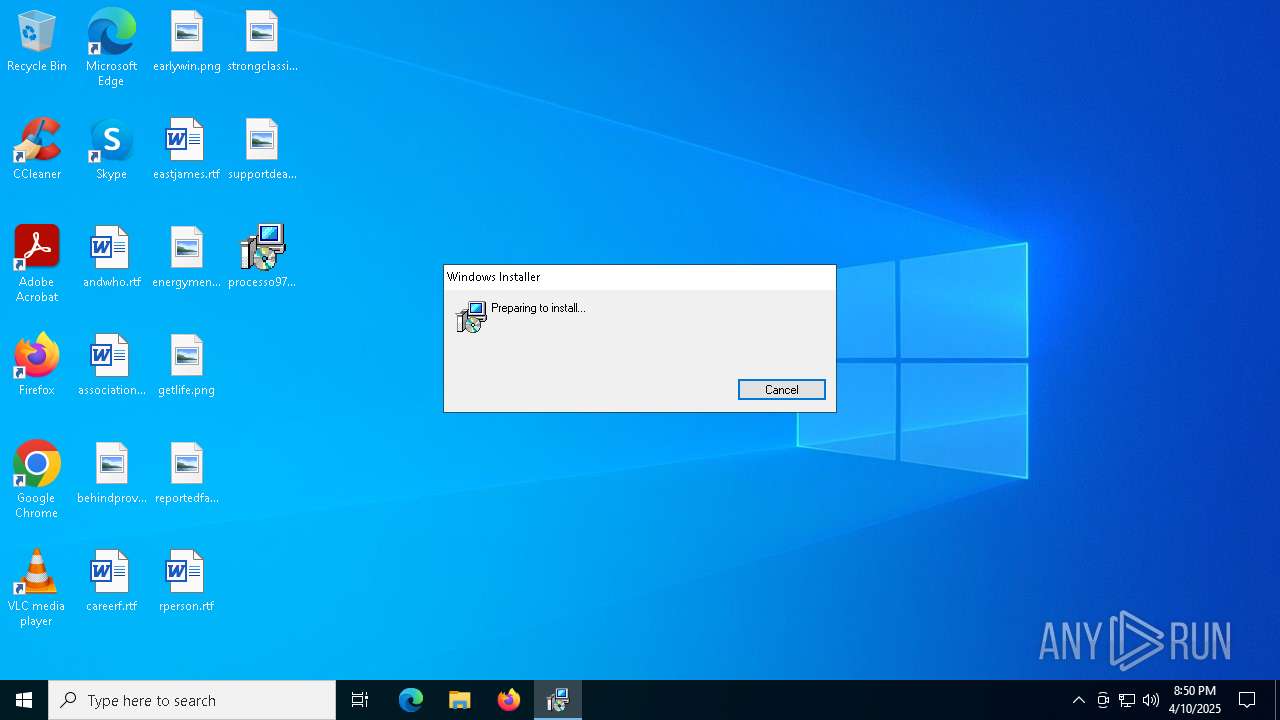
| File name: | processo974974.msi |
| Full analysis: | https://app.any.run/tasks/e151c515-d2ed-4e59-ad5c-ae5097febbdd |
| Verdict: | Malicious activity |
| Threats: | A loader is malicious software that infiltrates devices to deliver malicious payloads. This malware is capable of infecting victims’ computers, analyzing their system information, and installing other types of threats, such as trojans or stealers. Criminals usually deliver loaders through phishing emails and links by relying on social engineering to trick users into downloading and running their executables. Loaders employ advanced evasion and persistence tactics to avoid detection. |
| Analysis date: | April 10, 2025, 20:50:24 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, MSI Installer, Code page: 1252, Title: Installation Database, Subject: AteraAgent, Author: Atera networks, Keywords: Installer, Comments: This installer database contains the logic and data required to install AteraAgent., Template: Intel;1033, Revision Number: {721AD955-79FD-4019-BBF5-9DCC4C1175BB}, Create Time/Date: Wed Feb 28 10:52:02 2024, Last Saved Time/Date: Wed Feb 28 10:52:02 2024, Number of Pages: 200, Number of Words: 6, Name of Creating Application: Windows Installer XML Toolset (3.11.2.4516), Security: 2 |
| MD5: | 4166A7FC9A5726E2A468DC7E053B2A24 |
| SHA1: | FA2E7DE96F5F4CAFDC95767C4E8ADEE460D0399E |
| SHA256: | F2CF1589F2C34FB845C7514DB1A07ADE8E5F5B786E690F795507FDEDC871FD3C |
| SSDEEP: | 98304:JIZTffzvns6eLKLdpRwznfsJb+7J7ERXndiWaKzPtSjXmbABY/lT8vjkZBvrePVv:G3XP9No |
MALICIOUS
Starts NET.EXE for service management
- msiexec.exe (PID: 4812)
- net.exe (PID: 4784)
- net.exe (PID: 4152)
- msiexec.exe (PID: 4756)
- net.exe (PID: 4424)
Bypass execution policy to execute commands
- powershell.exe (PID: 6416)
- powershell.exe (PID: 1280)
- powershell.exe (PID: 5608)
Changes powershell execution policy (Bypass)
- AgentPackageAgentInformation.exe (PID: 8156)
- AgentPackageAgentInformation.exe (PID: 7692)
- AgentPackageAgentInformation.exe (PID: 4488)
Changes the autorun value in the registry
- dotnet-runtime-8.0.11-win-x64.exe (PID: 1188)
ATERA mutex has been found
- AgentPackageRuntimeInstaller.exe (PID: 5588)
- AgentPackageMonitoring.exe (PID: 6676)
SUSPICIOUS
Process drops legitimate windows executable
- msiexec.exe (PID: 7316)
- msiexec.exe (PID: 7496)
- AteraAgent.exe (PID: 7640)
- AteraAgent.exe (PID: 6136)
- AgentPackageUpgradeAgent.exe (PID: 4228)
- AgentPackageRuntimeInstaller.exe (PID: 5588)
- 8-0-11.exe (PID: 928)
- 8-0-11.exe (PID: 5156)
- dotnet-runtime-8.0.11-win-x64.exe (PID: 1188)
- AteraAgent.exe (PID: 4628)
Executes as Windows Service
- VSSVC.exe (PID: 7544)
- AteraAgent.exe (PID: 7640)
- AteraAgent.exe (PID: 6136)
- AteraAgent.exe (PID: 4628)
Executable content was dropped or overwritten
- rundll32.exe (PID: 6488)
- rundll32.exe (PID: 6476)
- rundll32.exe (PID: 5008)
- rundll32.exe (PID: 5400)
- AteraAgent.exe (PID: 7640)
- csc.exe (PID: 7808)
- AteraAgent.exe (PID: 6136)
- csc.exe (PID: 300)
- AgentPackageTicketing.exe (PID: 4884)
- AgentPackageUpgradeAgent.exe (PID: 4228)
- rundll32.exe (PID: 7176)
- rundll32.exe (PID: 7656)
- rundll32.exe (PID: 7608)
- rundll32.exe (PID: 7436)
- AgentPackageRuntimeInstaller.exe (PID: 5588)
- 8-0-11.exe (PID: 5156)
- dotnet-runtime-8.0.11-win-x64.exe (PID: 1188)
- 8-0-11.exe (PID: 928)
- SplashtopStreamer.exe (PID: 5508)
- PreVerCheck.exe (PID: 7652)
- AteraAgent.exe (PID: 4628)
- csc.exe (PID: 7216)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 7496)
Potential Corporate Privacy Violation
- rundll32.exe (PID: 6476)
- rundll32.exe (PID: 5400)
- AteraAgent.exe (PID: 7640)
- AgentPackageAgentInformation.exe (PID: 8124)
- AteraAgent.exe (PID: 6136)
- AgentPackageMonitoring.exe (PID: 2268)
- AgentPackageAgentInformation.exe (PID: 8156)
- AgentPackageInternalPoller.exe (PID: 904)
- AgentPackageMarketplace.exe (PID: 3396)
- AgentPackageAgentInformation.exe (PID: 7692)
- rundll32.exe (PID: 7656)
- rundll32.exe (PID: 7436)
- AteraAgent.exe (PID: 4628)
- AgentPackageInternalPoller.exe (PID: 4868)
- AgentPackageMarketplace.exe (PID: 6148)
- AgentPackageMonitoring.exe (PID: 6676)
Uses TASKKILL.EXE to kill process
- msiexec.exe (PID: 4812)
- cmd.exe (PID: 2908)
- cmd.exe (PID: 2896)
- cmd.exe (PID: 3760)
- cmd.exe (PID: 8100)
- cmd.exe (PID: 6252)
- cmd.exe (PID: 4012)
- cmd.exe (PID: 2780)
- cmd.exe (PID: 1040)
- msiexec.exe (PID: 4756)
- cmd.exe (PID: 7400)
- cmd.exe (PID: 1452)
Reads security settings of Internet Explorer
- AteraAgent.exe (PID: 7284)
- AteraAgent.exe (PID: 7640)
- AteraAgent.exe (PID: 6136)
- AgentPackageAgentInformation.exe (PID: 8156)
- AteraAgent.exe (PID: 3396)
- AteraAgent.exe (PID: 4628)
- 8-0-11.exe (PID: 5156)
- SplashtopStreamer.exe (PID: 5508)
- AgentPackageAgentInformation.exe (PID: 4488)
ATERAAGENT has been detected
- AteraAgent.exe (PID: 7640)
- AteraAgent.exe (PID: 6136)
- AteraAgent.exe (PID: 7284)
- AteraAgent.exe (PID: 5024)
- AteraAgent.exe (PID: 3396)
- AteraAgent.exe (PID: 4628)
Starts SC.EXE for service management
- AteraAgent.exe (PID: 7640)
- AteraAgent.exe (PID: 6136)
- AteraAgent.exe (PID: 4628)
Reads the date of Windows installation
- AteraAgent.exe (PID: 7640)
- AteraAgent.exe (PID: 6136)
- AteraAgent.exe (PID: 4628)
Restarts service on failure
- sc.exe (PID: 632)
- sc.exe (PID: 3888)
- sc.exe (PID: 1128)
Starts POWERSHELL.EXE for commands execution
- AgentPackageAgentInformation.exe (PID: 8156)
- cmd.exe (PID: 2344)
- AgentPackageAgentInformation.exe (PID: 7692)
- cmd.exe (PID: 6800)
- AgentPackageAgentInformation.exe (PID: 4488)
- cmd.exe (PID: 6104)
The process bypasses the loading of PowerShell profile settings
- AgentPackageAgentInformation.exe (PID: 8156)
- AgentPackageAgentInformation.exe (PID: 7692)
- AgentPackageAgentInformation.exe (PID: 4488)
The process executes Powershell scripts
- AgentPackageAgentInformation.exe (PID: 8156)
- cmd.exe (PID: 2344)
- AgentPackageAgentInformation.exe (PID: 7692)
- cmd.exe (PID: 6800)
- AgentPackageAgentInformation.exe (PID: 4488)
- cmd.exe (PID: 6104)
CSC.EXE is used to compile C# code
- csc.exe (PID: 7808)
- csc.exe (PID: 300)
- csc.exe (PID: 7216)
The process executes VB scripts
- cmd.exe (PID: 7696)
- cmd.exe (PID: 5776)
- cmd.exe (PID: 644)
Gets the drive type (SCRIPT)
- cscript.exe (PID: 2064)
- cscript.exe (PID: 6148)
- cscript.exe (PID: 2288)
Starts CMD.EXE for commands execution
- AgentPackageAgentInformation.exe (PID: 8156)
- AgentPackageAgentInformation.exe (PID: 7692)
- AgentPackageRuntimeInstaller.exe (PID: 5588)
- msiexec.exe (PID: 8012)
- AgentPackageAgentInformation.exe (PID: 4488)
Gets full path of the running script (SCRIPT)
- cscript.exe (PID: 2064)
- cscript.exe (PID: 6148)
- cscript.exe (PID: 2288)
Creates FileSystem object to access computer's file system (SCRIPT)
- cscript.exe (PID: 2064)
- cscript.exe (PID: 6148)
- cscript.exe (PID: 2288)
Accesses WMI object, sets custom ImpersonationLevel (SCRIPT)
- cscript.exe (PID: 2064)
- cscript.exe (PID: 6148)
- cscript.exe (PID: 2288)
Accesses computer name via WMI (SCRIPT)
- cscript.exe (PID: 2064)
- cscript.exe (PID: 6148)
- cscript.exe (PID: 2288)
Gets a collection of all available drive names (SCRIPT)
- cscript.exe (PID: 2064)
- cscript.exe (PID: 6148)
- cscript.exe (PID: 2288)
Executes application which crashes
- cscript.exe (PID: 2064)
- cscript.exe (PID: 6148)
- cscript.exe (PID: 2288)
The process creates files with name similar to system file names
- WerFault.exe (PID: 2104)
- AteraAgent.exe (PID: 6136)
- WerFault.exe (PID: 7156)
