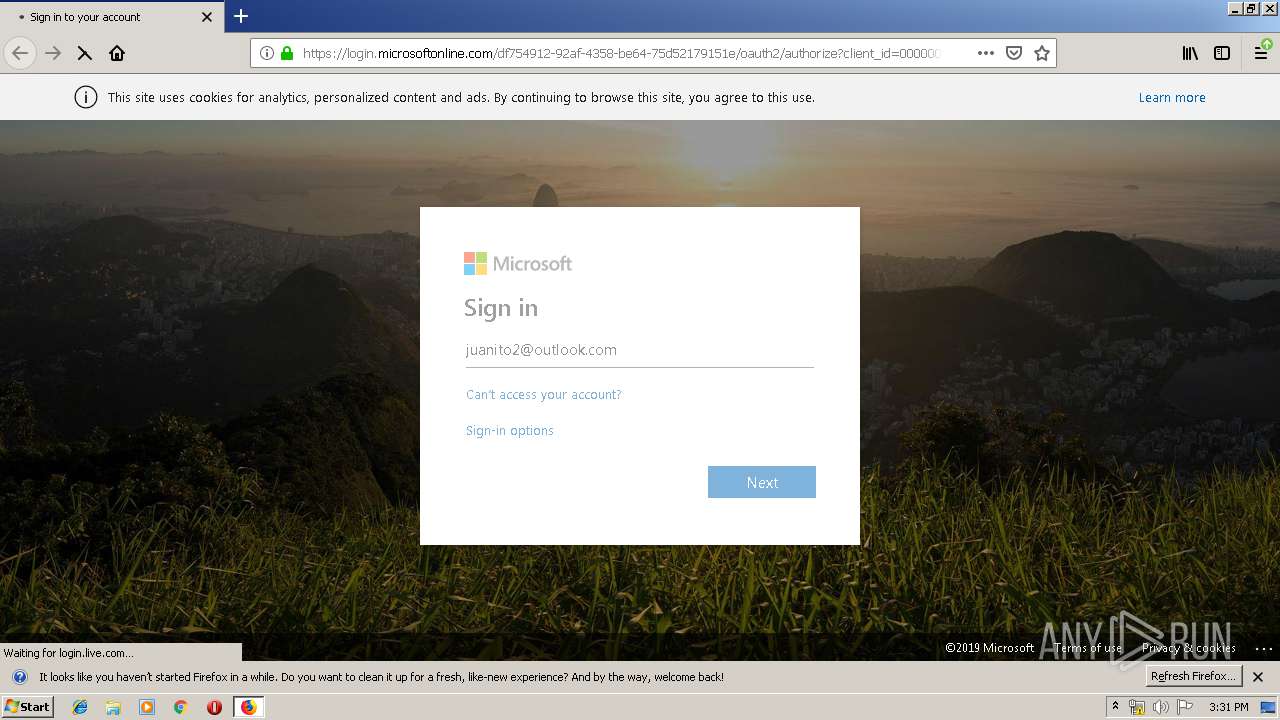
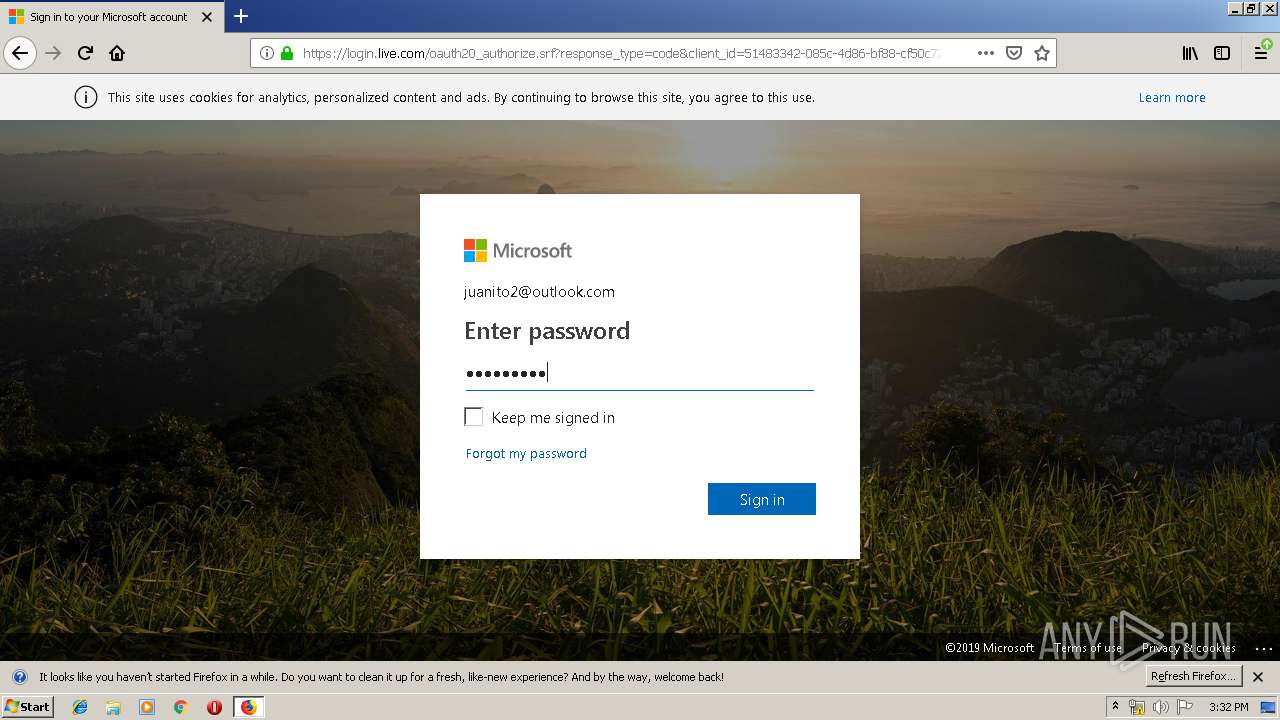
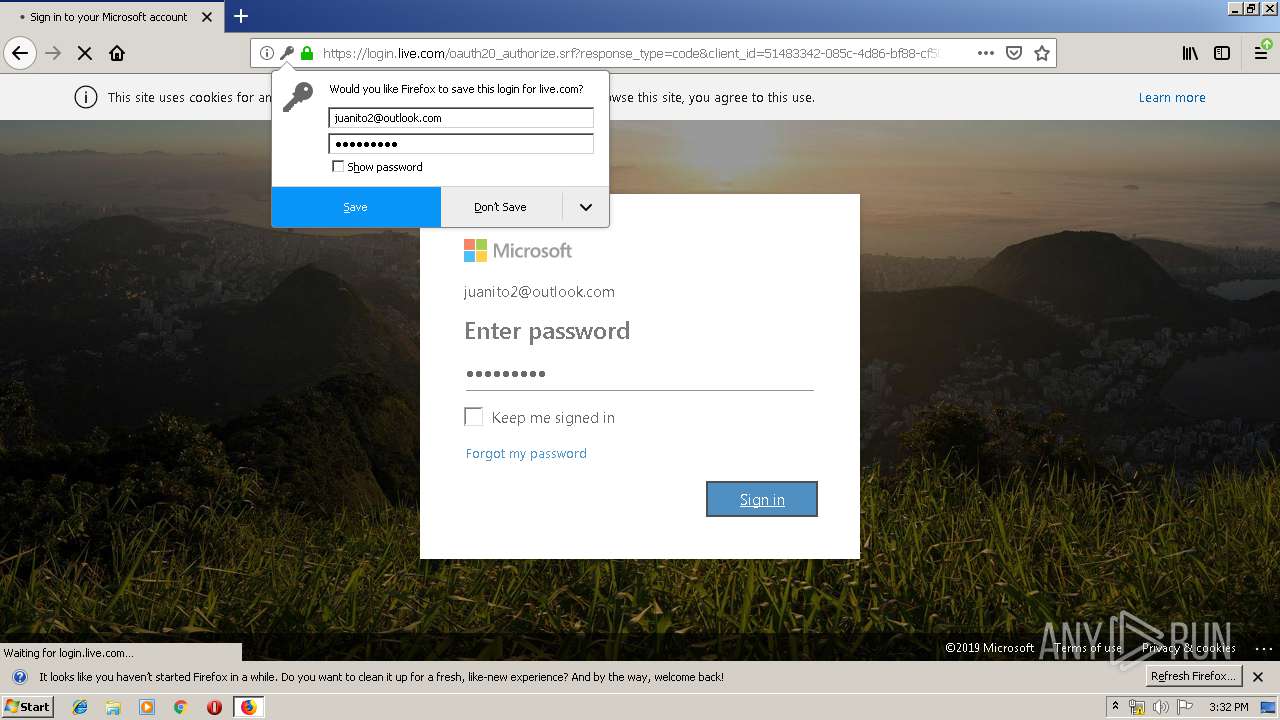
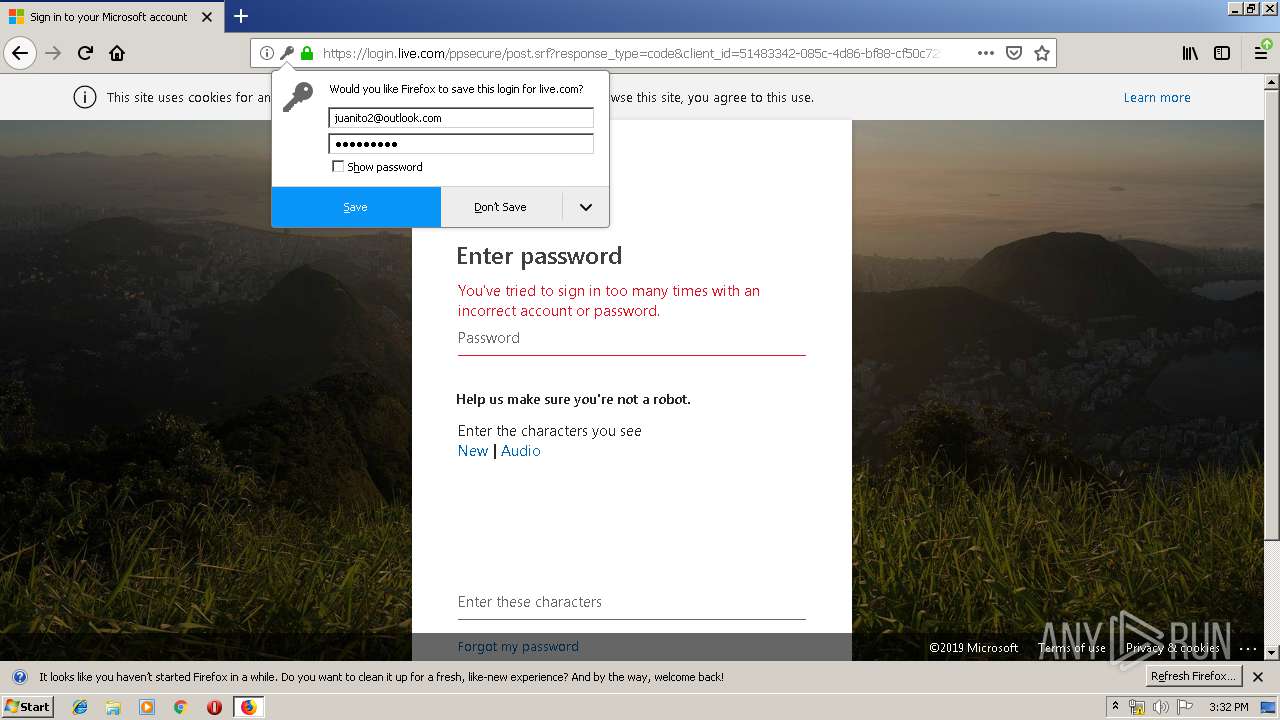
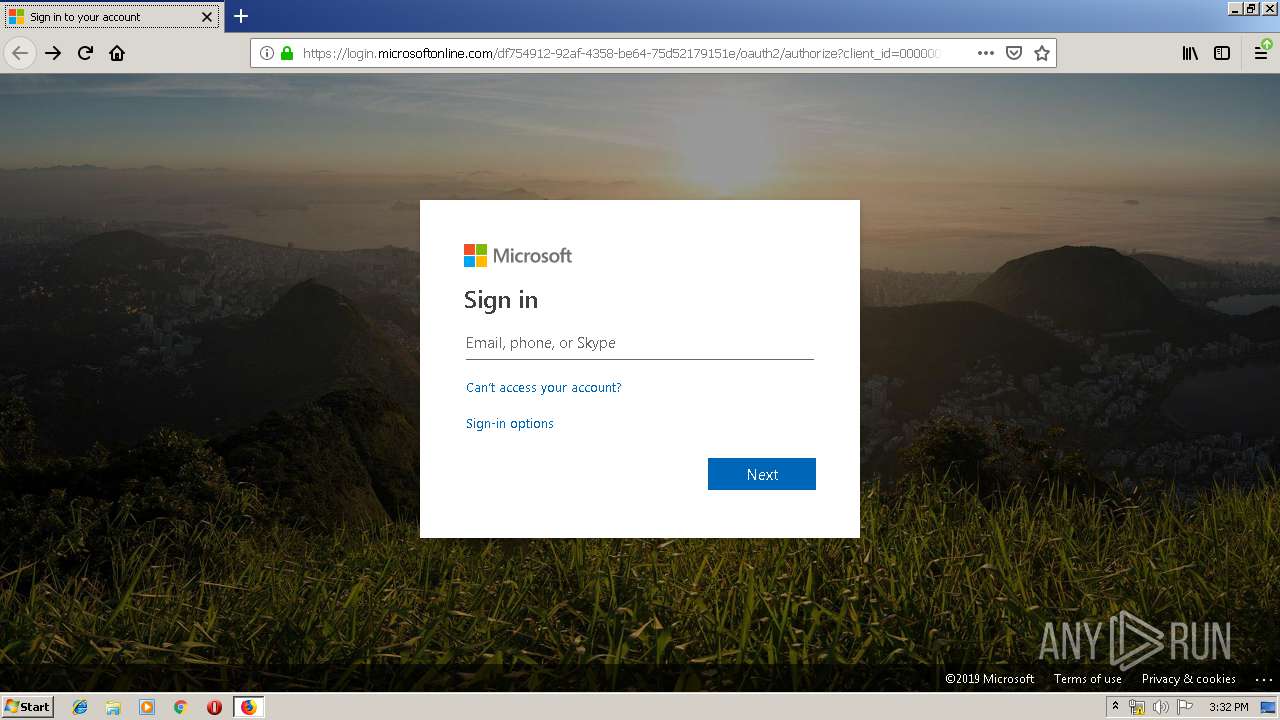
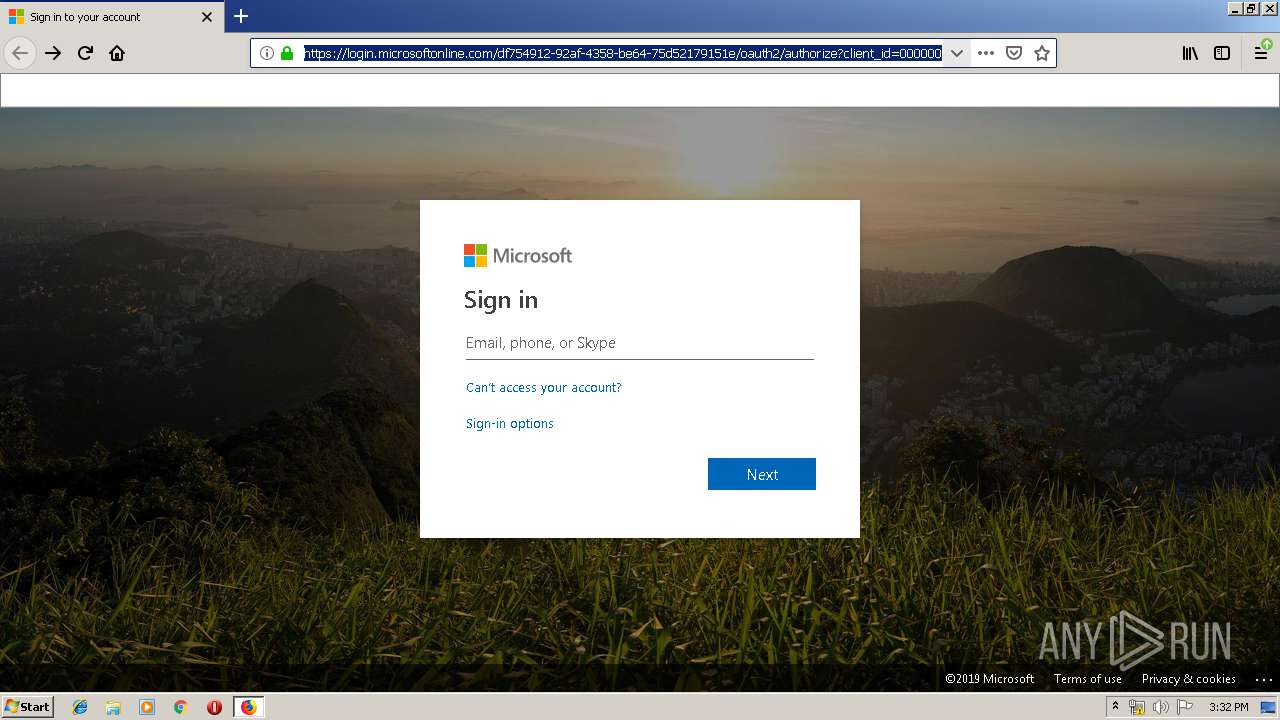
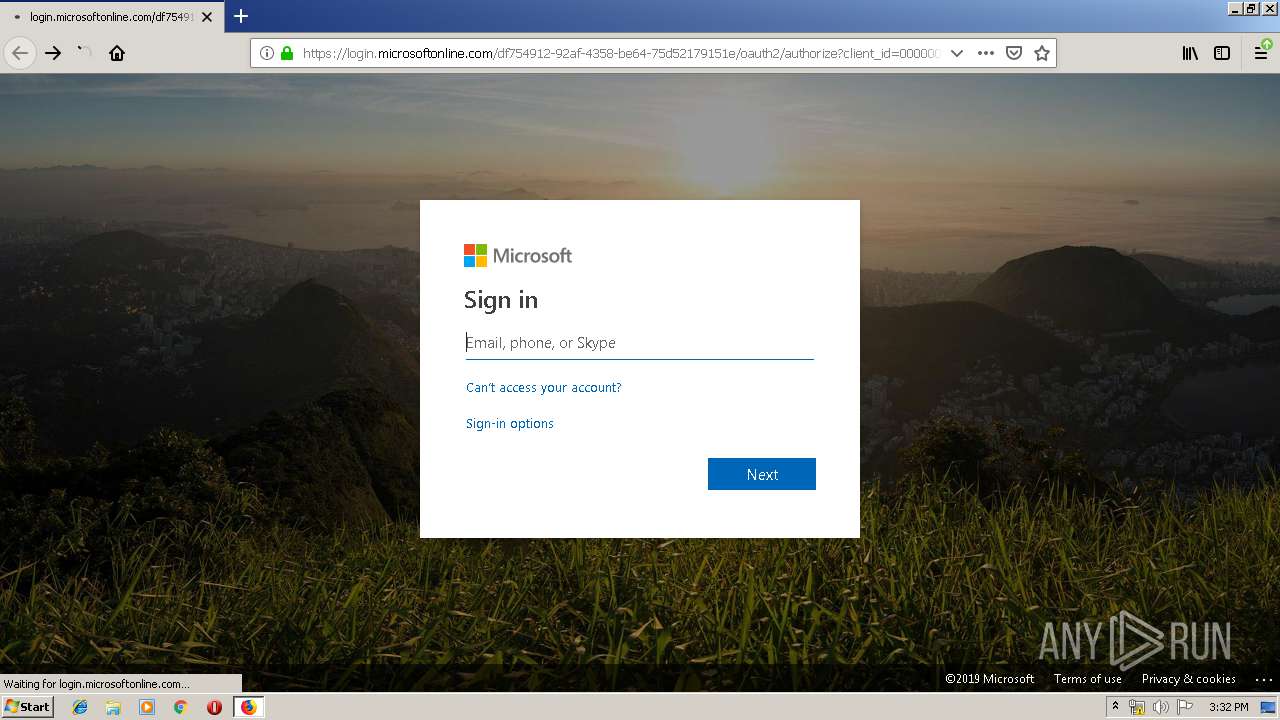
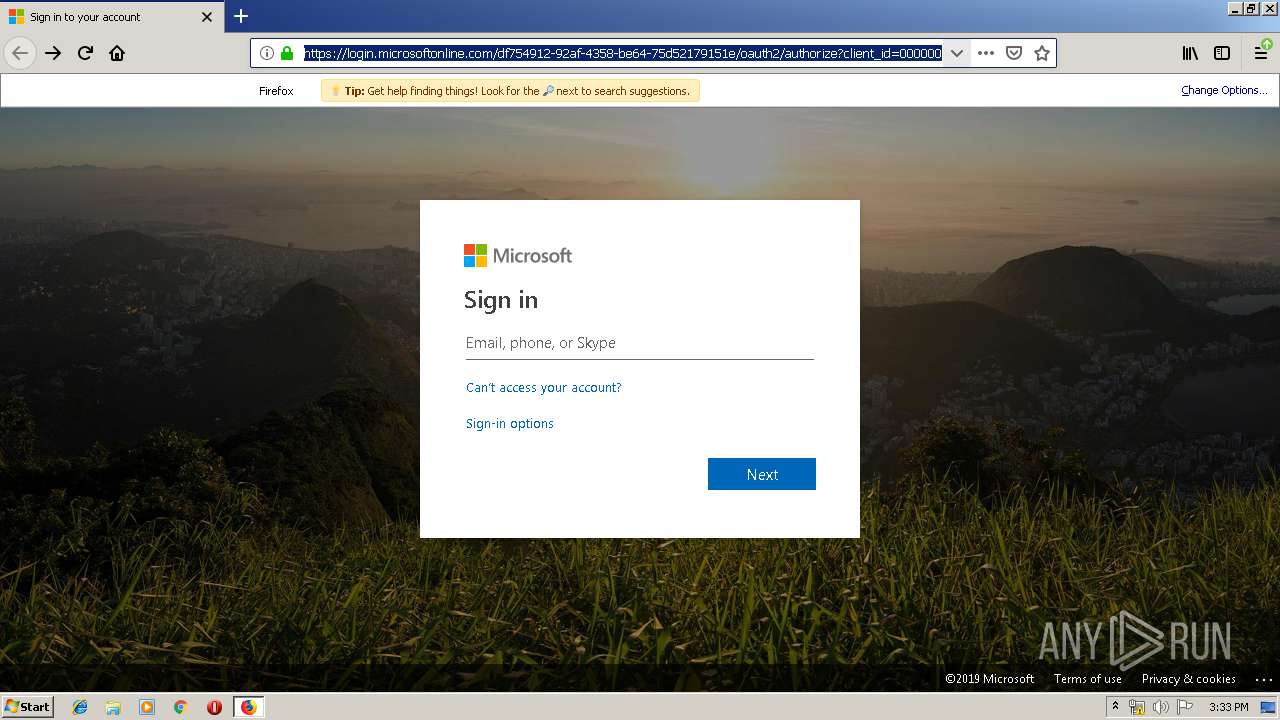
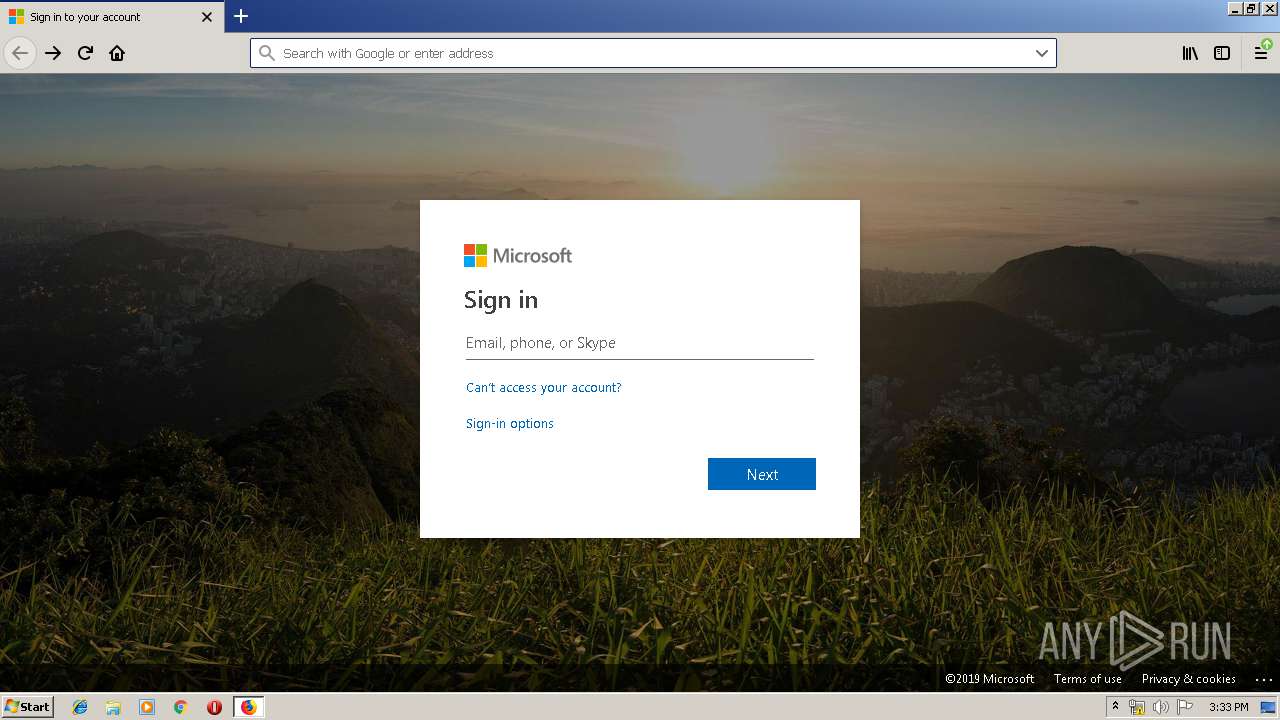
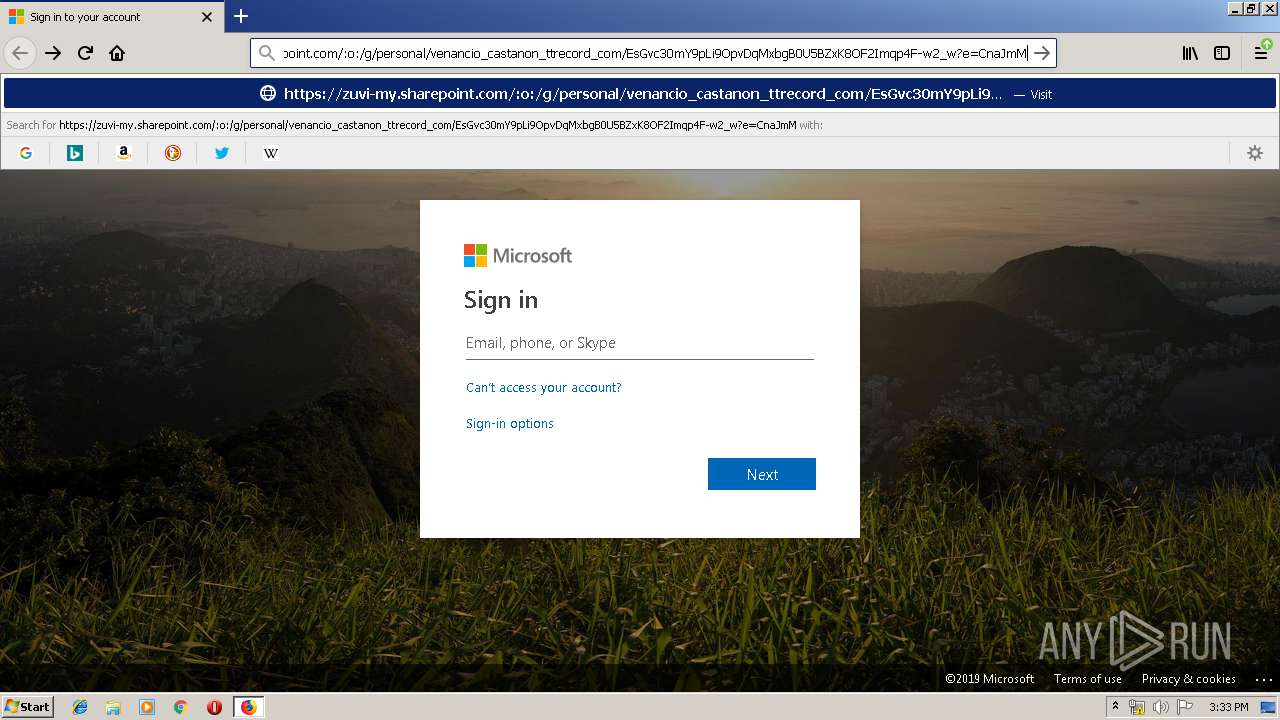
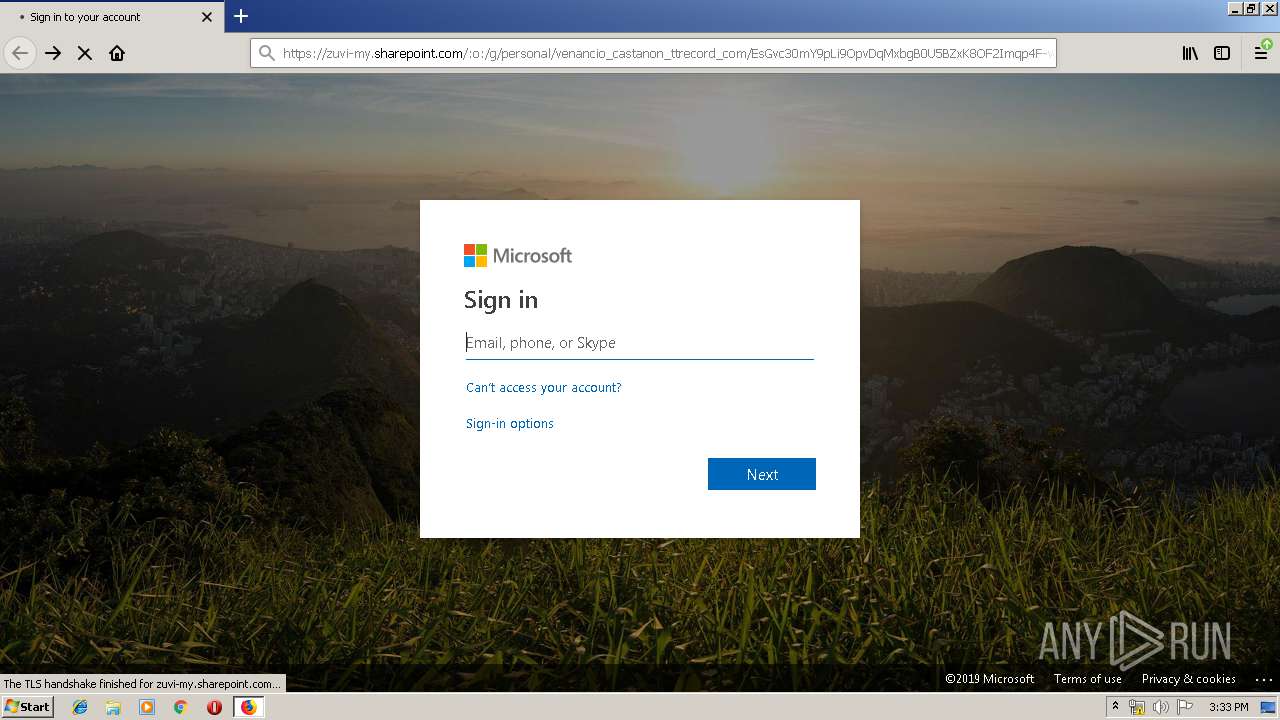
| URL: | https://zuvi-my.sharepoint.com/personal/venancio_castanon_ttrecord_com/_layouts/15/WopiFrame.aspx?sourcedoc={7d73afc1-6326-4bda-8bd3-a9bc3a8cc5b8}&action=view&wd=target%28Transactional%20Track%20Record%20Propuesta.one%7C48ae4680-daa1-4ae2-b322-fdc4107448de%2FTTR%20Propuesta%7C258e353a-b8e5-470d-bf6e-10032cf4bf67%2F%29 |
| Full analysis: | https://app.any.run/tasks/8f16fba7-ce0c-45aa-bd90-401a59a45157 |
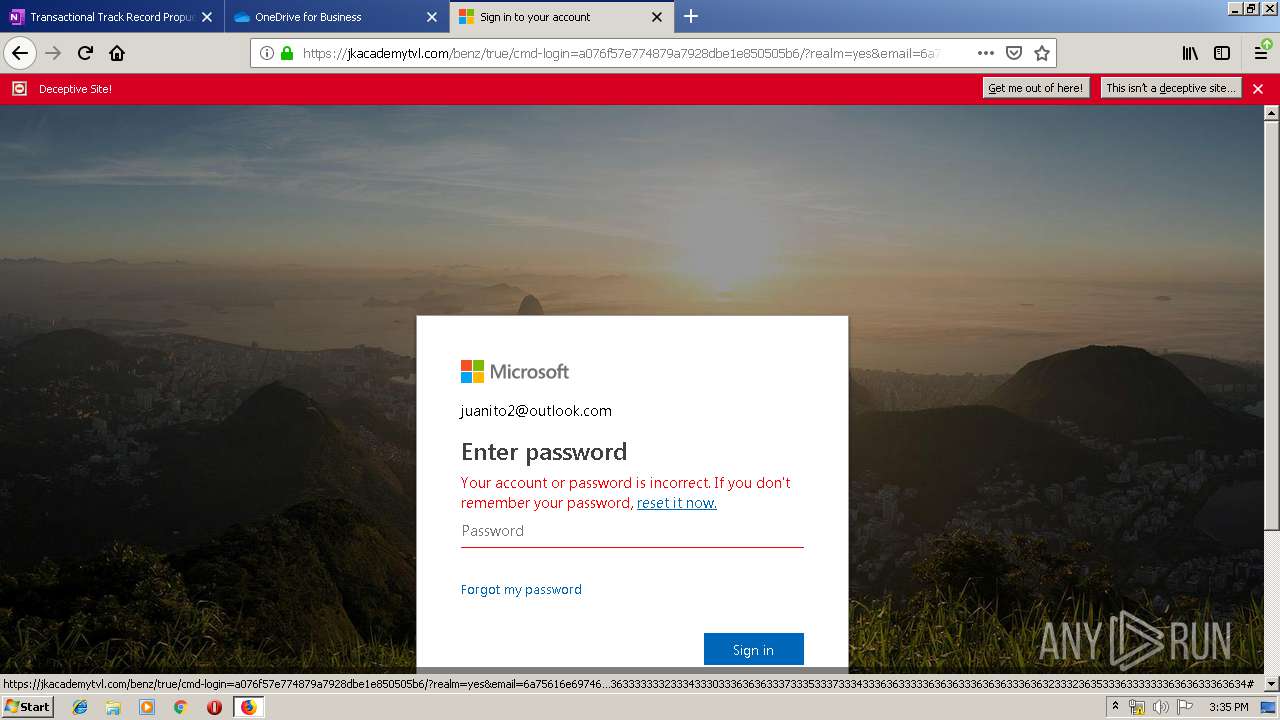
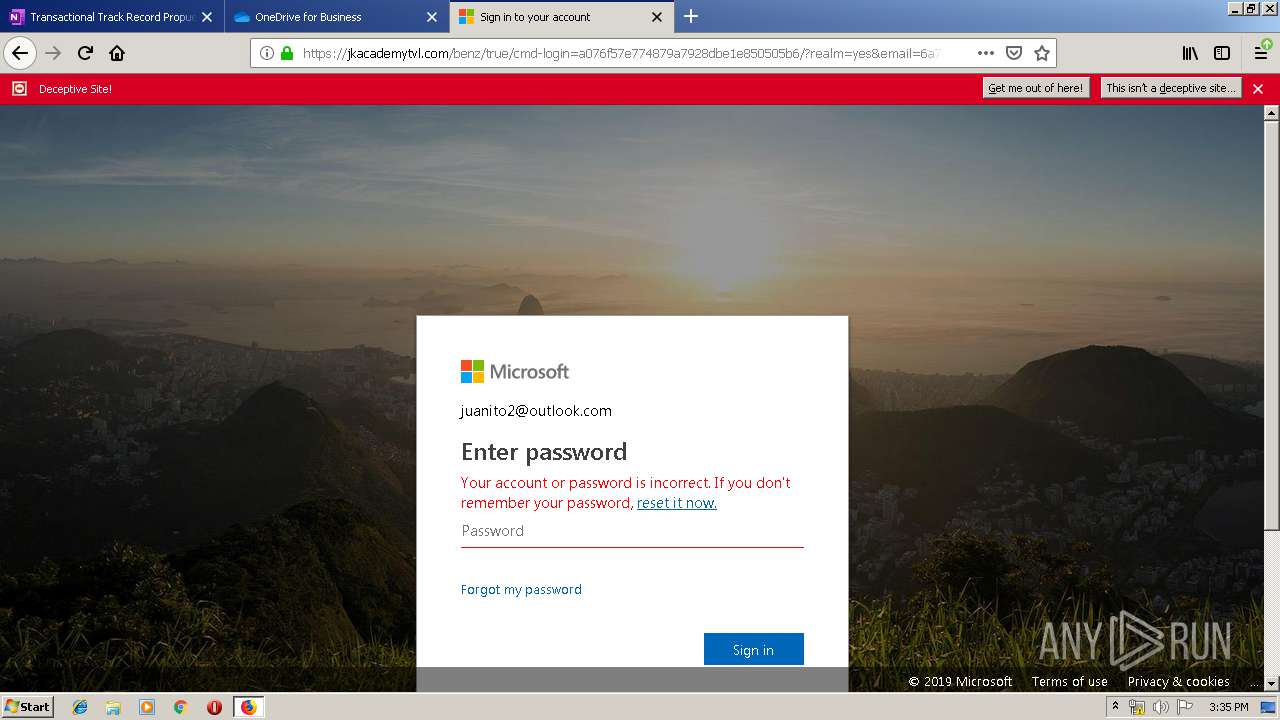
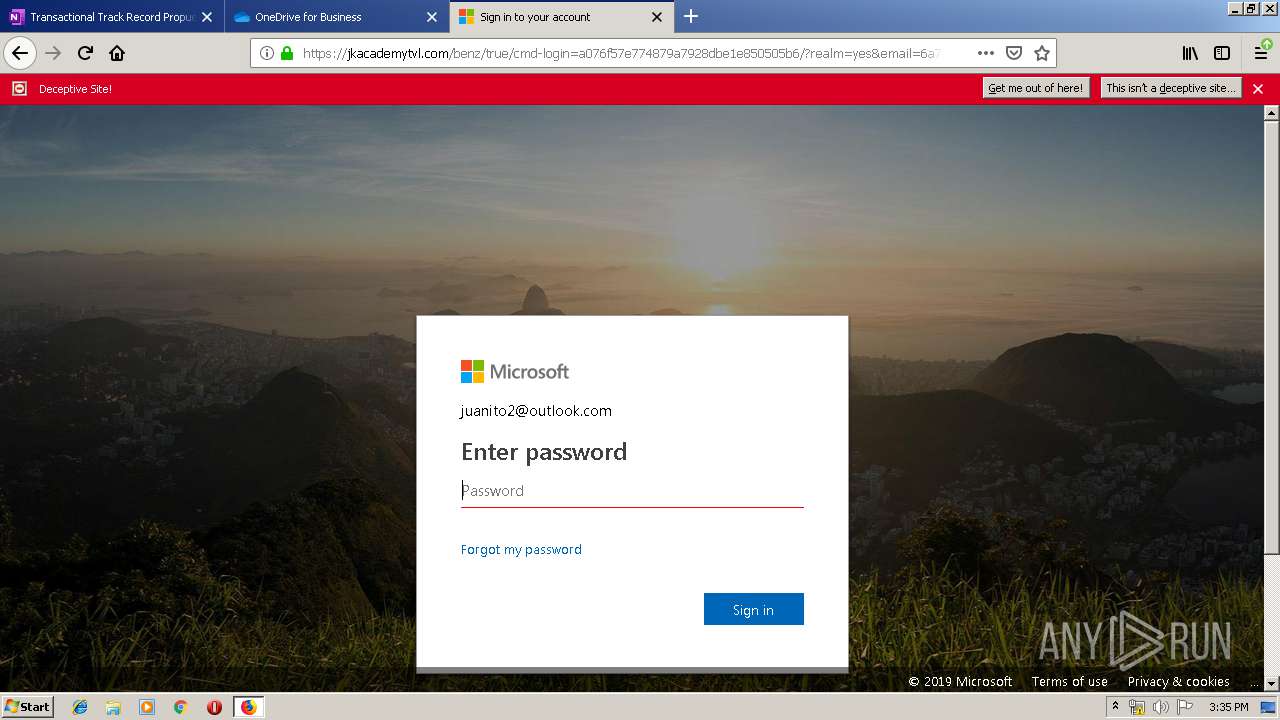
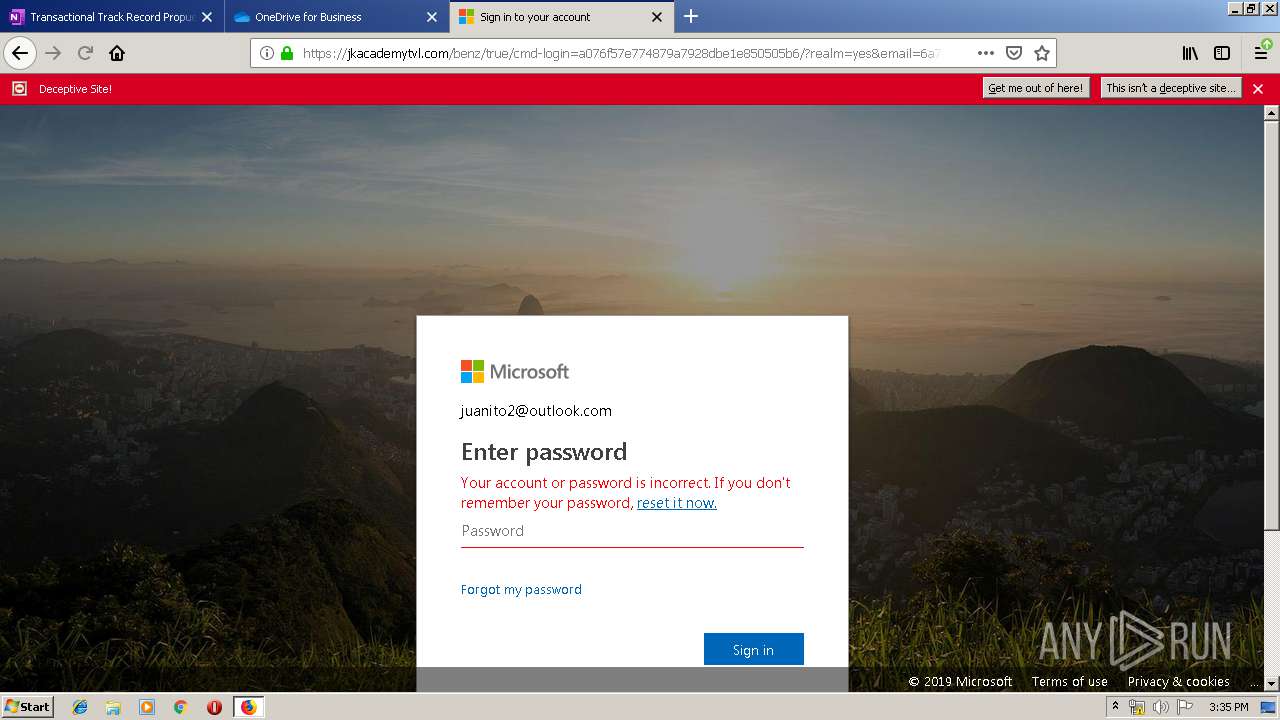
| Verdict: | Malicious activity |
| Analysis date: | June 19, 2019, 14:30:29 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 32413E0C094FE0F20EB1CD3401A307B6 |
| SHA1: | FDC876CE4DDE7C706BF37825628A52E79CA993B1 |
| SHA256: | F49F7F333F3CA0956B926BBEACE5686683766E860B9FE5B4980310AA437A3EA2 |
| SSDEEP: | 6:2iAfsX9Aw6RrtKIfE7/Pfr0WMQ3+kDHIHaFlES5JJMcF1P9iAVuGw1DjiX9J6TI8:2i9eRhfA/Pj7skDHIHakyF+AVtCDu0I8 |
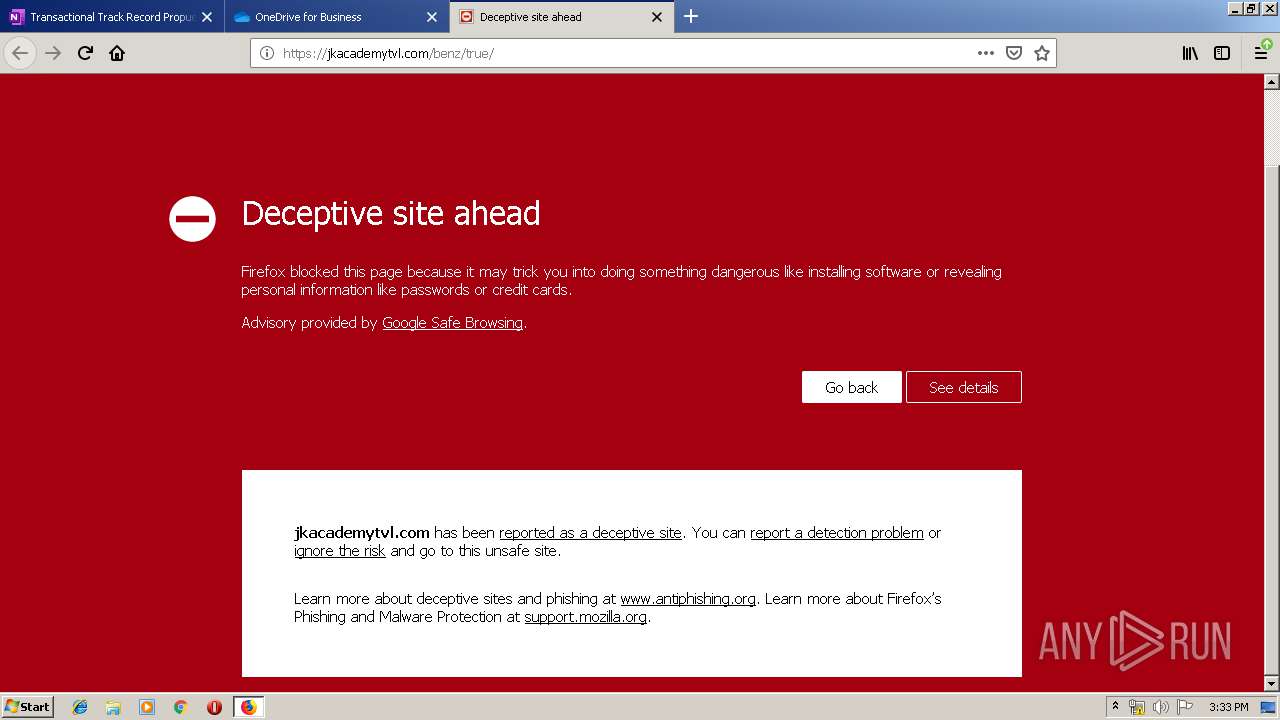
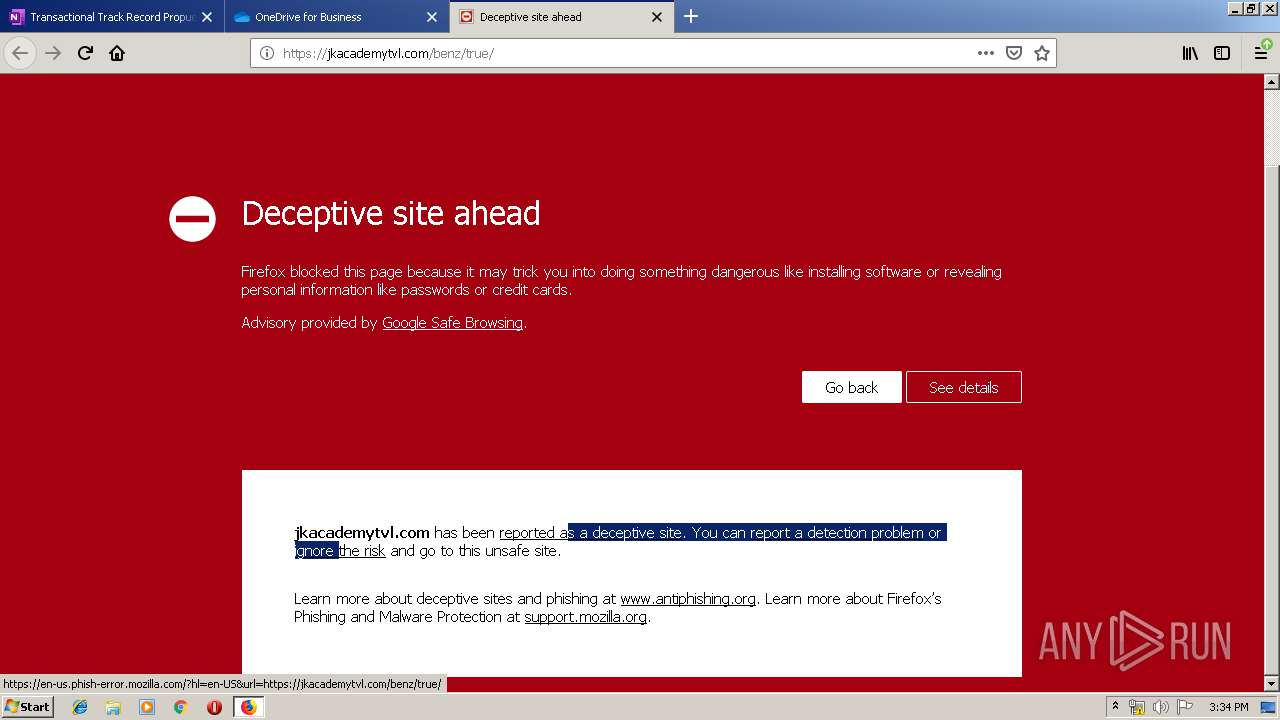
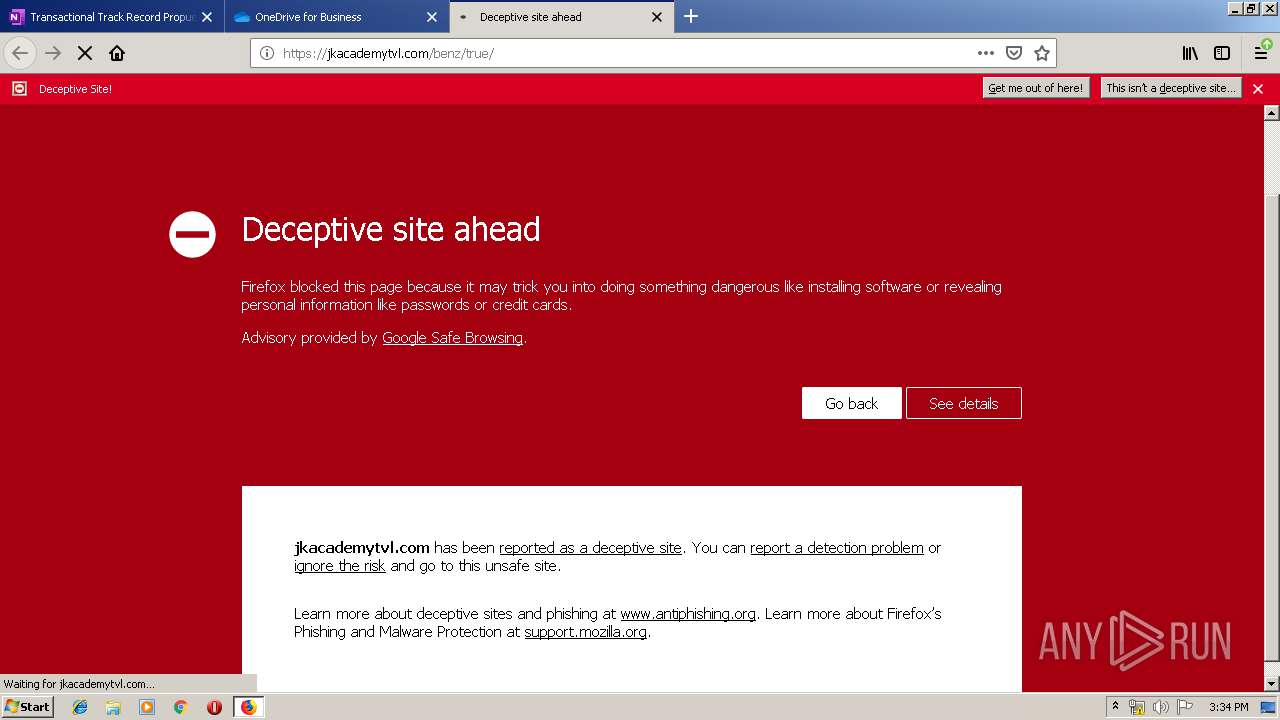
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- firefox.exe (PID: 3384)
Creates files in the program directory
- firefox.exe (PID: 3384)
INFO
Application launched itself
- firefox.exe (PID: 3384)
Reads settings of System Certificates
- firefox.exe (PID: 3384)
Reads CPU info
- firefox.exe (PID: 3384)
Dropped object may contain Bitcoin addresses
- firefox.exe (PID: 3384)
Creates files in the user directory
- firefox.exe (PID: 3384)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
37
Monitored processes
5
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1908 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="3384.20.1216337352\1910871179" -childID 3 -isForBrowser -prefsHandle 3172 -prefMapHandle 3544 -prefsLen 5824 -prefMapSize 180950 -schedulerPrefs 0001,2 -parentBuildID 20190225143501 -greomni "C:\Program Files\Mozilla Firefox\omni.ja" -appomni "C:\Program Files\Mozilla Firefox\browser\omni.ja" -appdir "C:\Program Files\Mozilla Firefox\browser" - 3384 "\\.\pipe\gecko-crash-server-pipe.3384" 3520 tab | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 65.0.2 Modules
| |||||||||||||||
| 2336 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="3384.6.707033108\429375834" -childID 1 -isForBrowser -prefsHandle 1300 -prefMapHandle 1304 -prefsLen 1 -prefMapSize 180950 -schedulerPrefs 0001,2 -parentBuildID 20190225143501 -greomni "C:\Program Files\Mozilla Firefox\omni.ja" -appomni "C:\Program Files\Mozilla Firefox\browser\omni.ja" -appdir "C:\Program Files\Mozilla Firefox\browser" - 3384 "\\.\pipe\gecko-crash-server-pipe.3384" 1692 tab | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 65.0.2 Modules
| |||||||||||||||
| 2896 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="3384.0.1524193629\1263927258" -parentBuildID 20190225143501 -greomni "C:\Program Files\Mozilla Firefox\omni.ja" -appomni "C:\Program Files\Mozilla Firefox\browser\omni.ja" -appdir "C:\Program Files\Mozilla Firefox\browser" - "C:\Users\admin\AppData\LocalLow\Mozilla\Temp-{ce348e4c-7d33-445e-89f9-60108c51bcaf}" 3384 "\\.\pipe\gecko-crash-server-pipe.3384" 1152 gpu | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 65.0.2 Modules
| |||||||||||||||
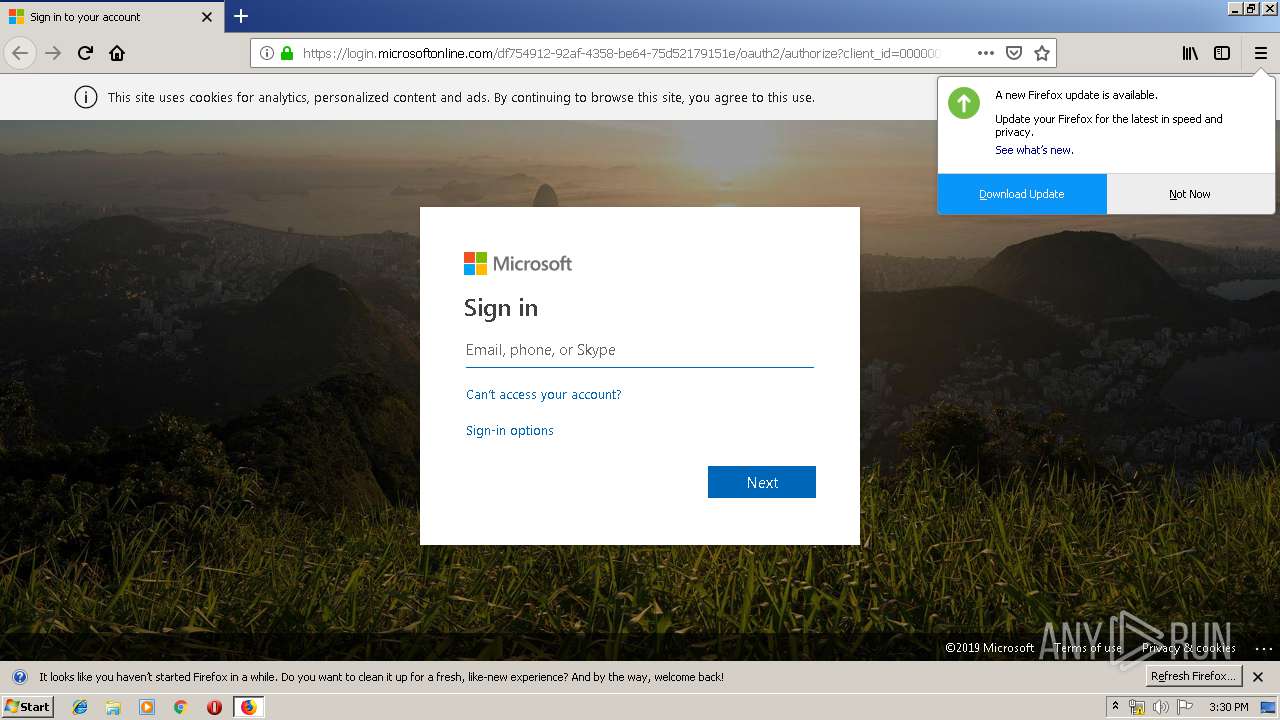
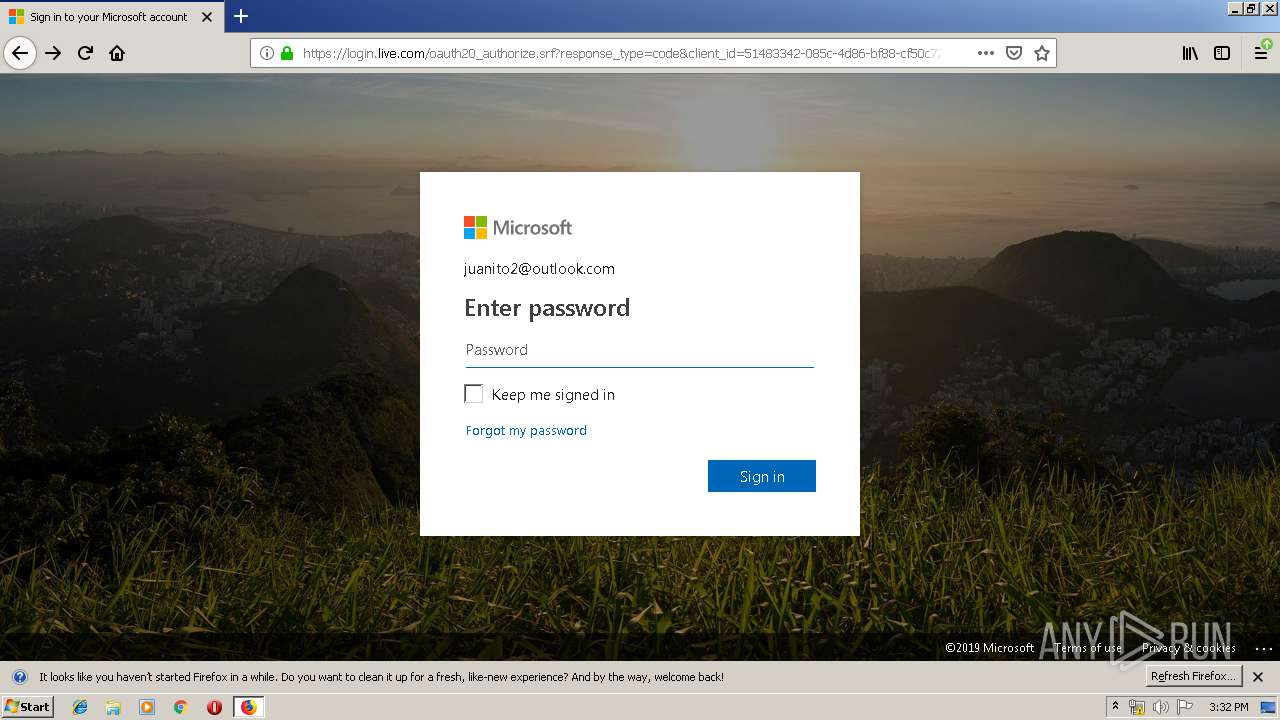
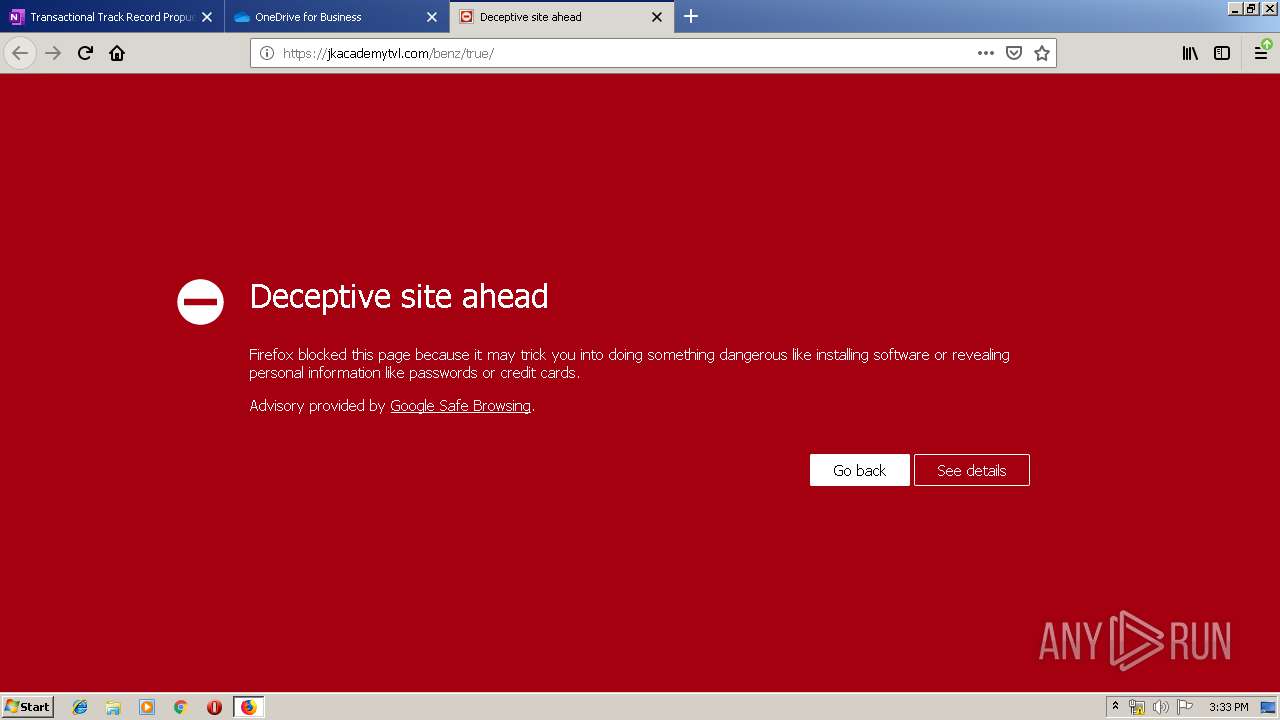
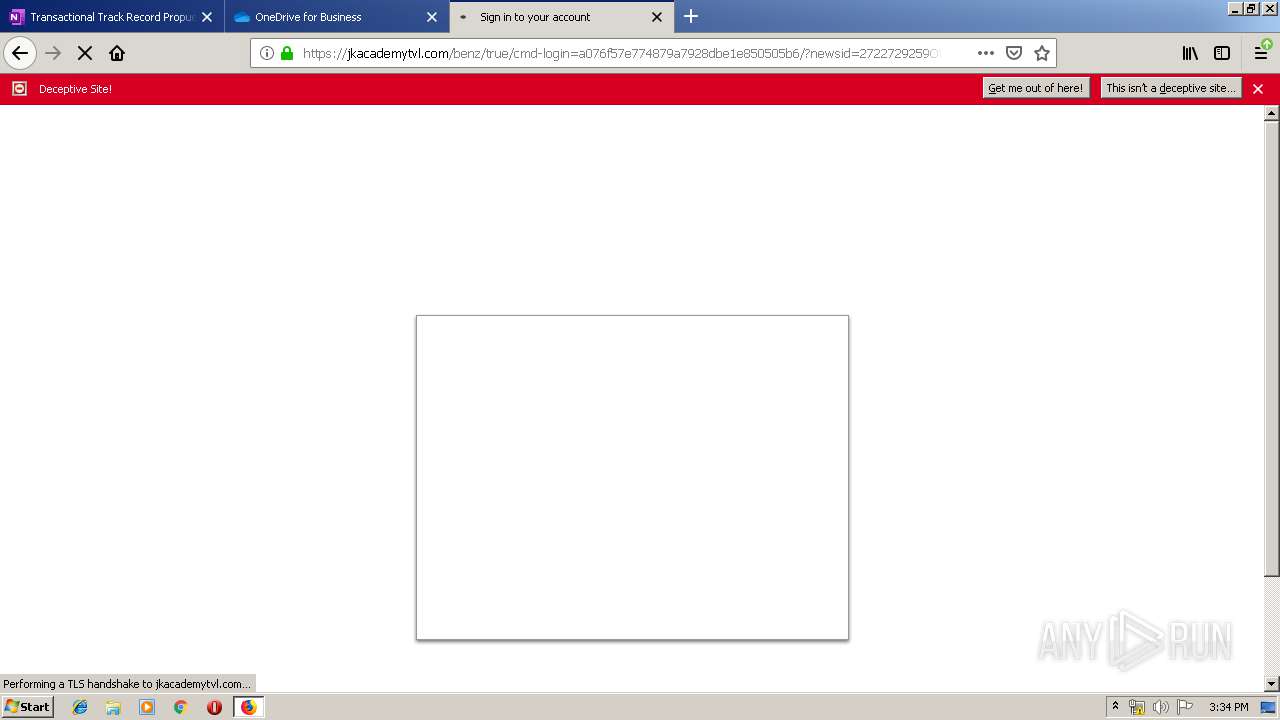
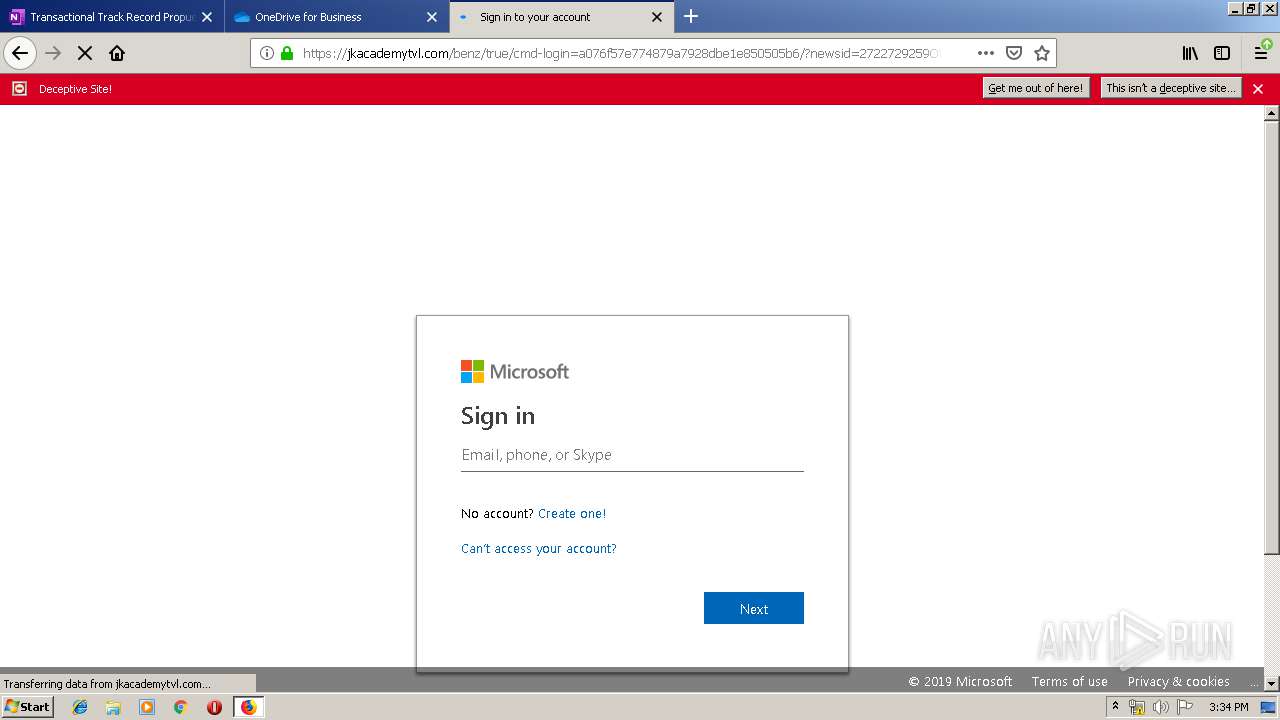
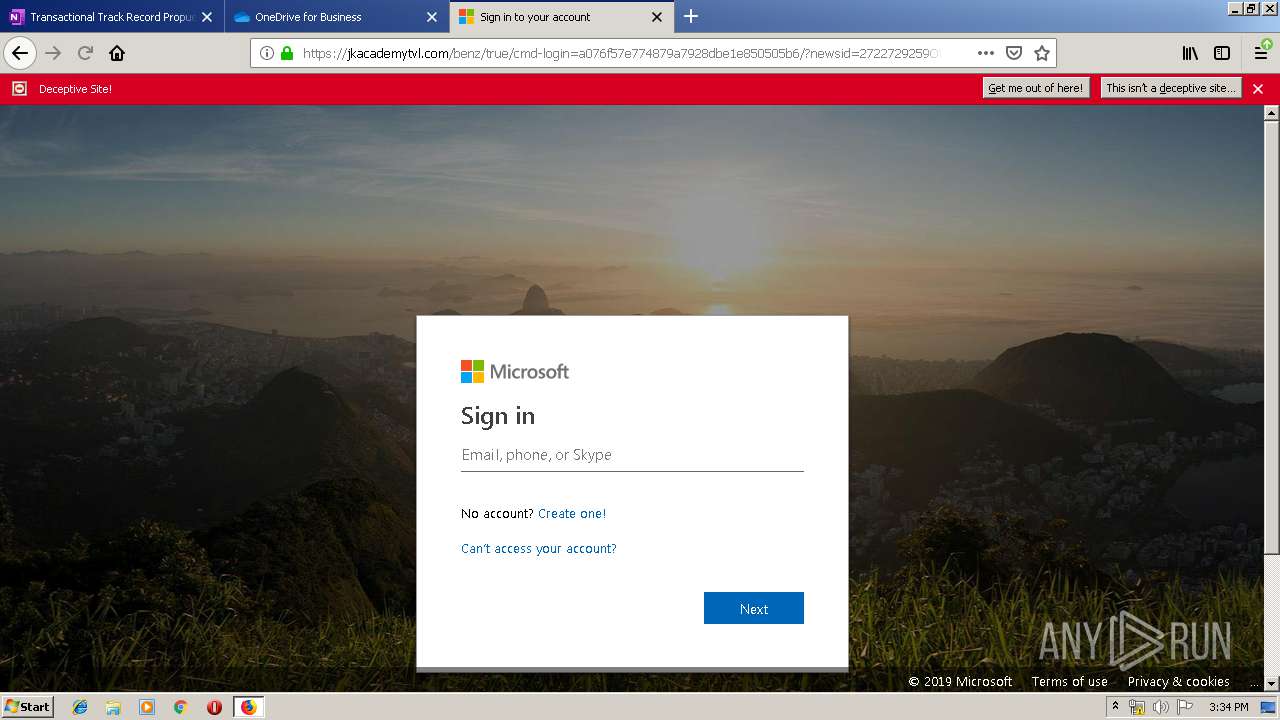
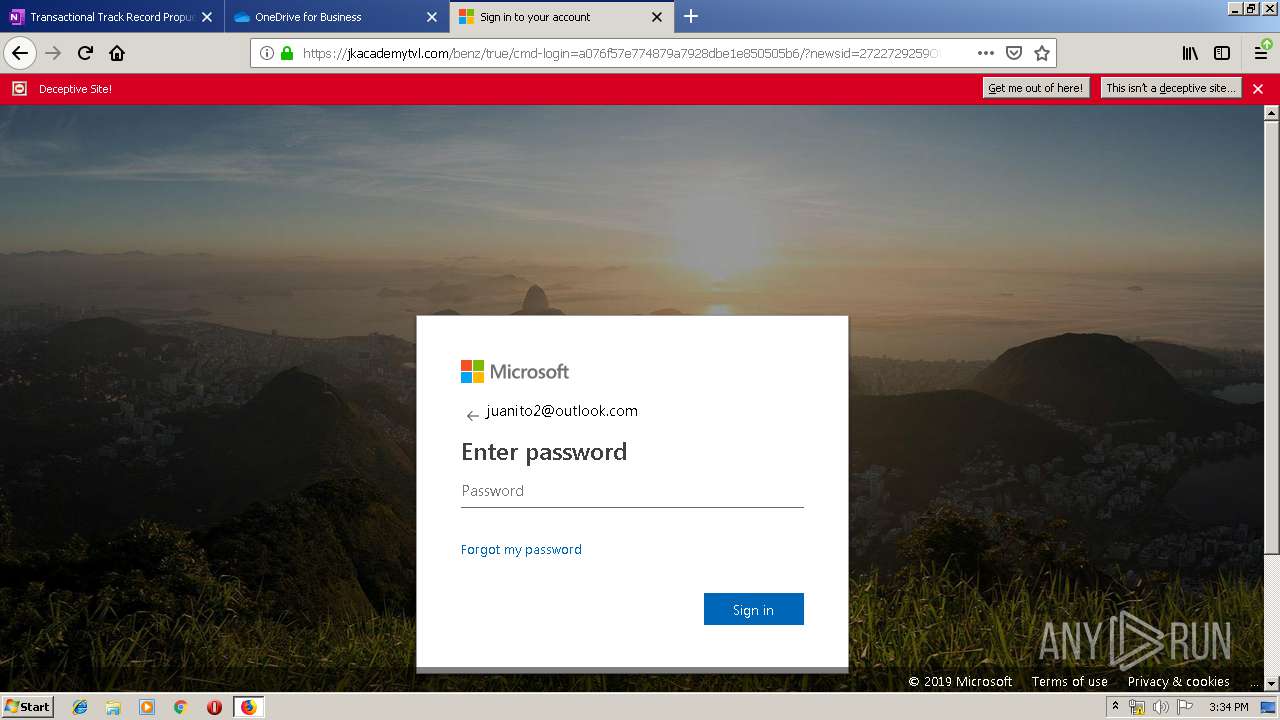
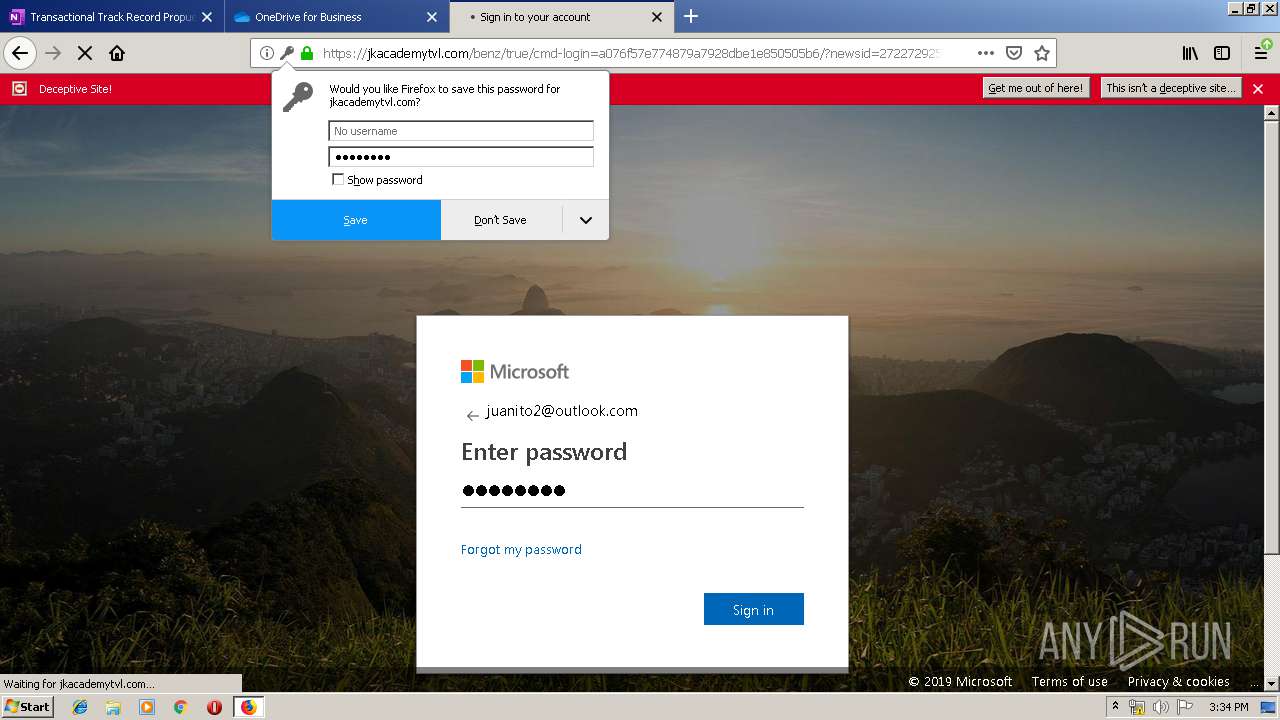
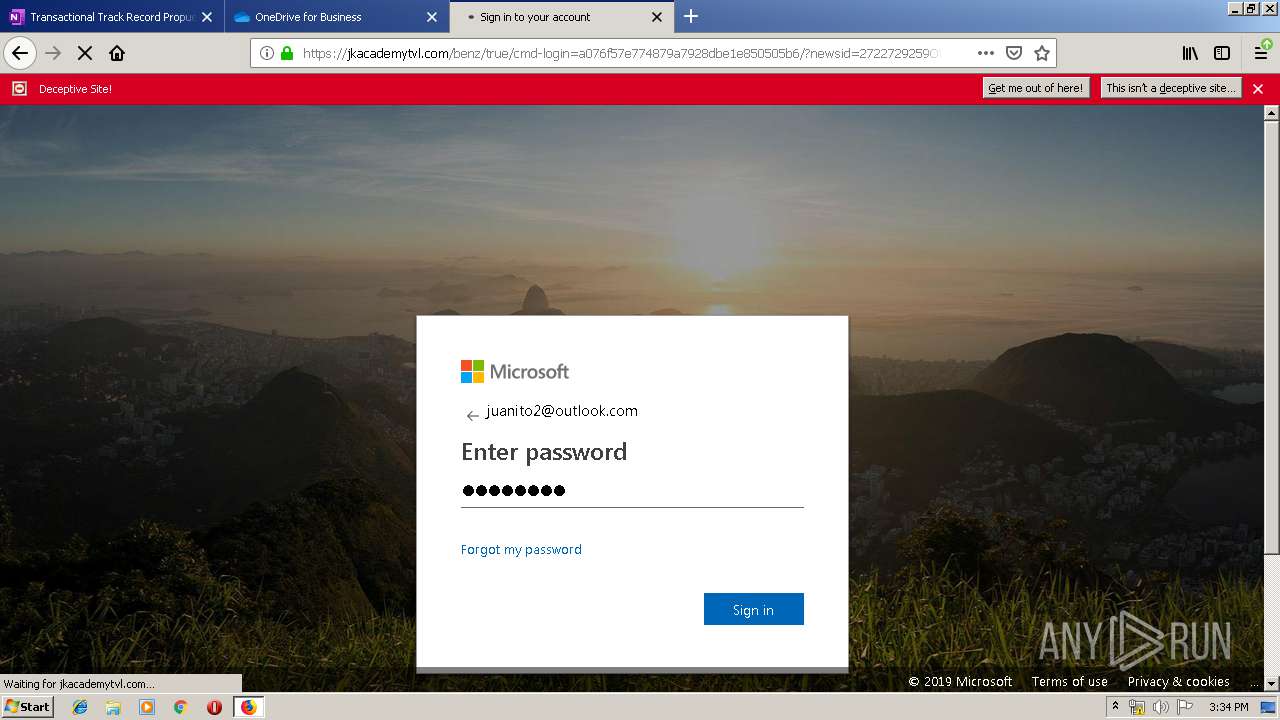
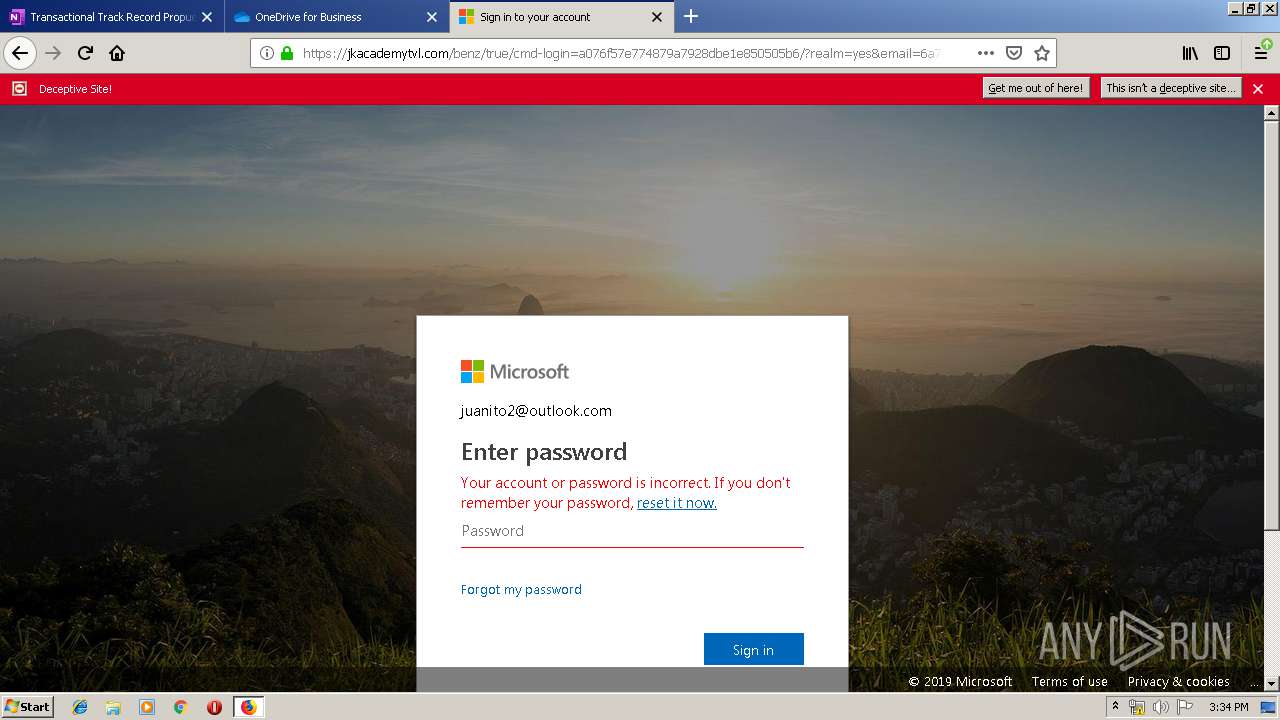
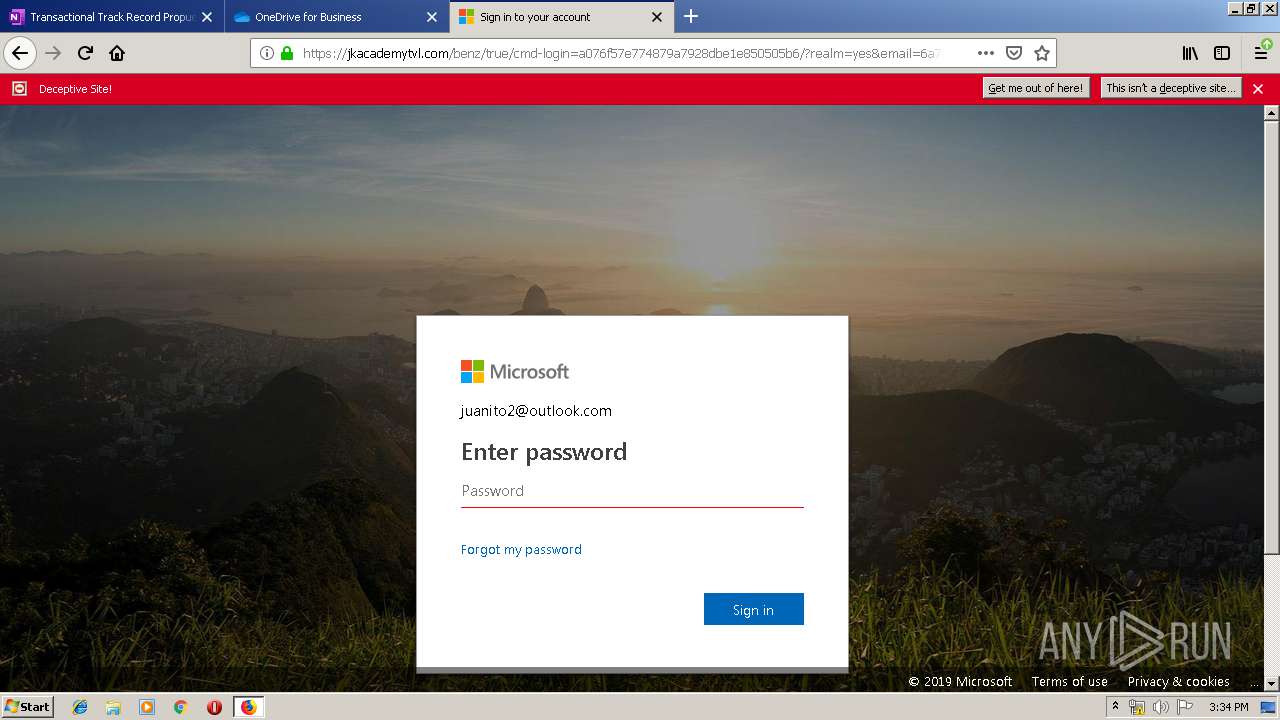
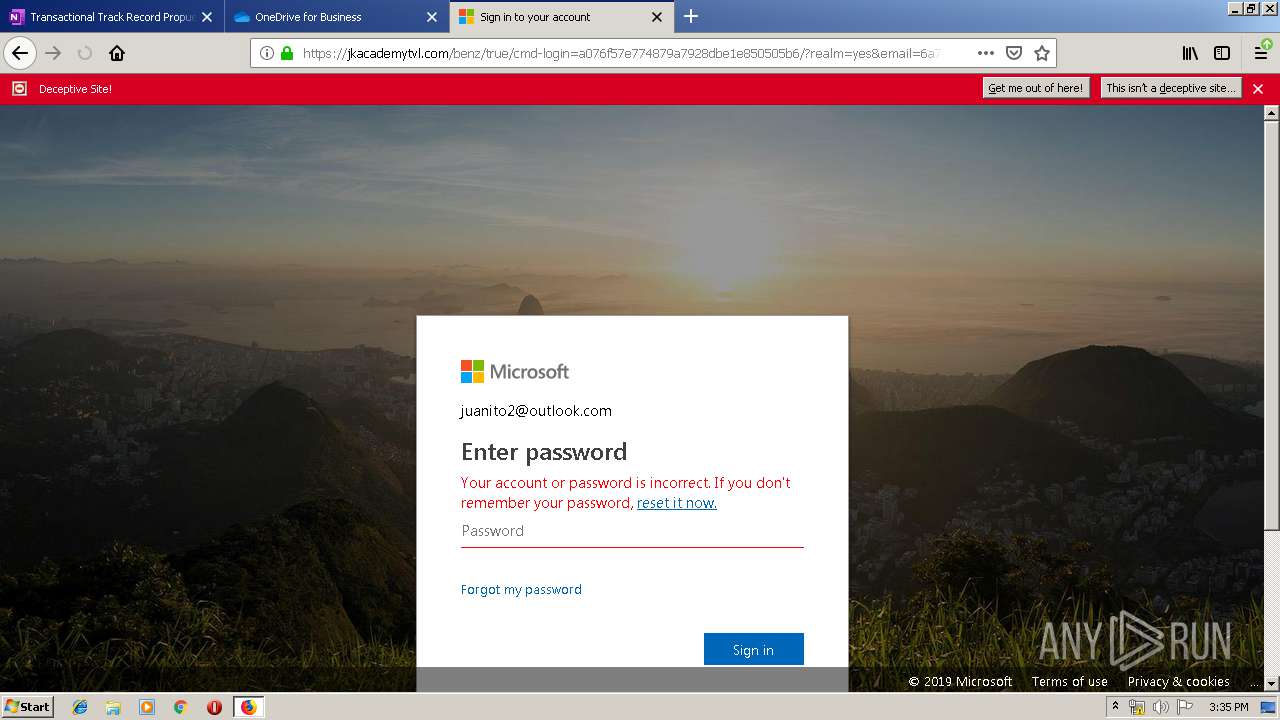
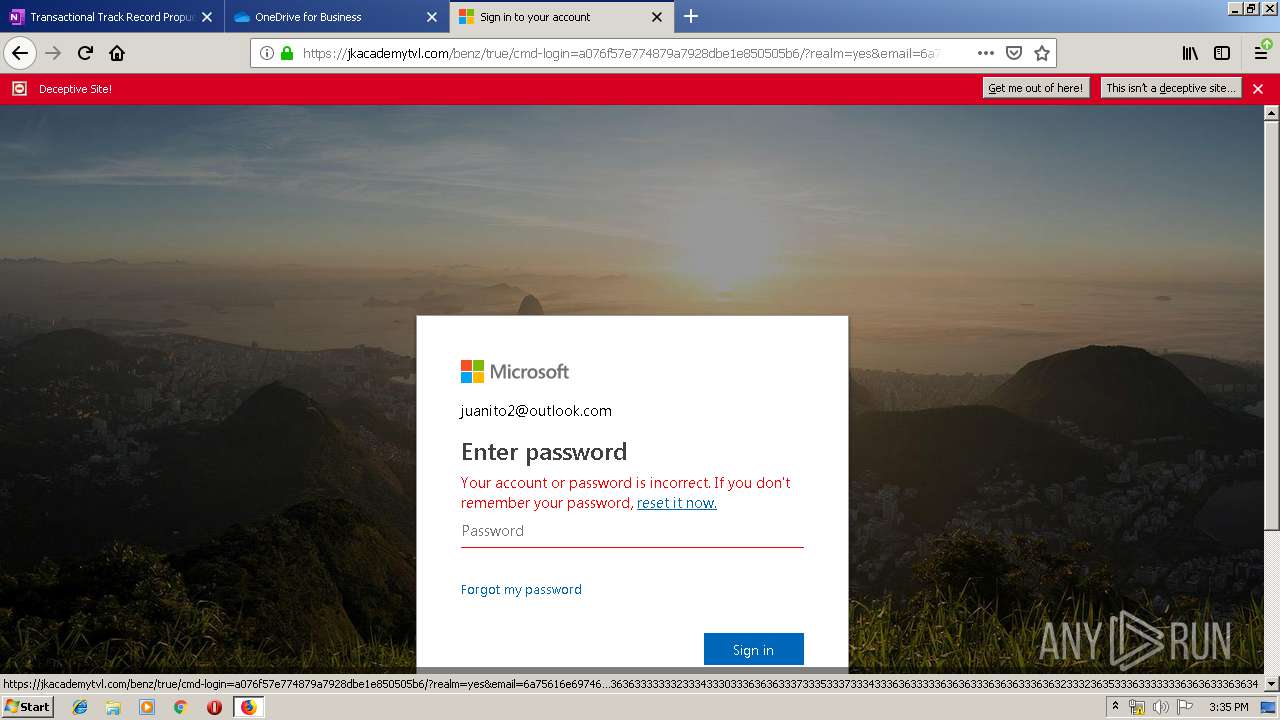
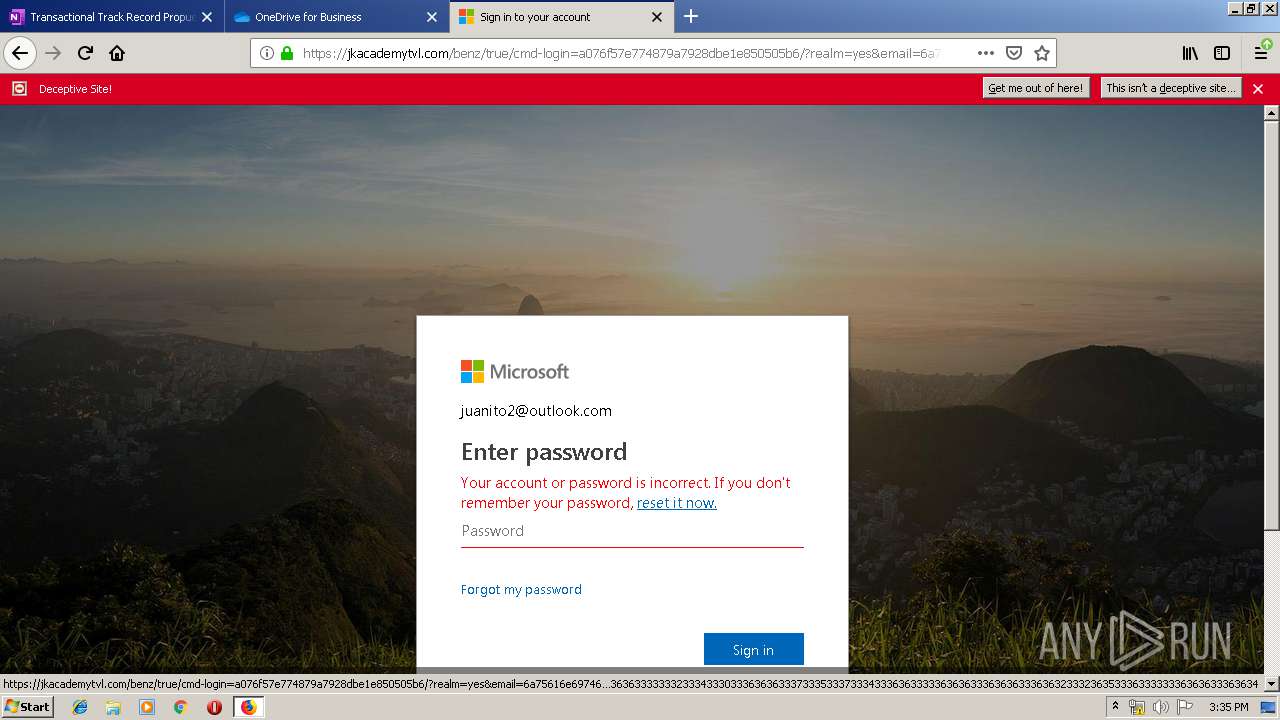
| 3384 | "C:\Program Files\Mozilla Firefox\firefox.exe" https://zuvi-my.sharepoint.com/personal/venancio_castanon_ttrecord_com/_layouts/15/WopiFrame.aspx?sourcedoc={7d73afc1-6326-4bda-8bd3-a9bc3a8cc5b8}&action=view&wd=target%28Transactional%20Track%20Record%20Propuesta.one%7C48ae4680-daa1-4ae2-b322-fdc4107448de%2FTTR%20Propuesta%7C258e353a-b8e5-470d-bf6e-10032cf4bf67%2F%29 | C:\Program Files\Mozilla Firefox\firefox.exe | explorer.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 65.0.2 Modules
| |||||||||||||||
| 3448 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="3384.13.780259903\1623590513" -childID 2 -isForBrowser -prefsHandle 2656 -prefMapHandle 2660 -prefsLen 216 -prefMapSize 180950 -schedulerPrefs 0001,2 -parentBuildID 20190225143501 -greomni "C:\Program Files\Mozilla Firefox\omni.ja" -appomni "C:\Program Files\Mozilla Firefox\browser\omni.ja" -appdir "C:\Program Files\Mozilla Firefox\browser" - 3384 "\\.\pipe\gecko-crash-server-pipe.3384" 2672 tab | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 65.0.2 Modules
| |||||||||||||||
Total events
1 546
Read events
1 534
Write events
12
Delete events
0
Modification events
| (PID) Process: | (3384) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3384) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000071000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3384) firefox.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
1
Suspicious files
272
Text files
103
Unknown types
125
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3384 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 3384 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\cookies.sqlite-shm | — | |
MD5:— | SHA256:— | |||
| 3384 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\cache2\trash18674 | — | |
MD5:— | SHA256:— | |||
| 3384 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\prefs-1.js | — | |
MD5:— | SHA256:— | |||
| 3384 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\sessionCheckpoints.json | — | |
MD5:— | SHA256:— | |||
| 3384 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\sessionCheckpoints.json.tmp | — | |
MD5:— | SHA256:— | |||
| 3384 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\1657114595AmcateirvtiSty.sqlite-shm | — | |
MD5:— | SHA256:— | |||
| 3384 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\startupCache\scriptCache-child-current.bin | binary | |
MD5:— | SHA256:— | |||
| 3384 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\startupCache\urlCache-current.bin | binary | |
MD5:— | SHA256:— | |||
| 3384 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\cert9.db | sqlite | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
18
TCP/UDP connections
108
DNS requests
214
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3384 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
3384 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
3384 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
