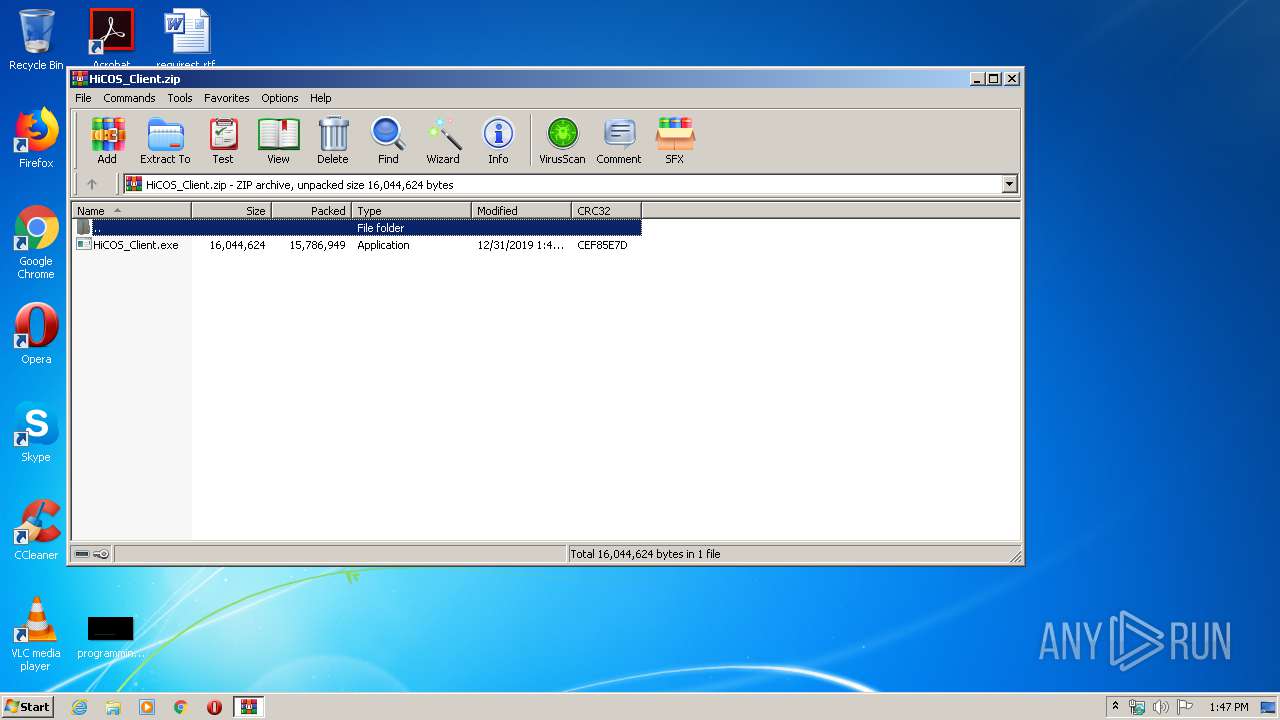
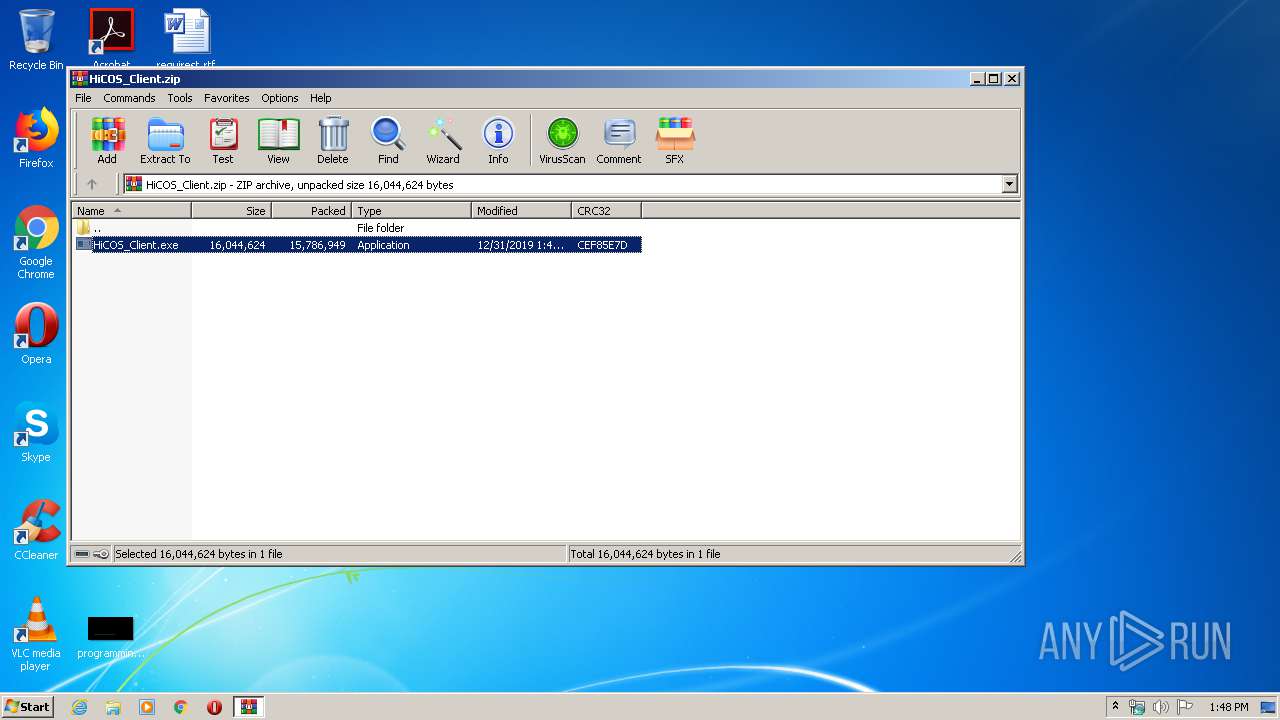
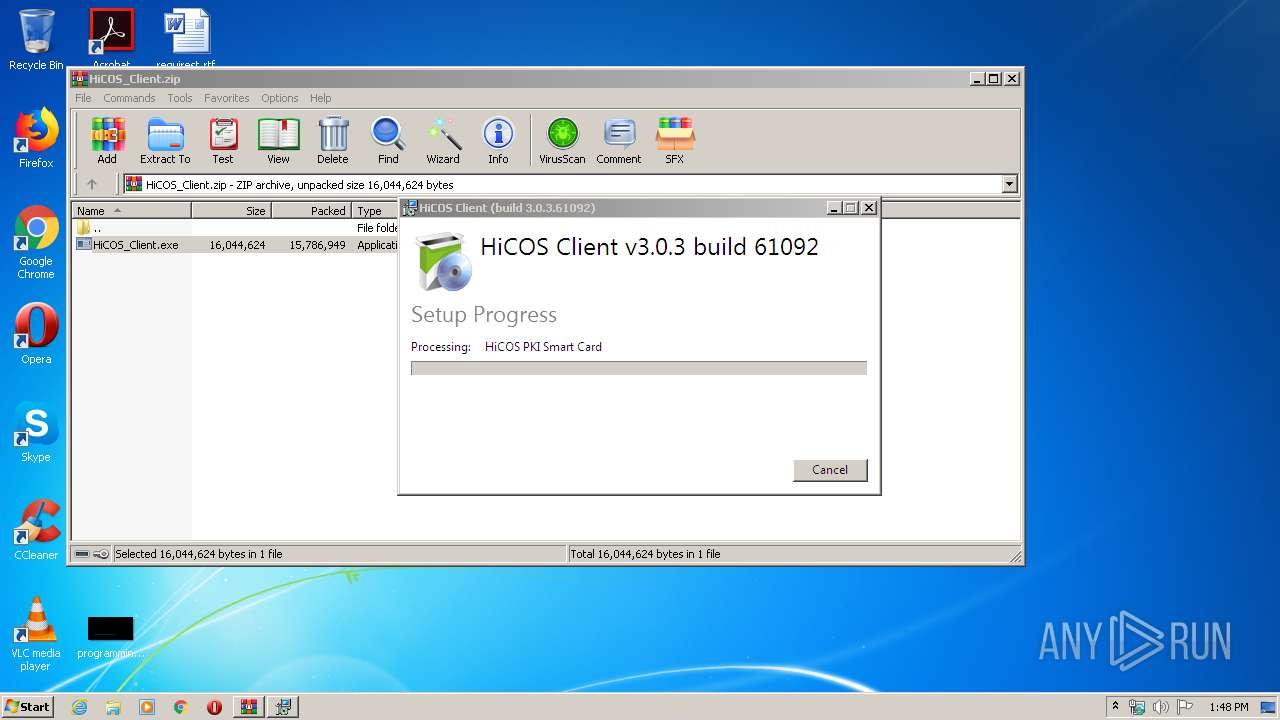
| File name: | HiCOS_Client.zip |
| Full analysis: | https://app.any.run/tasks/be4394d1-849e-4c25-9943-c587877b8664 |
| Verdict: | Malicious activity |
| Analysis date: | April 14, 2020, 12:47:28 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | B8CA4A7408B9FECA26D77DC470D3201C |
| SHA1: | 2B6512D62E92C9B613A69F23642B7D8A2C3BF699 |
| SHA256: | F43FA28C2FBEE4379DFEC1E36CF604DCFEB8330F797D8B5B08DE95A29B40DB1A |
| SSDEEP: | 393216:iTx9MYqeymyA7+RVg2HLt9MCSPAFeTDwOkyxDJySxcS:6x9Fq1mytRq6Lt+PaMDwXgs47 |
MALICIOUS
Loads dropped or rewritten executable
- HiCOS_Client.exe (PID: 1604)
- HiCOS_Client.exe (PID: 3692)
Application was dropped or rewritten from another process
- HiCOS_Client.exe (PID: 1604)
- HiCOS_Client.exe (PID: 2836)
- HiCOS_Client.exe (PID: 2572)
- HiCOS_Client.exe (PID: 3112)
- HiCOS_Client.exe (PID: 3692)
- HiCOS_Client.exe (PID: 2368)
Changes the autorun value in the registry
- HiCOS_Client.exe (PID: 2572)
SUSPICIOUS
Starts itself from another location
- HiCOS_Client.exe (PID: 1604)
- HiCOS_Client.exe (PID: 3112)
- HiCOS_Client.exe (PID: 3692)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2104)
- HiCOS_Client.exe (PID: 2836)
- HiCOS_Client.exe (PID: 1604)
- HiCOS_Client.exe (PID: 3112)
- HiCOS_Client.exe (PID: 2572)
- HiCOS_Client.exe (PID: 3692)
Executed as Windows Service
- vssvc.exe (PID: 2668)
Searches for installed software
- HiCOS_Client.exe (PID: 2572)
- HiCOS_Client.exe (PID: 2368)
Creates files in the program directory
- HiCOS_Client.exe (PID: 2572)
Creates a software uninstall entry
- HiCOS_Client.exe (PID: 2572)
INFO
Low-level read access rights to disk partition
- vssvc.exe (PID: 2668)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2019:12:31 09:41:06 |
| ZipCRC: | 0xcef85e7d |
| ZipCompressedSize: | 15786949 |
| ZipUncompressedSize: | 16044624 |
| ZipFileName: | HiCOS_Client.exe |
Total processes
46
Monitored processes
8
Malicious processes
5
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
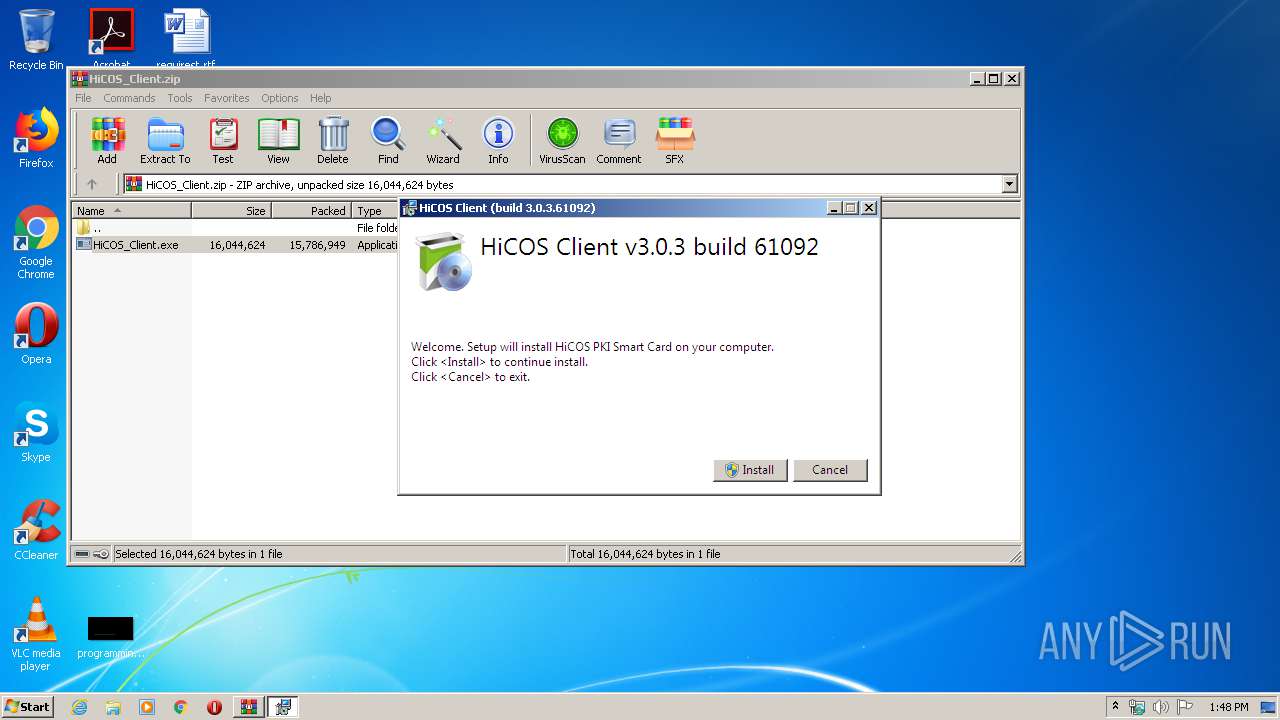
| 1604 | "C:\Users\admin\AppData\Local\Temp\{23493D56-EE2D-4E7F-9F9B-73E545EA4057}\.cr\HiCOS_Client.exe" -burn.clean.room="C:\Users\admin\AppData\Local\Temp\Rar$EXa2104.32574\HiCOS_Client.exe" -burn.filehandle.attached=148 -burn.filehandle.self=156 | C:\Users\admin\AppData\Local\Temp\{23493D56-EE2D-4E7F-9F9B-73E545EA4057}\.cr\HiCOS_Client.exe | HiCOS_Client.exe | ||||||||||||
User: admin Company: Chunghwa Telecom Integrity Level: MEDIUM Description: HiCOS PKI Smart Card Exit code: 0 Version: 3.0.3.61092 Modules
| |||||||||||||||
| 2104 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\HiCOS_Client.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2368 | "C:\Users\admin\AppData\Local\Temp\{D9F3D60B-618F-4777-936E-E6A0AEE8EBA6}\.be\HiCOS_Client.exe" -q -burn.elevated BurnPipe.{4EE9FCCE-E5D2-4779-B1D1-E5DD5AC55798} {85F93B0E-55A9-4B89-A264-86583D57954E} 3692 | C:\Users\admin\AppData\Local\Temp\{D9F3D60B-618F-4777-936E-E6A0AEE8EBA6}\.be\HiCOS_Client.exe | — | HiCOS_Client.exe | |||||||||||
