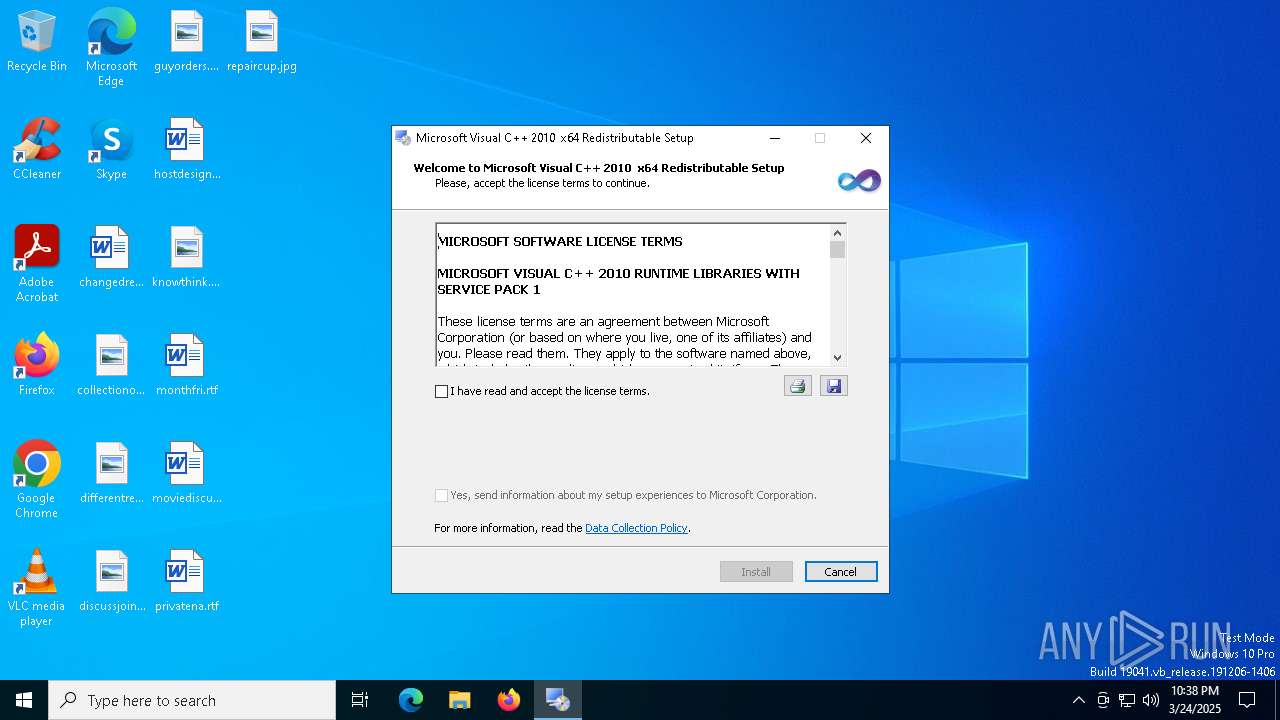
| File name: | vcredist_x64.exe |
| Full analysis: | https://app.any.run/tasks/c92b9f51-ca7c-4b54-a9e2-11e6a7fc0df0 |
| Verdict: | Malicious activity |
| Analysis date: | March 24, 2025, 22:37:54 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 3 sections |
| MD5: | 02A945866CD1B13E2375C024F0E18301 |
| SHA1: | 8691972F0A5BF919701AC3B80FB693FC715420C2 |
| SHA256: | F3B7A76D84D23F91957AA18456A14B4E90609E4CE8194C5653384ED38DADA6F3 |
| SSDEEP: | 98304:rLpCATIvI3UvnsDh1FJTbZVwu2mS6ee24/xUieZ7Ga67D+fX9hqSTwXE/arm9xnp:WiwHir3X28Pzy6mouQOV2wOS |
MALICIOUS
No malicious indicators.SUSPICIOUS
Starts a Microsoft application from unusual location
- vcredist_x64.exe (PID: 4880)
- vcredist_x64.exe (PID: 6268)
Process drops legitimate windows executable
- vcredist_x64.exe (PID: 6268)
- FontLab-8-Win64-Install-8950.tmp (PID: 7960)
Executable content was dropped or overwritten
- vcredist_x64.exe (PID: 6268)
- FontLab-8-Win64-Install-8950.exe (PID: 3800)
- FontLab-8-Win64-Install-8950.tmp (PID: 7960)
Creates file in the systems drive root
- vcredist_x64.exe (PID: 6268)
Reads security settings of Internet Explorer
- FontLab-8-Win64-Install-8950.tmp (PID: 9116)
- ShellExperienceHost.exe (PID: 5132)
Reads the Windows owner or organization settings
- FontLab-8-Win64-Install-8950.tmp (PID: 7960)
The process drops C-runtime libraries
- FontLab-8-Win64-Install-8950.tmp (PID: 7960)
Process drops python dynamic module
- FontLab-8-Win64-Install-8950.tmp (PID: 7960)
INFO
The sample compiled with english language support
- vcredist_x64.exe (PID: 6268)
- FontLab-8-Win64-Install-8950.tmp (PID: 7960)
Reads the machine GUID from the registry
- vcredist_x64.exe (PID: 6268)
Checks supported languages
- vcredist_x64.exe (PID: 6268)
- Setup.exe (PID: 6972)
- FontLab-8-Win64-Install-8950.tmp (PID: 9116)
- ShellExperienceHost.exe (PID: 5132)
- FontLab-8-Win64-Install-8950.exe (PID: 3800)
- FontLab-8-Win64-Install-8950.tmp (PID: 7960)
The sample compiled with japanese language support
- vcredist_x64.exe (PID: 6268)
The sample compiled with german language support
- vcredist_x64.exe (PID: 6268)
The sample compiled with russian language support
- vcredist_x64.exe (PID: 6268)
Reads the computer name
- vcredist_x64.exe (PID: 6268)
- Setup.exe (PID: 6972)
- ShellExperienceHost.exe (PID: 5132)
- FontLab-8-Win64-Install-8950.tmp (PID: 9116)
- FontLab-8-Win64-Install-8950.tmp (PID: 7960)
The sample compiled with korean language support
- vcredist_x64.exe (PID: 6268)
The sample compiled with spanish language support
- vcredist_x64.exe (PID: 6268)
The sample compiled with chinese language support
- vcredist_x64.exe (PID: 6268)
The sample compiled with Italian language support
- vcredist_x64.exe (PID: 6268)
Create files in a temporary directory
- Setup.exe (PID: 6972)
- FontLab-8-Win64-Install-8950.exe (PID: 3800)
- FontLab-8-Win64-Install-8950.tmp (PID: 7960)
The sample compiled with french language support
- vcredist_x64.exe (PID: 6268)
Reads security settings of Internet Explorer
- BackgroundTransferHost.exe (PID: 8084)
- BackgroundTransferHost.exe (PID: 1240)
- BackgroundTransferHost.exe (PID: 8164)
- BackgroundTransferHost.exe (PID: 9196)
- BackgroundTransferHost.exe (PID: 8696)
Checks proxy server information
- BackgroundTransferHost.exe (PID: 1240)
- slui.exe (PID: 7232)
Reads CPU info
- Setup.exe (PID: 6972)
Creates files or folders in the user directory
- BackgroundTransferHost.exe (PID: 1240)
- FontLab-8-Win64-Install-8950.tmp (PID: 7960)
Reads the software policy settings
- BackgroundTransferHost.exe (PID: 1240)
- slui.exe (PID: 5776)
- slui.exe (PID: 7232)
Process checks computer location settings
- FontLab-8-Win64-Install-8950.tmp (PID: 9116)
Creates files in the program directory
- FontLab-8-Win64-Install-8950.tmp (PID: 7960)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (35.8) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (31.7) |
| .scr | | | Windows screen saver (15) |
| .dll | | | Win32 Dynamic Link Library (generic) (7.5) |
| .exe | | | Win32 Executable (generic) (5.1) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2007:12:21 07:26:24+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit, Removable run from swap, Net run from swap |
| PEType: | PE32 |
| LinkerVersion: | 7.1 |
| CodeSize: | 34304 |
| InitializedDataSize: | 6656 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x63ff |
| OSVersion: | 5.2 |
| ImageVersion: | 5.2 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 10.0.40219.325 |
| ProductVersionNumber: | 10.0.40219.325 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Microsoft Corporation |
| FileDescription: | Microsoft Visual C++ 2010 x64 Redistributable Setup |
| FileVersion: | 10.0.40219.325 |
| InternalName: | vcredist_x64.exe |
| LegalCopyright: | © Microsoft Corporation. All rights reserved. |
| OriginalFileName: | vcredist_x64.exe |
| ProductName: | Microsoft Visual C++ 2010 x64 Redistributable |
| ProductVersion: | 10.0.40219.325 |
Total processes
247
Monitored processes
15
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 664 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1240 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
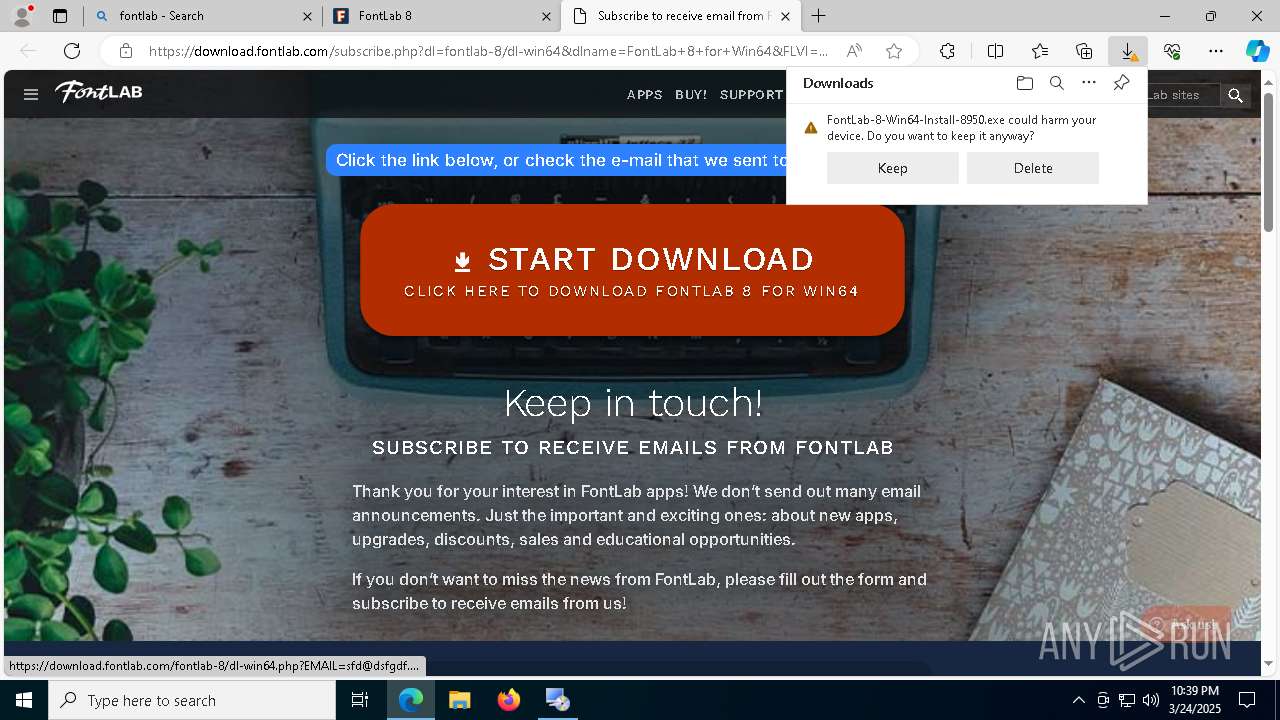
| 3800 | "C:\Users\admin\Downloads\FontLab-8-Win64-Install-8950.exe" /SPAWNWND=$20314 /NOTIFYWND=$3027A | C:\Users\admin\Downloads\FontLab-8-Win64-Install-8950.exe | FontLab-8-Win64-Install-8950.tmp | ||||||||||||
User: admin Company: Fontlab Ltd. Integrity Level: HIGH Description: FontLab 8 (64-bit) Setup Version: 8.9.5.0 Modules
| |||||||||||||||
| 4880 | "C:\Users\admin\AppData\Local\Temp\vcredist_x64.exe" | C:\Users\admin\AppData\Local\Temp\vcredist_x64.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Visual C++ 2010 x64 Redistributable Setup Exit code: 3221226540 Version: 10.0.40219.325 Modules
| |||||||||||||||
| 5132 | "C:\WINDOWS\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe" -ServerName:App.AppXtk181tbxbce2qsex02s8tw7hfxa9xb3t.mca | C:\Windows\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Shell Experience Host Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5776 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6268 | "C:\Users\admin\AppData\Local\Temp\vcredist_x64.exe" | C:\Users\admin\AppData\Local\Temp\vcredist_x64.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Visual C++ 2010 x64 Redistributable Setup Version: 10.0.40219.325 Modules
| |||||||||||||||
| 6972 | c:\b29d9ca21c65f2b9b070d1\Setup.exe | C:\b29d9ca21c65f2b9b070d1\Setup.exe | — | vcredist_x64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Setup Installer Version: 10.0.40219.325 built by: SP1LDR Modules
| |||||||||||||||
| 7232 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7960 | "C:\Users\admin\AppData\Local\Temp\is-71F2I.tmp\FontLab-8-Win64-Install-8950.tmp" /SL5="$7014E,109302015,900608,C:\Users\admin\Downloads\FontLab-8-Win64-Install-8950.exe" /SPAWNWND=$20314 /NOTIFYWND=$3027A | C:\Users\admin\AppData\Local\Temp\is-71F2I.tmp\FontLab-8-Win64-Install-8950.tmp | FontLab-8-Win64-Install-8950.exe | ||||||||||||
User: admin Company: Fontlab Ltd. Integrity Level: HIGH Description: Setup/Uninstall Version: 51.1052.0.0 Modules
| |||||||||||||||
Total events
4 265
Read events
4 248
Write events
17
Delete events
0
Modification events
| (PID) Process: | (8084) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (8084) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (8084) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1240) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1240) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1240) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (9196) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (9196) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (9196) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (8164) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
Executable files
185
Suspicious files
31
Text files
2 533
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6268 | vcredist_x64.exe | C:\b29d9ca21c65f2b9b070d1\SplashScreen.bmp | image | |
MD5:43B254D97B4FB6F9974AD3F935762C55 | SHA256:91A21EBA9F5E1674919EE3B36EFA99714CFB919491423D888CB56C0F25845969 | |||
| 6268 | vcredist_x64.exe | C:\b29d9ca21c65f2b9b070d1\ParameterInfo.xml | xml | |
MD5:5674D0BC3F4CDF572B9263332B2942C7 | SHA256:CBE5B9A27B1DDE70A9040790EAFF798E6534FF1EC2B4702CC4BE7221D18D2182 | |||
| 6268 | vcredist_x64.exe | C:\b29d9ca21c65f2b9b070d1\DisplayIcon.ico | image | |
MD5:F9657D290048E169FFABBBB9C7412BE0 | SHA256:B74AD253B9B8F9FCADE725336509143828EE739CC2B24782BE3ECFF26F229160 | |||
| 6268 | vcredist_x64.exe | C:\b29d9ca21c65f2b9b070d1\Strings.xml | xml | |
MD5:332ADF643747297B9BFA9527EAEFE084 | SHA256:E49545FEEAE22198728AD04236E31E02035AF7CC4D68E10CBECFFD08669CBECA | |||
| 6268 | vcredist_x64.exe | C:\b29d9ca21c65f2b9b070d1\SetupUi.xsd | xml | |
MD5:2FADD9E618EFF8175F2A6E8B95C0CACC | SHA256:222211E8F512EDF97D78BC93E1F271C922D5E91FA899E092B4A096776A704093 | |||
| 6268 | vcredist_x64.exe | C:\b29d9ca21c65f2b9b070d1\header.bmp | image | |
MD5:3AD1A8C3B96993BCDF45244BE2C00EEF | SHA256:133B86A4F1C67A159167489FDAEAB765BFA1050C23A7AE6D5C517188FB45F94A | |||
| 6268 | vcredist_x64.exe | C:\b29d9ca21c65f2b9b070d1\SetupUi.dll | executable | |
MD5:0D214CED87BF0B55883359160A68DACB | SHA256:29CF99D7E67B4C54BAFD109577A385387A39301BCDEC8AE4BA1A8A0044306713 | |||
| 6268 | vcredist_x64.exe | C:\b29d9ca21c65f2b9b070d1\sqmapi.dll | executable | |
MD5:3F0363B40376047EFF6A9B97D633B750 | SHA256:BD6395A58F55A8B1F4063E813CE7438F695B9B086BB965D8AC44E7A97D35A93C | |||
| 6268 | vcredist_x64.exe | C:\b29d9ca21c65f2b9b070d1\watermark.bmp | image | |
MD5:1A5CAAFACFC8C7766E404D019249CF67 | SHA256:2E87D5742413254DB10F7BD0762B6CDB98FF9C46CA9ACDDFD9B1C2E5418638F2 | |||
| 6268 | vcredist_x64.exe | C:\b29d9ca21c65f2b9b070d1\SetupEngine.dll | executable | |
MD5:63E7901D4FA7AC7766076720272060D0 | SHA256:A5116CCB17B242713E5645C2374ABF5827C0D2752B31553E3540C9123812E952 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
50
TCP/UDP connections
222
DNS requests
207
Threats
12
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
516 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
7348 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7348 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
1240 | BackgroundTransferHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6564 | msedge.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.sectigo.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSdE3gf41WAic8Uh9lF92%2BIJqh5qwQUMuuSmv81lkgvKEBCcCA2kVwXheYCEGIdbQxSAZ47kHkVIIkhHAo%3D | unknown | — | — | whitelisted |
8548 | svchost.exe | HEAD | 200 | 146.75.122.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/fb6dd03b-99d7-4cc8-a878-91c8e655c2d3?P1=1743003059&P2=404&P3=2&P4=CywAiflzwAYGaqL%2fWHXw%2b8XfirpcGKxPnN3lDWGlThKorU8UmBKEKLXNqgmGU4himEcKA92pw9RJY%2b7bhHxCow%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.48.23.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
3216 | svchost.exe | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 20.190.160.131:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2924 | SearchApp.exe | 104.126.37.130:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
516 | backgroundTaskHost.exe | 20.103.156.88:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
516 | backgroundTaskHost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.bing.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7228 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Hosted Libraries (ajax .googleapis .com) |
7228 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Hosted Libraries (ajax .googleapis .com) |
7228 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
7228 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
7228 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
7228 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
7228 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Hosted Libraries (ajax .googleapis .com) |
7228 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
7228 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
7228 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Hosted Libraries (ajax .googleapis .com) |