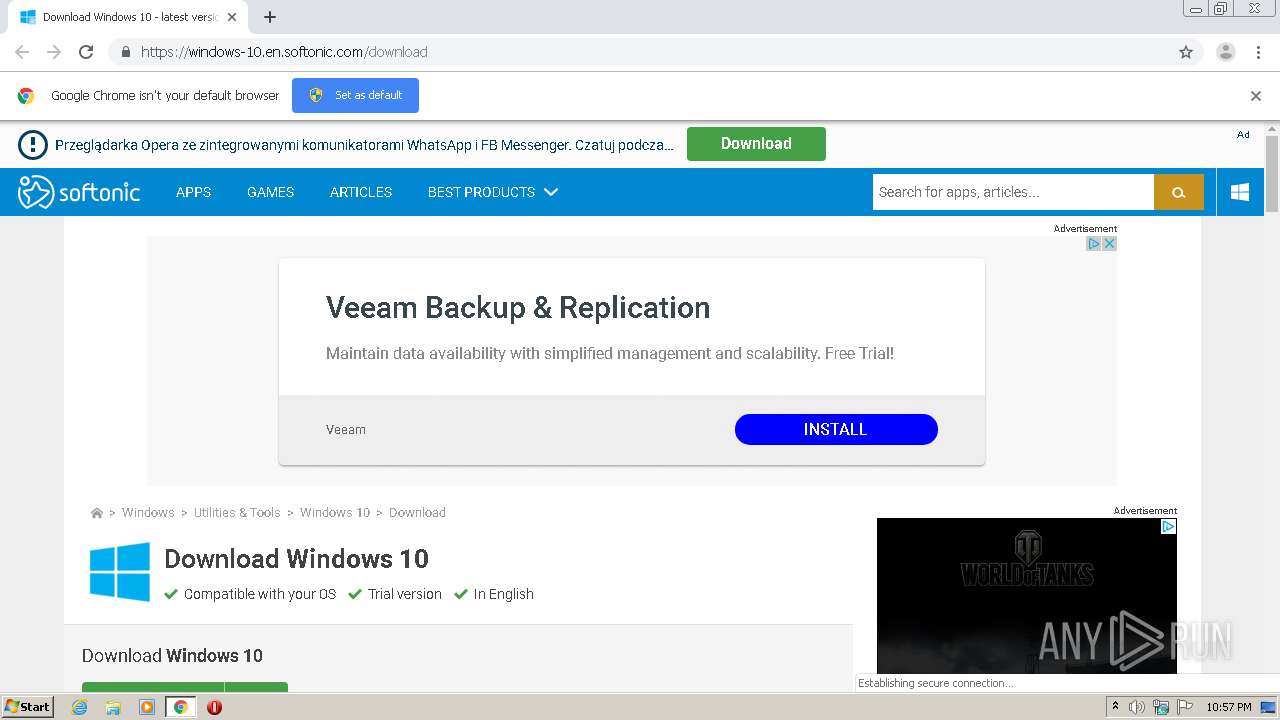
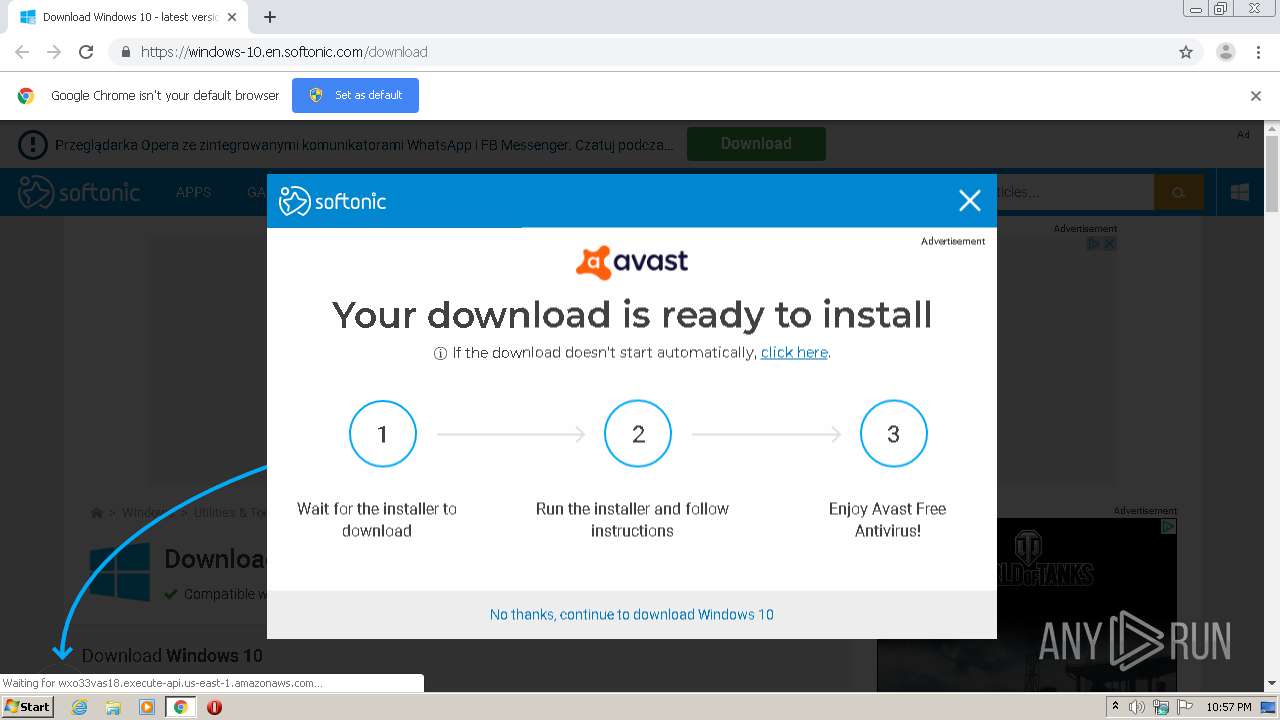
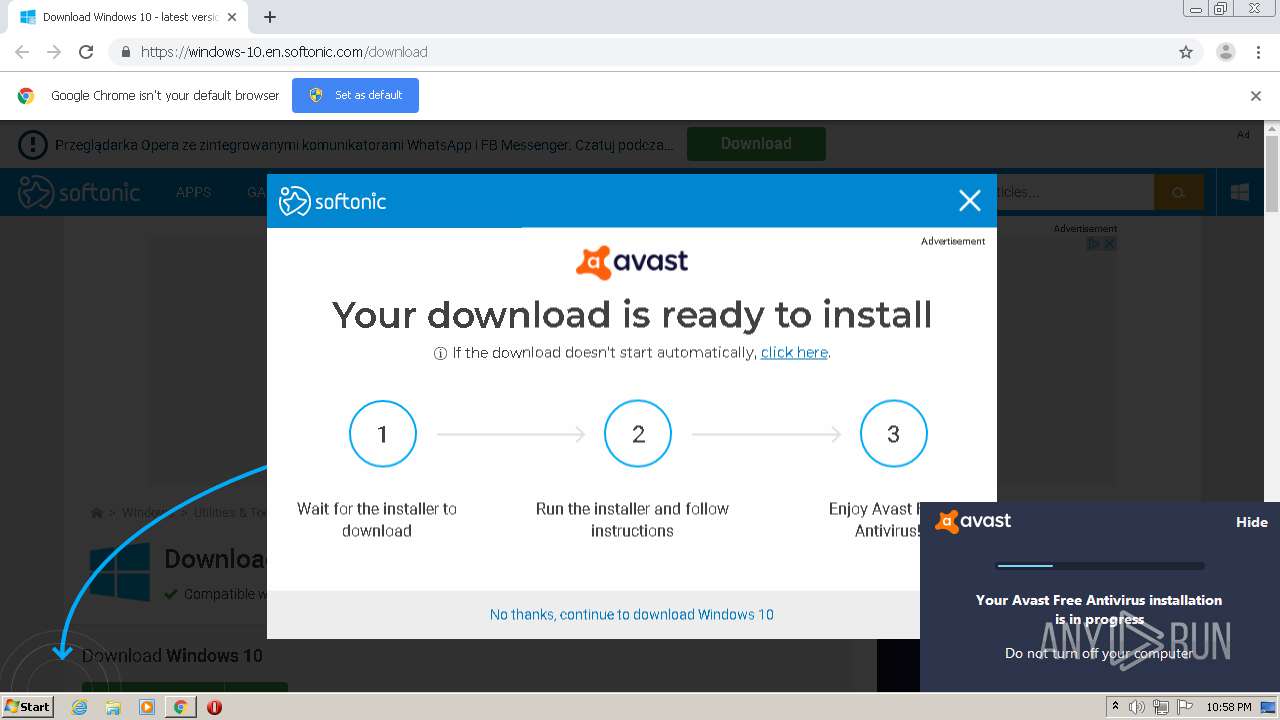
| URL: | https://windows-10.en.softonic.com/download |
| Full analysis: | https://app.any.run/tasks/d500629d-bc13-496d-9a55-91209df3f440 |
| Verdict: | Malicious activity |
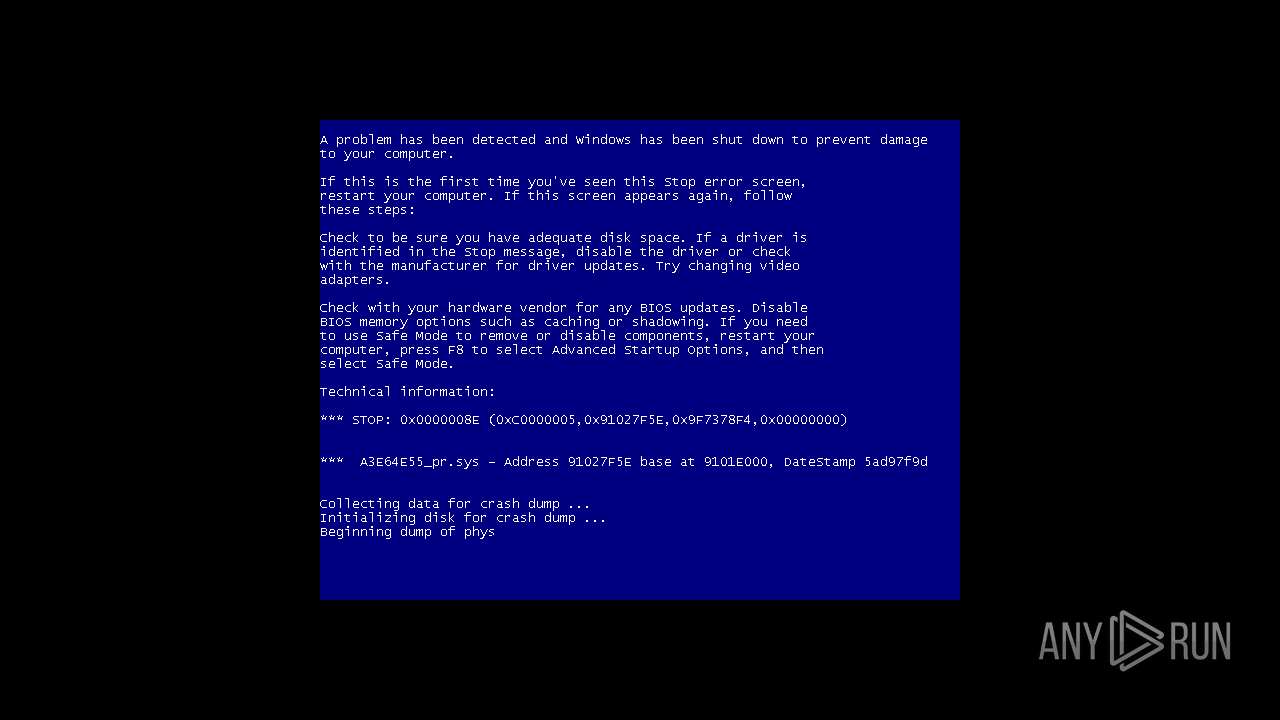
| Threats: | A loader is malicious software that infiltrates devices to deliver malicious payloads. This malware is capable of infecting victims’ computers, analyzing their system information, and installing other types of threats, such as trojans or stealers. Criminals usually deliver loaders through phishing emails and links by relying on social engineering to trick users into downloading and running their executables. Loaders employ advanced evasion and persistence tactics to avoid detection. |
| Analysis date: | September 19, 2020, 21:57:25 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 29A6BD14D9317BBE076DF3936ECD8631 |
| SHA1: | 94EF537A9F9906DFF29859FA4DF8B5095BABCEBA |
| SHA256: | F2F80EA88425E4AD972FEB430D64C5A66CD243A9940C78AABD354E55D1C04D5F |
| SSDEEP: | 3:N8dCEgHLGKMM:2lILGKMM |
MALICIOUS
Application was dropped or rewritten from another process
- avast_free_antivirus_setup_online.exe (PID: 1088)
- avast_free_antivirus_setup_online.exe (PID: 3020)
- instup.exe (PID: 1856)
- avast_free_antivirus_setup_online.exe (PID: 376)
- instup.exe (PID: 1664)
- sbr.exe (PID: 5600)
- AvEmUpdate.exe (PID: 2716)
- SetupInf.exe (PID: 5588)
- AvEmUpdate.exe (PID: 4492)
- AvEmUpdate.exe (PID: 5776)
- AvEmUpdate.exe (PID: 2732)
- CCUpdate.exe (PID: 4244)
- SetupInf.exe (PID: 4852)
- SetupInf.exe (PID: 5056)
- SetupInf.exe (PID: 5776)
- CCUpdate.exe (PID: 5188)
- CCUpdate.exe (PID: 5100)
- CCUpdate.exe (PID: 2652)
- avBugReport.exe (PID: 280)
- avBugReport.exe (PID: 2592)
- SetupInf.exe (PID: 4916)
- SetupInf.exe (PID: 6028)
- RegSvr.exe (PID: 4648)
- RegSvr.exe (PID: 4996)
- overseer.exe (PID: 3076)
- AvastNM.exe (PID: 4212)
- wsc_proxy.exe (PID: 6052)
- AvastSvc.exe (PID: 4588)
- aswEngSrv.exe (PID: 5044)
- CCUpdate.exe (PID: 5868)
- instup.exe (PID: 1532)
- wsc_proxy.exe (PID: 5096)
Changes settings of System certificates
- avast_free_antivirus_setup_online.exe (PID: 376)
- AvEmUpdate.exe (PID: 2716)
- SetupInf.exe (PID: 6028)
- AvastSvc.exe (PID: 4588)
Loads dropped or rewritten executable
- instup.exe (PID: 1664)
- instup.exe (PID: 1856)
- AvEmUpdate.exe (PID: 5776)
- CCUpdate.exe (PID: 5188)
- engsup.exe (PID: 5356)
- AvastSvc.exe (PID: 4588)
- engsup.exe (PID: 4764)
- aswEngSrv.exe (PID: 5044)
- chrome.exe (PID: 5724)
- chrome.exe (PID: 3124)
Changes the autorun value in the registry
- instup.exe (PID: 1856)
Loads the Task Scheduler COM API
- AvEmUpdate.exe (PID: 4492)
- AvEmUpdate.exe (PID: 2716)
- CCUpdate.exe (PID: 2652)
- CCUpdate.exe (PID: 5868)
- overseer.exe (PID: 3076)
Actions looks like stealing of personal data
- engsup.exe (PID: 4764)
SUSPICIOUS
Executable content was dropped or overwritten
- chrome.exe (PID: 2212)
- chrome.exe (PID: 540)
- avast_free_antivirus_setup_online.exe (PID: 1088)
- avast_free_antivirus_setup_online.exe (PID: 376)
- instup.exe (PID: 1664)
- instup.exe (PID: 1856)
- AvEmUpdate.exe (PID: 2716)
- AvEmUpdate.exe (PID: 5776)
- CCUpdate.exe (PID: 4244)
- CCUpdate.exe (PID: 2652)
- CCUpdate.exe (PID: 5100)
- SetupInf.exe (PID: 6028)
- DrvInst.exe (PID: 4164)
- engsup.exe (PID: 5356)
- overseer.exe (PID: 3076)
- AvastSvc.exe (PID: 4588)
Creates files in the Windows directory
- avast_free_antivirus_setup_online.exe (PID: 1088)
- avast_free_antivirus_setup_online.exe (PID: 376)
- instup.exe (PID: 1664)
- instup.exe (PID: 1856)
- AvEmUpdate.exe (PID: 2716)
- DrvInst.exe (PID: 4164)
- SetupInf.exe (PID: 6028)
- AvastSvc.exe (PID: 4588)
Low-level read access rights to disk partition
- avast_free_antivirus_setup_online.exe (PID: 1088)
- avast_free_antivirus_setup_online.exe (PID: 376)
- instup.exe (PID: 1664)
- instup.exe (PID: 1856)
- SetupInf.exe (PID: 5588)
- SetupInf.exe (PID: 5056)
- SetupInf.exe (PID: 4852)
- SetupInf.exe (PID: 5776)
- AvEmUpdate.exe (PID: 2716)
- AvEmUpdate.exe (PID: 2732)
- AvEmUpdate.exe (PID: 5776)
- CCUpdate.exe (PID: 4244)
- CCUpdate.exe (PID: 5100)
- CCUpdate.exe (PID: 2652)
- CCUpdate.exe (PID: 5188)
- CCUpdate.exe (PID: 5868)
- SetupInf.exe (PID: 4916)
- avBugReport.exe (PID: 2592)
- SetupInf.exe (PID: 6028)
- avBugReport.exe (PID: 280)
- RegSvr.exe (PID: 4648)
- RegSvr.exe (PID: 4996)
- overseer.exe (PID: 3076)
- wsc_proxy.exe (PID: 6052)
- AvastSvc.exe (PID: 4588)
- wsc_proxy.exe (PID: 5096)
Modifies files in Chrome extension folder
- chrome.exe (PID: 540)
Creates files in the program directory
- avast_free_antivirus_setup_online.exe (PID: 376)
- instup.exe (PID: 1664)
- instup.exe (PID: 1856)
- AvEmUpdate.exe (PID: 4492)
- AvEmUpdate.exe (PID: 2716)
- CCUpdate.exe (PID: 4244)
- CCUpdate.exe (PID: 2652)
- CCUpdate.exe (PID: 5100)
- CCUpdate.exe (PID: 5868)
- avBugReport.exe (PID: 280)
- avBugReport.exe (PID: 2592)
- engsup.exe (PID: 5356)
- AvastNM.exe (PID: 4212)
- wsc_proxy.exe (PID: 6052)
- AvastSvc.exe (PID: 4588)
- engsup.exe (PID: 4764)
- overseer.exe (PID: 3076)
- instup.exe (PID: 1532)
Adds / modifies Windows certificates
- avast_free_antivirus_setup_online.exe (PID: 376)
- AvEmUpdate.exe (PID: 2716)
Creates or modifies windows services
- instup.exe (PID: 1664)
- instup.exe (PID: 1856)
- AvastSvc.exe (PID: 4588)
Removes files from Windows directory
- instup.exe (PID: 1664)
- instup.exe (PID: 1856)
- AvEmUpdate.exe (PID: 2716)
- DrvInst.exe (PID: 4164)
- SetupInf.exe (PID: 6028)
- avast_free_antivirus_setup_online.exe (PID: 376)
Starts itself from another location
- instup.exe (PID: 1664)
- CCUpdate.exe (PID: 5100)
Modifies the open verb of a shell class
- instup.exe (PID: 1856)
Creates COM task schedule object
- instup.exe (PID: 1856)
- RegSvr.exe (PID: 4648)
- RegSvr.exe (PID: 4996)
Creates a software uninstall entry
- instup.exe (PID: 1856)
- AvEmUpdate.exe (PID: 5776)
Application launched itself
- AvEmUpdate.exe (PID: 2716)
- CCUpdate.exe (PID: 2652)
Creates files in the driver directory
- instup.exe (PID: 1856)
- AvEmUpdate.exe (PID: 2716)
- DrvInst.exe (PID: 4164)
- SetupInf.exe (PID: 6028)
Checks for external IP
- CCUpdate.exe (PID: 5100)
- CCUpdate.exe (PID: 2652)
- CCUpdate.exe (PID: 5188)
- CCUpdate.exe (PID: 5868)
- CCUpdate.exe (PID: 4244)
Executed via COM
- DrvInst.exe (PID: 4164)
Executed as Windows Service
- AvastSvc.exe (PID: 4588)
Reads the cookies of Google Chrome
- engsup.exe (PID: 4764)
Reads the cookies of Mozilla Firefox
- engsup.exe (PID: 4764)
INFO
Application launched itself
- chrome.exe (PID: 540)
Reads settings of System Certificates
- chrome.exe (PID: 540)
- chrome.exe (PID: 2212)
Reads Internet Cache Settings
- chrome.exe (PID: 540)
Reads the hosts file
- chrome.exe (PID: 540)
- chrome.exe (PID: 2212)
- instup.exe (PID: 1664)
- instup.exe (PID: 1856)
- overseer.exe (PID: 3076)
- AvastSvc.exe (PID: 4588)
Dropped object may contain Bitcoin addresses
- instup.exe (PID: 1856)
- AvEmUpdate.exe (PID: 2716)
Changes settings of System certificates
- chrome.exe (PID: 2212)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
137
Monitored processes
94
Malicious processes
19
Suspicious processes
10
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 280 | "C:\Program Files\Avast Software\Avast\avBugReport.exe" --send dumps|report --silent --guid ea5aa208-5cb7-4353-a6e6-3c86b709cd34 | C:\Program Files\Avast Software\Avast\avBugReport.exe | AvEmUpdate.exe | ||||||||||||
User: admin Company: AVAST Software Integrity Level: HIGH Description: Avast Antivirus Bug Report Exit code: 2 Version: 20.7.5568.0 Modules
| |||||||||||||||
| 376 | "C:\Windows\Temp\asw.6fe5cdc27f6b5030\avast_free_antivirus_setup_online.exe" /cookie:mmm_sft_ppi_004_927_m /ga_clientid:032c1543-8298-46c2-ab87-78e92a2bc892 /edat_dir:C:\Windows\Temp\asw.6fe5cdc27f6b5030 | C:\Windows\Temp\asw.6fe5cdc27f6b5030\avast_free_antivirus_setup_online.exe | avast_free_antivirus_setup_online.exe | ||||||||||||
User: admin Company: AVAST Software Integrity Level: HIGH Description: Avast Antivirus Exit code: 0 Version: 20.7.5568.0 Modules
| |||||||||||||||
| 540 | "C:\Program Files\Google\Chrome\Application\chrome.exe" "https://windows-10.en.softonic.com/download" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 592 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1024,8044618112790646357,9585450534060850497,131072 --enable-features=PasswordImport --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=11307390450167309085 --renderer-client-id=5 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2276 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 700 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1024,8044618112790646357,9585450534060850497,131072 --enable-features=PasswordImport --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=107559475206924486 --renderer-client-id=4 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2400 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 780 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1024,8044618112790646357,9585450534060850497,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=11522436177835601287 --renderer-client-id=8 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3432 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 928 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1024,8044618112790646357,9585450534060850497,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAADgAAAgAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=3104360722775355508 --mojo-platform-channel-handle=1036 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1020 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1024,8044618112790646357,9585450534060850497,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=9993363407132854555 --renderer-client-id=15 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4416 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1088 | "C:\Users\admin\Downloads\avast_free_antivirus_setup_online.exe" | C:\Users\admin\Downloads\avast_free_antivirus_setup_online.exe | chrome.exe | ||||||||||||
User: admin Company: AVAST Software Integrity Level: HIGH Description: Avast MicroInstaller Installer Exit code: 0 Version: 2.1.27.0 Modules
| |||||||||||||||
| 1532 | "C:\Program Files\Avast Software\Avast\setup\instup.exe" /wait /session_id:1 /finish_delayed_installation | C:\Program Files\Avast Software\Avast\setup\instup.exe | — | AvastSvc.exe | |||||||||||
User: admin Company: AVAST Software Integrity Level: HIGH Description: Avast Antivirus Installer Exit code: 0 Version: 20.7.5568.0 Modules
| |||||||||||||||
Total events
6 666
Read events
1 742
Write events
4 898
Delete events
26
Modification events
| (PID) Process: | (540) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (540) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (540) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (540) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (540) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (1776) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 540-13245026259859750 |
Value: 259 | |||
| (PID) Process: | (540) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (540) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (540) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 2832-13239195546717773 |
Value: 0 | |||
| (PID) Process: | (540) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
Executable files
502
Suspicious files
441
Text files
394
Unknown types
60
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 540 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old | — | |
MD5:— | SHA256:— | |||
| 540 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000032.dbtmp | — | |
MD5:— | SHA256:— | |||
| 540 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\0a2e7fa9-f7c5-4772-a1da-e1116777cc5a.tmp | — | |
MD5:— | SHA256:— | |||
| 540 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Feature Engagement Tracker\EventDB\LOG.old | text | |
MD5:— | SHA256:— | |||
| 540 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:— | SHA256:— | |||
| 540 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Session Storage\LOG.old | text | |
MD5:— | SHA256:— | |||
| 540 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Last Tabs | binary | |
MD5:— | SHA256:— | |||
| 540 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 540 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old~RFed916.TMP | — | |
MD5:— | SHA256:— | |||
| 540 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Feature Engagement Tracker\EventDB\LOG.old~RFed78f.TMP | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
128
TCP/UDP connections
509
DNS requests
441
Threats
26
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1664 | instup.exe | GET | 200 | 184.24.77.17:80 | http://h4444966.iavs9x.u.avast.com/iavs9x/offertool_ais-979.vpx | US | binary | 336 Kb | whitelisted |
1088 | avast_free_antivirus_setup_online.exe | GET | 200 | 2.16.177.19:80 | http://iavs9x.u.avast.com/iavs9x/avast_free_antivirus_setup_online.exe | unknown | executable | 7.85 Mb | whitelisted |
2212 | chrome.exe | GET | 200 | 176.126.58.209:80 | http://r6---sn-x2pm-3ufk.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOWFjQUFXV2lsMkZVdjR5Vk5VZHJTM3E1dw/7919.1028.0.0_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx?cms_redirect=yes&mh=sX&mip=84.17.55.74&mm=28&mn=sn-x2pm-3ufk&ms=nvh&mt=1600552577&mv=m&mvi=6&pl=23&shardbypass=yes | PL | crx | 834 Kb | whitelisted |
1664 | instup.exe | GET | 200 | 184.24.77.17:80 | http://h4444966.iavs9x.u.avast.com/iavs9x/avbugreport_ais-979.vpx | US | binary | 1.08 Mb | whitelisted |
1664 | instup.exe | GET | 200 | 184.24.77.17:80 | http://h4444966.iavs9x.u.avast.com/iavs9x/sbr_x86_ais-979.vpx | US | binary | 7.58 Kb | whitelisted |
1856 | instup.exe | GET | 200 | 185.225.251.41:80 | http://h4305360.vps18tiny.u.avcdn.net/vps18tiny/jrog2-4.vpx | unknown | binary | 861 Kb | suspicious |
1088 | avast_free_antivirus_setup_online.exe | POST | 204 | 5.62.40.204:80 | http://v7event.stats.avast.com/cgi-bin/iavsevents.cgi | DE | — | — | whitelisted |
1088 | avast_free_antivirus_setup_online.exe | POST | 204 | 5.62.40.204:80 | http://v7event.stats.avast.com/cgi-bin/iavsevents.cgi | DE | — | — | whitelisted |
2212 | chrome.exe | GET | 302 | 172.217.18.110:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOWFjQUFXV2lsMkZVdjR5Vk5VZHJTM3E1dw/7919.1028.0.0_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx | US | html | 525 b | whitelisted |
1664 | instup.exe | GET | 200 | 184.24.77.8:80 | http://r4427608.iavs9x.u.avast.com/iavs9x/servers.def.vpx | US | binary | 3.24 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2212 | chrome.exe | 172.217.16.163:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
2212 | chrome.exe | 172.217.18.168:443 | www.googletagmanager.com | Google Inc. | US | whitelisted |
2212 | chrome.exe | 172.217.22.66:443 | securepubads.g.doubleclick.net | Google Inc. | US | whitelisted |
2212 | chrome.exe | 172.217.18.109:443 | accounts.google.com | Google Inc. | US | suspicious |
2212 | chrome.exe | 151.101.2.133:443 | sc.sftcdn.net | Fastly | US | malicious |
2212 | chrome.exe | 35.227.233.104:443 | windows-10.en.softonic.com | — | US | malicious |
2212 | chrome.exe | 104.111.233.72:443 | images.sftcdn.net | Akamai International B.V. | NL | unknown |
2212 | chrome.exe | 99.86.5.213:443 | c.amazon-adsystem.com | AT&T Services, Inc. | US | unknown |
2212 | chrome.exe | 204.79.197.200:443 | bat.bing.com | Microsoft Corporation | US | whitelisted |
2212 | chrome.exe | 213.19.162.61:443 | fastlane.rubiconproject.com | The Rubicon Project, Inc. | GB | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
windows-10.en.softonic.com |
| malicious |
accounts.google.com |
| shared |
sc.sftcdn.net |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
securepubads.g.doubleclick.net |
| whitelisted |
fastlane.rubiconproject.com |
| whitelisted |
images.sftcdn.net |
| whitelisted |
sdk.privacy-center.org |
| shared |
c.amazon-adsystem.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1088 | avast_free_antivirus_setup_online.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2716 | AvEmUpdate.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
4244 | CCUpdate.exe | Potential Corporate Privacy Violation | ET POLICY External IP Lookup (avast .com) |
5100 | CCUpdate.exe | Potential Corporate Privacy Violation | ET POLICY External IP Lookup (avast .com) |
2652 | CCUpdate.exe | Potential Corporate Privacy Violation | ET POLICY External IP Lookup (avast .com) |
2652 | CCUpdate.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
5188 | CCUpdate.exe | Potential Corporate Privacy Violation | ET POLICY External IP Lookup (avast .com) |
5868 | CCUpdate.exe | Potential Corporate Privacy Violation | ET POLICY External IP Lookup (avast .com) |
4588 | AvastSvc.exe | Potential Corporate Privacy Violation | ET DNS Non-DNS or Non-Compliant DNS traffic on DNS port Reserved Bit Set |
4588 | AvastSvc.exe | Potential Corporate Privacy Violation | ET DNS Non-DNS or Non-Compliant DNS traffic on DNS port Opcode 8 through 15 set |
14 ETPRO signatures available at the full report
Process | Message |
|---|---|
AvastSvc.exe | [2020-09-19 22:00:22.127] [error ] [ring_client] [ 4588: 5940] asw::ring_client::NetworkStatus::isInternetAvailable::<lambda_58ccc668868625c53168cb8641761bb6>::operator () call anen failed
|
AvastSvc.exe | [2020-09-19 22:00:22.127] [error ] [ring_client] [ 4588: 5940] asw::ring_client::call_anen_exception failed reason: Request app.anen.global.get_connectivity was not processed. Routing parameters:
|
AvastSvc.exe | [2020-09-19 22:00:25.632] [error ] [av_pp_prov ] [ 4588: 3128] Exception: get_file_content 'C:\Program Files\Avast Software\Avast\gui_resources\default_av\updatefile.json'
Code: 0x00000003 (3)
|
AvastSvc.exe | [2020-09-19 22:00:28.782] [error ] [gui_cache ] [ 4588: 3128] Exception: Unable to enumerate directory 'C:\Program Files\Avast Software\Avast\gui_resources\*.*'!
Code: 0x00000003 (3)
|
AvastSvc.exe | [2020-09-19 22:00:28.835] [error ] [gui_cache ] [ 4588: 3432] failed to update shepherd
|
AvastSvc.exe | [2020-09-19 22:00:29.135] [error ] [tasks ] [ 4588: 5940] 'Burger::EventConsumer::OnFlush' task failed without a caller check.
Exception: Identity of Burger client was not set.
|