| File name: | build.exe |
| Full analysis: | https://app.any.run/tasks/9658f5ec-7347-4a53-a301-d68dfd6b692a |
| Verdict: | Malicious activity |
| Analysis date: | April 01, 2023, 01:31:34 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | 4D6FEEEACCFFCA24FCBEA6E39030DA3D |
| SHA1: | 62EEAC2D18404B15EC08AB48CDB168C8394398D5 |
| SHA256: | F41BB77A5E52B6D462542042739F7371404559DDC3FEC6A39739EB0131BBC7ED |
| SSDEEP: | 24576:G03i2Q9NXw2/wPOjdGxYqfw+Jwz/S/6RZs8nVW6k5JHkARt7DBAqn3:lSTq24GjdGSgw+W7SCRnVQTEQ/BA8 |
MALICIOUS
BLACKGUARD detected by memory dumps
- build.exe (PID: 2512)
Stealerium is detected
- build.exe (PID: 2512)
Steals credentials from Web Browsers
- build.exe (PID: 2512)
Actions looks like stealing of personal data
- build.exe (PID: 2512)
SUSPICIOUS
Reads the Internet Settings
- build.exe (PID: 2512)
Checks for external IP
- build.exe (PID: 2512)
Reads settings of System Certificates
- build.exe (PID: 2512)
Starts CMD.EXE for commands execution
- build.exe (PID: 2512)
Accesses Microsoft Outlook profiles
- build.exe (PID: 2512)
Starts application with an unusual extension
- cmd.exe (PID: 4056)
- cmd.exe (PID: 3104)
Uses NETSH.EXE to obtain data on the network
- cmd.exe (PID: 4056)
- cmd.exe (PID: 3104)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 4056)
Reads browser cookies
- build.exe (PID: 2512)
Loads DLL from Mozilla Firefox
- build.exe (PID: 2512)
INFO
Reads the computer name
- build.exe (PID: 2512)
Checks supported languages
- build.exe (PID: 2512)
- chcp.com (PID: 1868)
- chcp.com (PID: 3564)
The process checks LSA protection
- build.exe (PID: 2512)
- netsh.exe (PID: 2868)
- msiexec.exe (PID: 2776)
- netsh.exe (PID: 3600)
Reads the machine GUID from the registry
- build.exe (PID: 2512)
Reads Environment values
- build.exe (PID: 2512)
[YARA] WLAN manipulation strings were found
- build.exe (PID: 2512)
Create files in a temporary directory
- build.exe (PID: 2512)
Creates files or folders in the user directory
- build.exe (PID: 2512)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
BlackGuard
(PID) Process(2512) build.exe
C2 (1)https://{server}.gofile.io
Strings (704)LPOI94VFP3XBYJXSOT7A
ENCRYPTED:fleaTKsR0trQiaWh0H+vOvHR4WDn0LEpdxH+edudpJHMS6La1exY+RGGMe+dD0s4w6O2H6Vy+Byk9vPVPyauOqgEeVBlRm4qQM9Ja4WyzXEHz5RYlql8JxZ6BIhu5B+1YYhviWheu50yYYzovyxu22vFISy/Gs3hzHpWeRGmmgk=
facebook
twitter
chat
telegram
skype
discord
viber
message
gmail
protonmail
outlook
password
encryption
account
login
sign in
bank
credit
card
shop
sell
qiwi
money
paypal
bitcoin
monero
dashcoin
litecoin
etherium
stellarcoin
blockchain
paxful
investopedia
buybitcoinworldwide
cryptocurrency
crypto
trade
trading
wallet
coinomi
coinbase
porn
hentai
chaturbate
vk.com
ok.ru
instagram
whatsapp
linkedin
reddit
flickr
youtube
pinterest
tiktok
Document
docx
xlsx
pptx
indd
json
DataBase
kdbx
sqlite
SourceCode
html
swift
java
Image
jpeg
{"type": 1
username
avatar_url
content
?wait=true
/messages/
PATCH
logs
yyyy-MM-dd_h.mm.ss
.zip
({0})
({0} - MAX)
🏦 *Banking services*
💰 *Cryptocurrency services*
🎨 *Social networks*
🍓 *Porn websites*
🔑 Passwords
💳 CreditCards
🍪 Cookies
📂 AutoFill
⏳ History
🔖 Bookmarks
📦 Downloads
💰 Wallet Extensions
💰 Wallets
📡 FTP hosts
🔌 VPN accounts
🦢 Pidgin accounts
📫 Outlook accounts
✈️ Telegram sessions
☁️ Skype session
👾 Discord token
💬 Element session
💭 Signal session
🔓 Tox session
🎮 Steam session
🎮 Uplay session
🎮 BattleNET session
🗝 Windows product key
🛰 Wifi networks
📸 Webcam screenshot
🌃 Desktop screenshot
✅ Startup installed
⛔️ Startup disabled
✅ Clipper installed
⛔️ Clipper not installed
✅ Keylogger installed
⛔️ Keylogger not installed
📂 Images
📂 Documents
📂 Database files
📂 Source code files
"```
Sending passwords archive to Gofile
Sending report to discord
Report sent to discord
msgid.dat
history.dat
Starting keylogger modules...
Starting clipper modules...
www.
google
bing
yandex
duckduckgo
.com
.org
Unknown
Amex Card
^3[47][0-9]{13}$
BCGlobal
^(6541|6556)[0-9]{12}$
Carte Blanche Card
^389[0-9]{11}$
Diners Club Card
^3(?:0[0-5]|[68][0-9])[0-9]{11}$
Discover Card
6(?:011|5[0-9]{2})[0-9]{12}$
Insta Payment Card
^63[7-9][0-9]{13}$
JCB Card
^(?:2131|1800|35\\d{3})\\d{11}$
KoreanLocalCard
^9[0-9]{15}$
Laser Card
^(6304|6706|6709|6771)[0-9]{12,15}$
Maestro Card
^(5018|5020|5038|6304|6759|6761|6763)[0-9]{8,15}$
Mastercard
5[1-5][0-9]{14}$
Solo Card
^(6334|6767)[0-9]{12}|(6334|6767)[0-9]{14}|(6334|6767)[0-9]{15}$
Switch Card
^(4903|4905|4911|4936|6333|6759)[0-9]{12}|(4903|4905|4911|4936|6333|6759)[0-9]{14}|(4903|4905|4911|4936|6333|6759)[0-9]{15}|564182[0-9]{10}|564182[0-9]{12}|564182[0-9]{13}|633110[0-9]{10}|633110[0-9]{12}|633110[0-9]{13}$
Union Pay Card
^(62[0-9]{14,17})$
Visa Card
4[0-9]{12}(?:[0-9]{3})?$
Visa Master Card
^(?:4[0-9]{12}(?:[0-9]{3})?|5[1-5][0-9]{14})$
Express Card
3[47][0-9]{13}$
\FileZilla\
recentservers.xml
sitemanager.xml
Server
Pass
ftp://
Host
Port
Rǫ
Url:
\Hosts.txt
Running passwords recovery...
