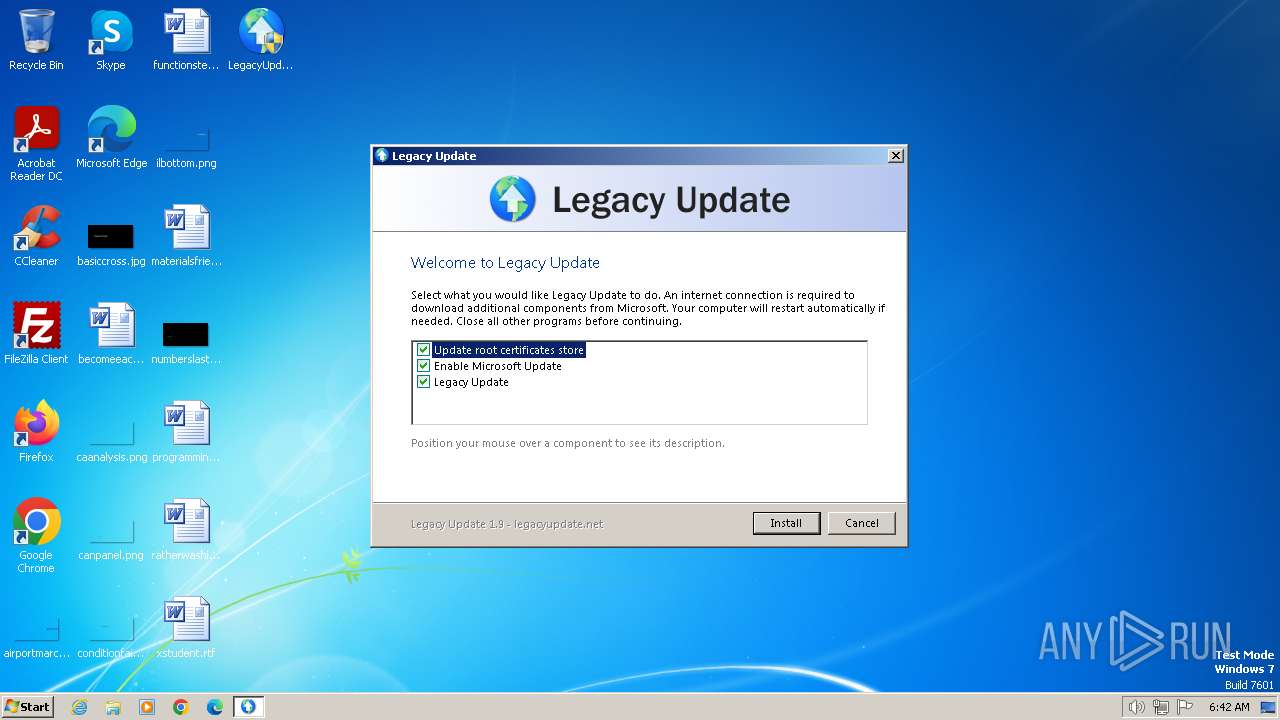
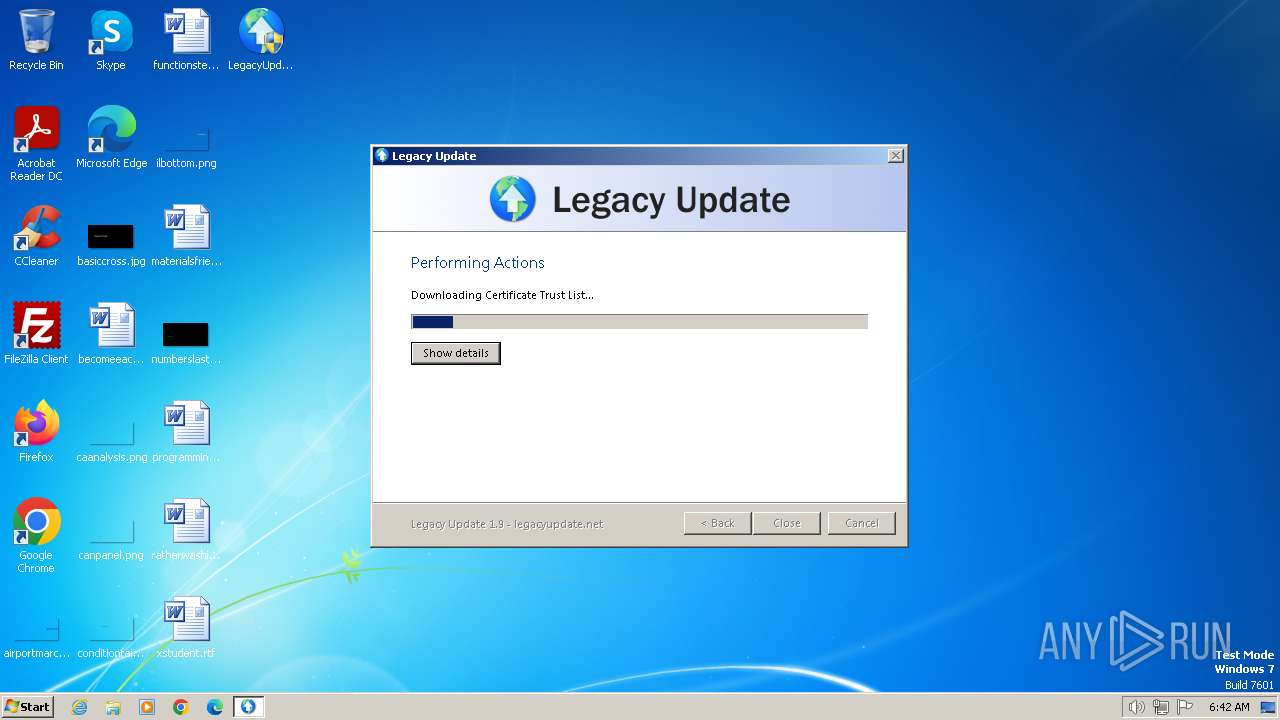
| download: | /LegacyUpdate/LegacyUpdate/releases/download/v1.9.0.0/LegacyUpdate-1.9.exe |
| Full analysis: | https://app.any.run/tasks/6465f3e3-79cf-4ceb-b145-45168c084ac4 |
| Verdict: | Malicious activity |
| Analysis date: | February 07, 2024, 06:42:00 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 (stripped to external PDB), for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | A0C1369D0226EE8E1E108280078883F8 |
| SHA1: | 7C17E830CECFBC1855B7F63051F6B109A3FCFEAB |
| SHA256: | F4808F6025F60CCCEE6FD8E15C36A8DB9340AD6A406E0166D1667770757BDA94 |
| SSDEEP: | 24576:zWSiriWVft7mdHfvaGXpOl4lUmugKPGRanTZjlf:zWSiriWRt7mdHfvaGXpOl4lU7gKPGRaf |
MALICIOUS
Drops the executable file immediately after the start
- LegacyUpdate-1.9.exe (PID: 3472)
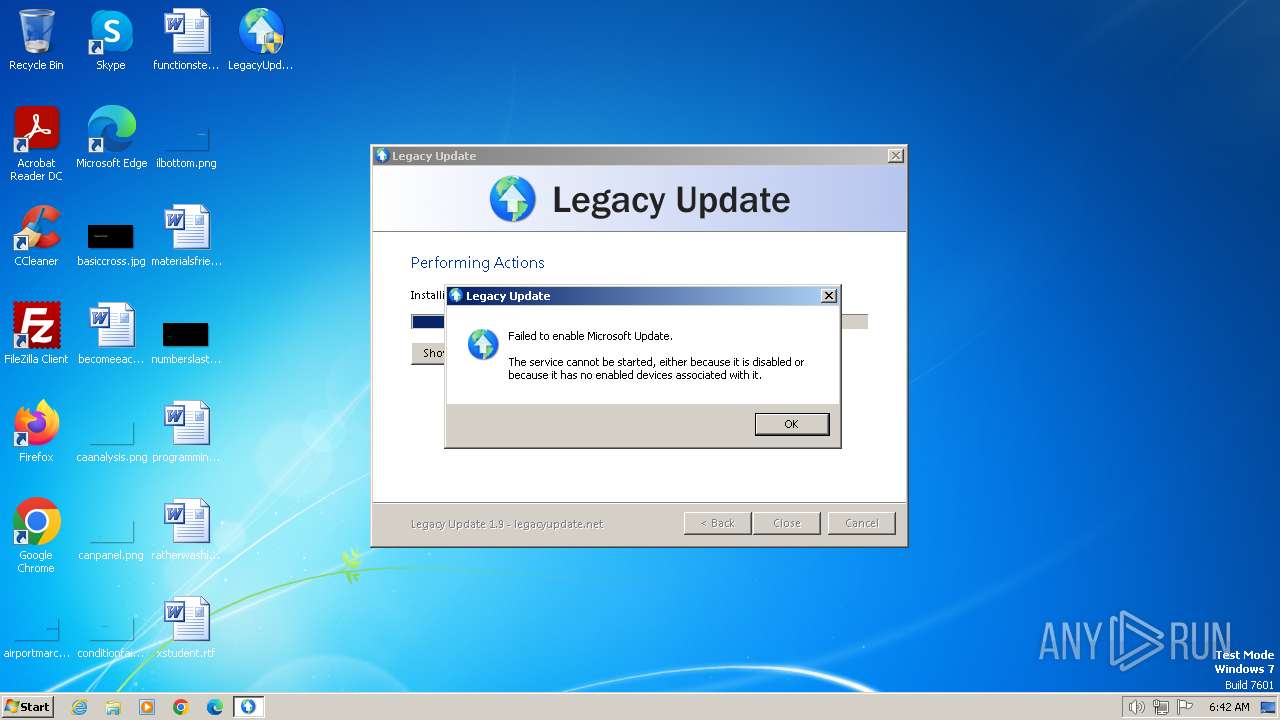
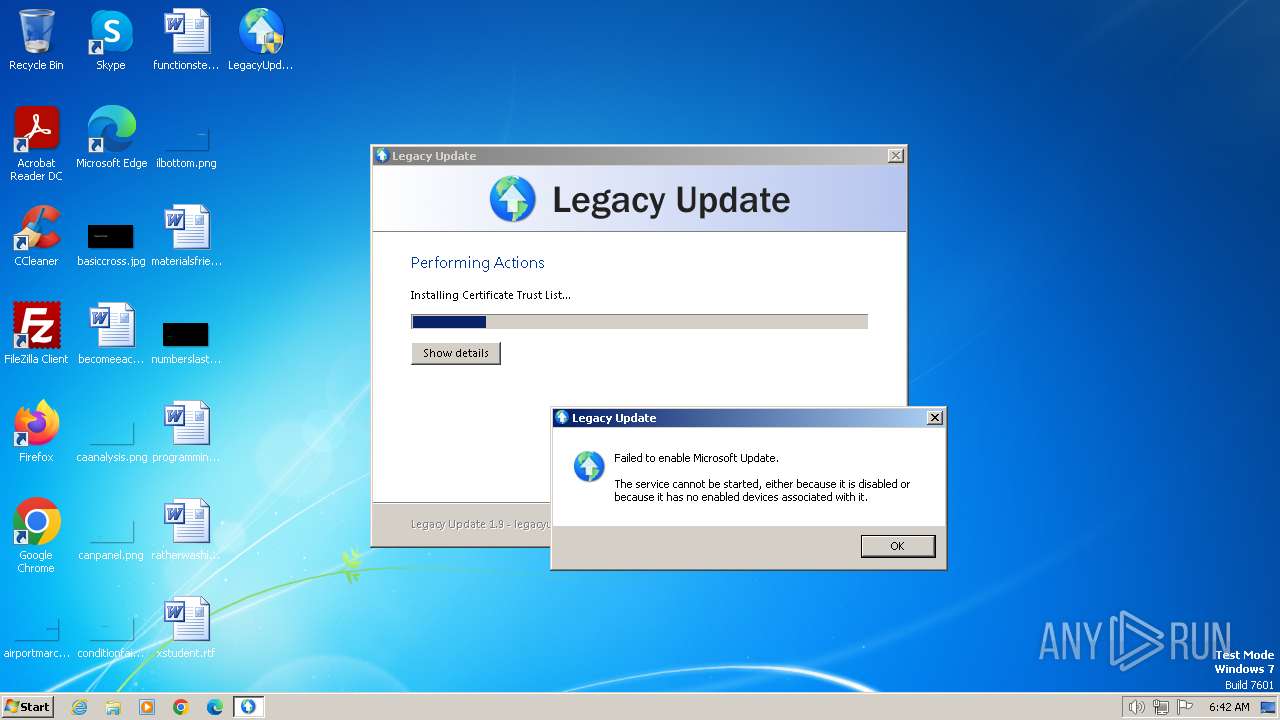
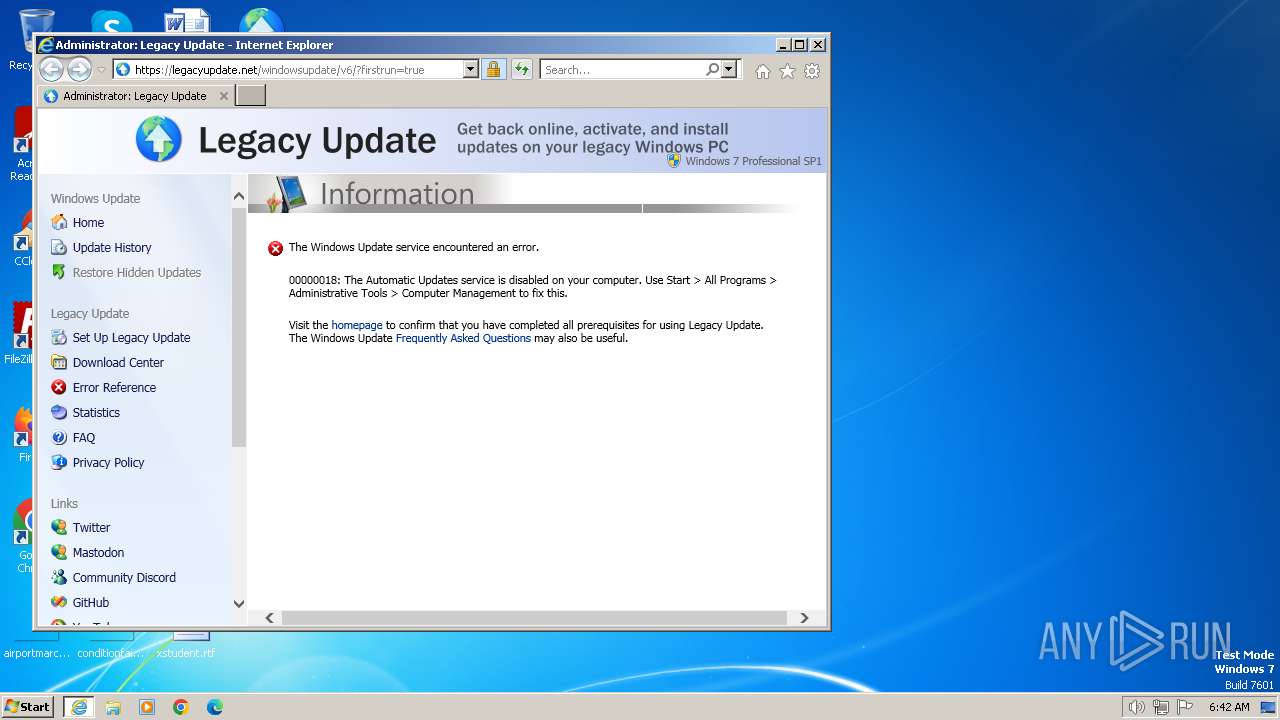
Uses NET.EXE to stop Windows Update service
- LegacyUpdate-1.9.exe (PID: 3472)
- net.exe (PID: 3548)
Starts NET.EXE for service management
- LegacyUpdate-1.9.exe (PID: 3472)
- net.exe (PID: 3548)
Registers / Runs the DLL via REGSVR32.EXE
- LegacyUpdate-1.9.exe (PID: 3472)
Starts NET.EXE to view/add/change user profiles
- net.exe (PID: 560)
- LegacyUpdate-1.9.exe (PID: 3472)
SUSPICIOUS
Malware-specific behavior (creating "System.dll" in Temp)
- LegacyUpdate-1.9.exe (PID: 3472)
Executable content was dropped or overwritten