User: admin Company: Chunghwa Telecom Integrity Level: HIGH Description: HiCOS PKI Smart Card Exit code: 0 Version: 3.0.3.40716 Modules
| |||||||||||||||
| 2572 | "C:\Users\admin\AppData\Local\Temp\{3185CEBA-5DFD-4FBD-B620-310A517BC9EA}\.be\HiCOS_Client.exe" -q -burn.elevated BurnPipe.{9DAF0BC3-8E98-4C46-9BA5-43B4C6672416} {6E15EE34-E353-4FB1-B58F-FABAD22570D4} 1604 | C:\Users\admin\AppData\Local\Temp\{3185CEBA-5DFD-4FBD-B620-310A517BC9EA}\.be\HiCOS_Client.exe | HiCOS_Client.exe | ||||||||||||
User: admin Company: Chunghwa Telecom Integrity Level: HIGH Description: HiCOS PKI Smart Card Exit code: 0 Version: 3.0.3.61092 Modules
| |||||||||||||||
| 2668 | C:\Windows\system32\vssvc.exe | C:\Windows\system32\vssvc.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2836 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2104.32574\HiCOS_Client.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2104.32574\HiCOS_Client.exe | WinRAR.exe | ||||||||||||
User: admin Company: Chunghwa Telecom Integrity Level: MEDIUM Description: HiCOS PKI Smart Card Exit code: 0 Version: 3.0.3.61092 Modules
| |||||||||||||||
| 3112 | "C:\ProgramData\Package Cache\B93A21009F4149B82073F4A2AB35FF7113FC31DF\HiCOS_Client.exe" /uninstall /norestart /quiet | C:\ProgramData\Package Cache\B93A21009F4149B82073F4A2AB35FF7113FC31DF\HiCOS_Client.exe | HiCOS_Client.exe | ||||||||||||
User: admin Company: Chunghwa Telecom Integrity Level: HIGH Description: HiCOS PKI Smart Card Exit code: 0 Version: 3.0.3.40716 Modules