Stealer >> Failed recursive remove directory with passwords
Software
strDataDir
\wallets
Zcash
\Zcash
Armory
\Armory
Bytecoin
\bytecoin
Jaxx
\com.liberty.jaxx\IndexedDB\file__0.indexeddb.leveldb
Exodus
\Exodus\exodus.wallet
Ethereum
\Ethereum\keystore
Electrum
\Electrum\wallets
AtomicWallet
\atomic\Local Storage\leveldb
Guarda
\Guarda\Local Storage\leveldb
Coinomi
\Coinomi\Coinomi\wallets
Litecoin
Dash
Bitcoin
NordVPN
NordVpn.exe*
user.config
//setting[@name='Username']/value
//setting[@name='Password']/value
\accounts.txt
Username:
OpenVPN Connect\profiles
\profiles
ovpn
profiles\
ProtonVPN
ProtonVPN.exe
\user.config
\Windows.txt
NAME:
Directory not exists
DRIVE-
.txt
Downloads
USERPROFILE
Dropbox
OneDrive
desktop.ini
Grabber
DropBox
SELECT * FROM Win32_Product
Name
Version
InstallDate
dd/MM/yyyy HH:mm:ss
IdentifyingNumber
\Apps.txt
BCDFGHJKMPQRTVWXY2346789
SOFTWARE\Microsoft\Windows NT\CurrentVersion
DigitalProductId
Failed to get DigitalProductId from registry
SELECT * FROM Win32_PnPEntity WHERE (PNPClass = 'Image' OR PNPClass = 'Camera')
GetConnectedCamerasCount : Query failed
WebcamScreenshot : Camera screenshot failed. (Count {0})
WebCap
\Webcam.jpg
/C chcp 65001 && netsh wlan show profile | findstr All
/C chcp 65001 && netsh wlan show profile name="
" key=clear | findstr Key
/C chcp 65001 && netsh wlan show networks mode=bssid
is not running
\ScanningNetworks.txt
65001
PROFILE:
\SavedNetworks.txt
\Process.txt
SELECT ExecutablePath, ProcessID FROM Win32_Process
ProcessID
ExecutablePath
\Desktop.jpg
Unknown System
root\CIMV2
SELECT * FROM win32_operatingsystem
HARDWARE\Description\System\CentralProcessor\0
Identifier
(64 Bit)
(32 Bit)
(Unknown)
\root\SecurityCenter2
Select * from AntivirusProduct
displayName
Not installed
No network adapters with an IPv4 address in the system!
Request failed
unknown
Failed
BSSID:
{"result":200
"lat":
"lon":
"range":
SELECT * FROM Win32_Processor
SELECT * FROM Win32_VideoController
Select * From Win32_ComputerSystem
TotalPhysicalMemory
yyyy-MM-dd h:mm:ss tt
\tokens.txt
Authorization
Unauthorized
Token is valid
Token is invalid
Connection error
[a-zA-Z0-9]{24}\.[a-zA-Z0-9]{6}\.[a-zA-Z0-9_\-]{27}|mfa\.[a-zA-Z0-9_\-]{84}
Discord\Local Storage\leveldb
Discord PTB\Local Storage\leveldb
Discord Canary\leveldb
.log
.ldb
leveldb
\leveldb
Element\Local Storage
databases
Session Storage
Local Storage
\databases
\Session Storage
\Local Storage
\sql
\config.json
Signal
Software\Microsoft\Office\15.0\Outlook\Profiles\Outlook\9375CFF0413111d3B88A00104B2A6676
Software\Microsoft\Office\16.0\Outlook\Profiles\Outlook\9375CFF0413111d3B88A00104B2A6676
Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\9375CFF0413111d3B88A00104B2A6676
Software\Microsoft\Windows Messaging Subsystem\Profiles\9375CFF0413111d3B88A00104B2A6676
SMTP Email Address
SMTP Server
POP3 Server
POP3 User Name
SMTP User Name
NNTP Email Address
NNTP User Name
NNTP Server
IMAP Server
IMAP User Name
Email
HTTP User
HTTP Server URL
POP3 User
IMAP User
HTTPMail User Name
HTTPMail Server
SMTP User
POP3 Password2
IMAP Password2
NNTP Password2
HTTPMail Password2
SMTP Password2
POP3 Password
IMAP Password
NNTP Password
HTTPMail Password
SMTP Password
\Outlook.txt
Password
null
^([a-zA-Z0-9_\-\.]+)@([a-zA-Z0-9_\-\.]+)\.([a-zA-Z]{2,5})$
^(?!:\/\/)([a-zA-Z0-9-_]+\.)*[a-zA-Z0-9][a-zA-Z0-9-_]+\.[a-zA-Z]{2,11}?$
\chatlogs
accounts.xml
Protocol:
Password:
.purple
0001
\0001
Microsoft\Skype for Desktop
\Telegram Desktop\tdata
Telegram
tdata
usertag
settings
key_data
BattleNET >> Session not found
*.db
*.config
Battle.net
versions
bytes
\versions.txt
VERSION:
mods
\mods.txt
MOD:
screenshots
\screenshots
\screenshots\
profile
options
servers
.minecraft
Software\Valve\Steam
Steam >> Application path not found in registry
SteamPath
Steam >> Application directory not found
Apps
Apps\
Installed
Running
Updating
Application
\ssnf
ssfn
\ssnf\
config
\configs
\configs\
RememberPassword
Autologin User:
AutoLoginUser
\SteamInfo.txt
Uplay >> Session not found
Ubisoft Game Launcher
Hostname:
Type:
###
### (
\Profiles
\places.sqlite
moz_bookmarks
\cookies.sqlite
moz_cookies
\mozglue.dll
\nss3.dll
NSS_Init
PK11SDR_Decrypt
NSS_Shutdown
\Bookmarks.txt
\Cookies.txt
\History.txt
\Passwords.txt
\Profiles\
moz_places
logins.json
key3.db
key4.db
\logins.json
,"logins":\[
,"potentiallyVulnerablePasswords"
Program Files\Mozilla Firefox
Users\Public
cert9.db
"hostname":"([^"]+)"
"encryptedUsername":"([^"]+)"
"encryptedPassword":"([^"]+)"
autofill
"bookmark_bar": {
"other": {
"name": "
"type": "url",
"url": "http
Failed to parse url
credit_cards
\Edge
\Login Data
\Web Data
\Bookmarks
\Cookies
\History
\CreditCards.txt
\AutoFill.txt
Edge_Auvitas