- msiexec.exe (PID: 7496)
- WerFault.exe (PID: 6072)
Searches for installed software
- AgentPackageAgentInformation.exe (PID: 7692)
Starts a Microsoft application from unusual location
- 8-0-11.exe (PID: 5156)
- dotnet-runtime-8.0.11-win-x64.exe (PID: 1188)
Starts itself from another location
- 8-0-11.exe (PID: 5156)
Creates a software uninstall entry
- dotnet-runtime-8.0.11-win-x64.exe (PID: 1188)
Drops a system driver (possible attempt to evade defenses)
- msiexec.exe (PID: 7496)
INFO
Manages system restore points
- SrTasks.exe (PID: 8056)
Checks supported languages
- msiexec.exe (PID: 7496)
- msiexec.exe (PID: 1672)
- msiexec.exe (PID: 4812)
- AteraAgent.exe (PID: 7284)
- AteraAgent.exe (PID: 7640)
- AgentPackageAgentInformation.exe (PID: 4488)
- AgentPackageAgentInformation.exe (PID: 8124)
- AgentPackageAgentInformation.exe (PID: 6488)
- AteraAgent.exe (PID: 6136)
- AgentPackageAgentInformation.exe (PID: 8156)
- AgentPackageSTRemote.exe (PID: 7184)
- AgentPackageMonitoring.exe (PID: 2268)
- csc.exe (PID: 7808)
- cvtres.exe (PID: 7344)
- AgentPackageAgentInformation.exe (PID: 7692)
- AgentPackageHeartbeat.exe (PID: 4572)
- AgentPackageSystemTools.exe (PID: 8164)
- AgentPackageInternalPoller.exe (PID: 904)
- csc.exe (PID: 300)
- cvtres.exe (PID: 8152)
- AgentPackageMarketplace.exe (PID: 3396)
- AgentPackageADRemote.exe (PID: 2980)
- AgentPackageUpgradeAgent.exe (PID: 4228)
- msiexec.exe (PID: 4756)
- AteraAgent.exe (PID: 5024)
- AteraAgent.exe (PID: 3396)
- AteraAgent.exe (PID: 4628)
- 8-0-11.exe (PID: 928)
- 8-0-11.exe (PID: 5156)
- dotnet-runtime-8.0.11-win-x64.exe (PID: 1188)
- SplashtopStreamer.exe (PID: 5508)
- PreVerCheck.exe (PID: 7652)
- msiexec.exe (PID: 8012)
- _is9C86.exe (PID: 5212)
- _is9C86.exe (PID: 872)
- _is9C86.exe (PID: 7540)
- _is9C86.exe (PID: 1676)
- _is9C86.exe (PID: 6768)
- _is9C86.exe (PID: 6028)
- _is9C86.exe (PID: 7428)
- AgentPackageTicketing.exe (PID: 4884)
- _isB09C.exe (PID: 8164)
- _isB09C.exe (PID: 6744)
- _isB09C.exe (PID: 7792)
- _isB09C.exe (PID: 5964)
- _isB09C.exe (PID: 4000)
- _isB09C.exe (PID: 8132)
- _isB09C.exe (PID: 2984)
- _isB09C.exe (PID: 904)
- _isB09C.exe (PID: 3396)
- _isB09C.exe (PID: 7796)
- AgentPackageHeartbeat.exe (PID: 3100)
- AgentPackageADRemote.exe (PID: 8144)
- Agent.Package.Watchdog.exe (PID: 4376)
- AgentPackageAgentInformation.exe (PID: 4488)
- AgentPackageMarketplace.exe (PID: 6148)
- AgentPackageSystemTools.exe (PID: 2040)
- Agent.Package.Availability.exe (PID: 644)
- csc.exe (PID: 7216)
- cvtres.exe (PID: 4980)
Creates files or folders in the user directory
- msiexec.exe (PID: 7316)
Reads the software policy settings
- msiexec.exe (PID: 7316)
- msiexec.exe (PID: 7496)
- AteraAgent.exe (PID: 7284)
- AteraAgent.exe (PID: 7640)
- rundll32.exe (PID: 5400)
- AgentPackageAgentInformation.exe (PID: 4488)
- AgentPackageAgentInformation.exe (PID: 8124)
- AteraAgent.exe (PID: 6136)
- AgentPackageSTRemote.exe (PID: 7184)
- AgentPackageMonitoring.exe (PID: 2268)
- AgentPackageAgentInformation.exe (PID: 8156)
- rundll32.exe (PID: 6476)
- AgentPackageHeartbeat.exe (PID: 4572)
- AgentPackageInternalPoller.exe (PID: 904)
- cscript.exe (PID: 6148)
- AgentPackageMarketplace.exe (PID: 3396)
- AgentPackageRuntimeInstaller.exe (PID: 5588)
- AgentPackageUpgradeAgent.exe (PID: 4228)
- AgentPackageAgentInformation.exe (PID: 7692)
- rundll32.exe (PID: 7656)
- AgentPackageTicketing.exe (PID: 4884)
- AteraAgent.exe (PID: 3396)
- rundll32.exe (PID: 7436)
- AteraAgent.exe (PID: 4628)
- msiexec.exe (PID: 8012)
- AgentPackageInternalPoller.exe (PID: 4868)
- AgentPackageHeartbeat.exe (PID: 3100)
- AgentPackageMarketplace.exe (PID: 6148)
- cscript.exe (PID: 2288)
- AgentPackageMonitoring.exe (PID: 6676)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 7316)
Reads the computer name
