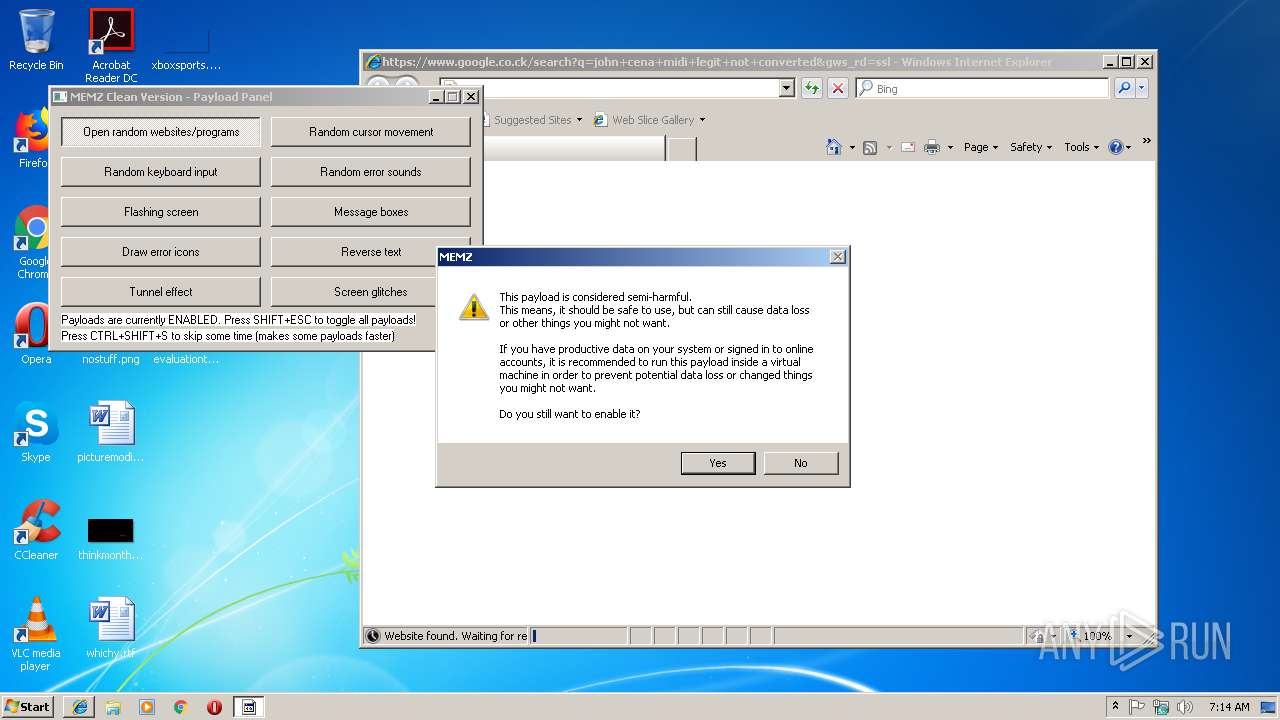
| File name: | MEMZ.bat |
| Full analysis: | https://app.any.run/tasks/d3734072-b990-4b99-ac42-f5615ea3409a |
| Verdict: | No threats detected |
| Analysis date: | January 15, 2019, 07:12:54 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/x-msdos-batch |
| File info: | DOS batch file, ASCII text, with CRLF line terminators |
| MD5: | D3AFC2D43861E88C19779C55C096FFB7 |
| SHA1: | DEC605FCF7E76E491392B15E303D38D2473C2EF2 |
| SHA256: | F4815BC9DDC736062D2E8A789E8B3F908AAAA5CA208B53F7E9B5745E7F1631B5 |
| SSDEEP: | 192:8AHhEURIWeh/p+dV7JUaC0tgo2+2Iri50RLKq+u8n20oLu2C32Vlz3:8AeatM/p+dVFG0tH2W+n23unglz3 |
MALICIOUS
Application was dropped or rewritten from another process
- MEMZ.exe (PID: 2960)
SUSPICIOUS
Executes scripts
- cmd.exe (PID: 3520)
Creates files in the user directory
- cscript.exe (PID: 2284)
- MEMZ.exe (PID: 2960)
Executable content was dropped or overwritten
- cscript.exe (PID: 2284)
Starts Internet Explorer
- MEMZ.exe (PID: 2960)
INFO
Creates files in the user directory
- iexplore.exe (PID: 2592)
Reads Internet Cache Settings
- iexplore.exe (PID: 2592)
