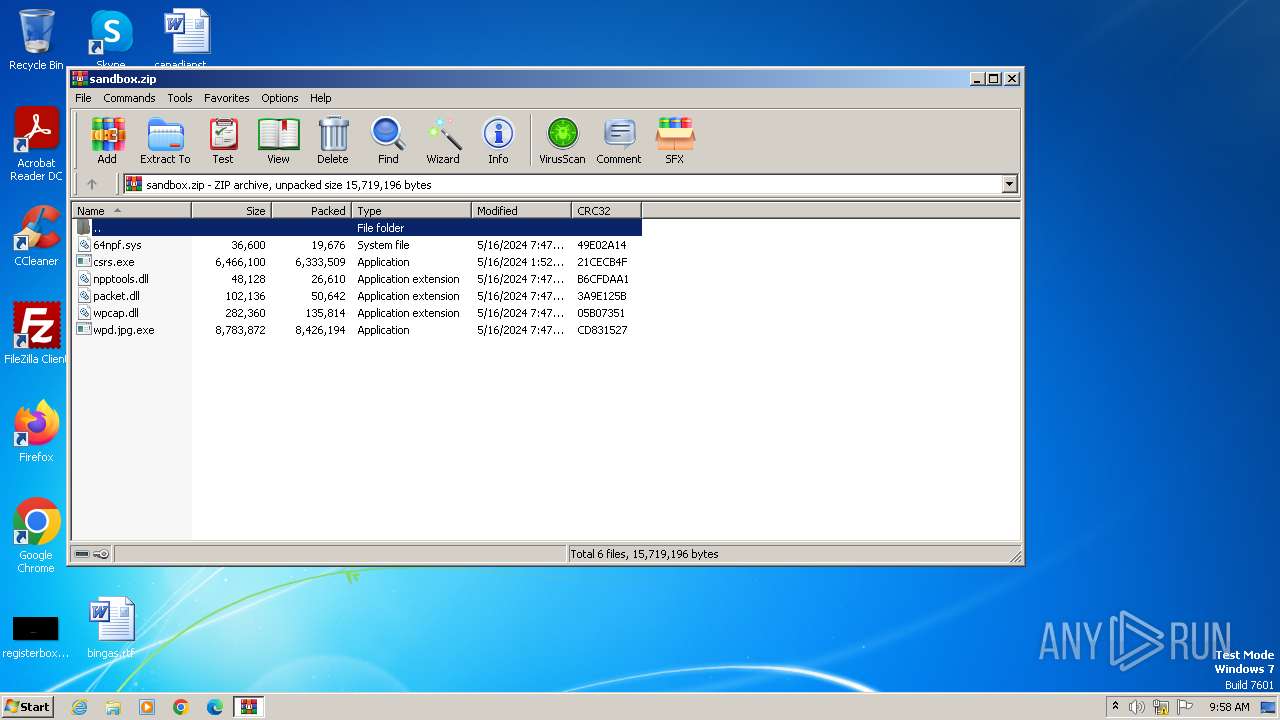
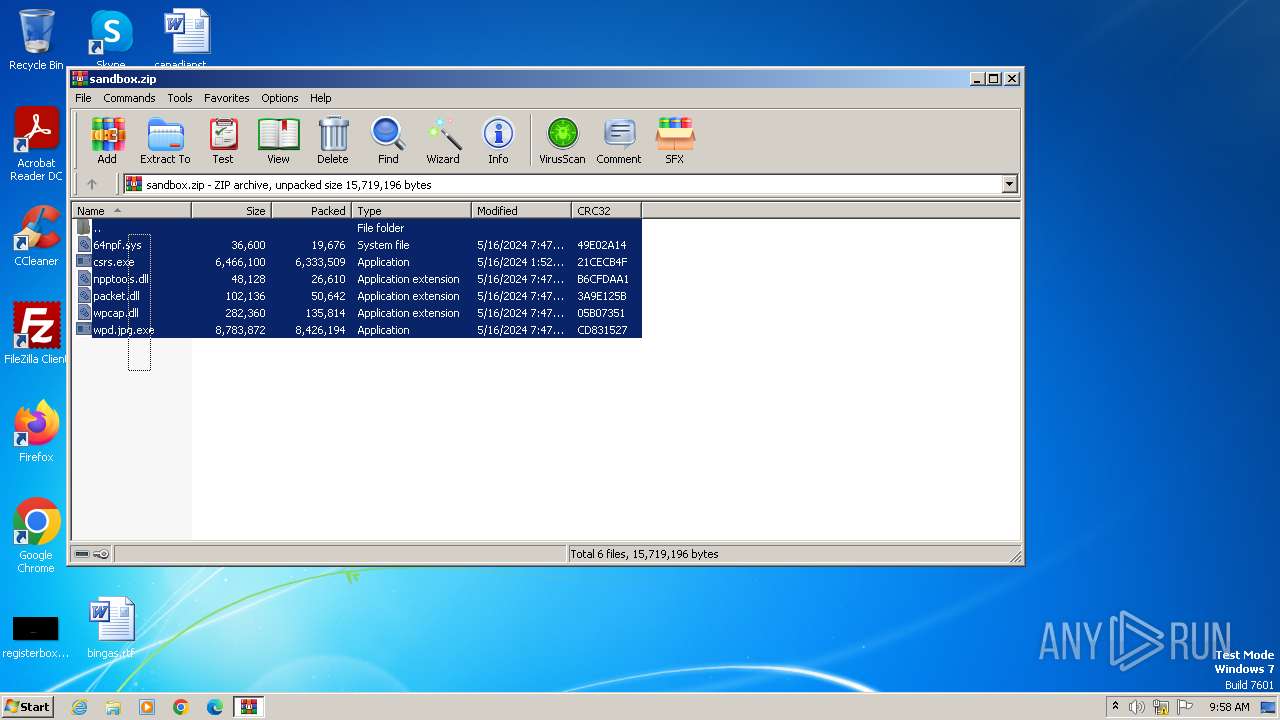
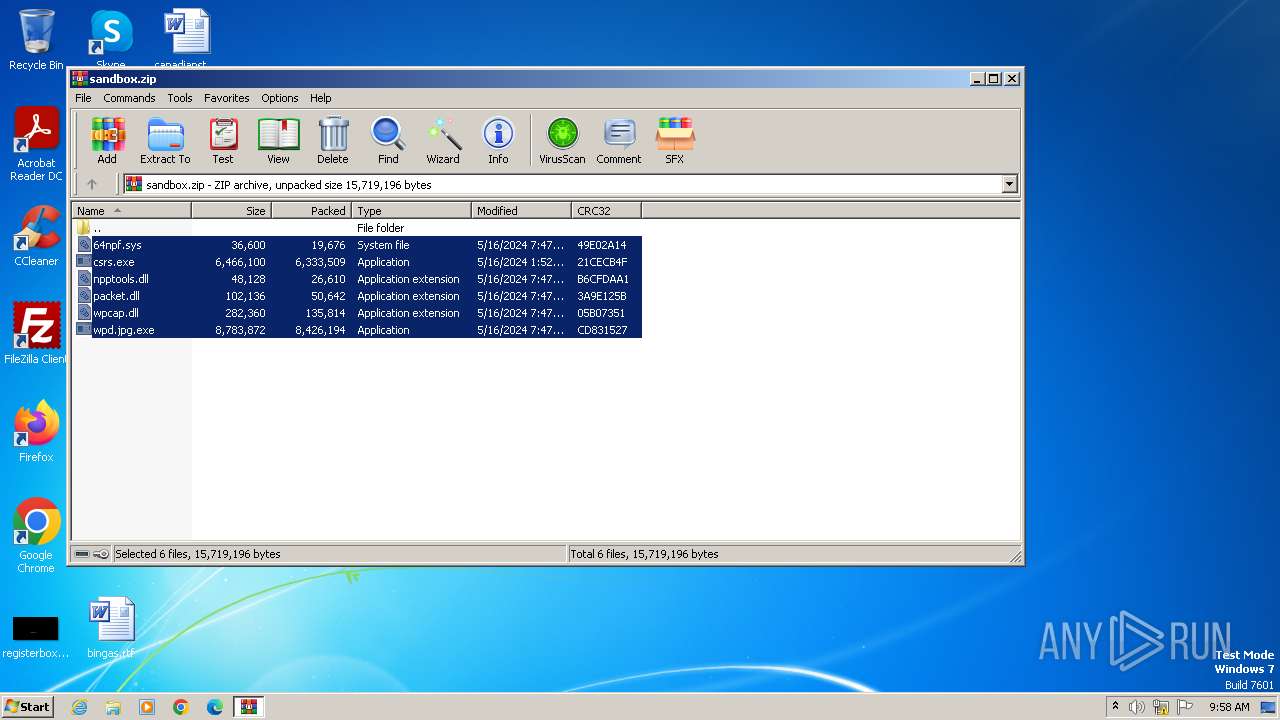
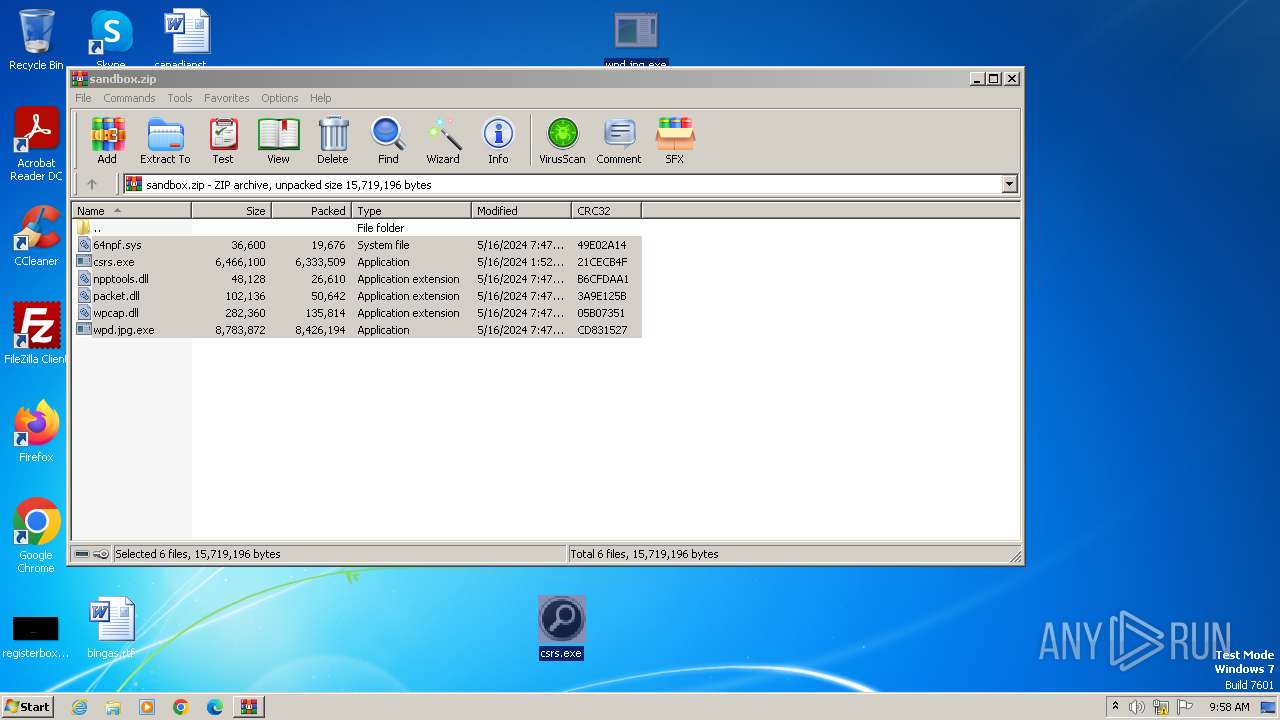
| File name: | sandbox.zip |
| Full analysis: | https://app.any.run/tasks/416aa2c6-dfa1-4c37-81e1-6d9bc765b794 |
| Verdict: | Malicious activity |
| Analysis date: | May 16, 2024, 08:58:08 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 97F16BD2A294002514CDEDA39CD80D88 |
| SHA1: | C7BABE683B0AEE3D4BFE75E1E68286542C4F23CA |
| SHA256: | F2C50DEFBDDD8A81FEAF36C4F6D354FE4AD7A5A3321605551D39485B4E13CCF1 |
| SSDEEP: | 196608:H8YmtLmXw71+H7u43x2CCaztlfjp6PzLo0n:cNgXQ1+bj3xbLzXfwPln |
MALICIOUS
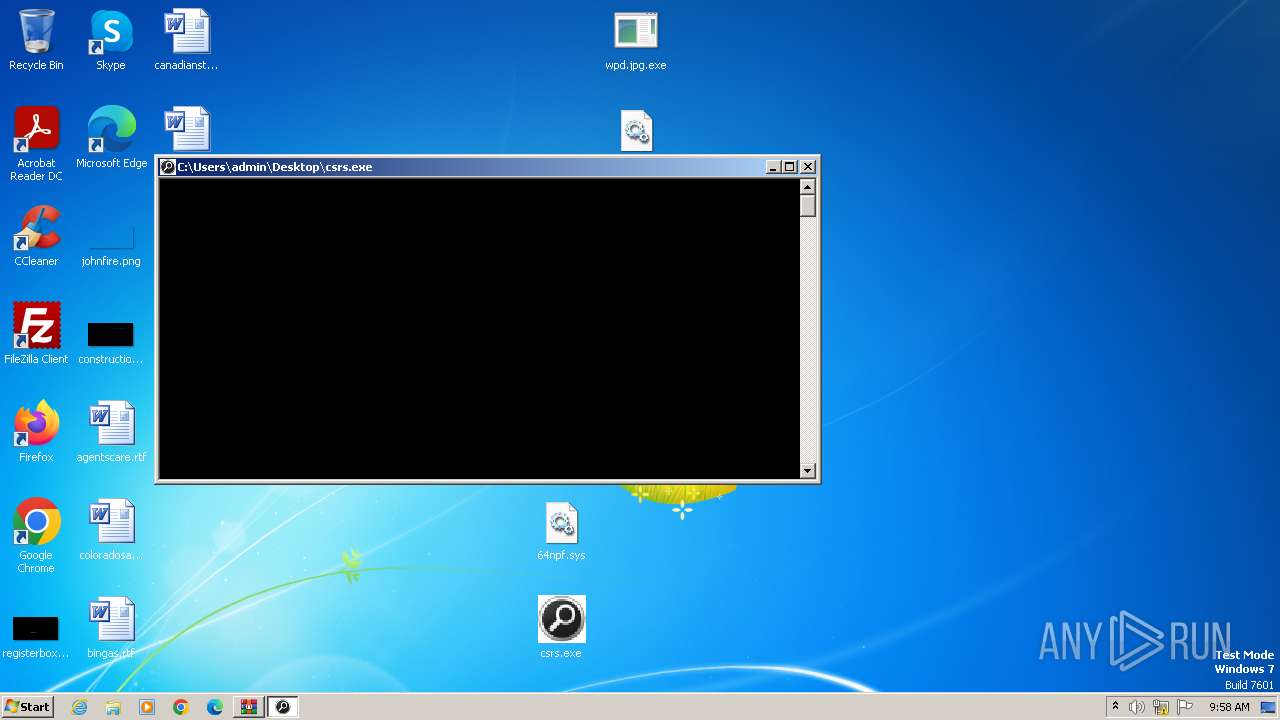
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3972)
- csrs.exe (PID: 4084)
- csrs.exe (PID: 2936)
Starts NET.EXE for service management
- net.exe (PID: 764)
- cmd.exe (PID: 728)
Starts SC.EXE for service management
- cmd.exe (PID: 728)
SUSPICIOUS
Drops a system driver (possible attempt to evade defenses)
- WinRAR.exe (PID: 3972)
Starts CMD.EXE for commands execution
- wpd.jpg.exe (PID: 1036)
Process drops legitimate windows executable
- WinRAR.exe (PID: 3972)
- csrs.exe (PID: 2936)
- csrs.exe (PID: 4084)
Starts a Microsoft application from unusual location
- csrs.exe (PID: 4084)
- csrs.exe (PID: 2936)
- csrs.exe (PID: 2968)
- csrs.exe (PID: 928)
Executable content was dropped or overwritten
- csrs.exe (PID: 4084)
- csrs.exe (PID: 2936)
Process drops python dynamic module
- csrs.exe (PID: 4084)
- csrs.exe (PID: 2936)
