz4FGi1g7sh7WZB9falugQB2CB0M:Z5q7gajmYz4vhKZB9BBdB0M |
MALICIOUS
Changes the autorun value in the registry
- AppLaunch.exe (PID: 1616)
Drops executable file immediately after starts
- AppLaunch.exe (PID: 1616)
Loads the Task Scheduler COM API
- schtasks.exe (PID: 2668)
- schtasks.exe (PID: 2344)
- schtasks.exe (PID: 2912)
- schtasks.exe (PID: 2532)
- schtasks.exe (PID: 1224)
- schtasks.exe (PID: 2520)
Application was dropped or rewritten from another process
- SearchProtocolHost.exe (PID: 760)
- AppLaunch.exe (PID: 1616)
- SearchFilterHost.exe (PID: 972)
SUSPICIOUS
Reads Environment values
- AppLaunch.exe (PID: 1616)
Reads the computer name
- AppLaunch.exe (PID: 1616)
Checks supported languages
- svchost.exe (PID: 2516)
- AppLaunch.exe (PID: 1616)
- SearchProtocolHost.exe (PID: 760)
- SearchFilterHost.exe (PID: 972)
- cmd.exe (PID: 2016)
Creates files in the user directory
- AppLaunch.exe (PID: 1616)
Creates files in the program directory
- AppLaunch.exe (PID: 1616)
Executed via WMI
- schtasks.exe (PID: 2344)
- schtasks.exe (PID: 2668)
- schtasks.exe (PID: 2912)
- schtasks.exe (PID: 2532)
- schtasks.exe (PID: 1224)
- schtasks.exe (PID: 2520)
Creates files in the Windows directory
- AppLaunch.exe (PID: 1616)
Executable content was dropped or overwritten
- AppLaunch.exe (PID: 1616)
Drops a file that was compiled in debug mode
- AppLaunch.exe (PID: 1616)
Executed via Task Scheduler
- SearchProtocolHost.exe (PID: 760)
- SearchFilterHost.exe (PID: 972)
Starts CMD.EXE for commands execution
- AppLaunch.exe (PID: 1616)
INFO
Checks supported languages
- schtasks.exe (PID: 2668)
- schtasks.exe (PID: 2344)
- schtasks.exe (PID: 2520)
- schtasks.exe (PID: 2912)
- schtasks.exe (PID: 2532)
- schtasks.exe (PID: 1224)
- w32tm.exe (PID: 2504)
- w32tm.exe (PID: 2520)
Reads the computer name
- schtasks.exe (PID: 2668)
- schtasks.exe (PID: 2344)
- schtasks.exe (PID: 2520)
- schtasks.exe (PID: 2912)
- schtasks.exe (PID: 2532)
- schtasks.exe (PID: 1224)
- w32tm.exe (PID: 2520)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .dll | | | Win32 Dynamic Link Library (generic) (43.5) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (29.8) |
| .exe | | | Generic Win/DOS Executable (13.2) |
| .exe | | | DOS Executable Generic (13.2) |
EXIF
EXE
| Subsystem: | Windows GUI |
|---|---|
| SubsystemVersion: | 6 |
| ImageVersion: | - |
| OSVersion: | 6 |
| EntryPoint: | 0x35000 |
| UninitializedDataSize: | - |
| InitializedDataSize: | 550400 |
| CodeSize: | 138752 |
| LinkerVersion: | 14.29 |
| PEType: | PE32 |
| TimeStamp: | 2022:02:08 21:32:57+01:00 |
| MachineType: | Intel 386 or later, and compatibles |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 08-Feb-2022 20:32:57 |
| Detected languages: |
|
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000080 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 12 |
| Time date stamp: | 08-Feb-2022 20:32:57 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
0x001F6000 | 0x002FB000 | 0x002C9600 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 7.99994 | |
.rsrc | 0x004F1000 | 0x00075000 | 0x00053400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 7.99938 |
.8kgJGxt | 0x00566000 | 0x0004B000 | 0x0004B000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 7.91889 |
.adata | 0x005B1000 | 0x00001000 | 0x00000000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 4.91161 | 381 | UNKNOWN | English - United States | RT_MANIFEST |
101 | 7.96976 | 475136 | UNKNOWN | Russian - Russia | RT_RCDATA |
Imports
kernel32.dll |
oleaut32.dll |
user32.dll |
Total processes
49
Monitored processes
13
Malicious processes
1
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 760 | C:\ProgramData\Documents\SearchProtocolHost.exe | C:\ProgramData\Documents\SearchProtocolHost.exe | — | taskeng.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 972 | C:\ProgramData\Mozilla\updates\308046B0AF4A39CB\SearchFilterHost.exe | C:\ProgramData\Mozilla\updates\308046B0AF4A39CB\SearchFilterHost.exe | — | taskeng.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET ClickOnce Launch Utility Exit code: 0 Version: 4.7.2558.0 built by: NET471REL1 Modules
| |||||||||||||||
| 1224 | schtasks.exe /create /tn "SearchProtocolHost" /sc minute /mo 5 /tr "'C:\ProgramData\Documents\SearchProtocolHost.exe'" /f | C:\Windows\system32\schtasks.exe | — | wmiprvse.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1616 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\AppLaunch.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\AppLaunch.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET ClickOnce Launch Utility Exit code: 0 Version: 4.7.2558.0 built by: NET471REL1 Modules
| |||||||||||||||
| 2016 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\0JvQ77EmgM.bat" " | C:\Windows\SysWOW64\cmd.exe | — | AppLaunch.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2344 | schtasks.exe /create /tn "SearchFilterHost" /sc minute /mo 13 /tr "'C:\ProgramData\Application Data\SearchFilterHost.exe'" /f | C:\Windows\system32\schtasks.exe | — | wmiprvse.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2504 | w32tm /stripchart /computer:localhost /period:5 /dataonly /samples:2 | C:\Windows\SysWOW64\w32tm.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Time Service Diagnostic Tool Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2516 | "C:\Users\admin\AppData\Local\Temp\svchost.exe" | C:\Users\admin\AppData\Local\Temp\svchost.exe | Explorer.EXE | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226505 Modules
| |||||||||||||||
| 2520 | schtasks.exe /create /tn "csrss" /sc minute /mo 12 /tr "'C:\Windows\Registration\CRMLog\csrss.exe'" /f | C:\Windows\system32\schtasks.exe | — | wmiprvse.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2520 | w32tm /stripchart /computer:localhost /period:5 /dataonly /samples:2 | C:\Windows\system32\w32tm.exe | — | w32tm.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Time Service Diagnostic Tool Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
1 222
Read events
1 207
Write events
15
Delete events
0
Modification events
| (PID) Process: | (1616) AppLaunch.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | lsm |
Value: "C:\Users\admin\Application Data\lsm.exe" | |||
| (PID) Process: | (1616) AppLaunch.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | SearchFilterHost |
Value: "C:\ProgramData\Application Data\SearchFilterHost.exe" | |||
| (PID) Process: | (1616) AppLaunch.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | csrss |
Value: "C:\Windows\Registration\CRMLog\csrss.exe" | |||
| (PID) Process: | (1616) AppLaunch.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | WmiPrvSE |
Value: "C:\Users\Public\Downloads\WmiPrvSE.exe" | |||
| (PID) Process: | (1616) AppLaunch.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | SearchFilterHost |
Value: "C:\ProgramData\Mozilla\updates\308046B0AF4A39CB\SearchFilterHost.exe" | |||
| (PID) Process: | (1616) AppLaunch.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | SearchProtocolHost |
Value: "C:\ProgramData\Documents\SearchProtocolHost.exe" | |||
| (PID) Process: | (1616) AppLaunch.exe | Key: | HKEY_CURRENT_USER\Software\62315eb2ce74ab76d140998bd2748fd3dd7d90ba |
| Operation: | write | Name: | bd03b5ae72e753c9c909409c7c281553382b0f5b |
Value: WyJDOlxcV2luZG93c1xcTWljcm9zb2Z0Lk5FVFxcRnJhbWV3b3JrXFx2NC4wLjMwMzE5XFxBcHBMYXVuY2guZXhlIiwiQzpcXFVzZXJzXFxhZG1pblxcQXBwbGljYXRpb24gRGF0YVxcbHNtLmV4ZSIsIkM6XFxQcm9ncmFtRGF0YVxcQXBwbGljYXRpb24gRGF0YVxcU2VhcmNoRmlsdGVySG9zdC5leGUiLCJDOlxcV2luZG93c1xcUmVnaXN0cmF0aW9uXFxDUk1Mb2dcXGNzcnNzLmV4ZSIsIkM6XFxVc2Vyc1xcUHVibGljXFxEb3dubG9hZHNcXFdtaVBydlNFLmV4ZSIsIkM6XFxQcm9ncmFtRGF0YVxcTW96aWxsYVxcdXBkYXRlc1xcMzA4MDQ2QjBBRjRBMzlDQlxcU2VhcmNoRmlsdGVySG9zdC5leGUiLCJDOlxcUHJvZ3JhbURhdGFcXERvY3VtZW50c1xcU2VhcmNoUHJvdG9jb2xIb3N0LmV4ZSJd | |||
| (PID) Process: | (1616) AppLaunch.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1616) AppLaunch.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1616) AppLaunch.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
Executable files
6
Suspicious files
0
Text files
8
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1616 | AppLaunch.exe | C:\Users\admin\AppData\Roaming\101b941d020240 | text | |
MD5:— | SHA256:— | |||
| 1616 | AppLaunch.exe | C:\Windows\Registration\CRMLog\886983d96e3d3e | text | |
MD5:— | SHA256:— | |||
| 1616 | AppLaunch.exe | C:\Users\Public\Downloads\24dbde2999530e | text | |
MD5:— | SHA256:— | |||
| 1616 | AppLaunch.exe | C:\ProgramData\Mozilla\updates\308046B0AF4A39CB\617403385cfa57 | text | |
MD5:— | SHA256:— | |||
| 1616 | AppLaunch.exe | C:\Users\Public\Documents\e8aa3d0a77e909 | text | |
MD5:— | SHA256:— | |||
| 1616 | AppLaunch.exe | C:\ProgramData\617403385cfa57 | text | |
MD5:— | SHA256:— | |||
| 1616 | AppLaunch.exe | C:\Windows\Registration\CRMLog\csrss.exe | executable | |
MD5:BC1A4DE777289D40DAC89AFD68C4AD03 | SHA256:74437FB7E1839A3EFBCF1A82397FBA04BBFBF46095DD95DBB7A95C39EF55EB2F | |||
| 1616 | AppLaunch.exe | C:\Users\admin\AppData\Roaming\lsm.exe | executable | |
MD5:BC1A4DE777289D40DAC89AFD68C4AD03 | SHA256:74437FB7E1839A3EFBCF1A82397FBA04BBFBF46095DD95DBB7A95C39EF55EB2F | |||
| 1616 | AppLaunch.exe | C:\ProgramData\Mozilla\updates\308046B0AF4A39CB\SearchFilterHost.exe | executable | |
MD5:BC1A4DE777289D40DAC89AFD68C4AD03 | SHA256:74437FB7E1839A3EFBCF1A82397FBA04BBFBF46095DD95DBB7A95C39EF55EB2F | |||
| 1616 | AppLaunch.exe | C:\Users\admin\AppData\Local\Temp\FE9OR05HxV | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report