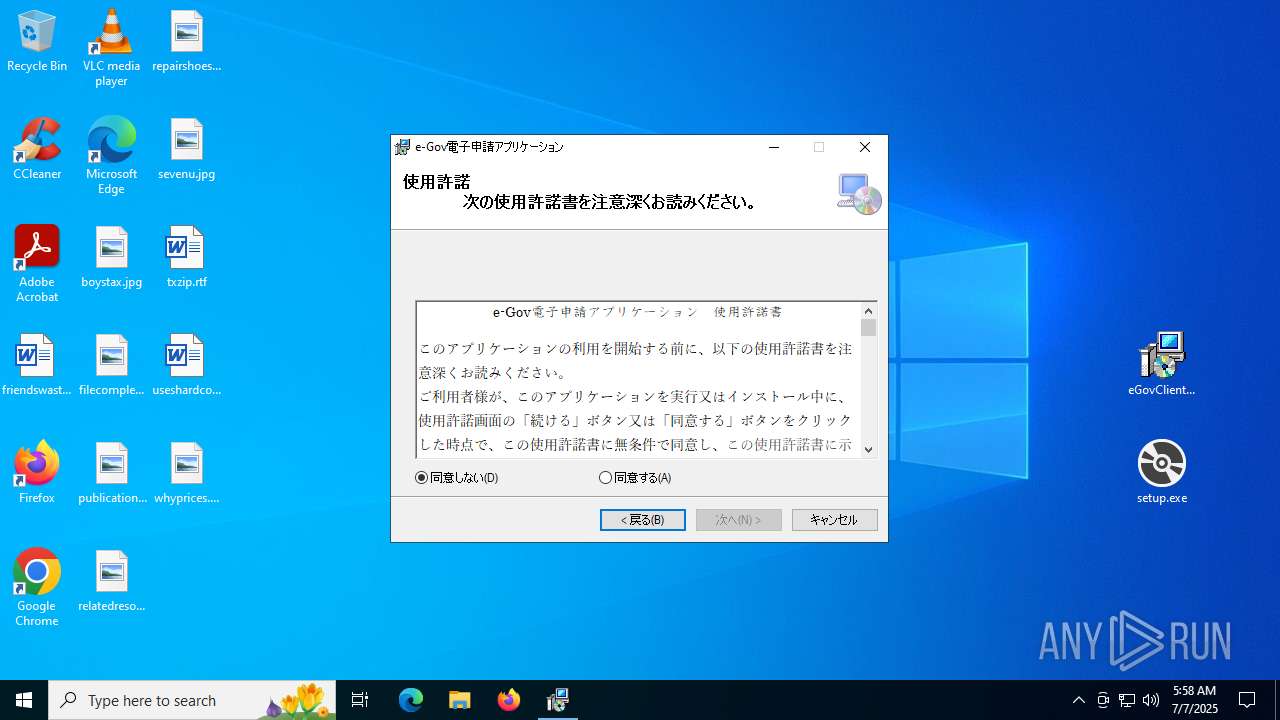
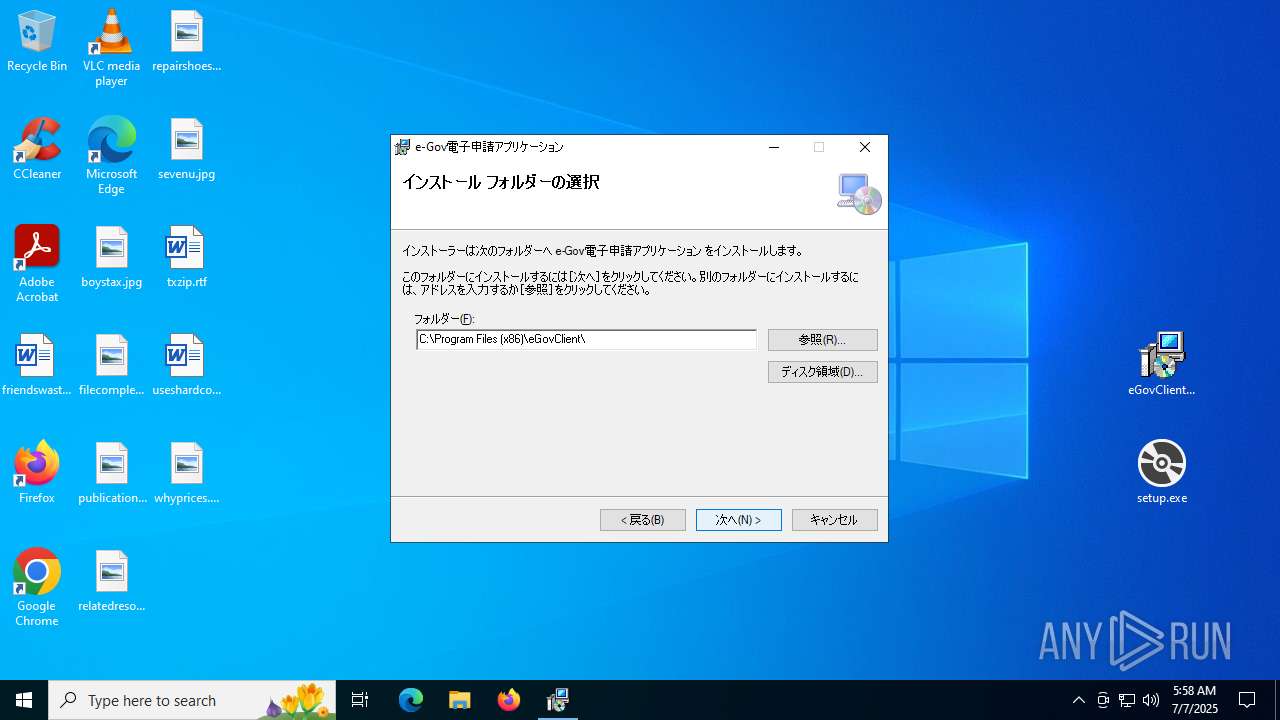
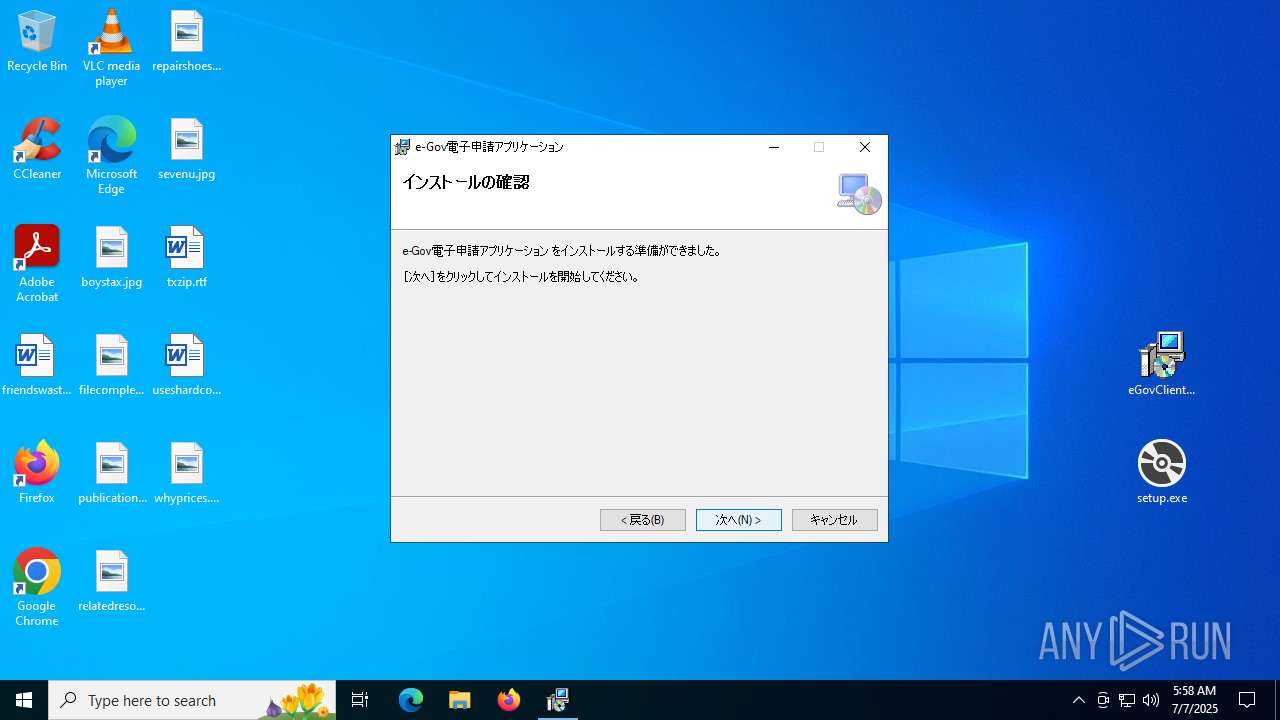
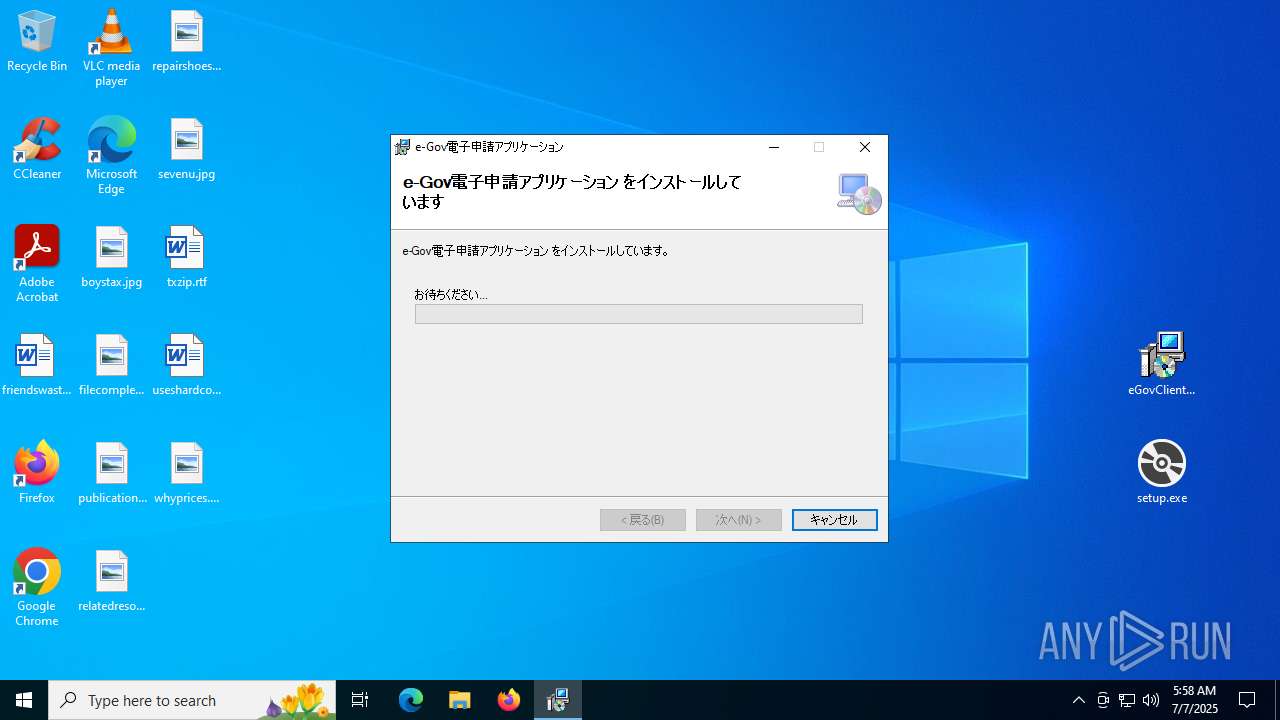
| File name: | eGovClientSetup_2.1.4.1 (1).zip |
| Full analysis: | https://app.any.run/tasks/ebfd4d33-65dd-4ed3-9b73-19252e5a0c2f |
| Verdict: | Malicious activity |
| Analysis date: | July 07, 2025, 05:57:43 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 07F9B5F2D0ED5B7A3051BDDA5AF47C3C |
| SHA1: | 6BB1499F57519E87C26A49E7FEDC495A6A13CB98 |
| SHA256: | F2CD012CD60452CBA4D8B832E245B019BFC490606696D28F10D49F4F69906C4F |
| SSDEEP: | 49152:yp0xv8th3dsMLwNcPFAU3JRy6qy+uLry4VT/uSHFfDIUHbP03Mh6RpUv2i2l3Wbe:Mft9SMLwaeU3JRy6qyBqg2SHFfDF83M2 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 1296)
- setup.exe (PID: 1332)
- NDP472-KB4054530-x86-x64-AllOS-JPN.exe (PID: 4844)
- msiexec.exe (PID: 3584)
Executable content was dropped or overwritten
- setup.exe (PID: 1332)
- NDP472-KB4054530-x86-x64-AllOS-JPN.exe (PID: 4844)
Reads security settings of Internet Explorer
- setup.exe (PID: 1332)
- eGovClient.exe (PID: 7064)
Starts a Microsoft application from unusual location
- NDP472-KB4054530-x86-x64-AllOS-JPN.exe (PID: 3672)
- NDP472-KB4054530-x86-x64-AllOS-JPN.exe (PID: 4844)
Creates file in the systems drive root
- NDP472-KB4054530-x86-x64-AllOS-JPN.exe (PID: 4844)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 3584)
Executes as Windows Service
- VSSVC.exe (PID: 1740)
Reads Microsoft Outlook installation path
- eGovClient.exe (PID: 7064)
Reads Internet Explorer settings
- eGovClient.exe (PID: 7064)
INFO
Manual execution by a user
- setup.exe (PID: 1332)
- eGovClient.exe (PID: 7064)
The sample compiled with english language support
- WinRAR.exe (PID: 1296)
- setup.exe (PID: 1332)
- NDP472-KB4054530-x86-x64-AllOS-JPN.exe (PID: 4844)
- msiexec.exe (PID: 3584)
- msiexec.exe (PID: 1636)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1296)
- msiexec.exe (PID: 1636)
- msiexec.exe (PID: 3584)
Reads the computer name
- setup.exe (PID: 1332)
- NDP472-KB4054530-x86-x64-AllOS-JPN.exe (PID: 4844)
- Setup.exe (PID: 5504)
- msiexec.exe (PID: 3584)
- msiexec.exe (PID: 2144)
- msiexec.exe (PID: 1760)
- eGovClient.exe (PID: 7064)
Checks supported languages
- NDP472-KB4054530-x86-x64-AllOS-JPN.exe (PID: 4844)
- setup.exe (PID: 1332)
- Setup.exe (PID: 5504)
- msiexec.exe (PID: 3584)
- msiexec.exe (PID: 2144)
- msiexec.exe (PID: 1760)
- eGovClient.exe (PID: 7064)
Checks proxy server information
- setup.exe (PID: 1332)
- msiexec.exe (PID: 1636)
- eGovClient.exe (PID: 7064)
- slui.exe (PID: 6788)
Create files in a temporary directory
- setup.exe (PID: 1332)
- NDP472-KB4054530-x86-x64-AllOS-JPN.exe (PID: 4844)
- Setup.exe (PID: 5504)
- msiexec.exe (PID: 2144)
- msiexec.exe (PID: 1760)
Reads the software policy settings
- setup.exe (PID: 1332)
- msiexec.exe (PID: 1636)
- eGovClient.exe (PID: 7064)
- msiexec.exe (PID: 3584)
- slui.exe (PID: 6788)
Reads the machine GUID from the registry
- setup.exe (PID: 1332)
- NDP472-KB4054530-x86-x64-AllOS-JPN.exe (PID: 4844)
- msiexec.exe (PID: 3584)
- eGovClient.exe (PID: 7064)
Creates files or folders in the user directory
- setup.exe (PID: 1332)
- msiexec.exe (PID: 1636)
- eGovClient.exe (PID: 7064)
Process checks computer location settings
- setup.exe (PID: 1332)
The sample compiled with japanese language support
- NDP472-KB4054530-x86-x64-AllOS-JPN.exe (PID: 4844)
Reads CPU info
- Setup.exe (PID: 5504)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 1636)
Manages system restore points
- SrTasks.exe (PID: 3844)
Creates a software uninstall entry
- msiexec.exe (PID: 3584)
Disables trace logs
- eGovClient.exe (PID: 7064)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:01:20 13:38:50 |
| ZipCRC: | 0x0b73eaa5 |
| ZipCompressedSize: | 1157788 |
| ZipUncompressedSize: | 2544128 |
| ZipFileName: | eGovClientSetup.msi |
Total processes
157
Monitored processes
14
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1296 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\eGovClientSetup_2.1.4.1 (1).zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
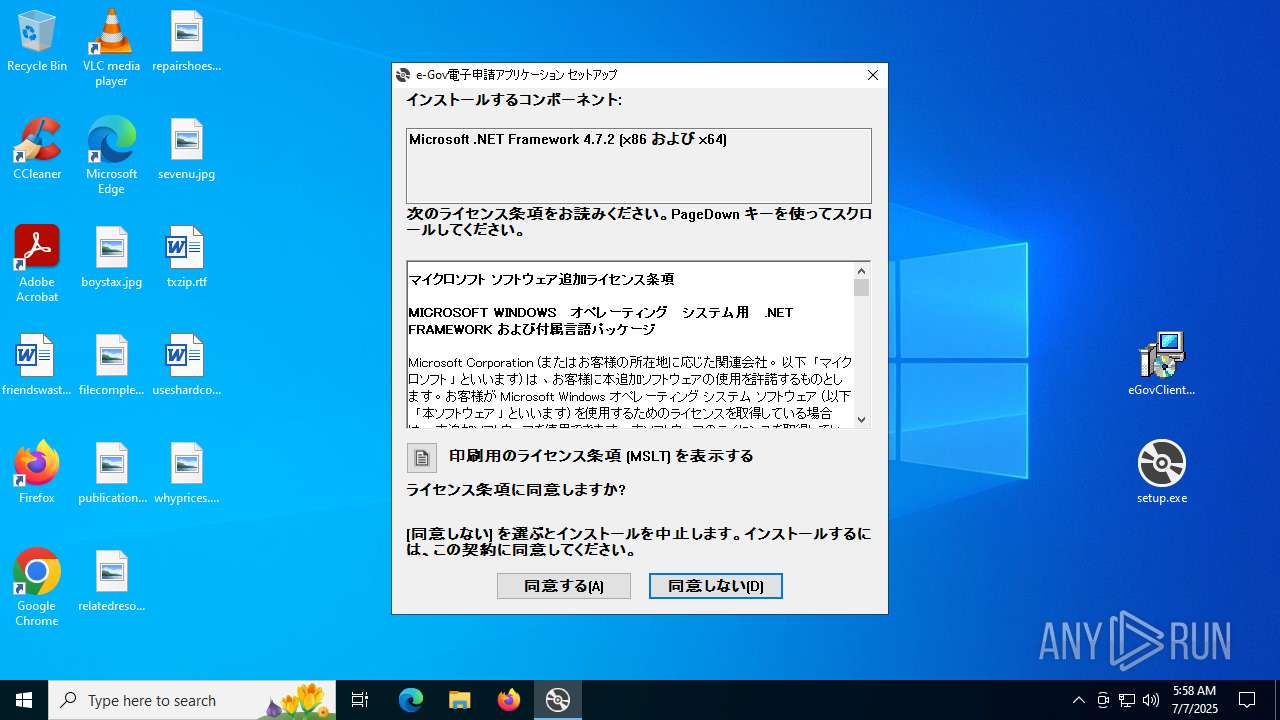
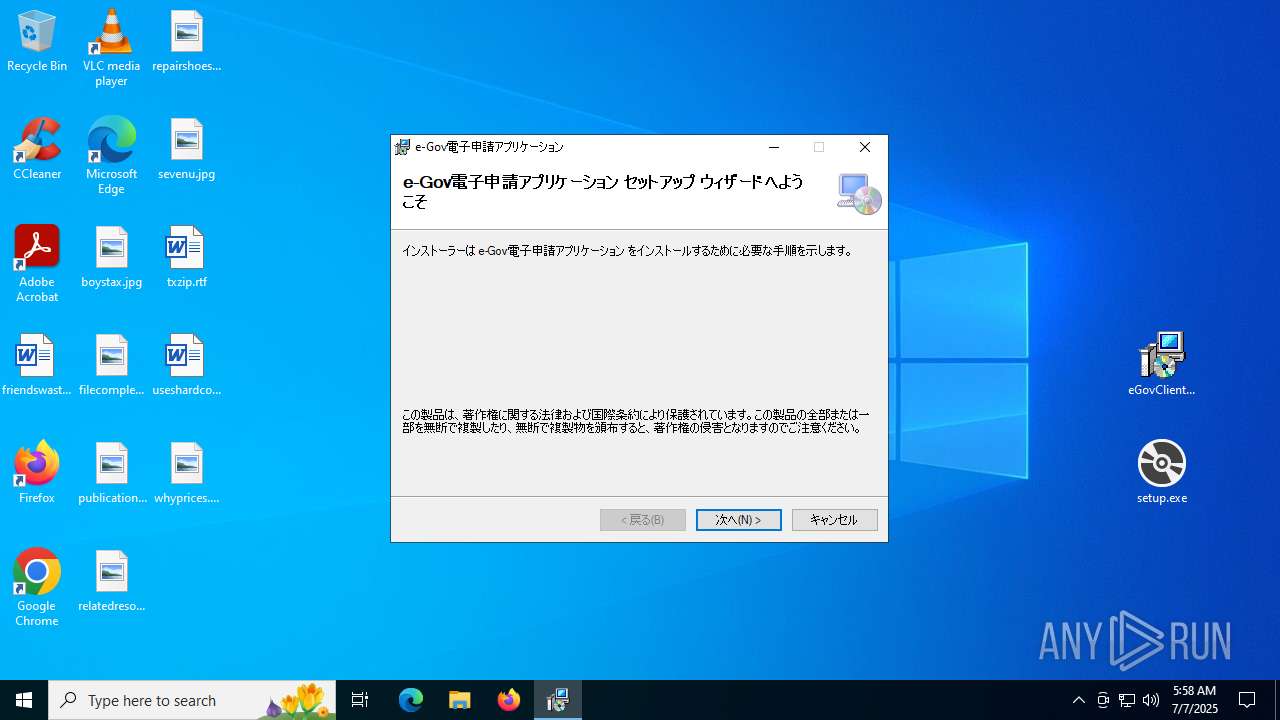
| 1332 | "C:\Users\admin\Desktop\setup.exe" | C:\Users\admin\Desktop\setup.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Setup Exit code: 0 Version: 17.0.35410.144 built by: d17.12 Modules
| |||||||||||||||
| 1336 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1636 | "C:\Windows\SysWOW64\msiexec.exe" -I "C:\Users\admin\Desktop\eGovClientSetup.msi" | C:\Windows\SysWOW64\msiexec.exe | setup.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1740 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1760 | C:\Windows\syswow64\MsiExec.exe -Embedding 81BBFC10A1C4F2D856D3F19EA02EC14E | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2144 | C:\Windows\syswow64\MsiExec.exe -Embedding DF1C088738FE22D0F9CABB07A098B9F8 C | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3584 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