- LegacyUpdate-1.9.exe (PID: 3472)
The process creates files with name similar to system file names
- LegacyUpdate-1.9.exe (PID: 3472)
Reads the Internet Settings
- LegacyUpdate-1.9.exe (PID: 3472)
Process drops legitimate windows executable
- LegacyUpdate-1.9.exe (PID: 3472)
Uses RUNDLL32.EXE to load library
- LegacyUpdate-1.9.exe (PID: 3472)
INFO
Reads the computer name
- LegacyUpdate-1.9.exe (PID: 3472)
Checks supported languages
- LegacyUpdate-1.9.exe (PID: 3472)
- updroots.exe (PID: 3000)
- updroots.exe (PID: 3436)
- updroots.exe (PID: 3580)
- updroots.exe (PID: 3412)
- updroots.exe (PID: 3600)
Checks proxy server information
- LegacyUpdate-1.9.exe (PID: 3472)
Create files in a temporary directory
- LegacyUpdate-1.9.exe (PID: 3472)
Creates files in the program directory
- LegacyUpdate-1.9.exe (PID: 3472)
Reads the machine GUID from the registry
- LegacyUpdate-1.9.exe (PID: 3472)
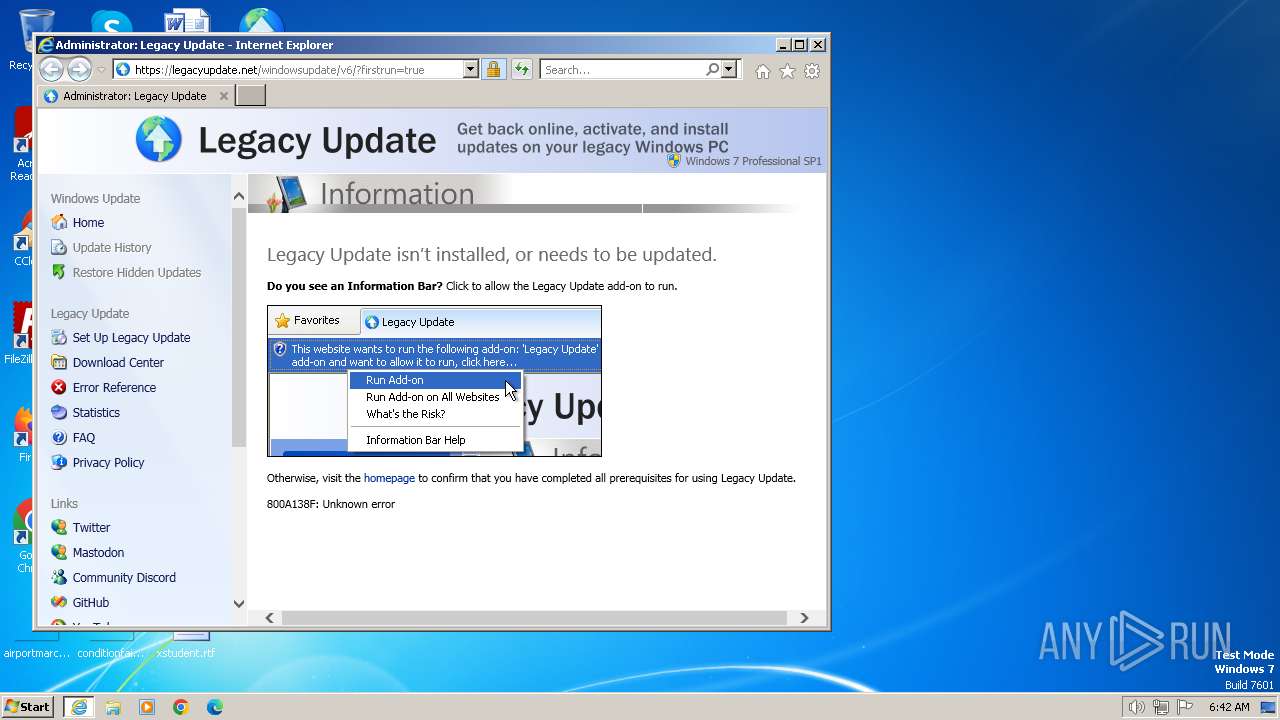
Application launched itself
- iexplore.exe (PID: 3704)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:07:20 09:58:41+02:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit, No debug |
| PEType: | PE32 |
| LinkerVersion: | 2.4 |
| CodeSize: | 44032 |
| InitializedDataSize: | 61952 |
| UninitializedDataSize: | 129024 |
| EntryPoint: | 0x4590 |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.9.0.0 |
| ProductVersionNumber: | 1.9.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Hashbang Productions |
| FileDescription: | Legacy Update |
| FileVersion: | 1.9.0.0 |
