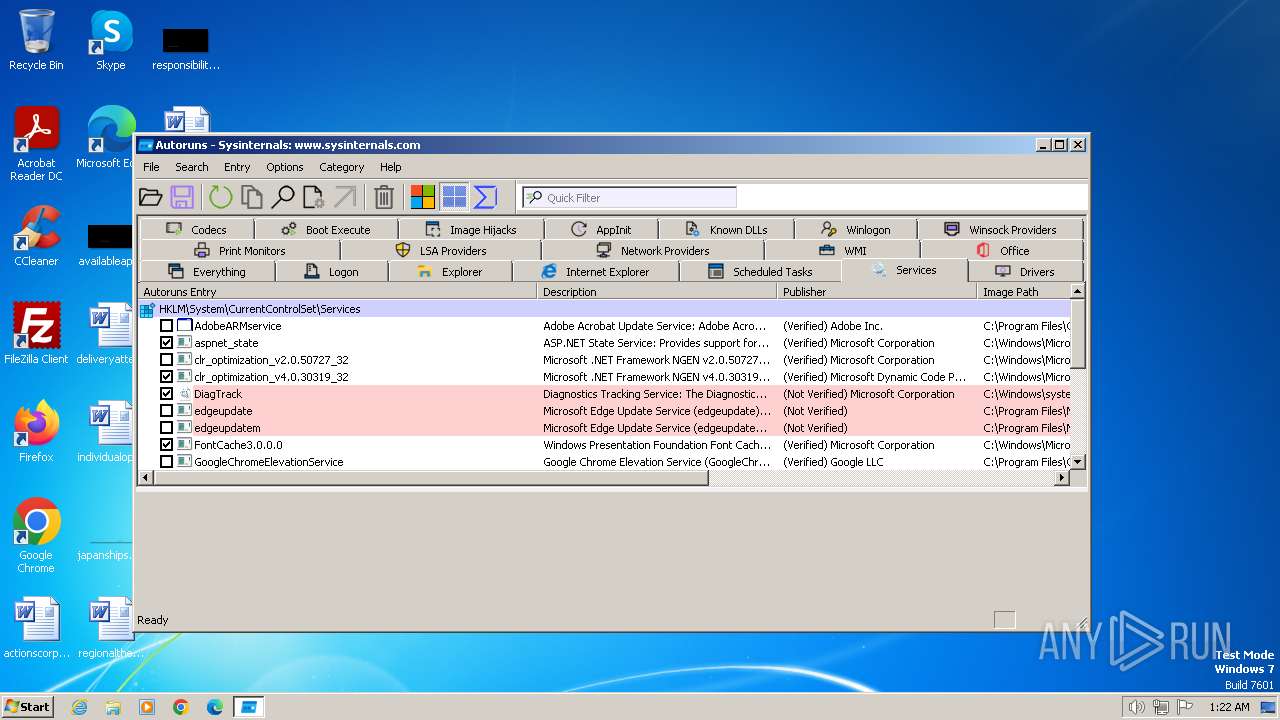
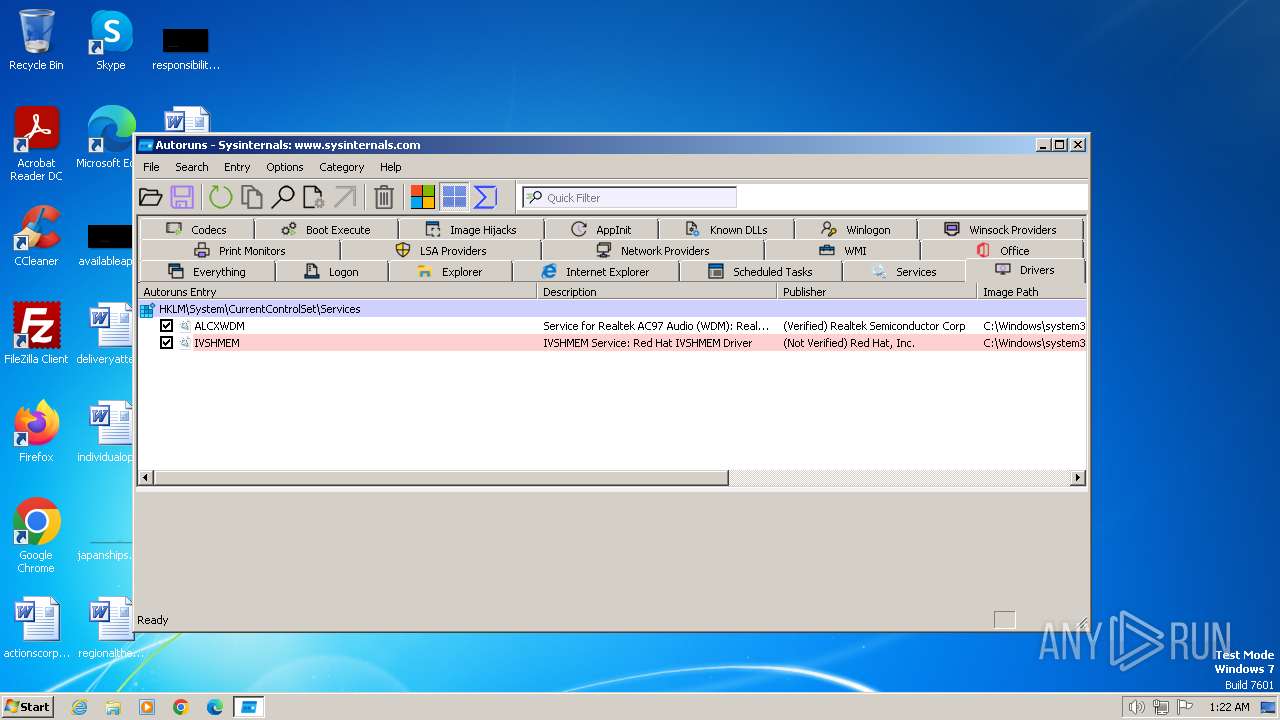
| File name: | autoruns.exe |
| Full analysis: | https://app.any.run/tasks/265df235-3a1e-4665-be21-e5dba489485b |
| Verdict: | Malicious activity |
| Analysis date: | March 28, 2024, 01:20:30 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 61506280FC7E663DB6715AC2206AF6D4 |
| SHA1: | 3B42F1E497C909D48343768B58E9E5222D540330 |
| SHA256: | F41051697B220757F3612ECD00749B952CE7BCAADD9DC782D79EF0338E45C3B6 |
| SSDEEP: | 24576:1SeGQxZ1urIU0zBOeUSX0Kdq6hDBiqddc:1SeGQxZ1urIU0zBZUSX0Kdq6hdiqddc |
MALICIOUS
Drops the executable file immediately after the start
- autoruns.exe (PID: 2120)
SUSPICIOUS
Reads settings of System Certificates
- autoruns.exe (PID: 2120)
Read startup parameters
- autoruns.exe (PID: 2120)
Reads security settings of Internet Explorer
- autoruns.exe (PID: 2120)
Reads the Internet Settings
- autoruns.exe (PID: 2120)
Checks Windows Trust Settings
- autoruns.exe (PID: 2120)
INFO
Reads product name
- autoruns.exe (PID: 2120)
Checks supported languages
- autoruns.exe (PID: 2120)
Reads the computer name
- autoruns.exe (PID: 2120)
Reads Microsoft Office registry keys
- autoruns.exe (PID: 2120)
Reads the machine GUID from the registry
- autoruns.exe (PID: 2120)
Creates files or folders in the user directory
- autoruns.exe (PID: 2120)
Reads Environment values
- autoruns.exe (PID: 2120)
Create files in a temporary directory
- autoruns.exe (PID: 2120)
Reads the software policy settings
- autoruns.exe (PID: 2120)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:02:01 10:45:10+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.37 |
| CodeSize: | 728576 |
| InitializedDataSize: | 1097216 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x7e65d |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 14.11.0.0 |
| ProductVersionNumber: | 14.11.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Dynamic link library |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Sysinternals - www.sysinternals.com |
| FileDescription: | Autostart program viewer |
| FileVersion: | 14.11 |
| InternalName: | Sysinternals Autoruns |
| LegalCopyright: | Copyright (C) 2002-2024 Mark Russinovich |
| OriginalFileName: | autoruns.exe |
| ProductName: | Sysinternals autoruns |
| ProductVersion: | 14.11 |
Total processes
38
Monitored processes
1
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2120 | "C:\Users\admin\AppData\Local\Temp\autoruns.exe" | C:\Users\admin\AppData\Local\Temp\autoruns.exe | explorer.exe | ||||||||||||