| |||||||||||||||
| 3692 | "C:\Users\admin\AppData\Local\Temp\{D293BC13-DA98-439D-8DBC-0668F19B0B14}\.cr\HiCOS_Client.exe" -burn.clean.room="C:\ProgramData\Package Cache\B93A21009F4149B82073F4A2AB35FF7113FC31DF\HiCOS_Client.exe" -burn.filehandle.attached=148 -burn.filehandle.self=156 /uninstall /norestart /quiet | C:\Users\admin\AppData\Local\Temp\{D293BC13-DA98-439D-8DBC-0668F19B0B14}\.cr\HiCOS_Client.exe | HiCOS_Client.exe | ||||||||||||
User: admin Company: Chunghwa Telecom Integrity Level: HIGH Description: HiCOS PKI Smart Card Exit code: 0 Version: 3.0.3.40716 Modules
| |||||||||||||||
Total events
1 501
Read events
1 301
Write events
200
Delete events
0
Modification events
| (PID) Process: | (2104) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2104) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2104) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2104) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\HiCOS_Client.zip | |||
| (PID) Process: | (2104) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2104) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2104) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2104) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2104) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2104) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
16
Suspicious files
2
Text files
12
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2572 | HiCOS_Client.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 2572 | HiCOS_Client.exe | C:\ProgramData\Package Cache\.unverified\HiCOS_Client.exe | — | |