| LegalCopyright: | © Hashbang Productions. All rights reserved. |
| ProductName: | Legacy Update |
| ProductVersion: | 1.9.0.0 |
Total processes
61
Monitored processes
16
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 560 | "C:\Windows\system32\net.exe" user /delete LegacyUpdateTemp | C:\Windows\System32\net.exe | — | LegacyUpdate-1.9.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 752 | "C:\Users\admin\Desktop\LegacyUpdate-1.9.exe" | C:\Users\admin\Desktop\LegacyUpdate-1.9.exe | — | explorer.exe | |||||||||||
User: admin Company: Hashbang Productions Integrity Level: MEDIUM Description: Legacy Update Exit code: 3221226540 Version: 1.9.0.0 Modules
| |||||||||||||||
| 2612 | C:\Windows\system32\net1 stop wuauserv | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 2 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3000 | "C:\ProgramData\Legacy Update\updroots.exe" authroots.sst | C:\ProgramData\Legacy Update\updroots.exe | — | LegacyUpdate-1.9.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: UPDROOTS Exit code: 0 Version: 5.2.3790.4456 built by: dnsrv(ansaboor) Modules
| |||||||||||||||
| 3320 | C:\Windows\system32\rundll32.exe "C:\Program Files\Legacy Update\LegacyUpdate.dll",LaunchUpdateSite firstrun | C:\Windows\System32\rundll32.exe | — | LegacyUpdate-1.9.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3412 | "C:\ProgramData\Legacy Update\updroots.exe" -l roots.sst | C:\ProgramData\Legacy Update\updroots.exe | — | LegacyUpdate-1.9.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: UPDROOTS Exit code: 0 Version: 5.2.3790.4456 built by: dnsrv(ansaboor) Modules
| |||||||||||||||
| 3436 | "C:\ProgramData\Legacy Update\updroots.exe" updroots.sst | C:\ProgramData\Legacy Update\updroots.exe | — | LegacyUpdate-1.9.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: UPDROOTS Exit code: 0 Version: 5.2.3790.4456 built by: dnsrv(ansaboor) Modules
| |||||||||||||||
| 3472 | "C:\Users\admin\Desktop\LegacyUpdate-1.9.exe" | C:\Users\admin\Desktop\LegacyUpdate-1.9.exe | explorer.exe | ||||||||||||
User: admin Company: Hashbang Productions Integrity Level: HIGH Description: Legacy Update Exit code: 0 Version: 1.9.0.0 Modules
| |||||||||||||||
| 3548 | "C:\Windows\system32\net.exe" stop wuauserv | C:\Windows\System32\net.exe | — | LegacyUpdate-1.9.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3580 | "C:\ProgramData\Legacy Update\updroots.exe" -d delroots.sst | C:\ProgramData\Legacy Update\updroots.exe | — | LegacyUpdate-1.9.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: UPDROOTS Exit code: 0 Version: 5.2.3790.4456 built by: dnsrv(ansaboor) Modules
| |||||||||||||||
Total events
55 410
Read events
52 740
Write events
2 245
Delete events
425
Modification events
| (PID) Process: | (3472) LegacyUpdate-1.9.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3472) LegacyUpdate-1.9.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000005B010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A8016B000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3472) LegacyUpdate-1.9.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | SecureProtocols |
Value: 2688 | |||
| (PID) Process: | (3472) LegacyUpdate-1.9.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | SecureProtocols |
Value: 2688 | |||
| (PID) Process: | (3472) LegacyUpdate-1.9.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\WinHttp |
| Operation: | write | Name: | DefaultSecureProtocols |
Value: 2560 | |||
| (PID) Process: | (3000) updroots.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\51501FBFCE69189D609CFAF140C576755DCC1FDF |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3000) updroots.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\E12DFB4B41D7D9C32B30514BAC1D81D8385E2D46 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3000) updroots.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\216B2A29E62A00CE820146D8244141B92511B279 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3000) updroots.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\74207441729CDD92EC7931D823108DC28192E2BB |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3000) updroots.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\D23209AD23D314232174E40D7F9D62139786633A |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
6
Suspicious files
24
Text files
98
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3472 | LegacyUpdate-1.9.exe | C:\Users\admin\AppData\Local\Temp\nsp360B.tmp\modern-header.bmp | image | |
MD5:6CA9768CE2CF8D08BEE76BDEFE77BD88 | SHA256:239BDF82D221779561CCD10461BE17C27EE84FF0D5C17B944C8549371F448621 | |||
| 3472 | LegacyUpdate-1.9.exe | C:\ProgramData\Legacy Update\roots.sst | binary | |
MD5:72544AFDFCF3014DDD8231146C52D218 | SHA256:A95D014BF5876D49AA3D7B7581F4B8650DC7305709AC800FBB4CC1D036C39347 | |||
| 3472 | LegacyUpdate-1.9.exe | C:\Users\admin\AppData\Local\Temp\nsp360B.tmp\LegacyUpdateNSIS.dll | executable | |
MD5:C61309F21AE08B3215E10E40E4BB12C5 | SHA256:890F79E630FCEAF2A73FFBF0C574A4F0D05CFBBE7E753A6AD135AE551FCDC2CD | |||
| 3472 | LegacyUpdate-1.9.exe | C:\Users\admin\AppData\Local\Temp\nsp360B.tmp\Patches.ini | text | |
MD5:2B1ABAD02C19544A1AE1488C24408290 | SHA256:02C8CBA89DF8F19FA0B06B4B7EBB97AC1B273701142C5E7CED0CCAA1DB3ABB1E | |||
| 3472 | LegacyUpdate-1.9.exe | C:\Program Files\Legacy Update\Uninstall.exe | executable | |
MD5:FB1E788FADE5E28EDF88405F899BF4B1 | SHA256:1CF23FF83E21FBD020F7BC964266658F06FB9B2CEB73D19C61B55851BCA5F620 | |||
| 3472 | LegacyUpdate-1.9.exe | C:\ProgramData\Legacy Update\disallowedcert.sst | binary | |
MD5:186256E148543246DC43D108E3B39E60 | SHA256:27DD3EBF1D7FFF7F033747E2DE467B8E86DA7EA81B789B57DF2312AE3CB41C96 | |||
| 3472 | LegacyUpdate-1.9.exe | C:\Program Files\Legacy Update\LegacyUpdate.dll | executable | |
MD5:FFB1A403CEE1D267AF43416AD6226121 | SHA256:7ADEB274998A4786D5E4543F7105100723E4D0D93926FC90B2FDC256F9F59FA7 | |||
| 3472 | LegacyUpdate-1.9.exe | C:\ProgramData\Legacy Update\authroots.sst | binary | |
