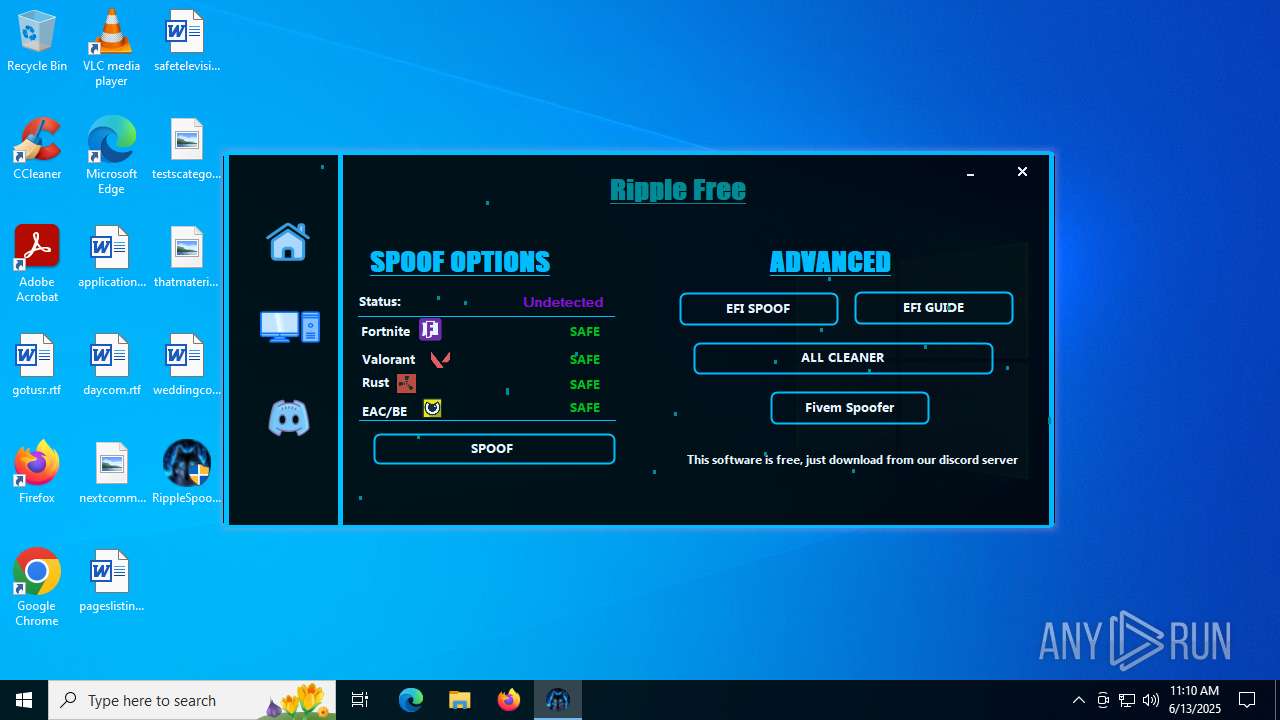
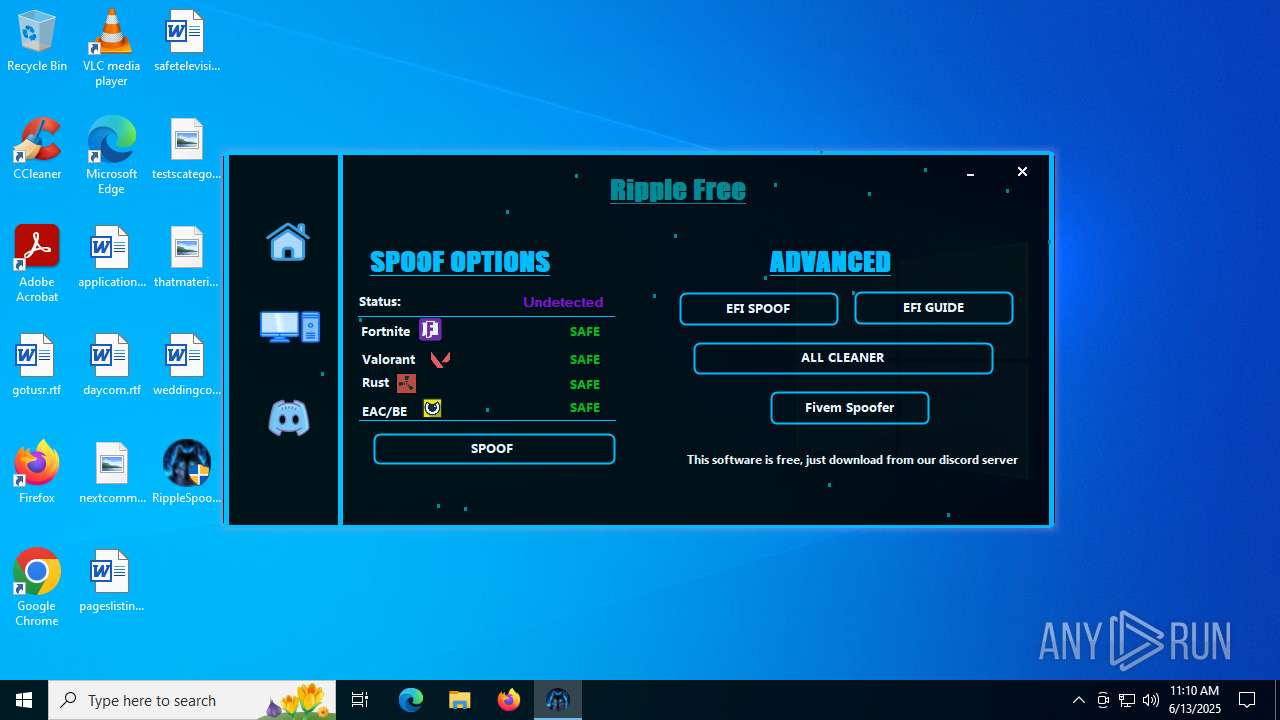
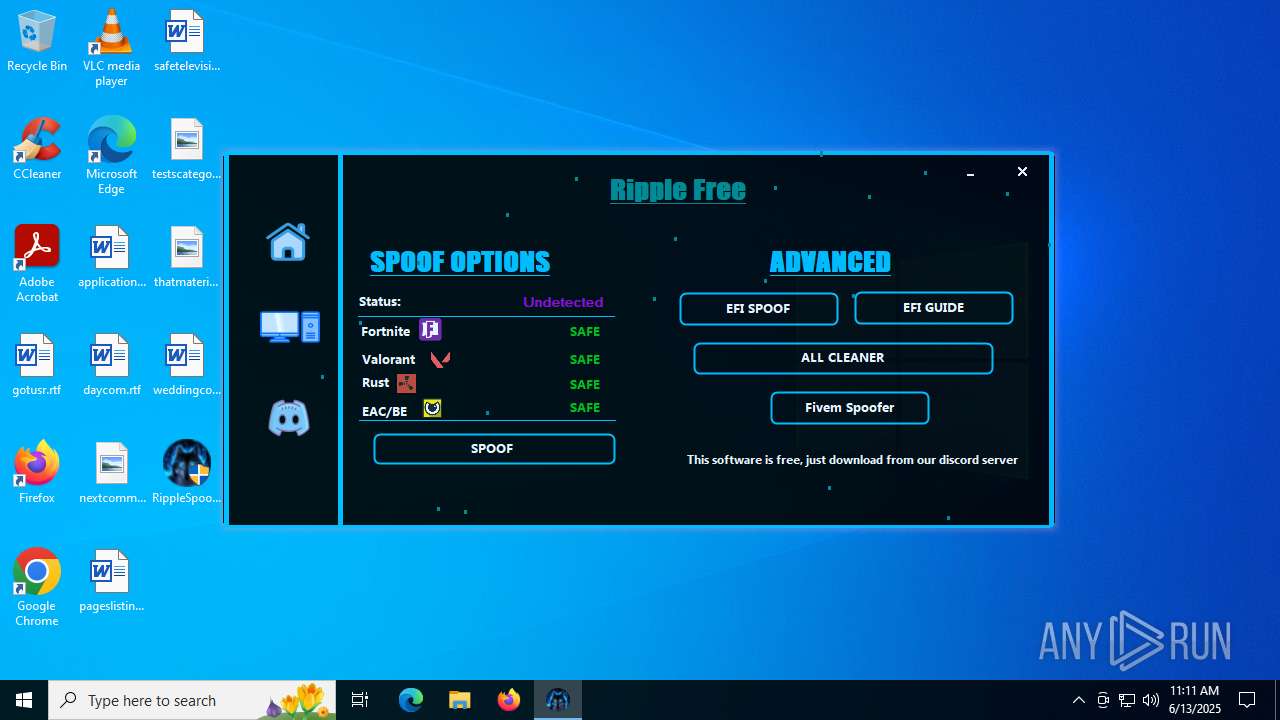
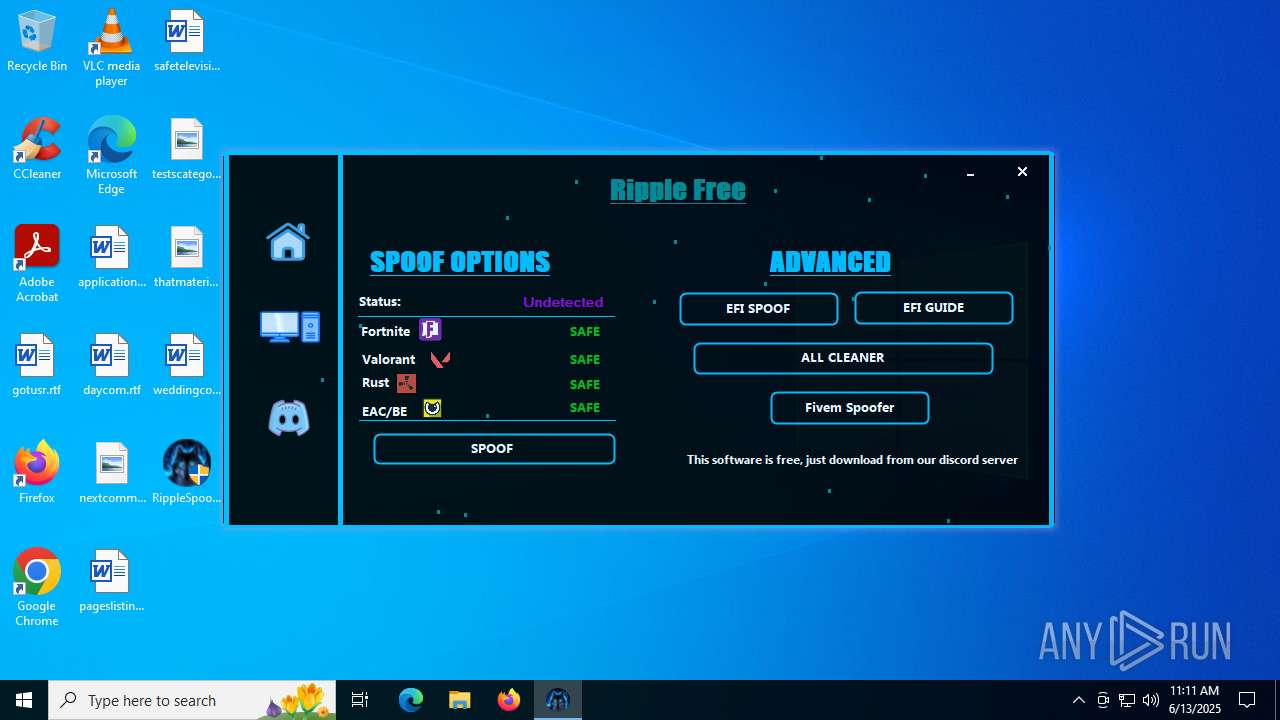
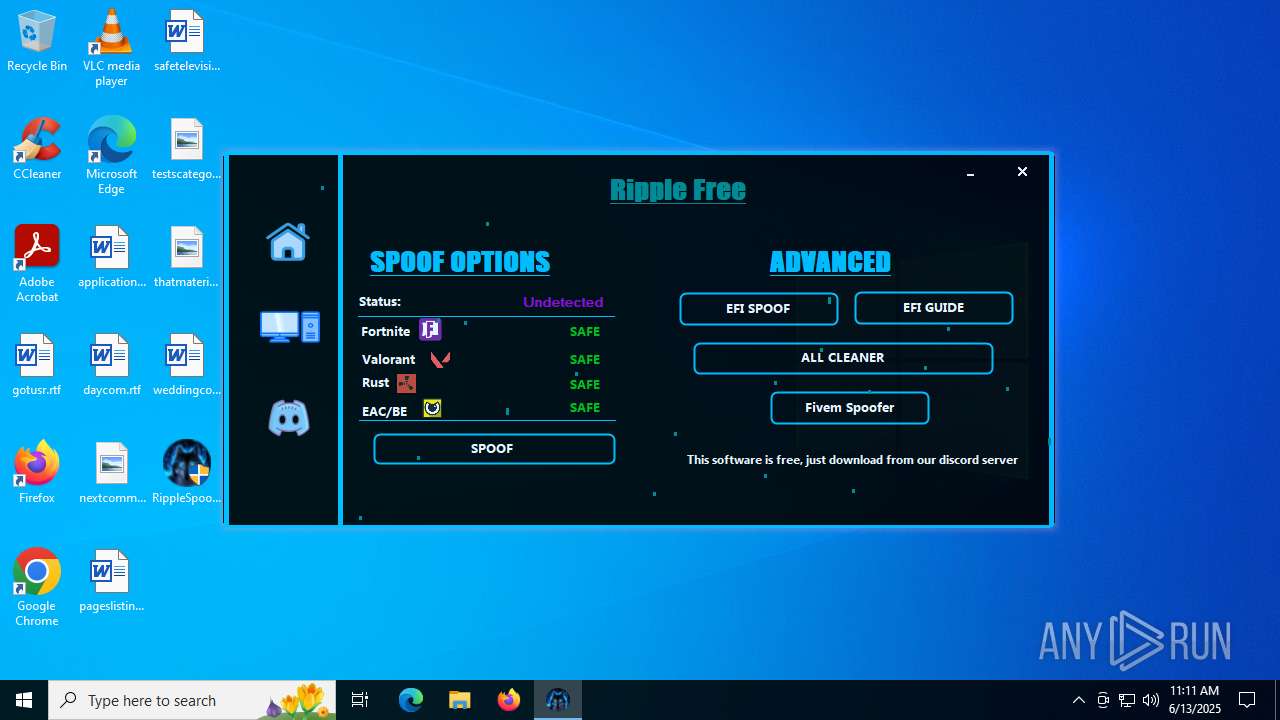
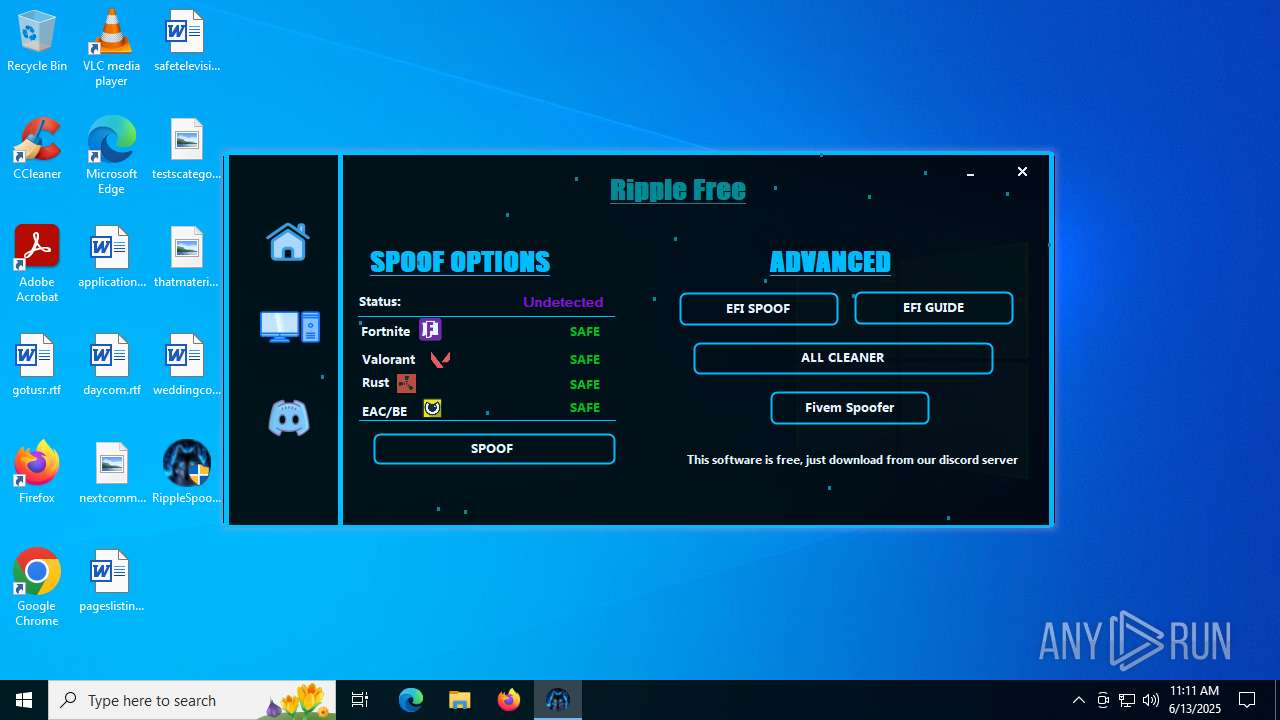
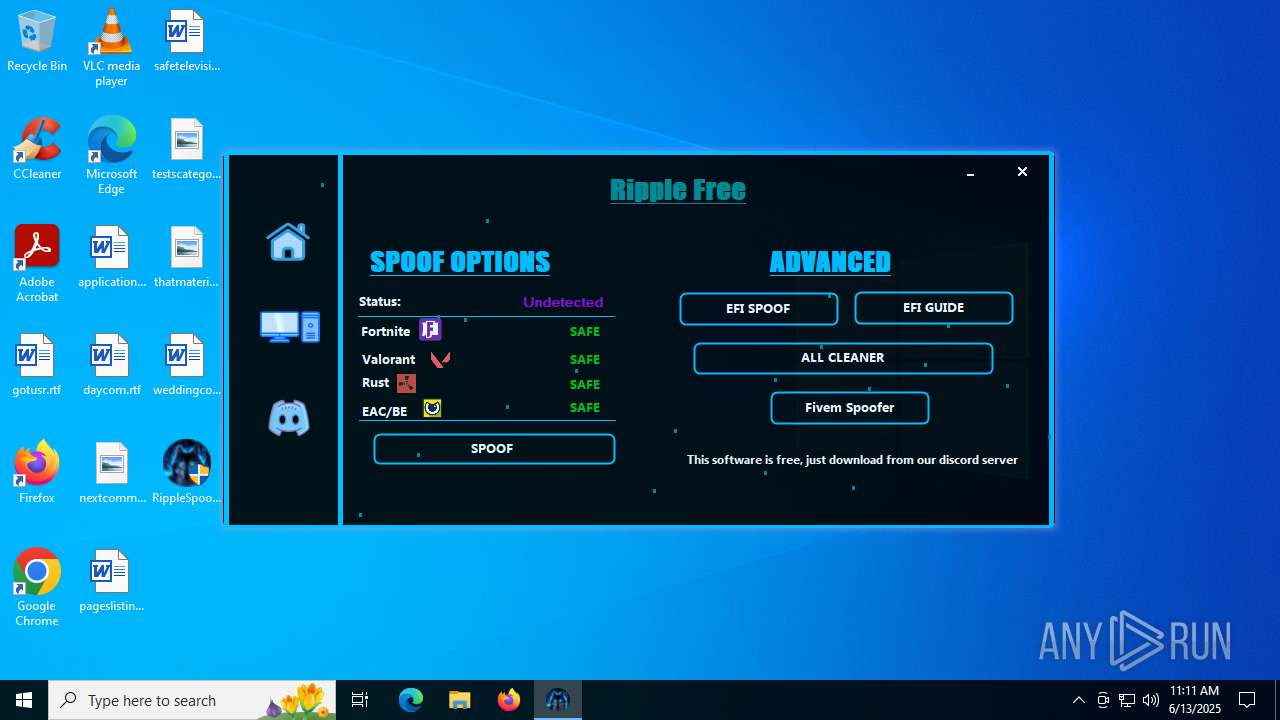
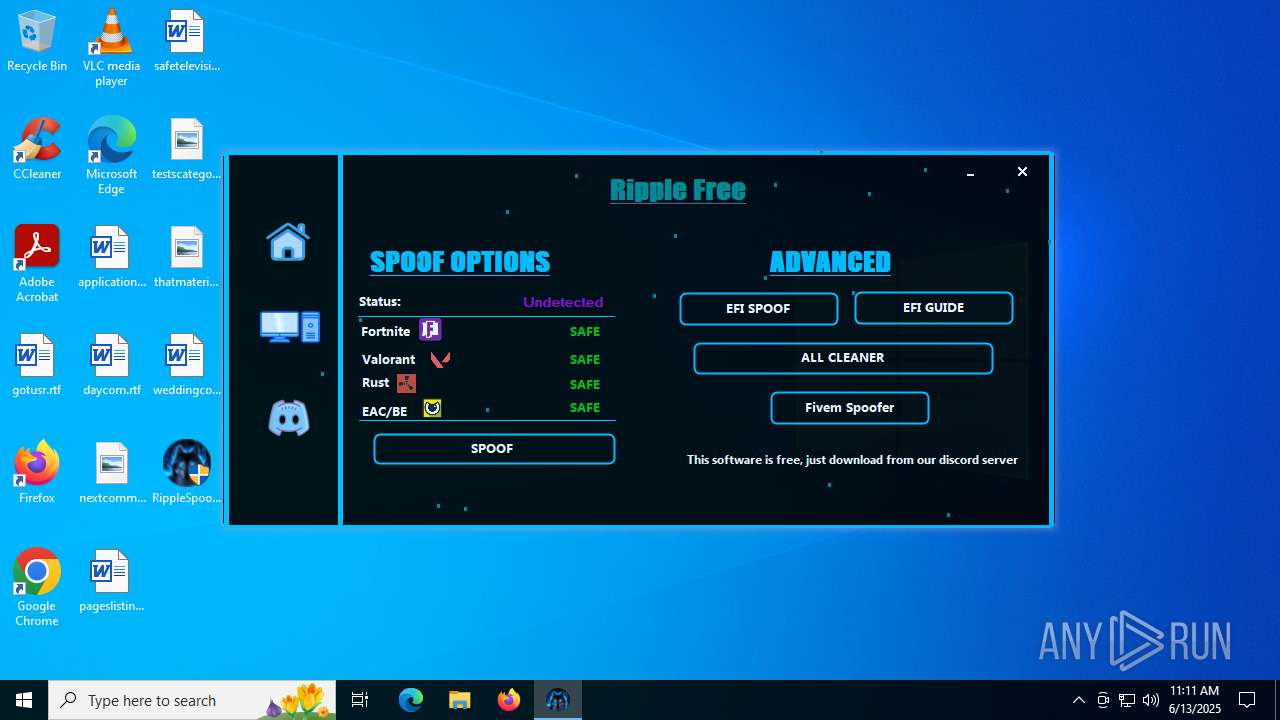
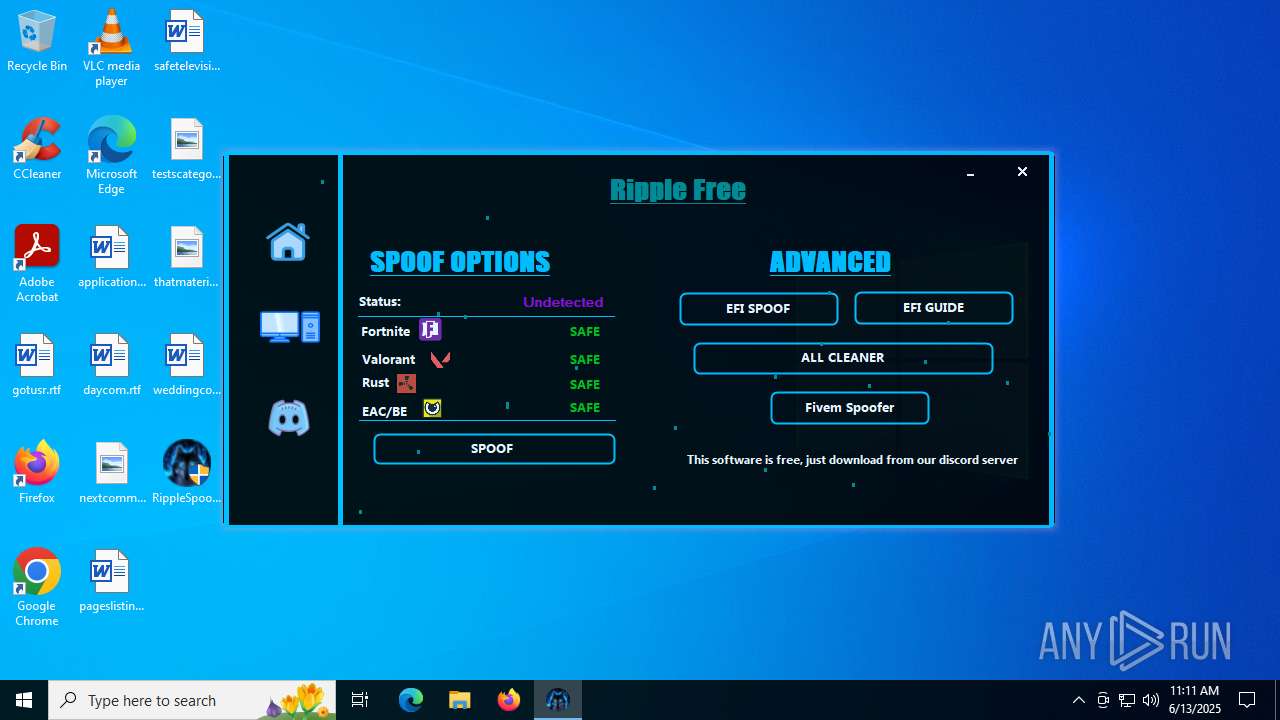
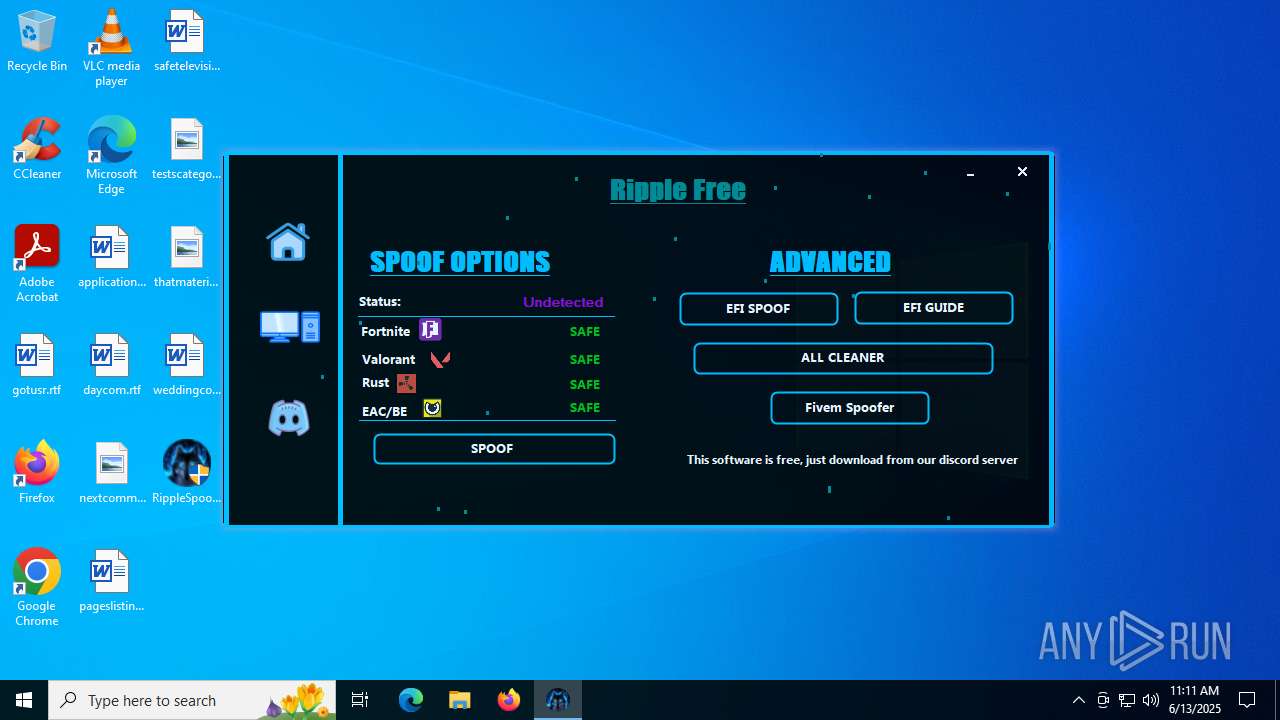
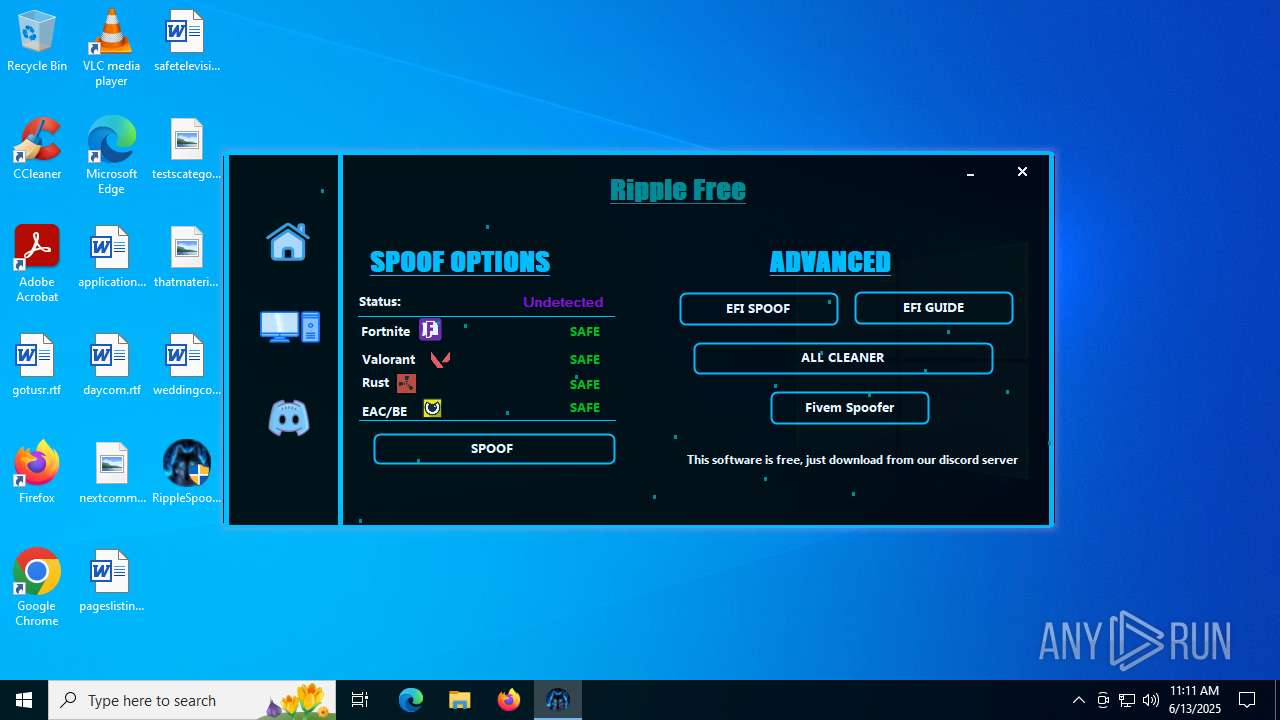
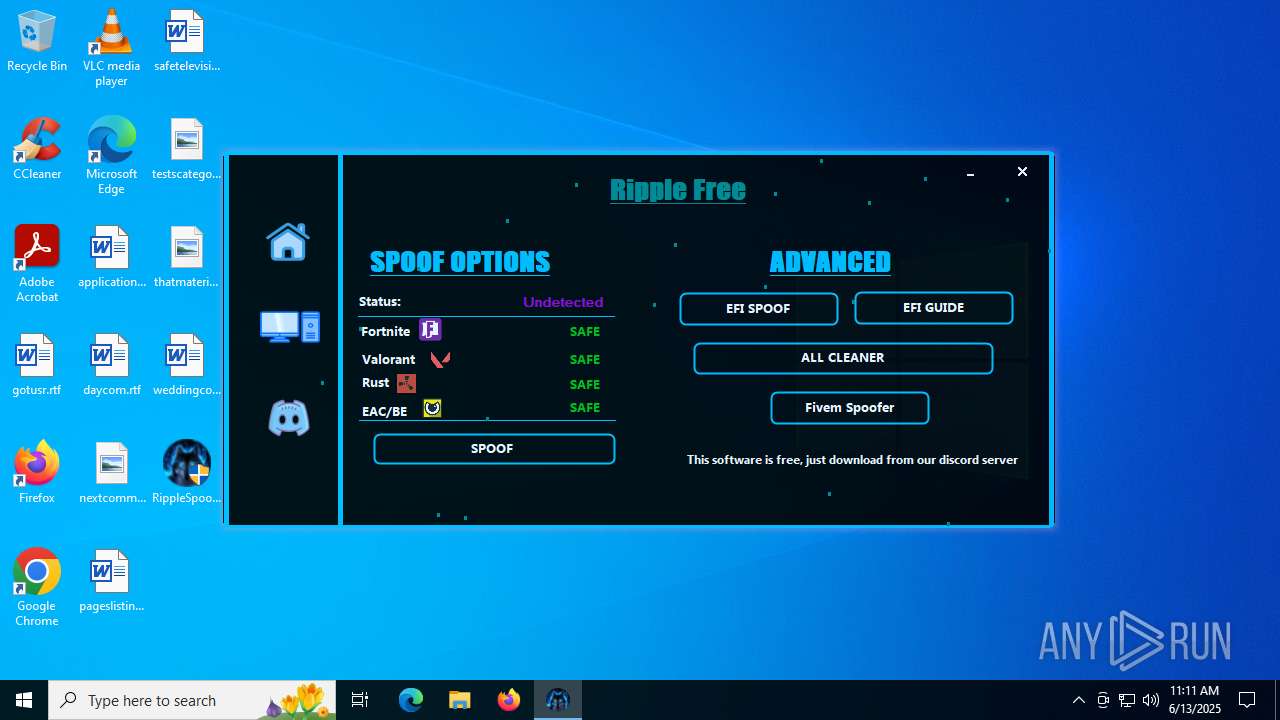
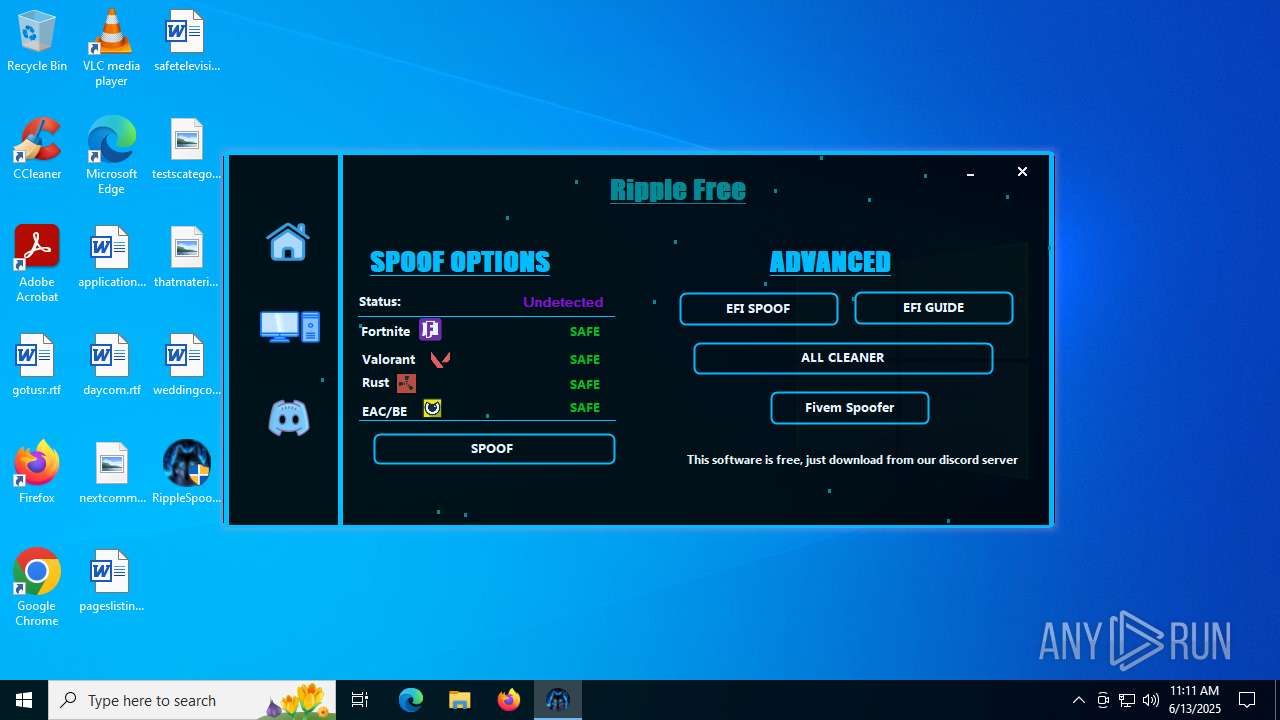
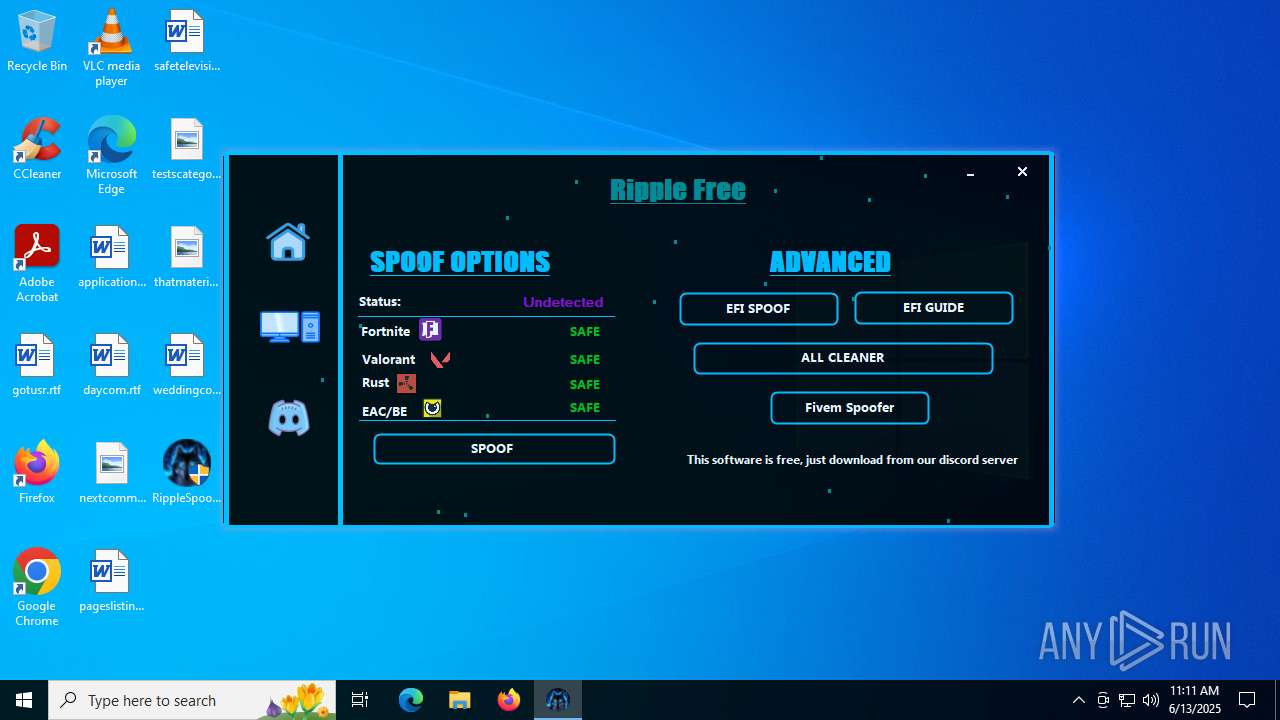
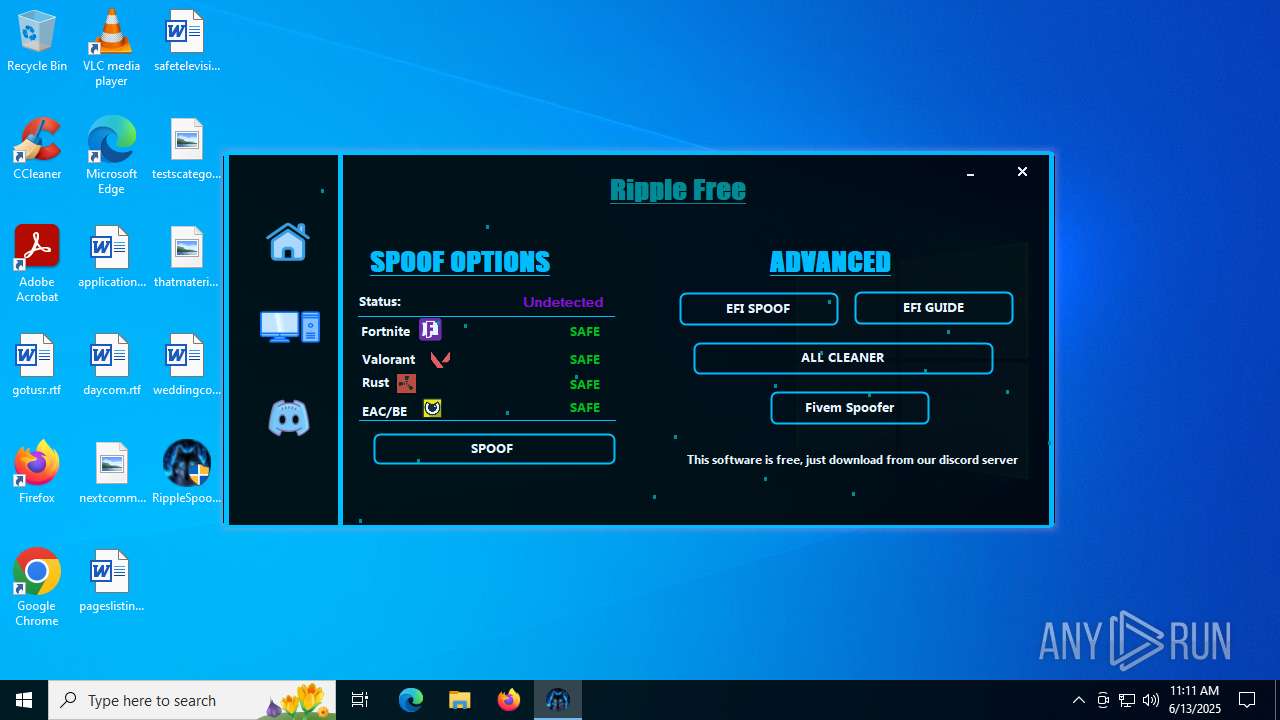
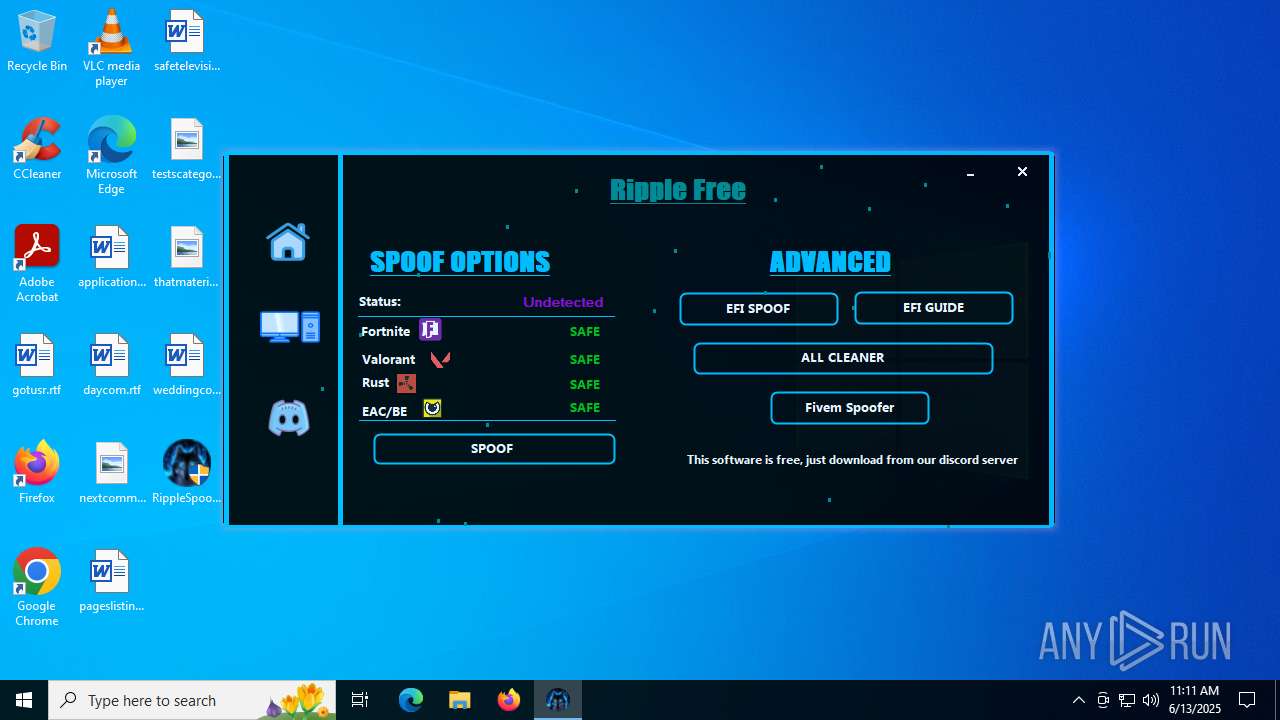
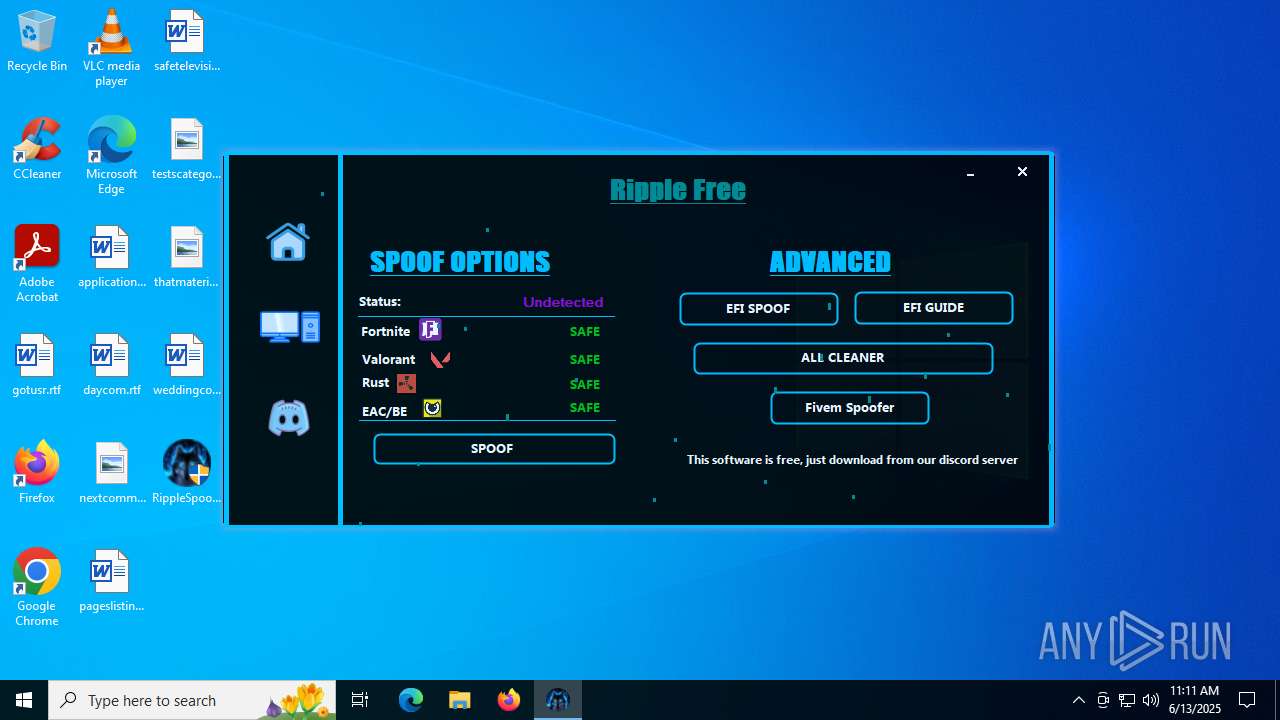
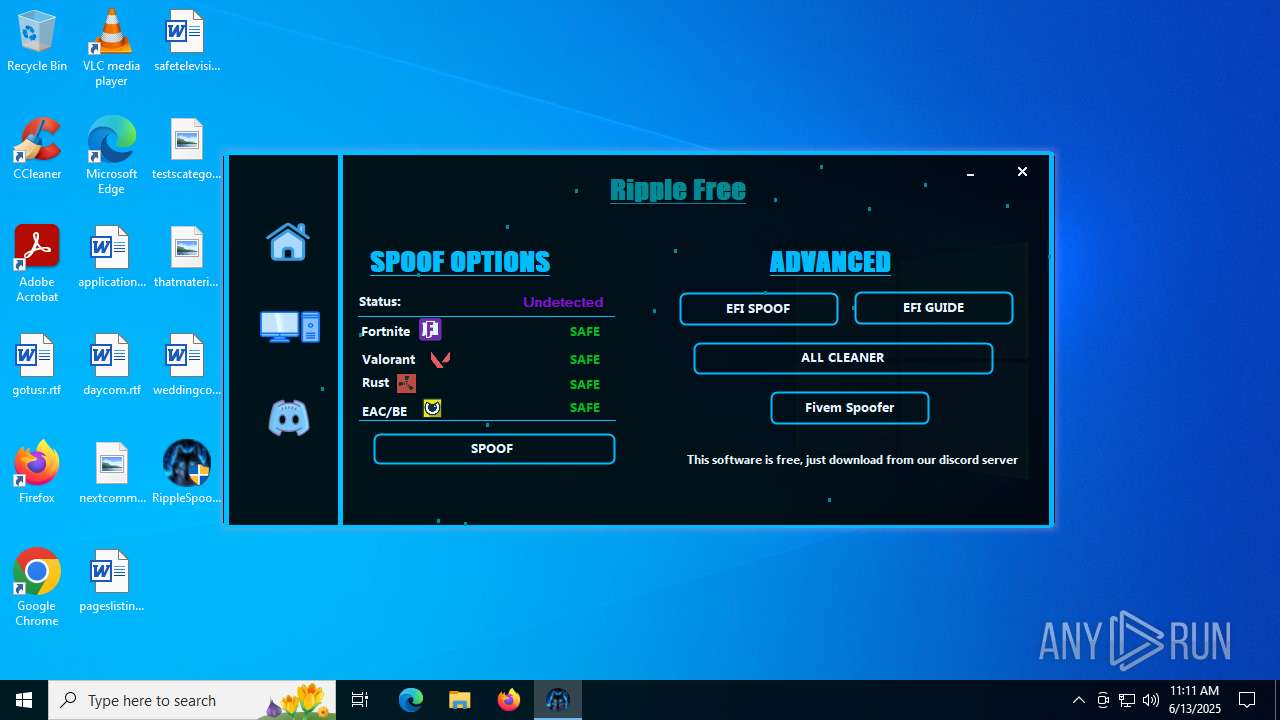
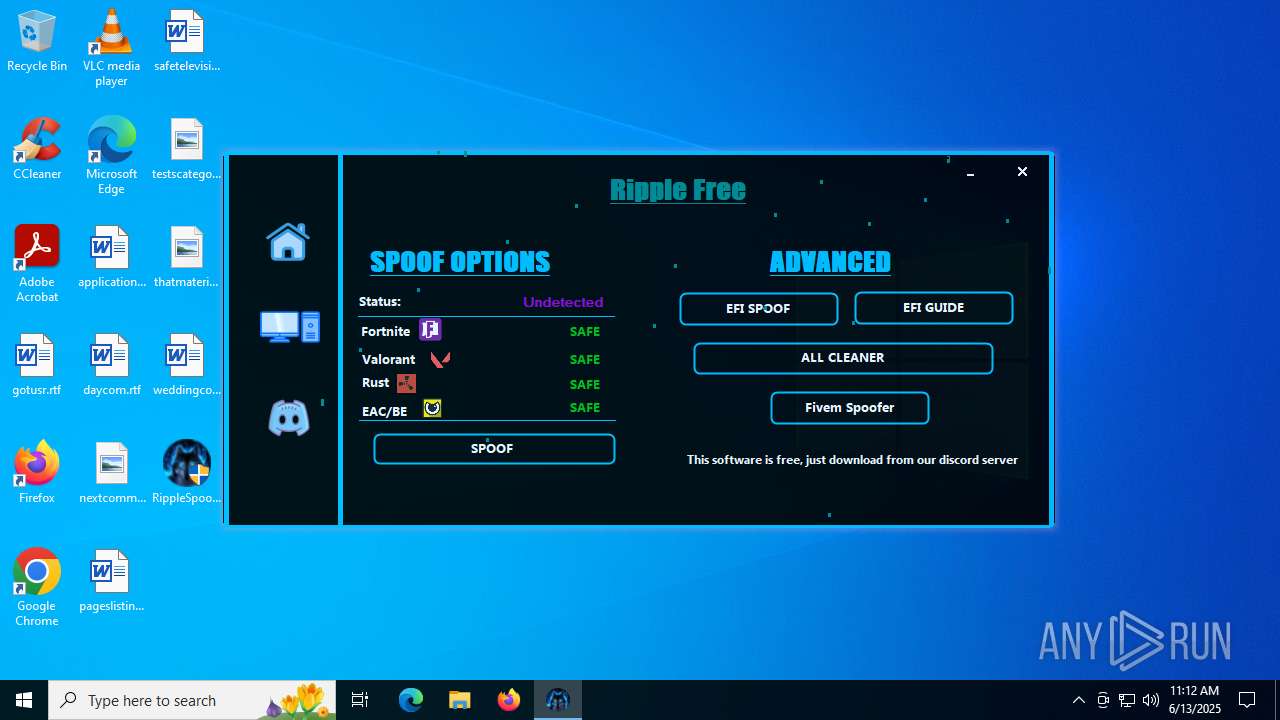
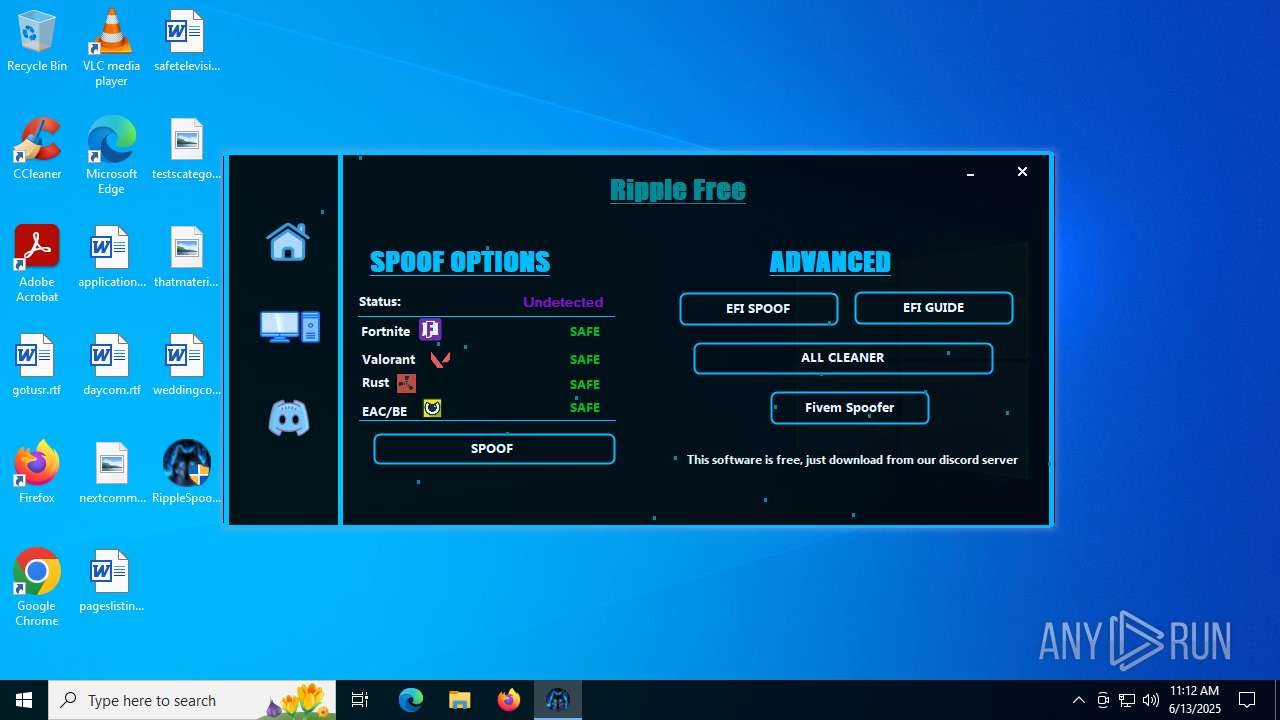
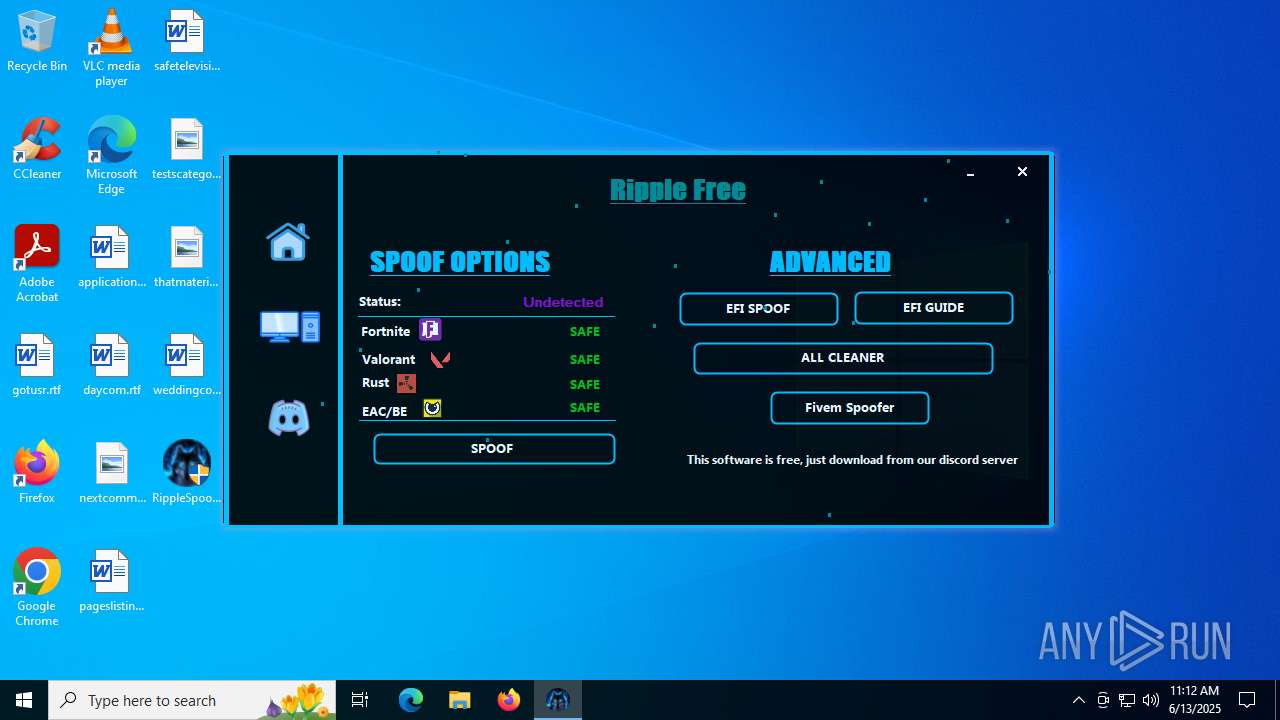
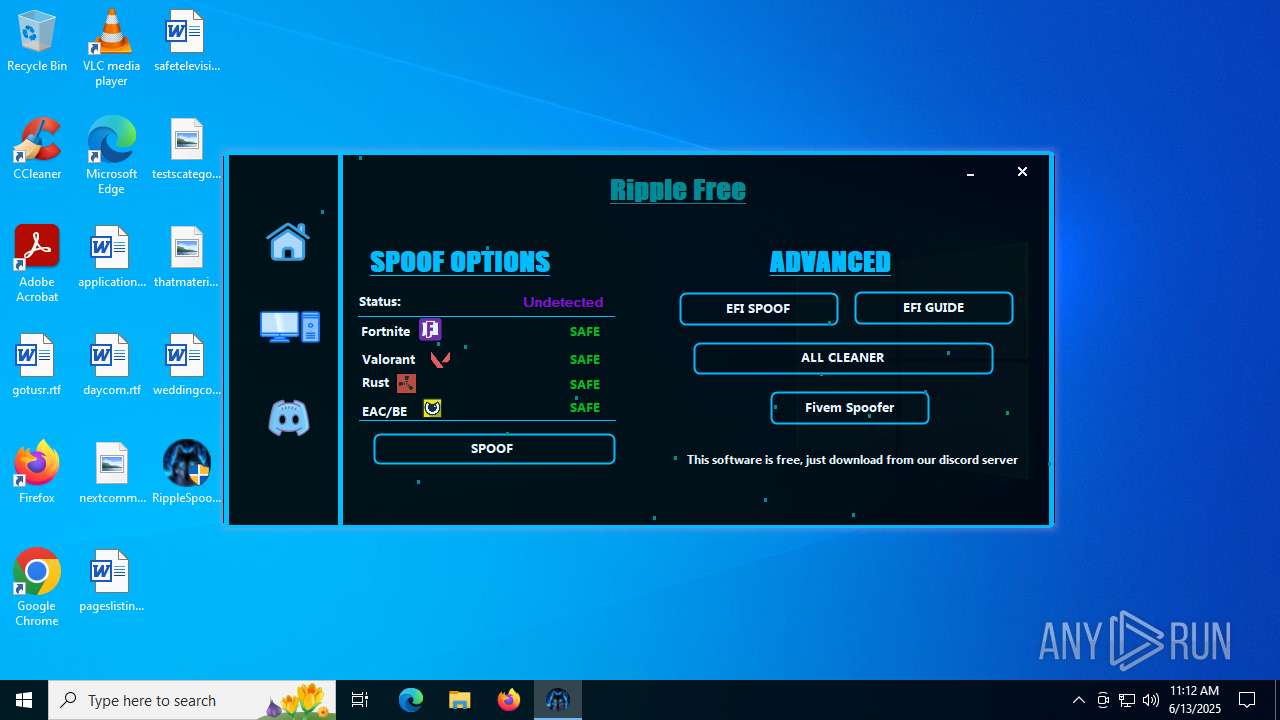
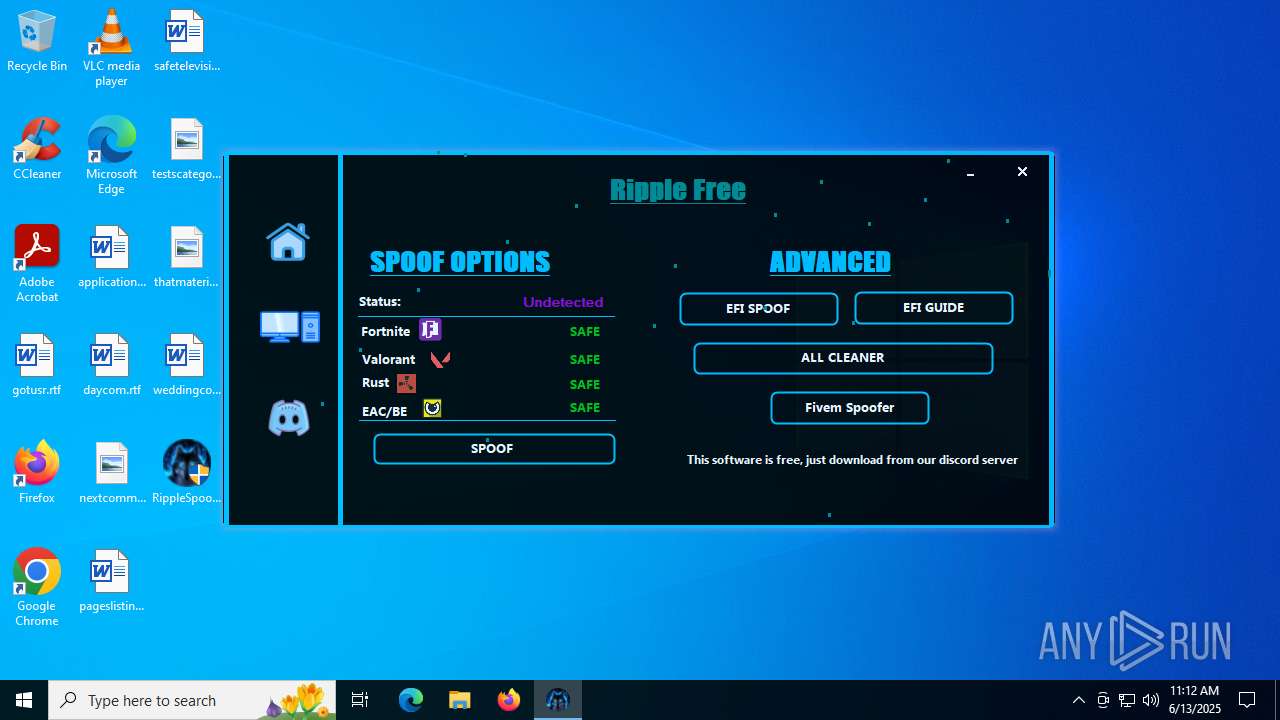
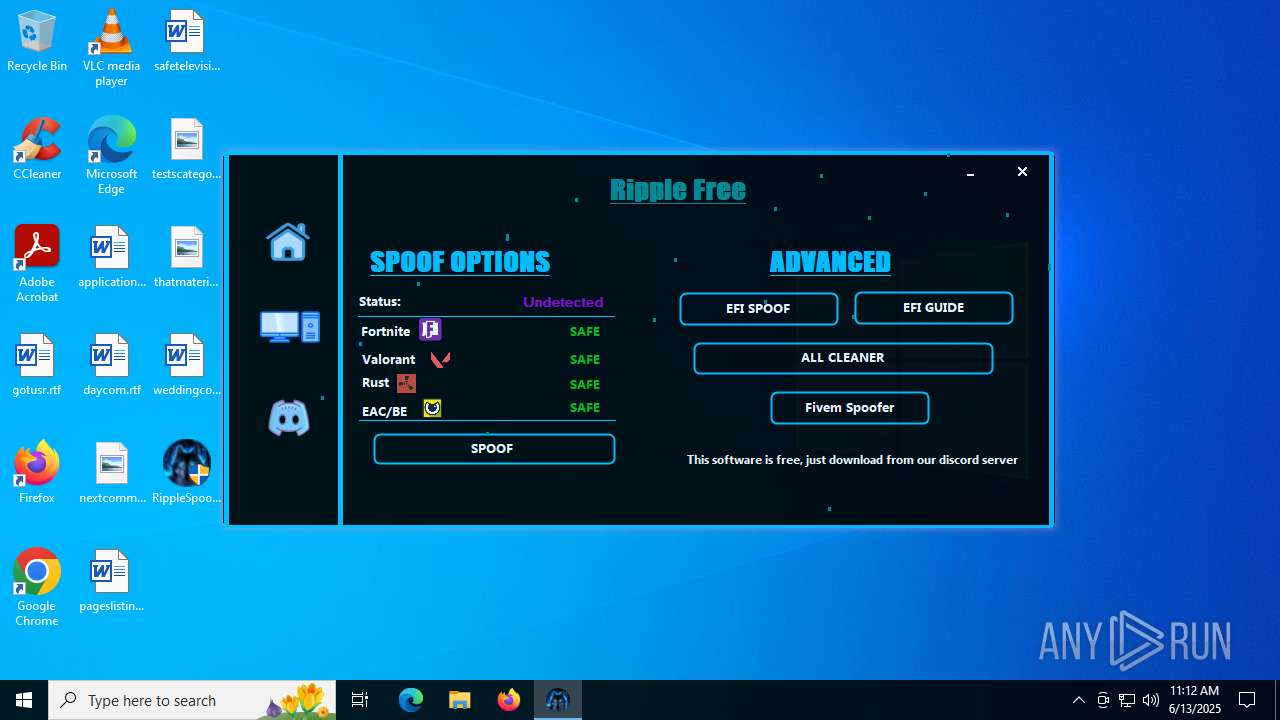
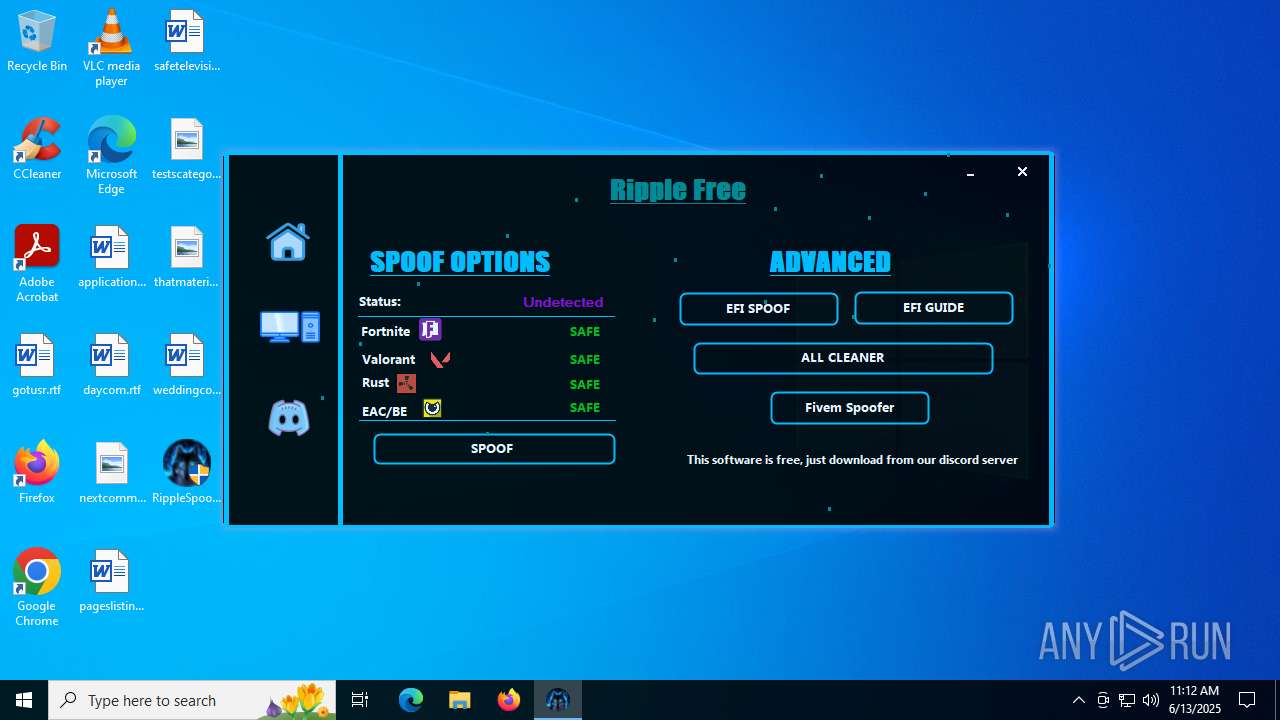
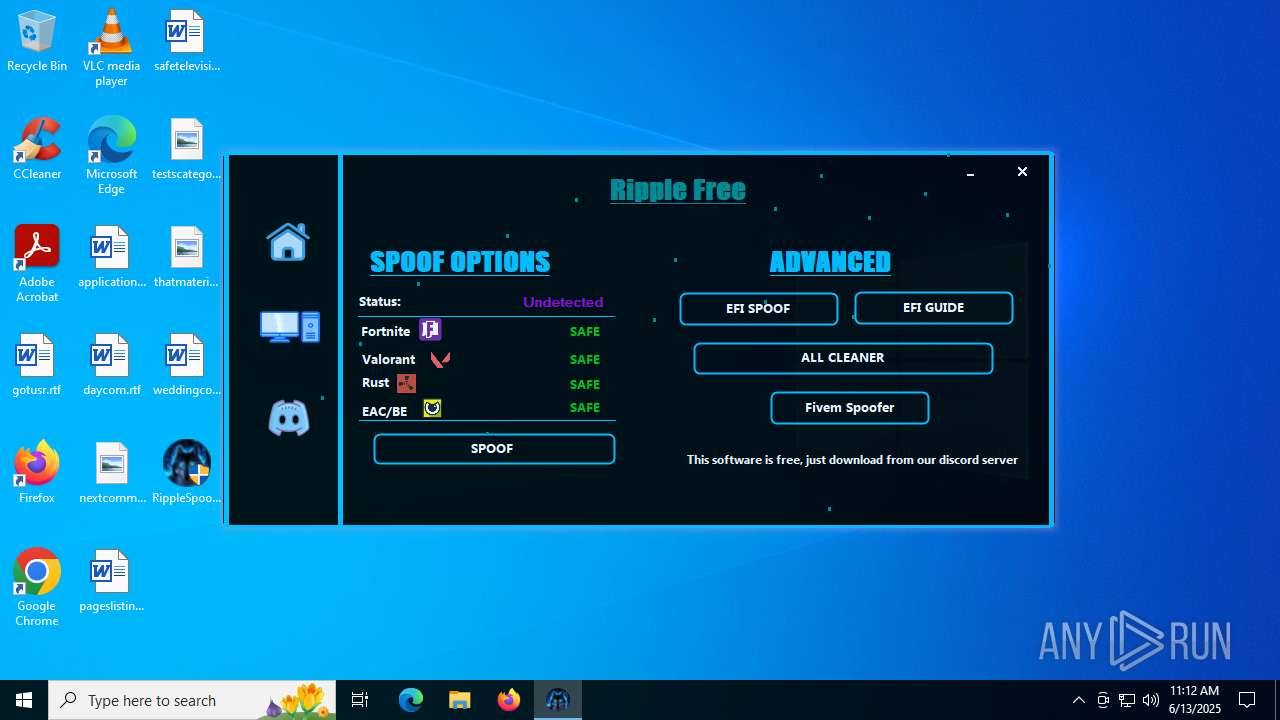
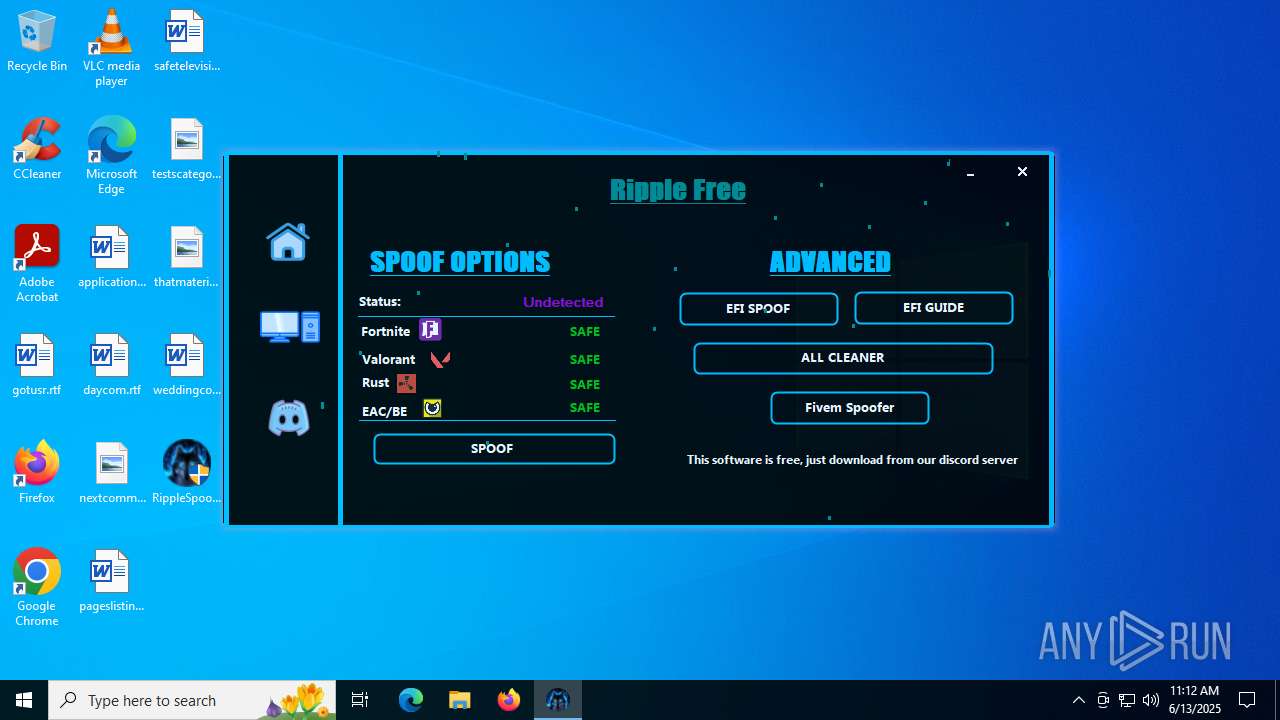
| File name: | RippleSpoofer.exe |
| Full analysis: | https://app.any.run/tasks/d988b19f-924e-405e-bfc0-6ffc17dcab97 |
| Verdict: | Malicious activity |
| Analysis date: | June 13, 2025, 11:10:21 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 6 sections |
| MD5: | 12861B2FA9C947F58DA9A0F27FF8C8FB |
| SHA1: | 898817A882D1574916842C4EEB3138804DF942FE |
| SHA256: | F30956927C8F595AC0988DAEEC027D05AD52880BAC2317EB57E1C335F8E8FEEB |
| SSDEEP: | 98304:iYIyd/lxzzu7EQcaXbh3eJ4w5BVqunigGjHA4PZtBgxPw4AAsTpQdETtzFHWS+ej:7715IatIlwO0Tdhti6JRA |
MALICIOUS
GENERIC has been found (auto)
- RippleSpoofer.exe (PID: 2780)
SUSPICIOUS
Reads the BIOS version
- RippleSpoofer.exe (PID: 2780)
INFO
Themida protector has been detected
- RippleSpoofer.exe (PID: 2780)
Process checks whether UAC notifications are on
- RippleSpoofer.exe (PID: 2780)
Reads the machine GUID from the registry
- RippleSpoofer.exe (PID: 2780)
Reads Environment values
- RippleSpoofer.exe (PID: 2780)
Reads the computer name
- RippleSpoofer.exe (PID: 2780)
Checks supported languages
- RippleSpoofer.exe (PID: 2780)
Disables trace logs
- RippleSpoofer.exe (PID: 2780)
Checks proxy server information
- RippleSpoofer.exe (PID: 2780)
- slui.exe (PID: 724)
Create files in a temporary directory
- RippleSpoofer.exe (PID: 2780)
Reads the software policy settings
- RippleSpoofer.exe (PID: 2780)
- slui.exe (PID: 724)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic Win/DOS Executable (50) |
|---|---|---|
| .exe | | | DOS Executable Generic (49.9) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:06:05 11:46:00+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 11 |
| CodeSize: | 6058496 |
| InitializedDataSize: | 9216 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xcdc058 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | Ripple Free Spoofer |
| CompanyName: | Ripple |
| FileDescription: | RippleFree |
| FileVersion: | 1.0.0.0 |
| InternalName: | RippleSpoofer.exe |
| LegalCopyright: | Ripple |
| LegalTrademarks: | Ripple |
| OriginalFileName: | RippleSpoofer.exe |
| ProductName: | Ripple |
| ProductVersion: | 1.0.0.0 |
| AssemblyVersion: | 1.0.0.0 |
Total processes
135
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 724 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2780 | "C:\Users\admin\Desktop\RippleSpoofer.exe" | C:\Users\admin\Desktop\RippleSpoofer.exe | explorer.exe | ||||||||||||
User: admin Company: Ripple Integrity Level: HIGH Description: RippleFree Version: 1.0.0.0 Modules
