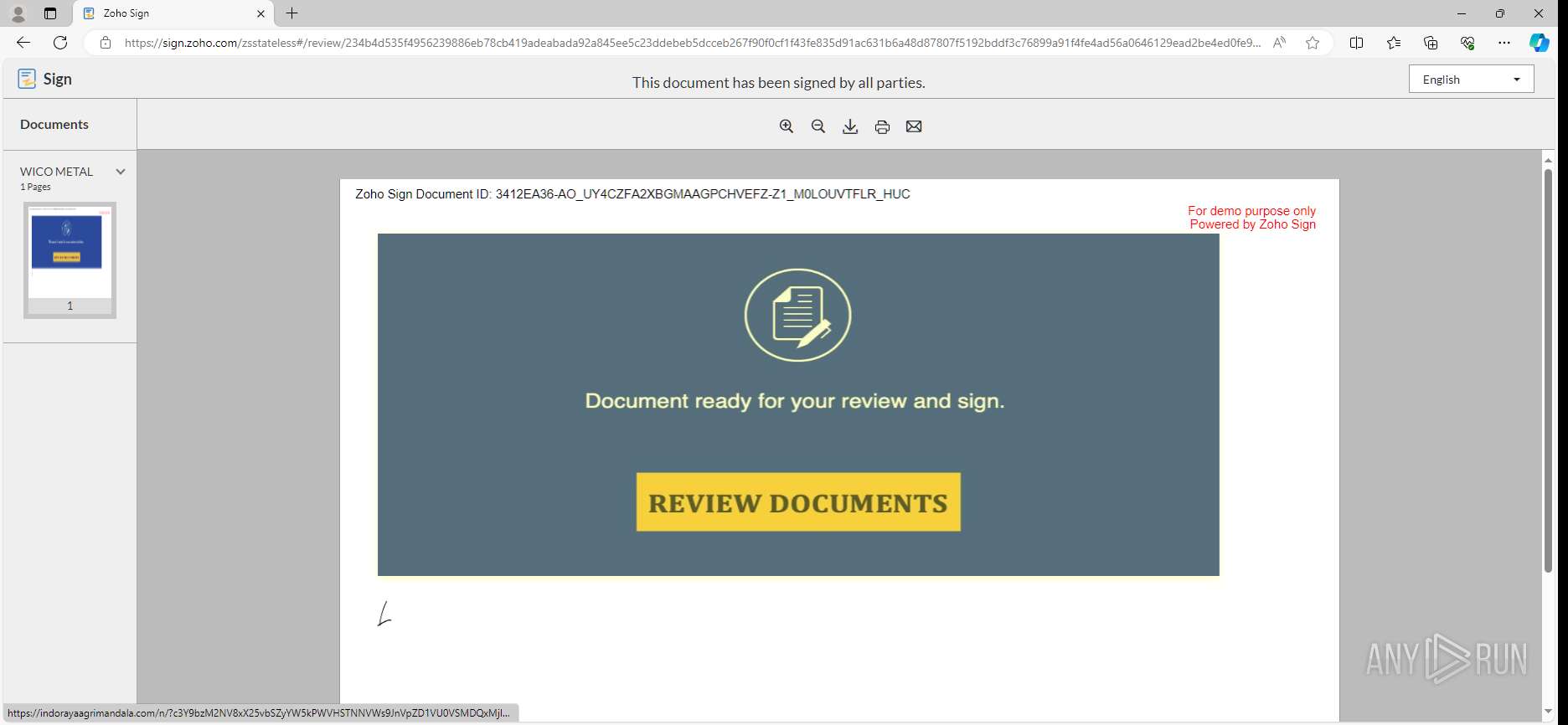
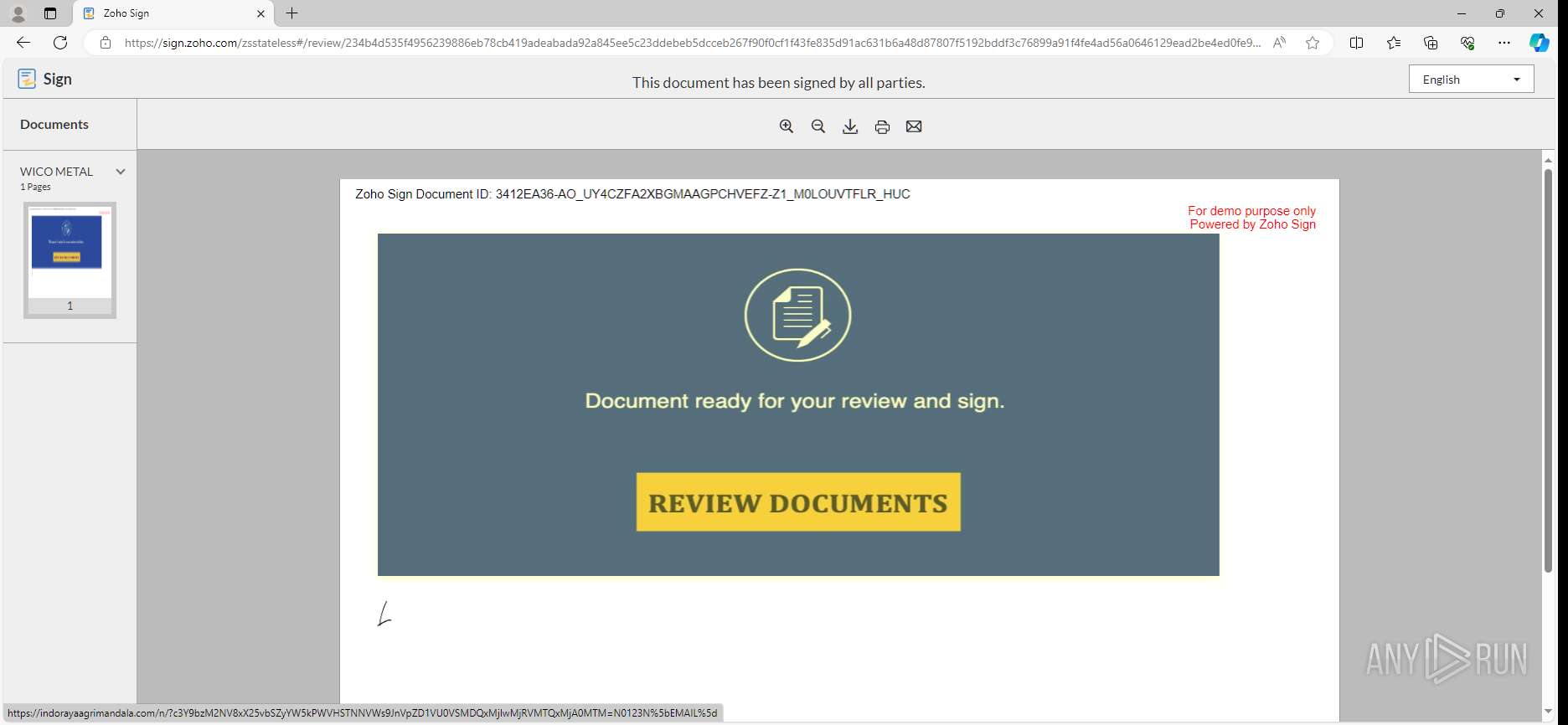
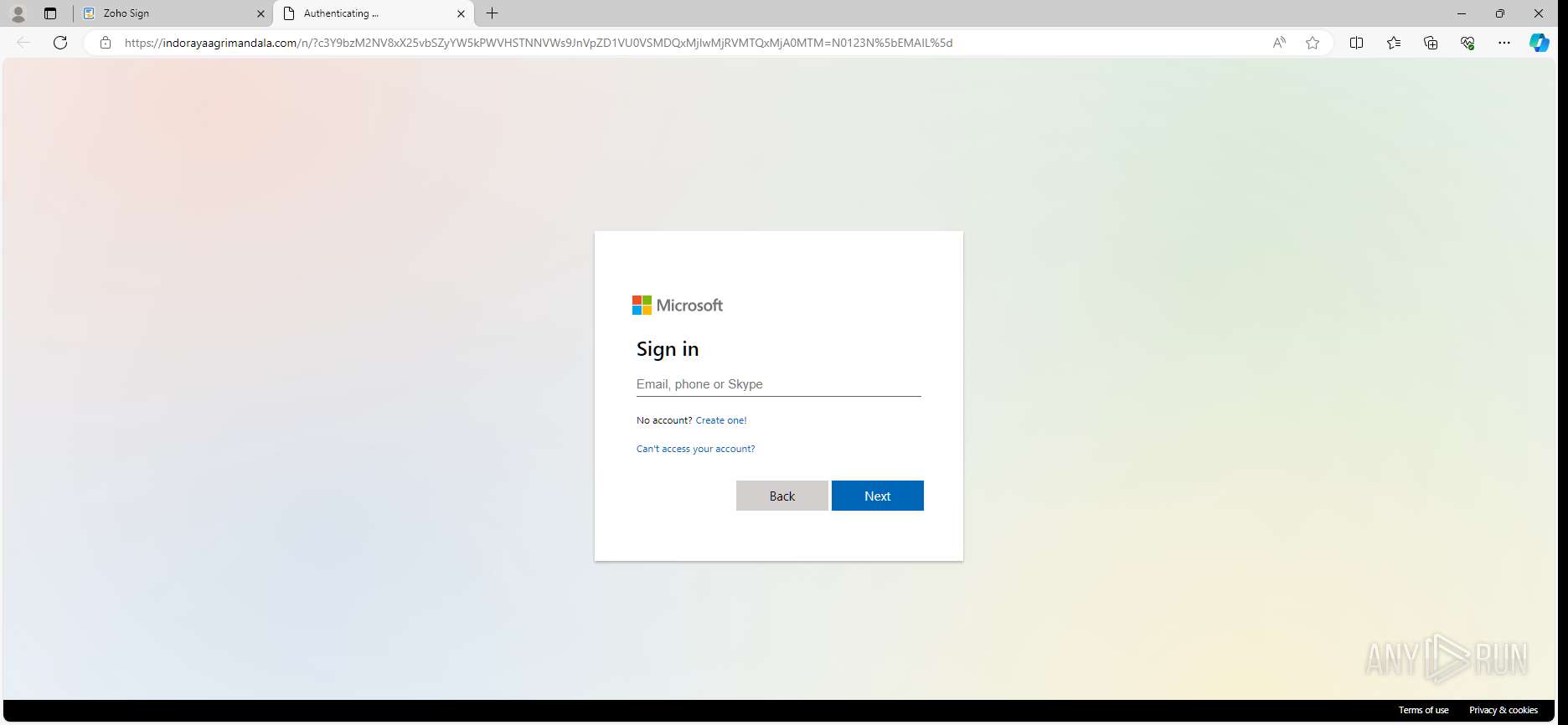
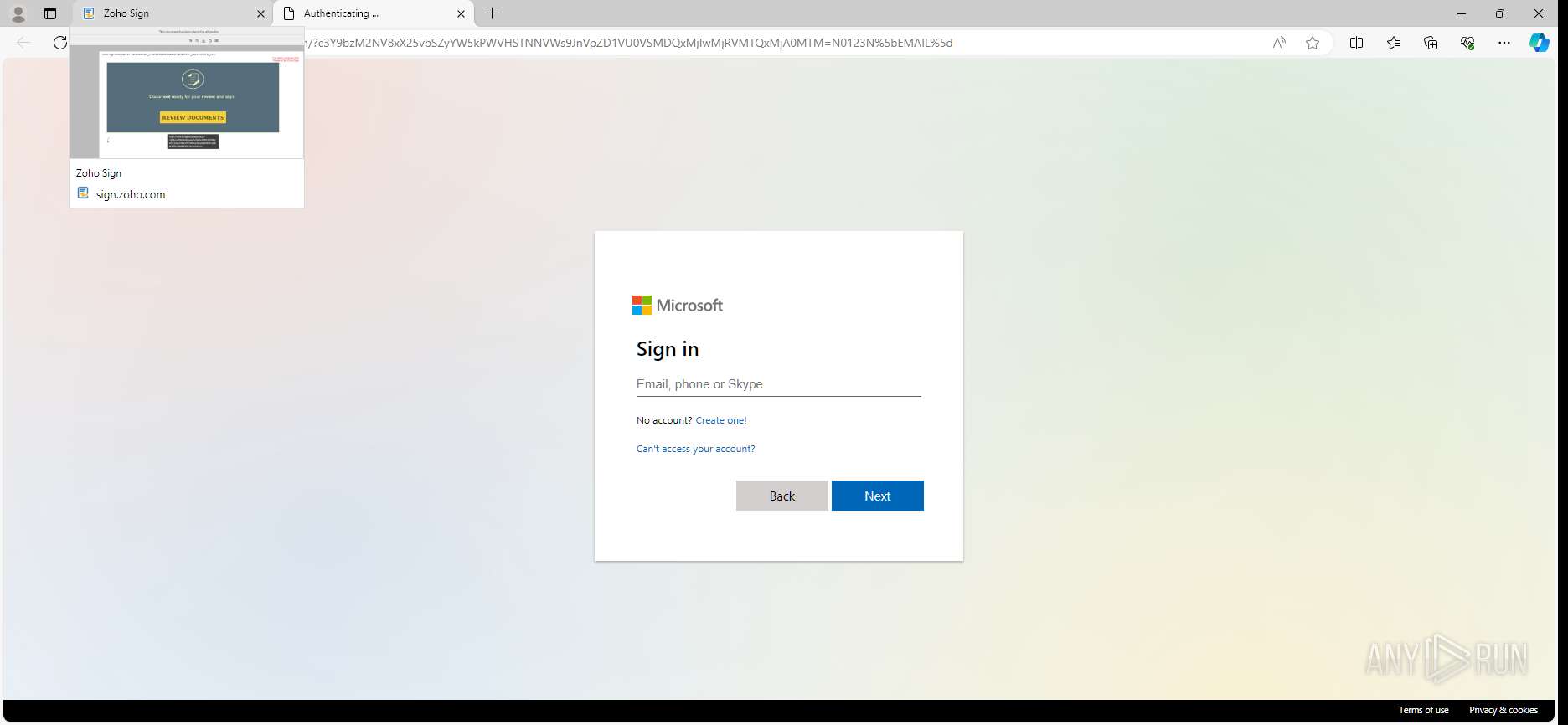
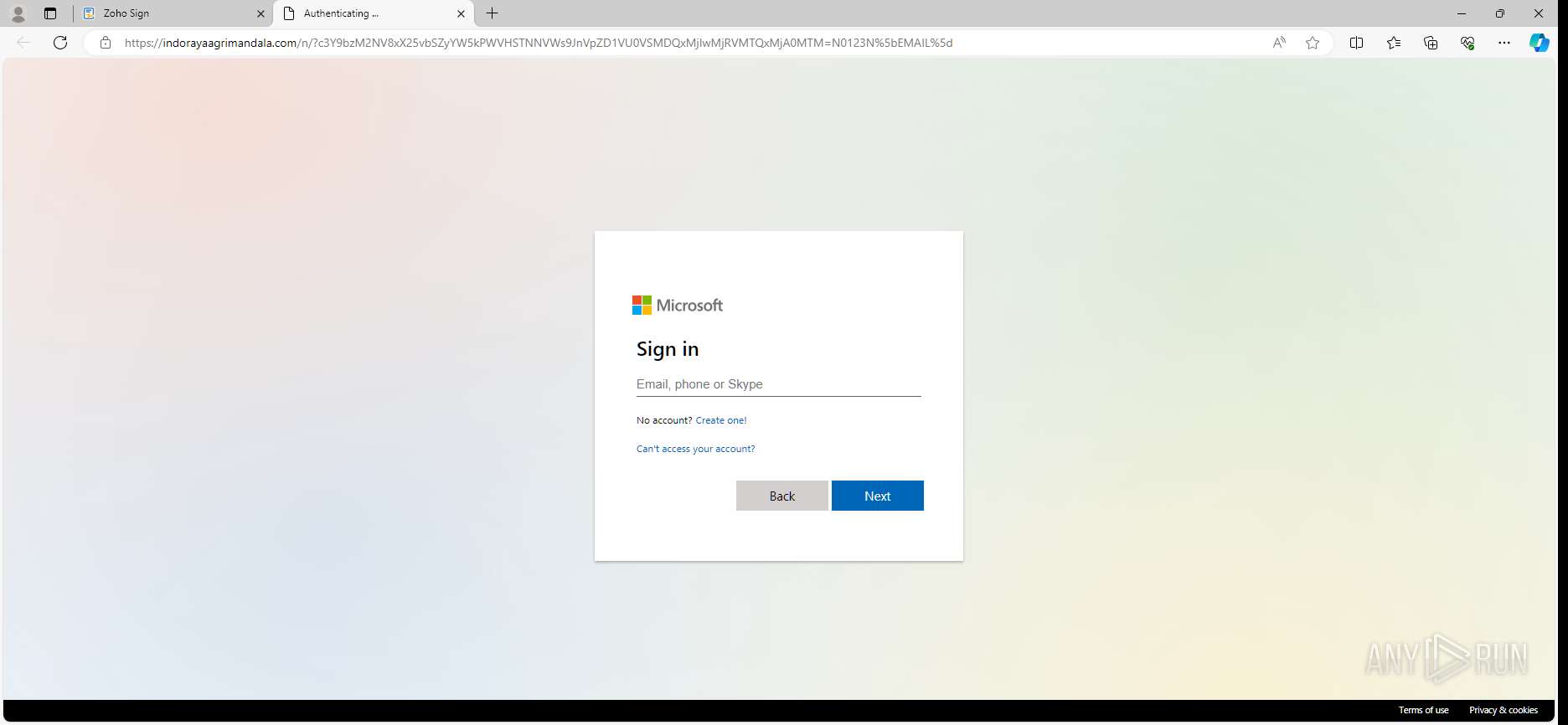
| URL: | https://sign.zoho.com/zsguest?locale=en&sign_id=234b4d535f4956239886eb78cb419adeabada92a845ee5c23ddebeb5dcceb267f90f0cf1f43fe835d91ac631b6a48d87807f5192bddf3c76899a91f4fe4ad56a0646129ead2be4ed0fe9c0c96ed6f9d650ffabb64034804c&action_type=SIGN |
| Full analysis: | https://app.any.run/tasks/2c1fee82-27d8-4f49-ae89-dfabfb58e8a7 |
| Verdict: | Malicious activity |
| Analysis date: | December 13, 2024, 20:16:42 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | E4D0ADC5BD54C705096EF7E6CFD21986 |
| SHA1: | E964AF1B0955A43BE895F5465650B5A5061718B1 |
| SHA256: | F3F2397E276C3B6246230EA6E53AFEC865D9B2E25FFFBA89DE5BB8A42348B291 |
| SSDEEP: | 3:N8B2fWGqQYAGOKQDRF/AyE/d02dSu0TXDnUUkFF7qQwcRNOWoQ2TGVABPclA1URQ:2dSGIhxEVNdMroUkP75forJiO1URy+2 |
MALICIOUS
PHISHING has been detected (SURICATA)
- msedge.exe (PID: 4792)
SUSPICIOUS
No suspicious indicators.INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
142
Monitored processes
1
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 4792 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=2604 --field-trial-handle=2320,i,16194277592197507296,15814343983252007256,262144 --variations-seed-version /prefetch:3 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | msedge.exe | |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 | ||||
Total events
0
Read events
0
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
52
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4792 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Cache\Cache_Data\f_0000c3 | binary | |
MD5:EDB740FDD46ECD983E980CF141AF73CB | SHA256:529AD85863AAF27FDF318C65E89BB62383EA361E6AB8AA2328184256F7301C3A | |||
| 4792 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Network\94f067fa-6ba6-40a1-9ef8-4eb12af62bbe.tmp | binary | |
MD5:ED74D0CC3CAB53CA501F3CD6C50FAA1A | SHA256:331BB0DA5A3BE7843A14503DA9547E7309F3631916C6112882FF36D75025E7EE | |||
| 4792 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Cache\Cache_Data\f_0000c1 | binary | |
MD5:7243ED6EAA5FCCEDF346B0F12C12537C | SHA256:61C03CBB835C0E3D069E081E12BBDDF7DFCD35CDD470C9011770DE8DD07085C4 | |||
| 4792 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Network\Network Persistent State | binary | |
MD5:ED74D0CC3CAB53CA501F3CD6C50FAA1A | SHA256:331BB0DA5A3BE7843A14503DA9547E7309F3631916C6112882FF36D75025E7EE | |||
| 4792 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Cache\Cache_Data\f_0000c2 | binary | |
MD5:2DA92D6D28E6AEBFAF92D918BC805A53 | SHA256:34493B13A023F823118078EEFDE94B416C14E9E074F4F5F7D483344913E7BB10 | |||
| 4792 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Cache\Cache_Data\f_0000ba | binary | |
MD5:7C03250F6D041DA6498DD14B40B3953D | SHA256:13CACBFC378A665E42C9E309DB42B95076DCCF8680F6F96D5892EABDD3A269DF | |||
| 4792 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Cache\Cache_Data\f_0000bb | binary | |
MD5:51F8035D941B096C86DF54A81D606A36 | SHA256:43BCE4CABF4EB46A8172CC2A00F6B11E7A6908DD6D08F58B4C822407FD1707BE | |||
| 4792 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Cache\Cache_Data\f_0000bf | binary | |
MD5:0C834AE5AD0F21A5FA64D035A37E8D96 | SHA256:4F84C8040046B224E339583F1A7265279D52E084143CD6B497691FDC4ABD613E | |||
| 4792 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Cache\Cache_Data\f_0000c6 | binary | |
MD5:EA125D825A967D049274ABC4F7B8056F | SHA256:00CF1770FBB9499B1F6FA164677CE569803D7BB8B97141E076414DF36D45F41B | |||
| 4792 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Network\Network Persistent State~RF2b72ec.TMP | binary | |
MD5:2A21453795942FD88CBB06714604B9FD | SHA256:5DFE0384325B556EE4B8668E502312B9BA6ADC298CD9213DDFA528CB959ADC06 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
115
TCP/UDP connections
94
DNS requests
61
Threats
17
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | HEAD | 200 | 23.218.208.109:443 | https://fs.microsoft.com/fs/windows/config.json | unknown | — | — | — |
5968 | svchost.exe | GET | 200 | 23.32.238.107:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4304 | MoUsoCoreWorker.exe | GET | 200 | 23.32.238.107:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 89.36.170.147:443 | https://static.zohocdn.com/sign/assets/embercli.d41d8cd98f00b204e9800998ecf8427e.css | unknown | — | — | — |
6440 | RUXIMICS.exe | GET | 200 | 23.32.238.107:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 204.141.43.101:443 | https://sign.zoho.com/zsguest?locale=en&sign_id=234b4d535f4956239886eb78cb419adeabada92a845ee5c23ddebeb5dcceb267f90f0cf1f43fe835d91ac631b6a48d87807f5192bddf3c76899a91f4fe4ad56a0646129ead2be4ed0fe9c0c96ed6f9d650ffabb64034804c&action_type=SIGN | unknown | html | 64.1 Kb | whitelisted |
— | — | GET | 200 | 89.36.170.147:443 | https://static.zohocdn.com/sign/assets/sign_util.27ef99e12eb7c24712a2093a40589373.js | unknown | binary | 8.31 Kb | whitelisted |
— | — | GET | 200 | 89.36.170.147:443 | https://static.zohocdn.com/sign/assets/style-max-767.b87cc62956d08864c4c24729d88e2544.css | unknown | text | 26.8 Kb | whitelisted |
— | — | GET | 200 | 89.36.170.147:443 | https://static.zohocdn.com/sign/assets/security_regex.730010e2b046f584fd4eafed572d4656.js | unknown | text | 1.42 Kb | whitelisted |
5968 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6440 | RUXIMICS.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4304 | MoUsoCoreWorker.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
5968 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4792 | msedge.exe | 52.182.143.211:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
— | — | 224.0.0.251:5353 | — | — | — | unknown |
5988 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4792 | msedge.exe | 204.141.43.101:443 | sign.zoho.com | ZOHO-AS | US | whitelisted |
7108 | svchost.exe | 23.218.208.109:443 | fs.microsoft.com | AKAMAI-AS | DE | whitelisted |
4792 | msedge.exe | 89.36.170.147:443 | static.zohocdn.com | Computerline GmbH | CH | whitelisted |
4792 | msedge.exe | 184.86.251.21:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
sign.zoho.com |
| whitelisted |
fs.microsoft.com |
| whitelisted |
static.zohocdn.com |
| whitelisted |
www.bing.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Bidirectional and low-latency communication CDN (cdn .socket .io) |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Bidirectional and low-latency communication CDN (cdn .socket .io) |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Request to Azure content delivery network (aadcdn .msauth .net) |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Request to Azure content delivery network (aadcdn .msauth .net) |
— | — | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Domain chain identified as Phishing (socketaad) |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Request to Azure content delivery network (aadcdn .msauth .net) |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Request to Azure content delivery network (aadcdn .msauth .net) |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Bidirectional and low-latency communication CDN (cdn .socket .io) |