\Microsoft\Edge\User Data\Default\Local Extension Settings\klfhbdnlcfcaccoakhceodhldjojboga
Edge_Math
\Microsoft\Edge\User Data\Default\Local Extension Settings\dfeccadlilpndjjohbjdblepmjeahlmm
Edge_Metamask
\Microsoft\Edge\User Data\Default\Local Extension Settings\ejbalbakoplchlghecdalmeeeajnimhm
Edge_MTV
\Microsoft\Edge\User Data\Default\Local Extension Settings\oooiblbdpdlecigodndinbpfopomaegl
Edge_Rabet
\Microsoft\Edge\User Data\Default\Local Extension Settings\aanjhgiamnacdfnlfnmgehjikagdbafd
Edge_Ronin
\Microsoft\Edge\User Data\Default\Local Extension Settings\bblmcdckkhkhfhhpfcchlpalebmonecp
Edge_Yoroi
\Microsoft\Edge\User Data\Default\Local Extension Settings\akoiaibnepcedcplijmiamnaigbepmcb
Edge_Zilpay
\Microsoft\Edge\User Data\Default\Local Extension Settings\fbekallmnjoeggkefjkbebpineneilec
Edge_Exodus
\Microsoft\Edge\User Data\Default\Local Extension Settings\jdiccldimpdaibmpdkjnbmckianbfold
Edge_Terra_Station
\Microsoft\Edge\User Data\Default\Local Extension Settings\ajkhoeiiokighlmdnlakpjfoobnjinie
Edge_Jaxx
\Microsoft\Edge\User Data\Default\Local Extension Settings\dmdimapfghaakeibppbfeokhgoikeoci
BCrypt.BCryptDecrypt() (get size) failed with status code: {0}
BCrypt.BCryptDecrypt(): authentication tag mismatch
BCrypt.BCryptDecrypt() failed with status code:{0}
BCrypt.BCryptOpenAlgorithmProvider() failed with status code:{0}
BCrypt.BCryptSetAlgorithmProperty(BCrypt.BCRYPT_CHAINING_MODE, BCrypt.BCRYPT_CHAIN_MODE_GCM) failed with status code:{0}
BCrypt.BCryptImportKey() failed with status code:{0}
BCrypt.BCryptGetProperty() (get size) failed with status code:{0}
BCrypt.BCryptGetProperty() failed with status code:{0}
ObjectLength
ChainingModeGCM
AuthTagLength
ChainingMode
KeyDataBlob
Microsoft Primitive Provider
"name
": "
Opera
\Opera Stable\Local State
\Local State
"encrypted_key":"(.*?)"
Opera Software
\Downloads.txt
cookies
downloads
Chrome_Binance
\Google\Chrome\User Data\Default\Local Extension Settings\fhbohimaelbohpjbbldcngcnapndodjp
Chrome_Bitapp
\Google\Chrome\User Data\Default\Local Extension Settings\fihkakfobkmkjojpchpfgcmhfjnmnfpi
Chrome_Coin98
\Google\Chrome\User Data\Default\Local Extension Settings\aeachknmefphepccionboohckonoeemg
Chrome_Equal
\Google\Chrome\User Data\Default\Local Extension Settings\blnieiiffboillknjnepogjhkgnoapac
Chrome_Guild
\Google\Chrome\User Data\Default\Local Extension Settings\nanjmdknhkinifnkgdcggcfnhdaammmj
Chrome_Iconex
\Google\Chrome\User Data\Default\Local Extension Settings\flpiciilemghbmfalicajoolhkkenfel
Chrome_Math
\Google\Chrome\User Data\Default\Local Extension Settings\afbcbjpbpfadlkmhmclhkeeodmamcflc
Chrome_Mobox
\Google\Chrome\User Data\Default\Local Extension Settings\fcckkdbjnoikooededlapcalpionmalo
Chrome_Phantom
\Google\Chrome\User Data\Default\Local Extension Settings\bfnaelmomeimhlpmgjnjophhpkkoljpa
Chrome_Tron
\Google\Chrome\User Data\Default\Local Extension Settings\ibnejdfjmmkpcnlpebklmnkoeoihofec
Chrome_XinPay
\Google\Chrome\User Data\Default\Local Extension Settings\bocpokimicclpaiekenaeelehdjllofo
Chrome_Ton
\Google\Chrome\User Data\Default\Local Extension Settings\nphplpgoakhhjchkkhmiggakijnkhfnd
Chrome_Metamask
\Google\Chrome\User Data\Default\Local Extension Settings\nkbihfbeogaeaoehlefnkodbefgpgknn
Chrome_Sollet
\Google\Chrome\User Data\Default\Local Extension Settings\fhmfendgdocmcbmfikdcogofphimnkno
Chrome_Slope
\Google\Chrome\User Data\Default\Local Extension Settings\pocmplpaccanhmnllbbkpgfliimjljgo
Chrome_Starcoin
\Google\Chrome\User Data\Default\Local Extension Settings\mfhbebgoclkghebffdldpobeajmbecfk
Chrome_Swash
\Google\Chrome\User Data\Default\Local Extension Settings\cmndjbecilbocjfkibfbifhngkdmjgog
Chrome_Finnie
\Google\Chrome\User Data\Default\Local Extension Settings\cjmkndjhnagcfbpiemnkdpomccnjblmj
Chrome_Keplr
\Google\Chrome\User Data\Default\Local Extension Settings\dmkamcknogkgcdfhhbddcghachkejeap
Chrome_Crocobit
\Google\Chrome\User Data\Default\Local Extension Settings\pnlfjmlcjdjgkddecgincndfgegkecke
Chrome_Oxygen
\Google\Chrome\User Data\Default\Local Extension Settings\fhilaheimglignddkjgofkcbgekhenbh
Chrome_Nifty
\Google\Chrome\User Data\Default\Local Extension Settings\jbdaocneiiinmjbjlgalhcelgbejmnid
Chrome_Liquality
\Google\Chrome\User Data\Default\Local Extension Settings\kpfopkelmapcoipemfendmdcghnegimn
urls
logins
hh.mm.ss
logs\keylogger\
yyyy-MM-dd
Space
Return
Escape
LControlKey
RControlKey
RShiftKey
LShiftKey
Back
LWin
Capital
[ENTER]
[ESC]
[CTRL]
[Shift]
[Back]
[WIN]
[Tab]
[CAPSLOCK: ON]
[CAPSLOCK: OFF]
logs\nsfw\
true
processhacker
netstat
netmon
tcpview
wireshark
filemon
regmon
cain
SbieDll
snxhk
cmdvrt32
Select * from Win32_ComputerSystem
Manufacturer
microsoft corporation
Model
VIRTUAL
vmware
VirtualBox
VMware
AntiAnalysis : Hosting detected!
