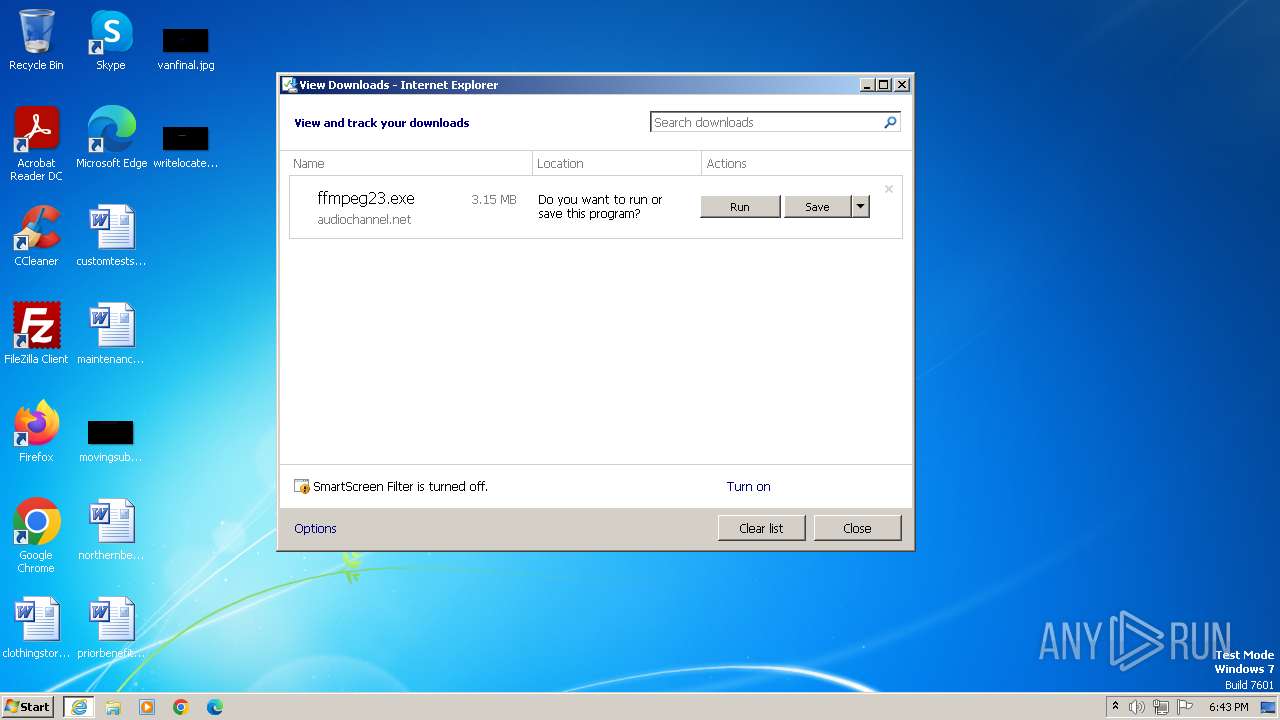
| URL: | audiochannel.net/components/ffmpeg23.exe |
| Full analysis: | https://app.any.run/tasks/54f479ac-d9e4-4c97-89f7-0167d4e8241a |
| Verdict: | Malicious activity |
| Analysis date: | November 03, 2023, 18:42:57 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| SHA1: | 8BD290756541413E79069C6A9F3C84F9DB556EE5 |
| SHA256: | F40702BAC2633F1B31AB60247DC093D7AE4BB0820C65B6AE06D3844DA07CAA45 |
| SSDEEP: | 3:5hPL+LxIOALgVXU:Dz+LdPU |
MALICIOUS
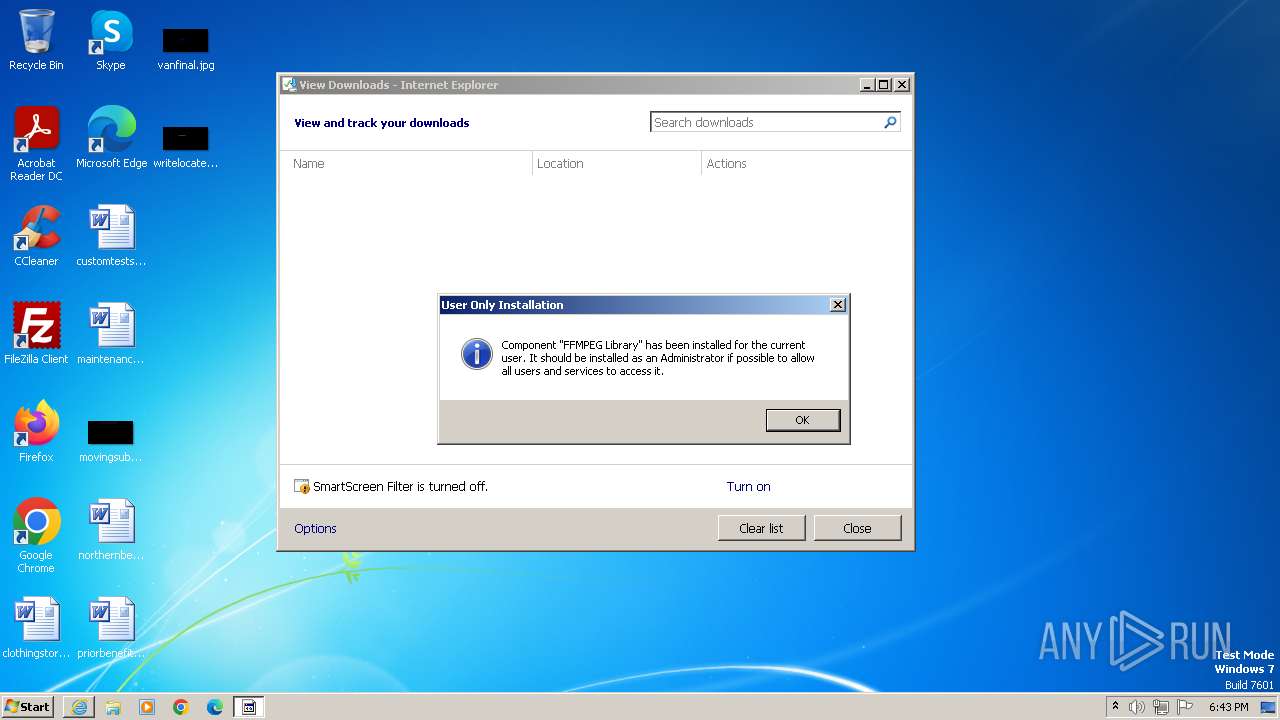
Drops the executable file immediately after the start
- ffmpeg23.exe (PID: 3668)
SUSPICIOUS
No suspicious indicators.INFO
Application launched itself
- iexplore.exe (PID: 3440)
Checks supported languages
- wmpnscfg.exe (PID: 3408)
- ffmpeg23.exe (PID: 3668)
Reads the computer name
- wmpnscfg.exe (PID: 3408)
Reads the machine GUID from the registry
- wmpnscfg.exe (PID: 3408)
Manual execution by a user
- wmpnscfg.exe (PID: 3408)
Creates files or folders in the user directory
- ffmpeg23.exe (PID: 3668)
The process uses the downloaded file
- iexplore.exe (PID: 3440)
Drops the executable file immediately after the start
- iexplore.exe (PID: 3440)
- iexplore.exe (PID: 3216)
Create files in a temporary directory
- ffmpeg23.exe (PID: 3668)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
38
Monitored processes
4
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3216 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3440 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3408 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3440 | "C:\Program Files\Internet Explorer\iexplore.exe" "audiochannel.net/components/ffmpeg23.exe" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3668 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\ffmpeg23.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\ffmpeg23.exe | — | iexplore.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
6 582
Read events
