| File name: | AacAmbientLighting.exe |
| Full analysis: | https://app.any.run/tasks/b4ae9d1b-479b-4750-a359-9ab9aa25f9fb |
| Verdict: | Malicious activity |
| Threats: | A loader is malicious software that infiltrates devices to deliver malicious payloads. This malware is capable of infecting victims’ computers, analyzing their system information, and installing other types of threats, such as trojans or stealers. Criminals usually deliver loaders through phishing emails and links by relying on social engineering to trick users into downloading and running their executables. Loaders employ advanced evasion and persistence tactics to avoid detection. |
| Analysis date: | July 27, 2024, 15:58:32 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 89EC913BFAAC3D75269EC758EF8E79B6 |
| SHA1: | 982BB9EE6D9CDD0DC300F2F365DEF2891E2D38D7 |
| SHA256: | F44D71A0BEA0171B085D6918F3341708E1276CE266990882C69887C2E9AAF636 |
| SSDEEP: | 98304:p+kUtYMPPYpOdld65kkWAhUEl6laXeBeFjfcrw7RyvCUtB9NgFAr1aPLqcuBqIO1:MF2p |
MALICIOUS
Drops the executable file immediately after the start
- AacAmbientLighting.exe (PID: 7032)
- cmd.exe (PID: 7156)
- vFnYSZsLbjSUjV.exe (PID: 2240)
- Appointments.pif (PID: 2692)
- cmd.exe (PID: 3648)
- Extras.pif (PID: 4656)
- Appointments.pif (PID: 4600)
Antivirus name has been found in the command line (generic signature)
- findstr.exe (PID: 7104)
- findstr.exe (PID: 2068)
- findstr.exe (PID: 1388)
- findstr.exe (PID: 4316)
- findstr.exe (PID: 4852)
- findstr.exe (PID: 504)
- findstr.exe (PID: 6648)
- findstr.exe (PID: 7132)
Scans artifacts that could help determine the target
- Appointments.pif (PID: 2692)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 3780)
Create files in the Startup directory
- cmd.exe (PID: 2192)
SUSPICIOUS
Reads the date of Windows installation
- AacAmbientLighting.exe (PID: 7032)
- AacAmbientLighting.exe (PID: 720)
- Appointments.pif (PID: 2692)
- vFnYSZsLbjSUjV.exe (PID: 2240)
- Appointments.pif (PID: 4600)
- EovJmduARXsqIm.exe (PID: 6524)
Reads security settings of Internet Explorer
- AacAmbientLighting.exe (PID: 7032)
- Appointments.pif (PID: 2692)
- AacAmbientLighting.exe (PID: 720)
- vFnYSZsLbjSUjV.exe (PID: 2240)
- Appointments.pif (PID: 4600)
- EovJmduARXsqIm.exe (PID: 6524)
Executing commands from ".cmd" file
- AacAmbientLighting.exe (PID: 7032)
- AacAmbientLighting.exe (PID: 720)
- vFnYSZsLbjSUjV.exe (PID: 2240)
- EovJmduARXsqIm.exe (PID: 6524)
Starts CMD.EXE for commands execution
- AacAmbientLighting.exe (PID: 7032)
- cmd.exe (PID: 7156)
- AacAmbientLighting.exe (PID: 720)
- vFnYSZsLbjSUjV.exe (PID: 2240)
- cmd.exe (PID: 5848)
- cmd.exe (PID: 3648)
- cmd.exe (PID: 644)
- EovJmduARXsqIm.exe (PID: 6524)
Get information on the list of running processes
- cmd.exe (PID: 7156)
- cmd.exe (PID: 5848)
- cmd.exe (PID: 3648)
- cmd.exe (PID: 644)
Application launched itself
