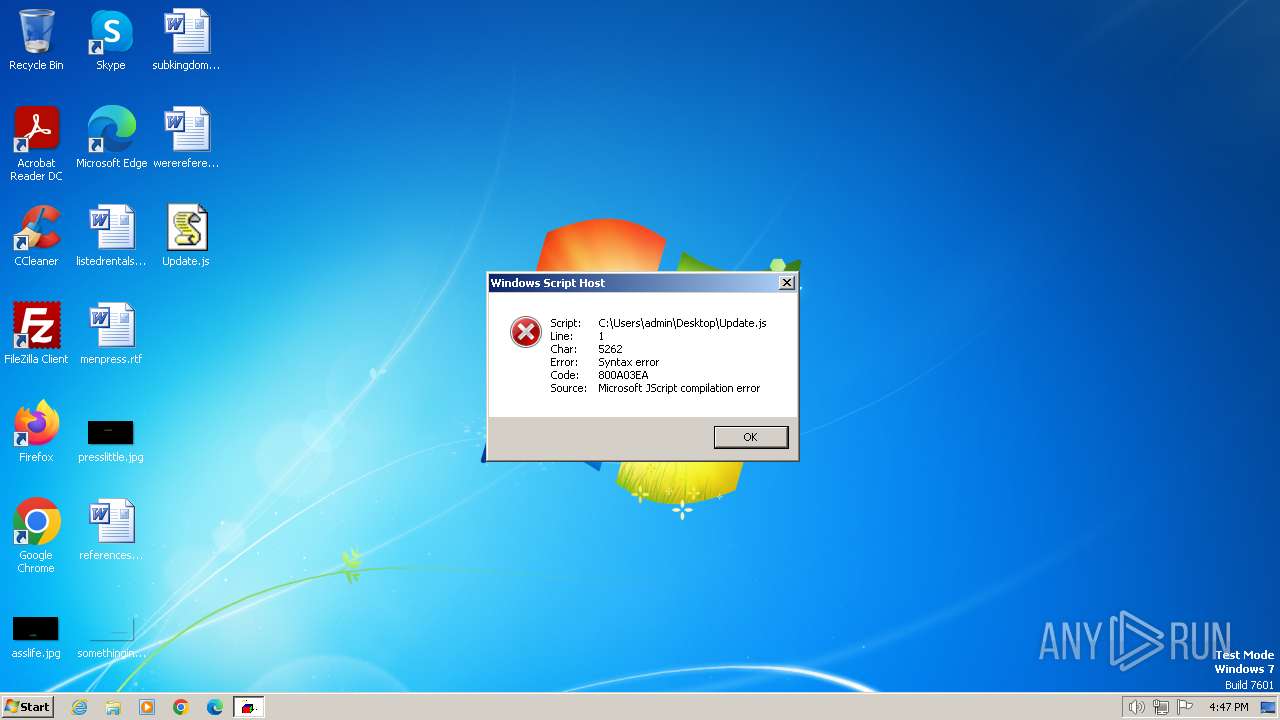
| File name: | Update.js |
| Full analysis: | https://app.any.run/tasks/89a80e42-2675-4ae5-99da-67165e63bb76 |
| Verdict: | Malicious activity |
| Analysis date: | December 19, 2023, 16:47:40 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| MIME: | text/plain |
| File info: | ASCII text, with very long lines, with no line terminators |
| MD5: | 2014FDDB53584D0719B8DF68F178A5B4 |
| SHA1: | 2D5C69A34AA0FF29404CE66568E41AC557E9A3FA |
| SHA256: | F342BA18CDDCEA3D9E1749635A31A7AE366EC3E06DB7B4D0588CAF31C0584D61 |
| SSDEEP: | 96:BkmmA2SxJ//fAt58DEZU0CBJJZ3LMjq+QU7PUBhGSH/1gHi3KJVym:BzL/fAteDW+mgvvGS1gHi3+gm |
MALICIOUS
Unusual connection from system programs
- wscript.exe (PID: 2036)
- wscript.exe (PID: 572)
Sends HTTP request (SCRIPT)
- wscript.exe (PID: 2036)
Connects to the CnC server
- wscript.exe (PID: 2036)
- wscript.exe (PID: 572)
Opens an HTTP connection (SCRIPT)
- wscript.exe (PID: 572)
- wscript.exe (PID: 2036)
Creates internet connection object (SCRIPT)
- wscript.exe (PID: 572)
- wscript.exe (PID: 2036)
SUSPICIOUS
Adds, changes, or deletes HTTP request header (SCRIPT)
- wscript.exe (PID: 572)
- wscript.exe (PID: 2036)
Reads the Internet Settings
- wscript.exe (PID: 572)
- wscript.exe (PID: 2036)
Adds/modifies Windows certificates
- wscript.exe (PID: 572)
- wscript.exe (PID: 2036)
INFO
Manual execution by a user
- wscript.exe (PID: 572)
Checks proxy server information
- wscript.exe (PID: 572)
- wscript.exe (PID: 2036)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
37
Monitored processes
2
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 572 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\Desktop\Update.js" | C:\Windows\System32\wscript.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2036 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\Desktop\Update.js" | C:\Windows\System32\wscript.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
Total events
6 678
Read events
6 589
Write events
81
Delete events
8
Modification events
| (PID) Process: | (2036) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2036) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2036) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2036) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2036) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2036) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000005B010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A8016B000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2036) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2036) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2036) wscript.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2036) wscript.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\D1CBCA5DB2D52A7F693B674DE5F05A1D0C957DF0 |
| Operation: | write | Name: | Blob |
Value: 53000000010000004300000030413022060C2B06010401B231010201050130123010060A2B0601040182373C0101030200C0301B060567810C010330123010060A2B0601040182373C0101030200C019000000010000001000000076935B5C5A037216DAAF8AAC76DF42C16200000001000000200000004FF460D54B9C86DABFBCFC5712E0400D2BED3FBC4D4FBDAA86E06ADCD2A9AD7A0B00000001000000180000005300650063007400690067006F00200045004300430000001400000001000000140000003AE10986D4CF19C29676744976DCE035C663639A1D0000000100000010000000280CF6042C30A2646644BA7286A3AA97030000000100000014000000D1CBCA5DB2D52A7F693B674DE5F05A1D0C957DF00F00000001000000300000000B043572C899DEC43EFD590CFCE610CF443A6315925EBFE589F7506907E44824608489581C7CA0E041458514CF157614090000000100000054000000305206082B0601050507030206082B06010505070303060A2B0601040182370A030406082B0601050507030406082B0601050507030606082B0601050507030706082B0601050507030106082B060105050703082000000001000000930200003082028F30820215A00302010202105C8B99C55A94C5D27156DECD8980CC26300A06082A8648CE3D040303308188310B3009060355040613025553311330110603550408130A4E6577204A6572736579311430120603550407130B4A65727365792043697479311E301C060355040A131554686520555345525452555354204E6574776F726B312E302C06035504031325555345525472757374204543432043657274696669636174696F6E20417574686F72697479301E170D3130303230313030303030305A170D3338303131383233353935395A308188310B3009060355040613025553311330110603550408130A4E6577204A6572736579311430120603550407130B4A65727365792043697479311E301C060355040A131554686520555345525452555354204E6574776F726B312E302C06035504031325555345525472757374204543432043657274696669636174696F6E20417574686F726974793076301006072A8648CE3D020106052B81040022036200041AAC545AA9F96823E77AD5246F53C65AD84BABC6D5B6D1E67371AEDD9CD60C61FDDBA08903B80514EC57CEEE5D3FE221B3CEF7D48A79E0A3837E2D97D061C4F199DC259163AB7F30A3B470E2C7A1339CF3BF2E5C53B15FB37D327F8A34E37979A3423040301D0603551D0E041604143AE10986D4CF19C29676744976DCE035C663639A300E0603551D0F0101FF040403020106300F0603551D130101FF040530030101FF300A06082A8648CE3D040303036800306502303667A11608DCE49700411D4EBEE16301CF3BAA421164A09D94390211795C7B1DFA64B9EE1642B3BF8AC209C4ECE4B14D023100E92A61478C524A4B4E1870F6D644D66EF583BA6D58BD24D95648EAEFC4A24681886A3A46D1A99B4DC961DAD15D576A18 | |||
Executable files
0
Suspicious files
8
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2036 | wscript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:2DF0E9E8064BC38E188E83C703D9AD7D | SHA256:95212AABA48CF66EF2DC6F33FC3579B3A44BE1042AAA06A0671EF1C0694DB90C | |||
| 2036 | wscript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\D0E1C4B6144E7ECAB3F020E4A19EFC29_03D1B482EE3032A122274428715A4E19 | binary | |
MD5:7F78DC0922A5E5F3FDD763A7242FF247 | SHA256:A4144C8306C7ECCF425E1FE78B2625CAA3A6C5F07D9DBE9753BF7F2BB56673DC | |||
| 2036 | wscript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B2FAF7692FD9FFBD64EDE317E42334BA_89854CA6A0F0936A4D2ECA78845CEA25 | binary | |
MD5:E263CED6BDA9E52D36099503278F53B4 | SHA256:AD55B329093B70235CE4C94ED374E8199AF1E86F02CA19A055FDAE8F22036C4A | |||
| 2036 | wscript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\D0E1C4B6144E7ECAB3F020E4A19EFC29_03D1B482EE3032A122274428715A4E19 | binary | |
MD5:7702BEF1CCF9A05E26CD48BB322C3BC4 | SHA256:BD121C276765D3BC996901F884E1E1FE782DCC18A937E6C1E138B6146DDF50AA | |||
| 2036 | wscript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\55D154709C8645E5B12AFD2F40C68DF6 | binary | |
MD5:88BCEB7B0BFA54FF13AD2BBD4AD0BCF7 | SHA256:AAF68409FF2FA07D0D51F8EAD3E23F1AC4CB9CF67D6D76A774FEA6024A979EE2 | |||
| 2036 | wscript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\55D154709C8645E5B12AFD2F40C68DF6 | binary | |
MD5:15E65F9D41AFE5988C584E39A661C272 | SHA256:C1ECDDE33DE0F3D92BBF1D31DED6030B7306D892A9FD91A61852207B897D557F | |||
| 2036 | wscript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B2FAF7692FD9FFBD64EDE317E42334BA_89854CA6A0F0936A4D2ECA78845CEA25 | binary | |
MD5:16EAC5FDF2DBFBAAE86AE8307806E6F9 | SHA256:A3F2AC69F1E5845B3ECB759B495477117BBA3A00FD02A813E08D0CFC8E87BBD1 | |||
| 2036 | wscript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
11
DNS requests
6
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2036 | wscript.exe | GET | 200 | 23.32.238.161:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?bab2a3bbcdb1182e | unknown | compressed | 4.66 Kb | unknown |
2036 | wscript.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEFZnHQTqT5lMbxCBR1nSdZQ%3D | unknown | binary | 1.42 Kb | unknown |
2036 | wscript.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSr83eyJy3njhjVpn5bEpfc6MXawQQUOuEJhtTPGcKWdnRJdtzgNcZjY5oCECO3bePBuysaUZYeCOq3ZOg%3D | unknown | binary | 978 b | unknown |
2036 | wscript.exe | GET | 200 | 172.64.149.23:80 | http://zerossl.ocsp.sectigo.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBQzH%2F4%2F%2FQuEFihPlI1WwH4Dktj2TQQUD2vmS845R672fpAeefAwkZLIX6MCEQCEk8%2FXA9XCejmwdJiqlPU2 | unknown | binary | 316 b | unknown |
1080 | svchost.exe | GET | 304 | 2.19.198.75:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?57666a24cb959564 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2036 | wscript.exe | 104.168.142.48:443 | jchdq.scheme.corycabana.net | HOSTWINDS | US | unknown |
2036 | wscript.exe | 23.32.238.161:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2036 | wscript.exe | 104.18.38.233:80 | ocsp.comodoca.com | CLOUDFLARENET | — | shared |
2036 | wscript.exe | 172.64.149.23:80 | ocsp.comodoca.com | CLOUDFLARENET | US | unknown |
572 | wscript.exe | 104.168.142.48:443 | jchdq.scheme.corycabana.net | HOSTWINDS | US | unknown |
1080 | svchost.exe | 2.19.198.75:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
jchdq.scheme.corycabana.net |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
zerossl.ocsp.sectigo.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE SocGholish CnC Domain in DNS Lookup (* .scheme .corycabana .net) |
2036 | wscript.exe | Domain Observed Used for C2 Detected | ET MALWARE SocGholish CnC Domain in TLS SNI (* .scheme .corycabana .net) |
2036 | wscript.exe | Misc activity | ET INFO Observed ZeroSSL SSL/TLS Certificate |
572 | wscript.exe | Domain Observed Used for C2 Detected | ET MALWARE SocGholish CnC Domain in TLS SNI (* .scheme .corycabana .net) |
572 | wscript.exe | Misc activity | ET INFO Observed ZeroSSL SSL/TLS Certificate |