- msiexec.exe (PID: 7496)
- msiexec.exe (PID: 1672)
- msiexec.exe (PID: 4812)
- AteraAgent.exe (PID: 7284)
- AteraAgent.exe (PID: 7640)
- AgentPackageAgentInformation.exe (PID: 4488)
- AgentPackageAgentInformation.exe (PID: 8124)
- AgentPackageAgentInformation.exe (PID: 6488)
- AteraAgent.exe (PID: 6136)
- AgentPackageAgentInformation.exe (PID: 8156)
- AgentPackageSTRemote.exe (PID: 7184)
- AgentPackageMonitoring.exe (PID: 2268)
- AgentPackageAgentInformation.exe (PID: 7692)
- AgentPackageHeartbeat.exe (PID: 4572)
- AgentPackageSystemTools.exe (PID: 8164)
- AgentPackageInternalPoller.exe (PID: 904)
- AgentPackageMarketplace.exe (PID: 3396)
- AgentPackageADRemote.exe (PID: 2980)
- AgentPackageOsUpdates.exe (PID: 2616)
- AgentPackageUpgradeAgent.exe (PID: 4228)
- AgentPackageTicketing.exe (PID: 4884)
- msiexec.exe (PID: 4756)
- AteraAgent.exe (PID: 5024)
- AteraAgent.exe (PID: 3396)
- AteraAgent.exe (PID: 4628)
- 8-0-11.exe (PID: 928)
- 8-0-11.exe (PID: 5156)
- SplashtopStreamer.exe (PID: 5508)
- msiexec.exe (PID: 8012)
- _is9C86.exe (PID: 5212)
- _is9C86.exe (PID: 7540)
- _is9C86.exe (PID: 6768)
- _is9C86.exe (PID: 6028)
- _is9C86.exe (PID: 7428)
- _isB09C.exe (PID: 8164)
- _isB09C.exe (PID: 6744)
- _isB09C.exe (PID: 7792)
- _isB09C.exe (PID: 8132)
- _isB09C.exe (PID: 3396)
- _isB09C.exe (PID: 904)
- _isB09C.exe (PID: 5964)
- _isB09C.exe (PID: 4000)
- _isB09C.exe (PID: 2984)
- AgentPackageHeartbeat.exe (PID: 3100)
- AgentPackageADRemote.exe (PID: 8144)
- Agent.Package.Watchdog.exe (PID: 4376)
- AgentPackageMarketplace.exe (PID: 6148)
- AgentPackageAgentInformation.exe (PID: 4488)
- AgentPackageMonitoring.exe (PID: 6676)
Executable content was dropped or overwritten
- msiexec.exe (PID: 7496)
- msiexec.exe (PID: 8012)
Reads the machine GUID from the registry
- msiexec.exe (PID: 7496)
- AteraAgent.exe (PID: 7640)
- AteraAgent.exe (PID: 7284)
- AgentPackageAgentInformation.exe (PID: 8124)
- AgentPackageAgentInformation.exe (PID: 6488)
- AteraAgent.exe (PID: 6136)
- AgentPackageAgentInformation.exe (PID: 4488)
- AgentPackageAgentInformation.exe (PID: 8156)
- AgentPackageSTRemote.exe (PID: 7184)
- AgentPackageMonitoring.exe (PID: 2268)
- csc.exe (PID: 7808)
- AgentPackageAgentInformation.exe (PID: 7692)
- AgentPackageHeartbeat.exe (PID: 4572)
- AgentPackageSystemTools.exe (PID: 8164)
- AgentPackageInternalPoller.exe (PID: 904)
- csc.exe (PID: 300)
- AgentPackageMarketplace.exe (PID: 3396)
- AgentPackageADRemote.exe (PID: 2980)
- AgentPackageOsUpdates.exe (PID: 2616)
- AgentPackageRuntimeInstaller.exe (PID: 5588)
- AgentPackageUpgradeAgent.exe (PID: 4228)
- AgentPackageTicketing.exe (PID: 4884)
- AteraAgent.exe (PID: 5024)
- AteraAgent.exe (PID: 3396)
- AteraAgent.exe (PID: 4628)
- dotnet-runtime-8.0.11-win-x64.exe (PID: 1188)
- msiexec.exe (PID: 8012)
- AgentPackageADRemote.exe (PID: 8144)
- AgentPackageHeartbeat.exe (PID: 3100)
- AgentPackageInternalPoller.exe (PID: 4868)
- AgentPackageMarketplace.exe (PID: 6148)
- AgentPackageAgentInformation.exe (PID: 4488)
- AgentPackageMonitoring.exe (PID: 6676)
- csc.exe (PID: 7216)
The sample compiled with english language support
- rundll32.exe (PID: 6488)
- rundll32.exe (PID: 6476)
- rundll32.exe (PID: 5008)
- rundll32.exe (PID: 5400)
- AteraAgent.exe (PID: 7640)
- AteraAgent.exe (PID: 6136)
- rundll32.exe (PID: 7176)
- rundll32.exe (PID: 7656)
- rundll32.exe (PID: 7608)
- rundll32.exe (PID: 7436)
- AgentPackageRuntimeInstaller.exe (PID: 5588)
- 8-0-11.exe (PID: 5156)
- 8-0-11.exe (PID: 928)
- msiexec.exe (PID: 7496)
- SplashtopStreamer.exe (PID: 5508)
- PreVerCheck.exe (PID: 7652)
- dotnet-runtime-8.0.11-win-x64.exe (PID: 1188)
- msiexec.exe (PID: 8012)
- AteraAgent.exe (PID: 4628)
Create files in a temporary directory
- rundll32.exe (PID: 6476)
- rundll32.exe (PID: 6488)
- rundll32.exe (PID: 5008)