AntiAnalysis : Process detected!
AntiAnalysis : Virtual machine detected!
AntiAnalysis : SandBox detected!
AntiAnalysis : Debugger detected!
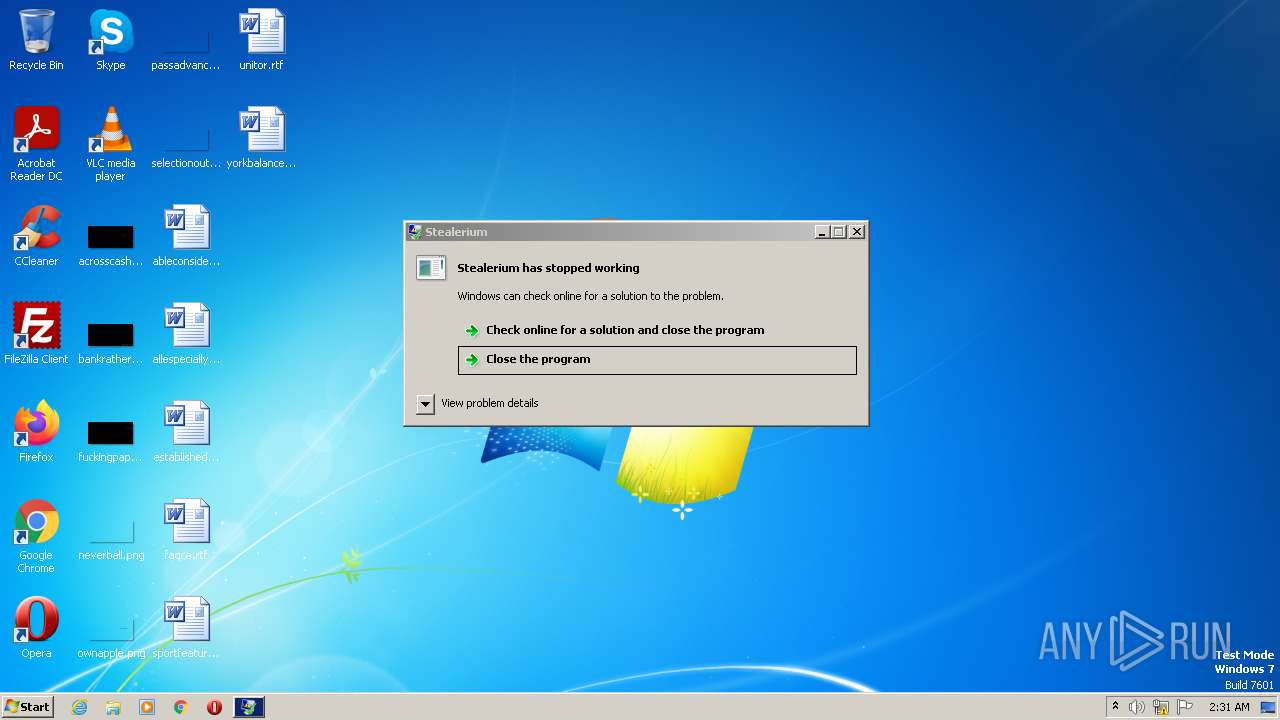
Sending fake error message box with code:
Exit code
Runtime error
.dll
.bat
chcp 65001
TaskKill /F /IM
Timeout /T 2 /Nobreak
SelfDestruct : Running self destruct procedure...
cmd.exe
StartDelay : Sleeping
SetFileCreationDate : Changing file
creation data
HideFile : Adding 'hidden' attribute to file
Startup : Adding to autorun...
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
ENCRYPTED:
{server}
uploadFile
downloadPage
apiv2
getServer
FileService status returned a
value.
(No data)
Banking services
Cryptocurrency services
Social networks
Porn websites
Archive
compression completed
Stealerium-Latest.log
\System
Report created
\Grabber
\Browsers
\Messenger\Discord
\Messenger\Pidgin
\Messenger\Outlook
\Messenger\Telegram
\Messenger\Skype
\Messenger\Element
\Messenger\Signal
\Messenger\Tox
\Messenger\ICQ
\Gaming\Steam
\Gaming\Uplay
\Gaming\BattleNET
\Gaming\Minecraft
\Wallets
\Wallets\Chrome_Wallet
\Wallets\Edge_Wallet
\FileZilla
\VPN\ProtonVPN
\VPN\OpenVPN
\VPN\NordVPN
\Directories
\System\ProductKey.txt
\System\Debug.txt
\System\Info.txt
\System\Clipboard.txt
UNIQUE
.tmpdb
.dat
\clipboard_logs.txt
logs\clipboard\
Clipper replaced to
.compressed
costura
costura.costura.dll.compressed
costura.costura.pdb.compressed
discord-webhook-client
costura.discord-webhook-client.dll.compressed
dotnetzip
costura.dotnetzip.dll.compressed
costura.dotnetzip.pdb.compressed
microsoft.bcl.asyncinterfaces
costura.microsoft.bcl.asyncinterfaces.dll.compressed
newtonsoft.json
costura.newtonsoft.json.dll.compressed
notifique-me
costura.notifique-me.dll.compressed
passwordgenerator
costura.passwordgenerator.dll.compressed
polly
costura.polly.dll.compressed
costura.polly.pdb.compressed
system.buffers
costura.system.buffers.dll.compressed
system.diagnostics.diagnosticsource
costura.system.diagnostics.diagnosticsource.dll.compressed
system.memory
costura.system.memory.dll.compressed
system.net.http.formatting
costura.system.net.http.formatting.dll.compressed
system.numerics.vectors
costura.system.numerics.vectors.dll.compressed
system.text.encodings.web
costura.system.text.encodings.web.dll.compressed
system.text.json
costura.system.text.json.dll.compressed
system.threading.tasks.extensions
costura.system.threading.tasks.extensions.dll.compressed
system.valuetuple
costura.system.valuetuple.dll.compressed
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (56.7) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (21.3) |
| .scr | | | Windows screen saver (10.1) |
| .dll | | | Win32 Dynamic Link Library (generic) (5) |
| .exe | | | Win32 Executable (generic) (3.4) |
EXIF
EXE
| AssemblyVersion: | 1.0.0.0 |
|---|---|
| ProductVersion: | 1.0.0.0 |
| ProductName: | Stealerium |
| OriginalFileName: | stub.exe |
| LegalTrademarks: | - |
| LegalCopyright: | Copyright © https://github.com/kgnfth 2022 |
| InternalName: | stub.exe |
| FileVersion: | 1.0.0.0 |
| FileDescription: | Stealerium |
| CompanyName: | - |
| Comments: | - |
| CharacterSet: | Unicode |
| LanguageCode: | Neutral |
| FileSubtype: | - |
| ObjectFileType: | Executable application |
| FileOS: | Win32 |
| FileFlags: | (none) |
| FileFlagsMask: | 0x003f |
| ProductVersionNumber: | 1.0.0.0 |
| FileVersionNumber: | 1.0.0.0 |
| Subsystem: | Windows GUI |
| SubsystemVersion: | 6 |
| ImageVersion: | - |
| OSVersion: | 4 |
| EntryPoint: | 0x17fb9e |
| UninitializedDataSize: | - |
| InitializedDataSize: | 5632 |
| CodeSize: | 1563648 |
| LinkerVersion: | 48 |
| PEType: | PE32 |
| ImageFileCharacteristics: | Executable, Large address aware, 32-bit |
| TimeStamp: | 2045:10:13 17:41:43+00:00 |
| MachineType: | Intel 386 or later, and compatibles |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 13-Oct-2045 17:41:43 |
| Comments: | - |
| CompanyName: | - |
| FileDescription: | Stealerium |
| FileVersion: | 1.0.0.0 |
| InternalName: | stub.exe |
| LegalCopyright: | Copyright © https://github.com/kgnfth 2022 |
| LegalTrademarks: | - |
| OriginalFilename: | stub.exe |
| ProductName: | Stealerium |
| ProductVersion: | 1.0.0.0 |
| Assembly Version: | 1.0.0.0 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000080 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 3 |
| Time date stamp: | 13-Oct-2045 17:41:43 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00002000 | 0x0017DBA4 | 0x0017DC00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 7.93625 |
.rsrc | 0x00180000 | 0x00001228 | 0x00001400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.83183 |
.reloc | 0x00182000 | 0x0000000C | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 0.10191 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.01396 | 3643 | UNKNOWN | UNKNOWN | RT_MANIFEST |
Imports
mscoree.dll |