6 524
Write events
55
Delete events
3
Modification events
| (PID) Process: | (3440) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (3440) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (3440) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (3440) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3440) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3440) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3440) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3440) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3440) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3440) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
8
Suspicious files
12
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3668 | ffmpeg23.exe | C:\Users\admin\AppData\Roaming\NCH Software\Components\ffmpeg23\avformat-55.nch.dll | executable | |
MD5:4F152CA5D7ACC7D163D9D6398F26E56B | SHA256:E91071179A57CB55A17E4A4F2897D680A40B79AAC72C71106770285B26C6461D | |||
| 3216 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\ffmpeg23[1].exe | executable | |
MD5:C8A5F19B0D7AFDA0DB3A558AE12465FD | SHA256:AF5DEF9DEF314346196EEDC19E702BDA71B269E8E1D82AFD96E93F5353441846 | |||
| 3216 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\ffmpeg23.exe.apilw7r.partial | executable | |
MD5:8F2DBFDBBF7D110E5093DF464197641A | SHA256:7CBB0774164EFB5FB4A170CC854E184D8CA67CE796B6BDA632FB692E89ABEC27 | |||
| 3668 | ffmpeg23.exe | C:\Users\admin\AppData\Local\Temp\CB83.tmp | compressed | |
MD5:B550A472ACA2CA71ABF3ABED56D2998F | SHA256:DECFF418DE57C1D42F64B5E3E61794BF7712B5530D6907E0345E27C01065BD6F | |||
| 3440 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{D0D01F91-7A78-11EE-A826-12A9866C77DE}.dat | binary | |
MD5:215E499AA86A58306601D71F546B2DD5 | SHA256:3087963C47D8A57B8F17363C70057009D6A281CBC7C2A052084092A5B027FA8B | |||
| 3440 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\ffmpeg23.exe.apilw7r.partial:Zone.Identifier | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
| 3668 | ffmpeg23.exe | C:\Users\admin\AppData\Roaming\NCH Software\Components\ffmpeg23\avutil-52.nch.dll | executable | |
MD5:60F5AE4A2D9CB28B97E0046BE0CEFB64 | SHA256:629E649E15712617A2A725EA73909E87DA4A814A957BD881AC0DCD20ECF73AE0 | |||
| 3668 | ffmpeg23.exe | C:\Users\admin\AppData\Local\Temp\CAD6.tmp | compressed | |
MD5:4501974AB5FCF6CA51FCBDB0B981FADD | SHA256:D31B029849B5538B807C427FAD368E980CDEA5166805D267906487BDBF2CC90D | |||
| 3668 | ffmpeg23.exe | C:\Users\admin\AppData\Roaming\NCH Software\Components\ffmpeg23\swscale-2.nch.dll | executable | |
MD5:82C2540D88F5AF37A09F9910BB12050A | SHA256:3B97534B1557ED1FA84F22FA40ECEE675964C7298558D3CC96B29163F06E74E6 | |||
| 3668 | ffmpeg23.exe | C:\Users\admin\AppData\Roaming\NCH Software\Components\ffmpeg23\avcodec-55.nch.dll | executable | |
MD5:6F2EF5FB03AA07BB35CFE8D15557738F | SHA256:F8A72279AA676BBC62B280368EDB9BA5D6848077936AEF98EF36D9EDD2CEAD9B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
12
DNS requests
6
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3440 | iexplore.exe | GET | 200 | 184.24.77.200:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?803fe1dbe68dd6c5 | unknown | compressed | 4.66 Kb | unknown |
3440 | iexplore.exe | GET | 200 | 184.24.77.200:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?da725366b68abe37 | unknown | compressed | 4.66 Kb | unknown |
3440 | iexplore.exe | GET | 200 | 184.24.77.200:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?d3d5aa83afc110f0 | unknown | compressed | 4.66 Kb | unknown |
3440 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3440 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | EDGECAST | US | whitelisted |
3440 | iexplore.exe | 184.24.77.200:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
3440 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3216 | iexplore.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |