| File name: | keyexp4.exe |
| Full analysis: | https://app.any.run/tasks/ebdf6a20-4126-46c7-8c30-831d318e3fd9 |
| Verdict: | Malicious activity |
| Analysis date: | January 18, 2019, 05:50:40 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | F98D52684DC19A44C41430C816721F51 |
| SHA1: | F78C8EC20045A7669212144367ECBBCD61D7BB18 |
| SHA256: | F2FEFC21ED3117BB7A836A42872241832E2B86F7CCA8176C5EDA7F5C5F21C27C |
| SSDEEP: | 196608:pNw4ppnqXTQs6yweP3xsSQ31W+bW3Gg1rKDDg3sSCLnLvvAfTFiyoamgBAE4V4B1:pK4ppv/ePx5Cf81rS3wSTAAERCw |
MALICIOUS
Application was dropped or rewritten from another process
- GLB8C33.tmp (PID: 2688)
- REGKEY~1.EXE (PID: 3864)
- SetACL.exe (PID: 1912)
- QkStart.exe (PID: 2632)
- SCHEDU~1.EXE (PID: 3748)
Loads dropped or rewritten executable
- GLB8C33.tmp (PID: 2688)
Writes to a start menu file
- GLB8C33.tmp (PID: 2688)
Loads the Task Scheduler COM API
- SCHEDU~1.EXE (PID: 3748)
SUSPICIOUS
Starts application with an unusual extension
- keyexp4.exe (PID: 2220)
Executable content was dropped or overwritten
- keyexp4.exe (PID: 2220)
- GLB8C33.tmp (PID: 2688)
Searches for installed software
- GLB8C33.tmp (PID: 2688)
- DllHost.exe (PID: 2748)
Creates files in the program directory
- GLB8C33.tmp (PID: 2688)
- REGKEY~1.EXE (PID: 3864)
Creates a software uninstall entry
- GLB8C33.tmp (PID: 2688)
Uses ICACLS.EXE to modify access control list
- SetACL.exe (PID: 1912)
Modifies the open verb of a shell class
- GLB8C33.tmp (PID: 2688)
INFO
Low-level read access rights to disk partition
- vssvc.exe (PID: 3596)
Dropped object may contain Bitcoin addresses
- GLB8C33.tmp (PID: 2688)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2007:08:16 20:13:16+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 7.1 |
| CodeSize: | 1024 |
| InitializedDataSize: | 16031744 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1000 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 4.4.1.1 |
| ProductVersionNumber: | 1032.4455.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows 16-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | Insight Software Solutions, Inc. |
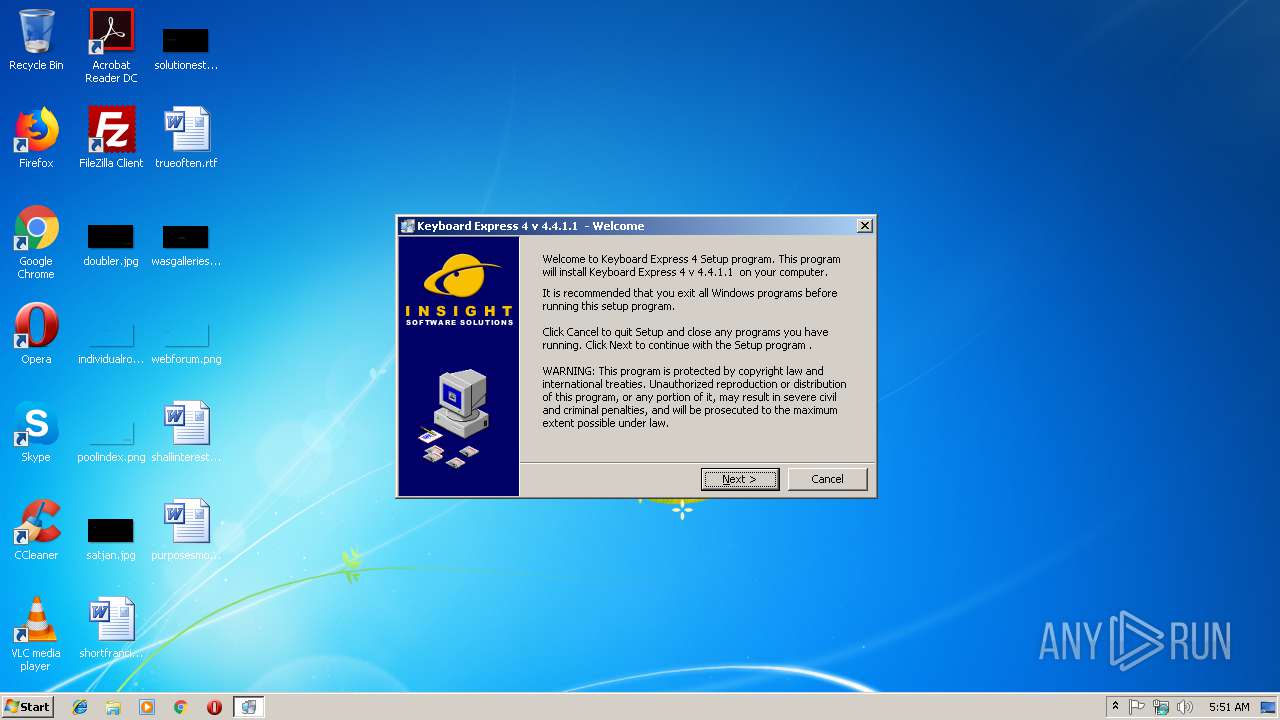
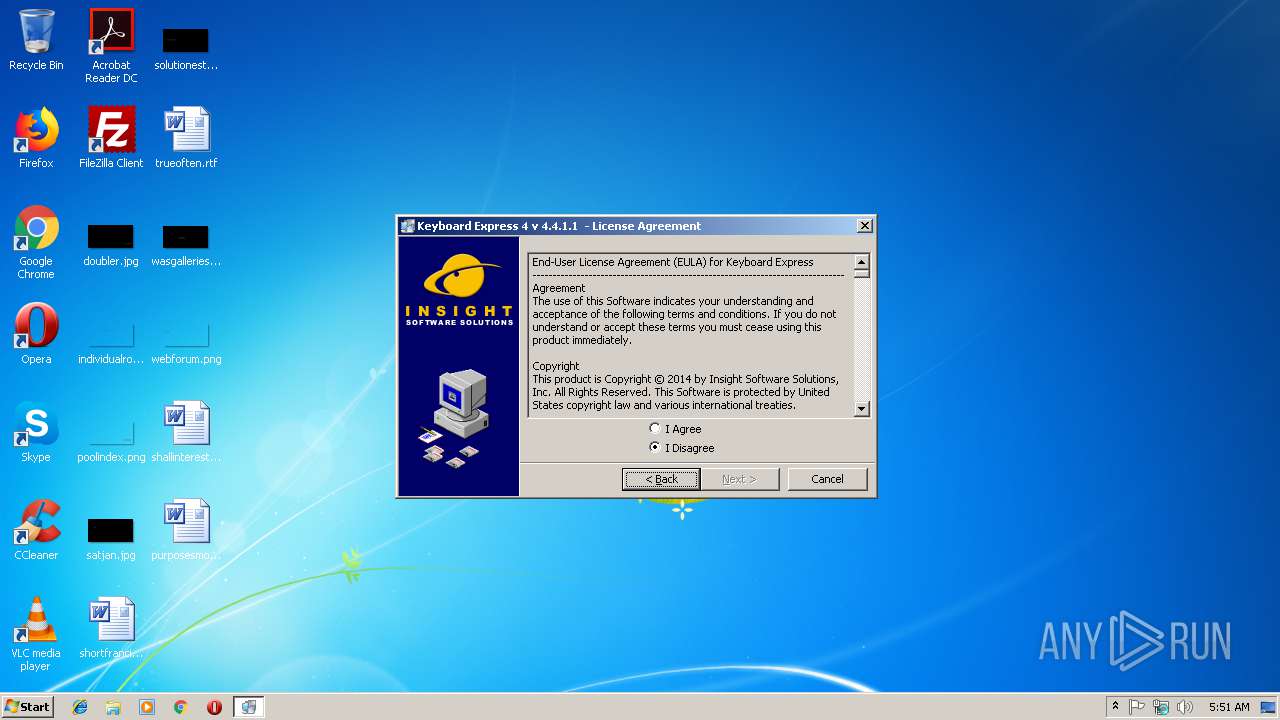
| FileDescription: | Keyboard Express 4 |
| FileVersion: | 4.4.1.1 |
| LegalCopyright: | (c) 2014 Insight Software Solutions, Inc |
Total processes
55
Monitored processes
16
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 672 | "C:\Windows\System32\notepad.exe" C:\Program Files\Keyboard Express 4\whatsnew.txt | C:\Windows\System32\notepad.exe | — | GLB8C33.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1912 | "C:\Users\admin\AppData\Local\Temp\SetACL.exe" | C:\Users\admin\AppData\Local\Temp\SetACL.exe | — | GLB8C33.tmp | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2220 | "C:\Users\admin\AppData\Local\Temp\keyexp4.exe" | C:\Users\admin\AppData\Local\Temp\keyexp4.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2608 | "C:\Windows\System32\icacls.exe" "C:\ProgramData\Insight Software Solutions" /grant BUILTIN\Users:(OI)(CI)F /T /C | C:\Windows\System32\icacls.exe | — | SetACL.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2632 | "C:\PROGRA~1\COMMON~1\INSIGH~1\QkStart.exe" /FC:\Program Files\Keyboard Express 4\KEQuickStart.doc /NKeyboard Express 4 | C:\PROGRA~1\COMMON~1\INSIGH~1\QkStart.exe | — | GLB8C33.tmp | |||||||||||
User: admin Company: Insight Software Solutions Integrity Level: HIGH Description: View Quick Start Information Exit code: 0 Version: 1.10.7.1 Modules
| |||||||||||||||
| 2688 | C:\Users\admin\AppData\Local\Temp\GLB8C33.tmp 6144 C:\Users\admin\AppData\Local\Temp\keyexp4.exe | C:\Users\admin\AppData\Local\Temp\GLB8C33.tmp | keyexp4.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2728 | DrvInst.exe "1" "200" "STORAGE\VolumeSnapshot\HarddiskVolumeSnapshot18" "" "" "6792c44eb" "00000000" "00000550" "00000330" | C:\Windows\system32\DrvInst.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2748 | C:\Windows\system32\DllHost.exe /Processid:{F32D97DF-E3E5-4CB9-9E3E-0EB5B4E49801} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3252 | "C:\Windows\System32\icacls.exe" "C:\ProgramData\Insight Software" /grant BUILTIN\Users:(OI)(CI)F /T /C | C:\Windows\System32\icacls.exe | — | SetACL.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3596 | "C:\Users\admin\AppData\Local\Temp\keyexp4.exe" | C:\Users\admin\AppData\Local\Temp\keyexp4.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 | |||||||||||||||
Total events
812
Read events
601
Write events
211
Delete events
0
Modification events
| (PID) Process: | (2688) GLB8C33.tmp | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4000000000000000166079D0F1AED401800A0000840A0000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2688) GLB8C33.tmp | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 4000000000000000166079D0F1AED401800A0000840A0000D0070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2688) GLB8C33.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 20 | |||
| (PID) Process: | (2688) GLB8C33.tmp | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 4000000000000000B8BCF7D0F1AED401800A0000840A0000D3070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2688) GLB8C33.tmp | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4000000000000000121FFAD0F1AED401800A0000400C0000E8030000010000000000000000000000F6B29588FA8AC94DAC9C21706C8FC9710000000000000000 | |||
| (PID) Process: | (2688) GLB8C33.tmp | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Leave) |
Value: 40000000000000003C940FD1F1AED401800A0000400C0000E8030000000000000000000000000000F6B29588FA8AC94DAC9C21706C8FC9710000000000000000 | |||
| (PID) Process: | (2688) GLB8C33.tmp | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Leave) |
Value: 400000000000000096F611D1F1AED401800A0000840A0000D3070000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2688) GLB8C33.tmp | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Leave) |
Value: 400000000000000096F611D1F1AED401800A0000840A0000D007000001000000000000000A010081F6B29588FA8AC94DAC9C21706C8FC9710000000000000000 | |||
| (PID) Process: | (2688) GLB8C33.tmp | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Leave) |
Value: 400000000000000096F611D1F1AED401800A0000840A0000D507000001000000000000000A010081000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2688) GLB8C33.tmp | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 400000000000000096F611D1F1AED401800A0000840A0000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
22
Suspicious files
4
Text files
67
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2748 | DllHost.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 2688 | GLB8C33.tmp | C:\Users\admin\AppData\Local\Temp\~GLH0000.TMP | — | |
MD5:— | SHA256:— | |||
| 2688 | GLB8C33.tmp | C:\Users\admin\AppData\Local\Temp\~GLH0001.TMP | — | |
MD5:— | SHA256:— | |||
| 3596 | vssvc.exe | C: | — | |
MD5:— | SHA256:— | |||
| 2688 | GLB8C33.tmp | C:\Program Files\Keyboard Express 4\~GLH0002.TMP | — | |
MD5:— | SHA256:— | |||
| 2688 | GLB8C33.tmp | C:\Program Files\Keyboard Express 4\~GLH0003.TMP | — | |
MD5:— | SHA256:— | |||
| 2688 | GLB8C33.tmp | C:\Program Files\Keyboard Express 4\~GLH0004.TMP | — | |
MD5:— | SHA256:— | |||
| 2688 | GLB8C33.tmp | C:\Program Files\Keyboard Express 4\~GLH0005.TMP | — | |
MD5:— | SHA256:— | |||
| 2688 | GLB8C33.tmp | C:\Program Files\Keyboard Express 4\~GLH0006.TMP | — | |
MD5:— | SHA256:— | |||
| 2688 | GLB8C33.tmp | C:\Program Files\Keyboard Express 4\~GLH0007.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report