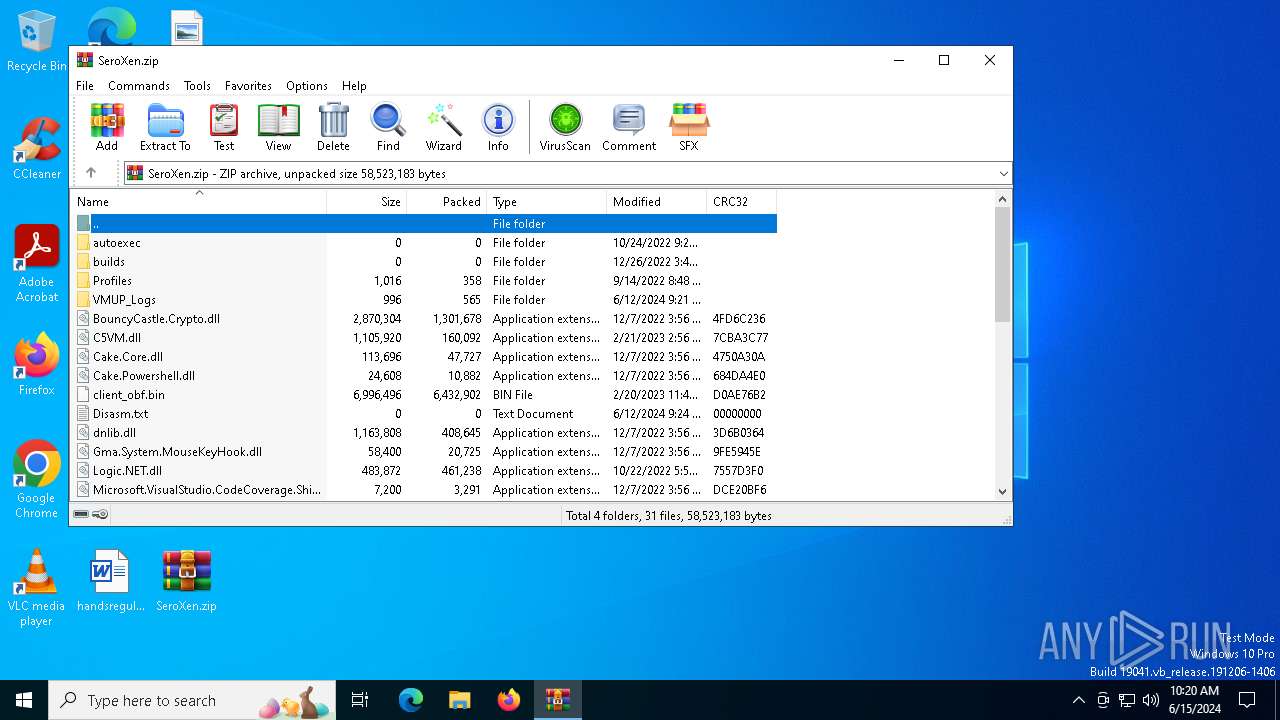
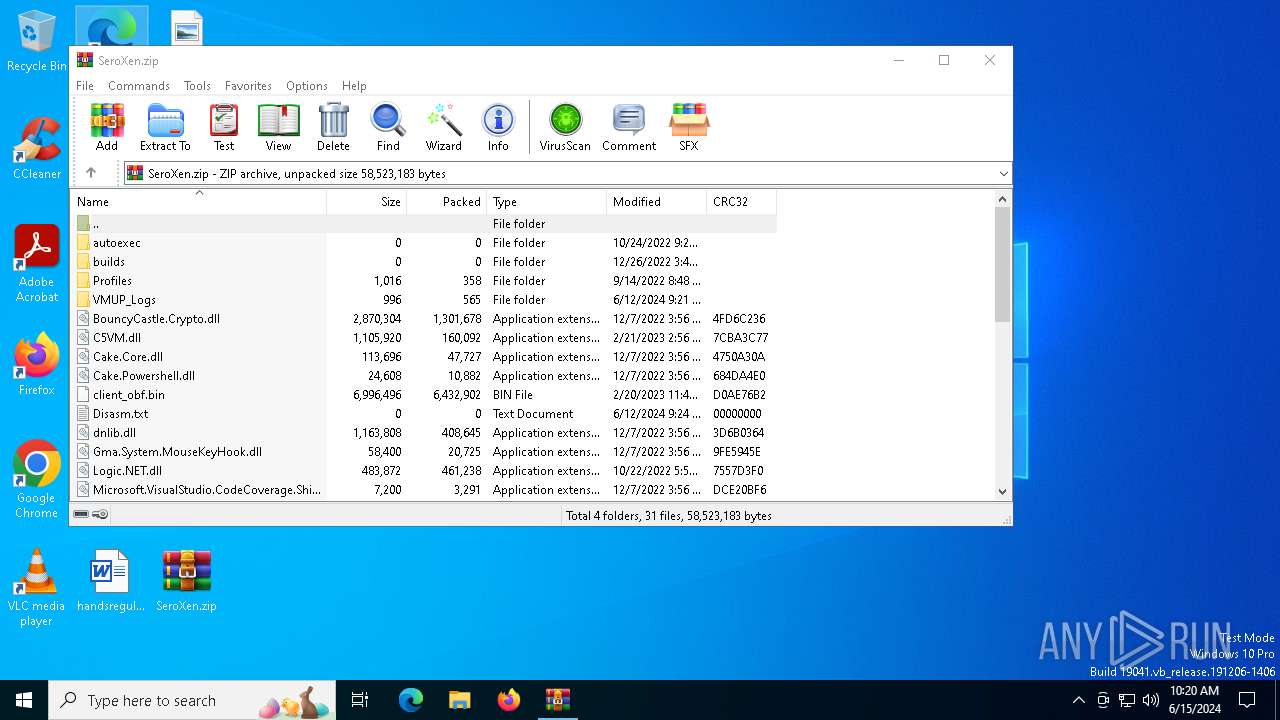
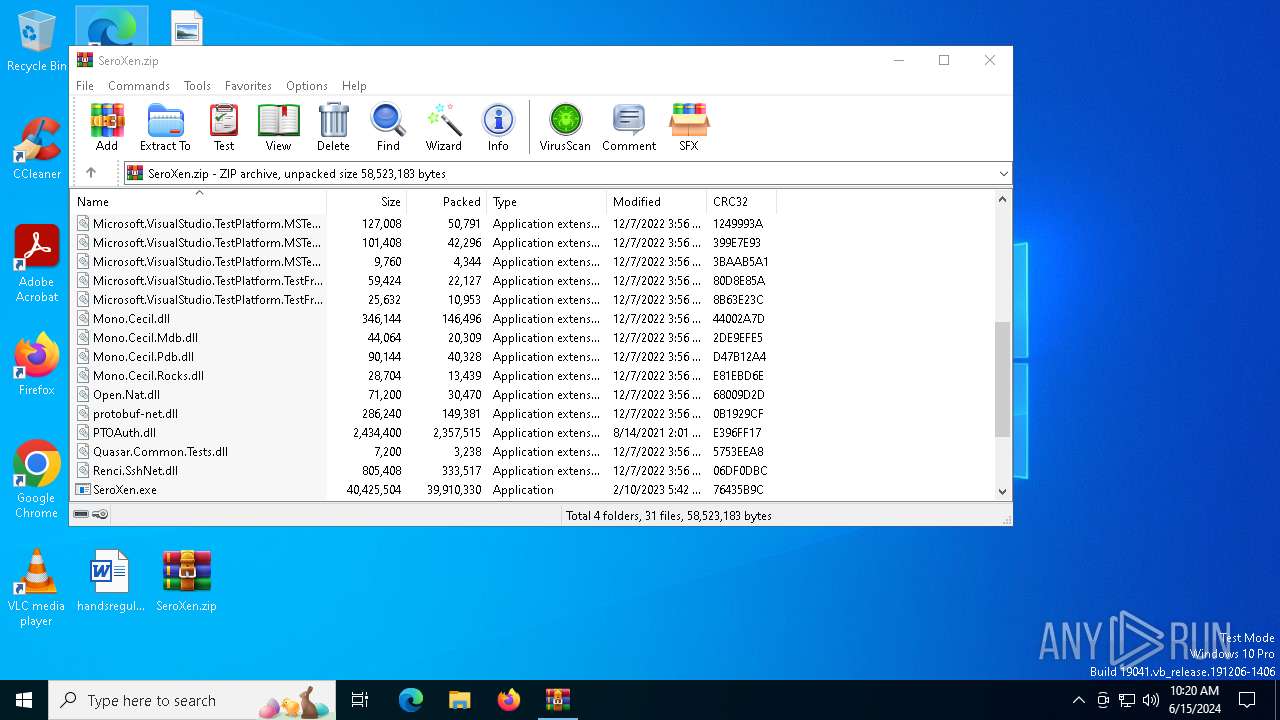
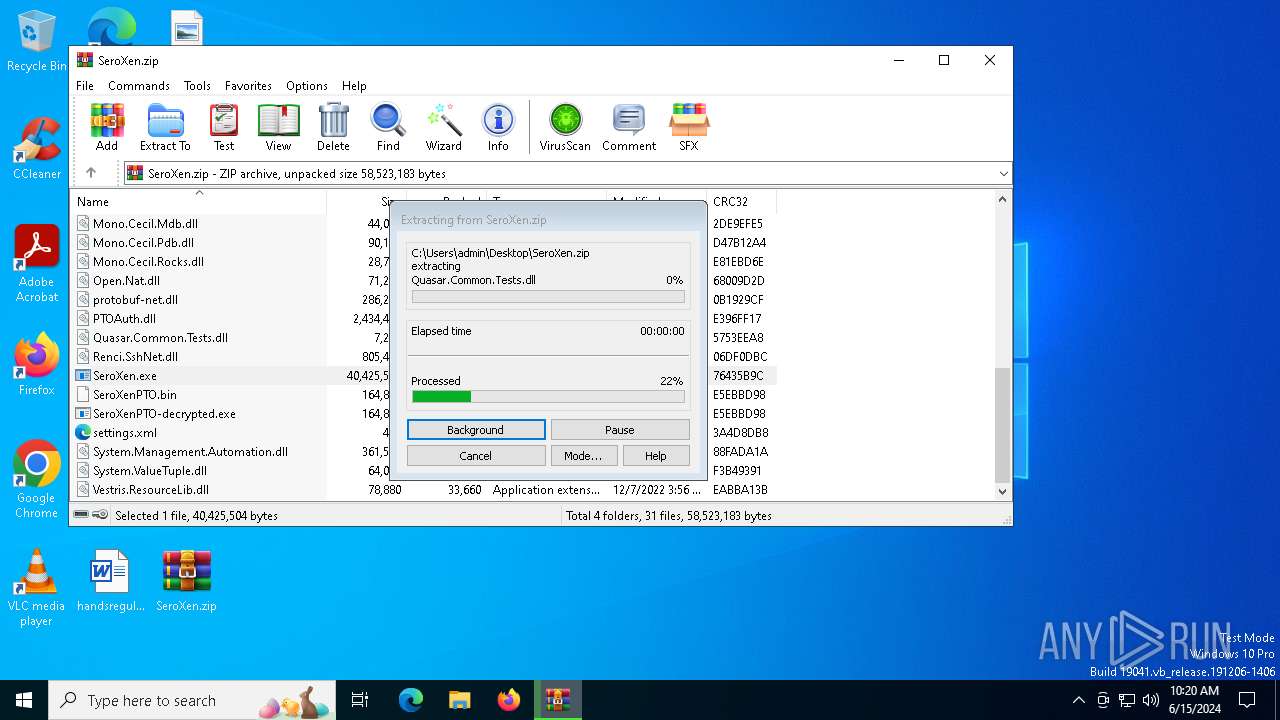
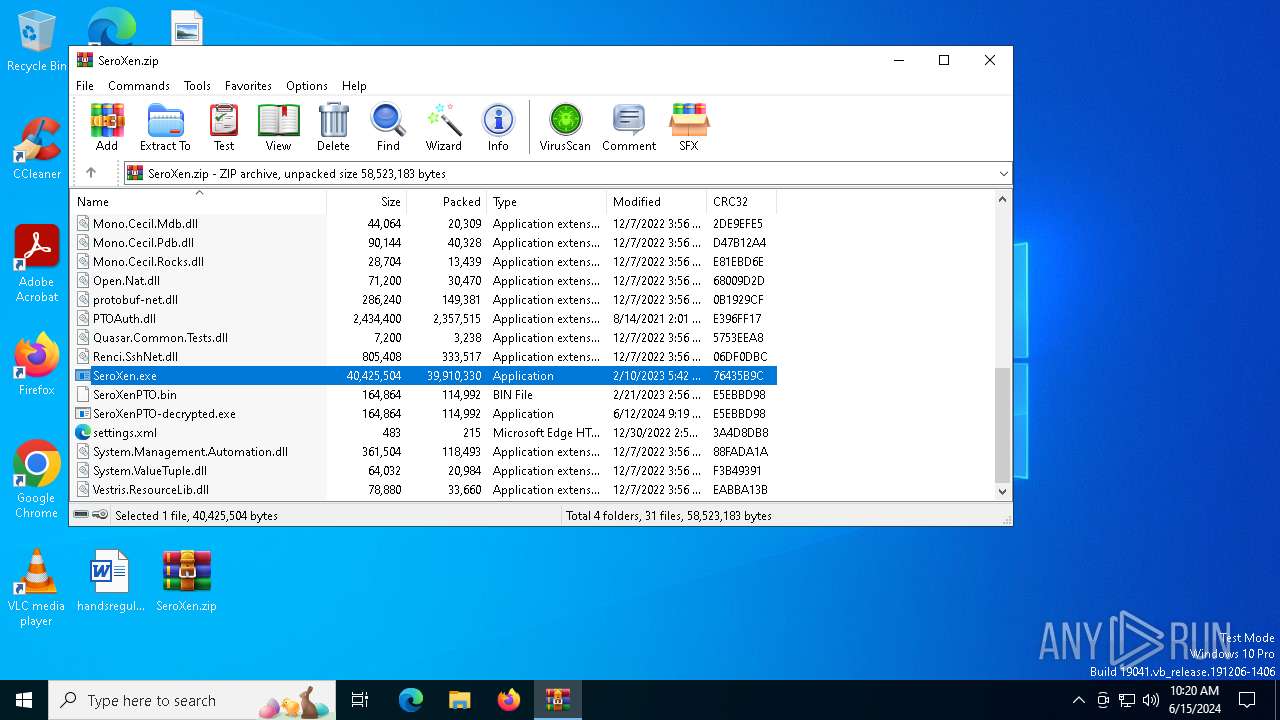
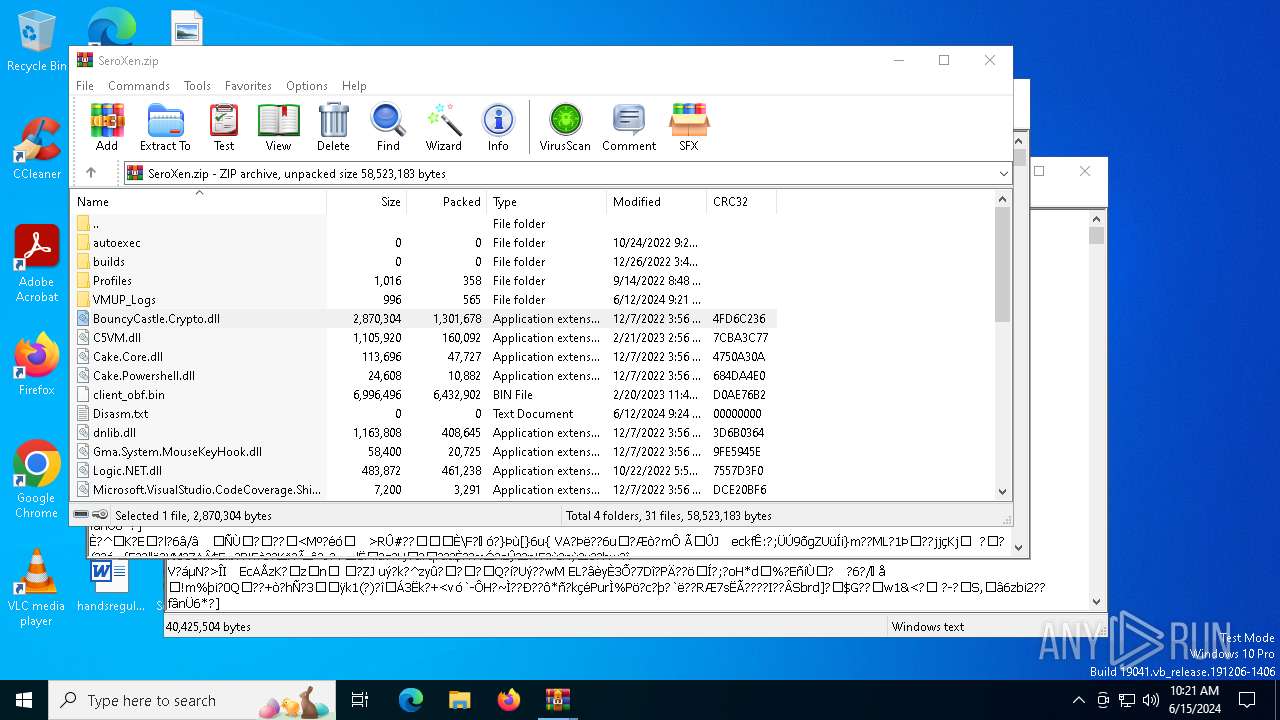
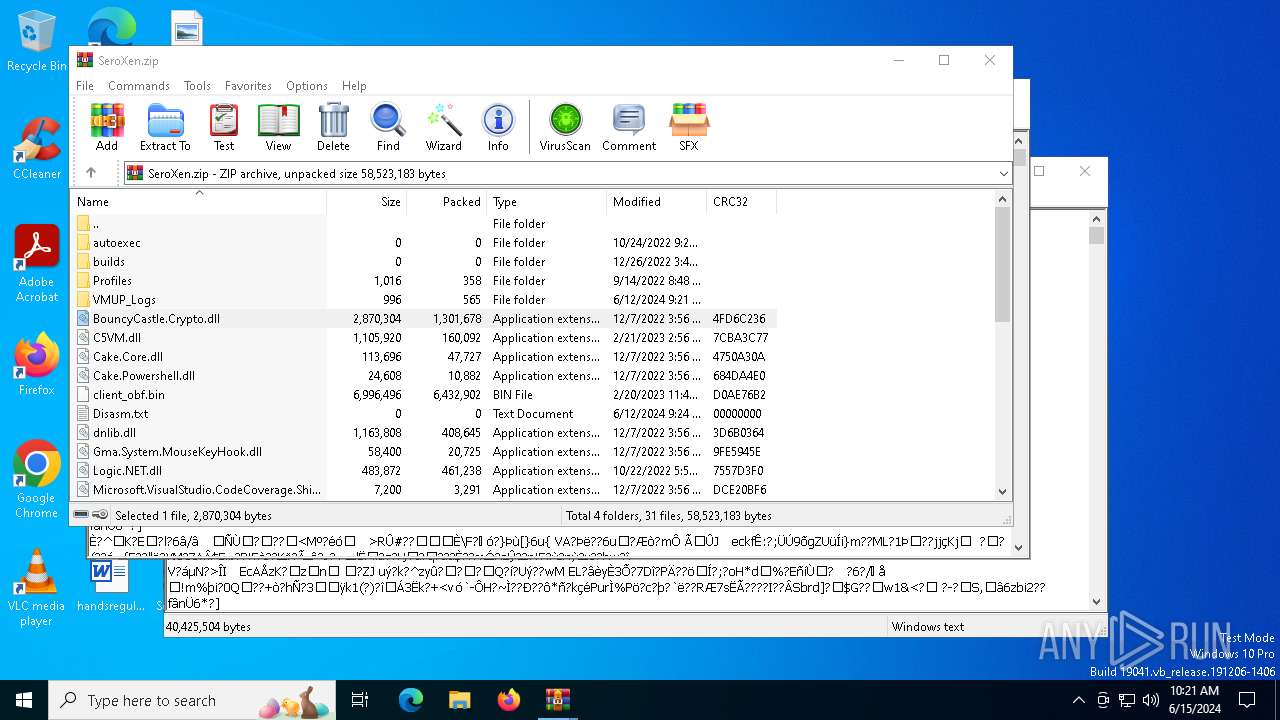
| File name: | SeroXen.zip |
| Full analysis: | https://app.any.run/tasks/54cdcf13-0aa3-4299-9bf0-d31742e1297a |
| Verdict: | Malicious activity |
| Analysis date: | June 15, 2024, 10:19:38 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | 02153FEBFDB4C44D05AA380C7D321DDE |
| SHA1: | 04C2D0A3A9055E332684344E6A0F8F8AAE6A4D0D |
| SHA256: | F2A22A1B44253073CDA975E57EE937304A434538F4DF0942A65B25889F0FA24B |
| SSDEEP: | 393216:OctvkuhTgeYUTVst+L3qtc4jXHG39FVYBdqUq06DW2RW+LQWtXum97:Ow1hTkqVY+LqnHGtFVYK10YRW+EWt+mZ |
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 4288)
- SeroXen.exe (PID: 6296)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 6244)
The process creates files with name similar to system file names
- WinRAR.exe (PID: 6244)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6244)
- SeroXen.exe (PID: 6296)
Executable content was dropped or overwritten
- SeroXen.exe (PID: 6296)
Reads the BIOS version
- SeroXen.exe (PID: 6296)
Checks Windows Trust Settings
- SeroXen.exe (PID: 6296)
INFO
Drops the executable file immediately after the start
- WinRAR.exe (PID: 6244)
Manual execution by a user
- WinRAR.exe (PID: 6244)
Checks supported languages
- SeroXen.exe (PID: 6296)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6244)
Reads the computer name
- SeroXen.exe (PID: 6296)
Create files in a temporary directory
- SeroXen.exe (PID: 6296)
Reads the machine GUID from the registry
- SeroXen.exe (PID: 6296)
Reads the software policy settings
- SeroXen.exe (PID: 6296)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (33.3) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2022:10:25 00:20:34 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | autoexec/ |
Total processes
116
Monitored processes
3
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 4288 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\SeroXen.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 6244 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\SeroXen.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 6296 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa6244.15075\SeroXen.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa6244.15075\SeroXen.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Quasar Server Version: 1.4.0 Modules
| |||||||||||||||
Total events
14 568
Read events
14 509
Write events
59
Delete events
0
Modification events
| (PID) Process: | (4288) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (4288) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (4288) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (4288) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\SeroXen.zip | |||
| (PID) Process: | (4288) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4288) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4288) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4288) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4288) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
| (PID) Process: | (4288) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
Executable files
28
Suspicious files
0
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6244 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6244.15075\client_obf.bin | — | |
MD5:— | SHA256:— | |||
| 6244 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6244.15075\C5VM.dll | executable | |
MD5:37691C7533A9327F520EBE21FAA72191 | SHA256:DE6F08708B8BC6562828C7787769D14752B2C1AB0B0E9B34B1ED44987BD2F842 | |||
| 6244 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6244.15075\dnlib.dll | executable | |
MD5:C044F897673C5D72F631204D36D0DCAD | SHA256:6D6EF70286BDC71C9973AAE7069B038BB245FFB83234F98A56359B613810D392 | |||
| 6244 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6244.15075\Microsoft.VisualStudio.TestPlatform.TestFramework.dll | executable | |
MD5:324815ABB2445918EF92D6B9EF33CB9F | SHA256:2C527E9A559DA4FFEC4C78E535B51D87A73703266428A6464C7FA79CBE706238 | |||
| 6244 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6244.15075\Microsoft.VisualStudio.TestPlatform.MSTestAdapter.PlatformServices.dll | executable | |
MD5:F838683824EBB1B333E7056B529E69D3 | SHA256:EC9A93948560FD6F5E219E01850946EF94992E18A0309B27D8DF5F3420B23AC2 | |||
| 6244 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6244.15075\SeroXen.exe | — | |
MD5:— | SHA256:— | |||
| 6244 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6244.15075\Microsoft.VisualStudio.TestPlatform.MSTest.TestAdapter.dll | executable | |
MD5:C462573A9DD520CD2E03652CA0EC9396 | SHA256:5BFC5ABE8BFCF35E4562D4782E5BABEB5708DB2D8714FD2170212384D2652D9B | |||
| 6244 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6244.15075\Logic.NET.dll | executable | |
MD5:F7C48E31A7B79A58CDD0A41B6D57147D | SHA256:ADC96B974AB1520EA0A18B7223F2E0084A52FEDC4841F4074C738007FCF3B39D | |||
| 6244 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6244.15075\Microsoft.VisualStudio.TestPlatform.MSTestAdapter.PlatformServices.Interface.dll | executable | |
MD5:4539091FA699D00D9F55BD2281139DAD | SHA256:BD19CE084093CB05A4186115857FB9D474C40DA992A29629333B4B4247A4DEDD | |||
| 6244 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6244.15075\Mono.Cecil.Mdb.dll | executable | |
MD5:308BFF23291C88669892A50E65652D76 | SHA256:91D67E936FFF5D3AC2749C9B13CEEBBDEA1B3BD4BC24C5CFFE55EA9AB4F2EECD | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
19
TCP/UDP connections
32
DNS requests
12
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4856 | RUXIMICS.exe | GET | 200 | 23.211.242.138:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
5576 | svchost.exe | GET | 200 | 23.211.242.138:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
5140 | MoUsoCoreWorker.exe | GET | 200 | 23.211.242.138:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
5140 | MoUsoCoreWorker.exe | GET | 200 | 23.205.37.177:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
5576 | svchost.exe | GET | 200 | 23.205.37.177:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
4856 | RUXIMICS.exe | GET | 200 | 23.205.37.177:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
— | — | GET | — | 23.211.242.197:443 | https://r.bing.com/rb/17/jnc,nj/6hU_LneafI_NFLeDvM367ebFaKQ.js?bu=DygxdoIBhQGIAX95fLsBvgExrgExwQE&or=w | unknown | — | — | unknown |
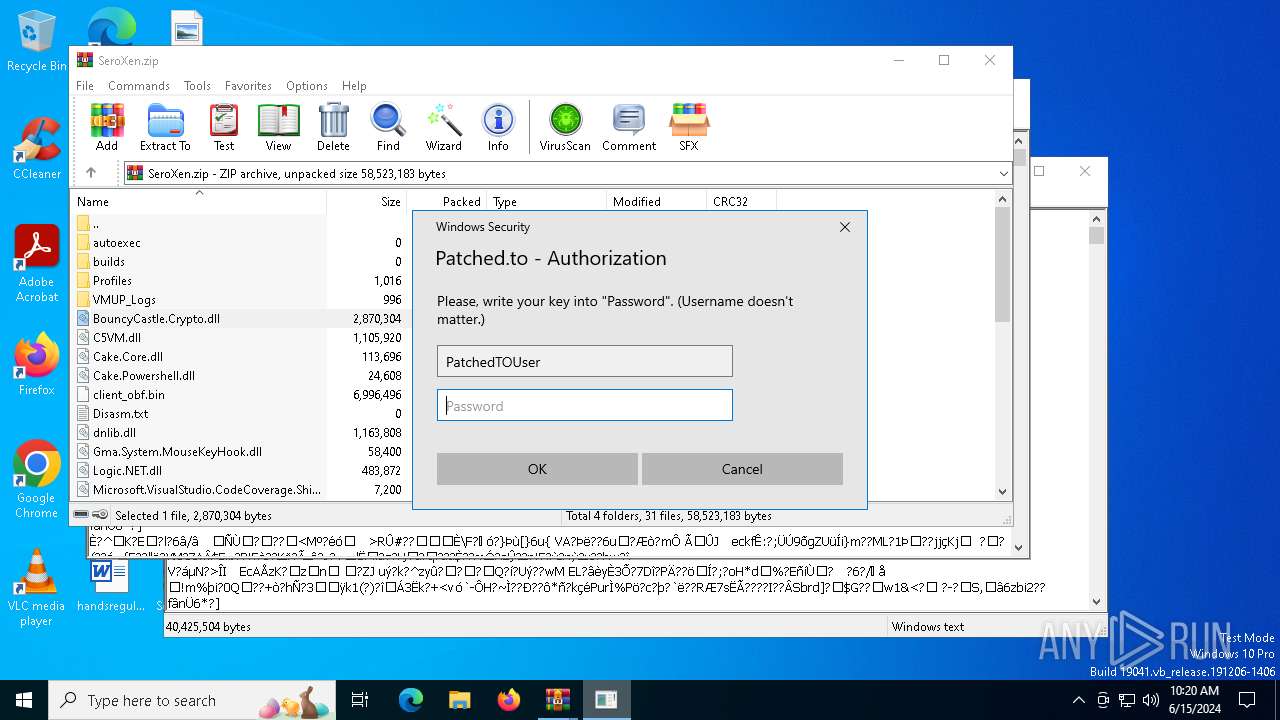
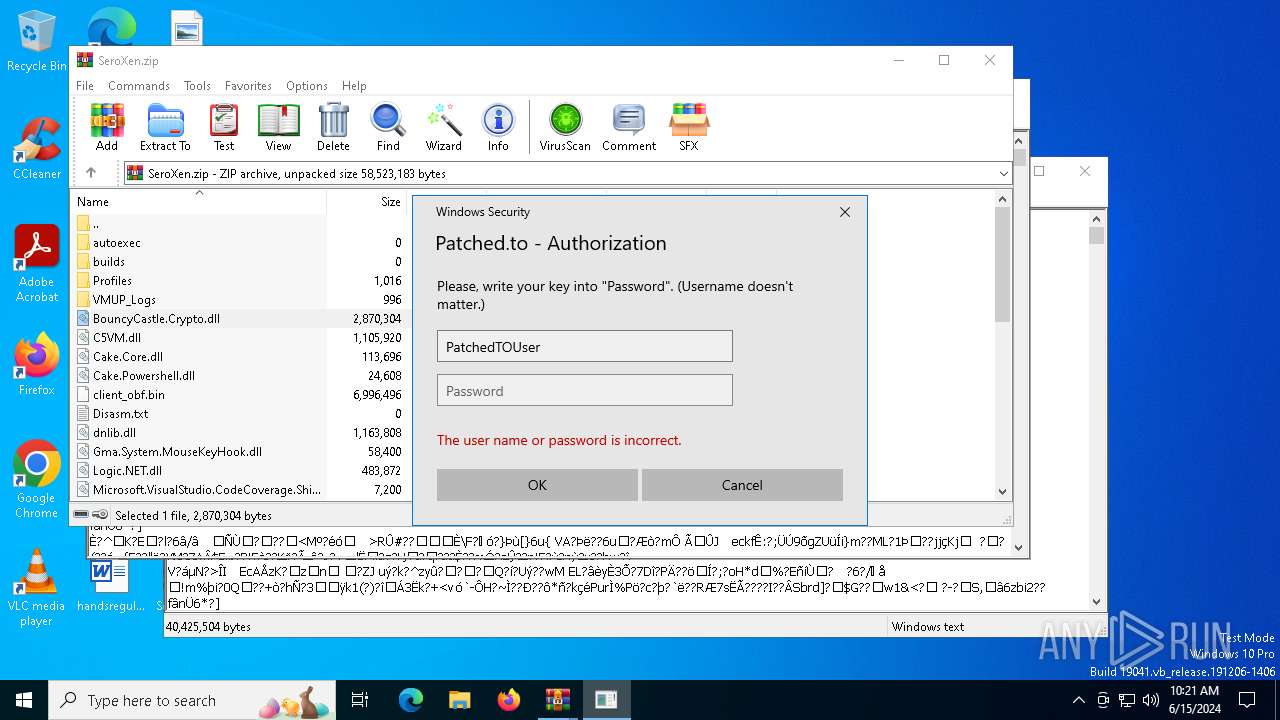
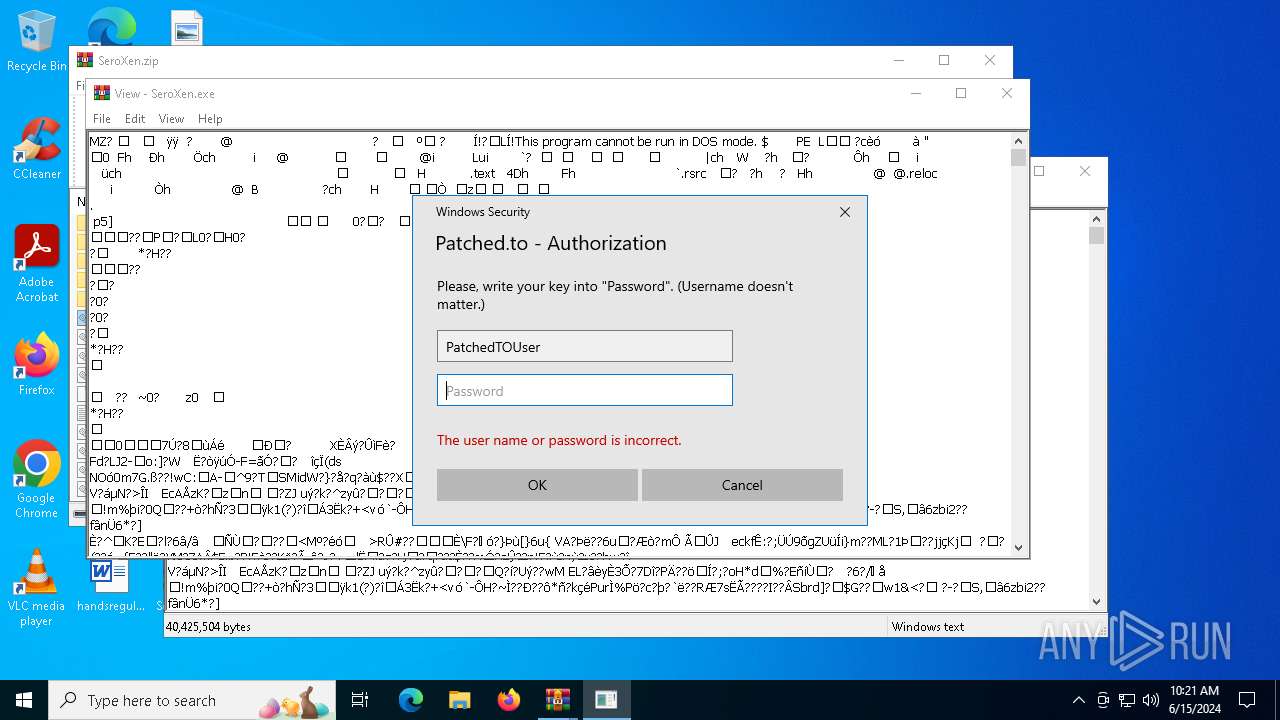
— | — | POST | 400 | 104.26.14.16:443 | https://auth.patched.to/SeroXen | unknown | binary | 16 b | unknown |
— | — | POST | 400 | 172.67.69.236:443 | https://auth.patched.to/SeroXen | unknown | binary | 16 b | unknown |
— | — | POST | 204 | 23.211.242.210:443 | https://www.bing.com/threshold/xls.aspx | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
4856 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
4856 | RUXIMICS.exe | 23.211.242.138:80 | crl.microsoft.com | Akamai International B.V. | US | unknown |
5140 | MoUsoCoreWorker.exe | 23.211.242.138:80 | crl.microsoft.com | Akamai International B.V. | US | unknown |
5576 | svchost.exe | 23.211.242.138:80 | crl.microsoft.com | Akamai International B.V. | US | unknown |
5140 | MoUsoCoreWorker.exe | 23.205.37.177:80 | www.microsoft.com | AKAMAI-AS | MX | unknown |
4856 | RUXIMICS.exe | 23.205.37.177:80 | www.microsoft.com | AKAMAI-AS | MX | unknown |
5576 | svchost.exe | 23.205.37.177:80 | www.microsoft.com | AKAMAI-AS | MX | unknown |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
5140 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
auth.patched.to |
| unknown |
www.bing.com |
| whitelisted |
r.bing.com |
| whitelisted |
fp.msedge.net |
| whitelisted |
b-ring.msedge.net |
| whitelisted |
dual-s-ring.msedge.net |
| unknown |
self.events.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2184 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .to TLD |
— | — | Generic Protocol Command Decode | SURICATA HTTP Request unrecognized authorization method |
— | — | Generic Protocol Command Decode | SURICATA HTTP Request unrecognized authorization method |