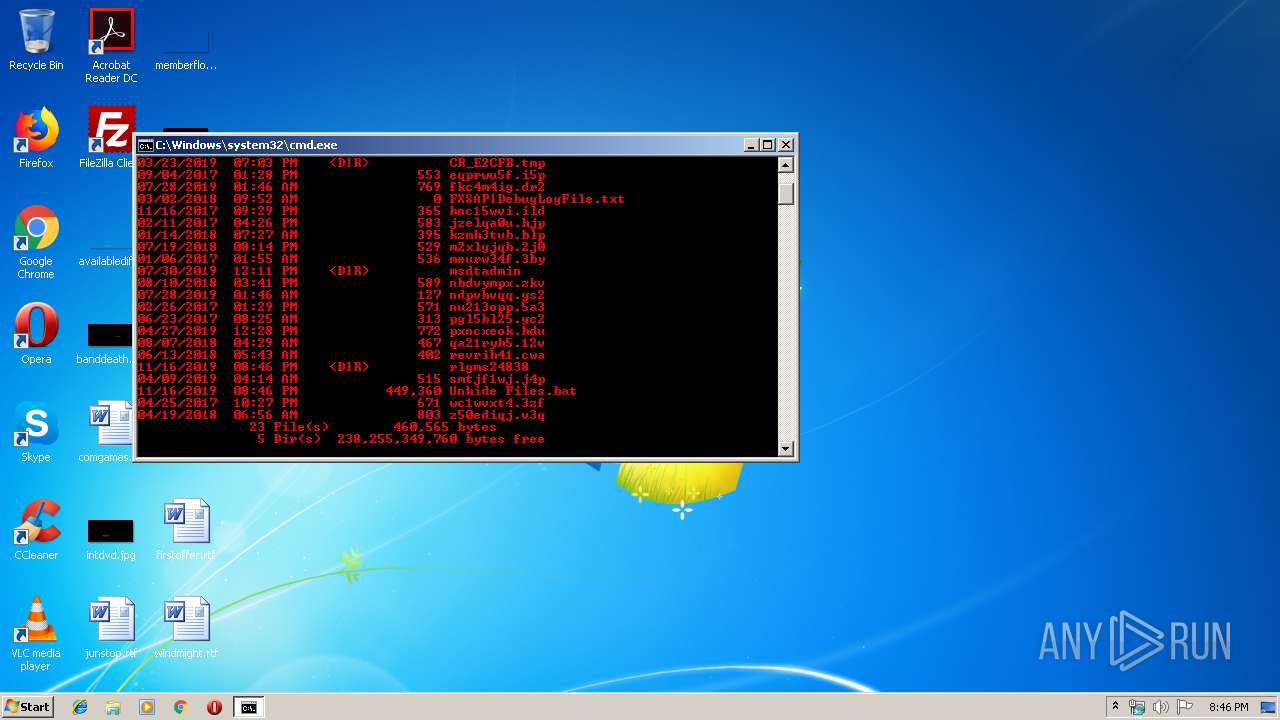
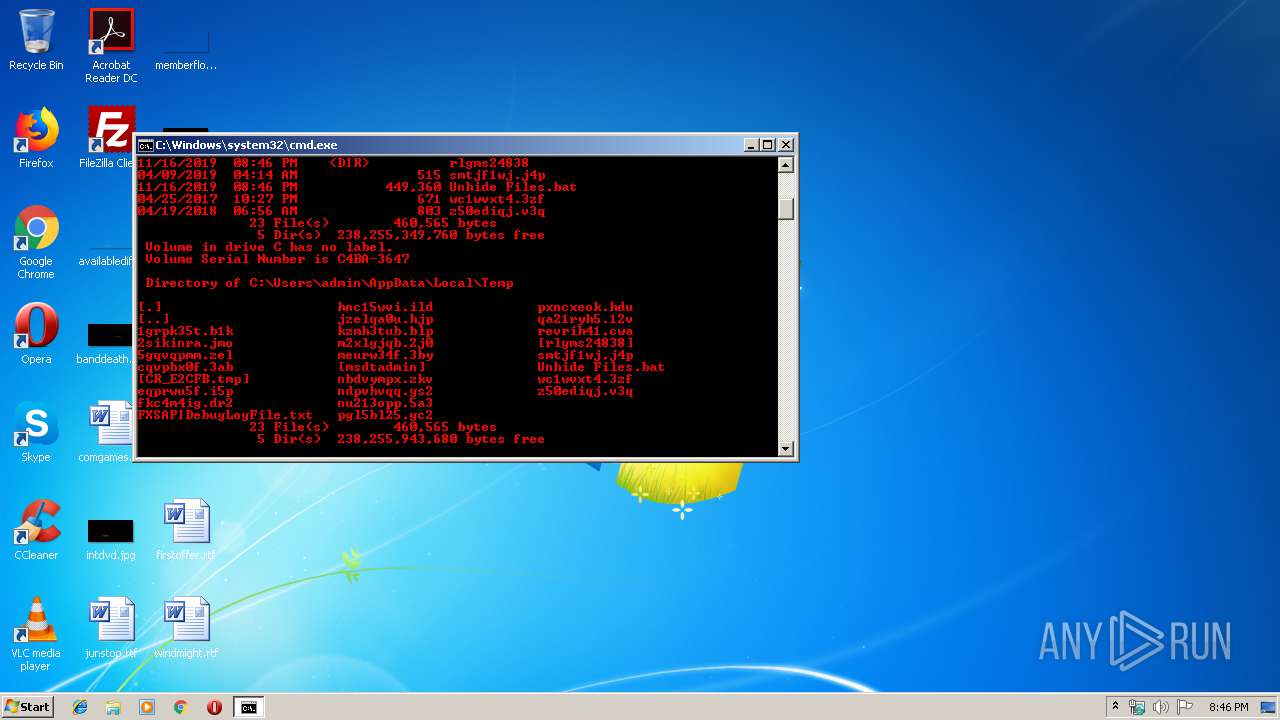
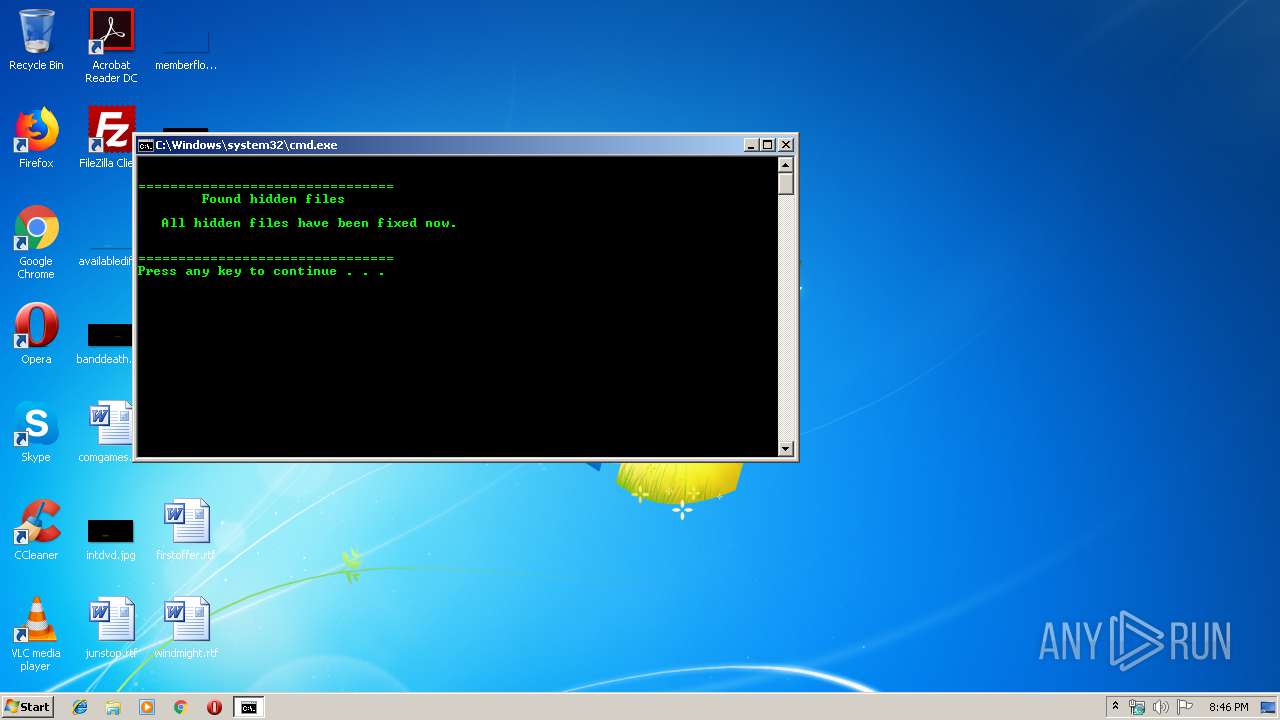
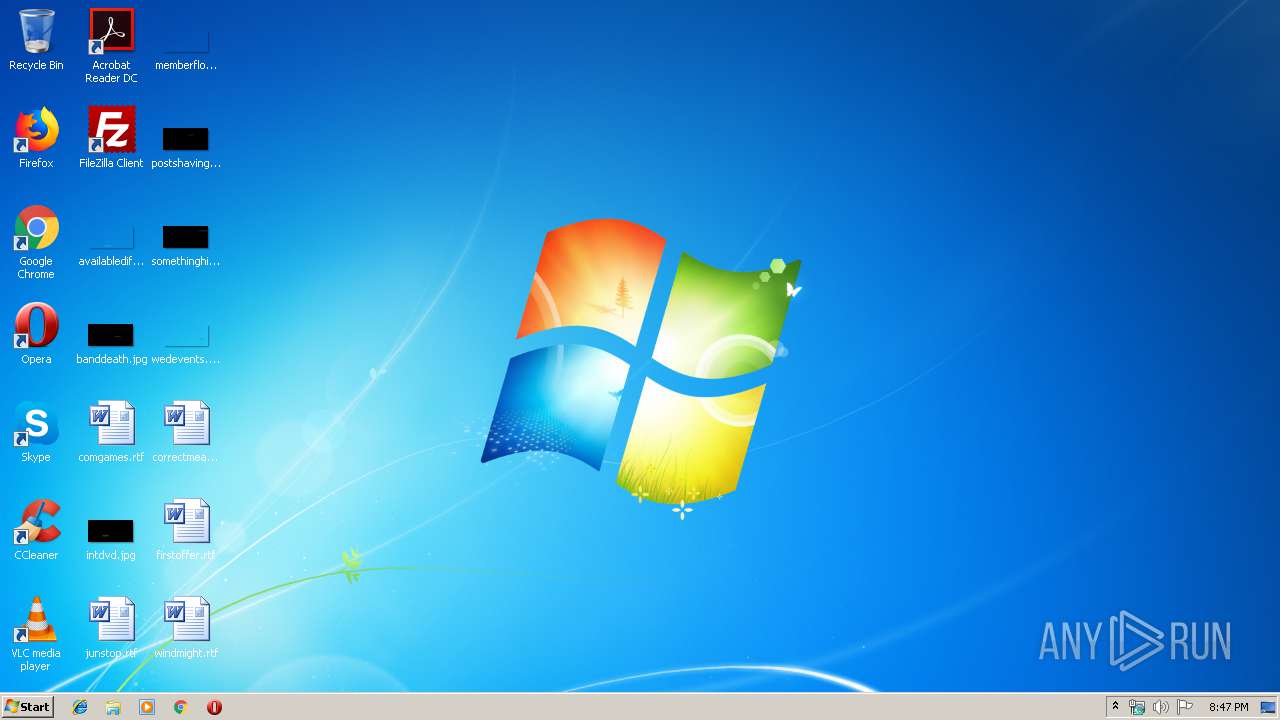
| File name: | Unhide Files.bat |
| Full analysis: | https://app.any.run/tasks/423105c4-a392-4375-a8b5-a96769b07987 |
| Verdict: | Malicious activity |
| Analysis date: | November 16, 2019, 20:46:40 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/octet-stream |
| File info: | data |
| MD5: | ED321251DC3B4F175E68BE78E694474D |
| SHA1: | 9E72DA35F476589E57754A6768E9914D7717F2E0 |
| SHA256: | F335F7098DE9B44F3849B8ADA84FCCA1AC09ED00F8936D60CB3CF8D085EEA2E5 |
| SSDEEP: | 12288:wnVHDWx5jouKbs3wPDdI3N4Pgq9vJvSuuqngHAJ:wnc/YsgrgN45 |
MALICIOUS
Application was dropped or rewritten from another process
- eng.exe (PID: 4064)
- rf.exe (PID: 3892)
- cmd.exe (PID: 2148)
- cmd.exe (PID: 1796)
- cmd.exe (PID: 2644)
- cmd.exe (PID: 236)
- cmd.exe (PID: 3364)
- cmd.exe (PID: 3388)
- cmd.exe (PID: 184)
- cmd.exe (PID: 1732)
- cmd.exe (PID: 3600)
- cmd.exe (PID: 2744)
- cmd.exe (PID: 1792)
- cmd.exe (PID: 1916)
- cmd.exe (PID: 1728)
- cmd.exe (PID: 3112)
- cmd.exe (PID: 2784)
- cmd.exe (PID: 3372)
- cmd.exe (PID: 1912)
- cmd.exe (PID: 3160)
- cmd.exe (PID: 640)
- cmd.exe (PID: 2844)
- cmd.exe (PID: 1012)
- svcnosts.exe (PID: 3980)
- svcnost.exe (PID: 4016)
Runs PING.EXE for delay simulation
- cmd.exe (PID: 2148)
Changes the autorun value in the registry
- rf.exe (PID: 3892)
SUSPICIOUS
Uses REG.EXE to modify Windows registry
- cmd.exe (PID: 236)
- cmd.exe (PID: 2148)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 2148)
- cmd.exe (PID: 2744)
- cmd.exe (PID: 1012)
- cmd.exe (PID: 2844)
- cmd.exe (PID: 1732)
- cmd.exe (PID: 3600)
Executable content was dropped or overwritten
- cmd.exe (PID: 2148)
- eng.exe (PID: 4064)
- rf.exe (PID: 3892)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 2148)
- rf.exe (PID: 3892)
Application launched itself
- cmd.exe (PID: 2148)
Creates executable files which already exist in Windows
- rf.exe (PID: 3892)
Writes to a desktop.ini file (may be used to cloak folders)
- rf.exe (PID: 3892)
Modifies the open verb of a shell class
- rf.exe (PID: 3892)
Starts itself from another location
- svcnosts.exe (PID: 3980)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .bib/bibtex/txt | | | BibTeX references (100) |
|---|
Total processes
107
Monitored processes
51
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 184 | "C:\Windows\system32\cmd.exe" /c cacls n:\sefera\Jnt\null\..\.. /g everyone:f /e /t | C:\Windows\system32\cmd.exe | — | rf.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 3 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 236 | cacls n:\System_VoIume_lnformation\Jnt\null\..\.. /r administrators /e /t | C:\Windows\system32\cacls.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Control ACLs Program Exit code: 3 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 236 | C:\Windows\system32\cmd.exe /c REG QUERY HKCU\SOFTWARE\bt | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 408 | cacls C:\sefera\Jnt\sovoyyboq\..