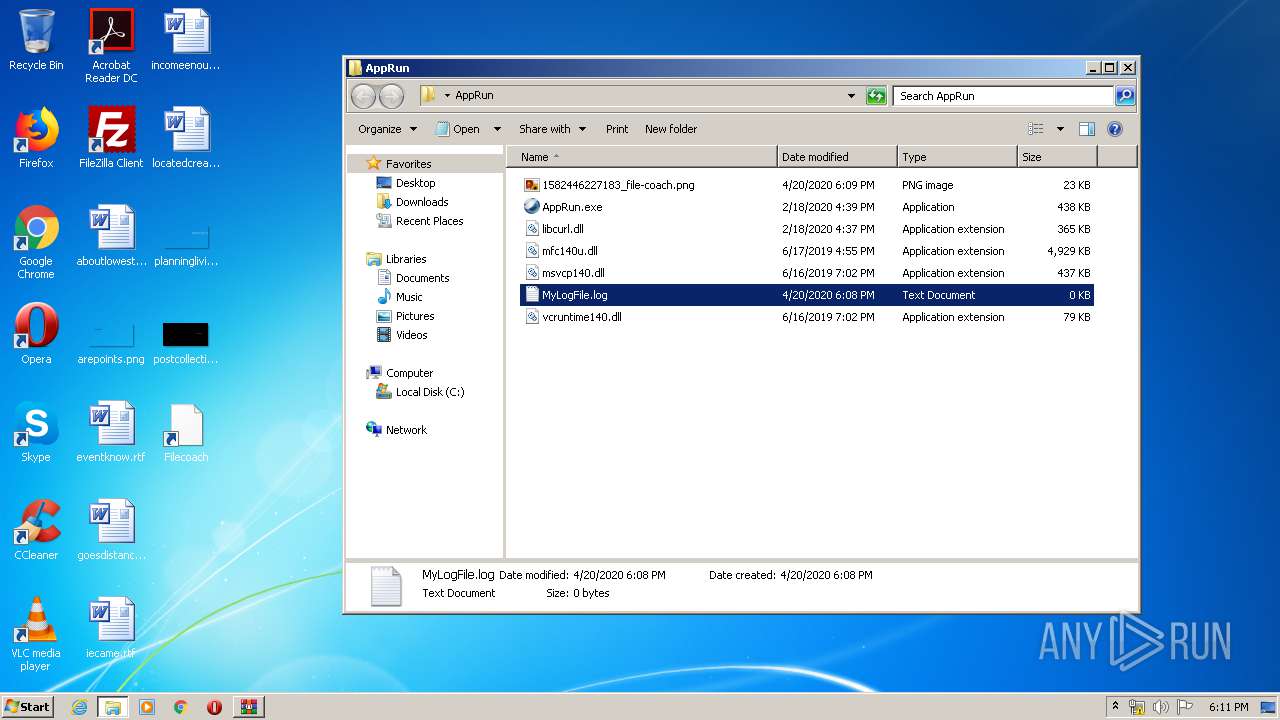
| File name: | AppRun.zip |
| Full analysis: | https://app.any.run/tasks/75621cc6-dade-4d13-8ae6-c76a0a5ca95e |
| Verdict: | Malicious activity |
| Analysis date: | April 20, 2020, 17:08:13 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 72278D837CD3A071A1F5402FA1C2D0D0 |
| SHA1: | D38F7946AC39E1F12B23B826138BCB93AF633DED |
| SHA256: | F2B77BB384E2B97979EAEFD6E305335DF7CC55A3EFC61C7FC6AA8BD8B9B33DE8 |
| SSDEEP: | 49152:1HctqXC3qK6kru5Zru3UAaRCjAm9qr2KsK2l+ONs4CTHHBrLaNb+wdNFhpVeecXp:1HsEC3qK6kru5Bu3UAaRCjAmcrV2kOv8 |
MALICIOUS
Loads dropped or rewritten executable
- AppRun.exe (PID: 2624)
- SearchProtocolHost.exe (PID: 744)
- AppRun.exe (PID: 2932)
Application was dropped or rewritten from another process
- AppRun.exe (PID: 2624)
- AppRun.exe (PID: 2932)
SUSPICIOUS
Creates files in the user directory
- AppRun.exe (PID: 2932)
Executable content was dropped or overwritten
- AppRun.exe (PID: 2624)
- AppRun.exe (PID: 2932)
Executed via COM
- DllHost.exe (PID: 1520)
INFO
Manual execution by user
- AppRun.exe (PID: 2932)
- AppRun.exe (PID: 2624)
- NOTEPAD.EXE (PID: 3404)
Dropped object may contain Bitcoin addresses
- AppRun.exe (PID: 2932)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2020:04:20 12:00:27 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | AppRun/ |
Total processes
47
Monitored processes
6
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 744 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe5_ Global\UsGthrCtrlFltPipeMssGthrPipe5 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1520 | C:\Windows\system32\DllHost.exe /Processid:{76D0CB12-7604-4048-B83C-1005C7DDC503} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
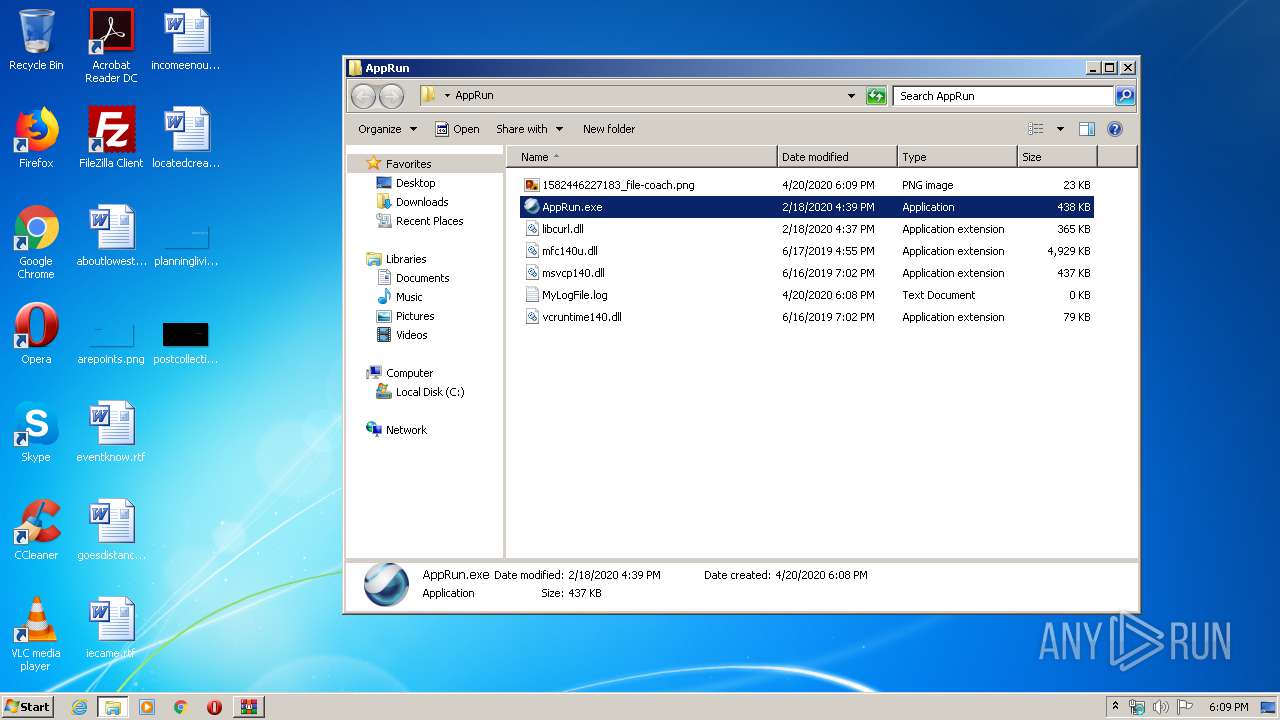
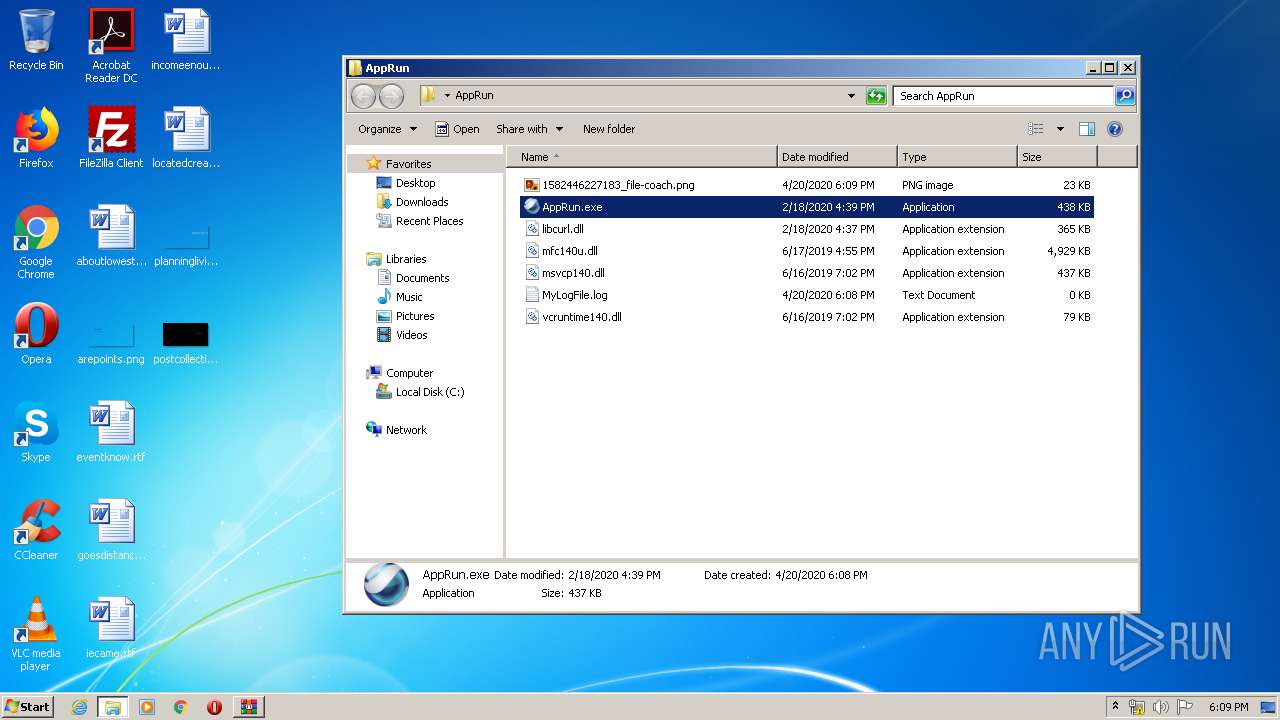
| 2624 | "C:\Users\admin\Desktop\AppRun\AppRun.exe" | C:\Users\admin\Desktop\AppRun\AppRun.exe | explorer.exe | ||||||||||||
User: admin Company: TODO: <Company name> Integrity Level: MEDIUM Description: AppRun Exit code: 0 Version: 1.0.0.2 Modules
| |||||||||||||||
| 2932 | "C:\Users\admin\Desktop\AppRun\AppRun.exe" | C:\Users\admin\Desktop\AppRun\AppRun.exe | explorer.exe | ||||||||||||
User: admin Company: TODO: <Company name> Integrity Level: MEDIUM Description: AppRun Exit code: 0 Version: 1.0.0.2 Modules
| |||||||||||||||
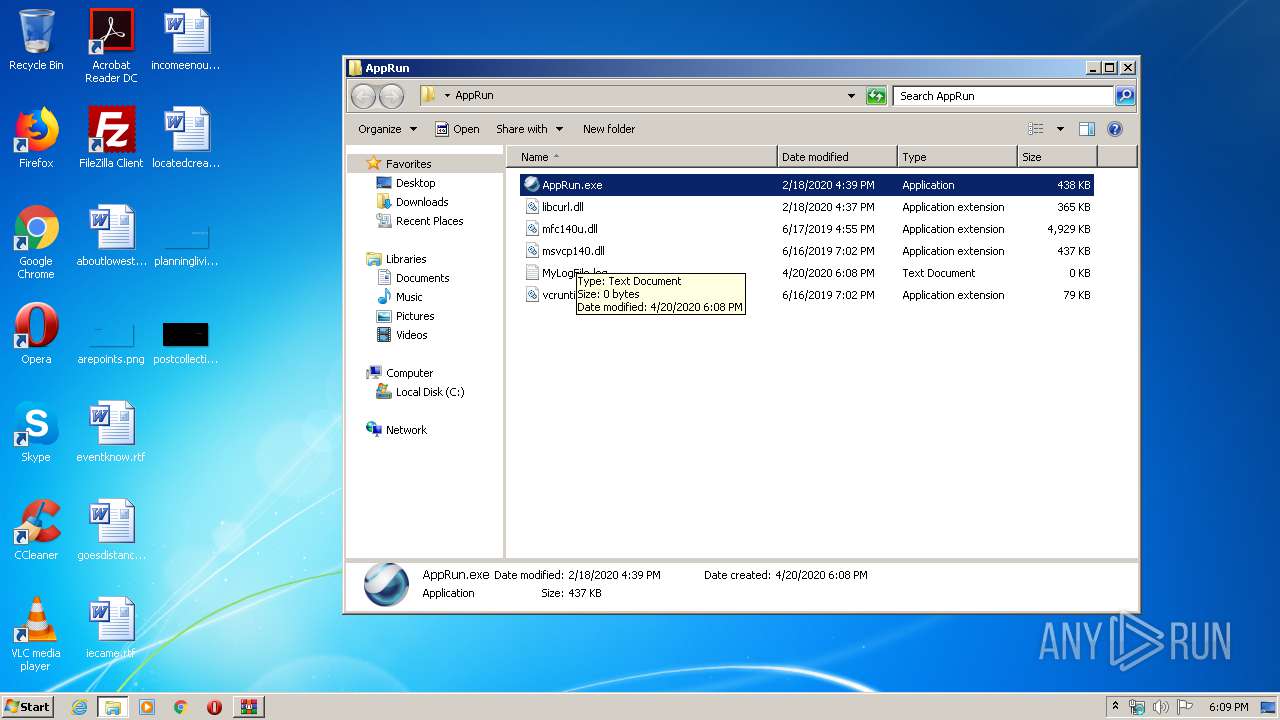
| 3404 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\AppRun\MyLogFile.log | C:\Windows\system32\NOTEPAD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3764 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Roaming\AppRun.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
Total events
1 099
Read events
1 082
Write events
17
Delete events
0
Modification events
| (PID) Process: | (3764) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3764) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3764) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3764) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Roaming\AppRun.zip | |||
| (PID) Process: | (3764) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3764) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3764) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3764) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2932) AppRun.exe | Key: | HKEY_CURRENT_USER\Software\Apprun |
| Operation: | write | Name: | Installed |
Value: 1 | |||
| (PID) Process: | (744) SearchProtocolHost.exe | Key: | HKEY_USERS\.DEFAULT\Software\Classes\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
11
Suspicious files
0
Text files
3
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3764 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3764.34894\AppRun\AppRun.exe | — | |
MD5:— | SHA256:— | |||
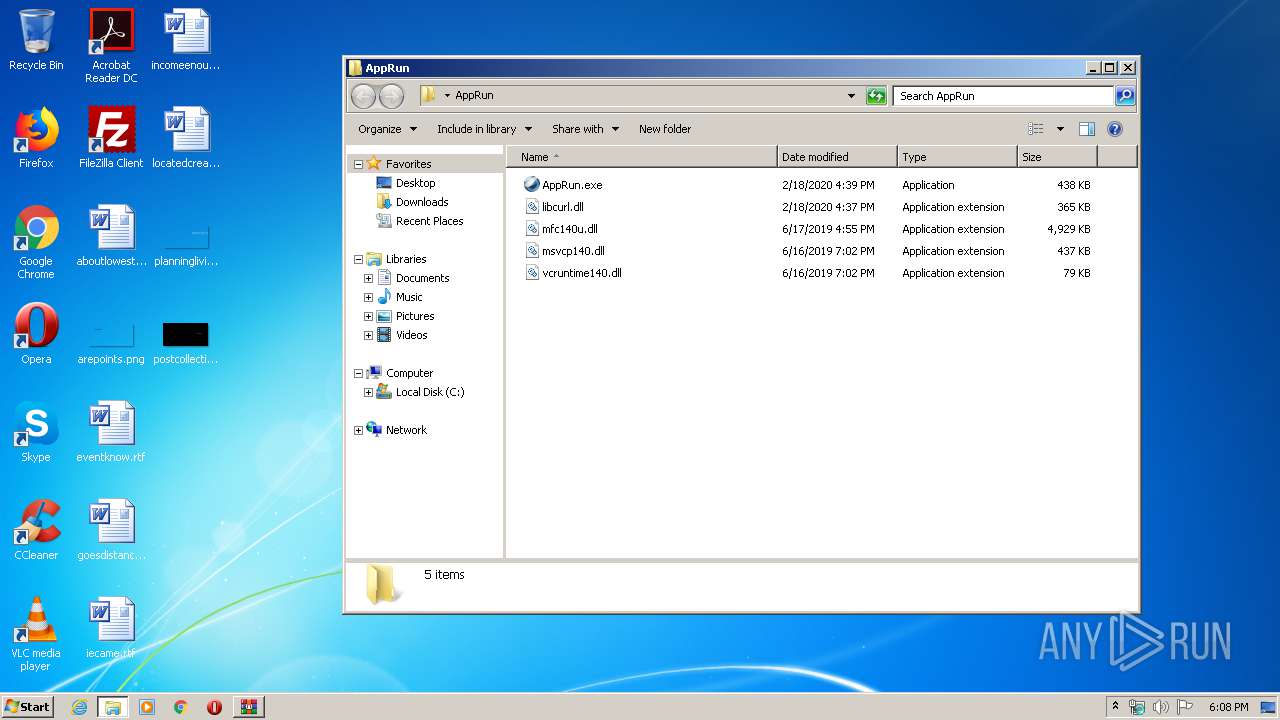
| 3764 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3764.34894\AppRun\libcurl.dll | — | |
MD5:— | SHA256:— | |||
| 3764 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3764.34894\AppRun\mfc140u.dll | — | |
MD5:— | SHA256:— | |||
| 3764 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3764.34894\AppRun\msvcp140.dll | — | |
MD5:— | SHA256:— | |||
| 3764 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3764.34894\AppRun\vcruntime140.dll | — | |
MD5:— | SHA256:— | |||
| 2932 | AppRun.exe | C:\Users\admin\AppData\Local\Temp\u29g.0 | executable | |
MD5:— | SHA256:— | |||
| 2932 | AppRun.exe | C:\Users\admin\AppData\Local\Temp\u29g.1 | executable | |
MD5:— | SHA256:— | |||
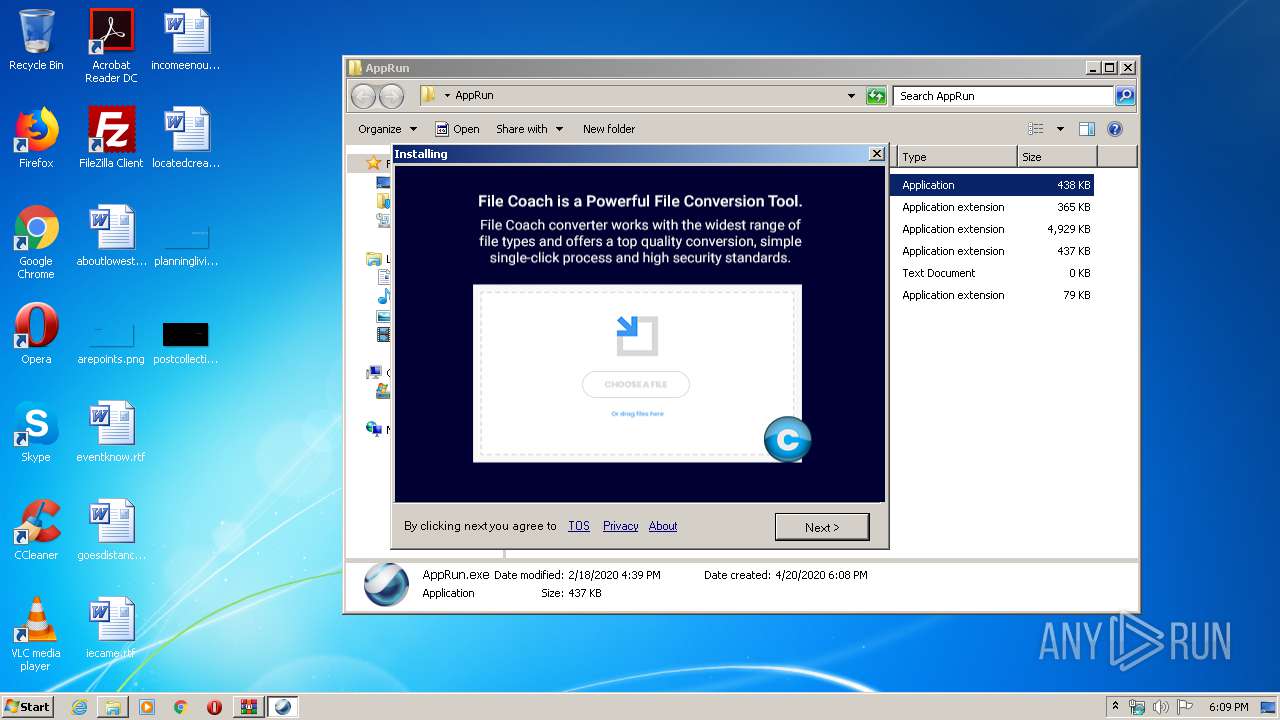
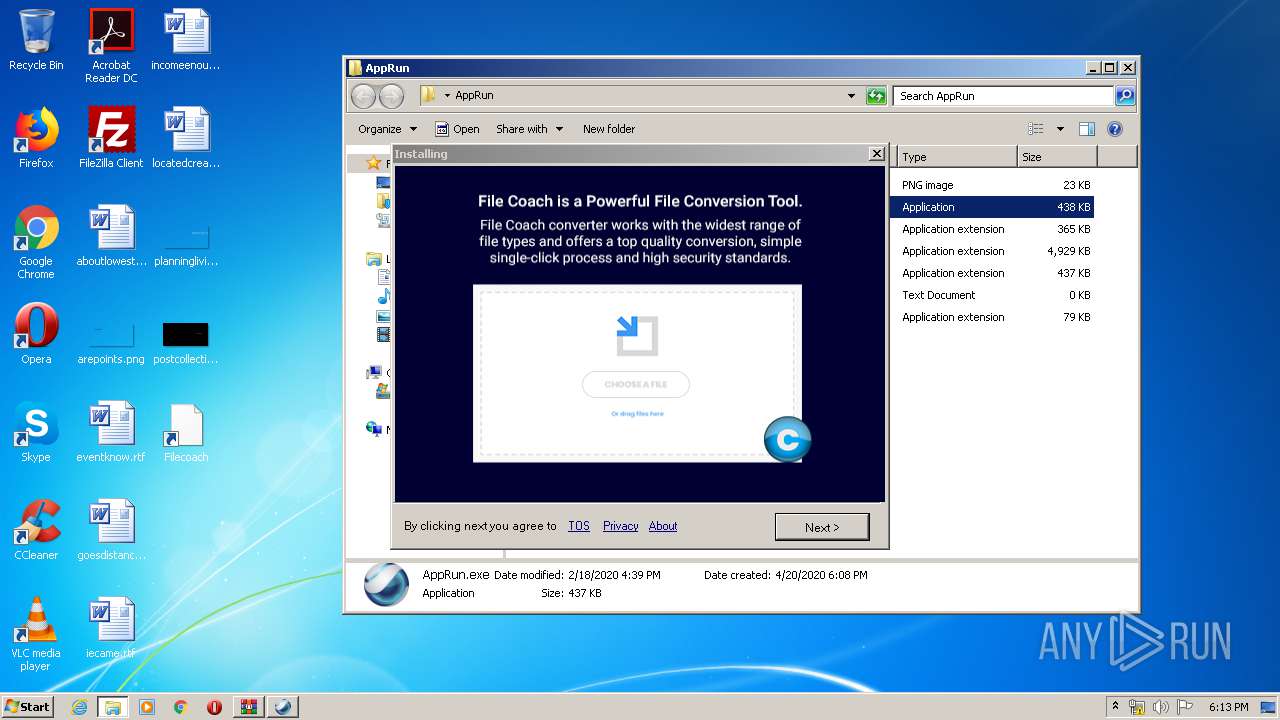
| 2932 | AppRun.exe | C:\Users\admin\Desktop\AppRun\1582446227183_file-coach.png | image | |
MD5:— | SHA256:— | |||
| 2932 | AppRun.exe | C:\Users\admin\AppData\Roaming\AppRun\AppRun.exe | executable | |
MD5:— | SHA256:— | |||
| 2932 | AppRun.exe | C:\Users\admin\AppData\Local\Temp\u29g.2 | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
81
DNS requests
10
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
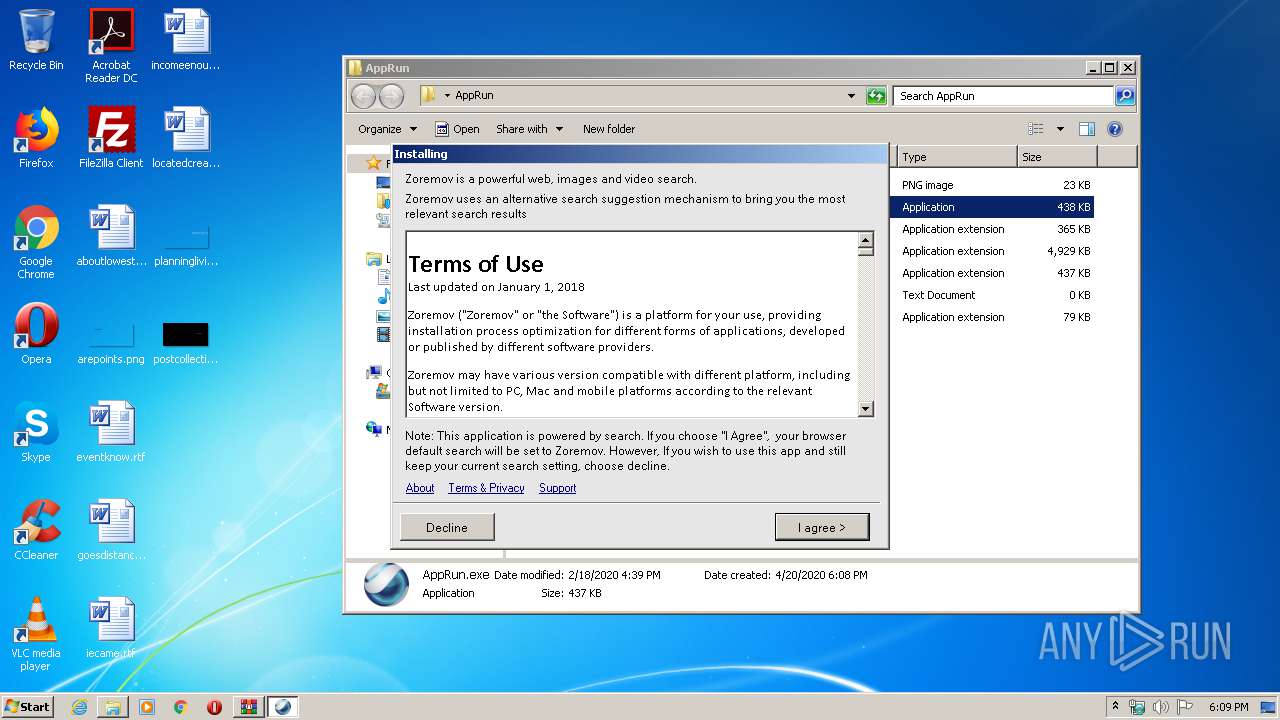
2932 | AppRun.exe | GET | 200 | 45.79.159.254:80 | http://alg.zoremov.com/monetize?chrome_sp_set=0&client_version=1248&date=1587402585732&default_browser=Internet+Explorer&download_browser=edge&edge_hp_set=0&edge_sp_set=0&emid=1F8BFBFF000506E34d513030303020312020202020202020202020205254004A04AF&event_show_install=1555313659267406&firefox_hp_set=0&firefox_sp_set=0&identity=Zoremov&ie_hp_set=0&ie_sp_set=0&info_b=GmNrQkVOCAtDWEVOUF9PUktVV15RTFRbWVpSQElha05BQAMKQ1RBQFNUT15PU0tbUF1WTEdAbGRBQkcJBQkEQF9MQ0xsaBg%3d&install_id=1555313659267406&is_install_accepted=1&is_set_hp_approved=1&is_set_sp_approved=1&is_sp_set=0&os_version=6.1.2%2f7601&session_id=3003064470&signature=GS_ABE_LABS_LTD_SIGNATURE | US | text | 141 b | suspicious |
2932 | AppRun.exe | GET | 200 | 45.79.159.254:80 | http://cache.zoremov.com/applications/1555313659267406/contents/en/images/1582446227183_file-coach.png | US | image | 22.7 Kb | suspicious |
2624 | AppRun.exe | GET | 200 | 45.79.159.254:80 | http://cache.zoremov.com/applications/1555313659267406/contents/en/images/1582446227183_file-coach.png | US | image | 22.7 Kb | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2932 | AppRun.exe | 45.79.159.254:443 | alg.zoremov.com | Linode, LLC | US | suspicious |
2624 | AppRun.exe | 45.79.159.254:443 | alg.zoremov.com | Linode, LLC | US | suspicious |
2932 | AppRun.exe | 45.79.159.254:80 | alg.zoremov.com | Linode, LLC | US | suspicious |
2932 | AppRun.exe | 69.164.210.196:443 | bi.tst.zoremov.com | Linode, LLC | US | unknown |
2624 | AppRun.exe | 45.79.159.254:80 | alg.zoremov.com | Linode, LLC | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
alg.zoremov.com |
| suspicious |
mdl.zoremov.com |
| suspicious |
bi.zoremov.com |
| suspicious |
cache.zoremov.com |
| suspicious |
bi.tst.zoremov.com |
| unknown |