MD5:— | SHA256:— | |||
| 1604 | HiCOS_Client.exe | C:\Users\admin\AppData\Local\Temp\{3185CEBA-5DFD-4FBD-B620-310A517BC9EA}\.ba\thm.xml | xml | |
MD5:— | SHA256:— | |||
| 2104 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2104.32574\HiCOS_Client.exe | executable | |
MD5:— | SHA256:— | |||
| 2836 | HiCOS_Client.exe | C:\Users\admin\AppData\Local\Temp\{23493D56-EE2D-4E7F-9F9B-73E545EA4057}\.cr\HiCOS_Client.exe | executable | |
MD5:— | SHA256:— | |||
| 1604 | HiCOS_Client.exe | C:\Users\admin\AppData\Local\Temp\{3185CEBA-5DFD-4FBD-B620-310A517BC9EA}\.ba\1033\thm.wxl | xml | |
MD5:— | SHA256:— | |||
| 1604 | HiCOS_Client.exe | C:\Users\admin\AppData\Local\Temp\{3185CEBA-5DFD-4FBD-B620-310A517BC9EA}\.ba\1028\thm.wxl | xml | |
MD5:— | SHA256:— | |||
| 1604 | HiCOS_Client.exe | C:\Users\admin\AppData\Local\Temp\{3185CEBA-5DFD-4FBD-B620-310A517BC9EA}\.ba\logo.png | image | |
MD5:28A07E19BF975467C019A2C3E9EA42EB | SHA256:BE59D01C996B92ECC886034DA74C38F7C2E6C6416EF3494520E2EDC4EF1705E9 | |||
| 1604 | HiCOS_Client.exe | C:\Users\admin\AppData\Local\Temp\{3185CEBA-5DFD-4FBD-B620-310A517BC9EA}\.ba\thm.wxl | xml | |
MD5:702E8B2C2D030B875C174F5054144396 | SHA256:73C7D5B719CBB1C15EBB1DB3B81BB0F18B0E60B136ACD4DBA23A0BDBE7A8D1D9 | |||
| 1604 | HiCOS_Client.exe | C:\Users\admin\AppData\Local\Temp\{3185CEBA-5DFD-4FBD-B620-310A517BC9EA}\HiCOS_Client.exe | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report