Starts SC.EXE for service management
- cmd.exe (PID: 112)
- cmd.exe (PID: 728)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 112)
- cmd.exe (PID: 2552)
Reads security settings of Internet Explorer
- wpd.jpg.exe (PID: 1036)
Reads the Internet Settings
- wpd.jpg.exe (PID: 1036)
Connects to the server without a host name
- wpd.jpg.exe (PID: 1036)
The process drops C-runtime libraries
- csrs.exe (PID: 2936)
- csrs.exe (PID: 4084)
Application launched itself
- csrs.exe (PID: 2936)
- csrs.exe (PID: 4084)
Connects to unusual port
- wpd.jpg.exe (PID: 1036)
INFO
Checks supported languages
- wpd.jpg.exe (PID: 1036)
- csrs.exe (PID: 4084)
- csrs.exe (PID: 2936)
- csrs.exe (PID: 2968)
- wmpnscfg.exe (PID: 1812)
- csrs.exe (PID: 928)
Manual execution by a user
- wpd.jpg.exe (PID: 1036)
- csrs.exe (PID: 4084)
- wmpnscfg.exe (PID: 1812)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3972)
Create files in a temporary directory
- csrs.exe (PID: 4084)
- csrs.exe (PID: 2936)
Reads the computer name
- wpd.jpg.exe (PID: 1036)
- wmpnscfg.exe (PID: 1812)
- csrs.exe (PID: 2968)
Creates files or folders in the user directory
- wpd.jpg.exe (PID: 1036)
Checks proxy server information
- wpd.jpg.exe (PID: 1036)
Reads the machine GUID from the registry
- wpd.jpg.exe (PID: 1036)
- csrs.exe (PID: 2968)
- csrs.exe (PID: 928)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:05:16 14:47:50 |
| ZipCRC: | 0x49e02a14 |
| ZipCompressedSize: | 19676 |
| ZipUncompressedSize: | 36600 |
| ZipFileName: | 64npf.sys |
Total processes
60
Monitored processes
21
Malicious processes
4
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 112 | C:\Windows\system32\cmd.exe /c taskkill /f /im csrs.exe&sc start netprofm&sc config netprofm start= auto&sc start NlaSvc&sc config NlaSvc start= auto | C:\Windows\System32\cmd.exe | — | wpd.jpg.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 5 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 304 | sc config NlaSvc start= auto | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: A tool to aid in developing services for WindowsNT Exit code: 5 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 588 | sc stop 1MpsSvc | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: A tool to aid in developing services for WindowsNT Exit code: 1060 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 728 | C:\Windows\system32\cmd.exe /c net stop WinNsaSrv&sc config WinNsaSrv start= disabled&sc1 stop sharedaccess&sc stop 1MpsSvc&sc config 1MpsSvc start= disabled&del *.log | C:\Windows\System32\cmd.exe | — | wpd.jpg.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 764 | net stop WinNsaSrv | C:\Windows\System32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 928 | "C:\Users\admin\Desktop\csrs.exe" | C:\Users\admin\Desktop\csrs.exe | — | csrs.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Editor Exit code: 4294967295 Version: 1.0.0.1 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1036 | "C:\Users\admin\Desktop\wpd.jpg.exe" | C:\Users\admin\Desktop\wpd.jpg.exe | explorer.exe | ||||||||||||
User: admin Company: Microl office Integrity Level: MEDIUM Description: Microl office Version: 1.0.0.2 Modules
| |||||||||||||||
| 1060 | C:\Windows\system32\net1 stop WinNsaSrv | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1592 | sc config 1MpsSvc start= disabled | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: A tool to aid in developing services for WindowsNT Exit code: 1060 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1756 | sc start NlaSvc | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: A tool to aid in developing services for WindowsNT Exit code: 1056 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
5 005
Read events
4 957
Write events
42
Delete events
6
Modification events
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\sandbox.zip | |||
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
54
Suspicious files
1
Text files
29
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3972 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3972.23014\packet.dll | executable | |
MD5:2CE150705BBEB30E6C8059CC530043AA | SHA256:CD9F4FB077C25013226E0883F9AE02E9CED9B71F07637081E55AE70FD0788F29 | |||
| 4084 | csrs.exe | C:\Users\admin\AppData\Local\Temp\_MEI40842\Crypto.Cipher._DES3.pyd | executable | |
MD5:71932C03533A6057002F10428F7F8722 | SHA256:D38A00DEA7B92A9D07ECB612D843AF0EF4A5EC278B36F68E404C4208253C2F95 | |||
| 3972 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3972.23014\wpd.jpg.exe | executable | |
MD5:1BFE19A314DD31D6ADDA302F177C3B7C | SHA256:B63CE450E4D34D1CDD727A1A246D38167F45AEACC69D15C6922EF723E49A3CF7 | |||
| 4084 | csrs.exe | C:\Users\admin\AppData\Local\Temp\_MEI40842\Crypto.Cipher._DES.pyd | executable | |
MD5:E2A21659FD3EEF7EB6F5874EA739E7E1 | SHA256:25F3DEE17035FD025FE73D7C17173FAF9EBCC7E165687C05DB197D7B5F4A7D04 | |||
| 3972 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3972.23014\csrs.exe | executable | |
MD5:ED43F6043F51FBA6B2A8A4062256154D | SHA256:A62C67BB2C90D79FFC64D3862C73EA77255581D224A8736C470DC72A6716C6E3 | |||
| 3972 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3972.23014\64npf.sys | executable | |
MD5:DE7FCC77F4A503AF4CA6A47D49B3713D | SHA256:4BFAA99393F635CD05D91A64DE73EDB5639412C129E049F0FE34F88517A10FC6 | |||
| 4084 | csrs.exe | C:\Users\admin\AppData\Local\Temp\_MEI40842\Crypto.Hash._SHA256.pyd | executable | |
MD5:859E18B29A1544F759D631269E4695E4 | SHA256:DA276F0283FA02FD3A128EC37F7CCD2C51AD50A98750259ECC2E06F588F161AC | |||
| 4084 | csrs.exe | C:\Users\admin\AppData\Local\Temp\_MEI40842\Crypto.Cipher._ARC4.pyd | executable | |
MD5:0895172AA8600E924753837C17228DD3 | SHA256:54C3303ECF28BFC90342BE4FB3E936B0E5E5DB701E35115EDDB3F428DD65355C | |||
| 4084 | csrs.exe | C:\Users\admin\AppData\Local\Temp\_MEI40842\Crypto.Hash._MD4.pyd | executable | |
MD5:8F892DD81E95D2EB665664BEC25A81C0 | SHA256:E9E7192BE4D2E97CF4C5079FB1CA6452513FCCDD822ABDF1AD9C189B33EEC026 | |||
| 3972 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3972.23014\wpcap.dll | executable | |
MD5:4633B298D57014627831CCAC89A2C50B | SHA256:B967E4DCE952F9232592E4C1753516081438702A53424005642700522055DBC9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
1 757
DNS requests
0
Threats
11
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1036 | wpd.jpg.exe | GET | 200 | 104.37.187.182:80 | http://104.37.187.182/xpxmr.txt | unknown | — | — | unknown |
1036 | wpd.jpg.exe | GET | 200 | 104.37.187.182:80 | http://104.37.187.182/wpdmd5.txt | unknown | — | — | unknown |
1036 | wpd.jpg.exe | GET | 200 | 104.37.187.182:80 | http://104.37.187.182/ver.txt | unknown | — | — | unknown |
1036 | wpd.jpg.exe | GET | 200 | 104.37.187.182:80 | http://104.37.187.182/shellver.txt | unknown | — | — | unknown |
1036 | wpd.jpg.exe | GET | 200 | 104.37.187.182:80 | http://104.37.187.182/xpxmr.txt | unknown | — | — | unknown |
1036 | wpd.jpg.exe | GET | 200 | 104.37.187.182:80 | http://104.37.187.182/ok/wpd.html | unknown | — | — | unknown |
1036 | wpd.jpg.exe | GET | 200 | 104.37.187.182:80 | http://104.37.187.182/wpdmd5.txt | unknown | — | — | unknown |
1036 | wpd.jpg.exe | GET | 200 | 104.37.187.182:80 | http://104.37.187.182/wpdtest.txt | unknown | — | — | unknown |
1036 | wpd.jpg.exe | GET | 200 | 104.37.187.182:80 | http://104.37.187.182/ok/wpd.html | unknown | — | — | unknown |
1036 | wpd.jpg.exe | GET | — | 104.37.187.182:80 | http://104.37.187.182/wpdtest.txt | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
1036 | wpd.jpg.exe | 104.37.187.182:80 | — | IS-AS-1 | US | unknown |
1036 | wpd.jpg.exe | 192.168.100.2:1433 | — | — | — | whitelisted |
1036 | wpd.jpg.exe | 192.168.100.1:1433 | — | — | — | unknown |
1036 | wpd.jpg.exe | 192.168.100.1:445 | — | — | — | unknown |
1036 | wpd.jpg.exe | 192.168.100.2:445 | — | — | — | whitelisted |
1036 | wpd.jpg.exe | 192.168.101.2:1433 | — | — | — | unknown |
1036 | wpd.jpg.exe | 192.168.101.3:1433 | — | — | — | unknown |
DNS requests
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Device Retrieving External IP Address Detected | SUSPICIOUS [ANY.RUN] Received IP address from server as result of HTTP request |
— | — | Device Retrieving External IP Address Detected | SUSPICIOUS [ANY.RUN] Received IP address from server as result of HTTP request |
1036 | wpd.jpg.exe | Misc activity | ET SCAN Behavioral Unusual Port 1433 traffic Potential Scan or Infection |
— | — | Misc activity | ET SCAN Behavioral Unusual Port 445 traffic Potential Scan or Infection |
1036 | wpd.jpg.exe | Misc activity | ET SCAN Behavioral Unusual Port 1433 traffic Potential Scan or Infection |
— | — | Misc activity | ET SCAN Behavioral Unusual Port 445 traffic Potential Scan or Infection |
— | — | Device Retrieving External IP Address Detected | SUSPICIOUS [ANY.RUN] Received IP address from server as result of HTTP request |
1036 | wpd.jpg.exe | Misc activity | ET SCAN Behavioral Unusual Port 1433 traffic Potential Scan or Infection |
— | — | Misc activity | ET SCAN Behavioral Unusual Port 445 traffic Potential Scan or Infection |
1036 | wpd.jpg.exe | Misc activity | ET SCAN Behavioral Unusual Port 1433 traffic Potential Scan or Infection |