| File name: | WebComponents.exe |
| Full analysis: | https://app.any.run/tasks/d97011e4-7a73-49ac-af4c-6f055bd25f75 |
| Verdict: | Malicious activity |
| Analysis date: | March 15, 2024, 06:37:59 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 38AF9A1EAF486CF7BFEC6303EDE4DF75 |
| SHA1: | BC805166BA6F51B0DE0CC4DDB7736070B2EBD434 |
| SHA256: | F46CB46DC580ECD32DBB661538763F23DBB07AB0FFA9FA7222988EA1B39D600A |
| SSDEEP: | 98304:Tmfr20GuBuNa7EX0QOtY1j5iKq23x7OFcegovSAZigjcxKpyqivJSIXvpREGlIOG:eUoRMHfKFdAa |
MALICIOUS
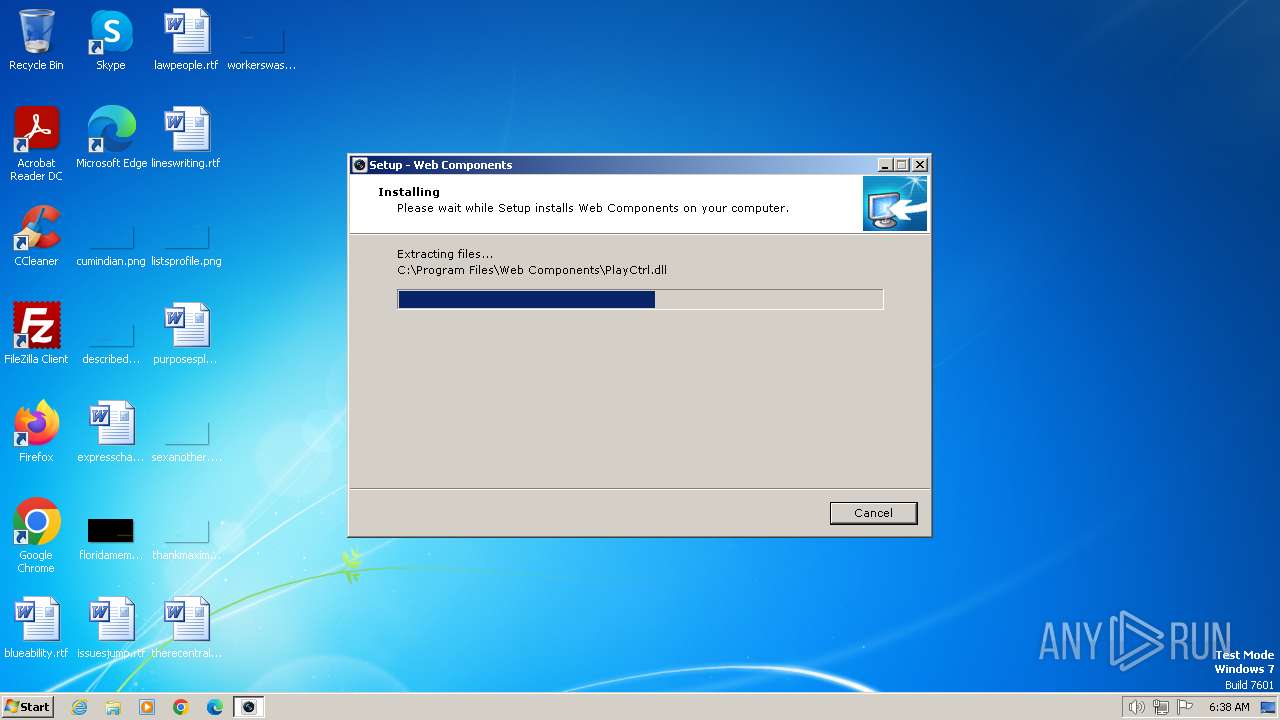
Drops the executable file immediately after the start
- WebComponents.exe (PID: 3916)
- WebComponents.exe (PID: 3464)
- WebComponents.tmp (PID: 3932)
Registers / Runs the DLL via REGSVR32.EXE
- WebComponents.tmp (PID: 3932)
SUSPICIOUS
Executable content was dropped or overwritten
- WebComponents.exe (PID: 3916)
- WebComponents.exe (PID: 3464)
- WebComponents.tmp (PID: 3932)
Process drops legitimate windows executable
- WebComponents.tmp (PID: 3932)
Reads the Windows owner or organization settings
- WebComponents.tmp (PID: 3932)
The process drops C-runtime libraries
- WebComponents.tmp (PID: 3932)
Creates/Modifies COM task schedule object
- regsvr32.exe (PID: 1040)
INFO
Checks supported languages
- WebComponents.exe (PID: 3916)
- WebComponents.tmp (PID: 3972)
- WebComponents.exe (PID: 3464)
- WebComponents.tmp (PID: 3932)
Reads the computer name
- WebComponents.tmp (PID: 3972)
- WebComponents.tmp (PID: 3932)
Create files in a temporary directory
- WebComponents.exe (PID: 3916)
- WebComponents.exe (PID: 3464)
- WebComponents.tmp (PID: 3932)
Creates files in the program directory
- WebComponents.tmp (PID: 3932)
Creates a software uninstall entry
- WebComponents.tmp (PID: 3932)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (77.7) |
|---|---|---|
| .exe | | | Win32 Executable Delphi generic (10) |
| .dll | | | Win32 Dynamic Link Library (generic) (4.6) |
| .exe | | | Win32 Executable (generic) (3.1) |
| .exe | | | Win16/32 Executable Delphi generic (1.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:19 22:22:17+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 37888 |
| InitializedDataSize: | 14848 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x9b24 |
| OSVersion: | 1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 3.0.8.34 |
| ProductVersionNumber: | 3.0.8.34 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | |
| FileDescription: | Web Components Setup |
| FileVersion: | 3.0.8.34 |
| LegalCopyright: | |
| ProductName: | Web Components |
| ProductVersion: | 3.0.8.34 |
Total processes
43
Monitored processes
5
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1040 | "C:\Windows\system32\regsvr32.exe" /s "C:\Program Files\Web Components\WebVideoActiveX.ocx" | C:\Windows\System32\regsvr32.exe | WebComponents.tmp | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3464 | "C:\Users\admin\AppData\Local\Temp\WebComponents.exe" /SPAWNWND=$1A01BC /NOTIFYWND=$E0170 | C:\Users\admin\AppData\Local\Temp\WebComponents.exe | WebComponents.tmp | ||||||||||||
User: admin Company: Integrity Level: HIGH Description: Web Components Setup Exit code: 0 Version: 3.0.8.34 Modules
| |||||||||||||||
| 3916 | "C:\Users\admin\AppData\Local\Temp\WebComponents.exe" | C:\Users\admin\AppData\Local\Temp\WebComponents.exe | explorer.exe | ||||||||||||
User: admin Company: Integrity Level: MEDIUM Description: Web Components Setup Exit code: 0 Version: 3.0.8.34 Modules
| |||||||||||||||
| 3932 | "C:\Users\admin\AppData\Local\Temp\is-4UK20.tmp\WebComponents.tmp" /SL5="$19013E,4808642,53760,C:\Users\admin\AppData\Local\Temp\WebComponents.exe" /SPAWNWND=$1A01BC /NOTIFYWND=$E0170 | C:\Users\admin\AppData\Local\Temp\is-4UK20.tmp\WebComponents.tmp | WebComponents.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.50.0.0 Modules
| |||||||||||||||
| 3972 | "C:\Users\admin\AppData\Local\Temp\is-RN7NK.tmp\WebComponents.tmp" /SL5="$E0170,4808642,53760,C:\Users\admin\AppData\Local\Temp\WebComponents.exe" | C:\Users\admin\AppData\Local\Temp\is-RN7NK.tmp\WebComponents.tmp | — | WebComponents.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.50.0.0 Modules
| |||||||||||||||
Total events
5 027
Read events
5 009
Write events
18
Delete events
0
Modification events
| (PID) Process: | (3932) WebComponents.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\MozillaPlugins\Web Components |
| Operation: | write | Name: | Path |
Value: C:\Program Files\Web Components\npWebVideoPlugin.dll | |||
| (PID) Process: | (1040) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Interface\{7F79CD87-2D7A-4086-807E-D5E1A3E37BE5}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.0 | |||
| (PID) Process: | (1040) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Interface\{DE8B9108-0847-49C1-8E58-5972B6137DFD}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.0 | |||
| (PID) Process: | (1040) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{E7EF736D-B4E6-4A5A-BA94-732D71107808}\InprocServer32 |
| Operation: | write | Name: | ThreadingModel |
Value: Apartment | |||
| (PID) Process: | (3932) WebComponents.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{03B13AF8-9625-478A-AF0E-205337B9415A}_is1 |
| Operation: | write | Name: | Inno Setup: Setup Version |
Value: 5.3.5 (a) | |||
| (PID) Process: | (3932) WebComponents.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{03B13AF8-9625-478A-AF0E-205337B9415A}_is1 |
| Operation: | write | Name: | Inno Setup: App Path |
Value: C:\Program Files\Web Components | |||
| (PID) Process: | (3932) WebComponents.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{03B13AF8-9625-478A-AF0E-205337B9415A}_is1 |
| Operation: | write | Name: | InstallLocation |
Value: C:\Program Files\Web Components\ | |||
| (PID) Process: | (3932) WebComponents.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{03B13AF8-9625-478A-AF0E-205337B9415A}_is1 |
| Operation: | write | Name: | Inno Setup: Icon Group |
Value: WebComponents | |||
| (PID) Process: | (3932) WebComponents.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{03B13AF8-9625-478A-AF0E-205337B9415A}_is1 |
| Operation: | write | Name: | Inno Setup: User |
Value: admin | |||
| (PID) Process: | (3932) WebComponents.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{03B13AF8-9625-478A-AF0E-205337B9415A}_is1 |
| Operation: | write | Name: | DisplayName |
Value: Web Components | |||
Executable files
43
Suspicious files
2
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3932 | WebComponents.tmp | C:\Users\admin\AppData\Local\Temp\is-3B49J.tmp\_isetup\_shfoldr.dll | executable | |
MD5:92DC6EF532FBB4A5C3201469A5B5EB63 | SHA256:9884E9D1B4F8A873CCBD81F8AD0AE257776D2348D027D811A56475E028360D87 | |||
| 3932 | WebComponents.tmp | C:\Users\admin\AppData\Local\Temp\is-3B49J.tmp\ISTask.dll | executable | |
MD5:86A1311D51C00B278CB7F27796EA442E | SHA256:E916BDF232744E00CBD8D608168A019C9F41A68A7E8390AA48CFB525276C483D | |||
| 3932 | WebComponents.tmp | C:\Program Files\Web Components\is-GV2E6.tmp | executable | |
MD5:2357DFBCBC4A0C3EC0DC36F18F280F01 | SHA256:135F0D03D60FD102E209B55A93173C3239981F2A8B346AF8F977E8933A26D5FE | |||
| 3932 | WebComponents.tmp | C:\Program Files\Web Components\unins000.exe | executable | |
MD5:2357DFBCBC4A0C3EC0DC36F18F280F01 | SHA256:135F0D03D60FD102E209B55A93173C3239981F2A8B346AF8F977E8933A26D5FE | |||
| 3932 | WebComponents.tmp | C:\Program Files\Web Components\NetStream.dll | executable | |
MD5:D8F56FFD4161B30A8EAF6CE2CCFC769F | SHA256:1FC8AA41772983F58E8A5B5AF93A95A9FF5616C0BF204F240CF1D6934BA7D4D3 | |||
| 3932 | WebComponents.tmp | C:\Program Files\Web Components\is-66P6C.tmp | executable | |
MD5:86A1311D51C00B278CB7F27796EA442E | SHA256:E916BDF232744E00CBD8D608168A019C9F41A68A7E8390AA48CFB525276C483D | |||
| 3932 | WebComponents.tmp | C:\Program Files\Web Components\ISTask.dll | executable | |
MD5:86A1311D51C00B278CB7F27796EA442E | SHA256:E916BDF232744E00CBD8D608168A019C9F41A68A7E8390AA48CFB525276C483D | |||
| 3932 | WebComponents.tmp | C:\Program Files\Web Components\WebVideoActiveX.ocx | executable | |
MD5:0856CB4BF54FB28B7C143860C77AC0C7 | SHA256:4E6934F5BD838D2DF41451E0CC24F1FA2585C6315C21D372C1904F6F9B3E6B2F | |||
| 3932 | WebComponents.tmp | C:\Program Files\Web Components\is-DU60M.tmp | executable | |
MD5:0856CB4BF54FB28B7C143860C77AC0C7 | SHA256:4E6934F5BD838D2DF41451E0CC24F1FA2585C6315C21D372C1904F6F9B3E6B2F | |||
| 3932 | WebComponents.tmp | C:\Program Files\Web Components\is-RAJ5I.tmp | executable | |
MD5:D8F56FFD4161B30A8EAF6CE2CCFC769F | SHA256:1FC8AA41772983F58E8A5B5AF93A95A9FF5616C0BF204F240CF1D6934BA7D4D3 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
DNS requests
Threats
Process | Message |
|---|---|
regsvr32.exe | CLocalConfig::GetLocalConfig
|
regsvr32.exe | Create local config file succ!
|
regsvr32.exe | CLocalConfig::GetLocalConfig parseFile failed!
|
regsvr32.exe | [Info]StreamTranClient---version:this RTSP version is asyn..
|
regsvr32.exe | [Debug]StreamTranClient---Create asyncio queue succ!
|
regsvr32.exe | [Info]StreamTranClient---version:this RTSP version is 1.1.3.101 2022_12_09..
|
regsvr32.exe | [Debug]StreamTranClient---Destroy asyncio queue succ!
|