Total processes
49
Monitored processes
9
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1868 | chcp 65001 | C:\Windows\System32\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Change CodePage Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2512 | "C:\Users\admin\AppData\Local\Temp\build.exe" | C:\Users\admin\AppData\Local\Temp\build.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Stealerium Exit code: 3762504530 Version: 1.0.0.0 Modules
BlackGuard(PID) Process(2512) build.exe C2 (1)https://{server}.gofile.io Strings (704)LPOI94VFP3XBYJXSOT7A ENCRYPTED:fleaTKsR0trQiaWh0H+vOvHR4WDn0LEpdxH+edudpJHMS6La1exY+RGGMe+dD0s4w6O2H6Vy+Byk9vPVPyauOqgEeVBlRm4qQM9Ja4WyzXEHz5RYlql8JxZ6BIhu5B+1YYhviWheu50yYYzovyxu22vFISy/Gs3hzHpWeRGmmgk= facebook twitter chat telegram skype discord viber message gmail protonmail outlook password encryption account login sign in bank credit card shop sell qiwi money paypal bitcoin monero dashcoin litecoin etherium stellarcoin blockchain paxful investopedia buybitcoinworldwide cryptocurrency crypto trade trading wallet coinomi coinbase porn hentai chaturbate vk.com ok.ru instagram whatsapp linkedin reddit flickr youtube pinterest tiktok Document docx xlsx pptx indd json DataBase kdbx sqlite SourceCode html swift java Image jpeg {"type": 1 username avatar_url content ?wait=true /messages/ PATCH logs yyyy-MM-dd_h.mm.ss .zip ({0}) ({0} - MAX) 🏦 *Banking services* 💰 *Cryptocurrency services* 🎨 *Social networks* 🍓 *Porn websites* 🔑 Passwords 💳 CreditCards 🍪 Cookies 📂 AutoFill ⏳ History 🔖 Bookmarks 📦 Downloads 💰 Wallet Extensions 💰 Wallets 📡 FTP hosts 🔌 VPN accounts 🦢 Pidgin accounts 📫 Outlook accounts ✈️ Telegram sessions ☁️ Skype session 👾 Discord token 💬 Element session 💭 Signal session 🔓 Tox session 🎮 Steam session 🎮 Uplay session 🎮 BattleNET session 🗝 Windows product key 🛰 Wifi networks 📸 Webcam screenshot 🌃 Desktop screenshot ✅ Startup installed ⛔️ Startup disabled ✅ Clipper installed ⛔️ Clipper not installed ✅ Keylogger installed ⛔️ Keylogger not installed 📂 Images 📂 Documents 📂 Database files 📂 Source code files "``` Sending passwords archive to Gofile Sending report to discord Report sent to discord msgid.dat history.dat Starting keylogger modules... Starting clipper modules... www. google bing yandex duckduckgo .com .org Unknown Amex Card ^3[47][0-9]{13}$ BCGlobal ^(6541|6556)[0-9]{12}$ Carte Blanche Card ^389[0-9]{11}$ Diners Club Card ^3(?:0[0-5]|[68][0-9])[0-9]{11}$ Discover Card 6(?:011|5[0-9]{2})[0-9]{12}$ Insta Payment Card ^63[7-9][0-9]{13}$ JCB Card ^(?:2131|1800|35\\d{3})\\d{11}$ KoreanLocalCard ^9[0-9]{15}$ Laser Card ^(6304|6706|6709|6771)[0-9]{12,15}$ Maestro Card ^(5018|5020|5038|6304|6759|6761|6763)[0-9]{8,15}$ Mastercard 5[1-5][0-9]{14}$ Solo Card ^(6334|6767)[0-9]{12}|(6334|6767)[0-9]{14}|(6334|6767)[0-9]{15}$ Switch Card ^(4903|4905|4911|4936|6333|6759)[0-9]{12}|(4903|4905|4911|4936|6333|6759)[0-9]{14}|(4903|4905|4911|4936|6333|6759)[0-9]{15}|564182[0-9]{10}|564182[0-9]{12}|564182[0-9]{13}|633110[0-9]{10}|633110[0-9]{12}|633110[0-9]{13}$ Union Pay Card ^(62[0-9]{14,17})$ Visa Card 4[0-9]{12}(?:[0-9]{3})?$ Visa Master Card ^(?:4[0-9]{12}(?:[0-9]{3})?|5[1-5][0-9]{14})$ Express Card 3[47][0-9]{13}$ \FileZilla\ recentservers.xml sitemanager.xml Server Pass ftp:// Host Port Rǫ Url: \Hosts.txt Running passwords recovery... Stealer >> Failed recursive remove directory with passwords Software strDataDir \wallets Zcash \Zcash Armory \Armory Bytecoin \bytecoin Jaxx \com.liberty.jaxx\IndexedDB\file__0.indexeddb.leveldb Exodus \Exodus\exodus.wallet Ethereum \Ethereum\keystore Electrum \Electrum\wallets AtomicWallet \atomic\Local Storage\leveldb Guarda \Guarda\Local Storage\leveldb Coinomi \Coinomi\Coinomi\wallets Litecoin Dash Bitcoin NordVPN NordVpn.exe* user.config //setting[@name='Username']/value //setting[@name='Password']/value \accounts.txt Username: OpenVPN Connect\profiles \profiles ovpn profiles\ ProtonVPN ProtonVPN.exe \user.config \Windows.txt NAME: Directory not exists DRIVE- .txt Downloads USERPROFILE Dropbox OneDrive desktop.ini Grabber DropBox SELECT * FROM Win32_Product Name Version InstallDate dd/MM/yyyy HH:mm:ss IdentifyingNumber \Apps.txt BCDFGHJKMPQRTVWXY2346789 SOFTWARE\Microsoft\Windows NT\CurrentVersion DigitalProductId Failed to get DigitalProductId from registry SELECT * FROM Win32_PnPEntity WHERE (PNPClass = 'Image' OR PNPClass = 'Camera') GetConnectedCamerasCount : Query failed WebcamScreenshot : Camera screenshot failed. (Count {0}) WebCap \Webcam.jpg /C chcp 65001 && netsh wlan show profile | findstr All /C chcp 65001 && netsh wlan show profile name=" " key=clear | findstr Key /C chcp 65001 && netsh wlan show networks mode=bssid is not running \ScanningNetworks.txt 65001 PROFILE: \SavedNetworks.txt \Process.txt SELECT ExecutablePath, ProcessID FROM Win32_Process ProcessID ExecutablePath \Desktop.jpg Unknown System root\CIMV2 SELECT * FROM win32_operatingsystem HARDWARE\Description\System\CentralProcessor\0 Identifier (64 Bit) (32 Bit) (Unknown) \root\SecurityCenter2 Select * from AntivirusProduct displayName Not installed No network adapters with an IPv4 address in the system! Request failed unknown Failed BSSID: {"result":200 "lat": "lon": "range": SELECT * FROM Win32_Processor SELECT * FROM Win32_VideoController Select * From Win32_ComputerSystem TotalPhysicalMemory yyyy-MM-dd h:mm:ss tt \tokens.txt Authorization Unauthorized Token is valid Token is invalid Connection error [a-zA-Z0-9]{24}\.[a-zA-Z0-9]{6}\.[a-zA-Z0-9_\-]{27}|mfa\.[a-zA-Z0-9_\-]{84} Discord\Local Storage\leveldb Discord PTB\Local Storage\leveldb Discord Canary\leveldb .log .ldb leveldb \leveldb Element\Local Storage databases Session Storage Local Storage \databases \Session Storage \Local Storage \sql \config.json Signal Software\Microsoft\Office\15.0\Outlook\Profiles\Outlook\9375CFF0413111d3B88A00104B2A6676 Software\Microsoft\Office\16.0\Outlook\Profiles\Outlook\9375CFF0413111d3B88A00104B2A6676 Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\9375CFF0413111d3B88A00104B2A6676 Software\Microsoft\Windows Messaging Subsystem\Profiles\9375CFF0413111d3B88A00104B2A6676 SMTP Email Address SMTP Server POP3 Server POP3 User Name SMTP User Name NNTP Email Address NNTP User Name NNTP Server IMAP Server IMAP User Name Email HTTP User HTTP Server URL POP3 User IMAP User HTTPMail User Name HTTPMail Server SMTP User POP3 Password2 IMAP Password2 NNTP Password2 HTTPMail Password2 SMTP Password2 POP3 Password IMAP Password NNTP Password HTTPMail Password SMTP Password \Outlook.txt Password null ^([a-zA-Z0-9_\-\.]+)@([a-zA-Z0-9_\-\.]+)\.([a-zA-Z]{2,5})$ ^(?!:\/\/)([a-zA-Z0-9-_]+\.)*[a-zA-Z0-9][a-zA-Z0-9-_]+\.[a-zA-Z]{2,11}?$ \chatlogs accounts.xml Protocol: Password: .purple 0001 \0001 Microsoft\Skype for Desktop \Telegram Desktop\tdata Telegram tdata usertag settings key_data BattleNET >> Session not found *.db *.config Battle.net versions bytes \versions.txt VERSION: mods \mods.txt MOD: screenshots \screenshots \screenshots\ profile options servers .minecraft Software\Valve\Steam Steam >> Application path not found in registry SteamPath Steam >> Application directory not found Apps Apps\ Installed Running Updating Application \ssnf ssfn \ssnf\ config \configs \configs\ RememberPassword Autologin User: AutoLoginUser \SteamInfo.txt Uplay >> Session not found Ubisoft Game Launcher Hostname: Type: ### ### ( \Profiles \places.sqlite moz_bookmarks \cookies.sqlite moz_cookies \mozglue.dll \nss3.dll NSS_Init PK11SDR_Decrypt NSS_Shutdown \Bookmarks.txt \Cookies.txt \History.txt \Passwords.txt \Profiles\ moz_places logins.json key3.db key4.db \logins.json ,"logins":\[ ,"potentiallyVulnerablePasswords" Program Files\Mozilla Firefox Users\Public cert9.db "hostname":"([^"]+)" "encryptedUsername":"([^"]+)" "encryptedPassword":"([^"]+)" autofill "bookmark_bar": { "other": { "name": " "type": "url", "url": "http Failed to parse url credit_cards \Edge \Login Data \Web Data \Bookmarks \Cookies \History \CreditCards.txt \AutoFill.txt Edge_Auvitas \Microsoft\Edge\User Data\Default\Local Extension Settings\klfhbdnlcfcaccoakhceodhldjojboga Edge_Math \Microsoft\Edge\User Data\Default\Local Extension Settings\dfeccadlilpndjjohbjdblepmjeahlmm Edge_Metamask \Microsoft\Edge\User Data\Default\Local Extension Settings\ejbalbakoplchlghecdalmeeeajnimhm Edge_MTV \Microsoft\Edge\User Data\Default\Local Extension Settings\oooiblbdpdlecigodndinbpfopomaegl Edge_Rabet \Microsoft\Edge\User Data\Default\Local Extension Settings\aanjhgiamnacdfnlfnmgehjikagdbafd Edge_Ronin \Microsoft\Edge\User Data\Default\Local Extension Settings\bblmcdckkhkhfhhpfcchlpalebmonecp Edge_Yoroi \Microsoft\Edge\User Data\Default\Local Extension Settings\akoiaibnepcedcplijmiamnaigbepmcb Edge_Zilpay \Microsoft\Edge\User Data\Default\Local Extension Settings\fbekallmnjoeggkefjkbebpineneilec Edge_Exodus \Microsoft\Edge\User Data\Default\Local Extension Settings\jdiccldimpdaibmpdkjnbmckianbfold Edge_Terra_Station \Microsoft\Edge\User Data\Default\Local Extension Settings\ajkhoeiiokighlmdnlakpjfoobnjinie Edge_Jaxx \Microsoft\Edge\User Data\Default\Local Extension Settings\dmdimapfghaakeibppbfeokhgoikeoci BCrypt.BCryptDecrypt() (get size) failed with status code: {0} BCrypt.BCryptDecrypt(): authentication tag mismatch BCrypt.BCryptDecrypt() failed with status code:{0} BCrypt.BCryptOpenAlgorithmProvider() failed with status code:{0} BCrypt.BCryptSetAlgorithmProperty(BCrypt.BCRYPT_CHAINING_MODE, BCrypt.BCRYPT_CHAIN_MODE_GCM) failed with status code:{0} BCrypt.BCryptImportKey() failed with status code:{0} BCrypt.BCryptGetProperty() (get size) failed with status code:{0} BCrypt.BCryptGetProperty() failed with status code:{0} ObjectLength ChainingModeGCM AuthTagLength ChainingMode KeyDataBlob Microsoft Primitive Provider "name ": " Opera \Opera Stable\Local State \Local State "encrypted_key":"(.*?)" Opera Software \Downloads.txt cookies downloads Chrome_Binance \Google\Chrome\User Data\Default\Local Extension Settings\fhbohimaelbohpjbbldcngcnapndodjp Chrome_Bitapp \Google\Chrome\User Data\Default\Local Extension Settings\fihkakfobkmkjojpchpfgcmhfjnmnfpi Chrome_Coin98 \Google\Chrome\User Data\Default\Local Extension Settings\aeachknmefphepccionboohckonoeemg Chrome_Equal \Google\Chrome\User Data\Default\Local Extension Settings\blnieiiffboillknjnepogjhkgnoapac Chrome_Guild \Google\Chrome\User Data\Default\Local Extension Settings\nanjmdknhkinifnkgdcggcfnhdaammmj Chrome_Iconex \Google\Chrome\User Data\Default\Local Extension Settings\flpiciilemghbmfalicajoolhkkenfel Chrome_Math \Google\Chrome\User Data\Default\Local Extension Settings\afbcbjpbpfadlkmhmclhkeeodmamcflc Chrome_Mobox \Google\Chrome\User Data\Default\Local Extension Settings\fcckkdbjnoikooededlapcalpionmalo Chrome_Phantom \Google\Chrome\User Data\Default\Local Extension Settings\bfnaelmomeimhlpmgjnjophhpkkoljpa Chrome_Tron \Google\Chrome\User Data\Default\Local Extension Settings\ibnejdfjmmkpcnlpebklmnkoeoihofec Chrome_XinPay \Google\Chrome\User Data\Default\Local Extension Settings\bocpokimicclpaiekenaeelehdjllofo Chrome_Ton \Google\Chrome\User Data\Default\Local Extension Settings\nphplpgoakhhjchkkhmiggakijnkhfnd Chrome_Metamask \Google\Chrome\User Data\Default\Local Extension Settings\nkbihfbeogaeaoehlefnkodbefgpgknn Chrome_Sollet \Google\Chrome\User Data\Default\Local Extension Settings\fhmfendgdocmcbmfikdcogofphimnkno Chrome_Slope \Google\Chrome\User Data\Default\Local Extension Settings\pocmplpaccanhmnllbbkpgfliimjljgo Chrome_Starcoin \Google\Chrome\User Data\Default\Local Extension Settings\mfhbebgoclkghebffdldpobeajmbecfk Chrome_Swash \Google\Chrome\User Data\Default\Local Extension Settings\cmndjbecilbocjfkibfbifhngkdmjgog Chrome_Finnie \Google\Chrome\User Data\Default\Local Extension Settings\cjmkndjhnagcfbpiemnkdpomccnjblmj Chrome_Keplr \Google\Chrome\User Data\Default\Local Extension Settings\dmkamcknogkgcdfhhbddcghachkejeap Chrome_Crocobit \Google\Chrome\User Data\Default\Local Extension Settings\pnlfjmlcjdjgkddecgincndfgegkecke Chrome_Oxygen \Google\Chrome\User Data\Default\Local Extension Settings\fhilaheimglignddkjgofkcbgekhenbh Chrome_Nifty \Google\Chrome\User Data\Default\Local Extension Settings\jbdaocneiiinmjbjlgalhcelgbejmnid Chrome_Liquality \Google\Chrome\User Data\Default\Local Extension Settings\kpfopkelmapcoipemfendmdcghnegimn urls logins hh.mm.ss logs\keylogger\ yyyy-MM-dd Space Return Escape LControlKey RControlKey RShiftKey LShiftKey Back LWin Capital [ENTER] [ESC] [CTRL] [Shift] [Back] [WIN] [Tab] [CAPSLOCK: ON] [CAPSLOCK: OFF] logs\nsfw\ true processhacker netstat netmon tcpview wireshark filemon regmon cain SbieDll snxhk cmdvrt32 Select * from Win32_ComputerSystem Manufacturer microsoft corporation Model VIRTUAL vmware VirtualBox VMware AntiAnalysis : Hosting detected! AntiAnalysis : Process detected! AntiAnalysis : Virtual machine detected! AntiAnalysis : SandBox detected! AntiAnalysis : Debugger detected! Sending fake error message box with code: Exit code Runtime error .dll .bat chcp 65001 TaskKill /F /IM Timeout /T 2 /Nobreak SelfDestruct : Running self destruct procedure... cmd.exe StartDelay : Sleeping SetFileCreationDate : Changing file creation data HideFile : Adding 'hidden' attribute to file Startup : Adding to autorun... SOFTWARE\Microsoft\Windows\CurrentVersion\Run ENCRYPTED: {server} uploadFile downloadPage apiv2 getServer FileService status returned a value. (No data) Banking services Cryptocurrency services Social networks Porn websites Archive compression completed Stealerium-Latest.log \System Report created \Grabber \Browsers \Messenger\Discord \Messenger\Pidgin \Messenger\Outlook \Messenger\Telegram \Messenger\Skype \Messenger\Element \Messenger\Signal \Messenger\Tox \Messenger\ICQ \Gaming\Steam \Gaming\Uplay \Gaming\BattleNET \Gaming\Minecraft \Wallets \Wallets\Chrome_Wallet \Wallets\Edge_Wallet \FileZilla \VPN\ProtonVPN \VPN\OpenVPN \VPN\NordVPN \Directories \System\ProductKey.txt \System\Debug.txt \System\Info.txt \System\Clipboard.txt UNIQUE .tmpdb .dat \clipboard_logs.txt logs\clipboard\ Clipper replaced to .compressed costura costura.costura.dll.compressed costura.costura.pdb.compressed discord-webhook-client costura.discord-webhook-client.dll.compressed dotnetzip costura.dotnetzip.dll.compressed costura.dotnetzip.pdb.compressed microsoft.bcl.asyncinterfaces costura.microsoft.bcl.asyncinterfaces.dll.compressed newtonsoft.json costura.newtonsoft.json.dll.compressed notifique-me costura.notifique-me.dll.compressed passwordgenerator costura.passwordgenerator.dll.compressed polly costura.polly.dll.compressed costura.polly.pdb.compressed system.buffers costura.system.buffers.dll.compressed system.diagnostics.diagnosticsource costura.system.diagnostics.diagnosticsource.dll.compressed system.memory costura.system.memory.dll.compressed system.net.http.formatting costura.system.net.http.formatting.dll.compressed system.numerics.vectors costura.system.numerics.vectors.dll.compressed system.text.encodings.web costura.system.text.encodings.web.dll.compressed system.text.json costura.system.text.json.dll.compressed system.threading.tasks.extensions costura.system.threading.tasks.extensions.dll.compressed system.valuetuple costura.system.valuetuple.dll.compressed | |||||||||||||||
| 2776 | C:\Windows\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2844 | findstr All | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2868 | netsh wlan show profile | C:\Windows\System32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3104 | "cmd.exe" /C chcp 65001 && netsh wlan show networks mode=bssid | C:\Windows\System32\cmd.exe | — | build.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3564 | chcp 65001 | C:\Windows\System32\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Change CodePage Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3600 | netsh wlan show networks mode=bssid | C:\Windows\System32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 4056 | "cmd.exe" /C chcp 65001 && netsh wlan show profile | findstr All | C:\Windows\System32\cmd.exe | — | build.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
8 770
Read events
8 558
Write events
212
Delete events
0
Modification events
| (PID) Process: | (2512) build.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2868) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3600) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
0
Suspicious files
8
Text files
68
Unknown types
20
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2512 | build.exe | C:\Users\admin\AppData\Local\Temp\Stealerium-Latest.log | text | |
MD5:— | SHA256:— | |||
| 2512 | build.exe | C:\Users\admin\AppData\Local\d0979d2a4904b46c7479d194def2561c\admin@USER-PC_en-US\System\Debug.txt | text | |
MD5:— | SHA256:— | |||
| 2512 | build.exe | C:\Users\admin\AppData\Local\d0979d2a4904b46c7479d194def2561c\admin@USER-PC_en-US\Grabber\DRIVE-C\Users\admin\Documents\artistsstatement.rtf | text | |
MD5:— | SHA256:— | |||
| 2512 | build.exe | C:\Users\admin\AppData\Local\d0979d2a4904b46c7479d194def2561c\admin@USER-PC_en-US\Grabber\DRIVE-C\Users\admin\Downloads\thankdeals.png | image | |
MD5:— | SHA256:— | |||
| 2512 | build.exe | C:\Users\admin\AppData\Local\Temp\tmp3583.tmp.dat | — | |
MD5:— | SHA256:— | |||
| 2512 | build.exe | C:\Users\admin\AppData\Local\d0979d2a4904b46c7479d194def2561c\admin@USER-PC_en-US\Grabber\DRIVE-C\Users\admin\Pictures\trialresponse.png | image | |
MD5:— | SHA256:— | |||
| 2512 | build.exe | C:\Users\admin\AppData\Local\d0979d2a4904b46c7479d194def2561c\admin@USER-PC_en-US\Grabber\DRIVE-C\Users\admin\Documents\careelectronics.rtf | text | |
MD5:— | SHA256:— | |||
| 2512 | build.exe | C:\Users\admin\AppData\Local\d0979d2a4904b46c7479d194def2561c\admin@USER-PC_en-US\Directories\Desktop.txt | text | |
MD5:— | SHA256:— | |||
| 2512 | build.exe | C:\Users\admin\AppData\Local\d0979d2a4904b46c7479d194def2561c\admin@USER-PC_en-US\Grabber\DRIVE-C\Users\admin\Documents\directionstool.rtf | text | |
MD5:— | SHA256:— | |||
| 2512 | build.exe | C:\Users\admin\AppData\Local\d0979d2a4904b46c7479d194def2561c\admin@USER-PC_en-US\Messenger\Skype\Local Storage\leveldb\000005.ldb | binary | |
MD5:481B01D81087F708E6C9DDEC34D987EC | SHA256:0816D2ABF723E8A066C9464D0335BA864AF53EAFDFBCD8C235AA16F1900B9DF3 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
3
DNS requests
3
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2512 | build.exe | GET | 200 | 104.18.114.97:80 | http://icanhazip.com/ | US | text | 14 b | shared |
2512 | build.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line/?fields=hosting | unknown | text | 5 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2512 | build.exe | 208.95.112.1:80 | ip-api.com | TUT-AS | US | malicious |
2512 | build.exe | 104.18.114.97:80 | icanhazip.com | CLOUDFLARENET | — | malicious |
— | — | 162.159.136.232:443 | discord.com | CLOUDFLARENET | — | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ip-api.com |
| malicious |
discord.com |
| whitelisted |
icanhazip.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2512 | build.exe | Potential Corporate Privacy Violation | AV POLICY Internal Host Retrieving External IP Address (ip-api. com) |
2512 | build.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
— | — | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
2512 | build.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
2512 | build.exe | Attempted Information Leak | ET POLICY IP Check Domain (icanhazip. com in HTTP Host) |