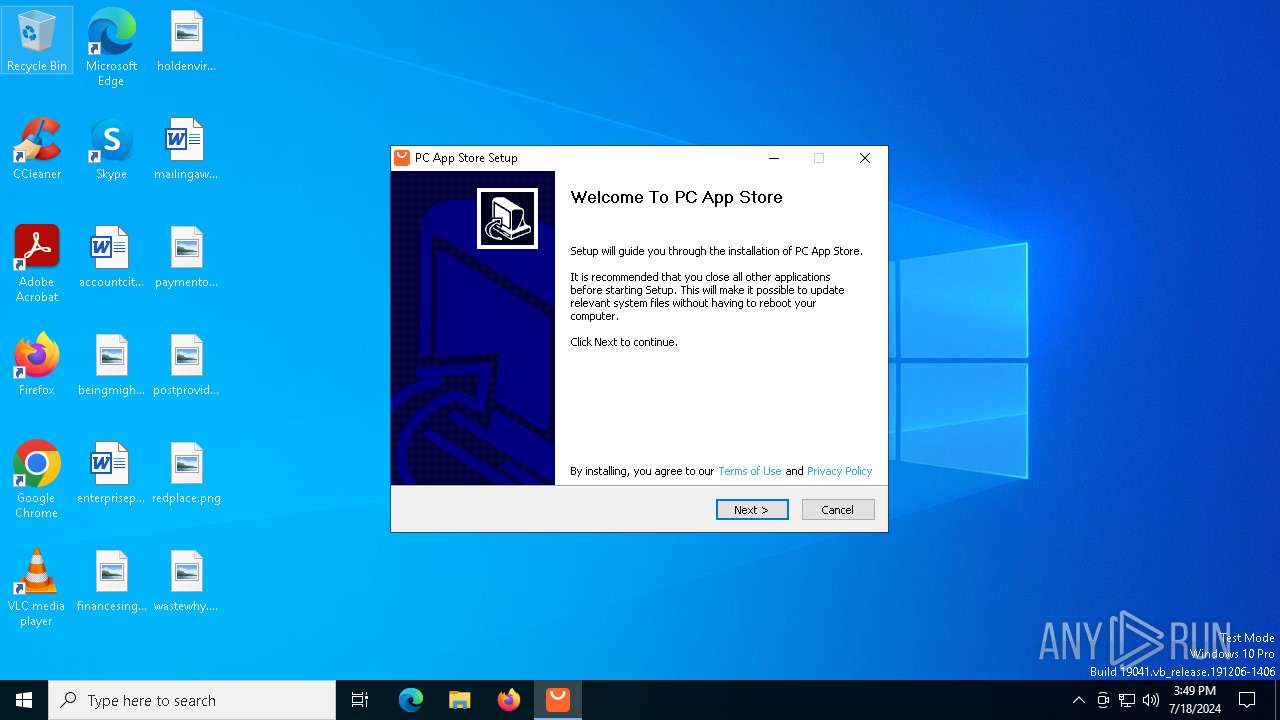
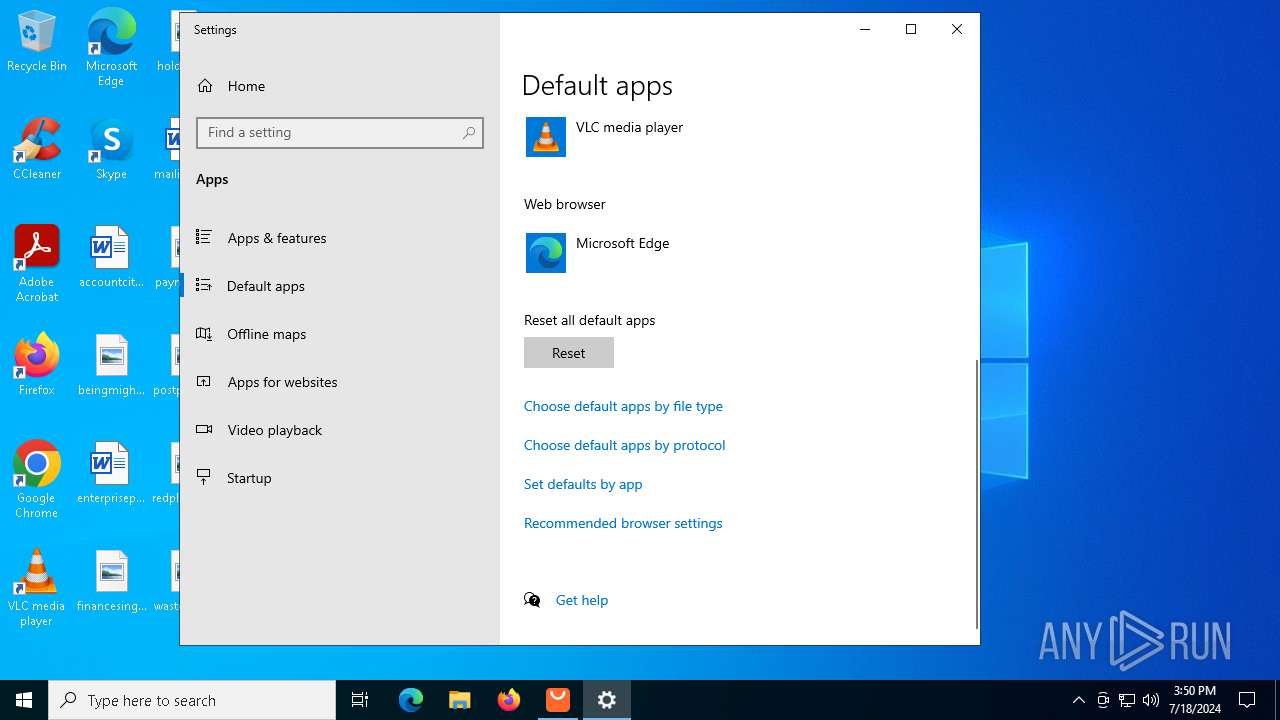
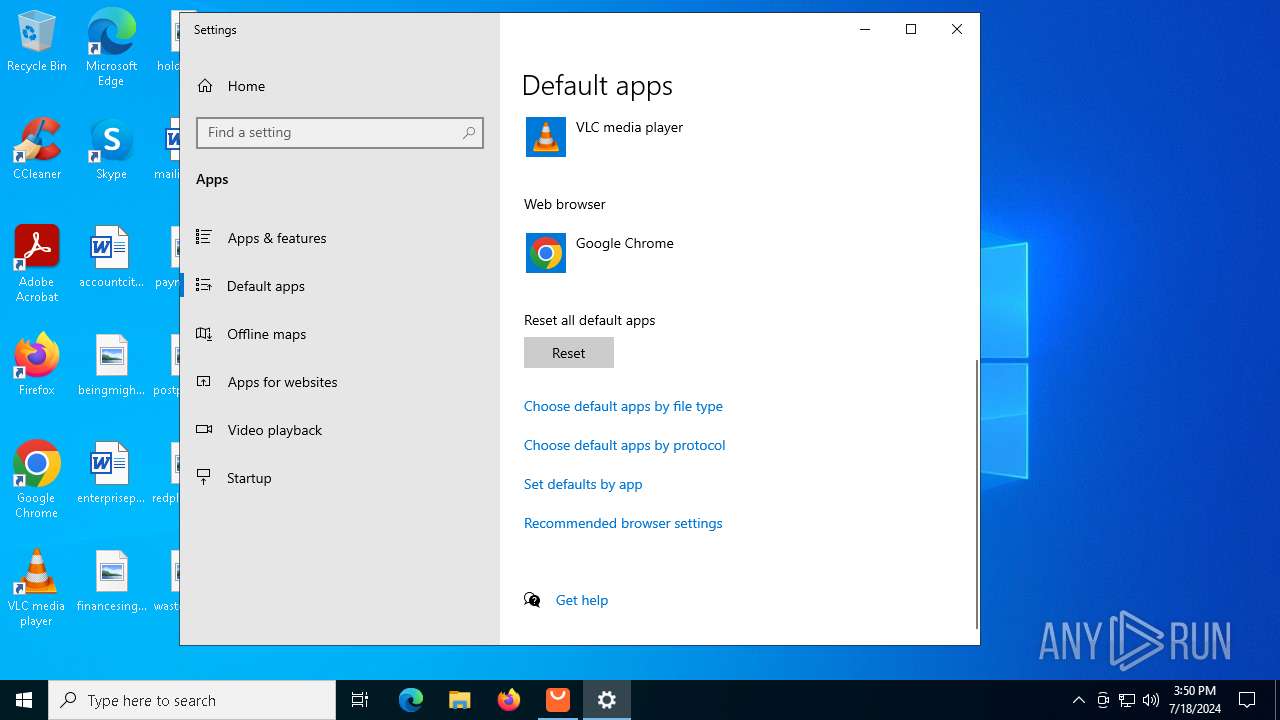
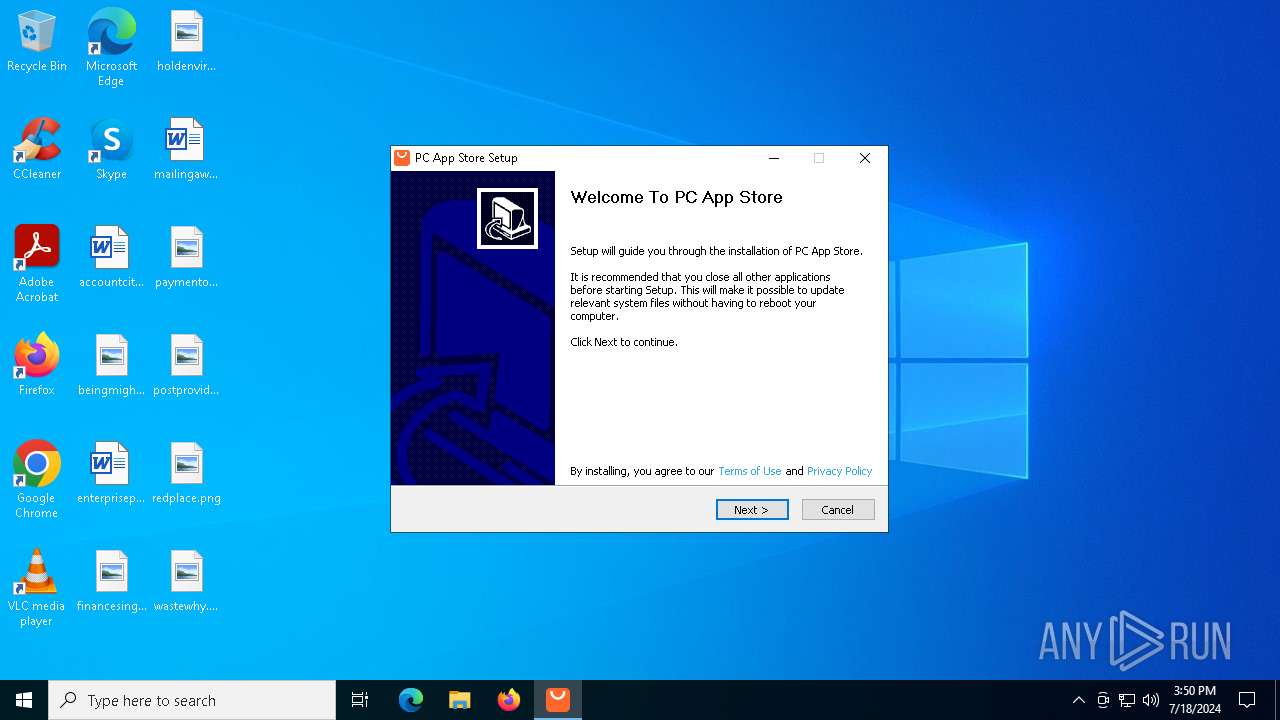
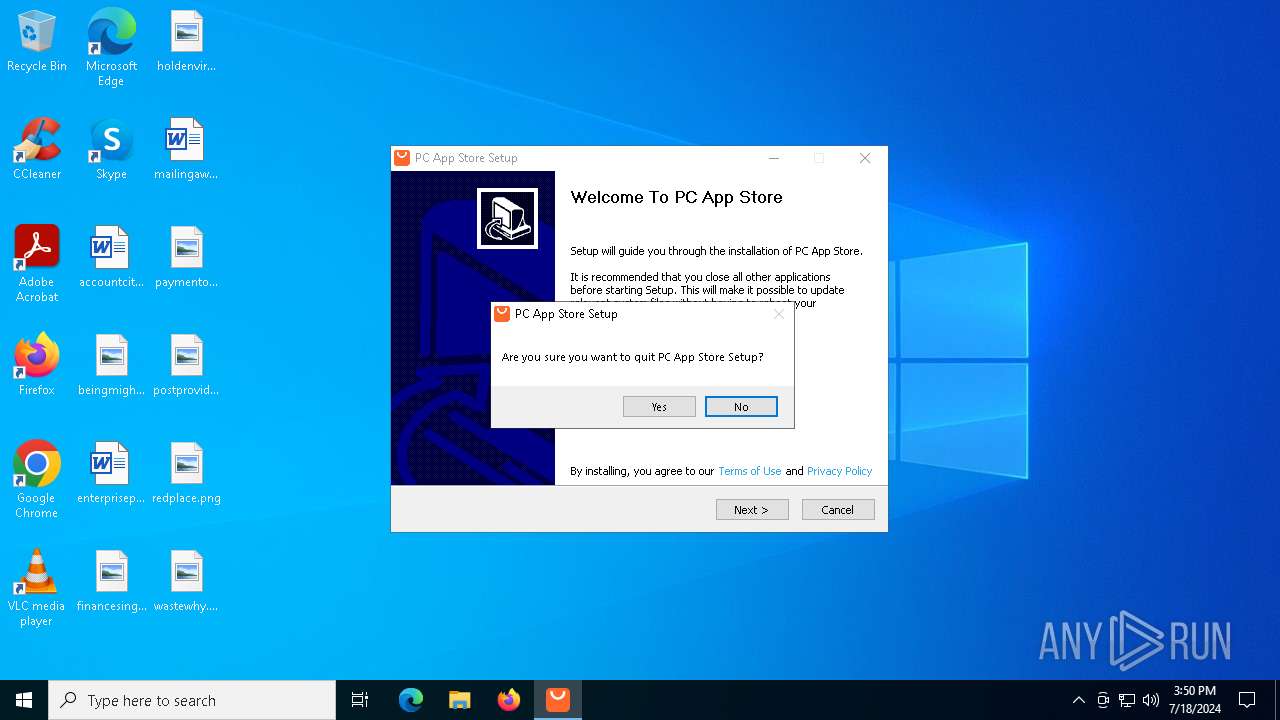
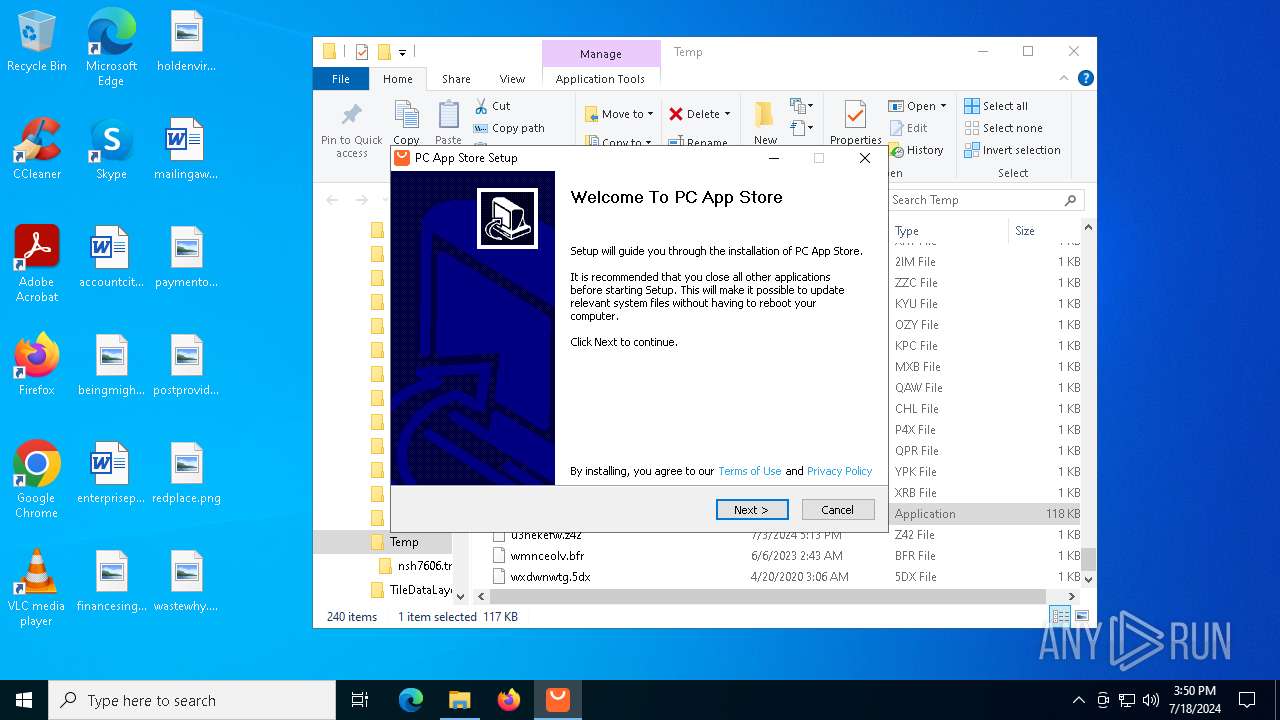
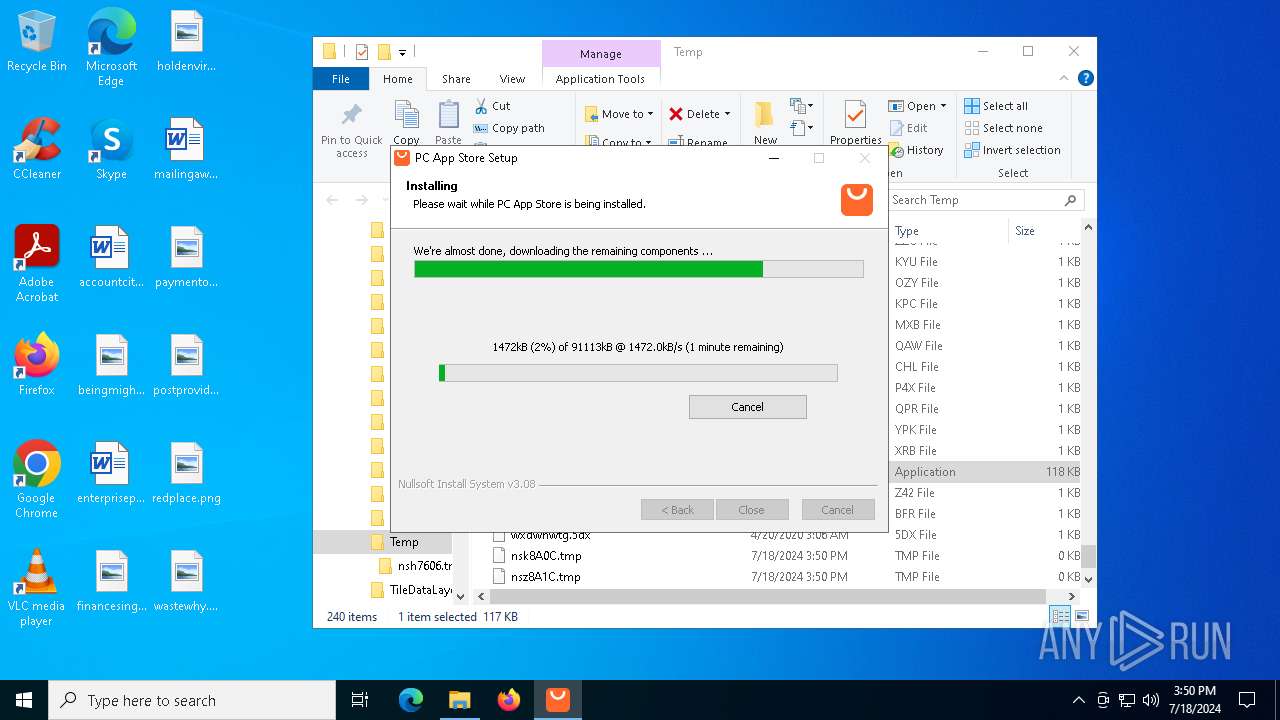
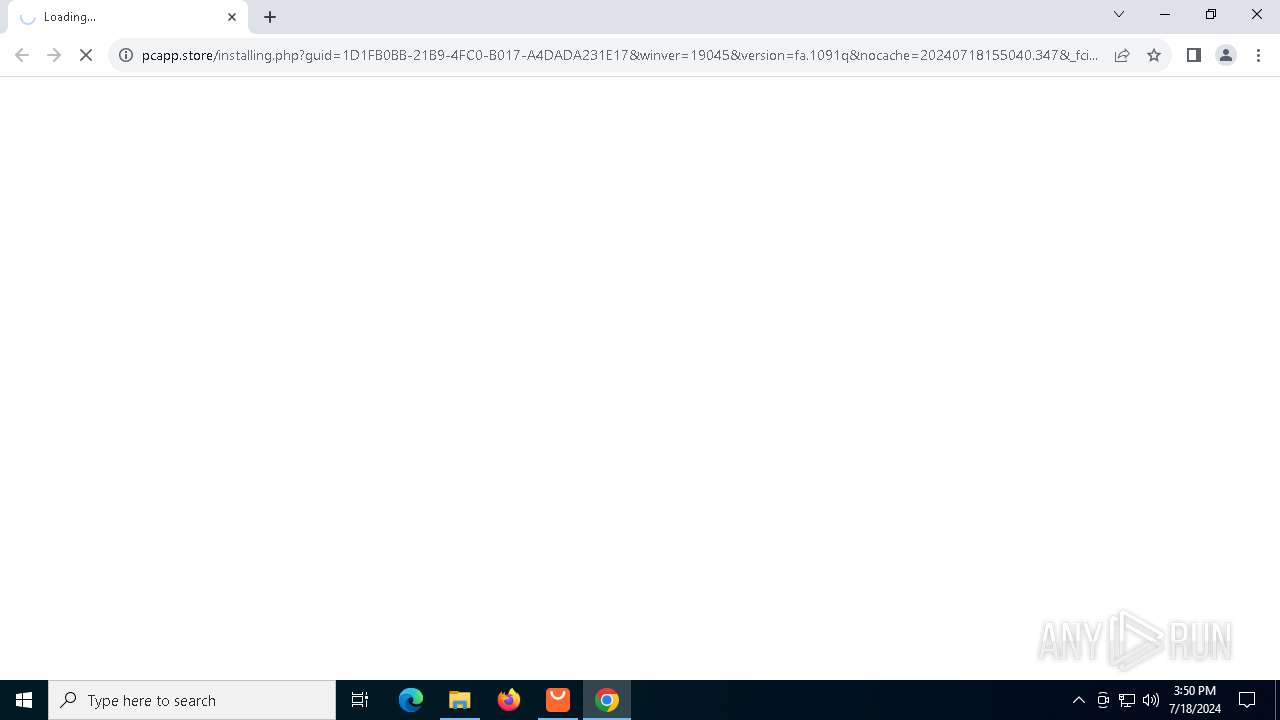
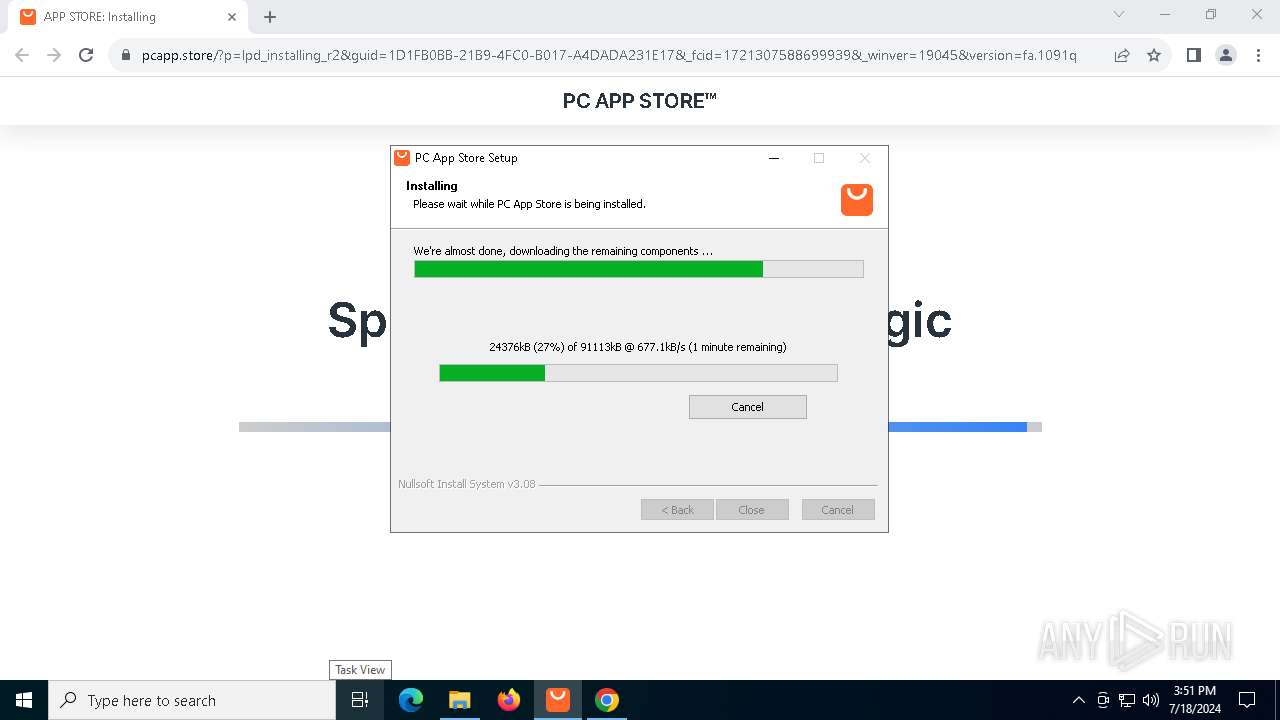
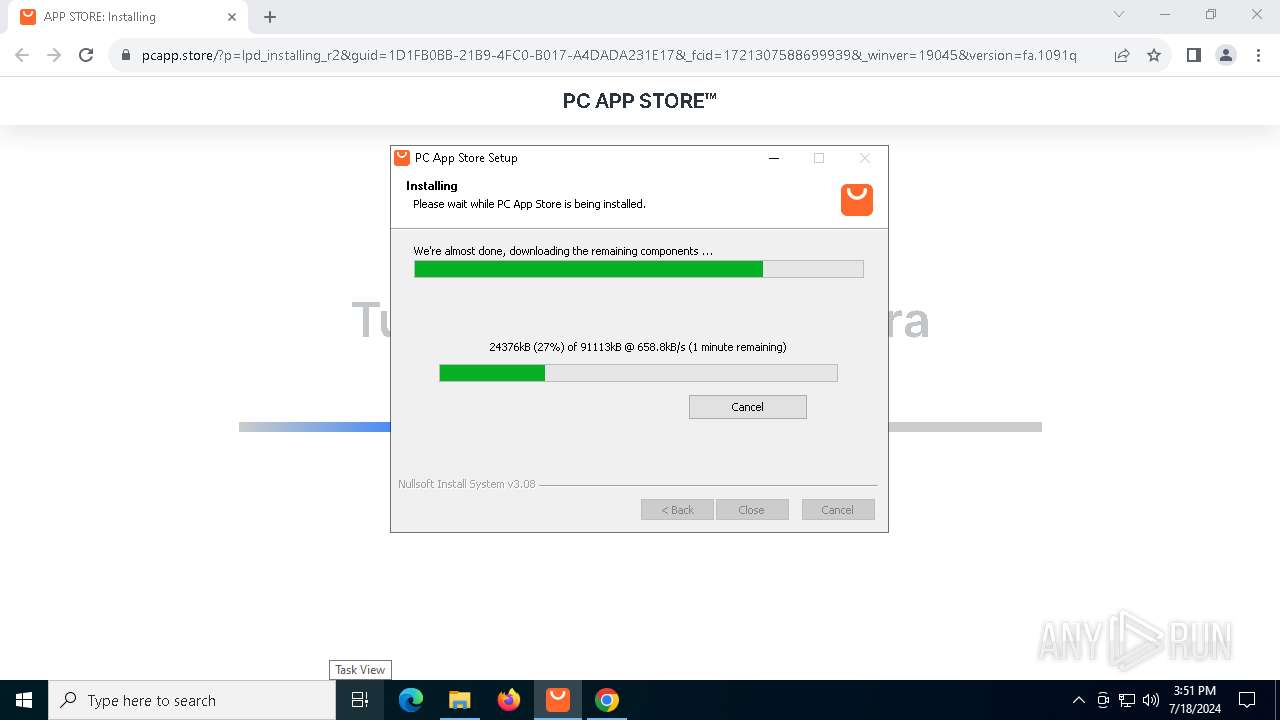
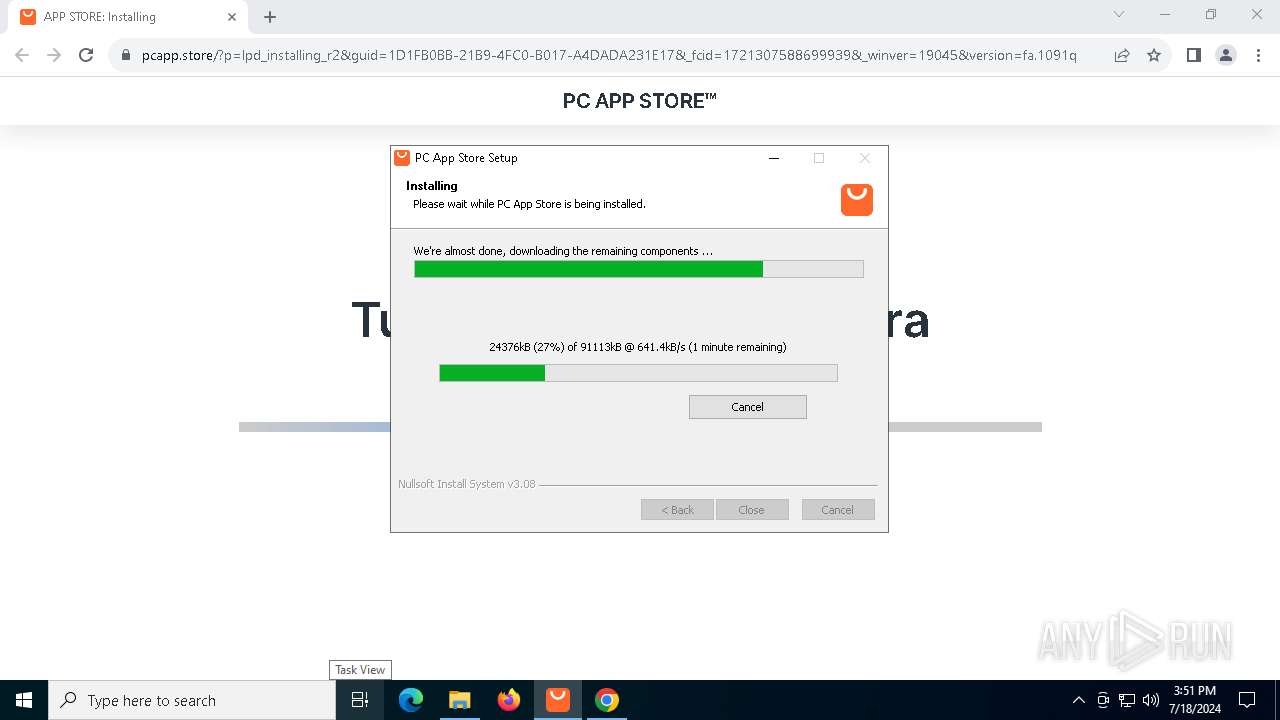
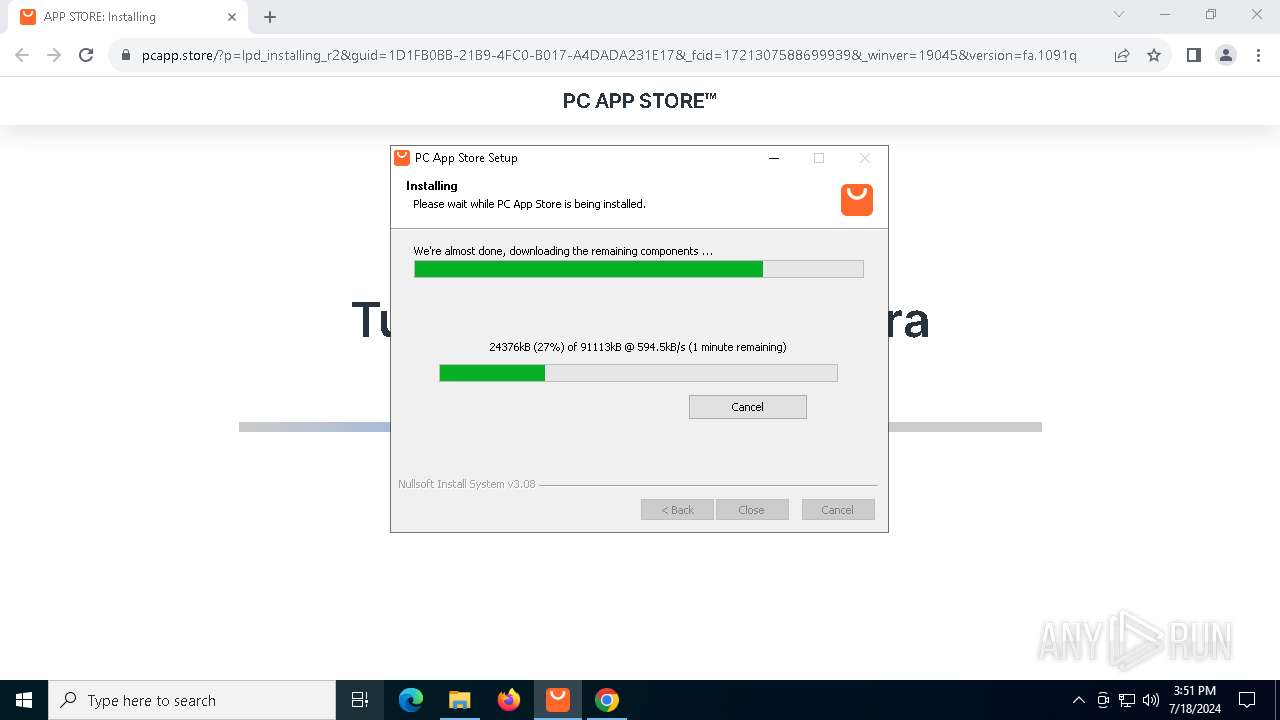
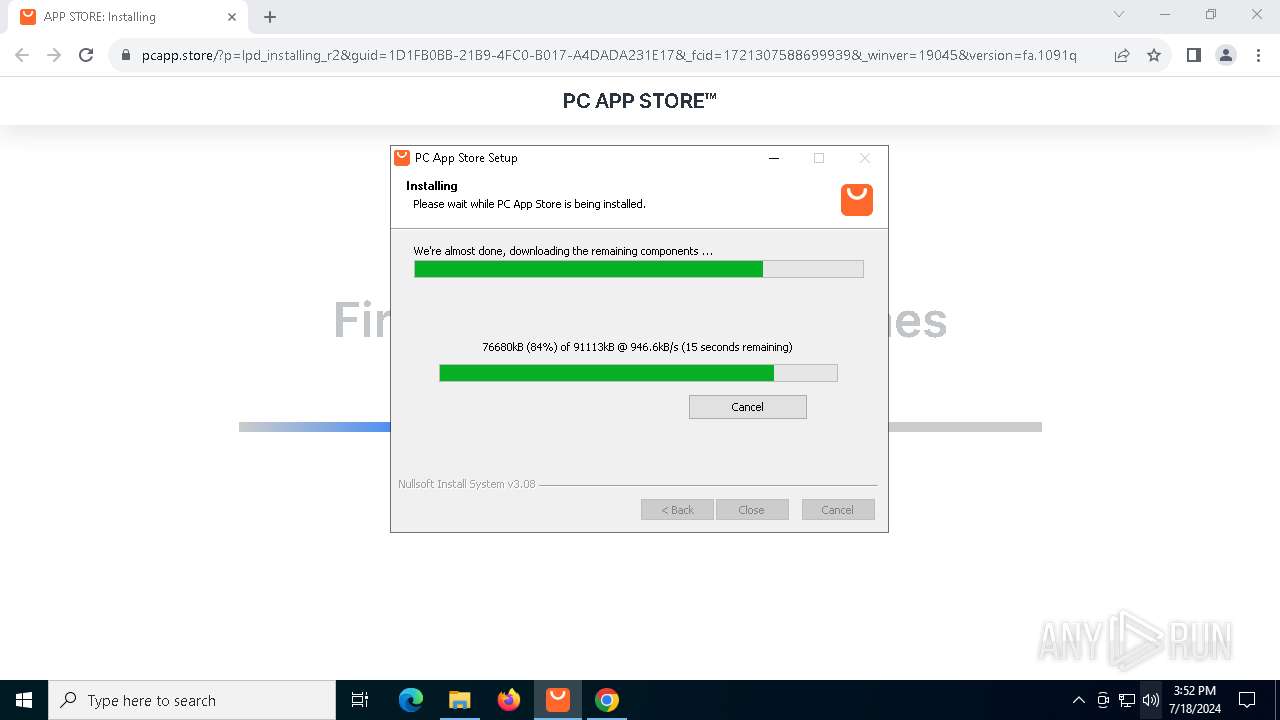
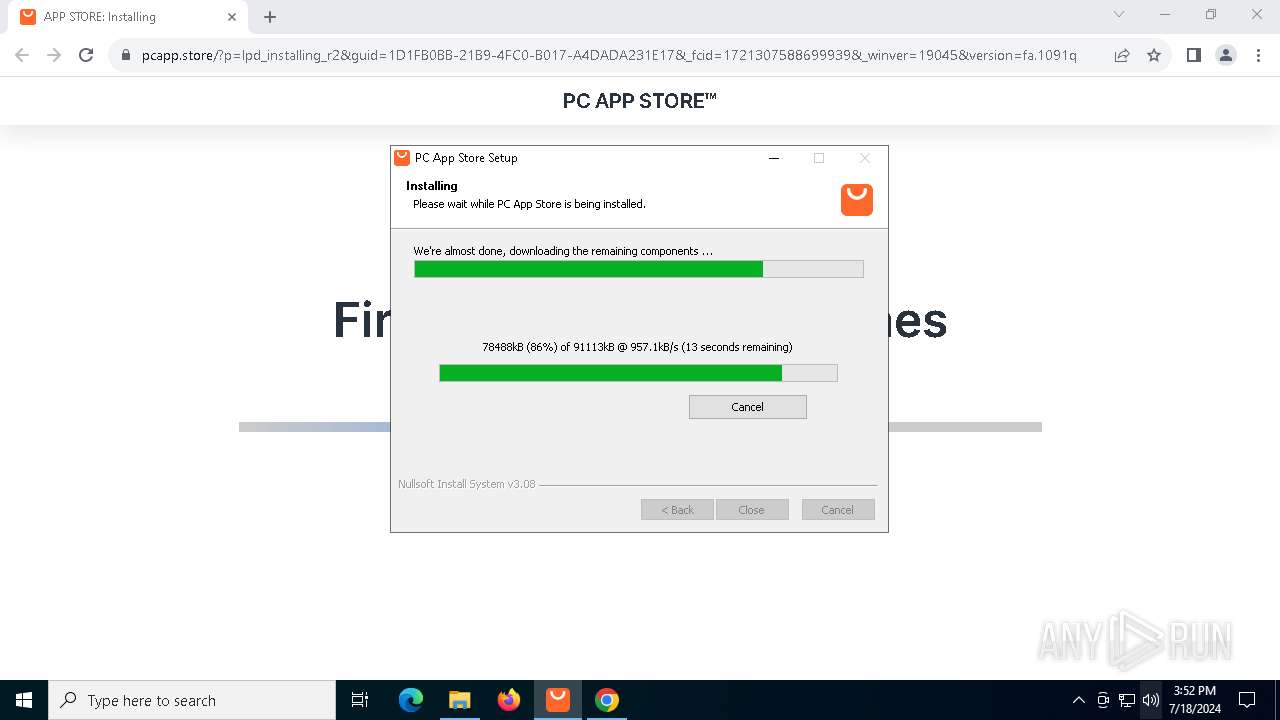
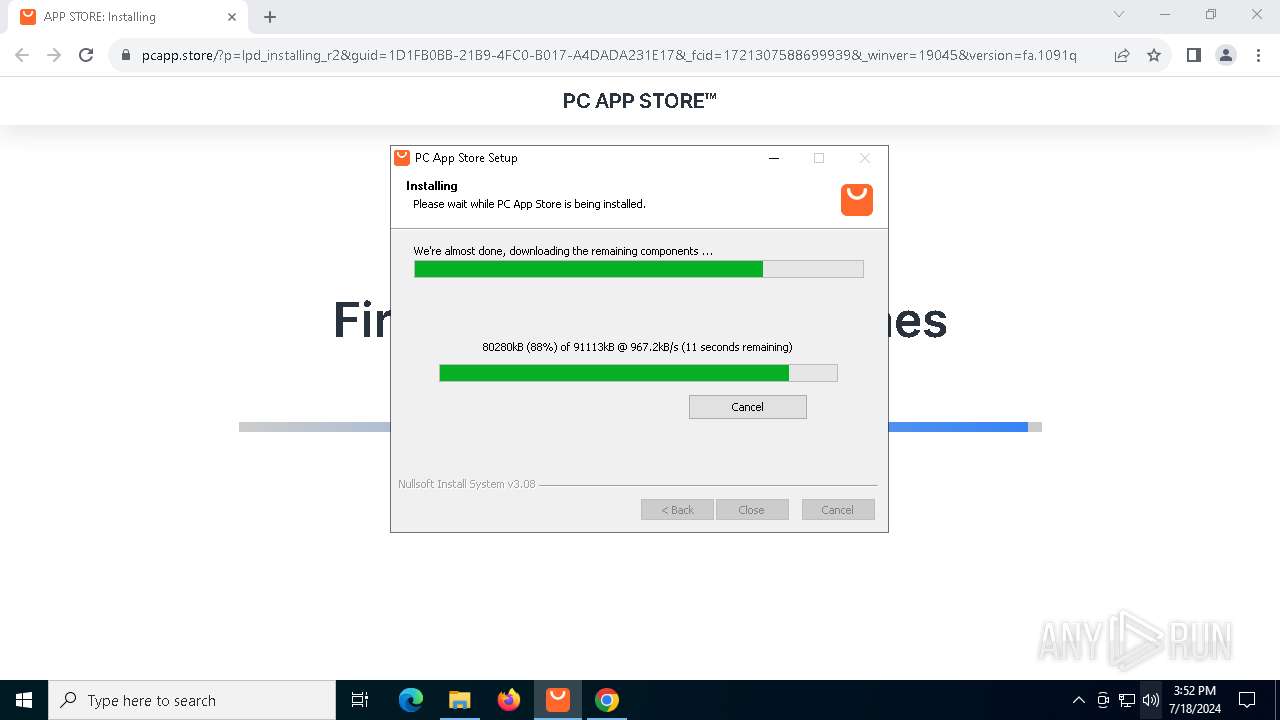
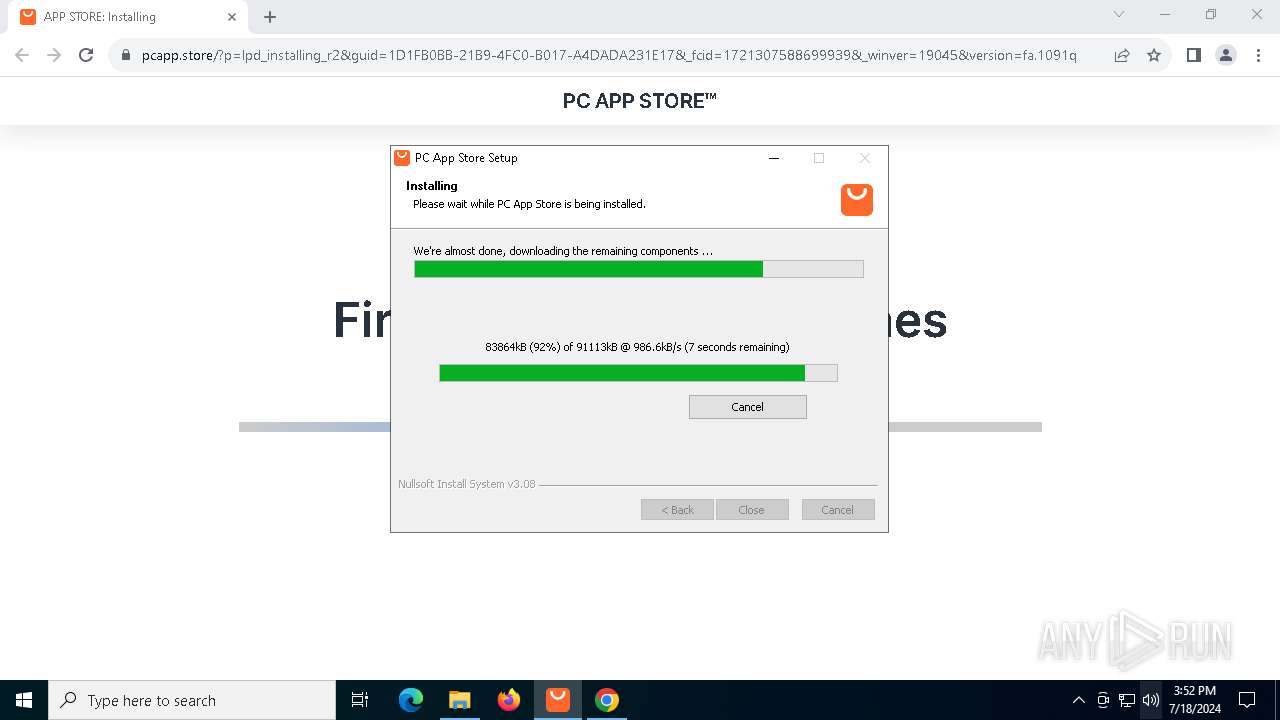
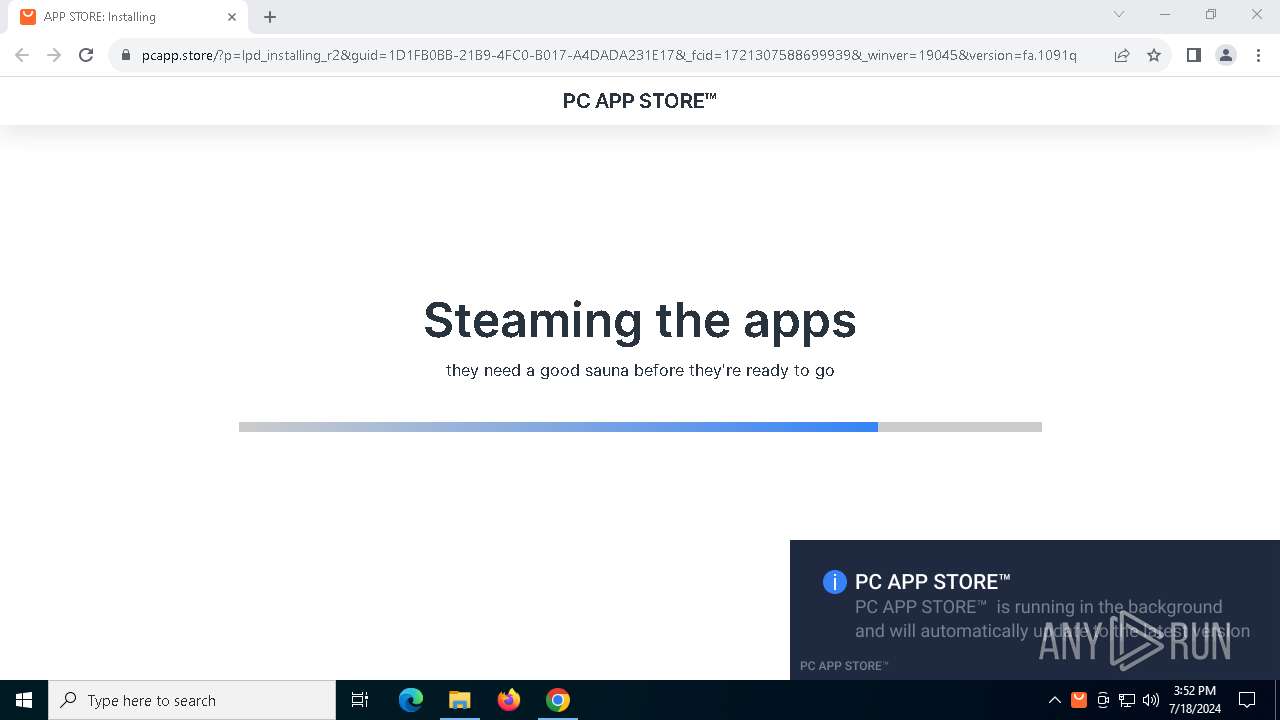
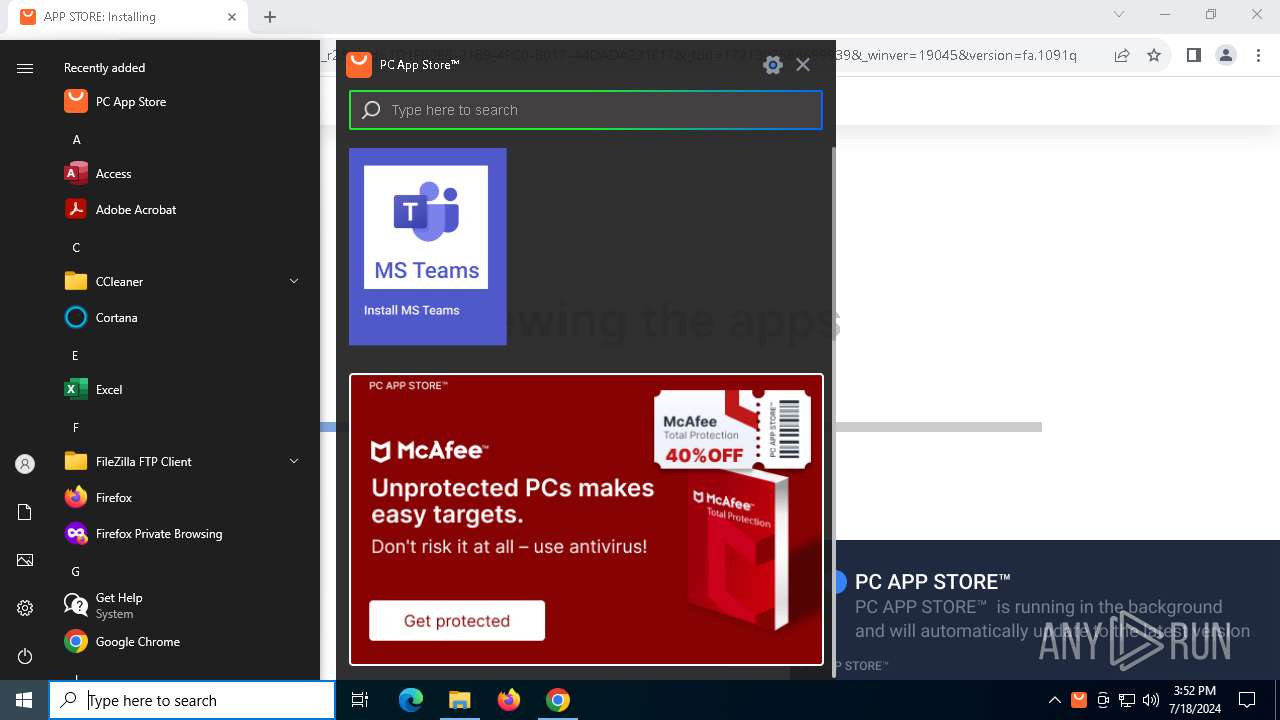
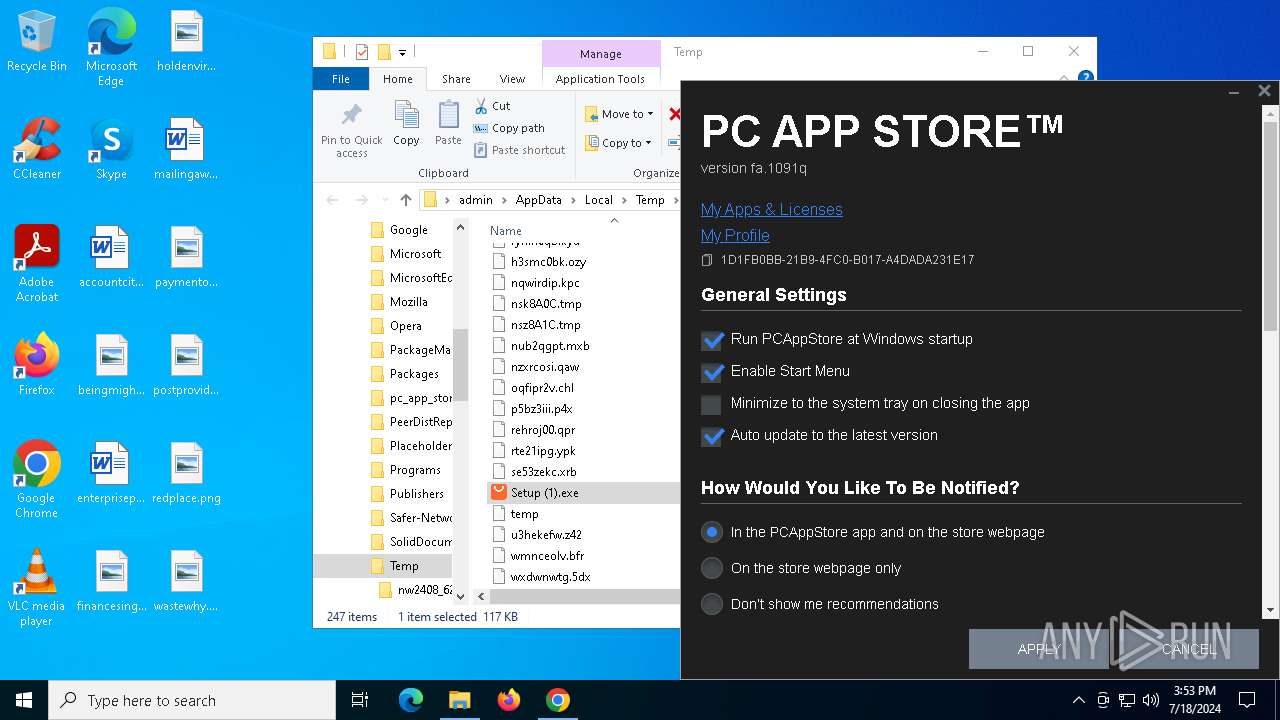
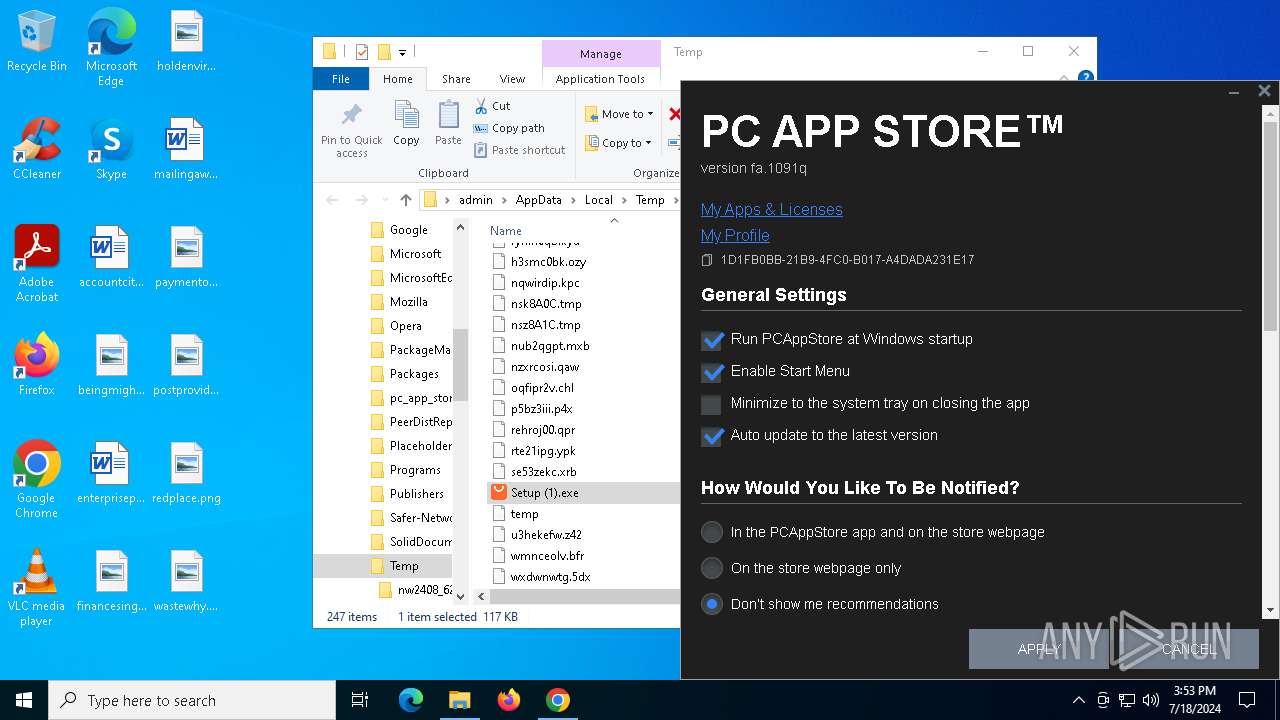
| File name: | Setup (1).exe |
| Full analysis: | https://app.any.run/tasks/b6294738-1224-48ab-ba9a-51de99cb1f64 |
| Verdict: | Malicious activity |
| Analysis date: | July 18, 2024, 15:49:33 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | E04FD9DECCD57BB0B26FF5132EA51BBD |
| SHA1: | 3ADE0F370874FE0029FA86EBCA31E7B0CE166B38 |
| SHA256: | F354B08DC1CF70F2504B1D6277AEBF260749BB4E780827376F9BC3030CFCC40E |
| SSDEEP: | 3072:aefw3AuNAP+5g3WBo9A/BwdKIkIXgtqr4gJ:a0wP3g4o9AWxHwtWd |
MALICIOUS
Drops the executable file immediately after the start
- Setup (1).exe (PID: 8008)
- Setup (1).exe (PID: 3872)
- nsk8A0C.tmp (PID: 1796)
Changes the autorun value in the registry
- nsk8A0C.tmp (PID: 1796)
Scans artifacts that could help determine the target
- Watchdog.exe (PID: 4956)
SUSPICIOUS
Malware-specific behavior (creating "System.dll" in Temp)
- Setup (1).exe (PID: 8008)
- Setup (1).exe (PID: 3872)
- nsk8A0C.tmp (PID: 1796)
Searches for installed software
- Setup (1).exe (PID: 8008)
- Setup (1).exe (PID: 3872)
- nsk8A0C.tmp (PID: 1796)
Reads security settings of Internet Explorer
- Setup (1).exe (PID: 8008)
- Setup (1).exe (PID: 3872)
- nsk8A0C.tmp (PID: 1796)
- Watchdog.exe (PID: 4956)
Executable content was dropped or overwritten
- Setup (1).exe (PID: 8008)
- Setup (1).exe (PID: 3872)
- nsk8A0C.tmp (PID: 1796)
The process creates files with name similar to system file names
- Setup (1).exe (PID: 8008)
- Setup (1).exe (PID: 3872)
- nsk8A0C.tmp (PID: 1796)
Checks Windows Trust Settings
- Setup (1).exe (PID: 8008)
- Setup (1).exe (PID: 3872)
- nsk8A0C.tmp (PID: 1796)
- Watchdog.exe (PID: 4956)
Reads the date of Windows installation
- SystemSettings.exe (PID: 7448)
Starts application with an unusual extension
- Setup (1).exe (PID: 3872)
Creates a software uninstall entry
- nsk8A0C.tmp (PID: 1796)
Process drops legitimate windows executable
- nsk8A0C.tmp (PID: 1796)
Application launched itself
- NW_store.exe (PID: 2408)
The process checks if it is being run in the virtual environment
- NW_store.exe (PID: 2408)
INFO
Checks supported languages
- Setup (1).exe (PID: 8008)
- SystemSettings.exe (PID: 7448)
- Setup (1).exe (PID: 3872)
- nsk8A0C.tmp (PID: 1796)
- PcAppStore.exe (PID: 6140)
- Watchdog.exe (PID: 4956)
- NW_store.exe (PID: 2408)
- NW_store.exe (PID: 4296)
- NW_store.exe (PID: 2252)
- NW_store.exe (PID: 7348)
- NW_store.exe (PID: 7528)
- NW_store.exe (PID: 7960)
- NW_store.exe (PID: 6256)
- NW_store.exe (PID: 8464)
- NW_store.exe (PID: 8288)
- NW_store.exe (PID: 6636)
- msiexec.exe (PID: 8420)
Reads the computer name
- Setup (1).exe (PID: 8008)
- SystemSettings.exe (PID: 7448)
- Setup (1).exe (PID: 3872)
- Watchdog.exe (PID: 4956)
- PcAppStore.exe (PID: 6140)
- nsk8A0C.tmp (PID: 1796)
- NW_store.exe (PID: 2408)
- NW_store.exe (PID: 2252)
- NW_store.exe (PID: 7348)
- NW_store.exe (PID: 4296)
- NW_store.exe (PID: 6256)
- NW_store.exe (PID: 8288)
- NW_store.exe (PID: 8464)
- NW_store.exe (PID: 6636)
- NW_store.exe (PID: 7960)
- msiexec.exe (PID: 8420)
Checks proxy server information
- Setup (1).exe (PID: 8008)
- Setup (1).exe (PID: 3872)
- Watchdog.exe (PID: 4956)
- nsk8A0C.tmp (PID: 1796)
- NW_store.exe (PID: 2408)
Create files in a temporary directory
- Setup (1).exe (PID: 8008)
- Setup (1).exe (PID: 3872)
- nsk8A0C.tmp (PID: 1796)
- NW_store.exe (PID: 2408)
Reads the machine GUID from the registry
- Setup (1).exe (PID: 8008)
- SystemSettings.exe (PID: 7448)
- Setup (1).exe (PID: 3872)
- nsk8A0C.tmp (PID: 1796)
- Watchdog.exe (PID: 4956)
- NW_store.exe (PID: 2408)
Reads the software policy settings
- Setup (1).exe (PID: 8008)
- SystemSettings.exe (PID: 7448)
- Setup (1).exe (PID: 3872)
- nsk8A0C.tmp (PID: 1796)
- Watchdog.exe (PID: 4956)
- PcAppStore.exe (PID: 6140)
Creates files or folders in the user directory
- Setup (1).exe (PID: 8008)
- Setup (1).exe (PID: 3872)
- nsk8A0C.tmp (PID: 1796)
- Watchdog.exe (PID: 4956)
- NW_store.exe (PID: 2408)
- NW_store.exe (PID: 4296)
- NW_store.exe (PID: 7348)
Reads Microsoft Office registry keys
- SystemSettings.exe (PID: 7448)
- Setup (1).exe (PID: 3872)
- chrome.exe (PID: 1332)
- NW_store.exe (PID: 2408)
Manual execution by a user
- Setup (1).exe (PID: 3872)
- Taskmgr.exe (PID: 8980)
- Taskmgr.exe (PID: 8904)
Reads Environment values
- Setup (1).exe (PID: 3872)
- PcAppStore.exe (PID: 6140)
- NW_store.exe (PID: 4296)
The process uses the downloaded file
- chrome.exe (PID: 3444)
- chrome.exe (PID: 7100)
- chrome.exe (PID: 7636)
- chrome.exe (PID: 5320)
- chrome.exe (PID: 3772)
- chrome.exe (PID: 2484)
- chrome.exe (PID: 7428)
- chrome.exe (PID: 2720)
Application launched itself
- chrome.exe (PID: 1332)
Process checks computer location settings
- NW_store.exe (PID: 2408)
- NW_store.exe (PID: 7528)
- NW_store.exe (PID: 7960)
Reads security settings of Internet Explorer
- Taskmgr.exe (PID: 8980)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2021:09:25 21:57:46+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 27136 |
| InitializedDataSize: | 186880 |
| UninitializedDataSize: | 2048 |
| EntryPoint: | 0x352d |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.1091 |
| ProductVersionNumber: | 1.0.0.1091 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
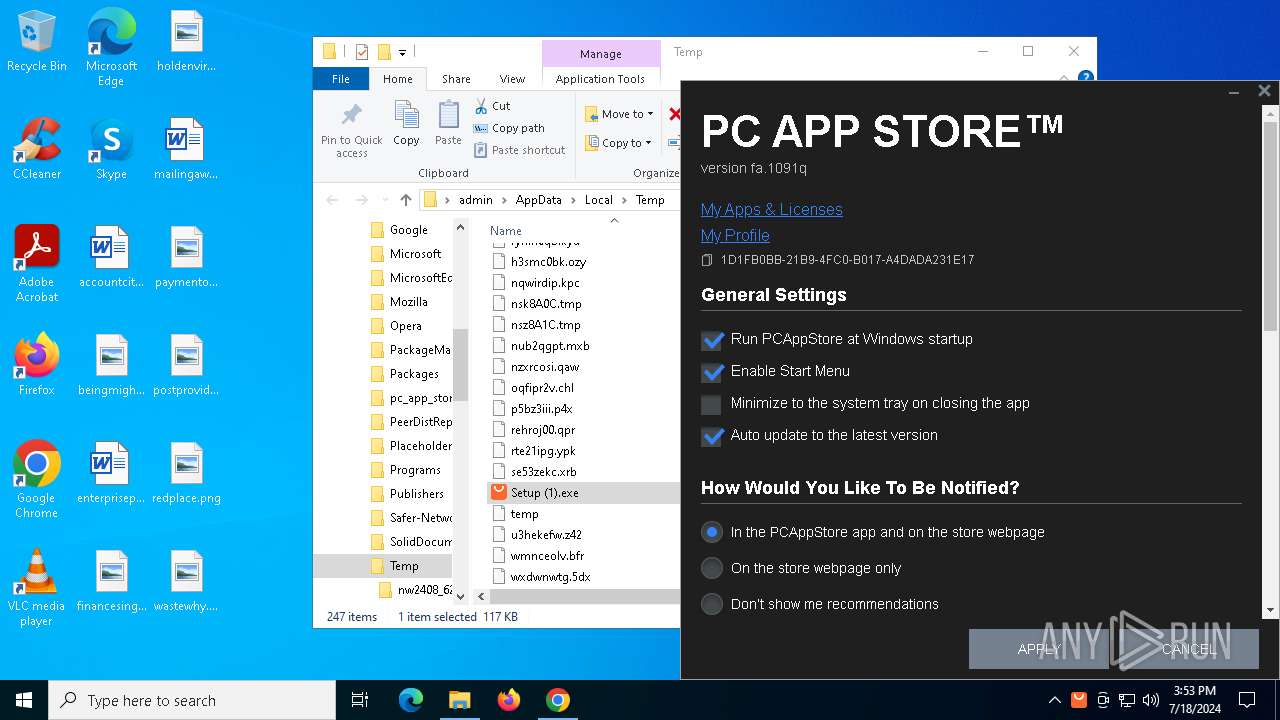
| CompanyName: | Fast Corporation LTD |
| FileDescription: | PC App Store Setup |
| LegalCopyright: | Fast Corporation LTD |
| ProductName: | PC App Store |
| ProductVersion: | 1.0.0.1091p |
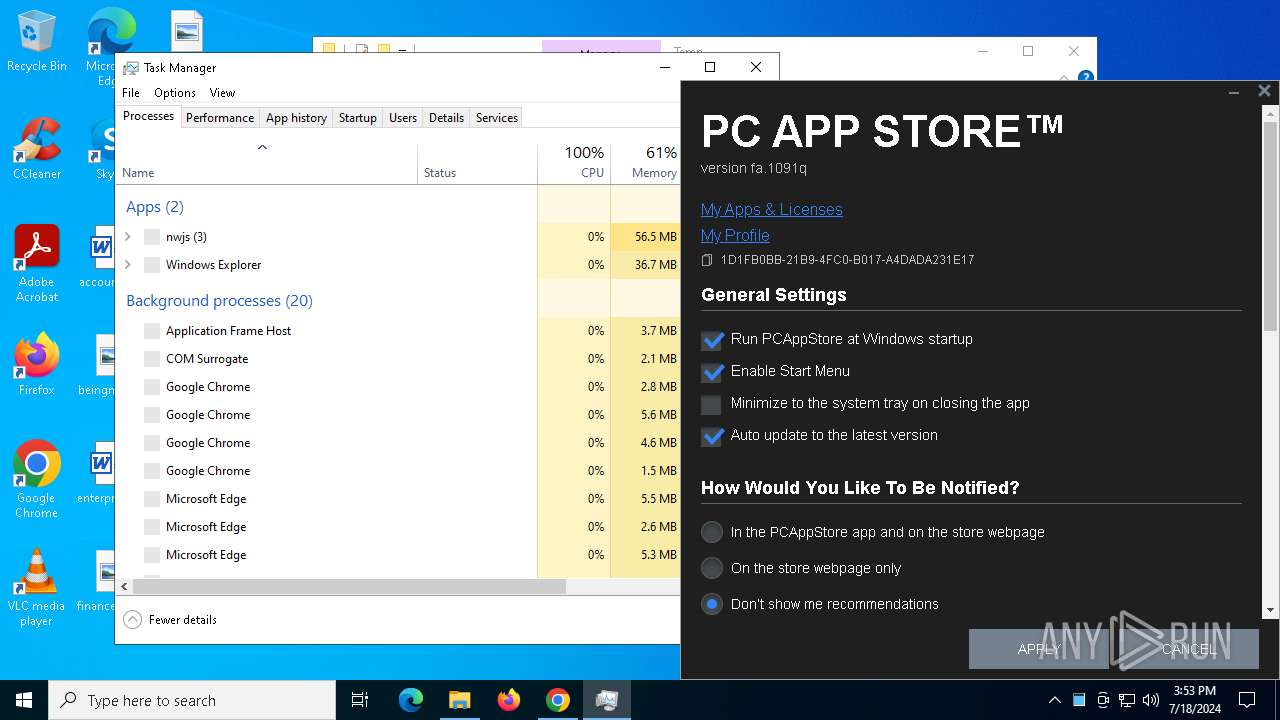
Total processes
225
Monitored processes
54
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1332 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --single-argument https://pcapp.store/installing.php?guid=1D1FB0BB-21B9-4FC0-B017-A4DADA231E17&winver=19045&version=fa.1091q&nocache=20240718155040.347&_fcid=1721307588699939 | C:\Program Files\Google\Chrome\Application\chrome.exe | Setup (1).exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1652 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.ProcessorMetrics --lang=en-US --service-sandbox-type=none --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5364 --field-trial-handle=1896,i,2066770564113373688,12923805757501603702,262144 --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1796 | "C:\Users\admin\AppData\Local\Temp\nsk8A0C.tmp" /internal 1721307588699939 /force | C:\Users\admin\AppData\Local\Temp\nsk8A0C.tmp | Setup (1).exe | ||||||||||||
User: admin Company: Fast Corporation LTD Integrity Level: MEDIUM Description: PC App Store Full Setup Exit code: 0 Modules
| |||||||||||||||
| 1940 | C:\WINDOWS\system32\DllHost.exe /Processid:{49F171DD-B51A-40D3-9A6C-52D674CC729D} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2252 | "C:\Users\admin\PCAppStore\nwjs\NW_store.exe" --type=gpu-process --no-sandbox --user-data-dir="C:\Users\admin\AppData\Local\pc_app_store\User Data" --nwapp-path=".\ui\." --no-appcompat-clear --start-stack-profiler --gpu-preferences=WAAAAAAAAADgAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=1812 --field-trial-handle=1816,i,9069999704661012722,5444006244033513164,262144 --variations-seed-version /prefetch:2 | C:\Users\admin\PCAppStore\nwjs\NW_store.exe | — | NW_store.exe | |||||||||||
User: admin Company: The NW.js Community Integrity Level: MEDIUM Description: nwjs Version: 0.85.0 Modules
| |||||||||||||||
| 2344 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5720 --field-trial-handle=1896,i,2066770564113373688,12923805757501603702,262144 --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 2408 | .\nwjs\NW_store.exe .\ui\. | C:\Users\admin\PCAppStore\nwjs\NW_store.exe | PcAppStore.exe | ||||||||||||
User: admin Company: The NW.js Community Integrity Level: MEDIUM Description: nwjs Version: 0.85.0 Modules
| |||||||||||||||
| 2484 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5560 --field-trial-handle=1896,i,2066770564113373688,12923805757501603702,262144 --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 2720 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5520 --field-trial-handle=1896,i,2066770564113373688,12923805757501603702,262144 --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 2788 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5600 --field-trial-handle=1896,i,2066770564113373688,12923805757501603702,262144 --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
Total events
73 685
Read events
73 407
Write events
258
Delete events
20
Modification events
| (PID) Process: | (8008) Setup (1).exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (8008) Setup (1).exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (8008) Setup (1).exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (8008) Setup (1).exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (8008) Setup (1).exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (8008) Setup (1).exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (8008) Setup (1).exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (7448) SystemSettings.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | @C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\Office16\oregres.dll,-202 |
Value: Outlook | |||
| (PID) Process: | (7448) SystemSettings.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
| (PID) Process: | (7448) SystemSettings.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
30
Suspicious files
404
Text files
189
Unknown types
25
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 8008 | Setup (1).exe | C:\Users\admin\AppData\Local\Temp\nst96F0.tmp\System.dll | executable | |
MD5:CFF85C549D536F651D4FB8387F1976F2 | SHA256:8DC562CDA7217A3A52DB898243DE3E2ED68B80E62DDCB8619545ED0B4E7F65A8 | |||
| 8008 | Setup (1).exe | C:\Users\admin\AppData\Local\Temp\nst96F0.tmp\image.gif | image | |
MD5:1636218C14C357455B5C872982E2A047 | SHA256:9B8B6285BF65F086E08701EEE04E57F2586E973A49C5A38660C9C6502A807045 | |||
| 8008 | Setup (1).exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_C39E9DBC666D19C07EEE7CD1E11AF8BE | der | |
MD5:D7CFD87D2D1A59ACC6443ACD93CB4089 | SHA256:0576DB75395022CA95FAD6719744E2F17BD89579F050ED2B74A19360FA1EFAA7 | |||
| 7448 | SystemSettings.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\US41F8KGHFA1DYBV7TIS.temp | binary | |
MD5:4FCB2A3EE025E4A10D21E1B154873FE2 | SHA256:90BF6BAA6F968A285F88620FBF91E1F5AA3E66E2BAD50FD16F37913280AD8228 | |||
| 7448 | SystemSettings.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\f18460fded109990.customDestinations-ms | binary | |
MD5:4FCB2A3EE025E4A10D21E1B154873FE2 | SHA256:90BF6BAA6F968A285F88620FBF91E1F5AA3E66E2BAD50FD16F37913280AD8228 | |||
| 8008 | Setup (1).exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\773CFF2C7835D48C4E76FE153DBA9F81_15174A80589B8DAF9768E9131F4845C0 | der | |
MD5:72C99859294BDF196EFA531B094E676E | SHA256:F260E649FDAAC223446061E47B47E0BE2EB17395AFDA46567EFB2E109F90978E | |||
| 8008 | Setup (1).exe | C:\Users\admin\AppData\Local\Temp\nst96F0.tmp\inetc.dll | executable | |
MD5:A35CDC9CF1D17216C0AB8C5282488EAD | SHA256:A793929232AFB78B1C5B2F45D82094098BCF01523159FAD1032147D8D5F9C4DF | |||
| 8008 | Setup (1).exe | C:\Users\admin\AppData\Local\Temp\nst96F0.tmp\modern-wizard.bmp | image | |
MD5:CBE40FD2B1EC96DAEDC65DA172D90022 | SHA256:3AD2DC318056D0A2024AF1804EA741146CFC18CC404649A44610CBF8B2056CF2 | |||
| 8008 | Setup (1).exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_C39E9DBC666D19C07EEE7CD1E11AF8BE | binary | |
MD5:749BAA5BDF8859D80D4ED26A521949ED | SHA256:D49105B55F0540614786E8A5BE88B01D32C2F29BEB0F14667AF448DFFD042971 | |||
| 1332 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
57
TCP/UDP connections
176
DNS requests
139
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5880 | svchost.exe | HEAD | 200 | 217.20.56.44:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/da421fd3-a679-418c-8790-7cfcec77ad0a?P1=1721432074&P2=404&P3=2&P4=n7IBRQOej%2bXMyCST9BQ%2fx6ZdKhVrX94zjxaubV05BytO5vqaha2kLTr%2fOeVyOatxUb%2f9uyVy%2bRErAUbp0BSI8w%3d%3d | unknown | — | — | whitelisted |
5880 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acwavsfwh3s4nh7vrki6xlktdmna_8947/hfnkpimlhhgieaddgfemjhofmfblmnib_8947_all_pq56432f76miemv5un42hrb7pa.crx3 | unknown | — | — | whitelisted |
5880 | svchost.exe | GET | 200 | 217.20.56.44:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/da421fd3-a679-418c-8790-7cfcec77ad0a?P1=1721432074&P2=404&P3=2&P4=n7IBRQOej%2bXMyCST9BQ%2fx6ZdKhVrX94zjxaubV05BytO5vqaha2kLTr%2fOeVyOatxUb%2f9uyVy%2bRErAUbp0BSI8w%3d%3d | unknown | — | — | whitelisted |
5880 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acwavsfwh3s4nh7vrki6xlktdmna_8947/hfnkpimlhhgieaddgfemjhofmfblmnib_8947_all_pq56432f76miemv5un42hrb7pa.crx3 | unknown | — | — | whitelisted |
5880 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acwavsfwh3s4nh7vrki6xlktdmna_8947/hfnkpimlhhgieaddgfemjhofmfblmnib_8947_all_pq56432f76miemv5un42hrb7pa.crx3 | unknown | — | — | whitelisted |
8008 | Setup (1).exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAsllCLO2YEqFaBOmVKKDvo%3D | unknown | — | — | whitelisted |
8008 | Setup (1).exe | GET | 200 | 192.229.221.95:80 | http://status.rapidssl.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRJiUKgT2m88fZ4nxc1Lu6M%2FjvkagQUDNtsgkkPSmcKuBTuesRIUojrVjgCEAJsJgstJqiVbIfWU4Raykw%3D | unknown | — | — | whitelisted |
5628 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
5880 | svchost.exe | HEAD | 200 | 217.20.56.44:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/6e6d05a2-47e8-42b8-85a0-e8b7ee48333a?P1=1721432074&P2=404&P3=2&P4=LzL5580BMpA%2b1KPlYfFp3BDcc2weIn4W6UJzDEDqRxgF%2fCE%2fp7K3Sl4ZwEsAir8I1INRaFe9390oGmpiwYPiIA%3d%3d | unknown | — | — | whitelisted |
5880 | svchost.exe | GET | 206 | 217.20.56.44:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/6e6d05a2-47e8-42b8-85a0-e8b7ee48333a?P1=1721432074&P2=404&P3=2&P4=LzL5580BMpA%2b1KPlYfFp3BDcc2weIn4W6UJzDEDqRxgF%2fCE%2fp7K3Sl4ZwEsAir8I1INRaFe9390oGmpiwYPiIA%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1796 | backgroundTaskHost.exe | 20.74.47.205:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | unknown |
4716 | svchost.exe | 40.126.31.67:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7856 | svchost.exe | 4.209.32.198:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
2760 | svchost.exe | 40.113.110.67:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
8008 | Setup (1).exe | 167.99.235.203:443 | pcapp.store | DIGITALOCEAN-ASN | US | unknown |
8008 | Setup (1).exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1796 | backgroundTaskHost.exe | 20.223.36.55:443 | fd.api.iris.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
3548 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
arc.msn.com |
| whitelisted |
login.live.com |
| whitelisted |
google.com |
| whitelisted |
pcapp.store |
| unknown |
ocsp.digicert.com |
| whitelisted |
status.rapidssl.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
cxcs.microsoft.net |
| whitelisted |