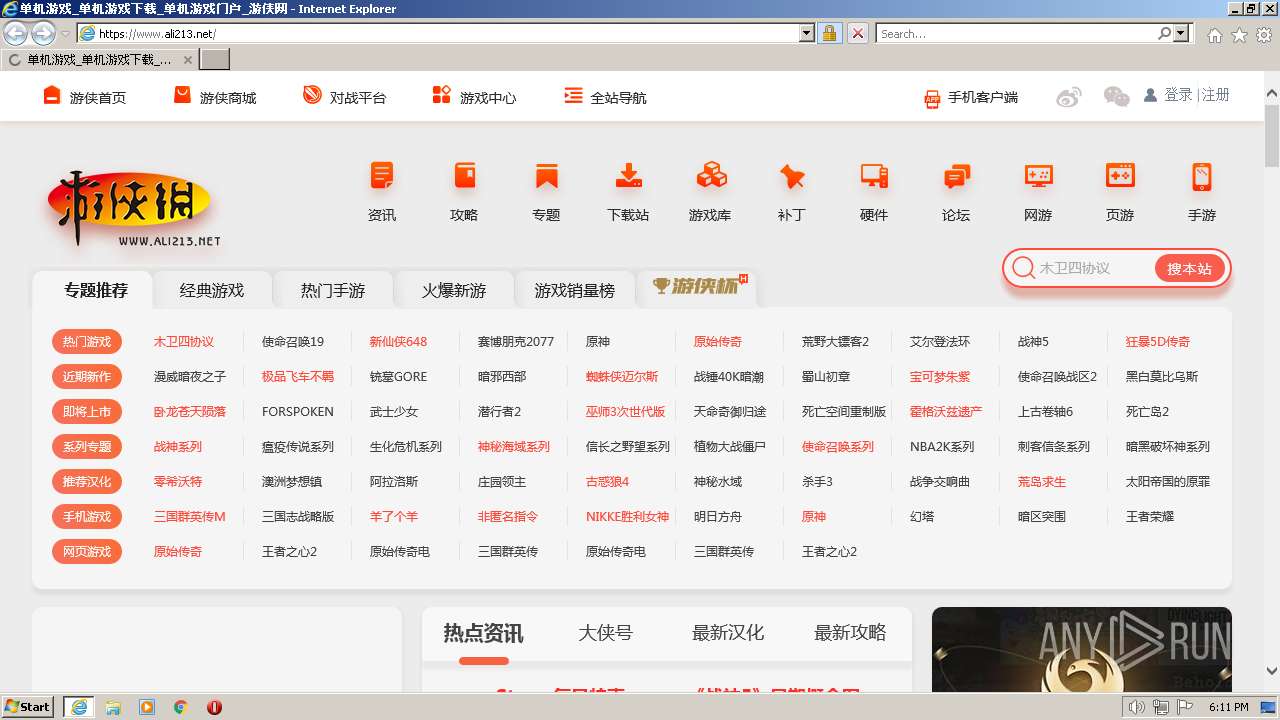
| URL: | https://www.ali213.net/ |
| Full analysis: | https://app.any.run/tasks/3794c549-83a4-47cb-8d9d-063497783fa6 |
| Verdict: | Malicious activity |
| Analysis date: | December 05, 2022, 18:11:04 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 8895E0B2261F817B0AF511BC47A029D7 |
| SHA1: | 65F5CED2EDB0B3E59D0FCFCC0A7EB8161854D2F3 |
| SHA256: | F2C40D3110DC1EF9CEE37A6B07BB8FEB7E2317AF969A0AF56629A9DCA2783CAD |
| SSDEEP: | 3:N8DSLJDLz:2OL5X |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Application launched itself
- iexplore.exe (PID: 1580)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
35
Monitored processes
2
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 404 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1580 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1580 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://www.ali213.net/" | C:\Program Files\Internet Explorer\iexplore.exe | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
14 255
Read events
14 140
Write events
115
Delete events
0
Modification events
| (PID) Process: | (1580) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (1580) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (1580) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31000788 | |||
| (PID) Process: | (1580) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 101587206 | |||
| (PID) Process: | (1580) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31000789 | |||
| (PID) Process: | (1580) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1580) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1580) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1580) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (1580) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
0
Suspicious files
14
Text files
50
Unknown types
11
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 404 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 1580 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_1DC6D7385EA816C957BA2B715AC5C442 | binary | |
MD5:— | SHA256:— | |||
| 404 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B398B80134F72209547439DB21AB308D_D14B79B440CDC26D7D21C81855E2C04D | binary | |
MD5:— | SHA256:— | |||
| 1580 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_1DC6D7385EA816C957BA2B715AC5C442 | der | |
MD5:— | SHA256:— | |||
| 404 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B398B80134F72209547439DB21AB308D_D14B79B440CDC26D7D21C81855E2C04D | der | |
MD5:— | SHA256:— | |||
| 404 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\ali-sso-pc-global-version-1[1].js | html | |
MD5:— | SHA256:— | |||
| 404 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\A703EA3C7C94B2431D59916C8740791D | der | |
MD5:— | SHA256:— | |||
| 404 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\index[1].js | text | |
MD5:— | SHA256:— | |||
| 1580 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\favicon[1].ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
| 404 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\jquery-1.8.3.min[1].js | text | |
MD5:3576A6E73C9DCCDBBC4A2CF8FF544AD7 | SHA256:61C6CAEBD23921741FB5FFE6603F16634FCA9840C2BF56AC8201E9264D6DACCF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
48
DNS requests
22
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
404 | iexplore.exe | GET | 200 | 172.64.155.188:80 | http://ocsp.sectigo.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRDC9IOTxN6GmyRjyTl2n4yTUczyAQUjYxexFStiuF36Zv5mwXhuAGNYeECEQCrg2GmcjJBlWFgo9R1F0x3 | US | der | 472 b | whitelisted |
— | — | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ5rEWLwbJFq%2FmAU80sm7E%3D | US | der | 471 b | whitelisted |
— | — | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSXi0cW5bD2WLrmnasWibg2OuPDpgQUVXRPsnJP9WC6UNHX5lFcmgGHGtcCEAbwcvwdRzLBvyjSLBPpVh0%3D | US | der | 471 b | whitelisted |
404 | iexplore.exe | GET | 200 | 101.198.193.5:80 | http://ocsp.crlocsp.cn/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQVV5D4a5Xuqta%2F7ArmfD0qkrlxDwQUDUmPFTN7wE%2B2%2Bzo4Cfw0Fdpg3RQCEBzdwoZzHA3jQeqlr4j1wzw%3D | CN | der | 471 b | suspicious |
404 | iexplore.exe | GET | 200 | 172.64.155.188:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEB0IKVQ4TL90r2m5kRab8C0%3D | US | der | 2.18 Kb | whitelisted |
404 | iexplore.exe | GET | 200 | 172.64.155.188:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | US | der | 2.18 Kb | whitelisted |
404 | iexplore.exe | GET | 200 | 172.64.155.188:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | US | der | 1.42 Kb | whitelisted |
1580 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
404 | iexplore.exe | GET | 200 | 172.64.155.188:80 | http://ocsp.usertrust.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEQDVbiRslO1jq7FG78GWtk%2Bw | US | der | 2.18 Kb | whitelisted |
1580 | iexplore.exe | GET | 200 | 23.216.77.80:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?d2691ac2c2cbac57 | US | compressed | 4.70 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
404 | iexplore.exe | 45.248.8.106:443 | web.ali213.net | CHINATELECOM JiangSu YangZhou IDC networkdescr: YangZhouJiangsu Province, P.R.China. | CN | unknown |
— | — | 93.184.220.29:80 | ocsp.digicert.com | EDGECAST | GB | whitelisted |
404 | iexplore.exe | 47.103.42.25:443 | v.trustutn.org | Hangzhou Alibaba Advertising Co.,Ltd. | CN | unknown |
1580 | iexplore.exe | 13.107.22.200:443 | www.bing.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1580 | iexplore.exe | 131.253.33.200:443 | www.bing.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1580 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | EDGECAST | GB | whitelisted |
1580 | iexplore.exe | 23.216.77.80:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | suspicious |
404 | iexplore.exe | 103.215.36.235:443 | pbmp.ali213.net | China Mobile communications corporation | CN | unknown |
404 | iexplore.exe | 114.55.58.152:443 | i.ali213.net | Hangzhou Alibaba Advertising Co.,Ltd. | CN | unknown |
404 | iexplore.exe | 60.12.147.52:443 | static.ali213.net | CHINA UNICOM China169 Backbone | CN | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
dns.msftncsi.com |
| shared |
ocsp.digicert.com |
| whitelisted |
static.ali213.net |
| unknown |
web.ali213.net |
| suspicious |
aqyzmedia.yunaq.com |
| suspicious |
v.trustutn.org |
| unknown |
ocsp.usertrust.com |
| whitelisted |