3384 | firefox.exe | POST | 200 | 104.18.24.243:80 | http://ocsp.msocsp.com/ | US | der | 1.79 Kb | whitelisted |
3384 | firefox.exe | POST | 200 | 104.18.24.243:80 | http://ocsp.msocsp.com/ | US | der | 1.79 Kb | whitelisted |
3384 | firefox.exe | POST | 200 | 104.18.24.243:80 | http://ocsp.msocsp.com/ | US | der | 1.79 Kb | whitelisted |
3384 | firefox.exe | POST | 200 | 216.58.207.35:80 | http://ocsp.pki.goog/GTSGIAG3 | US | der | 471 b | whitelisted |
3384 | firefox.exe | POST | 200 | 104.18.24.243:80 | http://ocsp.msocsp.com/ | US | der | 1.79 Kb | whitelisted |
3384 | firefox.exe | POST | 200 | 216.58.207.35:80 | http://ocsp.pki.goog/GTSGIAG3 | US | der | 471 b | whitelisted |
3384 | firefox.exe | POST | 200 | 216.58.210.3:80 | http://ocsp.pki.goog/GTSGIAG3 | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3384 | firefox.exe | 35.244.181.201:443 | aus5.mozilla.org | — | US | suspicious |
3384 | firefox.exe | 2.16.186.112:80 | detectportal.firefox.com | Akamai International B.V. | — | whitelisted |
3384 | firefox.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3384 | firefox.exe | 104.18.24.243:80 | ocsp.msocsp.com | Cloudflare Inc | US | shared |
3384 | firefox.exe | 172.217.23.170:443 | safebrowsing.googleapis.com | Google Inc. | US | whitelisted |
3384 | firefox.exe | 40.126.9.66:443 | login.windows.net | Microsoft Corporation | US | unknown |
3384 | firefox.exe | 216.58.210.3:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
3384 | firefox.exe | 34.213.89.114:443 | tiles.services.mozilla.com | Amazon.com, Inc. | US | unknown |
3384 | firefox.exe | 52.32.141.83:443 | shavar.services.mozilla.com | Amazon.com, Inc. | US | unknown |
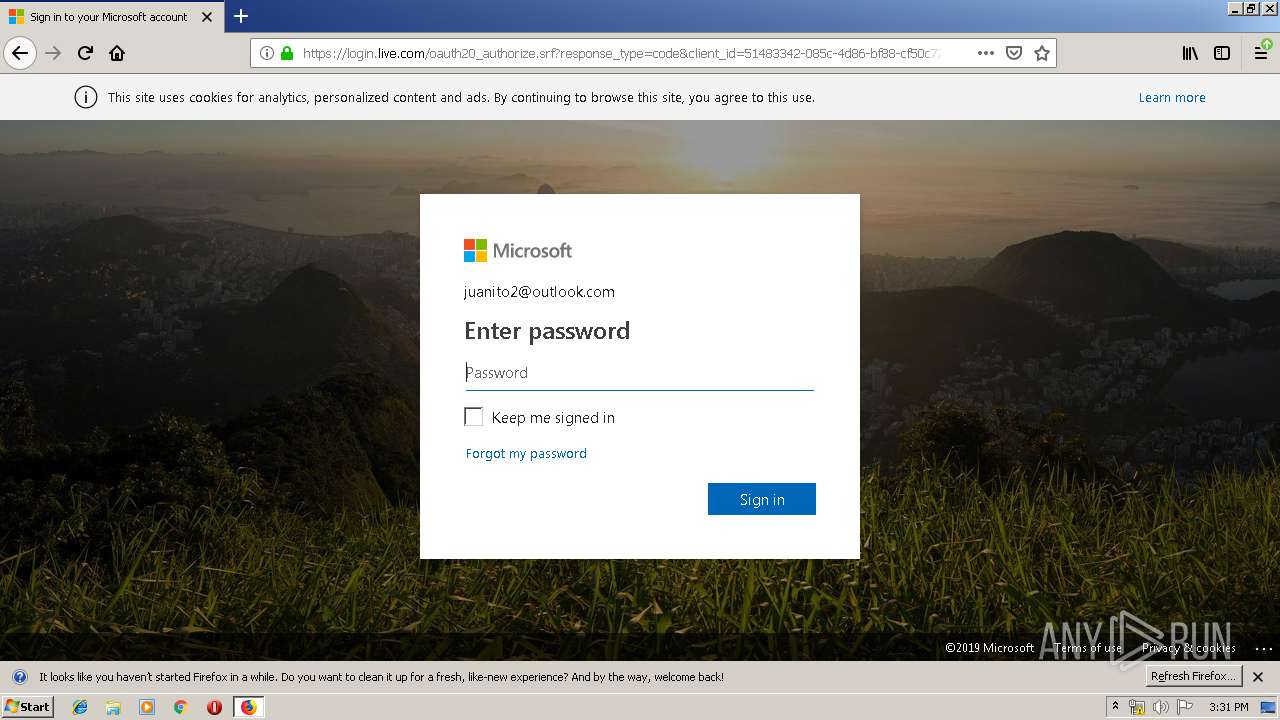
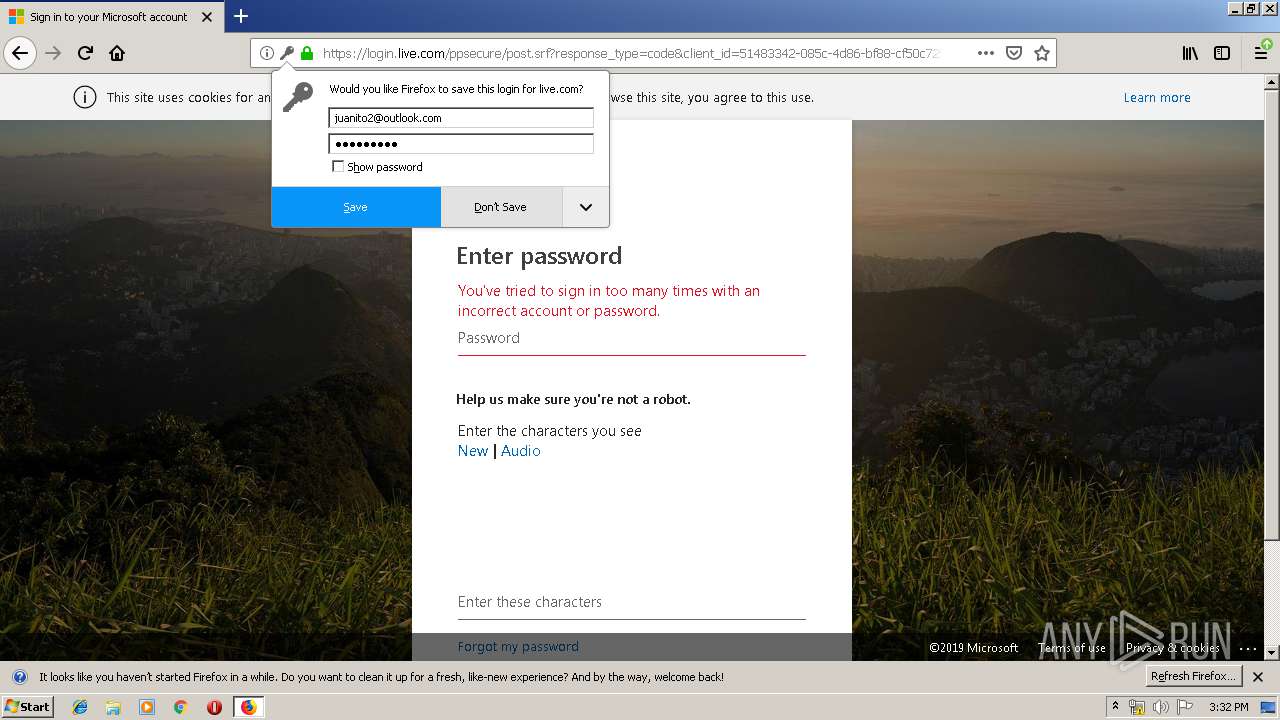
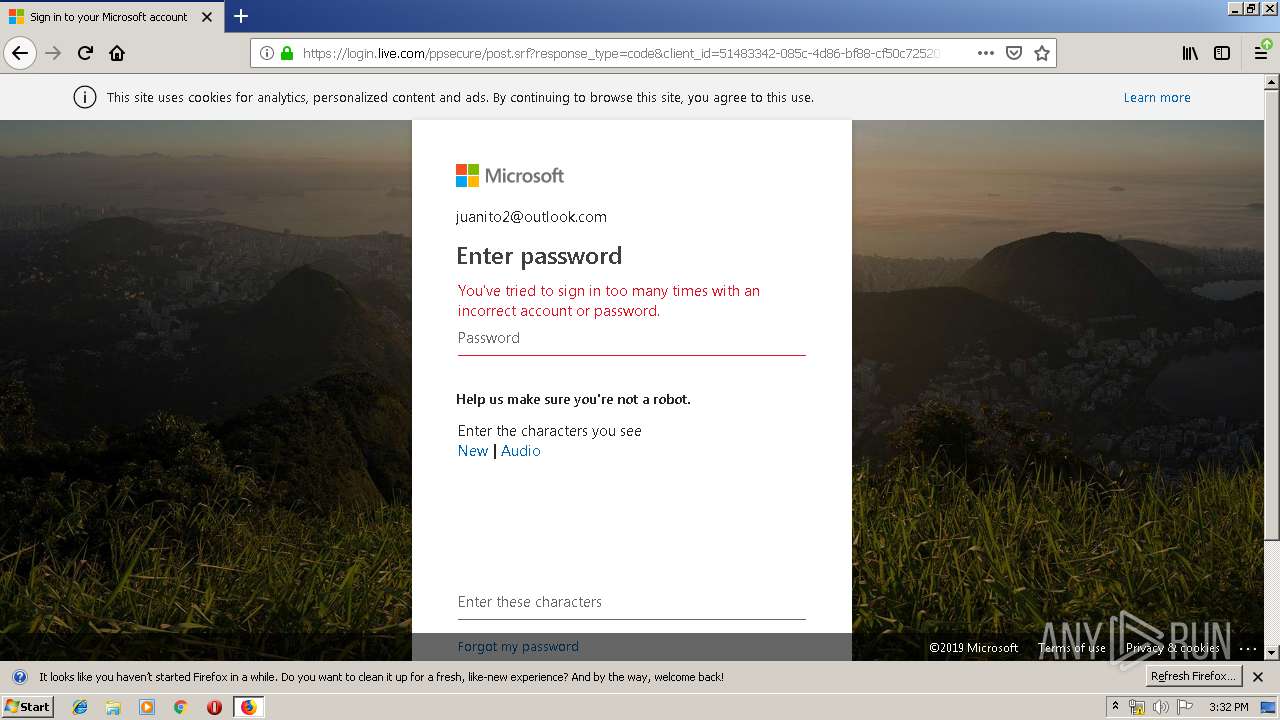
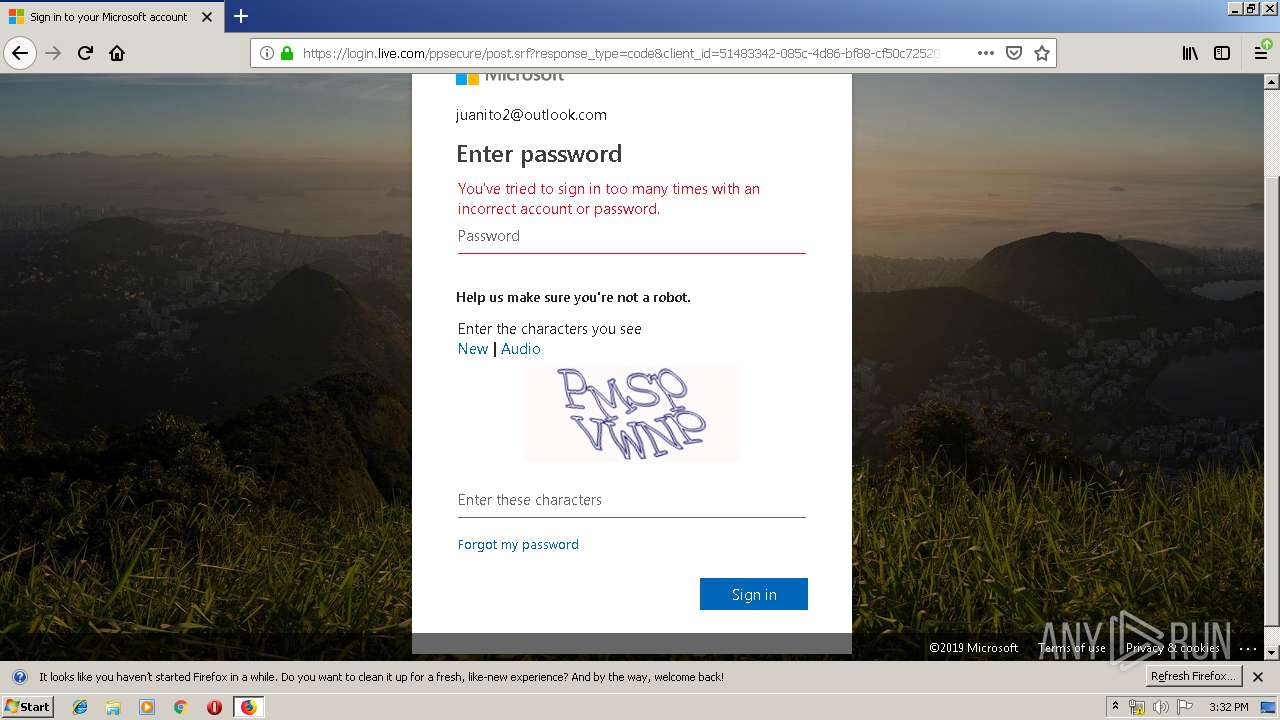
3384 | firefox.exe | 65.55.163.90:443 | login.live.com | Microsoft Corporation | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
zuvi-my.sharepoint.com |
| suspicious |
detectportal.firefox.com |
| whitelisted |
aus5.mozilla.org |
| whitelisted |
balrog-aus5.r53-2.services.mozilla.com |
| whitelisted |
a1089.dscd.akamai.net |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
search.services.mozilla.com |
| whitelisted |
cs9.wac.phicdn.net |
| whitelisted |
search.r53-2.services.mozilla.com |
| whitelisted |
prodnet10539-10532selectora0000.sharepointonline.com.akadns.net |
| unknown |