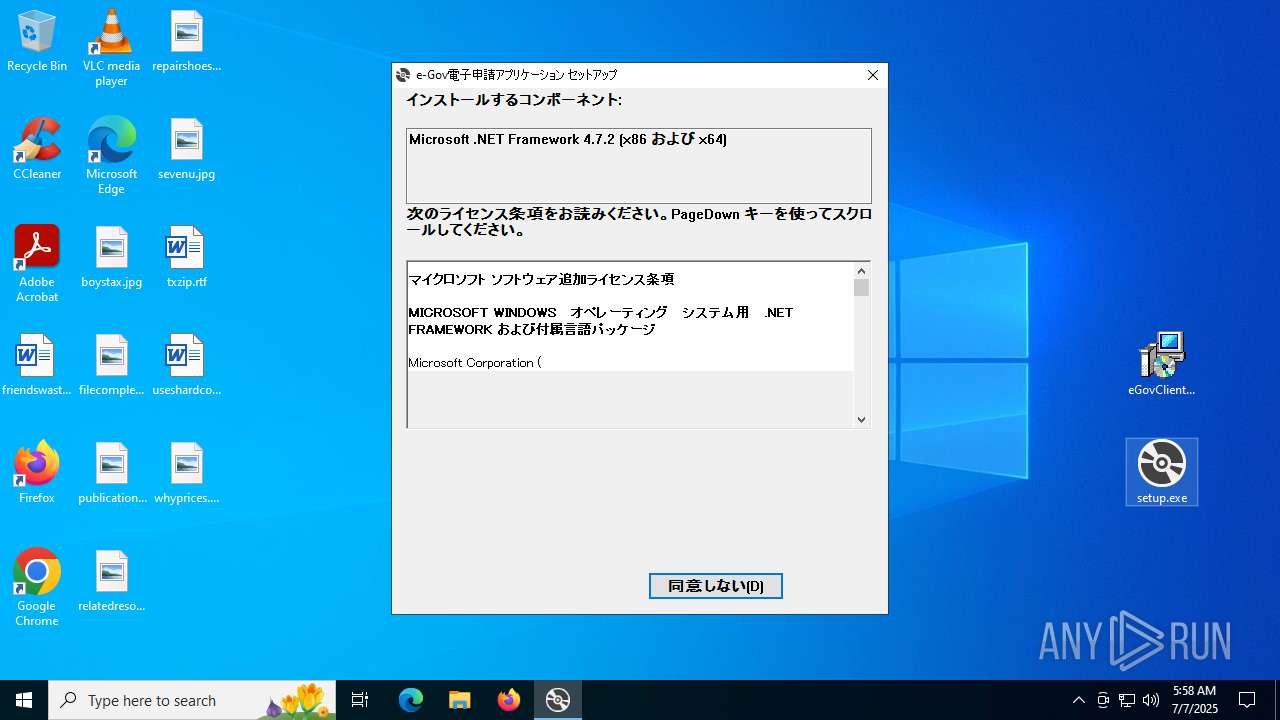
| 3672 | "C:\Users\admin\AppData\Local\Temp\VSD9114.tmp\DotNetFX472\NDP472-KB4054530-x86-x64-AllOS-JPN.exe" /q /norestart /skipenucheck /ChainingPackage FullX64ClickOnce | C:\Users\admin\AppData\Local\Temp\VSD9114.tmp\DotNetFX472\NDP472-KB4054530-x86-x64-AllOS-JPN.exe | — | setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Framework 4.7.2 (JPN) Setup Exit code: 3221226540 Version: 4.7.03062.00 Modules
| |||||||||||||||
| 3844 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Windows System Protection background tasks. Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
18 227
Read events
17 901
Write events
309
Delete events
17
Modification events
| (PID) Process: | (1296) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (1296) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (1296) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (1296) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\eGovClientSetup_2.1.4.1 (1).zip | |||
| (PID) Process: | (1296) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1296) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1296) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1296) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1296) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (1296) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
Executable files
21
Suspicious files
41
Text files
63
Unknown types
13
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4844 | NDP472-KB4054530-x86-x64-AllOS-JPN.exe | C:\2150f0d1662aefb63796\x64-Windows10.0-KB4054604-x64.cab | — | |
MD5:— | SHA256:— | |||
| 4844 | NDP472-KB4054530-x86-x64-AllOS-JPN.exe | C:\2150f0d1662aefb63796\x64-Windows10.0-KB4073134-x64.cab | — | |
MD5:— | SHA256:— | |||
| 1296 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1296.18713\eGovClientSetup.msi | executable | |
MD5:225EBF3465644C8B5269FB26EFE2BFD7 | SHA256:F89321A497C0D056ACF1C4AA4A1069DD1613822C539FFE62BE374533D71AC2C9 | |||
| 1332 | setup.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\26C212D9399727259664BDFCA073966E_F9F7D6A7ECE73106D2A8C63168CDA10D | binary | |
MD5:7FB190242C617197D474A9E82248E041 | SHA256:5ACE742228D554BC788BE338C8E40DAD35CE300BE93C2EA129D3957CF36F0981 | |||
| 1332 | setup.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\26C212D9399727259664BDFCA073966E_F9F7D6A7ECE73106D2A8C63168CDA10D | binary | |
MD5:7BB26CCF97A8BF5FA9C3A97863B643EB | SHA256:86DBAA33E4B861FE628D59D91999551B3DF359833C536CFA8FC58B2819C0864C | |||
| 1332 | setup.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\37C951188967C8EB88D99893D9D191FE | binary | |
MD5:C5A9A1FA545DCE16C7D97383A65C39EB | SHA256:07E7EAD940146E6DFD309CB85728721246E8A2586D1BC0C4D8B697A68B2EDA3A | |||
| 1296 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1296.18713\setup.exe | executable | |
MD5:6A495B84743F6DA931E341B109B6CE81 | SHA256:613B6E9722009D49A5625A79F9D7CADB781BD591F834B3310ACFCC49750BDFA0 | |||
| 4844 | NDP472-KB4054530-x86-x64-AllOS-JPN.exe | C:\2150f0d1662aefb63796\watermark.bmp | image | |
MD5:B0075CEE80173D764C0237E840BA5879 | SHA256:AB18374B3AAB10E5979E080D0410579F9771DB888BA1B80A5D81BA8896E2D33A | |||
| 1332 | setup.exe | C:\Users\admin\AppData\Local\Temp\VSD9114.tmp\setup.exe | executable | |
MD5:6A495B84743F6DA931E341B109B6CE81 | SHA256:613B6E9722009D49A5625A79F9D7CADB781BD591F834B3310ACFCC49750BDFA0 | |||
| 4844 | NDP472-KB4054530-x86-x64-AllOS-JPN.exe | C:\2150f0d1662aefb63796\Graphics\Rotate10.ico | image | |
MD5:0CCA04A3468575FDCEFEE9957E32F904 | SHA256:B94E68C711B3B06D9A63C80AD013C7C7BBDB5F8E82CBC866B246FF22D99B03FE | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
15
TCP/UDP connections
44
DNS requests
28
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6876 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1332 | setup.exe | GET | 302 | 95.100.186.9:80 | http://go.microsoft.com/fwlink/?LinkId=863258&clcid=0x411 | unknown | — | — | whitelisted |
1332 | setup.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicCodSigPCA2011_2011-07-08.crl | unknown | — | — | whitelisted |
1332 | setup.exe | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6812 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6812 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1636 | msiexec.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | — | — | whitelisted |
1636 | msiexec.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEAgEKqp9xdPHfTCgZY3shsY%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6492 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1268 | svchost.exe | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
6876 | svchost.exe | 40.126.32.138:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6876 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
download.visualstudio.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
Setup.exe | The operation completed successfully.
|