\.. /d everyone /e | C:\Windows\system32\cacls.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Control ACLs Program Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 532 | cacls n:\sefera\Jnt\null\..\.. /g everyone:f /e /t | C:\Windows\system32\cacls.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Control ACLs Program Exit code: 3 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 640 | "C:\Windows\system32\cmd.exe" /c cacls n:\System_VoIume_lnformation\Jnt\null\..\.. /g everyone:f /e /t | C:\Windows\system32\cmd.exe | — | rf.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 3 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1012 | "C:\Windows\system32\cmd.exe" /c attrib C:\sefera\Jnt\sovoyyboq\..\.. +r +s +h | C:\Windows\system32\cmd.exe | — | rf.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1016 | cacls C:\System_VoIume_lnformation\Jnt\uibewyio\..\.. /d admin /e | C:\Windows\system32\cacls.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Control ACLs Program Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1028 | cacls n:\sefera\Jnt\null\..\.. /r administrators /e /t | C:\Windows\system32\cacls.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Control ACLs Program Exit code: 3 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1600 | cacls C:\sefera\Jnt\sovoyyboq\..\.. /d admin /e | C:\Windows\system32\cacls.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Control ACLs Program Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
658
Read events
624
Write events
34
Delete events
0
Modification events
| (PID) Process: | (4064) eng.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (4064) eng.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3892) rf.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3892) rf.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3892) rf.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Microsoft |
| Operation: | write | Name: | STR |
Value: C|sovoyyboq|uibewyio|svcnost|svcnosts | |||
| (PID) Process: | (3892) rf.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | Explorers |
Value: C:\Windows\explorer.exe /root c:\windows\system32\rundll32.exe ..\windows\system32\user32.dll.ShellExecute(%s), C:\System_VoIume_lnformation\Jnt\uibewyio\bmz\explorer.exe, 0xff3leca | |||
| (PID) Process: | (3892) rf.exe | Key: | HKEY_CLASSES_ROOT\.exe |
| Operation: | write | Name: | |
Value: exefiles | |||
| (PID) Process: | (3892) rf.exe | Key: | HKEY_CLASSES_ROOT\exefiles\shell\open\command |
| Operation: | write | Name: | |
Value: "C:\System_VoIume_lnformation\Jnt\uibewyio\explorers.exe" rts "%1" | |||
| (PID) Process: | (4060) reg.exe | Key: | HKEY_CURRENT_USER\Software\bt |
| Operation: | write | Name: | gp |
Value: 20:4 | |||
| (PID) Process: | (3892) rf.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Microsoft |
| Operation: | write | Name: | SLK |
Value: 0 | |||
Executable files
6
Suspicious files
2
Text files
3
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3892 | rf.exe | C:\sefera\Jnt\sovoyyboq\svcnosts.exe | executable | |
MD5:— | SHA256:— | |||
| 3892 | rf.exe | C:\sefera\Jnt\sovoyyboq\gotera.bmp | binary | |
MD5:— | SHA256:— | |||
| 3892 | rf.exe | C:\System_VoIume_lnformation\Jnt\uibewyio\explorers.exe | executable | |
MD5:— | SHA256:— | |||
| 2148 | cmd.exe | C:\Users\admin\AppData\Local\Temp\rlgms24838\unrf.dll | bib | |
MD5:— | SHA256:— | |||
| 3892 | rf.exe | C:\sefera\Jnt\sovoyyboq\svcnost.exe | executable | |
MD5:— | SHA256:— | |||
| 4064 | eng.exe | C:\Users\admin\AppData\Local\Temp\rlgms24838\rf.exe | executable | |
MD5:— | SHA256:— | |||
| 2148 | cmd.exe | C:\Users\admin\AppData\Local\Temp\rlgms24838\eng.exe | executable | |
MD5:D1AB72DB2BEDD2F255D35DA3DA0D4B16 | SHA256:047F3C5A7AB0EA05F35B2CA8037BF62DD4228786D07707064DBD0D46569305D0 | |||
| 3892 | rf.exe | C:\System_VoIume_lnformation\Jnt\uibewyio\gotera.bmp | binary | |
MD5:— | SHA256:— | |||
| 2148 | cmd.exe | C:\Users\admin\AppData\Local\Temp\rlgms24838\sk.js | text | |
MD5:3ABAFFE780DACFD3C83A6D79D3456CD1 | SHA256:1D16BCFDCC3ACBD37D4E39E07DF2FA6F496FB4B9998D6F1D83C5E076860AFC6B | |||
| 3892 | rf.exe | C:\sefera\desktop.ini | ini | |
MD5:ADC4B5D4444D26293DC782B6238CA6F0 | SHA256:ABE8A5933FF450A89B8E9A736F08874B43B7355D17FFE6540C4A6EAD0F0995D3 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
2
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4016 | svcnost.exe | 151.101.1.195:443 | clear-march.firebaseapp.com | Fastly | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clear-march.firebaseapp.com |
| malicious |