- cmd.exe (PID: 7156)
- cmd.exe (PID: 5848)
- cmd.exe (PID: 3648)
- cmd.exe (PID: 644)
Drops a file with a rarely used extension (PIF)
- cmd.exe (PID: 7156)
- cmd.exe (PID: 3648)
- Extras.pif (PID: 4656)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 7156)
- cmd.exe (PID: 5848)
- cmd.exe (PID: 3648)
- cmd.exe (PID: 644)
Executable content was dropped or overwritten
- cmd.exe (PID: 7156)
- Appointments.pif (PID: 2692)
- cmd.exe (PID: 3648)
- Extras.pif (PID: 4656)
- Appointments.pif (PID: 4600)
Suspicious file concatenation
- cmd.exe (PID: 1328)
- cmd.exe (PID: 3476)
- cmd.exe (PID: 3660)
- cmd.exe (PID: 3572)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 7156)
- cmd.exe (PID: 5848)
- cmd.exe (PID: 3648)
- cmd.exe (PID: 644)
Checks Windows Trust Settings
- Appointments.pif (PID: 2692)
- Appointments.pif (PID: 4600)
The executable file from the user directory is run by the CMD process
- Appointments.pif (PID: 2692)
- Appointments.pif (PID: 4600)
- Extras.pif (PID: 4656)
- Extras.pif (PID: 7156)
Process drops legitimate windows executable
- Appointments.pif (PID: 2692)
Starts application with an unusual extension
- cmd.exe (PID: 5848)
- cmd.exe (PID: 3648)
- cmd.exe (PID: 644)
- cmd.exe (PID: 7156)
INFO
Create files in a temporary directory
- AacAmbientLighting.exe (PID: 7032)
- Appointments.pif (PID: 2692)
- AacAmbientLighting.exe (PID: 720)
- vFnYSZsLbjSUjV.exe (PID: 2240)
- EovJmduARXsqIm.exe (PID: 6524)
Checks supported languages
- AacAmbientLighting.exe (PID: 7032)
- Appointments.pif (PID: 2692)
- vFnYSZsLbjSUjV.exe (PID: 2240)
- AacAmbientLighting.exe (PID: 720)
- Appointments.pif (PID: 4600)
- Extras.pif (PID: 4656)
- EovJmduARXsqIm.exe (PID: 6524)
- Extras.pif (PID: 7156)
- Extras.pif (PID: 132)
Reads the computer name
- AacAmbientLighting.exe (PID: 7032)
- Appointments.pif (PID: 2692)
- AacAmbientLighting.exe (PID: 720)
- vFnYSZsLbjSUjV.exe (PID: 2240)
- Appointments.pif (PID: 4600)
- Extras.pif (PID: 4656)
- EovJmduARXsqIm.exe (PID: 6524)
Process checks computer location settings
- AacAmbientLighting.exe (PID: 7032)
- AacAmbientLighting.exe (PID: 720)
- Appointments.pif (PID: 2692)
- vFnYSZsLbjSUjV.exe (PID: 2240)
- Appointments.pif (PID: 4600)
- EovJmduARXsqIm.exe (PID: 6524)
Reads mouse settings
- Appointments.pif (PID: 2692)
- Appointments.pif (PID: 4600)
- Extras.pif (PID: 4656)
- Extras.pif (PID: 7156)
Reads the machine GUID from the registry
- Appointments.pif (PID: 2692)
- Appointments.pif (PID: 4600)
Checks proxy server information
- Appointments.pif (PID: 2692)
- Appointments.pif (PID: 4600)
- slui.exe (PID: 2748)
Reads the software policy settings
- Appointments.pif (PID: 2692)
- slui.exe (PID: 2748)
- Appointments.pif (PID: 4600)
Creates files or folders in the user directory
- Appointments.pif (PID: 2692)
- Extras.pif (PID: 4656)
- Appointments.pif (PID: 4600)
- Extras.pif (PID: 132)