MD5:23C2C0DD2BE80C8F65332394FBB3DF1E | SHA256:28BB8CDE08B28E0A6B084288251BB936CE4375C8A32DA2B42325961475FE586D | |||
| 3472 | LegacyUpdate-1.9.exe | C:\ProgramData\Legacy Update\updroots.exe | executable | |
MD5:063DD2B2CEFF421E944446057A77FCE9 | SHA256:9E538A58AED94A7748DF9262AE0343DEA9EFCE8D9117E0868EB404E1098747B6 | |||
| 3472 | LegacyUpdate-1.9.exe | C:\ProgramData\Legacy Update\delroots.sst | binary | |
MD5:21B91F351B958AC6F19B189FB9C65F1B | SHA256:6F265A63551B8ACB57F8B6E90B7AAD945EFB2B3F9A3CB203CA21E9E9A1D88040 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
34
DNS requests
14
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3924 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
3704 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAxq6XzO1ZmDhpCgCp6lMhQ%3D | unknown | binary | 471 b | unknown |
1080 | svchost.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?1dd404ff67a3d8ee | unknown | compressed | 65.2 Kb | unknown |
3472 | LegacyUpdate-1.9.exe | GET | 200 | 93.184.221.240:80 | http://download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authroots.sst | unknown | binary | 32.5 Kb | unknown |
3472 | LegacyUpdate-1.9.exe | GET | 200 | 93.184.221.240:80 | http://download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/updroots.sst | unknown | binary | 625 Kb | unknown |
3472 | LegacyUpdate-1.9.exe | GET | 200 | 93.184.221.240:80 | http://download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/delroots.sst | unknown | binary | 187 Kb | unknown |
3472 | LegacyUpdate-1.9.exe | GET | 200 | 93.184.221.240:80 | http://download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/roots.sst | unknown | binary | 5.29 Kb | unknown |
3472 | LegacyUpdate-1.9.exe | GET | 200 | 93.184.221.240:80 | http://download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcert.sst | unknown | binary | 113 Kb | unknown |
3924 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?bbe50deb7db51181 | unknown | — | — | unknown |
3704 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAzlnDD9eoNTLi0BRrMy%2BWU%3D | unknown | binary | 312 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3472 | LegacyUpdate-1.9.exe | 93.184.221.240:80 | download.windowsupdate.com | EDGECAST | GB | whitelisted |
3924 | iexplore.exe | 188.114.97.3:443 | legacyupdate.net | CLOUDFLARENET | NL | unknown |
3924 | iexplore.exe | 93.184.221.240:80 | download.windowsupdate.com | EDGECAST | GB | whitelisted |
3924 | iexplore.exe | 142.250.185.131:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
3704 | iexplore.exe | 2.19.120.32:443 | www.bing.com | Akamai International B.V. | DE | unknown |
3704 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3948 | iexplore.exe | 188.114.97.3:443 | legacyupdate.net | CLOUDFLARENET | NL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
download.windowsupdate.com |
| whitelisted |
legacyupdate.net |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
ieonline.microsoft.com |
| whitelisted |