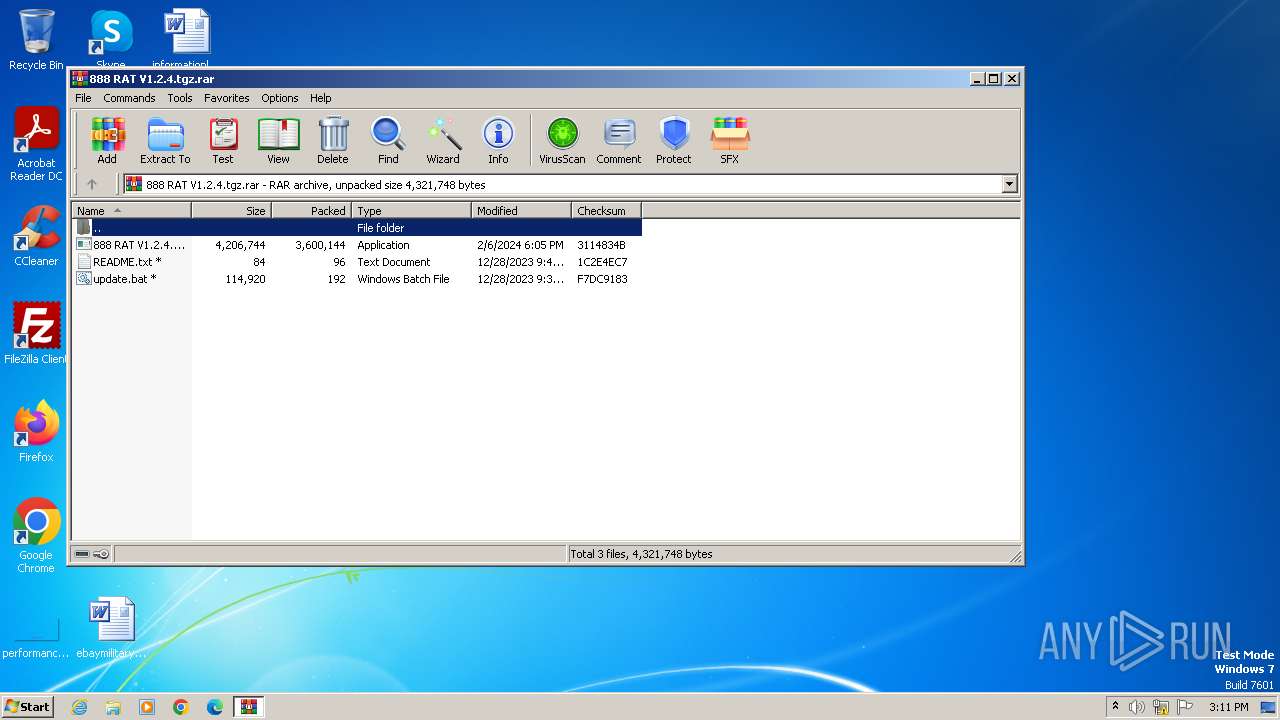
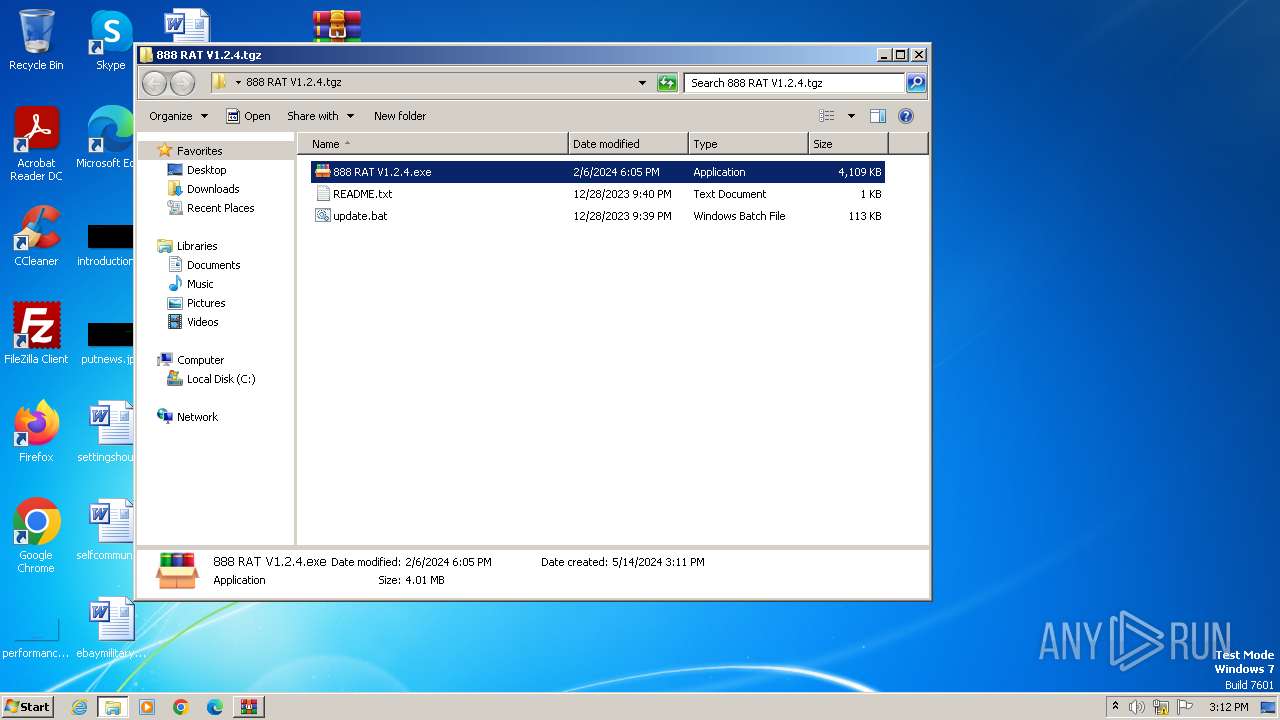
| File name: | 888 RAT V1.2.4.tgz |
| Full analysis: | https://app.any.run/tasks/db1e37dc-0a3f-44c6-86f0-1c6de06f61a6 |
| Verdict: | Malicious activity |
| Threats: | DCrat, also known as Dark Crystal RAT, is a remote access trojan (RAT), which was first introduced in 2018. It is a modular malware that can be customized to perform different tasks. For instance, it can steal passwords, crypto wallet information, hijack Telegram and Steam accounts, and more. Attackers may use a variety of methods to distribute DCrat, but phishing email campaigns are the most common. |
| Analysis date: | May 14, 2024, 14:10:53 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 516DAB882A60942F29D3D2679A6D1F2F |
| SHA1: | 53532F5F3BDD38972458FBCF82A001D5AB1A6335 |
| SHA256: | F4953BD1ABEDF170D163BFE181B8CB6D15A593EB32DF8A0FAC76DFD706A668BC |
| SSDEEP: | 98304:iaHXcjvAvu9+UVcV5CG9sPEZ9ByEAO3gx5i8EmR0zTwDQHwbSfRTny7FQZ/zqx/1:iWbtXY |
MALICIOUS
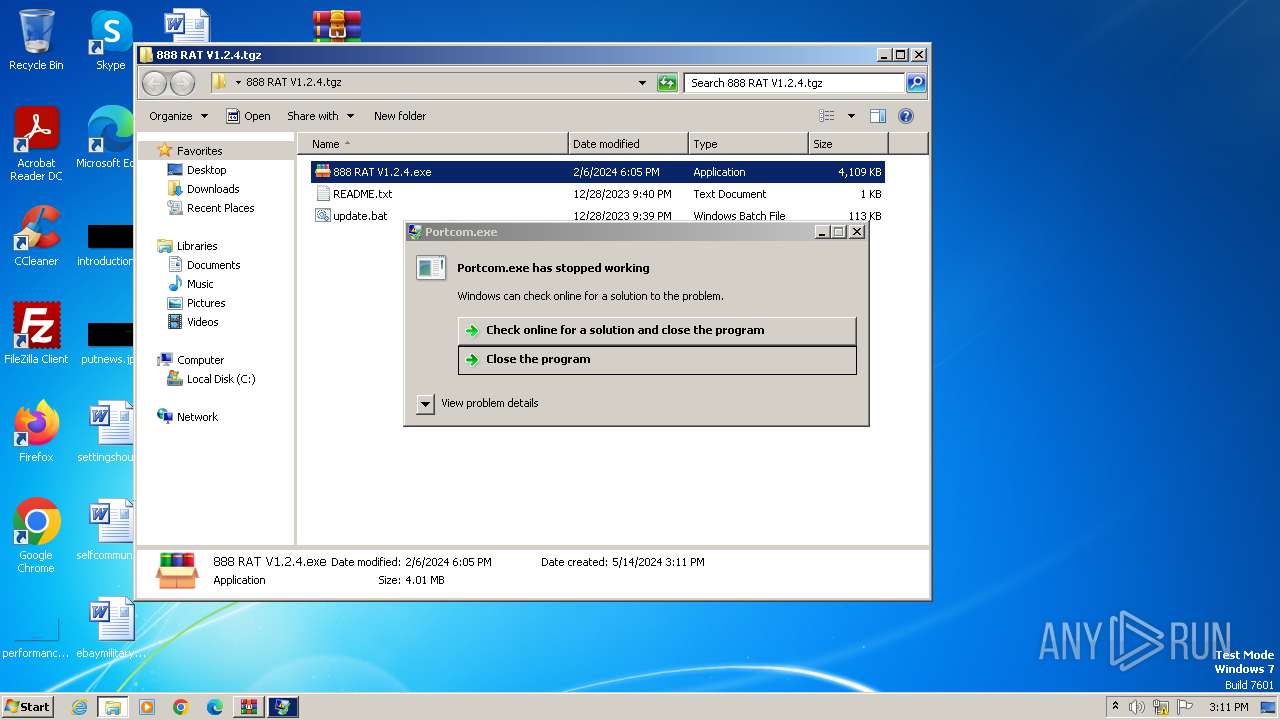
Drops the executable file immediately after the start
- 888 RAT V1.2.4.exe (PID: 2024)
- Portcom.exe (PID: 728)
Uses sleep, probably for evasion detection (SCRIPT)
- wscript.exe (PID: 1680)
DcRAT is detected
- Portcom.exe (PID: 728)
SUSPICIOUS
Reads security settings of Internet Explorer
- 888 RAT V1.2.4.exe (PID: 2024)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 1680)
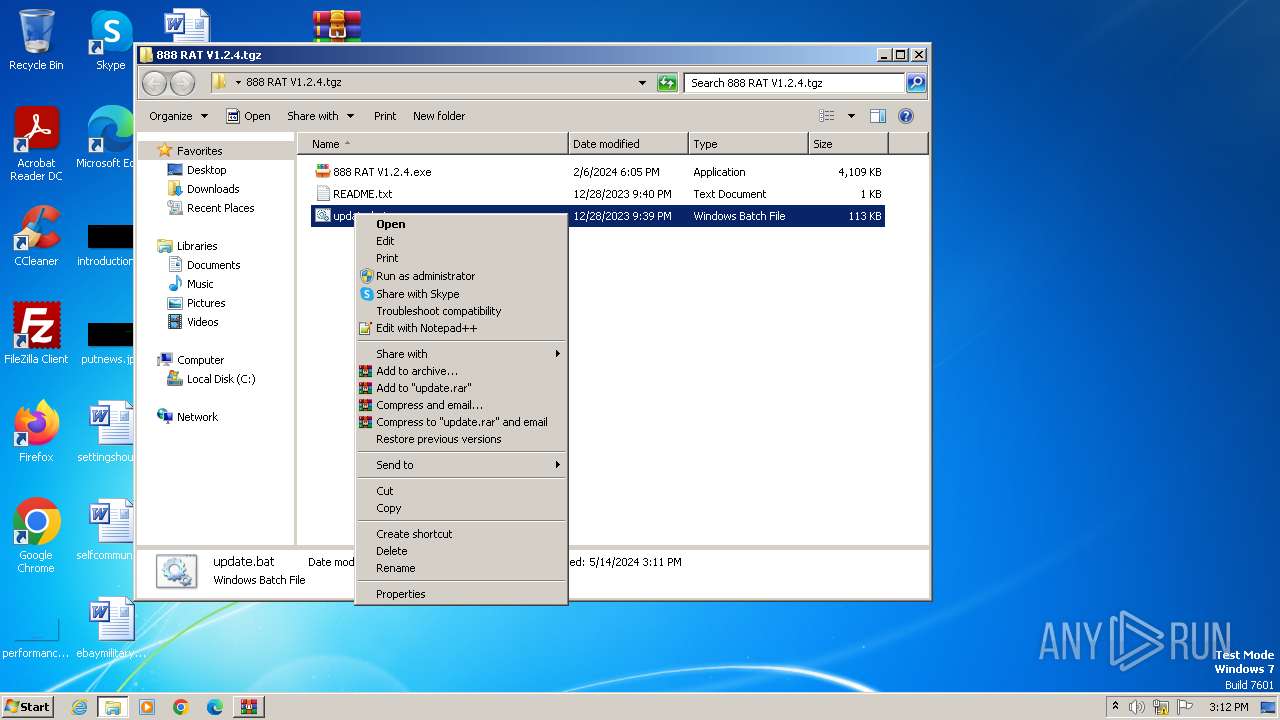
Executing commands from a ".bat" file
- wscript.exe (PID: 1680)
Runs shell command (SCRIPT)
- wscript.exe (PID: 1680)
Executable content was dropped or overwritten
- Portcom.exe (PID: 728)
- 888 RAT V1.2.4.exe (PID: 2024)
Reads the Internet Settings
- wscript.exe (PID: 1680)
- 888 RAT V1.2.4.exe (PID: 2024)
INFO
Drops the executable file immediately after the start
- WinRAR.exe (PID: 4076)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4076)
Manual execution by a user
- WinRAR.exe (PID: 4076)
- 888 RAT V1.2.4.exe (PID: 2024)
- cmd.exe (PID: 1928)
Reads the computer name
- 888 RAT V1.2.4.exe (PID: 2024)
- Portcom.exe (PID: 728)
Checks supported languages
- 888 RAT V1.2.4.exe (PID: 2024)
- Portcom.exe (PID: 728)
Reads the machine GUID from the registry
- Portcom.exe (PID: 728)
Reads Environment values
- Portcom.exe (PID: 728)
Reads product name
- Portcom.exe (PID: 728)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
48
Monitored processes
7
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 728 | "C:\netsvc/Portcom.exe" | C:\netsvc\Portcom.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225477 Version: 1.2.7.1277 Modules
| |||||||||||||||
| 1580 | C:\Windows\system32\cmd.exe /c ""C:\netsvc\A9uOgbPrn6knFTM7.bat" " | C:\Windows\System32\cmd.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 3221225477 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1680 | "C:\Windows\System32\WScript.exe" "C:\netsvc\yQ611EYDnSsii3grttjyEe5A.vbe" | C:\Windows\System32\wscript.exe | — | 888 RAT V1.2.4.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 1928 | "C:\Windows\System32\cmd.exe" /C "C:\Users\admin\Desktop\888 RAT V1.2.4.tgz\update.bat" | C:\Windows\System32\cmd.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2024 | "C:\Users\admin\Desktop\888 RAT V1.2.4.tgz\888 RAT V1.2.4.exe" | C:\Users\admin\Desktop\888 RAT V1.2.4.tgz\888 RAT V1.2.4.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3964 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\888 RAT V1.2.4.tgz.rar" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 4076 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\888 RAT V1.2.4.tgz.rar" "?\" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
7 679
Read events
7 617
Write events
62
Delete events
0
Modification events
| (PID) Process: | (3964) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3964) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3964) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3964) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3964) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3964) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3964) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\888 RAT V1.2.4.tgz.rar | |||
| (PID) Process: | (3964) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3964) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3964) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
3
Suspicious files
1
Text files
3
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 728 | Portcom.exe | C:\Users\admin\Desktop\DxzOmorB.log | — | |
MD5:— | SHA256:— | |||
| 4076 | WinRAR.exe | C:\Users\admin\Desktop\888 RAT V1.2.4.tgz\888 RAT V1.2.4.exe | executable | |
MD5:3E435CD35029624F9EAB749A5F34DF75 | SHA256:AFBFD2222E3972AB0B7D29D94B3CD0E6D5603920D5AB8C7C307A32230C8BA02E | |||
| 2024 | 888 RAT V1.2.4.exe | C:\netsvc\Portcom.exe | executable | |
MD5:C36CAE02A54AB29419091C48F326484E | SHA256:65D322E933B69E5202F23F0AAEE38873C7069224B7438C50006437976EBC306F | |||
| 4076 | WinRAR.exe | C:\Users\admin\Desktop\888 RAT V1.2.4.tgz\update.bat | text | |
MD5:75566BDA98088EB3DE6FF4EA480D7A6F | SHA256:A8D562BFD47C712B8B55EF9AD110E3587E30E3B63245E0A4796436F036EBF07F | |||
| 2024 | 888 RAT V1.2.4.exe | C:\netsvc\A9uOgbPrn6knFTM7.bat | text | |
MD5:302BBF3C84BEE7FE6740C5CA70219DF8 | SHA256:FE698371850D8DDA8B88D2A1498633E738A318D3E7F0E9B3ECEC17E90D5987A1 | |||
| 2024 | 888 RAT V1.2.4.exe | C:\netsvc\yQ611EYDnSsii3grttjyEe5A.vbe | vbe | |
MD5:35930F49781D4E06097AEEB64DFC31F2 | SHA256:FE9EC2FB23BAD2E971705CDEB9047A90C6B87C2B06743DFC1BA91EF919A08EB0 | |||
| 728 | Portcom.exe | C:\Users\admin\Desktop\BvNfQEnG.log | executable | |
MD5:16B480082780CC1D8C23FB05468F64E7 | SHA256:7A080D8BD178EC02C7F39F7F941479074C450C4FDD8E963C993D2FB5537C7708 | |||
| 4076 | WinRAR.exe | C:\Users\admin\Desktop\888 RAT V1.2.4.tgz\README.txt | text | |
MD5:A6ABC6CD1E2D04AF2351292CB8659BB8 | SHA256:3497A4ED47001D8CF4C64492AB8E72D66F2EB3DA2A235658C740629D845BB7C4 | |||
| 3964 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\888 RAT V1.2.4.tgz_rar.rar | compressed | |
MD5:1158722A332CF1E37DB2721C8321983B | SHA256:258F8C4330FC1BE193D0C36F9EC0B955B55436F4B9FE2F22C7910EA43AB0CF44 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
2
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
1660 | WerFault.exe | 104.208.16.93:443 | watson.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
watson.microsoft.com |
| whitelisted |