Changes internet zones settings
- iexplore.exe (PID: 2244)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
35
Monitored processes
5
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2244 | "C:\Program Files\Internet Explorer\iexplore.exe" -nohome | C:\Program Files\Internet Explorer\iexplore.exe | MEMZ.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2284 | cscript x.js | C:\Windows\system32\cscript.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2592 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2244 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
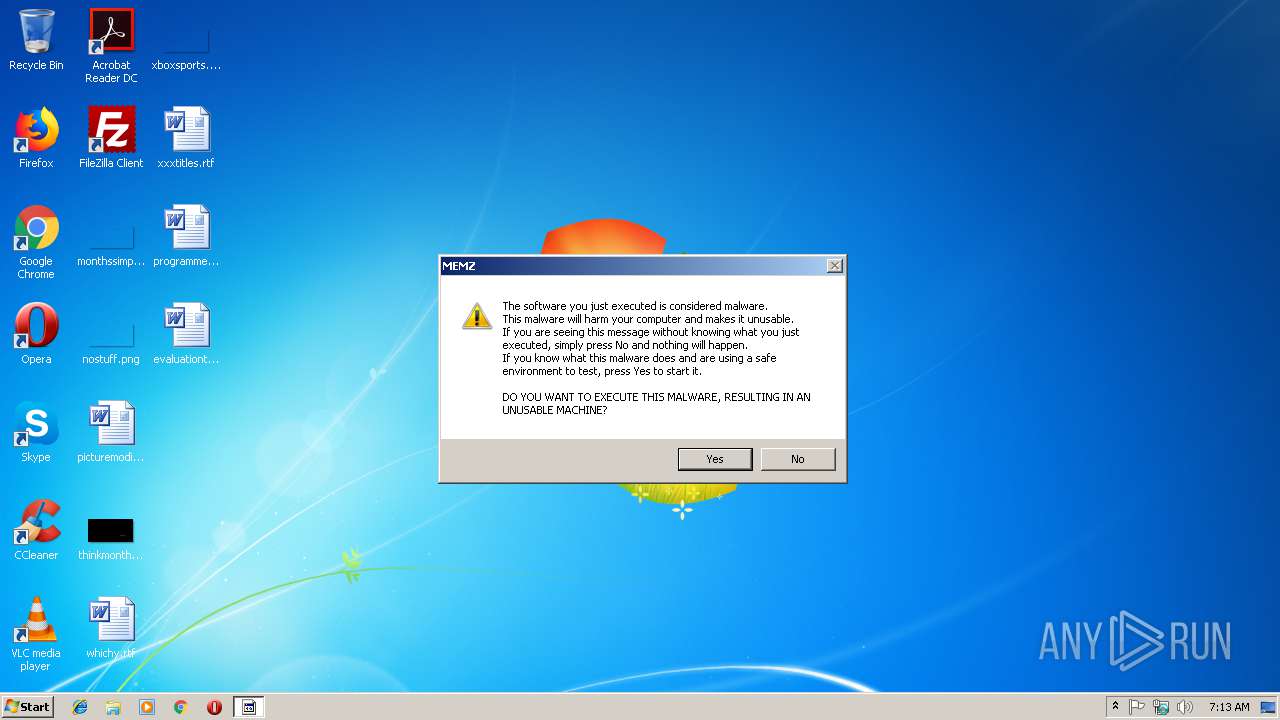
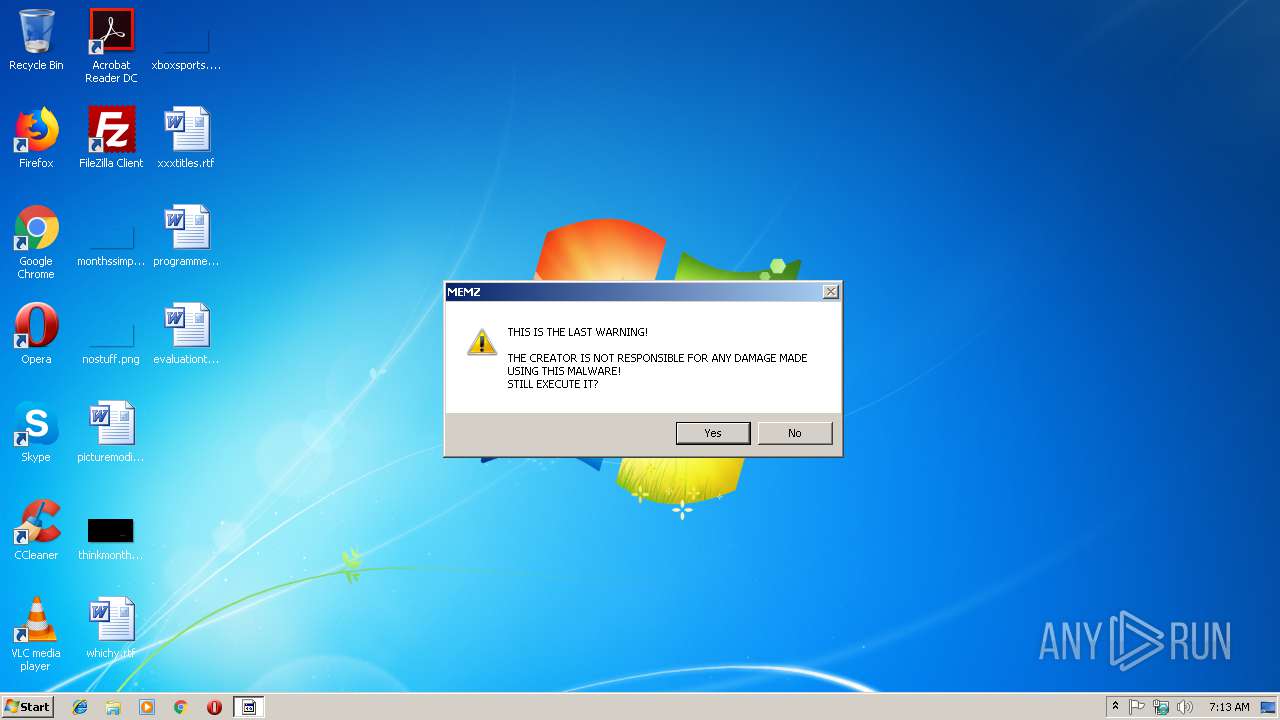
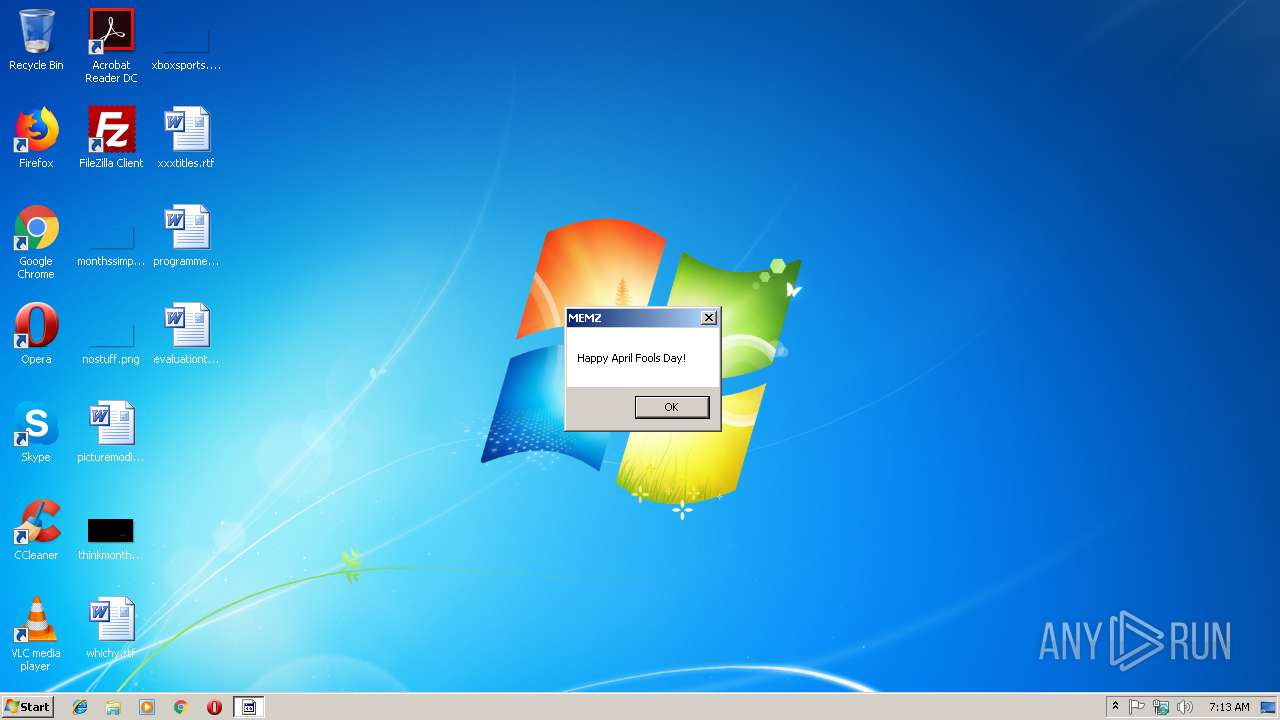
| 2960 | "C:\Users\admin\AppData\Roaming\MEMZ.exe" | C:\Users\admin\AppData\Roaming\MEMZ.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
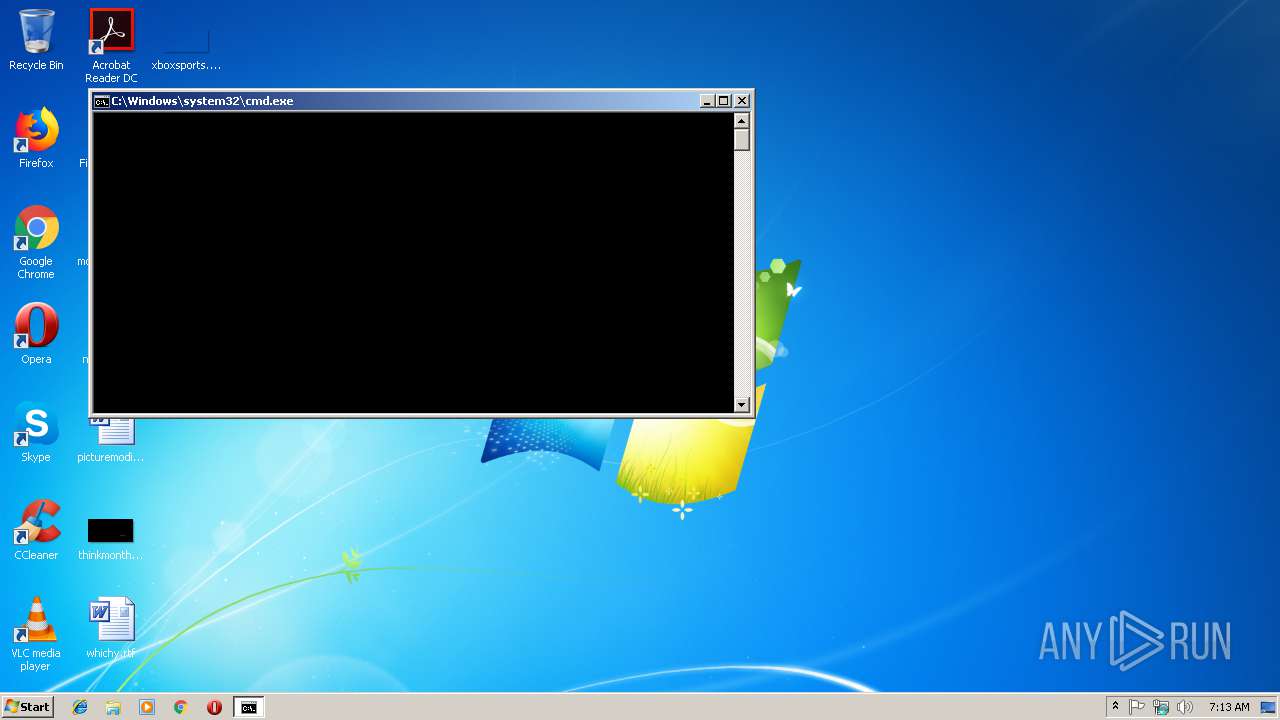
| 3520 | cmd /c ""C:\Users\admin\AppData\Local\Temp\MEMZ.bat" " | C:\Windows\system32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
728
Read events
679
Write events
49
Delete events
0
Modification events
| (PID) Process: | (2284) cscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2284) cscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2244) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2244) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2244) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2244) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (2244) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2244) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000069000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2244) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {1A70F57B-1895-11E9-BAD8-5254004A04AF} |
Value: 0 | |||
| (PID) Process: | (2244) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Type |
Value: 4 | |||
Executable files
1
Suspicious files
1
Text files
70
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2244 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\RB73MZ6Y\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 2244 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2592 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\admin@google.co[1].txt | — | |
MD5:— | SHA256:— | |||
| 3520 | cmd.exe | C:\Users\admin\AppData\Local\Temp\x | text | |
MD5:— | SHA256:— | |||
| 2284 | cscript.exe | C:\Users\admin\AppData\Roaming\MEMZ.exe | executable | |
MD5:D1F882DA71D058BDE723DEB56F1D912B | SHA256:BA100A74C6603DFCD4FE0E7DED04FCA6FABE7F6610B6F5AD4566E85C1203995E | |||
| 2244 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\RB73MZ6Y\favicon[3].png | image | |
MD5:9FB559A691078558E77D6848202F6541 | SHA256:6D8A01DC7647BC218D003B58FE04049E24A9359900B7E0CEBAE76EDF85B8B914 | |||
| 2592 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\admin@google.co[3].txt | text | |
MD5:— | SHA256:— | |||
| 2592 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\admin@google.co[4].txt | text | |
MD5:— | SHA256:— | |||
| 2592 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\admin@google.co[2].txt | text | |
MD5:— | SHA256:— | |||
| 2284 | cscript.exe | C:\Users\admin\AppData\Local\Temp\z.zip | compressed | |
MD5:B299BD2EA62A3798465208B7153946BB | SHA256:E19B4A5672907931803F20F76445441F9D73A149ECDB43D40D6815DFFA401AEC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
4
DNS requests
3
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2592 | iexplore.exe | GET | — | 172.217.23.131:80 | http://www.google.co.ck/search?q=how+2+buy+weed | US | — | — | whitelisted |
2244 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
2592 | iexplore.exe | GET | 301 | 108.177.127.103:80 | http://google.co.ck/search?q=john+cena+midi+legit+not+converted | US | html | 264 b | whitelisted |
2592 | iexplore.exe | GET | 301 | 108.177.127.103:80 | http://google.co.ck/search?q=how+2+buy+weed | US | html | 244 b | whitelisted |
2592 | iexplore.exe | GET | 302 | 172.217.23.131:80 | http://www.google.co.ck/search?q=john+cena+midi+legit+not+converted | US | html | 280 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2592 | iexplore.exe | 108.177.127.103:80 | google.co.ck | Google Inc. | US | whitelisted |
2244 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
2592 | iexplore.exe | 172.217.23.131:80 | www.google.co.ck | Google Inc. | US | whitelisted |
2592 | iexplore.exe | 172.217.23.131:443 | www.google.co.ck | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
google.co.ck |
| whitelisted |
www.google.co.ck |
| whitelisted |