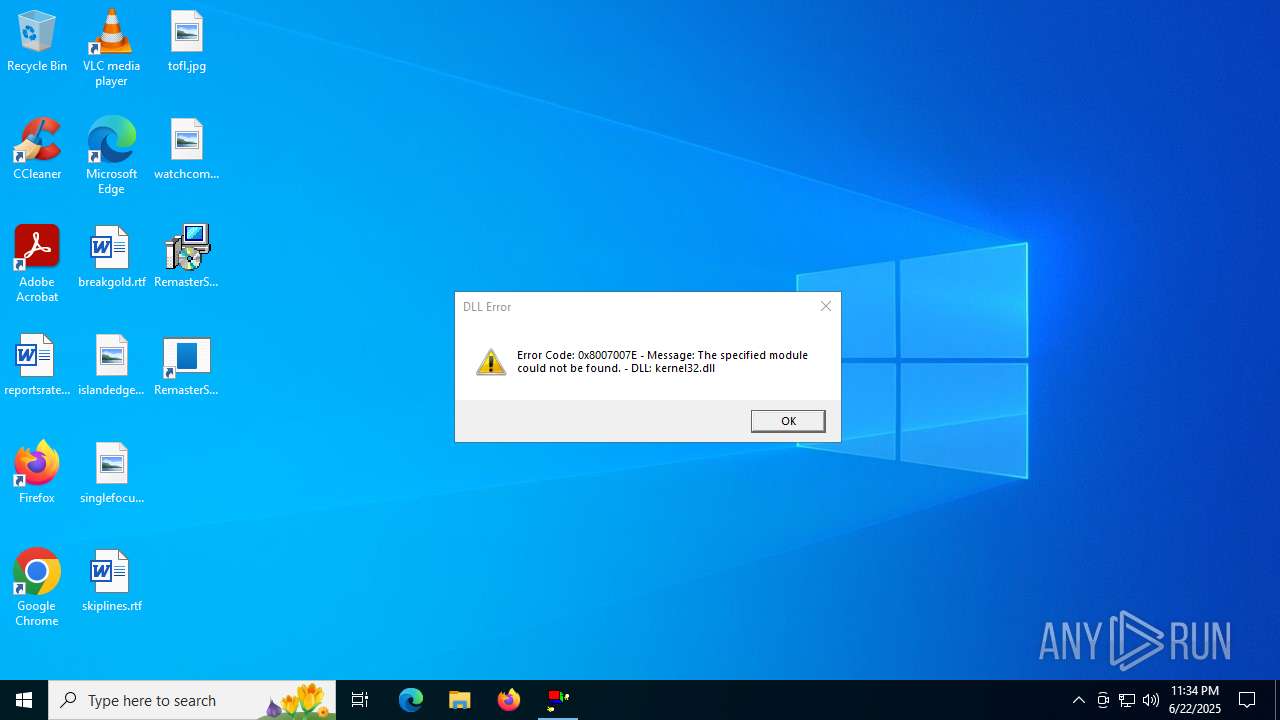
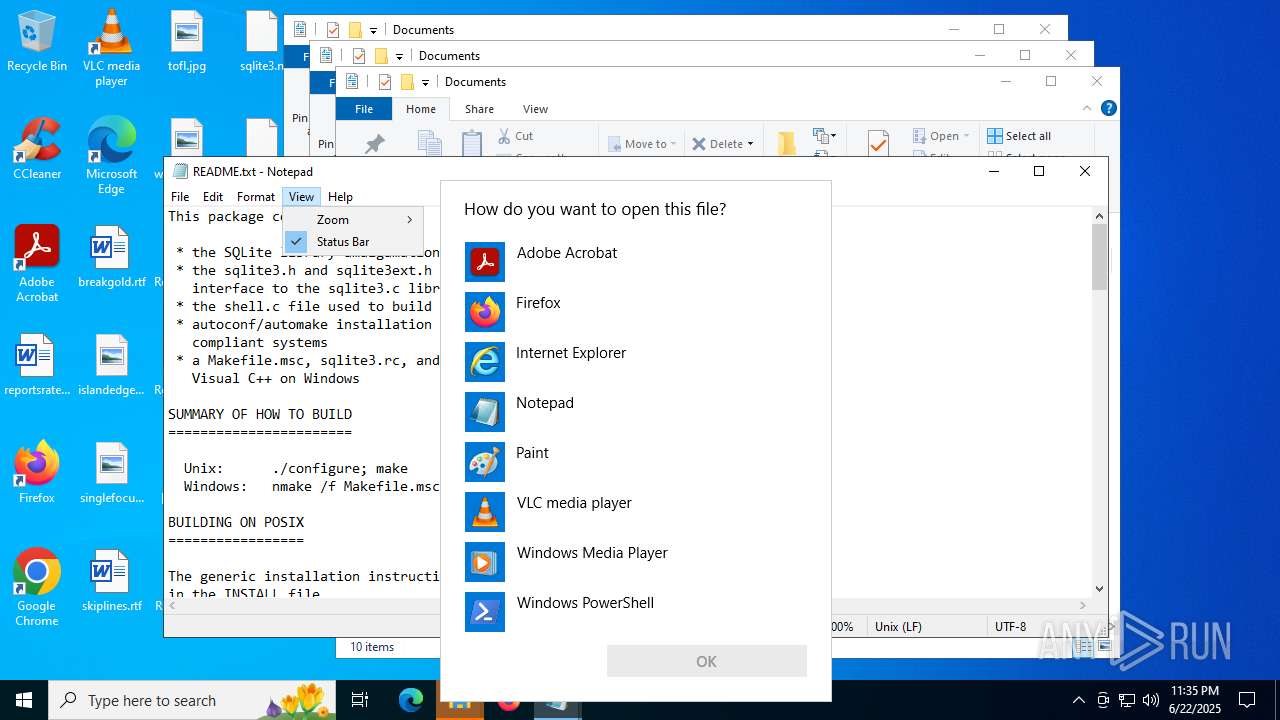
| File name: | RemasterSouls1.0.0.msi |
| Full analysis: | https://app.any.run/tasks/98baad22-f5a8-4385-b3c6-517d2c72ba62 |
| Verdict: | Malicious activity |
| Threats: | Stealers are a group of malicious software that are intended for gaining unauthorized access to users’ information and transferring it to the attacker. The stealer malware category includes various types of programs that focus on their particular kind of data, including files, passwords, and cryptocurrency. Stealers are capable of spying on their targets by recording their keystrokes and taking screenshots. This type of malware is primarily distributed as part of phishing campaigns. |
| Analysis date: | June 22, 2025, 23:33:16 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.2, MSI Installer, Code page: 1252, Title: Installation Database, Subject: RemasterSouls, Author: Unreal Game Inc., Keywords: Installer, Comments: This installer database contains the logic and data required to install RemasterSouls., Template: x64;1033, Revision Number: {D0C3A7BA-8C3A-45F4-9376-1247E442C08B}, Create Time/Date: Sun Jun 8 23:00:34 2025, Last Saved Time/Date: Sun Jun 8 23:00:34 2025, Number of Pages: 500, Number of Words: 2, Name of Creating Application: WiX Toolset (4.0.0.5512), Security: 2 |
| MD5: | A8E6C877B08E7D57DCA3BC630E61D7F2 |
| SHA1: | 7CA074378C2A75088C85BA9E773B025046135D6F |
| SHA256: | F3A00C61814CFBB3D5ACE0BFC9AB618637034B1BABC852B3CC2EB59699E5F338 |
| SSDEEP: | 1572864:myYv/svjhfPP3EtISzLHNOy3EpdxajkrK8TuhZ:myo2NfH3CpHHNfEpOjuLKh |
MALICIOUS
Create files in the Startup directory
- RemasterSouls.exe (PID: 6472)
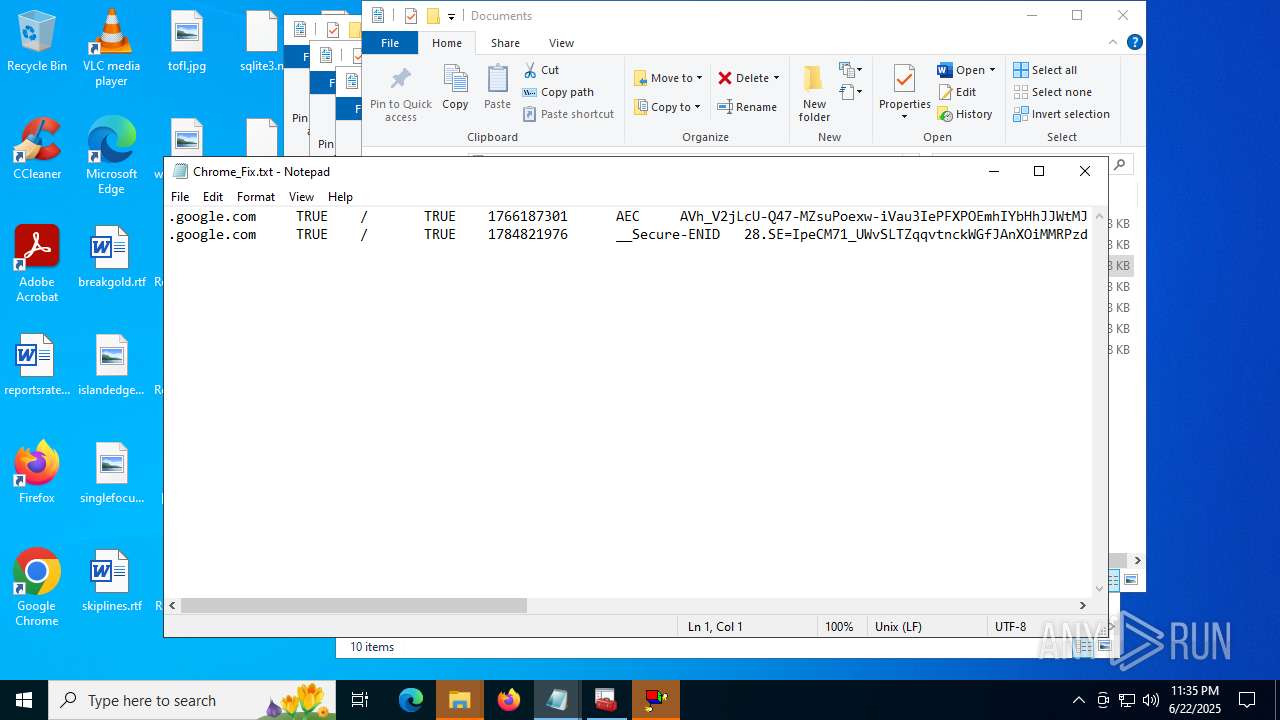
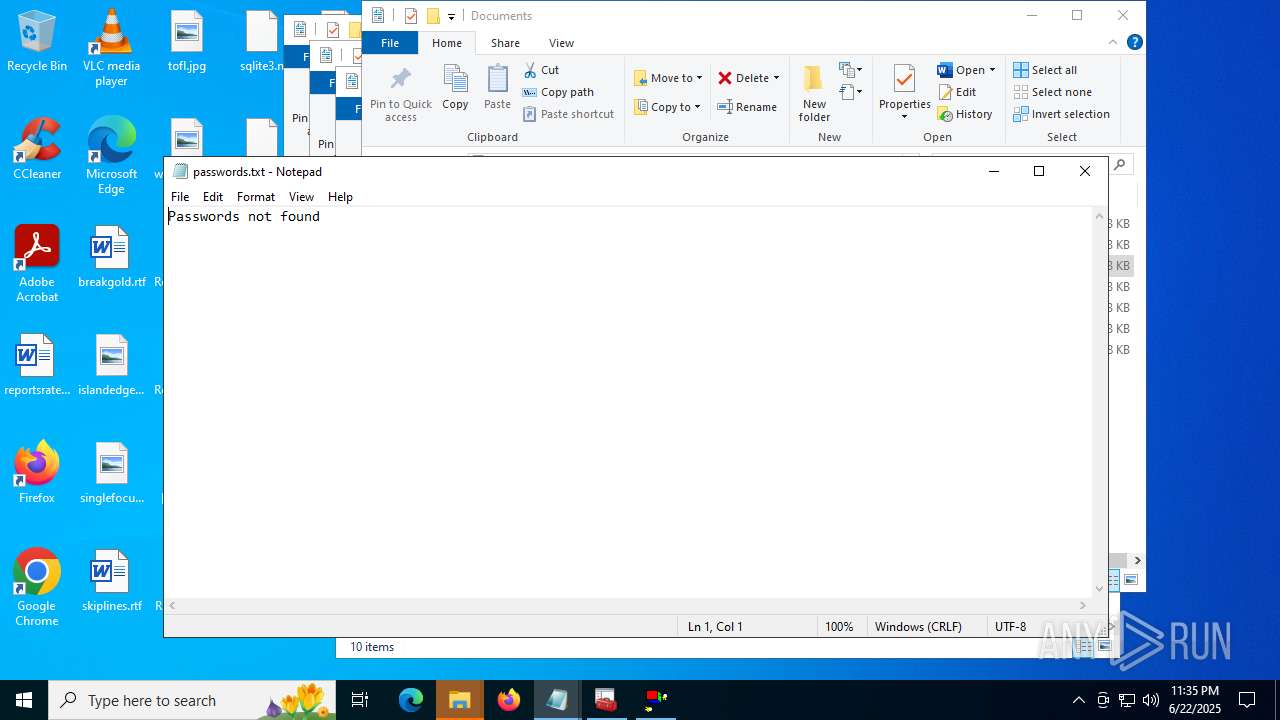
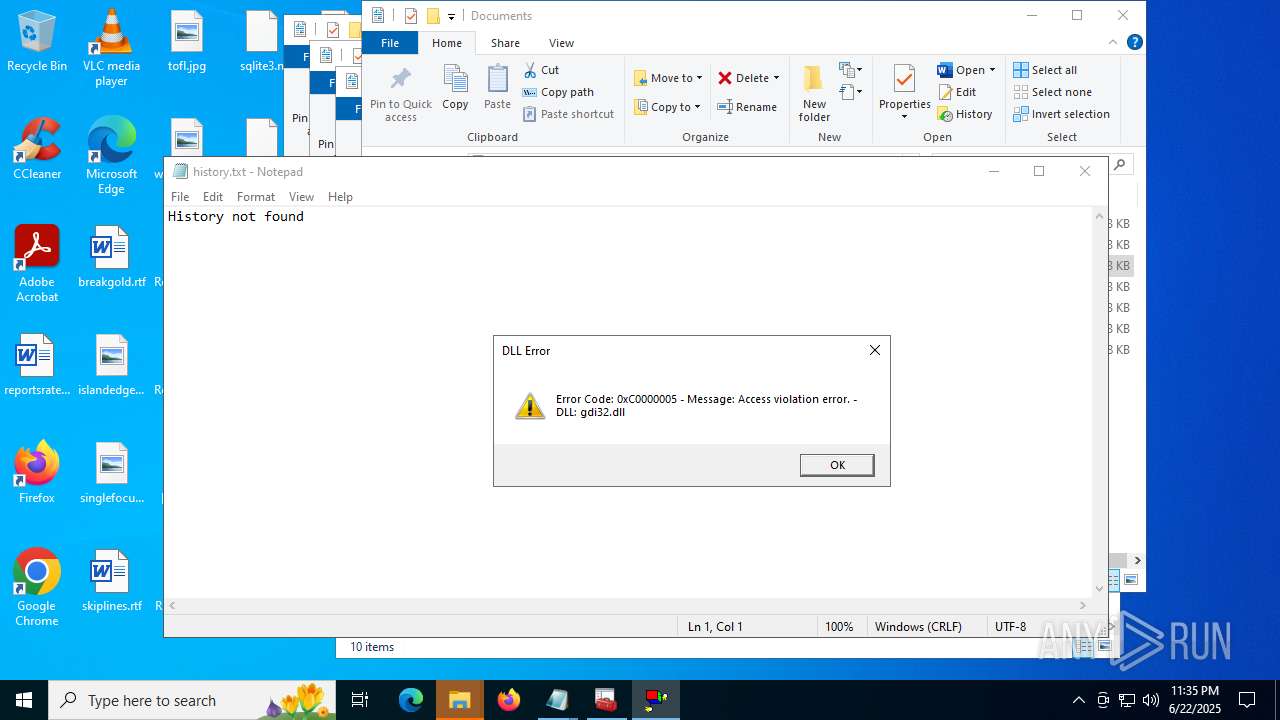
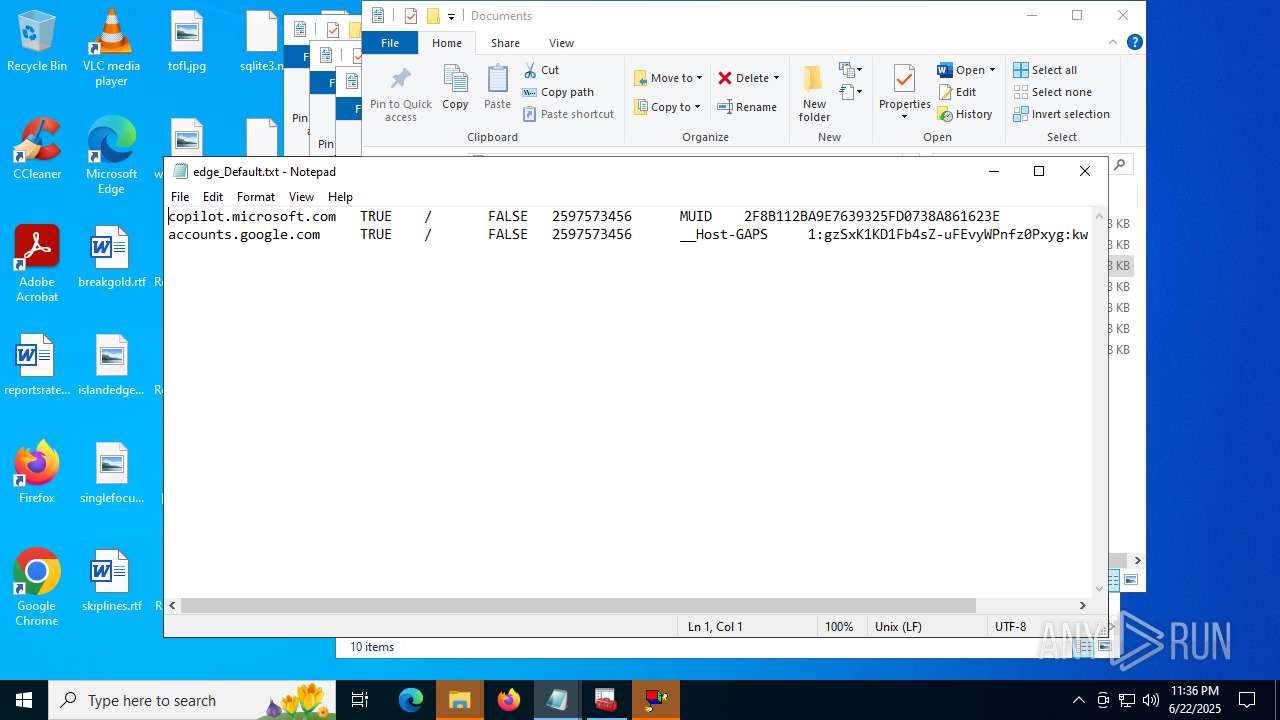
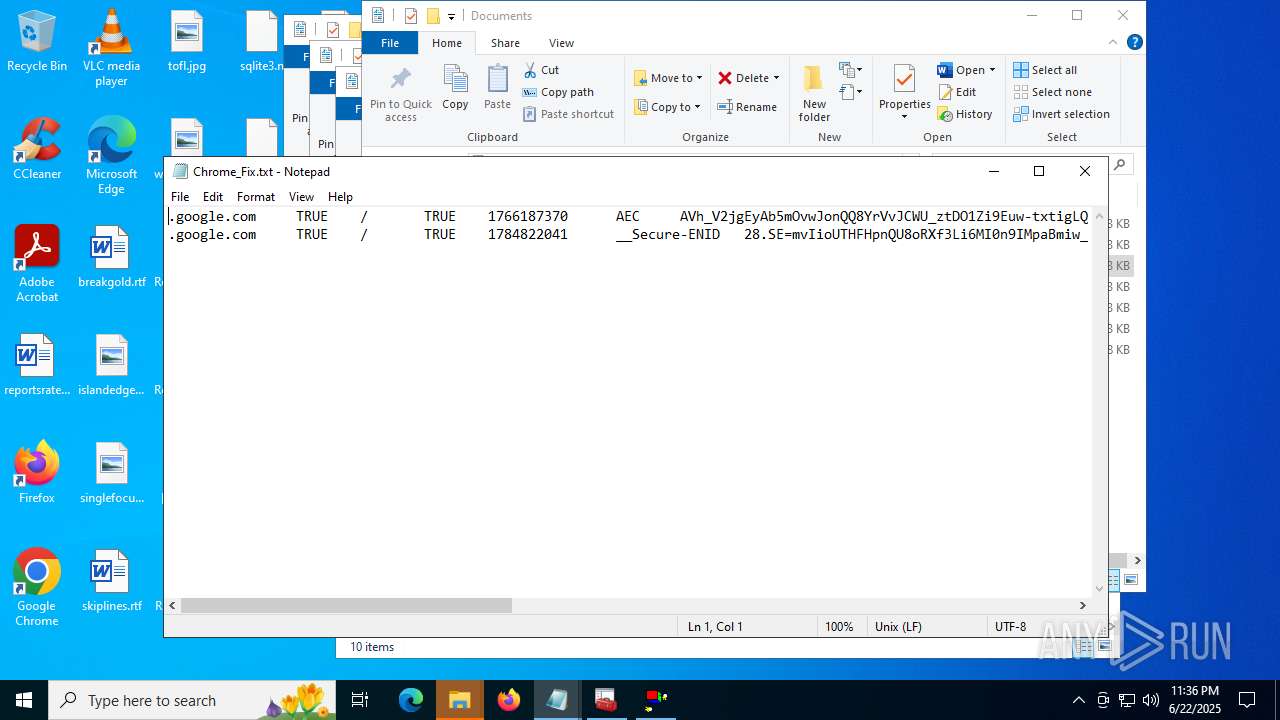
Steals credentials from Web Browsers
- RemasterSouls.exe (PID: 6472)
Actions looks like stealing of personal data
- RemasterSouls.exe (PID: 6472)
Modifies files in the Chrome extension folder
- RemasterSouls.exe (PID: 6472)
Suspicious browser debugging (Possible cookie theft)
- msedge.exe (PID: 6504)
- msedge.exe (PID: 2792)
- msedge.exe (PID: 4116)
DISCORDGRABBER has been detected (YARA)
- RemasterSouls.exe (PID: 6472)
SUSPICIOUS
Reads the Windows owner or organization settings
- msiexec.exe (PID: 1160)
Process drops legitimate windows executable
- msiexec.exe (PID: 1160)
Starts CMD.EXE for commands execution
- RemasterSouls.exe (PID: 6472)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 4808)
Accesses product unique identifier via WMI (SCRIPT)
- WMIC.exe (PID: 6256)
Executes as Windows Service
- VSSVC.exe (PID: 2648)
The process executes VB scripts
- cmd.exe (PID: 3388)
- cmd.exe (PID: 3640)
- cmd.exe (PID: 4172)
- cmd.exe (PID: 2604)
- cmd.exe (PID: 7320)
- cmd.exe (PID: 7608)
- cmd.exe (PID: 6220)
- cmd.exe (PID: 7404)
- cmd.exe (PID: 2272)
- cmd.exe (PID: 7776)
Cryptography encrypted command line is found
- powershell.exe (PID: 6960)
- cmd.exe (PID: 6376)
- cmd.exe (PID: 3396)
- powershell.exe (PID: 6876)
- powershell.exe (PID: 2272)
- cmd.exe (PID: 7288)
- cmd.exe (PID: 8092)
- powershell.exe (PID: 7192)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 6376)
- cmd.exe (PID: 3396)
- cmd.exe (PID: 7288)
- cmd.exe (PID: 8092)
Uses TASKKILL.EXE to kill Browsers
- cmd.exe (PID: 7040)
- cmd.exe (PID: 8112)
- cmd.exe (PID: 7984)
- cmd.exe (PID: 7500)
- cmd.exe (PID: 4984)
- cmd.exe (PID: 4676)
- cmd.exe (PID: 2580)
- cmd.exe (PID: 6236)
- cmd.exe (PID: 7260)
Application launched itself
- RemasterSouls.exe (PID: 6472)
MS Edge headless start
- msedge.exe (PID: 6504)
- msedge.exe (PID: 2792)
- msedge.exe (PID: 7892)
- msedge.exe (PID: 7420)
- msedge.exe (PID: 4116)
Possible usage of Discord/Telegram API has been detected (YARA)
- RemasterSouls.exe (PID: 6472)
Checks for external IP
- RemasterSouls.exe (PID: 6472)
Potential Corporate Privacy Violation
- RemasterSouls.exe (PID: 6472)
INFO
Reads the computer name
- msiexec.exe (PID: 1160)
- RemasterSouls.exe (PID: 6472)
- RemasterSouls.exe (PID: 2464)
- RemasterSouls.exe (PID: 6304)
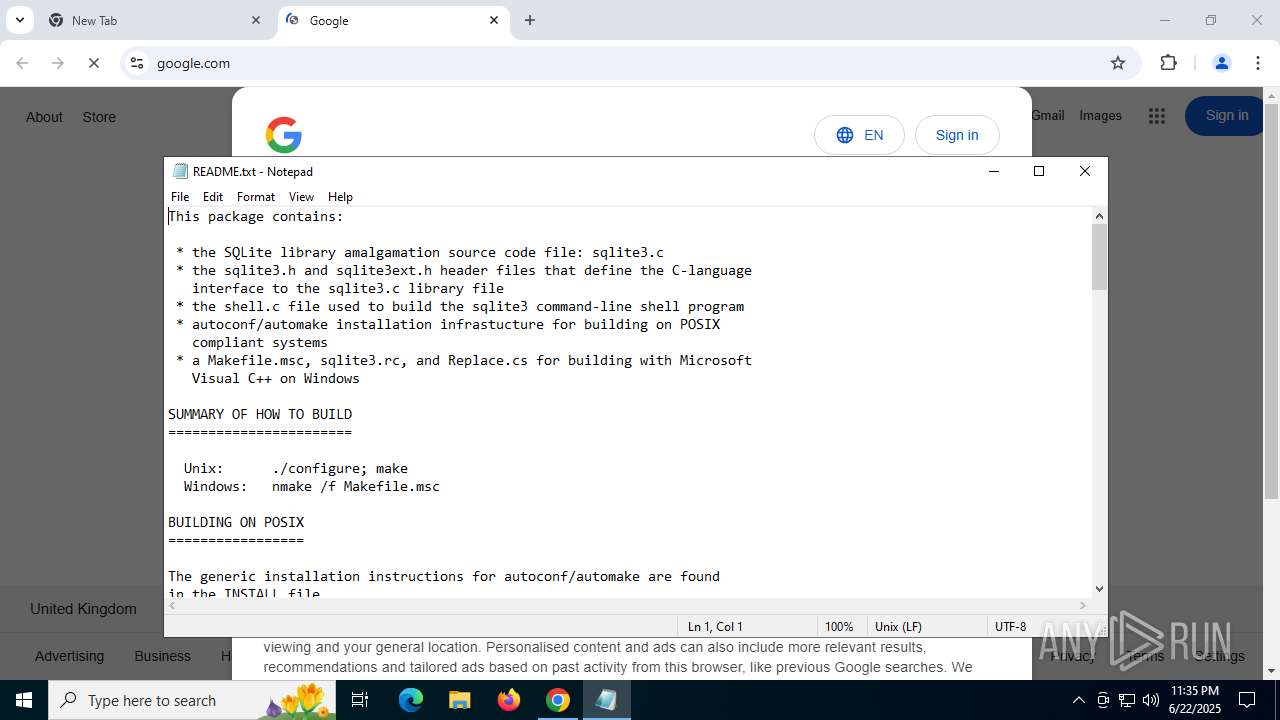
An automatically generated document
- msiexec.exe (PID: 1216)
Checks supported languages
- msiexec.exe (PID: 1160)
- RemasterSouls.exe (PID: 6472)
- RemasterSouls.exe (PID: 6304)
- RemasterSouls.exe (PID: 2464)
Manages system restore points
- SrTasks.exe (PID: 6620)
Executable content was dropped or overwritten
- msiexec.exe (PID: 1160)
The sample compiled with english language support
- msiexec.exe (PID: 1160)
Reads product name
- RemasterSouls.exe (PID: 6472)
Creates files or folders in the user directory
- msiexec.exe (PID: 1160)
- RemasterSouls.exe (PID: 6472)
Creates a software uninstall entry
- msiexec.exe (PID: 1160)
Reads Environment values
- RemasterSouls.exe (PID: 6472)
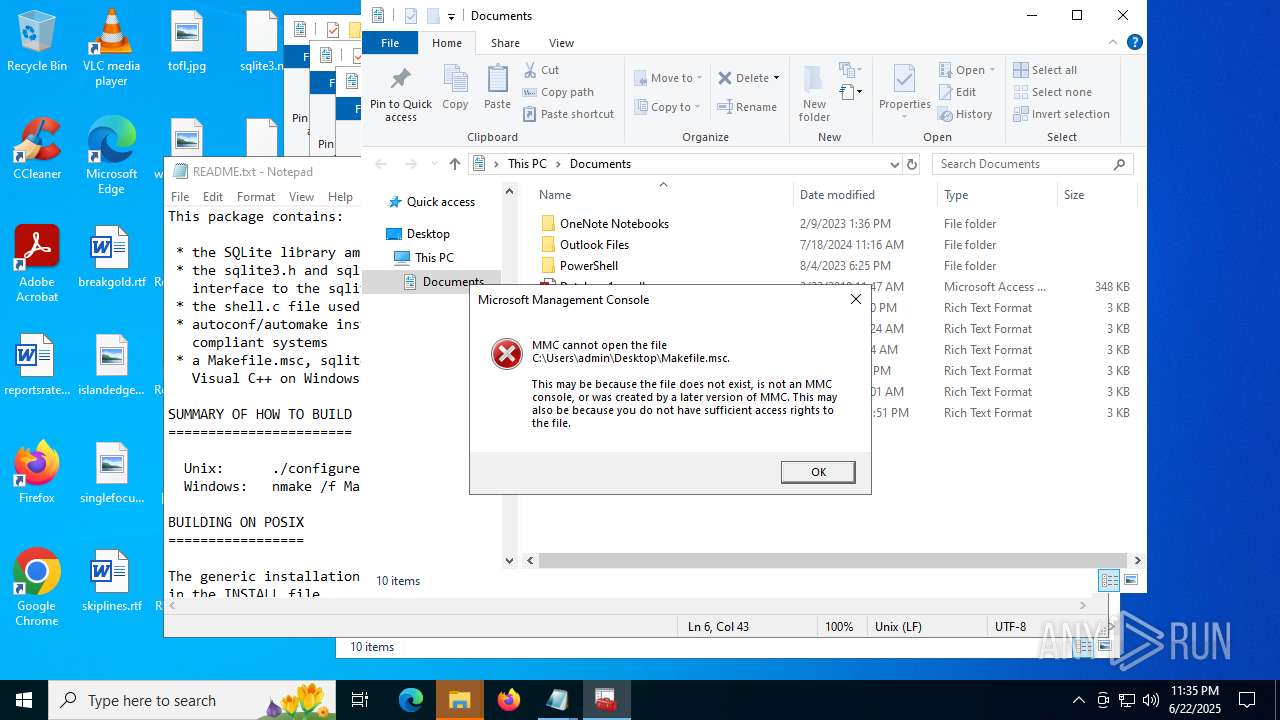
Reads security settings of Internet Explorer
- WMIC.exe (PID: 6256)
- cscript.exe (PID: 5168)
- cscript.exe (PID: 3620)
- cscript.exe (PID: 2192)
- cscript.exe (PID: 2276)
- notepad.exe (PID: 7844)
- mmc.exe (PID: 6460)
- cscript.exe (PID: 4048)
- notepad.exe (PID: 7524)
- cscript.exe (PID: 7536)
- notepad.exe (PID: 7520)
- notepad.exe (PID: 7968)
- notepad.exe (PID: 3740)
- cscript.exe (PID: 2536)
- notepad.exe (PID: 3748)
- cscript.exe (PID: 3832)
- notepad.exe (PID: 7672)
- cscript.exe (PID: 7340)
- cscript.exe (PID: 7280)
- notepad.exe (PID: 8144)
Launching a file from the Startup directory
- RemasterSouls.exe (PID: 6472)
Create files in a temporary directory
- RemasterSouls.exe (PID: 6472)
Manual execution by a user
- RemasterSouls.exe (PID: 3780)
- notepad.exe (PID: 7844)
- notepad.exe (PID: 7600)
- OpenWith.exe (PID: 5124)
- mmc.exe (PID: 1068)
- mmc.exe (PID: 6460)
- notepad.exe (PID: 7524)
- notepad.exe (PID: 7520)
- notepad.exe (PID: 3740)
- notepad.exe (PID: 7968)
- notepad.exe (PID: 3748)
- notepad.exe (PID: 7672)
- notepad.exe (PID: 8144)
Reads the machine GUID from the registry
- RemasterSouls.exe (PID: 6472)
Checks proxy server information
- RemasterSouls.exe (PID: 6472)
- slui.exe (PID: 7420)
Application launched itself
- chrome.exe (PID: 7584)
- chrome.exe (PID: 6524)
- msedge.exe (PID: 2792)
- chrome.exe (PID: 2588)
- chrome.exe (PID: 5400)
- msedge.exe (PID: 4116)
Launching a file from the Downloads directory
- chrome.exe (PID: 6524)
- chrome.exe (PID: 5400)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 5124)
Process checks computer location settings
- RemasterSouls.exe (PID: 6472)
Reads CPU info
- RemasterSouls.exe (PID: 6472)
Attempting to use instant messaging service
- RemasterSouls.exe (PID: 6472)
Reads the software policy settings
- slui.exe (PID: 7420)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
ims-api
(PID) Process(6472) RemasterSouls.exe
Discord-Webhook-Tokens (1)1351005460357972070/SXoMeRxXloxFLC14Iz800D-21axliclPRdXjK4XBrNiuJsTt_PR269CNemtWIZarAeF9
Discord-Info-Links
1351005460357972070/SXoMeRxXloxFLC14Iz800D-21axliclPRdXjK4XBrNiuJsTt_PR269CNemtWIZarAeF9
Get Webhook Infohttps://discord.com/api/webhooks/1351005460357972070/SXoMeRxXloxFLC14Iz800D-21axliclPRdXjK4XBrNiuJsTt_PR269CNemtWIZarAeF9
Discord-Webhook-Tokens (1)1377403035801747496/cmRvL4zrpqc3hFBBH0SkXFrjf0x4ddoZVZ4lKZaHxYAboA4DKC__uXAcp_-_ORHHKWYf
Discord-Info-Links
1377403035801747496/cmRvL4zrpqc3hFBBH0SkXFrjf0x4ddoZVZ4lKZaHxYAboA4DKC__uXAcp_-_ORHHKWYf
Get Webhook Infohttps://discord.com/api/webhooks/1377403035801747496/cmRvL4zrpqc3hFBBH0SkXFrjf0x4ddoZVZ4lKZaHxYAboA4DKC__uXAcp_-_ORHHKWYf
Discord-Webhook-Tokens (3)1380398122836168797/wVhO47Z2iFlmQJL_U-MBmSsi6MJ0ghGyr4ksn0Okel_9wuRkx2c-7yStj0wbc8dZu13B
1351005460357972070/SXoMeRxXloxFLC14Iz800D-21axliclPRdXjK4XBrNiuJsTt_PR269CNemtWIZarAeF9
1377403035801747496/cmRvL4zrpqc3hFBBH0SkXFrjf0x4ddoZVZ4lKZaHxYAboA4DKC__uXAcp_-_ORHHKWYf
Discord-Info-Links
1380398122836168797/wVhO47Z2iFlmQJL_U-MBmSsi6MJ0ghGyr4ksn0Okel_9wuRkx2c-7yStj0wbc8dZu13B
Get Webhook Infohttps://discord.com/api/webhooks/1380398122836168797/wVhO47Z2iFlmQJL_U-MBmSsi6MJ0ghGyr4ksn0Okel_9wuRkx2c-7yStj0wbc8dZu13B
1351005460357972070/SXoMeRxXloxFLC14Iz800D-21axliclPRdXjK4XBrNiuJsTt_PR269CNemtWIZarAeF9
Get Webhook Infohttps://discord.com/api/webhooks/1351005460357972070/SXoMeRxXloxFLC14Iz800D-21axliclPRdXjK4XBrNiuJsTt_PR269CNemtWIZarAeF9
1377403035801747496/cmRvL4zrpqc3hFBBH0SkXFrjf0x4ddoZVZ4lKZaHxYAboA4DKC__uXAcp_-_ORHHKWYf
Get Webhook Infohttps://discord.com/api/webhooks/1377403035801747496/cmRvL4zrpqc3hFBBH0SkXFrjf0x4ddoZVZ4lKZaHxYAboA4DKC__uXAcp_-_ORHHKWYf
Discord-Webhook-Tokens (2)1380398122836168797/wVhO47Z2iFlmQJL_U-MBmSsi6MJ0ghGyr4ksn0Okel_9wuRkx2c-7yStj0wbc8dZu13B
1377403035801747496/cmRvL4zrpqc3hFBBH0SkXFrjf0x4ddoZVZ4lKZaHxYAboA4DKC__uXAcp_-_ORHHKWYf
Discord-Info-Links
1380398122836168797/wVhO47Z2iFlmQJL_U-MBmSsi6MJ0ghGyr4ksn0Okel_9wuRkx2c-7yStj0wbc8dZu13B
Get Webhook Infohttps://discord.com/api/webhooks/1380398122836168797/wVhO47Z2iFlmQJL_U-MBmSsi6MJ0ghGyr4ksn0Okel_9wuRkx2c-7yStj0wbc8dZu13B
1377403035801747496/cmRvL4zrpqc3hFBBH0SkXFrjf0x4ddoZVZ4lKZaHxYAboA4DKC__uXAcp_-_ORHHKWYf
Get Webhook Infohttps://discord.com/api/webhooks/1377403035801747496/cmRvL4zrpqc3hFBBH0SkXFrjf0x4ddoZVZ4lKZaHxYAboA4DKC__uXAcp_-_ORHHKWYf
TRiD
| .msi | | | Microsoft Installer (100) |
|---|
EXIF
FlashPix
| CodePage: | Windows Latin 1 (Western European) |
|---|---|
| Title: | Installation Database |
| Subject: | RemasterSouls |
| Author: | Unreal Game Inc. |
| Keywords: | Installer |
| Comments: | This installer database contains the logic and data required to install RemasterSouls. |
| Template: | x64;1033 |
| RevisionNumber: | {D0C3A7BA-8C3A-45F4-9376-1247E442C08B} |
| CreateDate: | 2025:06:08 23:00:34 |
| ModifyDate: | 2025:06:08 23:00:34 |
| Pages: | 500 |
| Words: | 2 |
| Software: | WiX Toolset (4.0.0.5512) |
| Security: | Read-only recommended |
Total processes
292
Monitored processes
165
Malicious processes
5
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 756 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --string-annotations --extension-process --enable-dinosaur-easter-egg-alt-images --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --field-trial-handle=3972,i,12411509968188840706,1267158542817515006,262144 --variations-seed-version=20250620-130034.957000 --mojo-platform-channel-handle=3912 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 768 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --string-annotations --enable-dinosaur-easter-egg-alt-images --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=10 --field-trial-handle=5776,i,12411509968188840706,1267158542817515006,262144 --variations-seed-version=20250620-130034.957000 --mojo-platform-channel-handle=5784 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 1 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 1068 | "C:\WINDOWS\system32\mmc.exe" C:\Users\admin\Desktop\Makefile.msc | C:\Windows\System32\mmc.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Management Console Exit code: 3221226540 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1068 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win64 --annotation=prod=Chrome --annotation=ver=133.0.6943.127 --initial-client-data=0x21c,0x220,0x224,0x1f8,0x228,0x7ffc44c6fff8,0x7ffc44c70004,0x7ffc44c70010 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 1160 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1216 | "C:\Windows\System32\msiexec.exe" /i C:\Users\admin\Desktop\RemasterSouls1.0.0.msi | C:\Windows\System32\msiexec.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1576 | taskkill /F /T /IM msedge.exe | C:\Windows\System32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1712 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --disable-quic --string-annotations --field-trial-handle=2124,i,12411509968188840706,1267158542817515006,262144 --variations-seed-version=20250620-130034.957000 --mojo-platform-channel-handle=2116 /prefetch:3 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 1 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 1800 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2192 | cscript //Nologo "C:\Users\admin\AppData\Local\Temp\8679372186.vbs" | C:\Windows\System32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
Total events
60 545
Read events
60 121
Write events
404
Delete events
20
Modification events
| (PID) Process: | (2648) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\ASR Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000982A971FCEE3DB01580A0000E4110000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2648) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000982A971FCEE3DB01580A0000F41A0000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2648) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\Registry Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000982A971FCEE3DB01580A00005C160000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2648) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\Shadow Copy Optimization Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000982A971FCEE3DB01580A000008100000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2648) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Leave) |
Value: 480000000000000073F19B1FCEE3DB01580A0000F41A0000E80300000000000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2648) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\11000001 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2648) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\11000001 |
| Operation: | write | Name: | Element |
Value: 0000000000000000000000000000000006000000000000004800000000000000715E5C2FA985EB1190A89A9B763584210000000000000000745E5C2FA985EB1190A89A9B7635842100000000000000000000000000000000 | |||
| (PID) Process: | (2648) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\12000002 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2648) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\12000002 |
| Operation: | write | Name: | Element |
Value: \EFI\Microsoft\Boot\bootmgfw.efi | |||
| (PID) Process: | (2648) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{5b970157-8568-11eb-b45c-806e6f6e6963}\Elements\11000001 |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
18
Suspicious files
285
Text files
186
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1160 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 1160 | msiexec.exe | C:\Windows\Installer\17b594.msi | — | |
MD5:— | SHA256:— | |||
| 1160 | msiexec.exe | C:\Users\admin\AppData\Local\Programs\remastersouls\LICENSES.chromium.html | — | |
MD5:— | SHA256:— | |||
| 1160 | msiexec.exe | C:\Users\admin\AppData\Local\Programs\remastersouls\RemasterSouls.exe | — | |
MD5:— | SHA256:— | |||
| 1160 | msiexec.exe | C:\Users\admin\AppData\Local\Programs\remastersouls\icudtl.dat | — | |
MD5:— | SHA256:— | |||
| 1160 | msiexec.exe | C:\Users\admin\AppData\Local\Programs\remastersouls\resources.pak | — | |
MD5:— | SHA256:— | |||
| 1160 | msiexec.exe | C:\Users\admin\AppData\Local\Programs\remastersouls\resources\app.asar | — | |
MD5:— | SHA256:— | |||
| 1160 | msiexec.exe | C:\System Volume Information\SPP\snapshot-2 | binary | |
MD5:662E3F3D949C56ED722DD926E20C49B2 | SHA256:7AF092673E1132F65EC27E2F67E3A671485F49F023B9CA0071FBAC19CC71F74E | |||
| 1160 | msiexec.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{f5070dfd-5b9a-4be5-be66-1b8e47662866}_OnDiskSnapshotProp | binary | |
MD5:662E3F3D949C56ED722DD926E20C49B2 | SHA256:7AF092673E1132F65EC27E2F67E3A671485F49F023B9CA0071FBAC19CC71F74E | |||
| 1160 | msiexec.exe | C:\Windows\Installer\inprogressinstallinfo.ipi | binary | |
MD5:54C9E37E92AF780FDA8906F1EF326ACE | SHA256:696DC28131BA2A5F44B468E395DB517CA52CB4FEE587BF5099B0B61733F62F0F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
172
TCP/UDP connections
150
DNS requests
111
Threats
27
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | POST | 200 | 40.126.32.140:443 | https://login.live.com/RST2.srf | unknown | xml | 11.1 Kb | whitelisted |
— | — | POST | 200 | 40.126.32.138:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 16.7 Kb | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.55.104.172:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.55.104.172:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.55.104.172:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | POST | 403 | 23.35.229.160:443 | https://go.microsoft.com/fwlink/?LinkID=2257403&clcid=0x409 | unknown | html | 386 b | whitelisted |
— | — | POST | 403 | 23.35.229.160:443 | https://go.microsoft.com/fwlink/?LinkID=2257403&clcid=0x409 | unknown | html | 386 b | whitelisted |
— | — | POST | 403 | 23.35.229.160:443 | https://go.microsoft.com/fwlink/?LinkID=2257403&clcid=0x409 | unknown | html | 386 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.55.104.172:80 | crl.microsoft.com | Akamai International B.V. | US | whitelisted |
1268 | svchost.exe | 23.55.104.172:80 | crl.microsoft.com | Akamai International B.V. | US | whitelisted |
— | — | 23.55.104.172:80 | crl.microsoft.com | Akamai International B.V. | US | whitelisted |
5944 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
1268 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2200 | svchost.exe | Potentially Bad Traffic | ET FILE_SHARING Online File Storage Domain in DNS Lookup (gofile .io) |
6472 | RemasterSouls.exe | Misc activity | ET FILE_SHARING File Sharing Related Domain in TLS SNI (gofile .io) |
— | — | A Network Trojan was detected | ET MALWARE Suspicious Zipped Filename in Outbound POST Request (Passwords.txt) M2 |
— | — | A Network Trojan was detected | ET MALWARE Suspicious Zipped Filename in Outbound POST Request (passwords.txt) M2 |
— | — | A Network Trojan was detected | ET MALWARE Suspicious Zipped Filename in Outbound POST Request (Passwords.txt) |
— | — | Device Retrieving External IP Address Detected | SUSPICIOUS [ANY.RUN] An IP address was received from the server as a result of an HTTP request |
2200 | svchost.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
2200 | svchost.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
6472 | RemasterSouls.exe | Potential Corporate Privacy Violation | ET INFO IP Check Domain (myexternalip .com in TLS SNI) |
2200 | svchost.exe | Misc activity | ET INFO Discord Chat Service Domain in DNS Lookup (discord .com) |
Process | Message |
|---|---|
msedge.exe | RecursiveDirectoryCreate( C:\Users\admin\AppData\Local\Microsoft\Edge\User Data directory exists )
|
msedge.exe | RecursiveDirectoryCreate( C:\Users\admin\AppData\Local\Microsoft\Edge\User Data directory exists )
|