| |||||||||||||||
| 3756 | "C:\Users\admin\Desktop\RippleSpoofer.exe" | C:\Users\admin\Desktop\RippleSpoofer.exe | — | explorer.exe | |||||||||||
User: admin Company: Ripple Integrity Level: MEDIUM Description: RippleFree Exit code: 3221226540 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
8 541
Read events
8 527
Write events
14
Delete events
0
Modification events
| (PID) Process: | (2780) RippleSpoofer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\RippleSpoofer_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2780) RippleSpoofer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\RippleSpoofer_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (2780) RippleSpoofer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\RippleSpoofer_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (2780) RippleSpoofer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\RippleSpoofer_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (2780) RippleSpoofer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\RippleSpoofer_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (2780) RippleSpoofer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\RippleSpoofer_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (2780) RippleSpoofer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\RippleSpoofer_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (2780) RippleSpoofer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\RippleSpoofer_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2780) RippleSpoofer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\RippleSpoofer_RASMANCS |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (2780) RippleSpoofer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\RippleSpoofer_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
0
Suspicious files
0
Text files
1
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2780 | RippleSpoofer.exe | C:\Users\admin\AppData\Local\Temp\hardware_info.txt | text | |
MD5:1D3F7FF374369B5439EA392AB43DC37C | SHA256:DA6AD99C7D1DE69D785F6B46C9B8299DF5A230DFC6B668250BECB37597D37CD4 | |||
| 2780 | RippleSpoofer.exe | C:\Users\admin\AppData\Local\Temp\tmpB575.tmp.mp3 | mp3 | |
MD5:244CC3A6C2FABF8A05CF40C3BEA324E0 | SHA256:7C61C3EF11AD80C2941EAD551179F02D6CBD472AD53DC613708313F0E7B9171A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
24
DNS requests
12
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 162.125.72.15:443 | https://uc71d8b6074d1c980ded9b9ada30.dl.dropboxusercontent.com/cd/0/get/CrjR4d2rt-IVOlQKwlE-UYC8ivwrj0YGL1bapAipuDWUPr13hAYEV7E3UIEe7b_QDNSgGf9EIora9dtTFskNs-hV2efXFzEqSnM12TEqiVAFoPI34n5tLjux6WBXu-QqQw5zrKO87WaHJa3uWHW6TEKd/file?dl=1 | unknown | binary | 26 b | whitelisted |
— | — | GET | 302 | 162.125.72.18:443 | https://www.dropbox.com/scl/fi/j1bdx8xt5sn0aev5u78pp/version.json?rlkey=eorwhrvdwhq8zb2b0lp4tztnk&st=6pj7js9s&dl=1 | unknown | text | 17 b | whitelisted |
1268 | svchost.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
5476 | RUXIMICS.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5476 | RUXIMICS.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
5476 | RUXIMICS.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
1268 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5476 | RUXIMICS.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 2.23.181.156:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 2.23.181.156:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
www.dropbox.com |
| whitelisted |
uc71d8b6074d1c980ded9b9ada30.dl.dropboxusercontent.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |