| File name: | 5fcn95ww_public 64bit.exe |
| Full analysis: | https://app.any.run/tasks/535df240-1d92-4aa8-947a-f7187fd71b58 |
| Verdict: | Malicious activity |
| Analysis date: | June 01, 2025, 02:21:44 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 5 sections |
| MD5: | E0B22AC5B6C09E089A02772BE04B005E |
| SHA1: | C1594A4831AD5F62E231C5FCA3B4826E11115D80 |
| SHA256: | F381EACCFB0370A05E6C634DBC3FF7E687BA5DF068830CBDC3269C6A872F368F |
| SSDEEP: | 98304:1ZHw62YM5edhayjO1f9HUwmQzZxnj/ryOwiJFGZgE7p1zCQPVqPZwgJ8Wvh9hT0K:ldgxjHXYQ |
MALICIOUS
Executing a file with an untrusted certificate
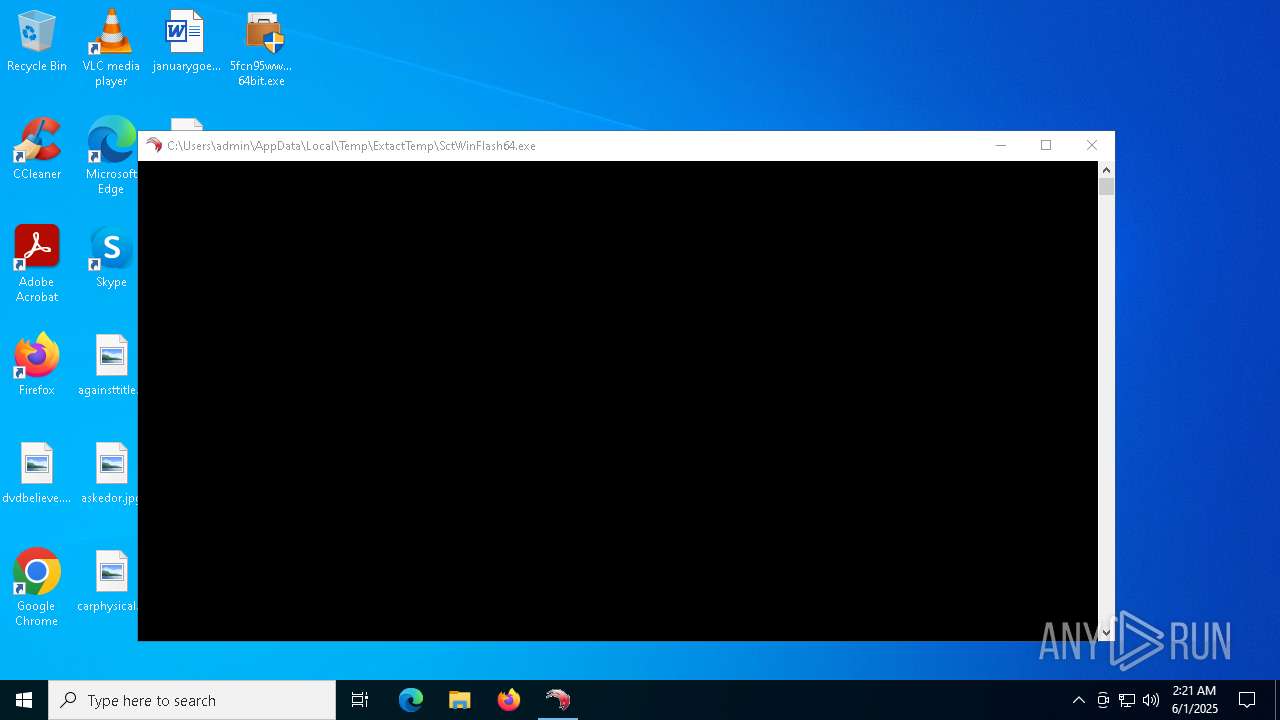
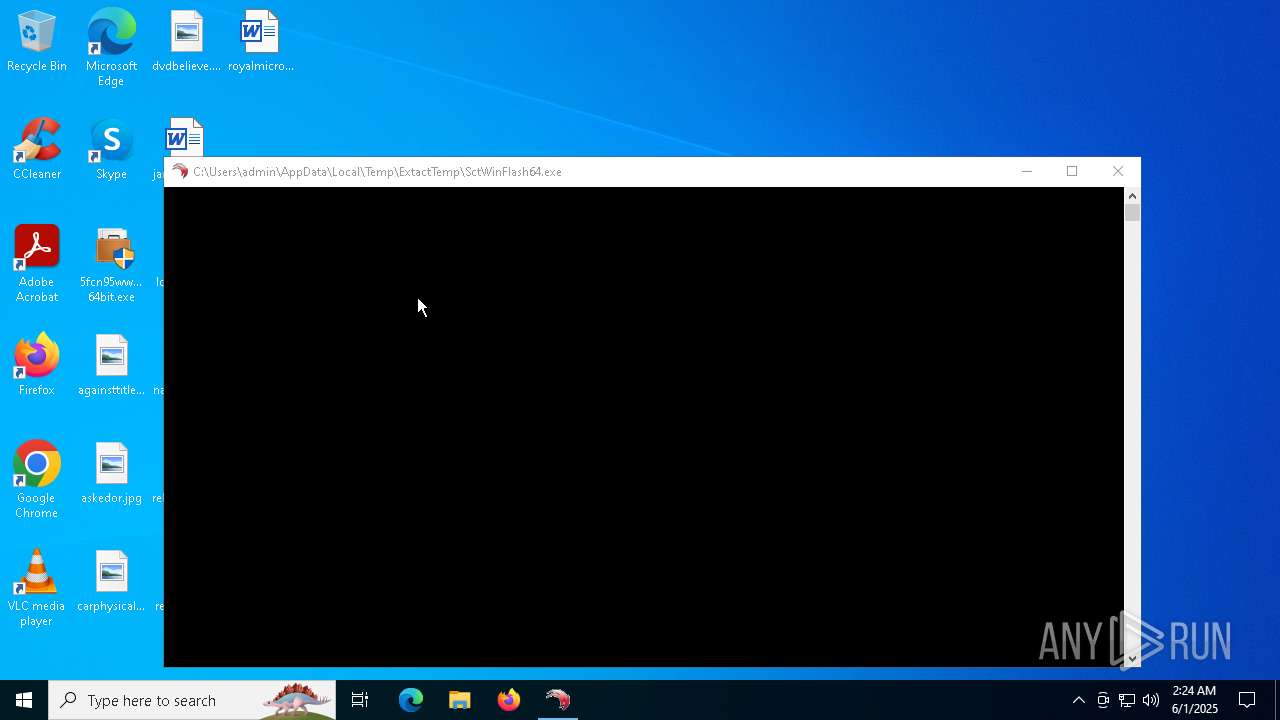
- SctWinFlash64.exe (PID: 7036)
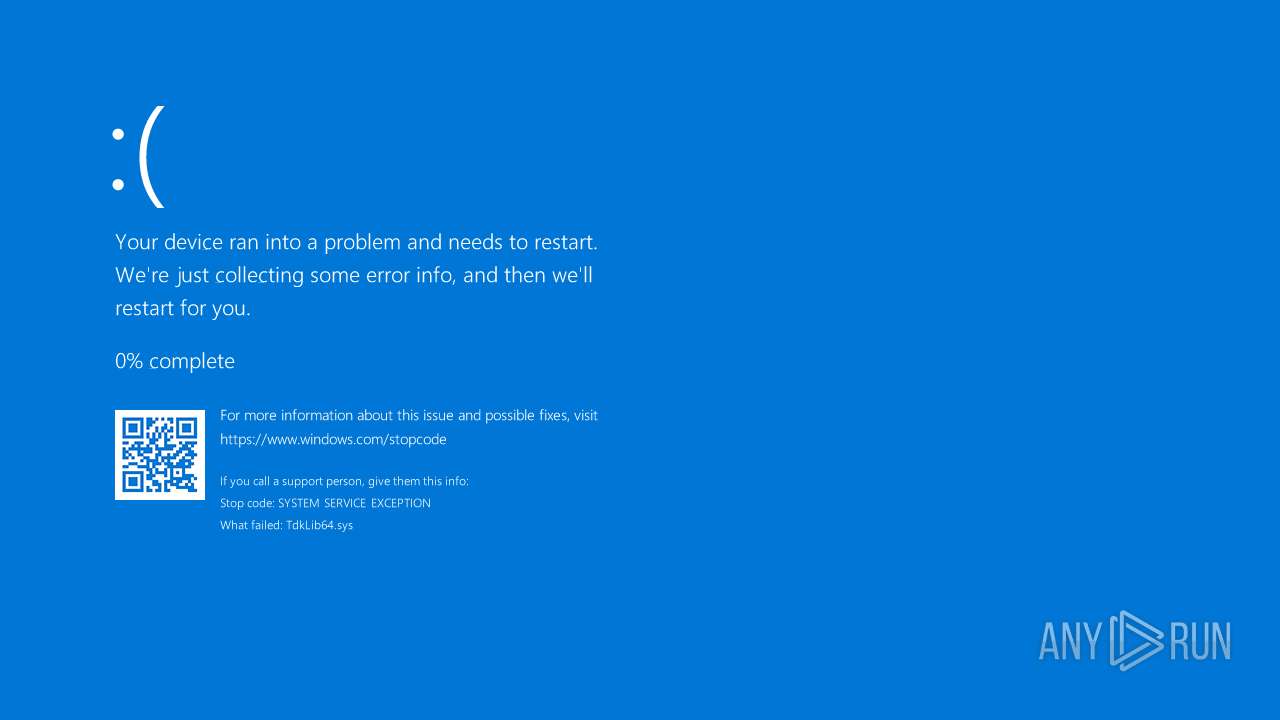
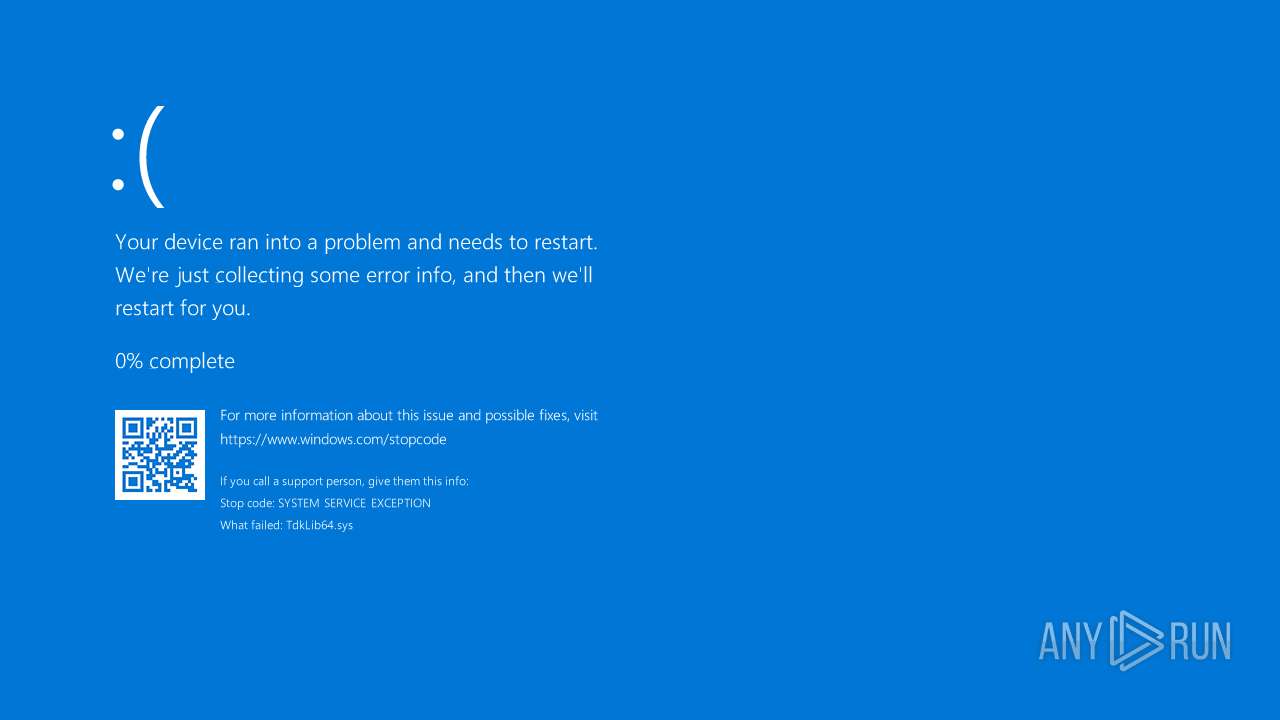
Vulnerable driver has been detected
- WinFlash64.exe (PID: 7104)
SUSPICIOUS
The process executes via Task Scheduler
- PLUGScheduler.exe (PID: 3160)
Executable content was dropped or overwritten
- 5fcn95ww_public 64bit.exe (PID: 6976)
- WinFlash64.exe (PID: 7104)
Drops a system driver (possible attempt to evade defenses)
- WinFlash64.exe (PID: 7104)
INFO
Checks supported languages
- PLUGScheduler.exe (PID: 3160)
- RUXIMICS.exe (PID: 4660)
Manual execution by a user
- mspaint.exe (PID: 6620)
- 5fcn95ww_public 64bit.exe (PID: 6976)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2011:11:24 03:41:25+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 8 |
| CodeSize: | 216576 |
| InitializedDataSize: | 136192 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1aa70 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.3.6.0 |
| ProductVersionNumber: | 1.3.6.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | Phoenix Technologies Ltd. |
| FileDescription: | Extractor for Windows |
| FileVersion: | 1, 3, 6, 0 |
| InternalName: | WinExtractor.exe |
| LegalCopyright: | Copyright (C) 2011 Phoenix Technologies Ltd. |
| OriginalFileName: | WinExtractor.exe |
| ProductName: | TDK Packer (Extractor for Windows) |
| ProductVersion: | 1, 3, 6, 0 |
Total processes
253
Monitored processes
8
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3160 | "C:\Program Files\RUXIM\PLUGscheduler.exe" | C:\Program Files\RUXIM\PLUGScheduler.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Update LifeCycle Component Scheduler Exit code: 0 Version: 10.0.19041.3623 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4660 | %ProgramFiles%\RUXIM\RUXIMICS.EXE /onlyloadcampaigns | C:\Program Files\RUXIM\RUXIMICS.exe | PLUGScheduler.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Reusable UX Interaction Manager Exit code: 0 Version: 10.0.19041.3623 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6092 | %ProgramFiles%\RUXIM\RUXIMICS.EXE /nonetwork | C:\Program Files\RUXIM\RUXIMICS.exe | — | PLUGScheduler.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Reusable UX Interaction Manager Exit code: 0 Version: 10.0.19041.3623 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6620 | "C:\WINDOWS\system32\mspaint.exe" "C:\Users\admin\Downloads\playerrape.jpg" | C:\Windows\System32\mspaint.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Paint Exit code: 0 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6976 | "C:\Users\admin\Desktop\5fcn95ww_public 64bit.exe" | C:\Users\admin\Desktop\5fcn95ww_public 64bit.exe | explorer.exe | ||||||||||||
User: admin Company: Phoenix Technologies Ltd. Integrity Level: HIGH Description: Extractor for Windows Version: 1, 3, 6, 0 Modules
| |||||||||||||||
| 7036 | "C:\Users\admin\AppData\Local\Temp\ExtactTemp\SctWinFlash64.exe" | C:\Users\admin\AppData\Local\Temp\ExtactTemp\SctWinFlash64.exe | — | 5fcn95ww_public 64bit.exe | |||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 7044 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SctWinFlash64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7104 | C:\Users\admin\AppData\Local\Temp\ExtactTemp\WinFlash64.exe -help | C:\Users\admin\AppData\Local\Temp\ExtactTemp\WinFlash64.exe | SctWinFlash64.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
Total events
2 566
Read events
2 523
Write events
42
Delete events
1
Modification events
| (PID) Process: | (4660) RUXIMICS.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowsUpdate\PLUG\OneSettingsSync |
| Operation: | write | Name: | x-ms-onesetinterval |
Value: 1440 | |||
| (PID) Process: | (4660) RUXIMICS.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowsUpdate\PLUG\OneSettingsSync |
| Operation: | write | Name: | RefreshAfter |
Value: 5420063A65D3DB01 | |||
| (PID) Process: | (3160) PLUGScheduler.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowsUpdate\PLUG\Scheduler\Activity\State\OneSettings |
| Operation: | write | Name: | ExecutionCount |
Value: 7 | |||
| (PID) Process: | (3160) PLUGScheduler.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowsUpdate\PLUG\Scheduler\Activity\State\OneSettings |
| Operation: | write | Name: | LastExecutionResult |
Value: 0 | |||
| (PID) Process: | (3160) PLUGScheduler.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowsUpdate\PLUG\Scheduler\Activity\State\OneSettings |
| Operation: | write | Name: | LastExecutionExitCode |
Value: 0 | |||
| (PID) Process: | (3160) PLUGScheduler.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowsUpdate\PLUG\Scheduler\Activity\State\OneSettings |
| Operation: | write | Name: | LastExecutionTime |
Value: 54609C0F9CD2DB01 | |||
| (PID) Process: | (3160) PLUGScheduler.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowsUpdate\PLUG\Scheduler\Activity\State\DTU |
| Operation: | write | Name: | ExecutionCount |
Value: 7 | |||
| (PID) Process: | (3160) PLUGScheduler.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowsUpdate\PLUG\Scheduler\Activity\State\DTU |
| Operation: | write | Name: | LastExecutionResult |
Value: | |||
| (PID) Process: | (3160) PLUGScheduler.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowsUpdate\PLUG\Scheduler\Activity\State\DTU |
| Operation: | write | Name: | LastExecutionExitCode |
Value: | |||
| (PID) Process: | (3160) PLUGScheduler.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowsUpdate\PLUG\Scheduler\Activity\State\DTU |
| Operation: | write | Name: | LastExecutionTime |
Value: 54609C0F9CD2DB01 | |||
Executable files
3
Suspicious files
135
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3160 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.047.etl | binary | |
MD5:A23907B6FDD47DCABFDFD7CF2FCD7671 | SHA256:0C9C33FE9E984A2E5A70EBA51F36B9929A86199E424AF2F8080E1267B87DC970 | |||
| 3160 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.048.etl | binary | |
MD5:5EA68411BF8E9EAF4621BAF73F61449E | SHA256:9D4CA5A1D871F819C139A498BB910A63576C2FE6367853544F8D172D8B6EBFF7 | |||
| 3160 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.032.etl | binary | |
MD5:AB9303129E2242D02DC2069E5A4F3896 | SHA256:9031A5BD681D52A903A2BCA625F6D9D8B1456B26D2335CA8170BB39A2FE8F2A0 | |||
| 3160 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.033.etl | binary | |
MD5:DCB94F822B793FF178C7332174A89DFB | SHA256:4AB418FA76DFA333D37F7401B40B0B0F0E806876C79AB2F36CD3FD7CCAD8665B | |||
| 3160 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.043.etl | binary | |
MD5:B53B2070E686FFB1FBC8B06994E7C8D7 | SHA256:A3ABD06F4E40CB700B1908AB6BCD2E27455E13EF076E0BF2345BB2FA369EF802 | |||
| 3160 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.035.etl | binary | |
MD5:A477FE56C25FCDB850EA1AAB8D01B5C2 | SHA256:5C85DC2B41C2D076D6B2653C0BA5F5681ADABFEBDA8883C704E625EB9338F505 | |||
| 3160 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.045.etl | binary | |
MD5:A7A21FBC9D00F33F186B34A50E170C13 | SHA256:64CAC91E46D4FC832958232A658431CBF9D8D9F265653ACA2BEB32428D4688EC | |||
| 3160 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.042.etl | binary | |
MD5:8A2BDE0EAFA7E946196A1B114AB636E9 | SHA256:1C338CBDD9316D7FD8F208341466FEDC554A04D489B3A86C736EC3831A2F2BA2 | |||
| 3160 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.037.etl | binary | |
MD5:F9485F2BA891697F8B6CF8FB1E7F42C0 | SHA256:69146D4AAEFB8609745B6CA780B48ABC66054AA3CDB8061248CF7B32F3B32617 | |||
| 3160 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.041.etl | binary | |
MD5:C1F87CF12DD702D2185E703BA004D216 | SHA256:9D993487866C9538DC19F281A6346E1796E7478C7C164D61437AF6E698C66125 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
39
DNS requests
23
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.20.245.137:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.20.245.137:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3728 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4660 | RUXIMICS.exe | GET | 200 | 2.20.245.137:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4660 | RUXIMICS.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5560 | SIHClient.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5560 | SIHClient.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4808 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 2.20.245.137:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 224.0.0.251:5353 | — | — | — | unknown |
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
2968 | OfficeClickToRun.exe | 52.109.28.46:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
2968 | OfficeClickToRun.exe | 52.123.129.14:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3728 | SearchApp.exe | 2.19.96.128:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
th.bing.com |
| whitelisted |