User: admin Company: Sysinternals - www.sysinternals.com Integrity Level: MEDIUM Description: Autostart program viewer Version: 14.11 Modules
| |||||||||||||||
Total events
120 242
Read events
120 125
Write events
117
Delete events
0
Modification events
| (PID) Process: | (2120) autoruns.exe | Key: | HKEY_CURRENT_USER\Software\Sysinternals\Autoruns |
| Operation: | write | Name: | EulaAccepted |
Value: 1 | |||
| (PID) Process: | (2120) autoruns.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2120) autoruns.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\System32\wshtcpip.dll,-60100 |
Value: MSAFD Tcpip [TCP/IP] | |||
| (PID) Process: | (2120) autoruns.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\System32\wshtcpip.dll,-60101 |
Value: MSAFD Tcpip [UDP/IP] | |||
| (PID) Process: | (2120) autoruns.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\System32\wshtcpip.dll,-60102 |
Value: MSAFD Tcpip [RAW/IP] | |||
| (PID) Process: | (2120) autoruns.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\System32\wship6.dll,-60100 |
Value: MSAFD Tcpip [TCP/IPv6] | |||
| (PID) Process: | (2120) autoruns.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\System32\wship6.dll,-60101 |
Value: MSAFD Tcpip [UDP/IPv6] | |||
| (PID) Process: | (2120) autoruns.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\System32\wship6.dll,-60102 |
Value: MSAFD Tcpip [RAW/IPv6] | |||
| (PID) Process: | (2120) autoruns.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\System32\wshqos.dll,-100 |
Value: RSVP TCPv6 Service Provider | |||
| (PID) Process: | (2120) autoruns.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\System32\wshqos.dll,-101 |
Value: RSVP TCP Service Provider | |||
Executable files
0
Suspicious files
11
Text files
0
Unknown types
10
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2120 | autoruns.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 2120 | autoruns.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\A583E2A51BFBDC1E492A57B7C8325850 | binary | |
MD5:— | SHA256:— | |||
| 2120 | autoruns.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\A583E2A51BFBDC1E492A57B7C8325850 | binary | |
MD5:— | SHA256:— | |||
| 2120 | autoruns.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\2CD1F910DD5DC23C234E99A91DE345C0 | binary | |
MD5:— | SHA256:— | |||
| 2120 | autoruns.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\2CD1F910DD5DC23C234E99A91DE345C0 | binary | |
MD5:— | SHA256:— | |||
| 2120 | autoruns.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\4C7F163ED126D5C3CB9457F68EC64E9E | binary | |
MD5:— | SHA256:— | |||
| 2120 | autoruns.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\4C7F163ED126D5C3CB9457F68EC64E9E | binary | |
MD5:— | SHA256:— | |||
| 2120 | autoruns.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\696F3DE637E6DE85B458996D49D759AD | binary | |
MD5:— | SHA256:— | |||
| 2120 | autoruns.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\696F3DE637E6DE85B458996D49D759AD | binary | |
MD5:— | SHA256:— | |||
| 2120 | autoruns.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B8CC409ACDBF2A2FE04C56F2875B1FD6 | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
8
DNS requests
5
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2120 | autoruns.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?174f274616bc7e17 | unknown | — | — | unknown |
2120 | autoruns.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | unknown |
2120 | autoruns.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicWinProPCA2011_2011-10-19.crl | unknown | — | — | unknown |
2120 | autoruns.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/WinPCA.crl | unknown | — | — | unknown |
2120 | autoruns.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | unknown | — | — | unknown |
2120 | autoruns.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/microsoftrootcert.crl | unknown | — | — | unknown |
2120 | autoruns.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicrosoftTimeStampPCA.crl | unknown | — | — | unknown |
2120 | autoruns.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?cdcac0d55ba8ca09 | unknown | — | — | unknown |
2120 | autoruns.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Windows%20Verification%20PCA(1).crl | unknown | — | — | unknown |
2120 | autoruns.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/certs/Microsoft%20Development%20Root%20Certificate%20Authority%202014.crt | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2120 | autoruns.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
2120 | autoruns.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
2120 | autoruns.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | unknown |
1080 | svchost.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ctldl.windowsupdate.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |