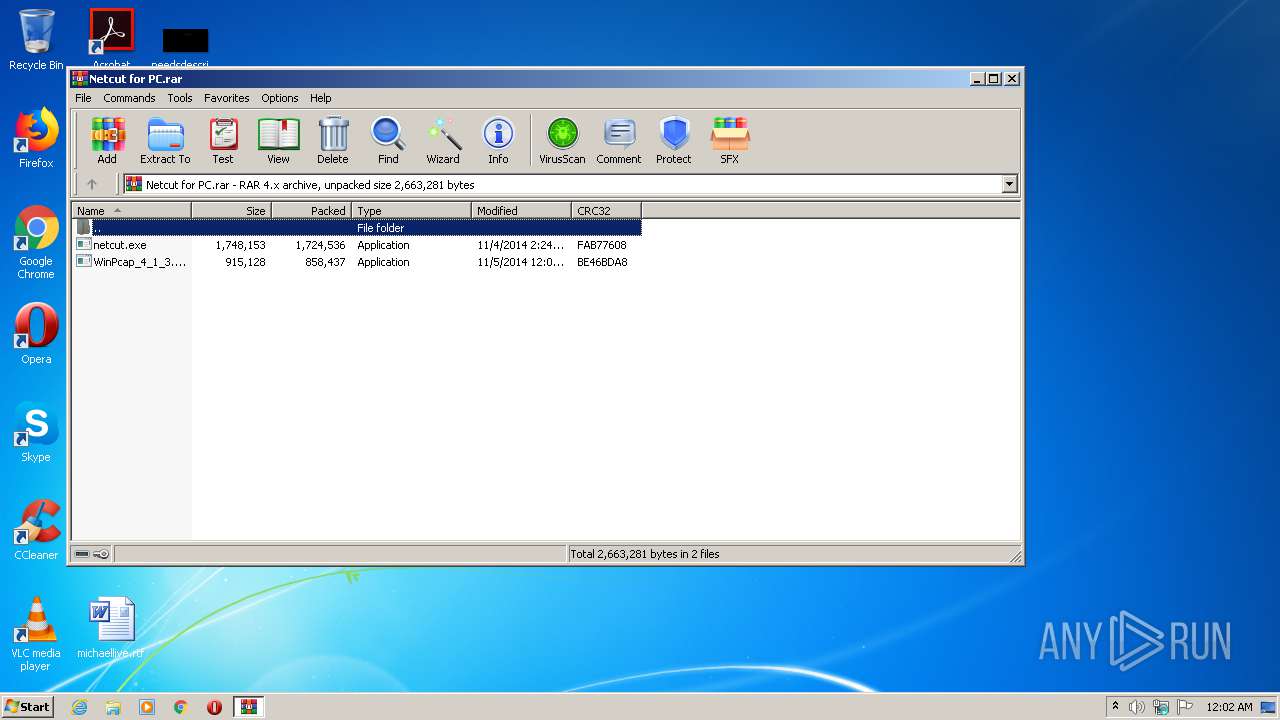
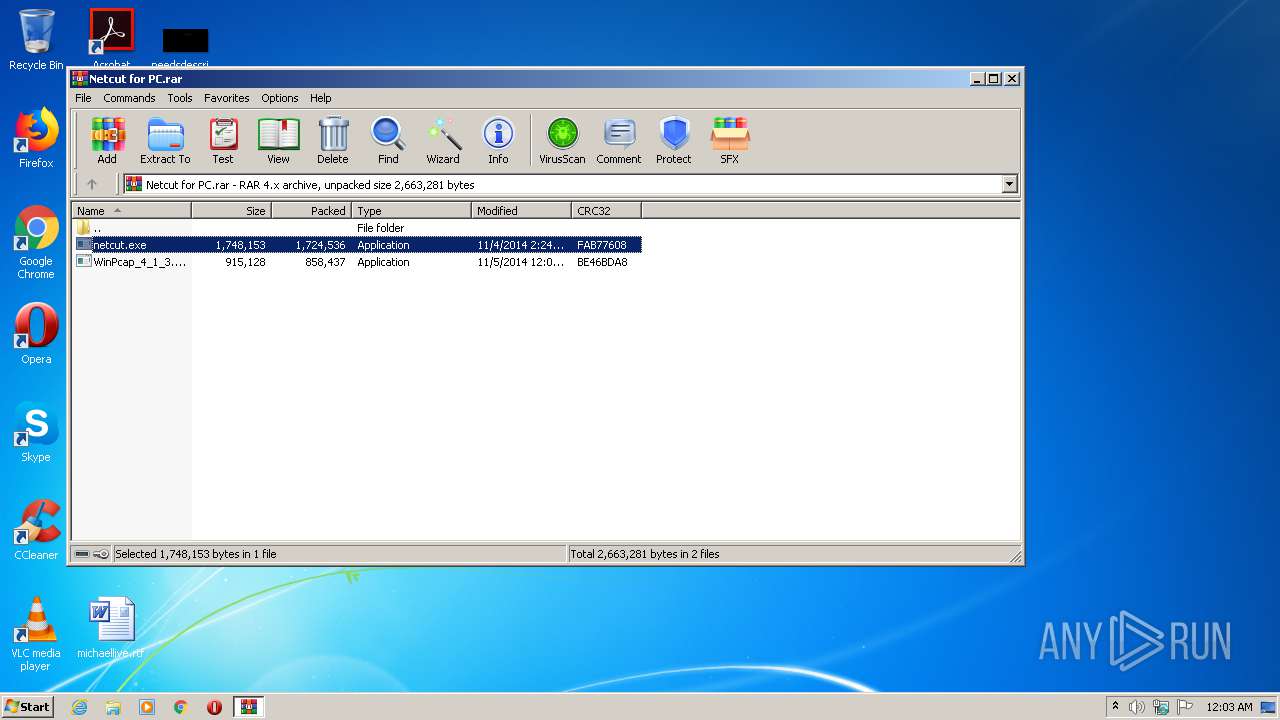
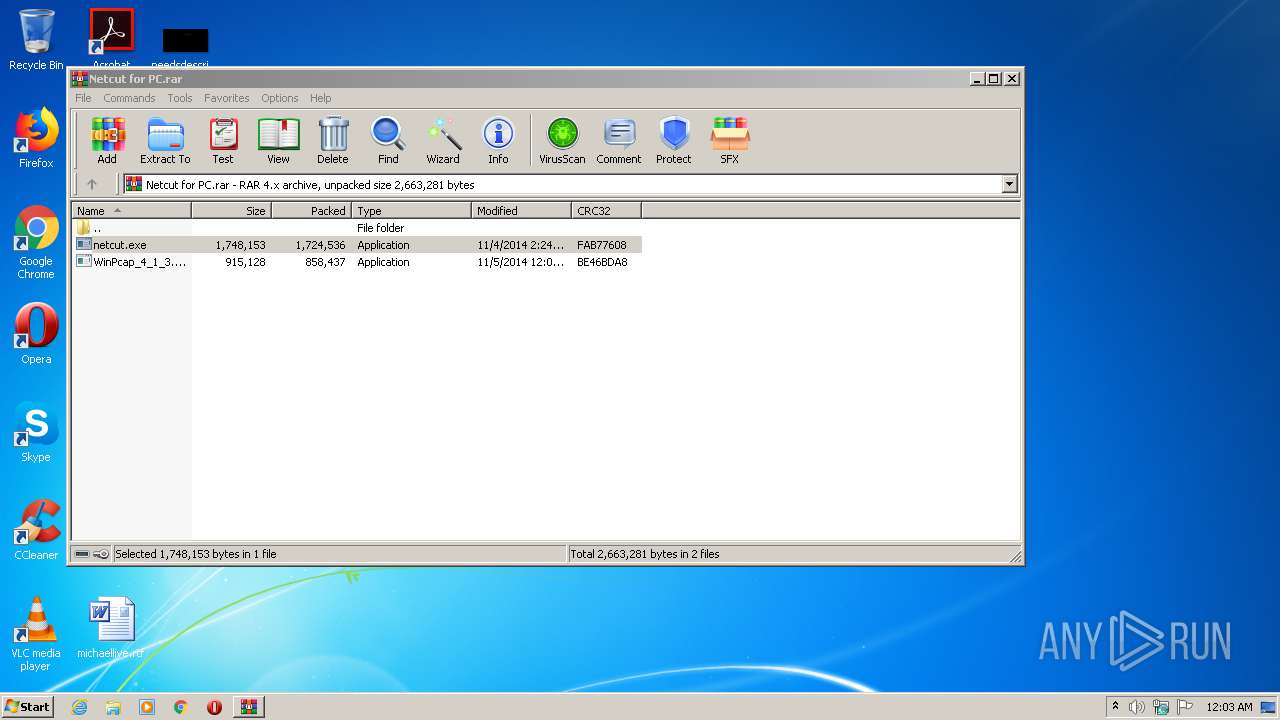
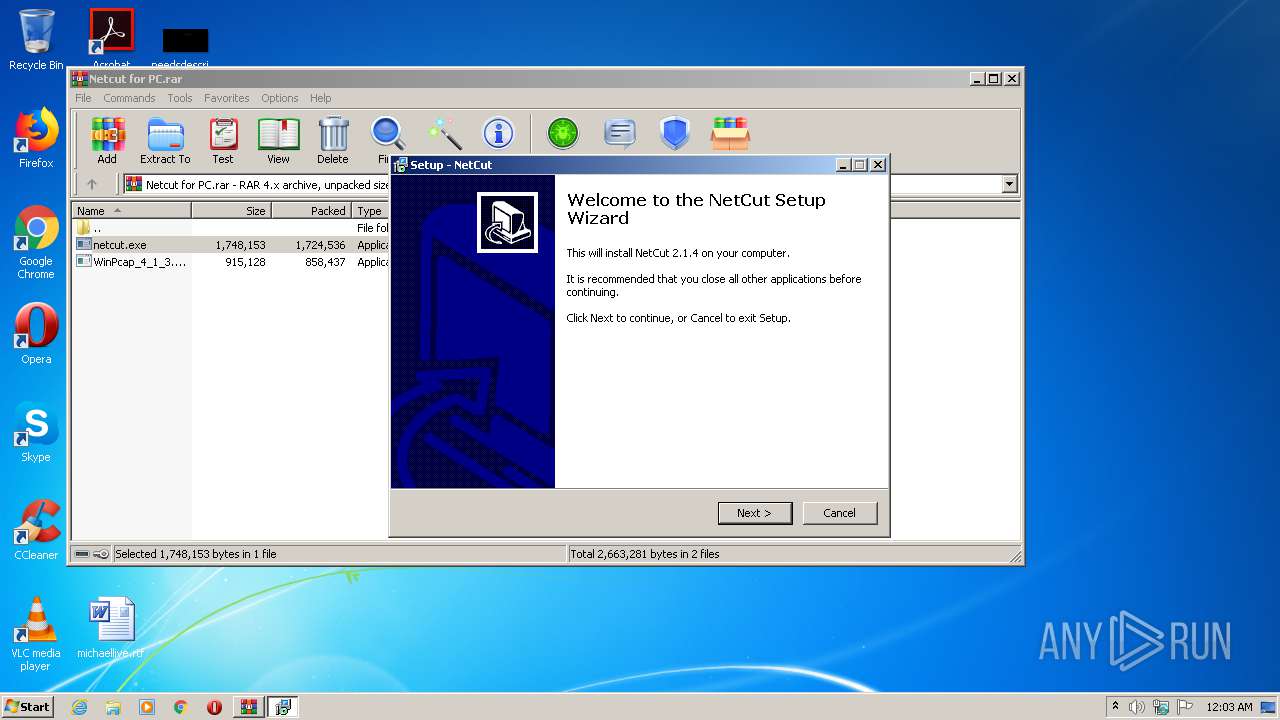
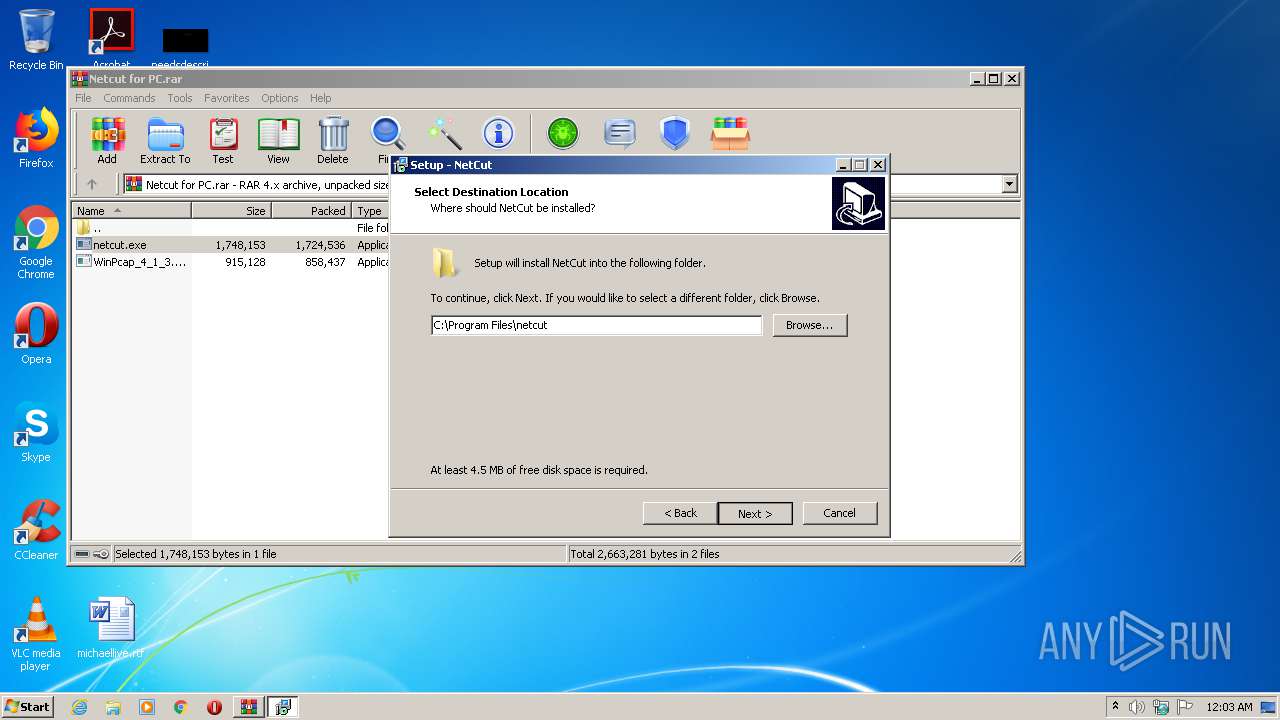
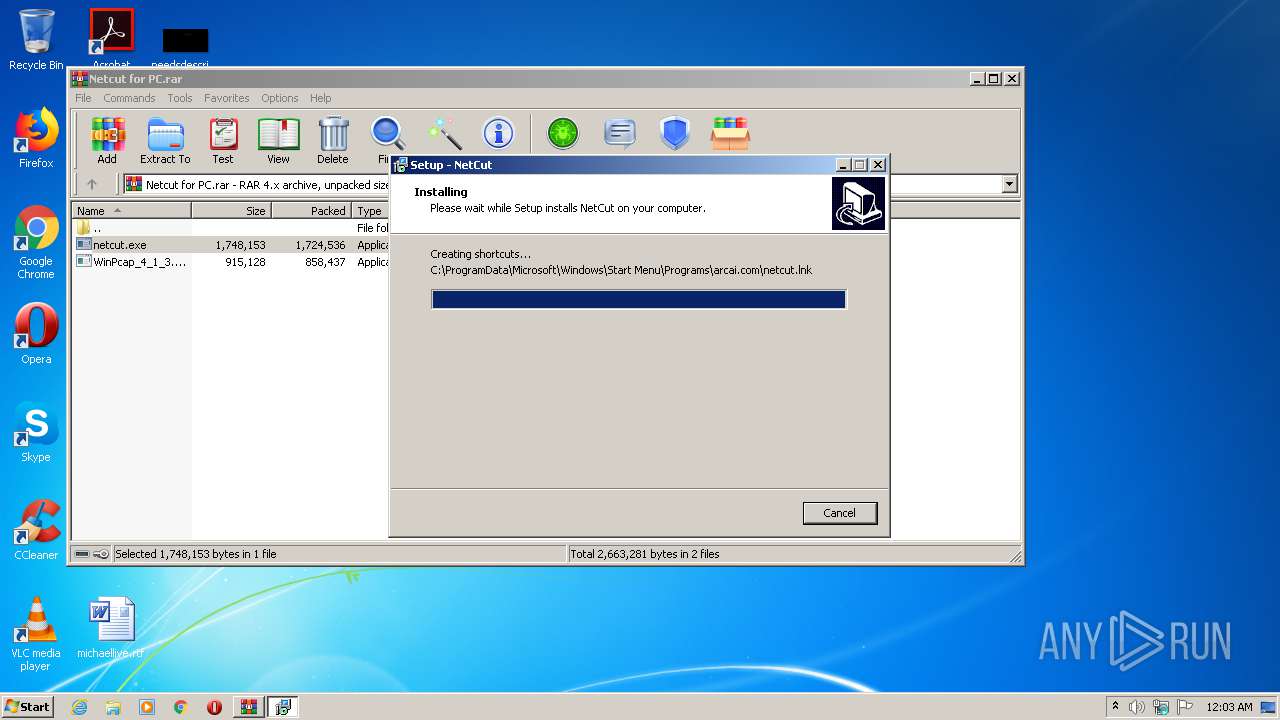
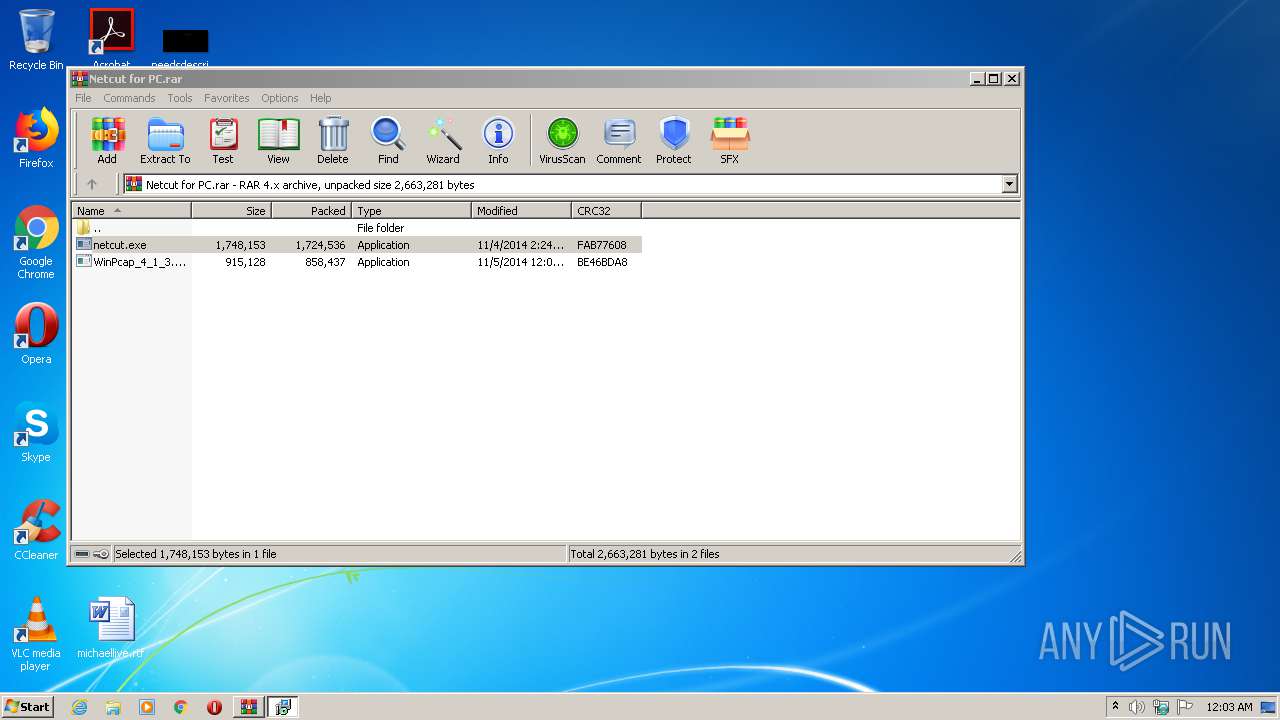
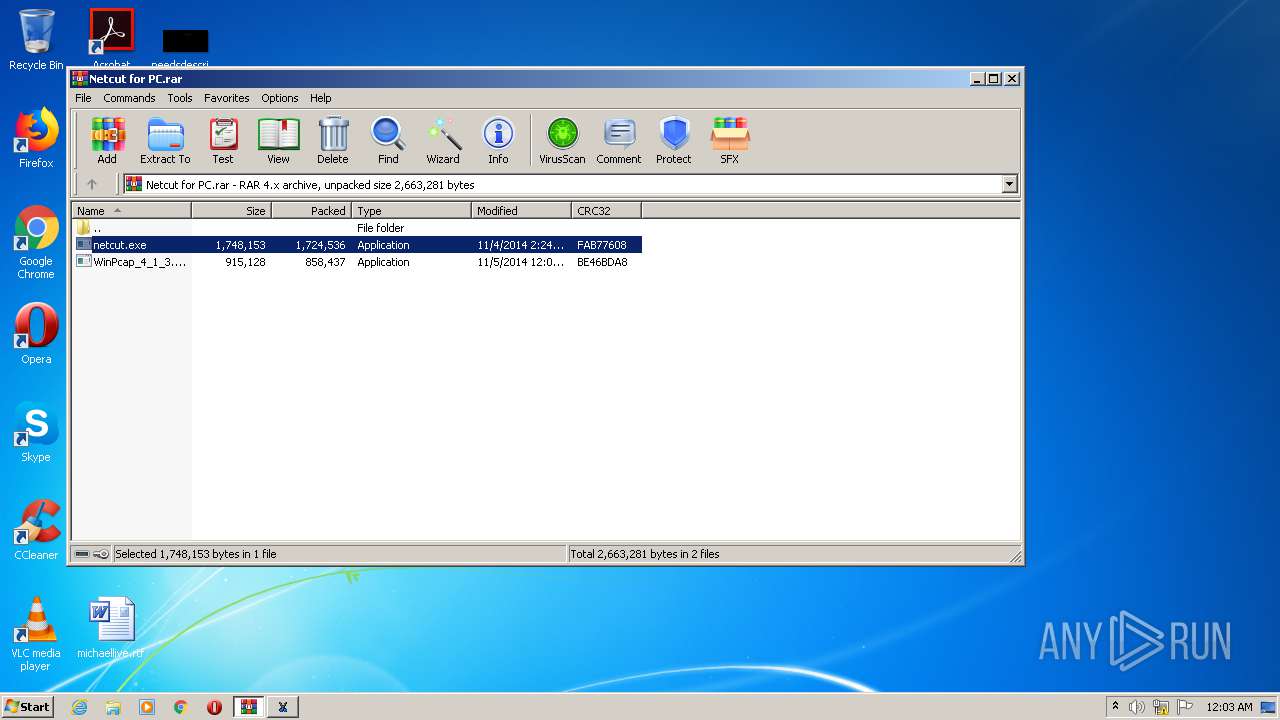
| File name: | Netcut for PC.rar |
| Full analysis: | https://app.any.run/tasks/278a491e-2150-4155-9d00-a02f2668d04f |
| Verdict: | Malicious activity |
| Analysis date: | July 23, 2020, 23:02:07 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32 |
| MD5: | 2B08BF22CF4BDEF87437725E420684F8 |
| SHA1: | 98339B487147A4188E5FBDDEEA9EDDC85B87F96F |
| SHA256: | F3CCBC53DAD6FFF04EE0A79E73ECB5594804DC92B04B796F24116C698E387D00 |
| SSDEEP: | 49152:FB1ym1Na5jmnXCsF/qj4ZRIMNcUnQo9aKOc74rFFARFiEr9IHBp:H19Na8F/HkMNcoQCaKO/AziBp |
MALICIOUS
Application was dropped or rewritten from another process
- netcut.exe (PID: 3016)
- AIPS.exe (PID: 2748)
- AIPS.exe (PID: 3412)
- winpcap.exe (PID: 1072)
- netcut.exe (PID: 2196)
- AIPS.exe (PID: 1836)
- netcut.exe (PID: 1752)
Registers / Runs the DLL via REGSVR32.EXE
- netcut.tmp (PID: 3120)
Changes the autorun value in the registry
- netcut.tmp (PID: 3120)
Loads dropped or rewritten executable
- regsvr32.exe (PID: 2204)
- winpcap.exe (PID: 1072)
- netcut.exe (PID: 2196)
- regsvr32.exe (PID: 2752)
Starts NET.EXE for service management
- winpcap.exe (PID: 1072)
SUSPICIOUS
Executable content was dropped or overwritten
- netcut.exe (PID: 3016)
- WinRAR.exe (PID: 952)
- netcut.exe (PID: 1752)
- netcut.tmp (PID: 3120)
- winpcap.exe (PID: 1072)
Creates files in the Windows directory
- netcut.tmp (PID: 3120)
- winpcap.exe (PID: 1072)
Creates files in the user directory
- netcut.tmp (PID: 3120)
Executed as Windows Service
- AIPS.exe (PID: 3412)
Reads Internet Cache Settings
- winpcap.exe (PID: 1072)
Creates files in the program directory
- winpcap.exe (PID: 1072)
Reads internet explorer settings
- winpcap.exe (PID: 1072)
Creates or modifies windows services
- winpcap.exe (PID: 1072)
Creates files in the driver directory
- winpcap.exe (PID: 1072)
Creates a software uninstall entry
- winpcap.exe (PID: 1072)
INFO
Application was dropped or rewritten from another process
- netcut.tmp (PID: 3972)
- netcut.tmp (PID: 3120)
Loads dropped or rewritten executable
- netcut.tmp (PID: 3120)
Creates files in the program directory
- netcut.tmp (PID: 3120)
Reads the hosts file
- AIPS.exe (PID: 2748)
- AIPS.exe (PID: 1836)
- AIPS.exe (PID: 3412)
- netcut.exe (PID: 2196)
Creates a software uninstall entry
- netcut.tmp (PID: 3120)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| CompressedSize: | 1724572 |
|---|---|
| UncompressedSize: | 1748153 |