Creates files in the program directory
- Appointments.pif (PID: 2692)
- Appointments.pif (PID: 4600)
Manual execution by a user
- AacAmbientLighting.exe (PID: 720)
- cmd.exe (PID: 3780)
- cmd.exe (PID: 2192)
- Extras.pif (PID: 132)
- Extras.pif (PID: 7016)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2012:02:24 19:19:54+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 10 |
| CodeSize: | 28160 |
| InitializedDataSize: | 446976 |
| UninitializedDataSize: | 16896 |
| EntryPoint: | 0x3883 |
| OSVersion: | 5 |
| ImageVersion: | 6 |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 6.6.0.8957 |
| ProductVersionNumber: | 33.2.1.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Dynamic link library |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
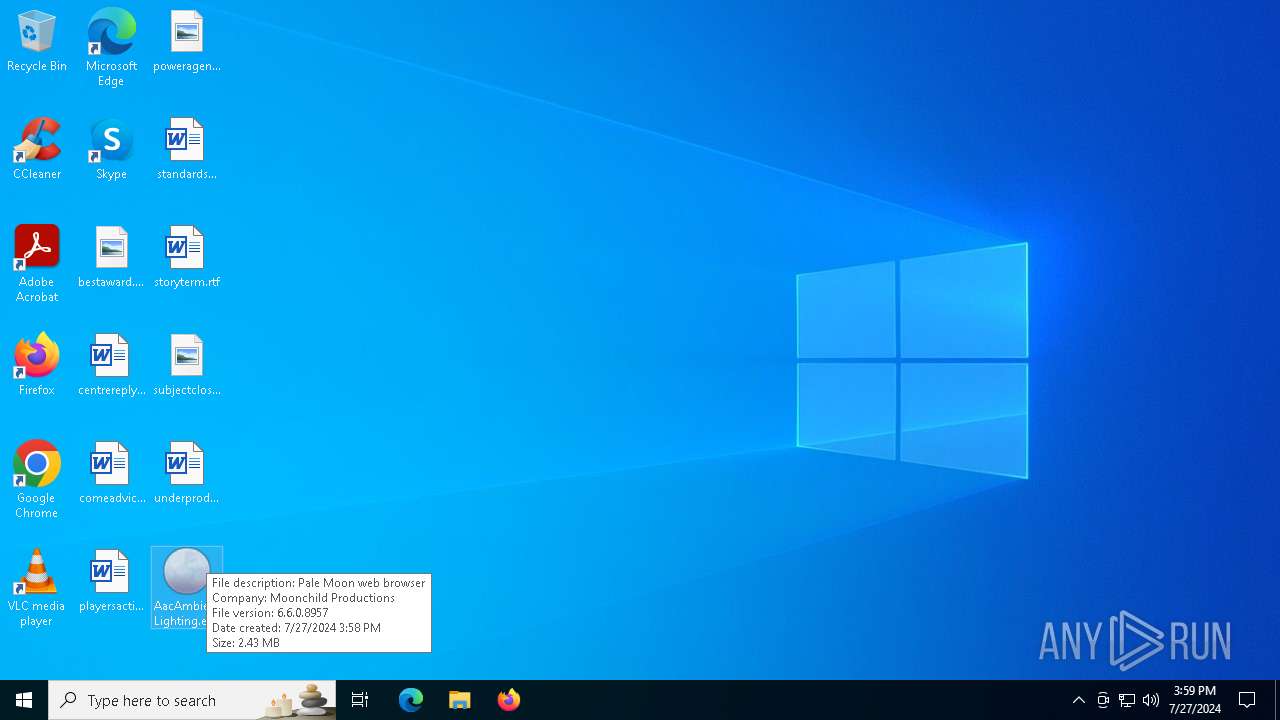
| LegalCopyright: | ©Pale Moon, Firefox and Mozilla Developers, available under the MPL 2.0. |
| CompanyName: | Moonchild Productions |
| FileDescription: | Pale Moon web browser |
| FileVersion: | 6.6.0 |
| ProductVersion: | 33.2.1 |
| InternalName: | Pale Moon |
| LegalTrademarks: | The Pale Moon logo and project names are trademarks of Moonchild Productions. |
| OriginalFileName: | palemoon.exe |
| ProductName: | Pale Moon |
| BuildID: | 20240710123718 |
Total processes
187
Monitored processes
55
Malicious processes
10
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 132 | C:\Users\admin\AppData\Local\Temp\649005\Extras.pif | C:\Users\admin\AppData\Local\Temp\649005\Extras.pif | — | explorer.exe | |||||||||||
User: admin Company: AutoIt Team Integrity Level: MEDIUM Description: AutoIt v3 Script Exit code: 0 Version: 3, 3, 14, 4 Modules
| |||||||||||||||
| 308 | timeout 5 | C:\Windows\SysWOW64\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: timeout - pauses command processing Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 504 | findstr /I "avastui.exe avgui.exe bdservicehost.exe nswscsvc.exe sophoshealth.exe" | C:\Windows\SysWOW64\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 644 | "C:\Windows\System32\cmd.exe" /k move Rm Rm.cmd & Rm.cmd & exit | C:\Windows\SysWOW64\cmd.exe | — | EovJmduARXsqIm.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 9009 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 720 | "C:\Users\admin\Desktop\AacAmbientLighting.exe" | C:\Users\admin\Desktop\AacAmbientLighting.exe | — | explorer.exe | |||||||||||
User: admin Company: Moonchild Productions Integrity Level: MEDIUM Description: Pale Moon web browser Exit code: 0 Version: 6.6.0 Modules
| |||||||||||||||
| 736 | tasklist | C:\Windows\SysWOW64\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1028 | timeout 5 | C:\Windows\SysWOW64\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: timeout - pauses command processing Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1264 | tasklist | C:\Windows\SysWOW64\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1292 | timeout 5 | C:\Windows\SysWOW64\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: timeout - pauses command processing Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1328 | cmd /c copy /b Applicant + Valve + Bin + Reaction + Preceding + Ties 801511\n | C:\Windows\SysWOW64\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
29 889
Read events
29 835
Write events
54
Delete events
0
Modification events
| (PID) Process: | (7032) AacAmbientLighting.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (7032) AacAmbientLighting.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (7032) AacAmbientLighting.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (7032) AacAmbientLighting.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2692) Appointments.pif | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2692) Appointments.pif | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2692) Appointments.pif | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2692) Appointments.pif | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2692) Appointments.pif | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2692) Appointments.pif | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
Executable files
12
Suspicious files
117
Text files
89
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7032 | AacAmbientLighting.exe | C:\Users\admin\AppData\Local\Temp\Cop | binary | |
MD5:8002B5DB58BDDA7AD73683F1DF7D6A6F | SHA256:286F88AE05BD8622DCDDE80705529340B28EEFE8546606CEA78CBD1C15E39EC9 | |||
| 7032 | AacAmbientLighting.exe | C:\Users\admin\AppData\Local\Temp\Achieved | gmc | |
MD5:00E956AF2FA4911317C8EA04F000DA3E | SHA256:8F36A1D535F2E1338D2DB47C96135E2F1ACFCB327060CD96D8C5DAB78AB7F558 | |||
| 7032 | AacAmbientLighting.exe | C:\Users\admin\AppData\Local\Temp\Naturally | binary | |
MD5:BD8099BB827B3048AACD0DCEBED8A034 | SHA256:540A2922103562BE8E359B0D532B82D8A65AB94AA513B274247B353C91176592 | |||
| 7032 | AacAmbientLighting.exe | C:\Users\admin\AppData\Local\Temp\Cancelled | text | |
MD5:C0B82387727F8BF4862DB5A5DCE59215 | SHA256:E9A47DDA2F440BC7FB029BC8C801C455D8F16AB95505A3D4F3BD7EBA919355D2 | |||
| 7032 | AacAmbientLighting.exe | C:\Users\admin\AppData\Local\Temp\Aged | binary | |
MD5:B042AB8A19036DB81E1EA7DAA6F30D08 | SHA256:7F9746E7DD60C643AF58A39CF8AD3BEAFAB424C58AACCE664B926215CDD839A4 | |||
| 7032 | AacAmbientLighting.exe | C:\Users\admin\AppData\Local\Temp\Upon | abr | |
MD5:4BBC3585B0E37BF75403CEC60A17DEC0 | SHA256:B63FA5BDEFDAA0919E49BA4B23834A0DA5625025C58D6A8AAA5D6AC3FF2B0032 | |||
| 7032 | AacAmbientLighting.exe | C:\Users\admin\AppData\Local\Temp\Flavor | binary | |
MD5:7613B1E338FAD672482240461F021DA7 | SHA256:AC450B3CF524A758B78079D85AE03EFCF8E049AD7BD38FDD847F46EE2BDF289A | |||