- rundll32.exe (PID: 5400)
Checks proxy server information
- rundll32.exe (PID: 6476)
- rundll32.exe (PID: 5400)
Creates a software uninstall entry
- msiexec.exe (PID: 7496)
Reads Environment values
- AteraAgent.exe (PID: 7284)
- AteraAgent.exe (PID: 7640)
- AgentPackageAgentInformation.exe (PID: 4488)
- AgentPackageAgentInformation.exe (PID: 8124)
- AgentPackageAgentInformation.exe (PID: 6488)
- AteraAgent.exe (PID: 6136)
- AgentPackageAgentInformation.exe (PID: 8156)
- AgentPackageSTRemote.exe (PID: 7184)
- AgentPackageMonitoring.exe (PID: 2268)
- AgentPackageAgentInformation.exe (PID: 7692)
- AgentPackageHeartbeat.exe (PID: 4572)
- AgentPackageSystemTools.exe (PID: 8164)
- AgentPackageInternalPoller.exe (PID: 904)
- AgentPackageMarketplace.exe (PID: 3396)
- AgentPackageADRemote.exe (PID: 2980)
- AgentPackageOsUpdates.exe (PID: 2616)
- AgentPackageUpgradeAgent.exe (PID: 4228)
- AgentPackageTicketing.exe (PID: 4884)
- AteraAgent.exe (PID: 5024)
- AteraAgent.exe (PID: 4628)
- AgentPackageHeartbeat.exe (PID: 3100)
- AgentPackageADRemote.exe (PID: 8144)
- AgentPackageInternalPoller.exe (PID: 4868)
- AgentPackageAgentInformation.exe (PID: 4488)
- AgentPackageMarketplace.exe (PID: 6148)
- AgentPackageMonitoring.exe (PID: 6676)
Creates files in the program directory
- AteraAgent.exe (PID: 7284)
- AteraAgent.exe (PID: 7640)
- AgentPackageMonitoring.exe (PID: 2268)
- AteraAgent.exe (PID: 6136)
- AgentPackageAgentInformation.exe (PID: 8156)
- AgentPackageSystemTools.exe (PID: 8164)
- AgentPackageInternalPoller.exe (PID: 904)
- AgentPackageUpgradeAgent.exe (PID: 4228)
- AgentPackageTicketing.exe (PID: 4884)
- AteraAgent.exe (PID: 3396)
- AgentPackageRuntimeInstaller.exe (PID: 5588)
- dotnet-runtime-8.0.11-win-x64.exe (PID: 1188)
- AgentPackageSTRemote.exe (PID: 7184)
- AteraAgent.exe (PID: 4628)
- AgentPackageInternalPoller.exe (PID: 4868)
- AgentPackageMonitoring.exe (PID: 6676)
Disables trace logs
- AteraAgent.exe (PID: 7640)
- rundll32.exe (PID: 5400)
- AgentPackageAgentInformation.exe (PID: 4488)
- AgentPackageAgentInformation.exe (PID: 8124)
- AteraAgent.exe (PID: 6136)
- AgentPackageSTRemote.exe (PID: 7184)
- AgentPackageMonitoring.exe (PID: 2268)
- rundll32.exe (PID: 6476)
- AgentPackageAgentInformation.exe (PID: 8156)
- AgentPackageHeartbeat.exe (PID: 4572)
- AgentPackageMarketplace.exe (PID: 3396)
- AgentPackageUpgradeAgent.exe (PID: 4228)
- AgentPackageTicketing.exe (PID: 4884)
- rundll32.exe (PID: 7656)
- rundll32.exe (PID: 7436)
- AteraAgent.exe (PID: 4628)
- AgentPackageInternalPoller.exe (PID: 4868)
- AgentPackageHeartbeat.exe (PID: 3100)
- AgentPackageMarketplace.exe (PID: 6148)
- AgentPackageMonitoring.exe (PID: 6676)
SPLASHTOP has been detected
- AgentPackageSTRemote.exe (PID: 7184)
- msiexec.exe (PID: 7496)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 6700)
- powershell.exe (PID: 1676)
- powershell.exe (PID: 872)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (98.5) |
|---|---|---|
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| CodePage: | Windows Latin 1 (Western European) |
|---|---|
| Title: | Installation Database |
| Subject: | AteraAgent |
| Author: | Atera networks |
| Keywords: | Installer |
| Comments: | This installer database contains the logic and data required to install AteraAgent. |
| Template: | Intel;1033 |
| RevisionNumber: | {721AD955-79FD-4019-BBF5-9DCC4C1175BB} |
| CreateDate: | 2024:02:28 10:52:02 |
| ModifyDate: | 2024:02:28 10:52:02 |
| Pages: | 200 |
| Words: | 6 |
| Software: | Windows Installer XML Toolset (3.11.2.4516) |
| Security: | Read-only recommended |
Total processes
333
Monitored processes
196
Malicious processes
17
Suspicious processes
10
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 300 | "C:\Windows\Microsoft.NET\Framework64\v4.0.30319\csc.exe" /noconfig /fullpaths @"C:\WINDOWS\TEMP\u5gasy0y\u5gasy0y.cmdline" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\csc.exe | powershell.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Visual C# Command Line Compiler Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 516 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | AgentPackageAgentInformation.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 516 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | sc.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 616 | powershell.exe -File "C:\Program Files\Microsoft Office\Office16\vNextDiag.ps1" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 632 | "C:\Windows\System32\sc.exe" failure AteraAgent reset= 600 actions= restart/25000 | C:\Windows\System32\sc.exe | — | AteraAgent.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Service Control Manager Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 632 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | AgentPackageMarketplace.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 632 | taskkill.exe /F /IM SRManager.exe /T | C:\Windows\SysWOW64\taskkill.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Terminates Processes Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 644 | "C:\Program Files\ATERA Networks\AteraAgent\Packages\Agent.Package.Availability\Agent.Package.Availability.exe" 9ef0ff40-1954-4c0a-acd7-0b3d39cc5d46 "96edae5c-af7f-4fc2-beba-31d76a816f7c" agent-api.atera.com/Production 443 or8ixLi90Mf "connect" 001Q300000RfSDkIAN | C:\Program Files\ATERA Networks\AteraAgent\Packages\Agent.Package.Availability\Agent.Package.Availability.exe | AteraAgent.exe | ||||||||||||
User: SYSTEM Company: Agent.Package.Availability Integrity Level: SYSTEM Description: Agent.Package.Availability Exit code: 2147516547 Version: 0.19.0.0 Modules
| |||||||||||||||
| 644 | "C:\Windows\System32\cmd.exe" /c cscript "C:\Program Files\Microsoft Office\Office16\ospp.vbs" /dstatus | C:\Windows\System32\cmd.exe | — | AgentPackageAgentInformation.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Command Processor Exit code: 255 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 840 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
192 479
Read events
190 767
Write events
1 524
Delete events
188
Modification events
| (PID) Process: | (7496) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4800000000000000E8BF7B365AAADB01481D0000681D0000D50700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7496) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 4800000000000000E8BF7B365AAADB01481D0000681D0000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7496) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 48000000000000001567B7365AAADB01481D0000681D0000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7496) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 48000000000000001567B7365AAADB01481D0000681D0000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7496) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 4800000000000000681BBC365AAADB01481D0000681D0000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7496) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 4800000000000000E8E5C0365AAADB01481D0000681D0000D00700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7496) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 4800000000000000862524385AAADB01481D0000681D0000D30700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7544) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\Shadow Copy Optimization Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000963037385AAADB01781D0000981D0000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7544) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000963037385AAADB01781D0000941D0000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7544) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\ASR Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000963037385AAADB01781D0000541E0000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
943
Suspicious files
194
Text files
238
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7496 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 7316 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\8EC9B1D0ABBD7F98B401D425828828CE_93E8F0A6DF0B1F1414474691911362FC | binary | |
MD5:AB926873E3B75457660BC228F46AC413 | SHA256:6F88E1AEF5B9312A053019BD12B28EFEA0F07C3BAD4BC0B9ACC63260153CD5E4 | |||
| 7316 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\C8E534EE129F27D55460CE17FD628216_1130D9B25898B0DB0D4F04DC5B93F141 | binary | |
MD5:A634D8513EDA0CB405CC40E9B77589A3 | SHA256:8915BBE20BA5A976DCC74CCF21AED0DDA0AC20A3568E6A3116E83444F11A6BAA | |||
| 7316 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\698460A0B6E60F2F602361424D832905_8BB23D43DE574E82F2BEE0DF0EC47EEB | binary | |
MD5:A7B26537FB5F12CAAD7D3B03AA1D11B8 | SHA256:F104036CFEC5AB902DFB5F0FBE4F19F9A25A1120DB33813ED94B82E99EE93EE9 | |||
| 7316 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\8EC9B1D0ABBD7F98B401D425828828CE_93E8F0A6DF0B1F1414474691911362FC | binary | |
MD5:F70C78AF15F64B6BBE31A21C45D24D03 | SHA256:7A695E22E3BF144558E8C2D2175AD05FB726D262F587616647539F1FC5BE8AE8 | |||
| 7496 | msiexec.exe | C:\System Volume Information\SPP\snapshot-2 | binary | |
MD5:348724FEA7B90AAC1258817CE10D5E2B | SHA256:63F079B3270BD30D9355E06ACFE72B5F9C4795537A321879AAF8CA32B85DB8ED | |||
| 6476 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\MSI27BA.tmp-\Microsoft.Deployment.WindowsInstaller.dll | executable | |
MD5:1A5CAEA6734FDD07CAA514C3F3FB75DA | SHA256:CF06D4ED4A8BAF88C82D6C9AE0EFC81C469DE6DA8788AB35F373B350A4B4CDCA | |||
| 7316 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\698460A0B6E60F2F602361424D832905_8BB23D43DE574E82F2BEE0DF0EC47EEB | binary | |
MD5:E77FFD247EBC00B0EDA41B84C0BEF28A | SHA256:DEE7730F64C4DED13160F7B9464DBD7156FC5669096F678EA3236279ED6C50A9 | |||
| 6476 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\MSI27BA.tmp-\System.Management.dll | executable | |
MD5:878E361C41C05C0519BFC72C7D6E141C | SHA256:24DE61B5CAB2E3495FE8D817FB6E80094662846F976CF38997987270F8BBAE40 | |||
| 7496 | msiexec.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{d43e413e-7156-4262-aaf6-b9b4aa253cdb}_OnDiskSnapshotProp | binary | |
MD5:348724FEA7B90AAC1258817CE10D5E2B | SHA256:63F079B3270BD30D9355E06ACFE72B5F9C4795537A321879AAF8CA32B85DB8ED | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
116
TCP/UDP connections
75
DNS requests
29
Threats
44
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2104 | svchost.exe | GET | 200 | 2.19.11.105:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7316 | msiexec.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA6bGI750C3n79tQ4ghAGFo%3D | unknown | — | — | whitelisted |
7316 | msiexec.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEAnTy%2FhDMohv9omwS69%2Fdow%3D | unknown | — | — | whitelisted |
7316 | msiexec.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | — | — | whitelisted |
7284 | AteraAgent.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | — | — | whitelisted |
7284 | AteraAgent.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEAooSZl45YmN9AojjrilUug%3D | unknown | — | — | whitelisted |
7284 | AteraAgent.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA6bGI750C3n79tQ4ghAGFo%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 35.157.63.228:443 | https://ps.pndsn.com/time/0?pnsdk=NET45CSharp6.13.0.0&requestid=88b3721d-0a5b-4900-8233-52715624f7b3&uuid=9ef0ff40-1954-4c0a-acd7-0b3d39cc5d46 | unknown | text | 19 b | unknown |