| OperatingSystem: | Win32 |
| ModifyDate: | 2014:11:04 14:24:12 |
| PackingMethod: | Normal |
| ArchivedFileName: | netcut.exe |
Total processes
55
Monitored processes
14
Malicious processes
6
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 784 | net start npf | C:\Windows\system32\net.exe | — | winpcap.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 952 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Netcut for PC.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
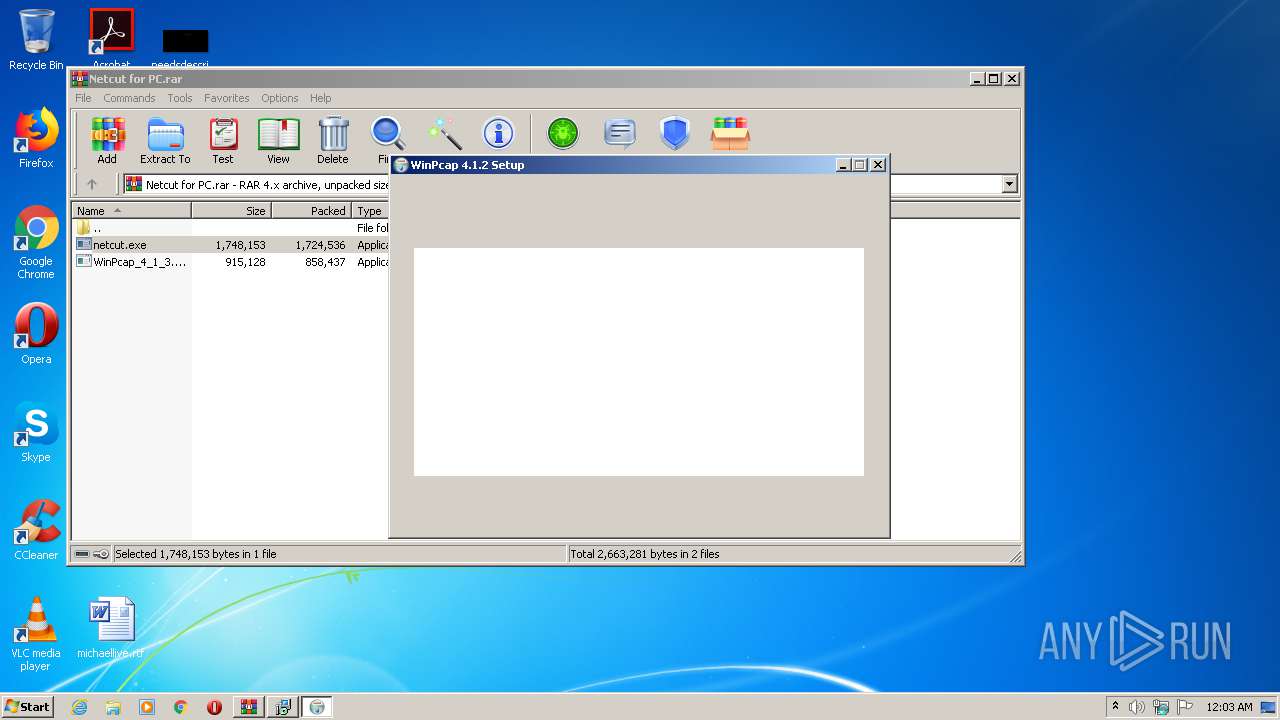
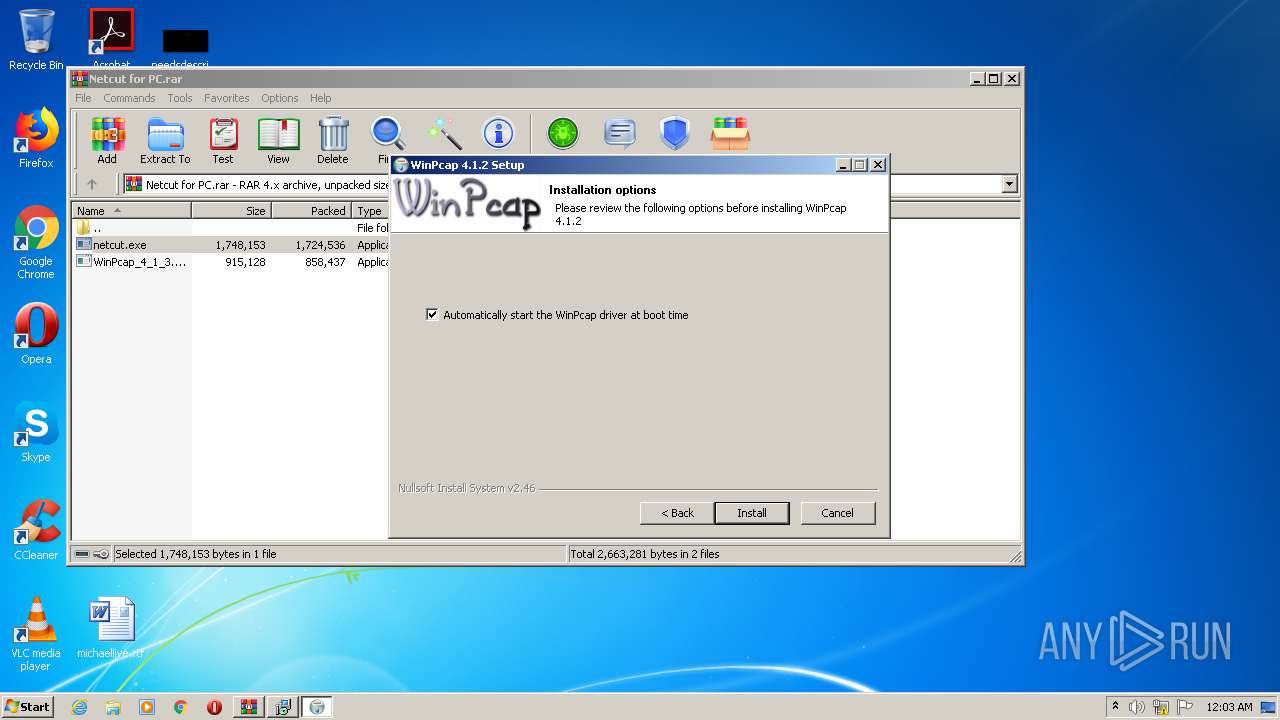
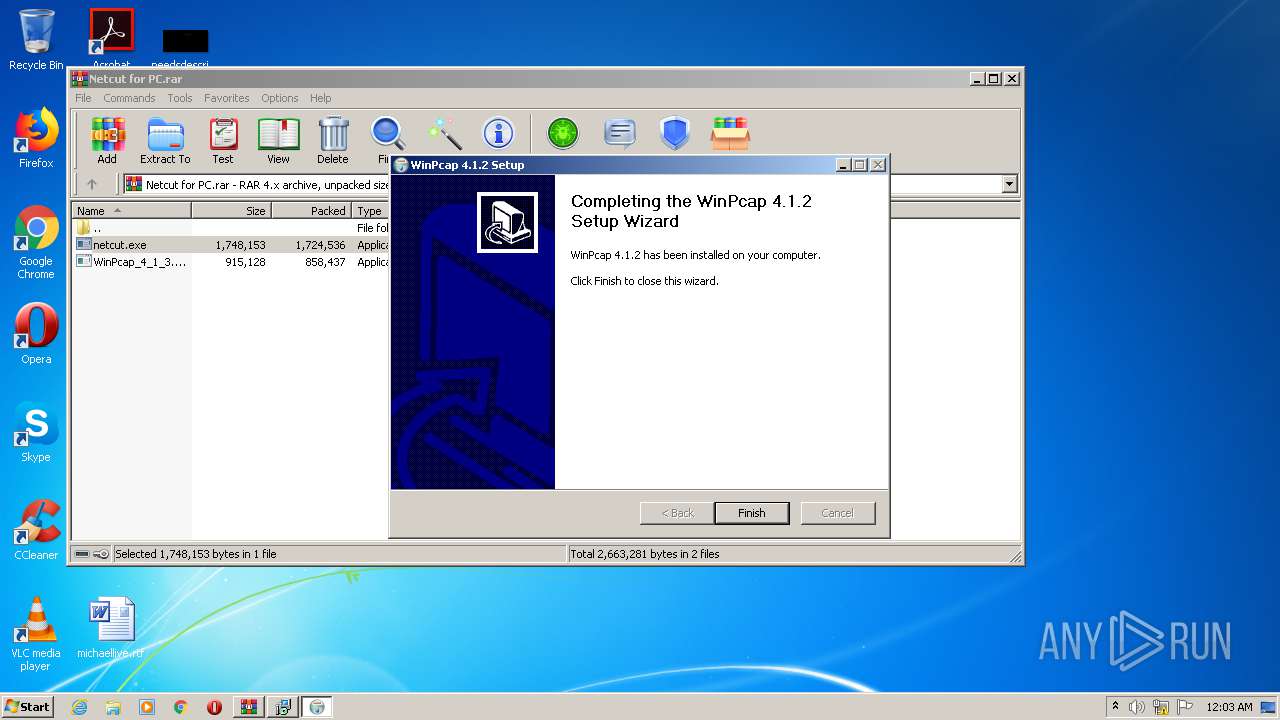
| 1072 | "C:\Program Files\netcut\winpcap.exe" | C:\Program Files\netcut\winpcap.exe | netcut.tmp | ||||||||||||
User: admin Company: CACE Technologies, Inc. Integrity Level: HIGH Description: WinPcap 4.1.2 installer Exit code: 0 Version: 4.1.0.2001 Modules
| |||||||||||||||
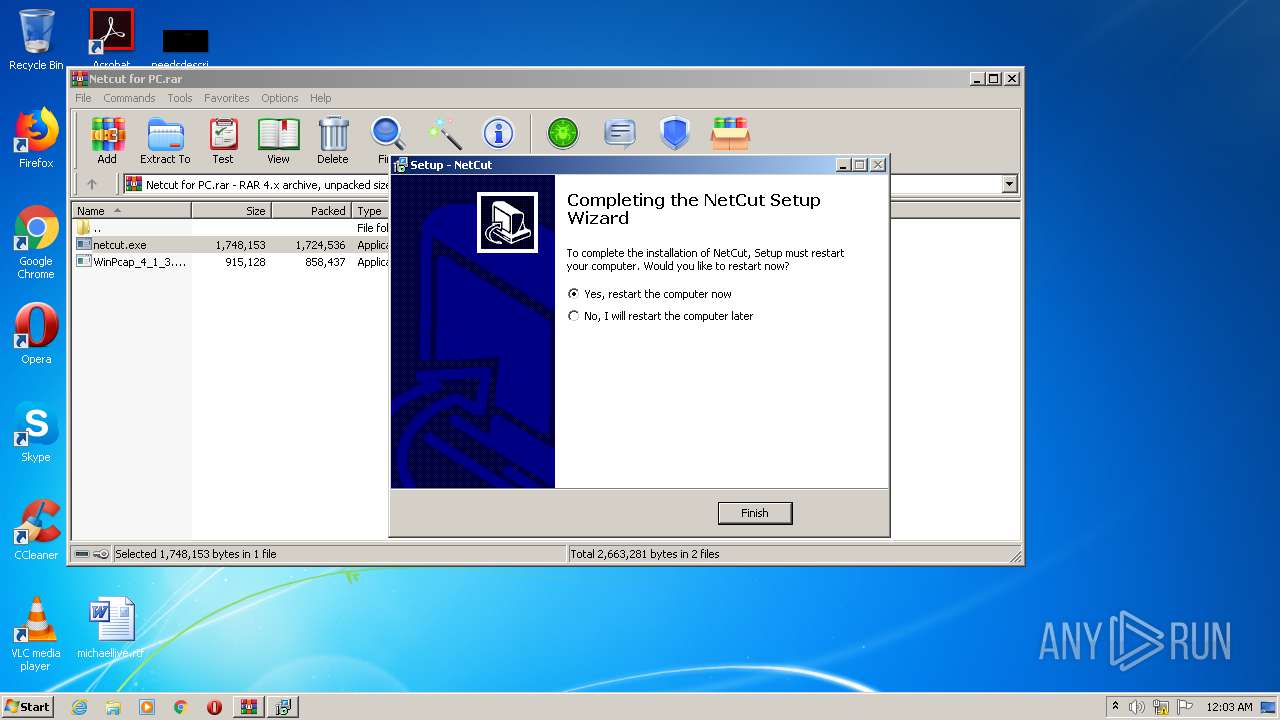
| 1752 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa952.21773\netcut.exe" /SPAWNWND=$2017A /NOTIFYWND=$2015A | C:\Users\admin\AppData\Local\Temp\Rar$EXa952.21773\netcut.exe | netcut.tmp | ||||||||||||
User: admin Company: arcai.com Integrity Level: HIGH Description: NetCut Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 1836 | "C:\Program Files\netcut\services\AIPS.exe" install | C:\Program Files\netcut\services\AIPS.exe | — | netcut.tmp | |||||||||||
User: admin Company: Arcai.com Integrity Level: HIGH Description: Arp Intelligent Protection Service Exit code: 1 Version: 214 Modules
| |||||||||||||||
| 2196 | "C:\Program Files\netcut\netcut.exe" | C:\Program Files\netcut\netcut.exe | — | netcut.tmp | |||||||||||
User: admin Company: Arcai.com Integrity Level: HIGH Description: NetCut Arp Spoof Application Exit code: 0 Version: 214 Modules
| |||||||||||||||
| 2204 | "C:\Windows\system32\regsvr32.exe" /s actskn43.ocx | C:\Windows\system32\regsvr32.exe | — | netcut.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2216 | C:\Windows\system32\net1 start npf | C:\Windows\system32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2748 | "C:\Program Files\netcut\services\AIPS.exe" setup netcut "\"C:\Program Files\netcut\netcut.exe\"" | C:\Program Files\netcut\services\AIPS.exe | — | netcut.tmp | |||||||||||
User: admin Company: Arcai.com Integrity Level: HIGH Description: Arp Intelligent Protection Service Exit code: 0 Version: 214 Modules
| |||||||||||||||
| 2752 | "C:\Windows\system32\regsvr32.exe" /s "C:\Windows\system32\actskn43.ocx" | C:\Windows\system32\regsvr32.exe | — | netcut.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 484
Read events
1 172
Write events
231
Delete events
81
Modification events
| (PID) Process: | (952) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (952) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (952) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\132\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (952) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Netcut for PC.rar | |||
| (PID) Process: | (952) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (952) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (952) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (952) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (952) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (952) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
26
Suspicious files
1
Text files
44
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3120 | netcut.tmp | C:\Program Files\netcut\is-DI5DT.tmp | — | |
MD5:— | SHA256:— | |||
| 3120 | netcut.tmp | C:\Program Files\netcut\is-26EGL.tmp | — | |
MD5:— | SHA256:— | |||
| 3120 | netcut.tmp | C:\Program Files\netcut\is-MDLJN.tmp | — | |
MD5:— | SHA256:— | |||
| 3120 | netcut.tmp | C:\Program Files\netcut\services\is-VO1D9.tmp | — | |
MD5:— | SHA256:— | |||
| 3120 | netcut.tmp | C:\Program Files\netcut\services\is-PTE0D.tmp | — | |
MD5:— | SHA256:— | |||
| 3120 | netcut.tmp | C:\Program Files\netcut\is-FBD08.tmp | — | |
MD5:— | SHA256:— | |||
| 3120 | netcut.tmp | C:\Windows\system32\is-ROG0M.tmp | — | |
MD5:— | SHA256:— | |||
| 3120 | netcut.tmp | C:\Program Files\netcut\is-T7F94.tmp | — | |
MD5:— | SHA256:— | |||
| 3120 | netcut.tmp | C:\Program Files\netcut\is-G44IG.tmp | — | |
MD5:— | SHA256:— | |||
| 952 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa952.21773\netcut.exe | executable | |
MD5:59DA0505B981F62DF58C541E51C0BE54 | SHA256:369307CC4B4DE620A57961D3863F2A907A1583C03D8BCBACC03293C9F01ABDB4 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report