| 7032 | AacAmbientLighting.exe | C:\Users\admin\AppData\Local\Temp\Villa | binary | |
MD5:BE12291F76AA73EF666C64FDCA6774C2 | SHA256:1BA57420DDC56E09E2CAC154D39CE17EDF1A58ACBE39BE11183E51D7CDC27491 | |||
| 7032 | AacAmbientLighting.exe | C:\Users\admin\AppData\Local\Temp\Grown | abr | |
MD5:A0C469D49827B1F728DDB5178BDC4FA6 | SHA256:A3CA84D5BDB94F34CE7FF1E6BF38155A7790633AAF301564F6FC178816F1E29F | |||
| 7032 | AacAmbientLighting.exe | C:\Users\admin\AppData\Local\Temp\Ties | ini | |
MD5:F3C4A22F12FE13CCAA211DDB1FE1114B | SHA256:AD6A515649D98FFFECC2E712368E6C0007ED4721C8AB40B58DE3853A77DC3E6D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
25
DNS requests
14
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | POST | 200 | 104.208.16.92:443 | https://self.events.data.microsoft.com/OneCollector/1.0/ | unknown | binary | 9 b | unknown |
— | — | GET | 200 | 188.114.97.9:443 | https://t2rl.pwarticles.pro/scar/Runtie.exe | unknown | executable | 5.45 Mb | unknown |
— | — | GET | 200 | 188.114.96.9:443 | https://t2rl.pwarticles.pro/scar/data.rar | unknown | compressed | 9.69 Mb | unknown |
— | — | GET | 200 | 13.107.246.45:443 | https://fp-afd-nocache-ccp.azureedge.net/apc/trans.gif?5d4a2dcba33e699653c21a0699ed0e8d | unknown | image | 43 b | unknown |
— | — | POST | 204 | 92.123.104.63:443 | https://www.bing.com/threshold/xls.aspx | unknown | — | — | unknown |
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | unknown |
— | — | GET | 200 | 91.108.107.41:443 | https://officialdomain345.online/stub/UnRAR.dll | unknown | executable | 304 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1180 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4820 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6012 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4128 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 92.123.104.52:443 | — | Akamai International B.V. | DE | unknown |
— | — | 131.253.33.254:443 | a-ring-fallback.msedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
— | — | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3952 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
AMpBwvvBIuHNOTwNi.AMpBwvvBIuHNOTwNi |
| unknown |
self.events.data.microsoft.com |
| whitelisted |
officialdomain345.online |
| unknown |
t2rl.pwarticles.pro |
| unknown |
zWjfqxpNSYvLaHiQsqX.zWjfqxpNSYvLaHiQsqX |
| unknown |
a-ring-fallback.msedge.net |
| unknown |
fp-afd-nocache-ccp.azureedge.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
— | — | A Network Trojan was detected | ET MALWARE Possible Windows executable sent when remote host claims to send a Text File |
— | — | A Network Trojan was detected | ET MALWARE Likely Evil EXE download from MSXMLHTTP non-exe extension M2 |
— | — | A Network Trojan was detected | ET HUNTING SUSPICIOUS Firesale gTLD EXE DL with no Referer June 13 2016 |
1 ETPRO signatures available at the full report