— | — | POST | 200 | 40.119.152.241:443 | https://agent-api.atera.com/Production/Agent/track-event | unknown | — | — | whitelisted |
— | — | POST | 200 | 40.119.152.241:443 | https://agent-api.atera.com/Production/Agent/track-event | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4244 | RUXIMICS.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 2.19.11.105:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
7316 | msiexec.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6476 | rundll32.exe | 40.119.152.241:443 | agent-api.atera.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
7284 | AteraAgent.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
agent-api.atera.com |
| whitelisted |
ps.pndsn.com |
| unknown |
ps.atera.com |
| whitelisted |
my.splashtop.com |
| whitelisted |
download.splashtop.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6476 | rundll32.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Possible Atera Remote Access Software Domain observed in TLS SNI (agent-api .atera .com) |
7640 | AteraAgent.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Possible Atera Remote Access Software Domain observed in TLS SNI (agent-api .atera .com) |
5400 | rundll32.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Possible Atera Remote Access Software Domain observed in TLS SNI (agent-api .atera .com) |
7640 | AteraAgent.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Possible Atera Remote Access Software Domain observed in TLS SNI (agent-api .atera .com) |
— | — | Misc activity | SUSPICIOUS [ANY.RUN] Sent Host Name in HTTP POST Body |
7640 | AteraAgent.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Possible Atera Remote Access Software Domain observed in TLS SNI (agent-api .atera .com) |
7640 | AteraAgent.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Possible Atera Remote Access Software Domain observed in TLS SNI (agent-api .atera .com) |
7640 | AteraAgent.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Possible Atera Remote Access Software Domain observed in TLS SNI (agent-api .atera .com) |
8124 | AgentPackageAgentInformation.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Possible Atera Remote Access Software Domain observed in TLS SNI (agent-api .atera .com) |
7640 | AteraAgent.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Possible Atera Remote Access Software Domain observed in TLS SNI (agent-api .atera .com) |
Process | Message |
|---|---|
AgentPackageMonitoring.exe | Native library pre-loader is trying to load native SQLite library "C:\Program Files (x86)\ATERA Networks\AteraAgent\Packages\AgentPackageMonitoring\x64\SQLite.Interop.dll"...
|
SplashtopStreamer.exe | [5508]2025-04-10 20:52:30 [CUnPack::FindHeader] Sign Size:10240 (Last=0) |
SplashtopStreamer.exe | [5508]2025-04-10 20:52:30 [CUnPack::FindHeader] Header offset:434176 (Last=183) |
SplashtopStreamer.exe | [5508]2025-04-10 20:52:30 [CUtility::OSInfo] OS 10.0(19045) x64:1 (Last=0) |
SplashtopStreamer.exe | [5508]2025-04-10 20:52:30 [CUnPack::FindHeader] Name:C:\WINDOWS\TEMP\SplashtopStreamer.exe (Last=0) |
SplashtopStreamer.exe | [5508]2025-04-10 20:52:30 [CUnPack::UnPackFiles] FreeSpace:231760363520 FileSize:53075456 (Last=0) |
SplashtopStreamer.exe | [5508]2025-04-10 20:52:30 [CUnPack::UnPackFiles] (1/5)UnPack file name:C:\WINDOWS\TEMP\unpack\setup.msi (53075456) (Last=0) |
SplashtopStreamer.exe | [5508]2025-04-10 20:52:30 [CUnPack::UnPackFiles] FreeSpace:231697793024 FileSize:15 (Last=183) |
SplashtopStreamer.exe | [5508]2025-04-10 20:52:30 [CUnPack::UnPackFiles] UnPack count:1 len:53075456 File:(null) (Last=0) |
SplashtopStreamer.exe | [5508]2025-04-10 20:52:30 [CUnPack::UnPackFiles] FreeSpace:231697772544 FileSize:3383808 (Last=183) |