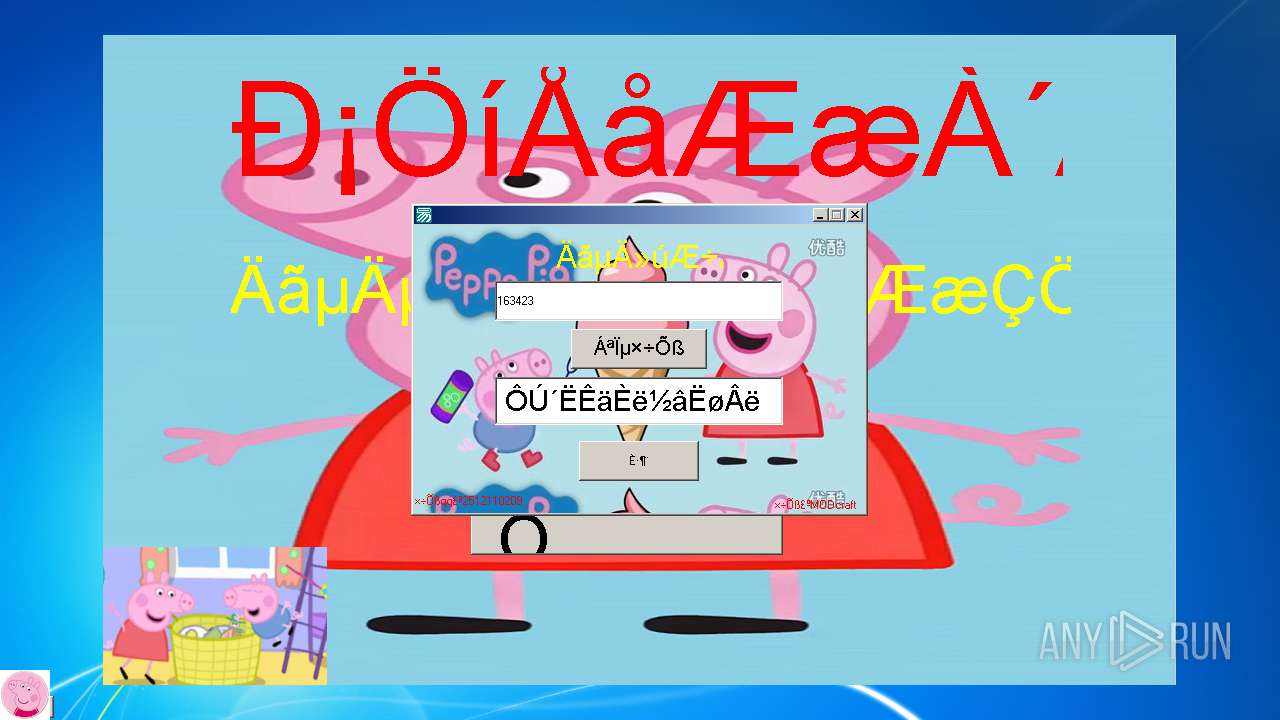
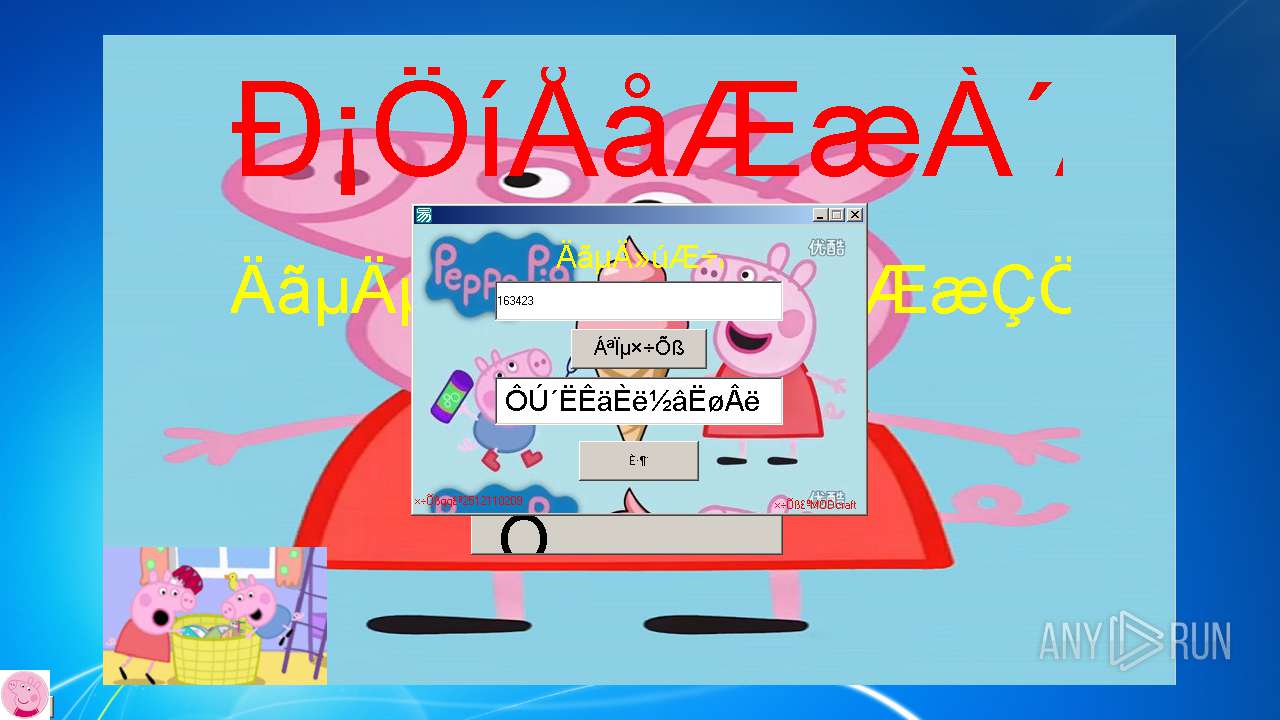
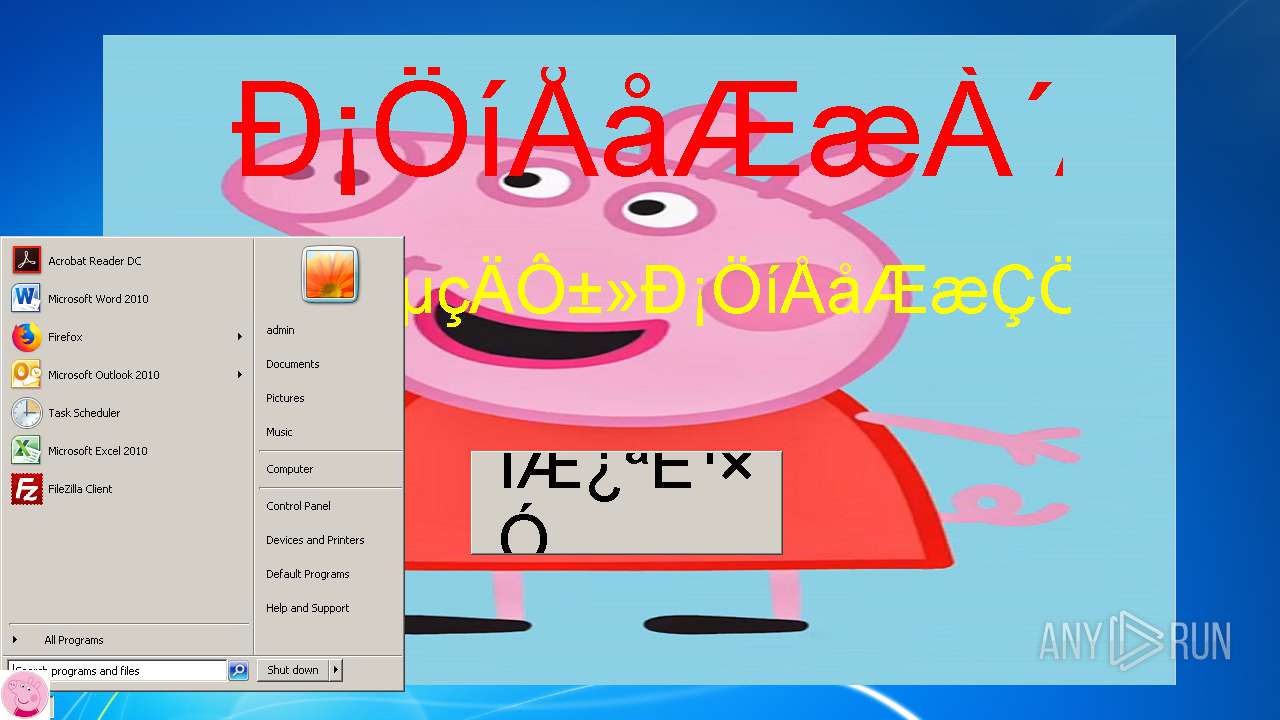
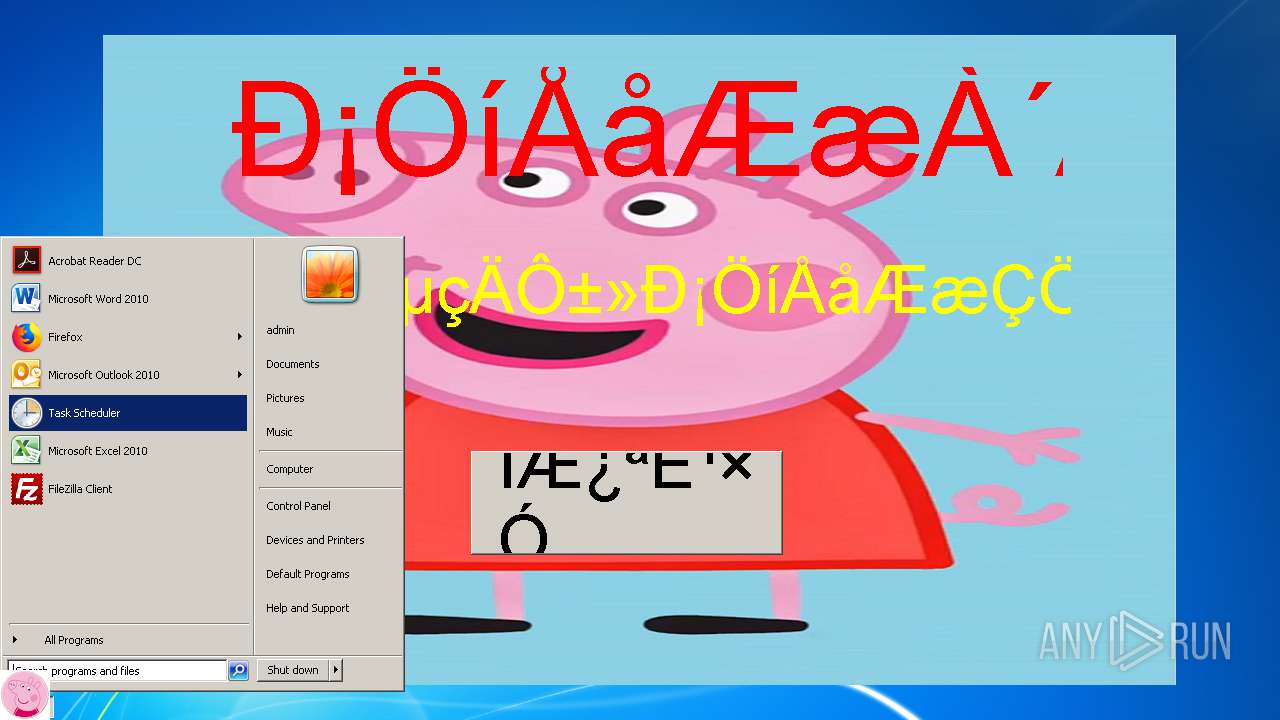
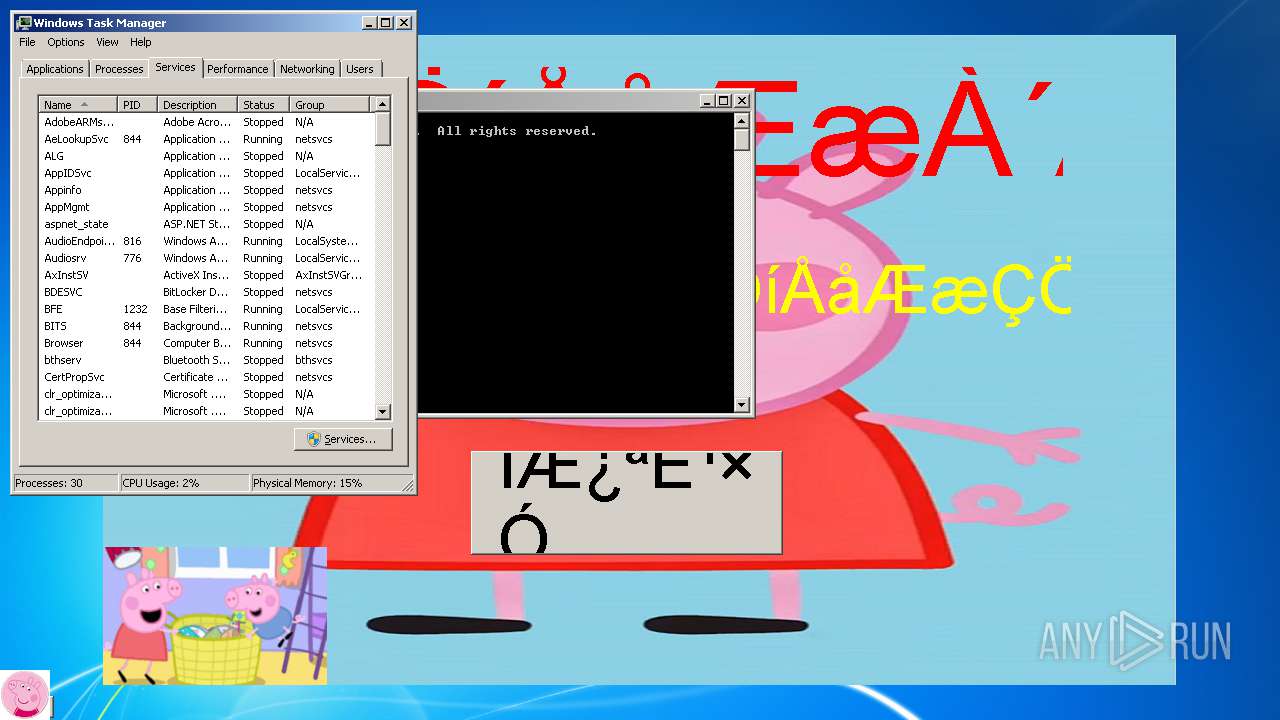
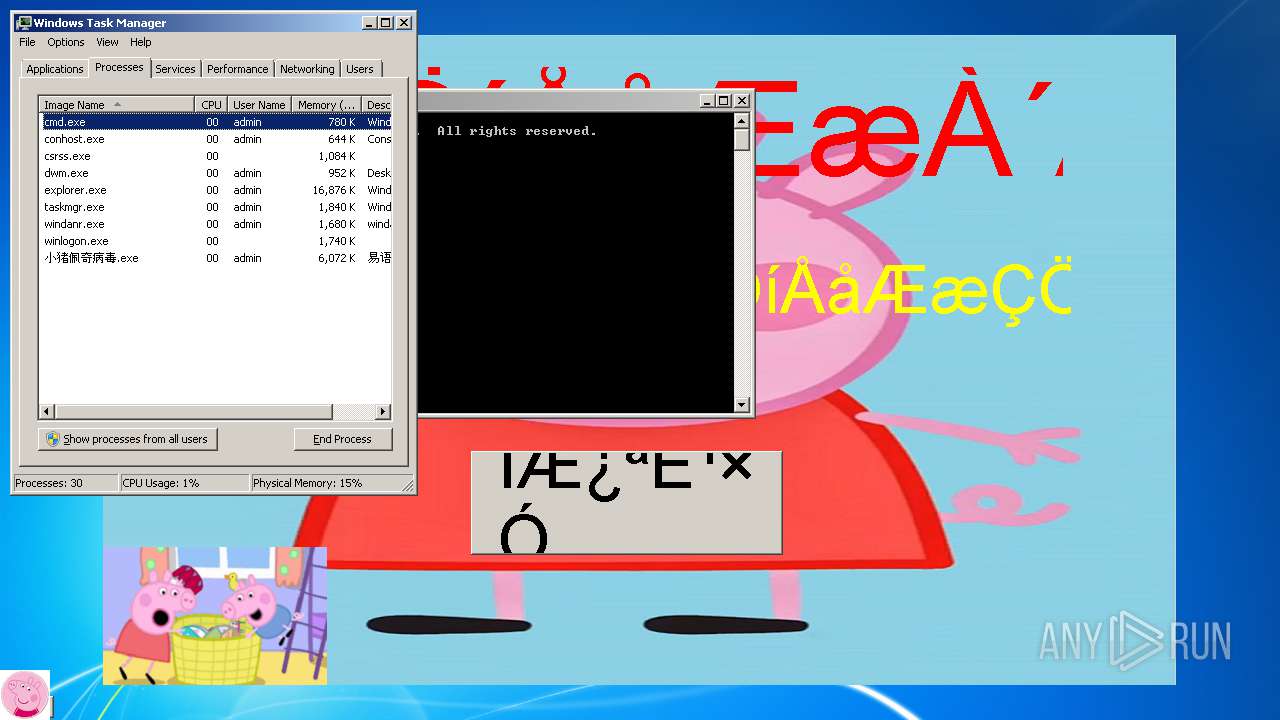
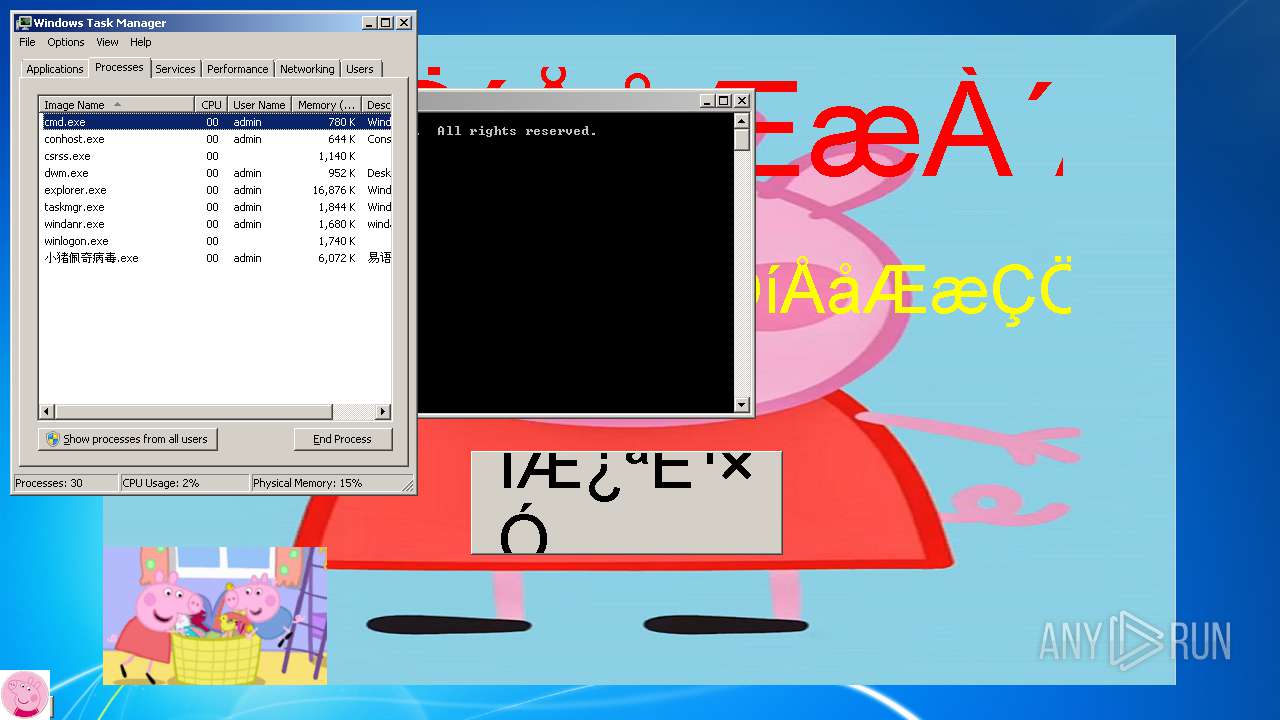
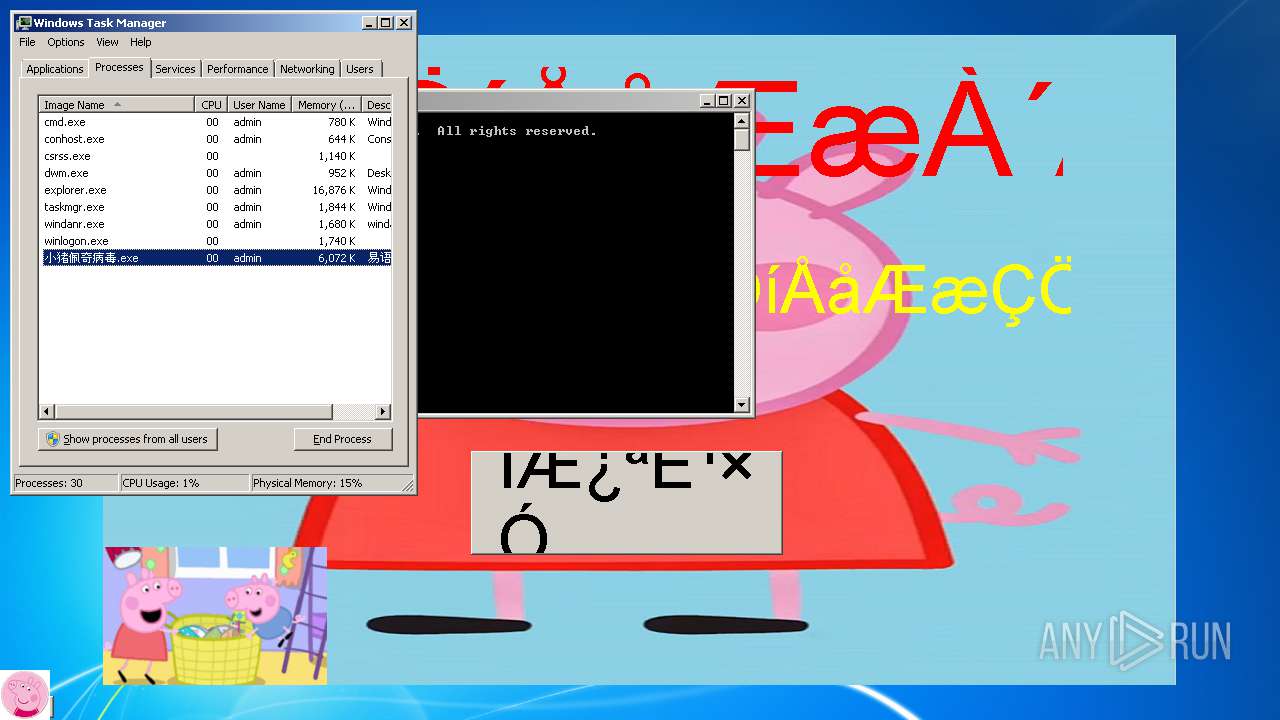
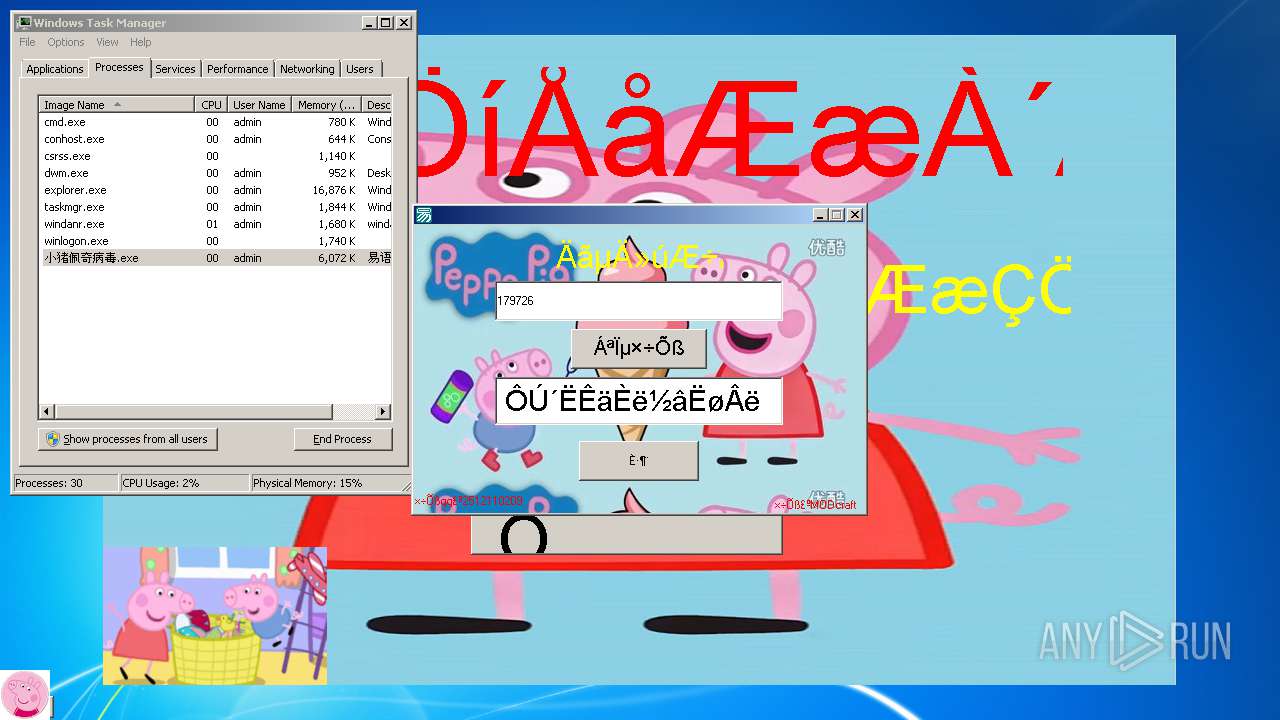
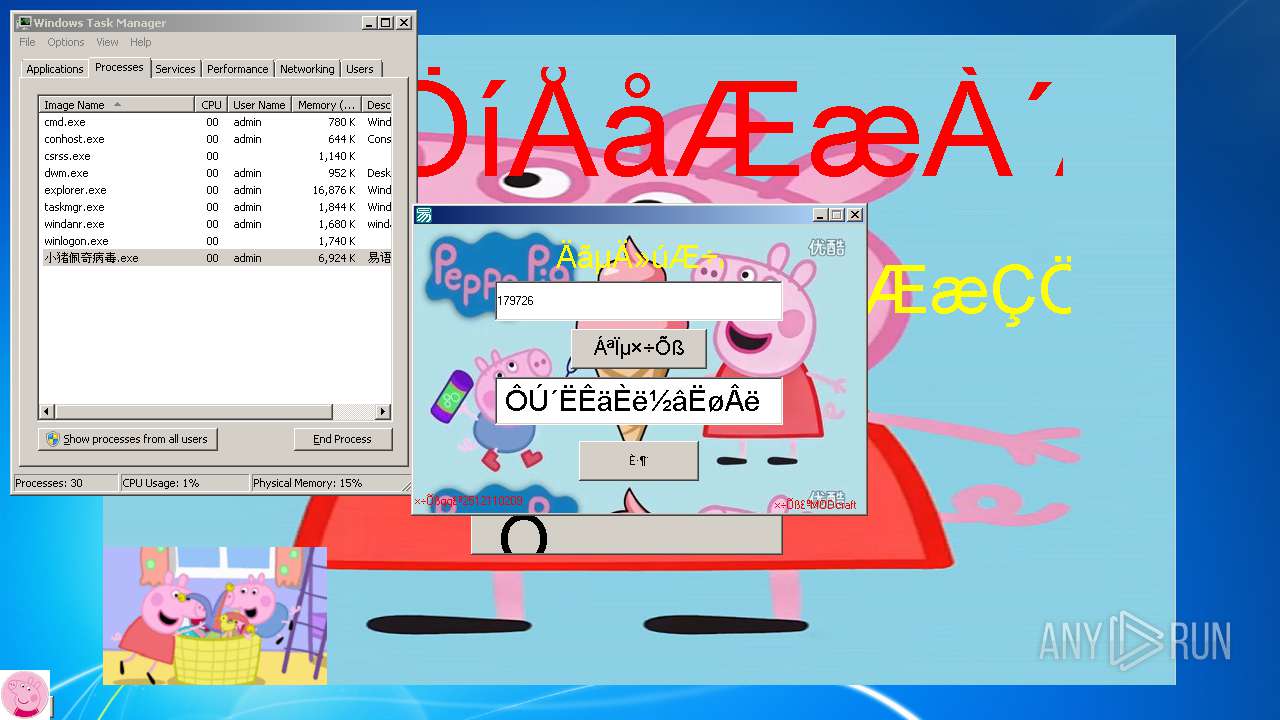
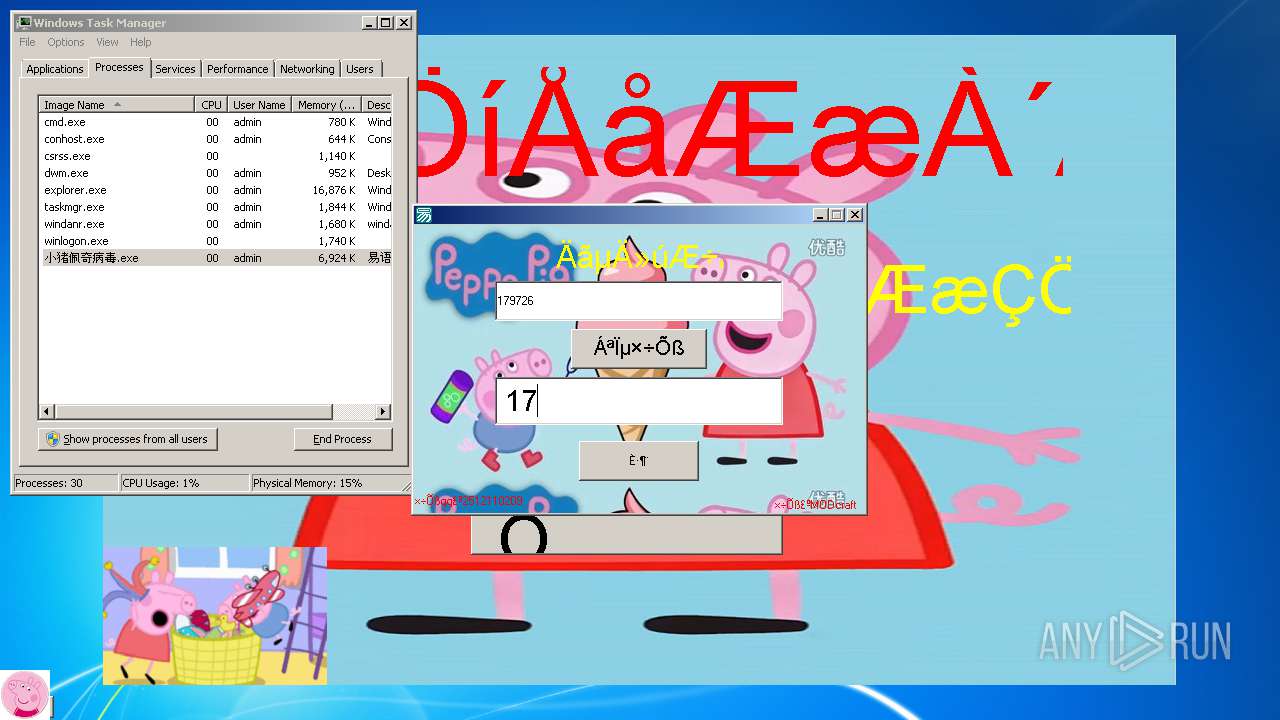
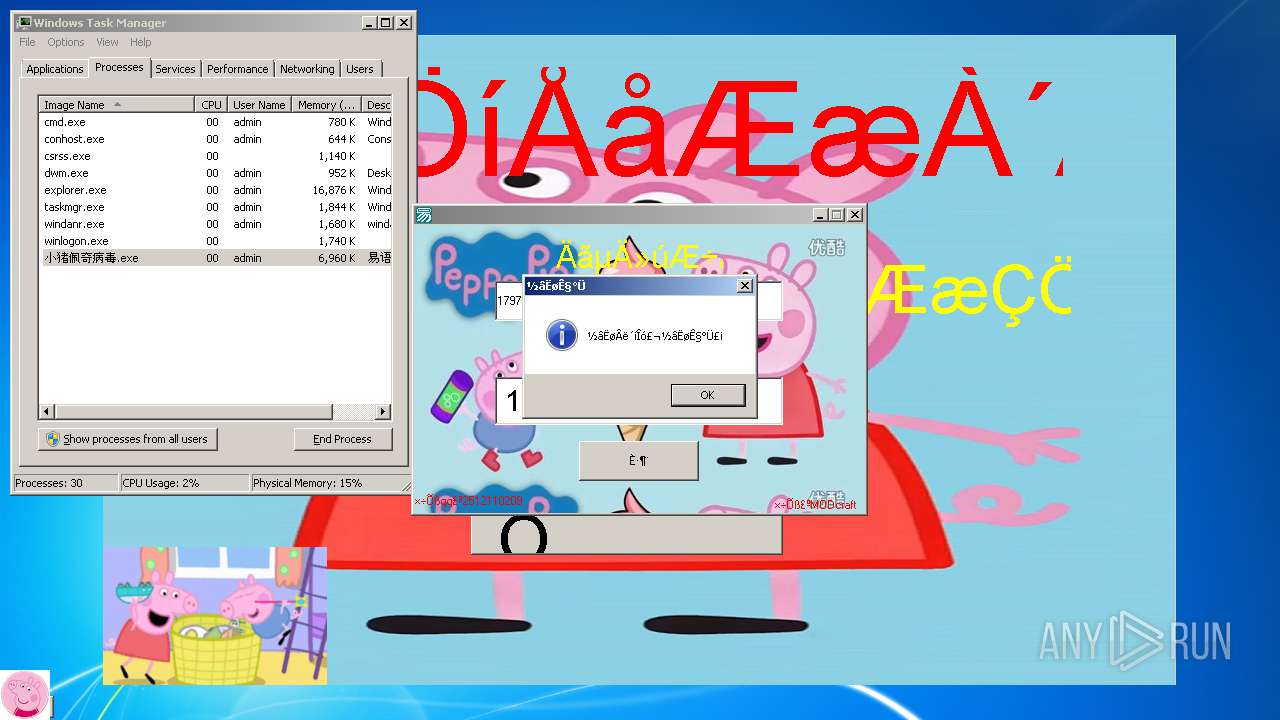
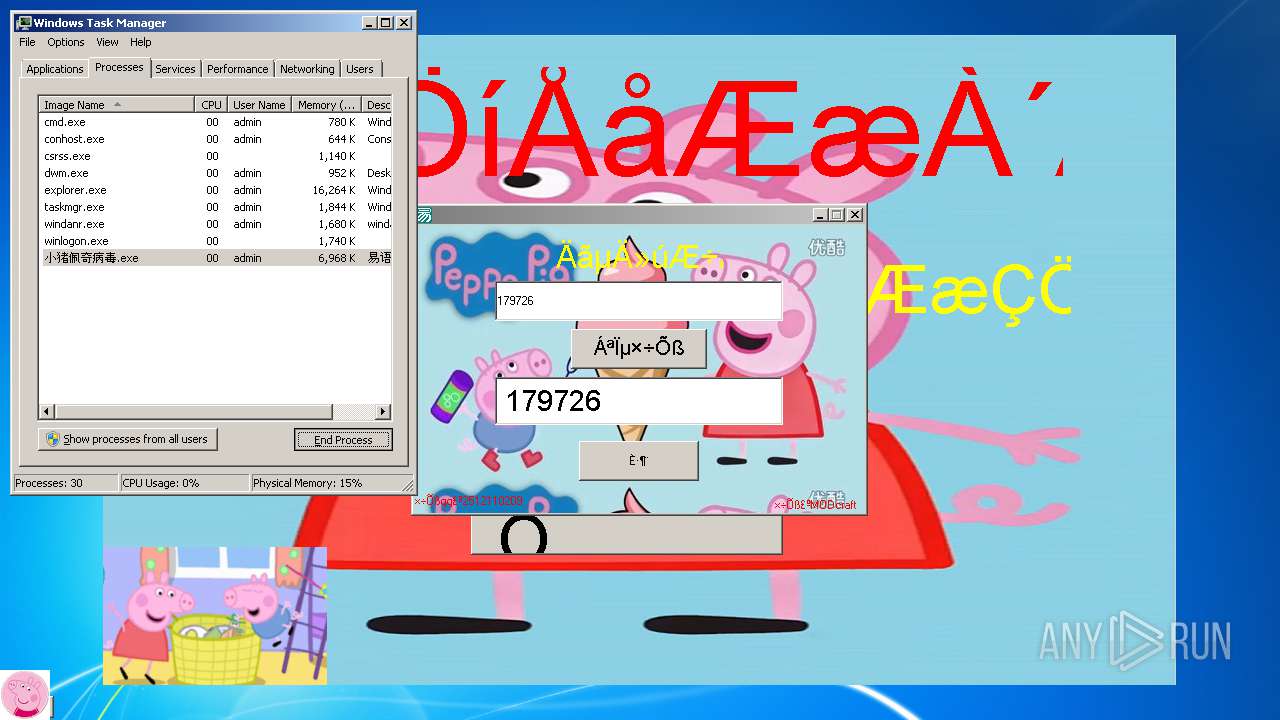
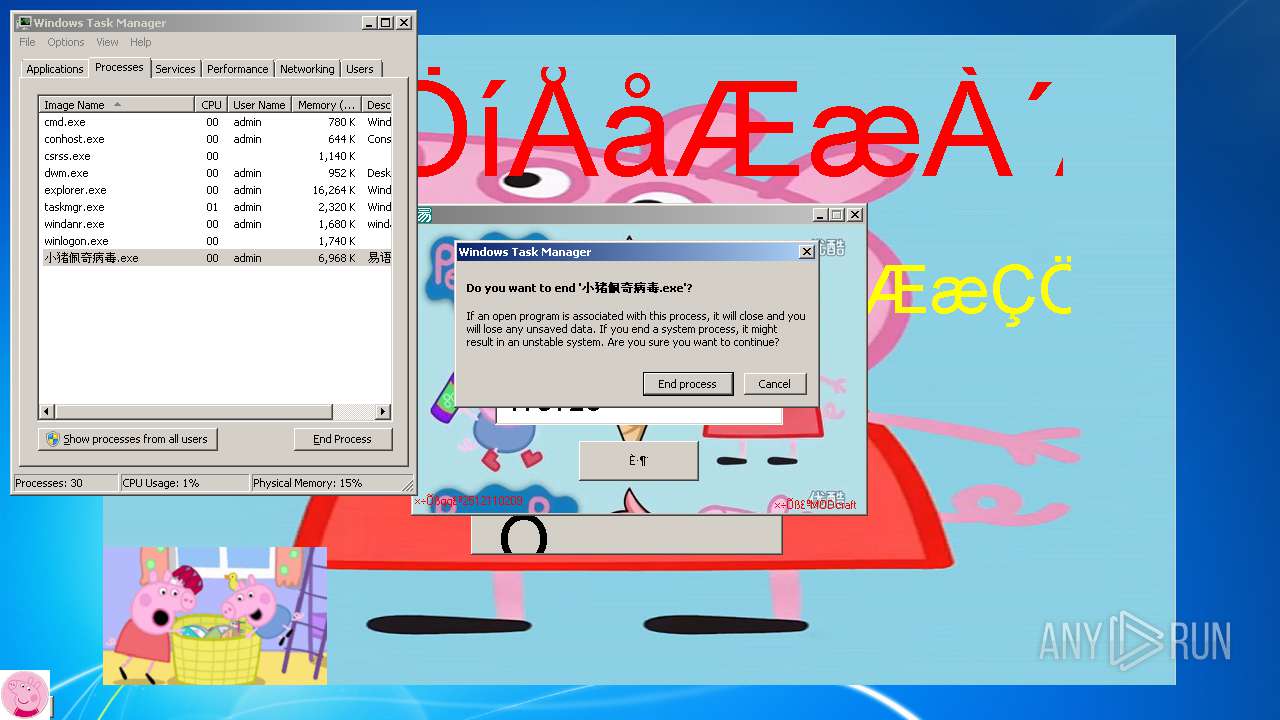
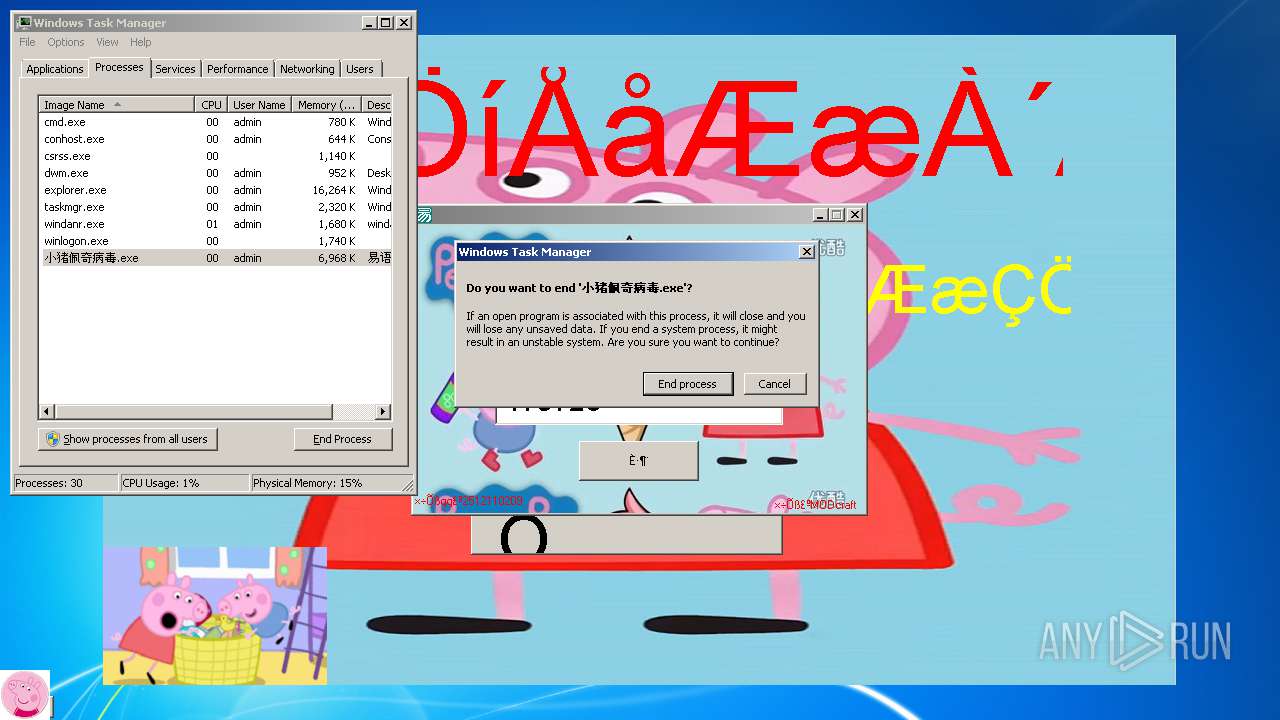
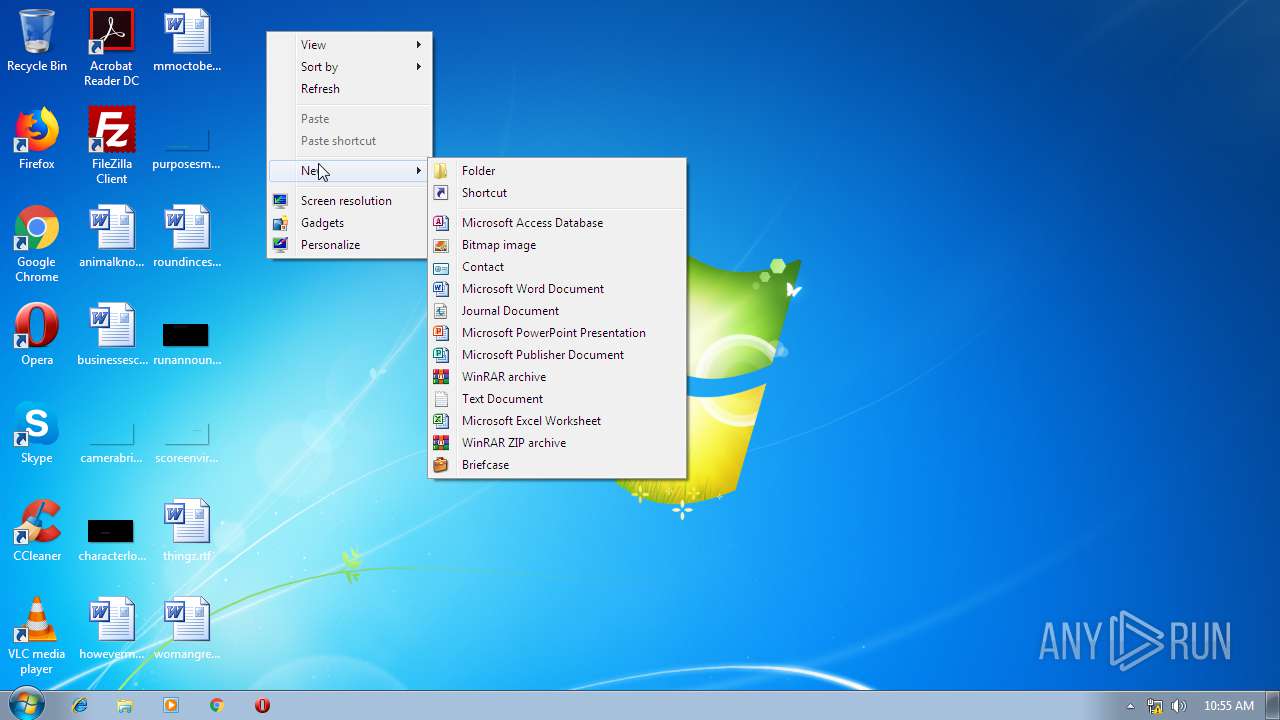
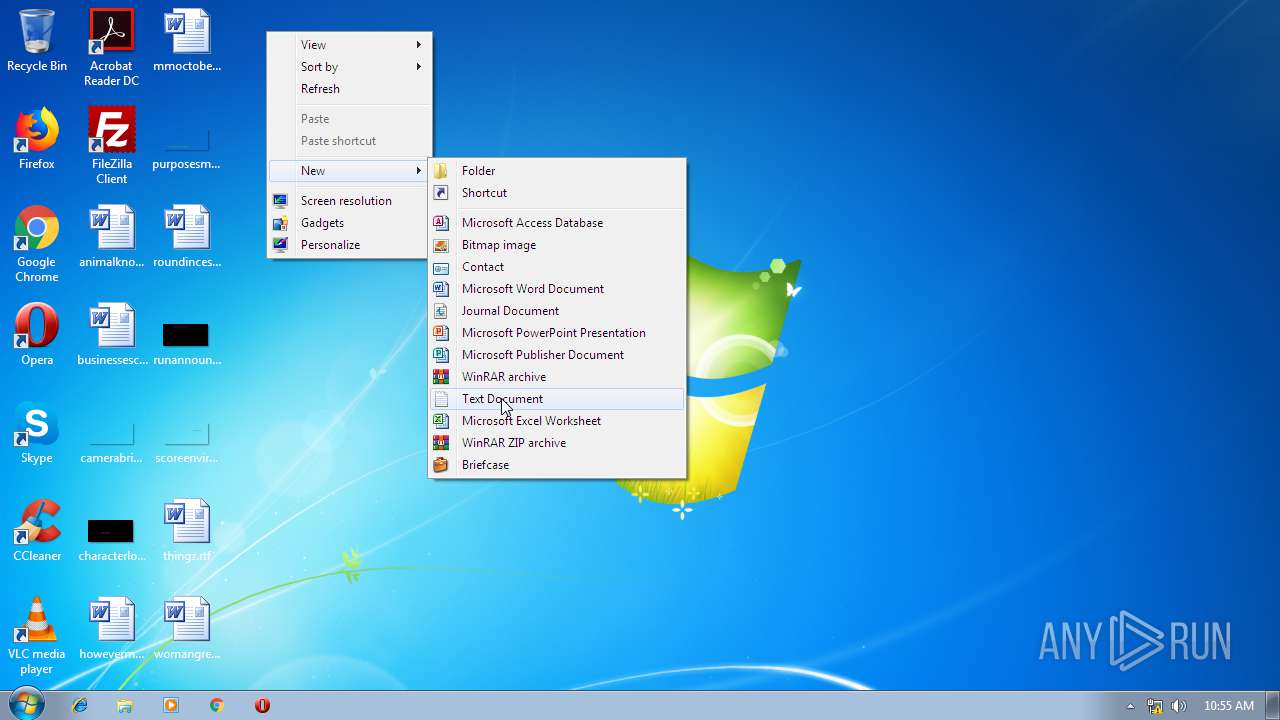
| File name: | 小猪佩奇病毒.exe |
| Full analysis: | https://app.any.run/tasks/547c8f5a-9369-4f89-9b4c-9af6fc179e15 |
| Verdict: | Malicious activity |
| Analysis date: | December 14, 2018, 10:52:18 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 9C86085906E801C97A56DE6AC4A824BA |
| SHA1: | 934F5B3236E90597AFD74EC1DCE2D013182CE4E6 |
| SHA256: | F294FD0554A24564459EE99ED4EEF6345959B97D1075FADCF50D6791A38906E4 |
| SSDEEP: | 24576:0O61wqI3S1/l6j51IuCH4nkd6l7obbFGN:0O61wS1/loKuydG |
MALICIOUS
Changes the autorun value in the registry
- 小猪佩奇病毒.exe (PID: 3508)
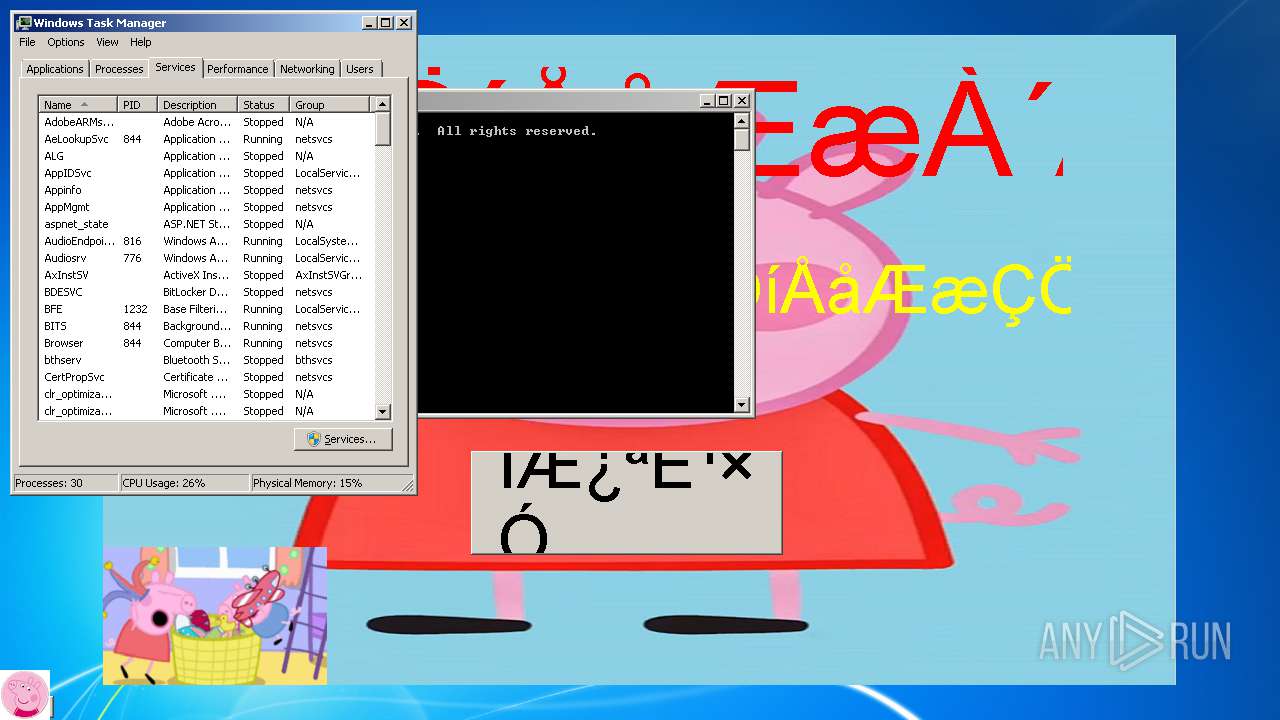
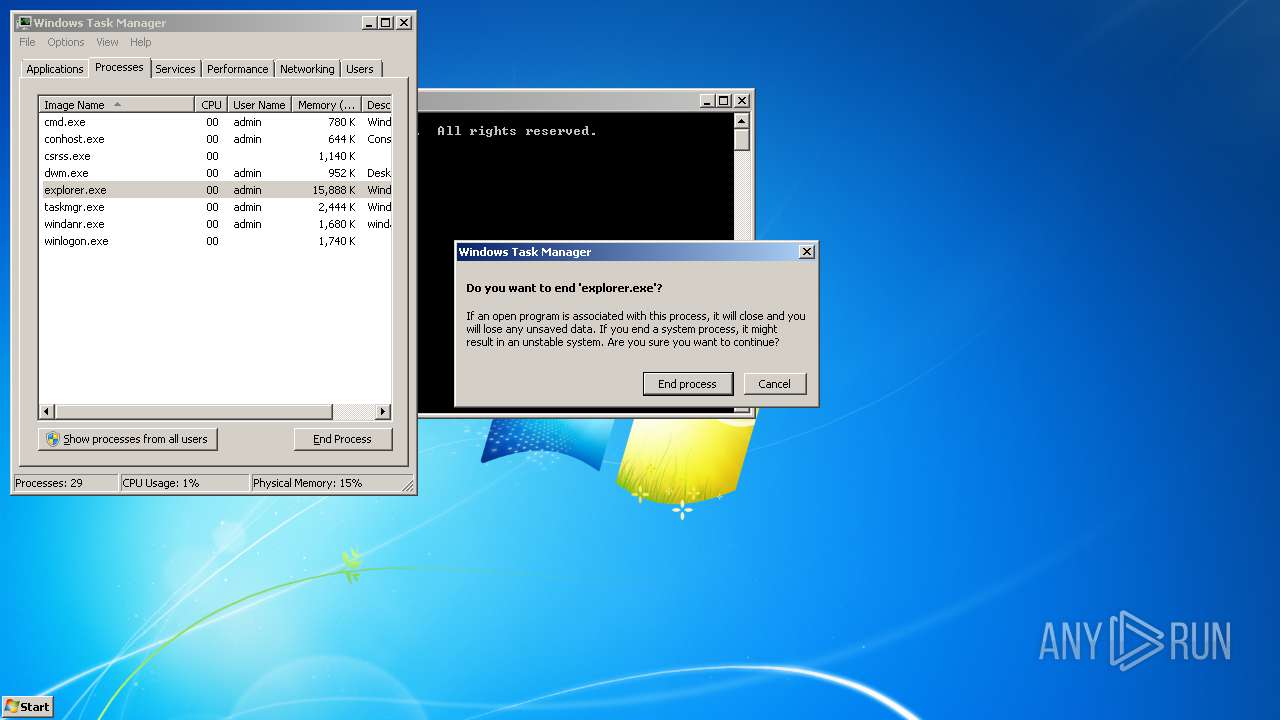
Loads the Task Scheduler COM API
- explorer.exe (PID: 2536)
SUSPICIOUS
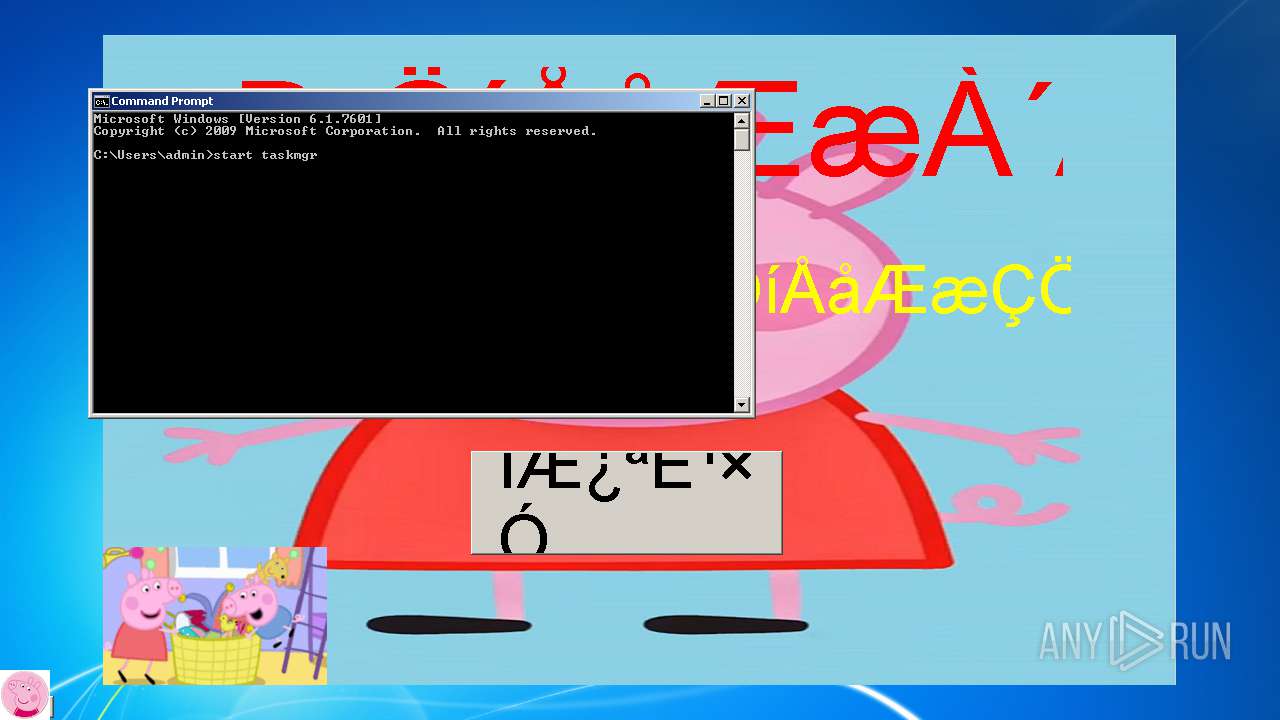
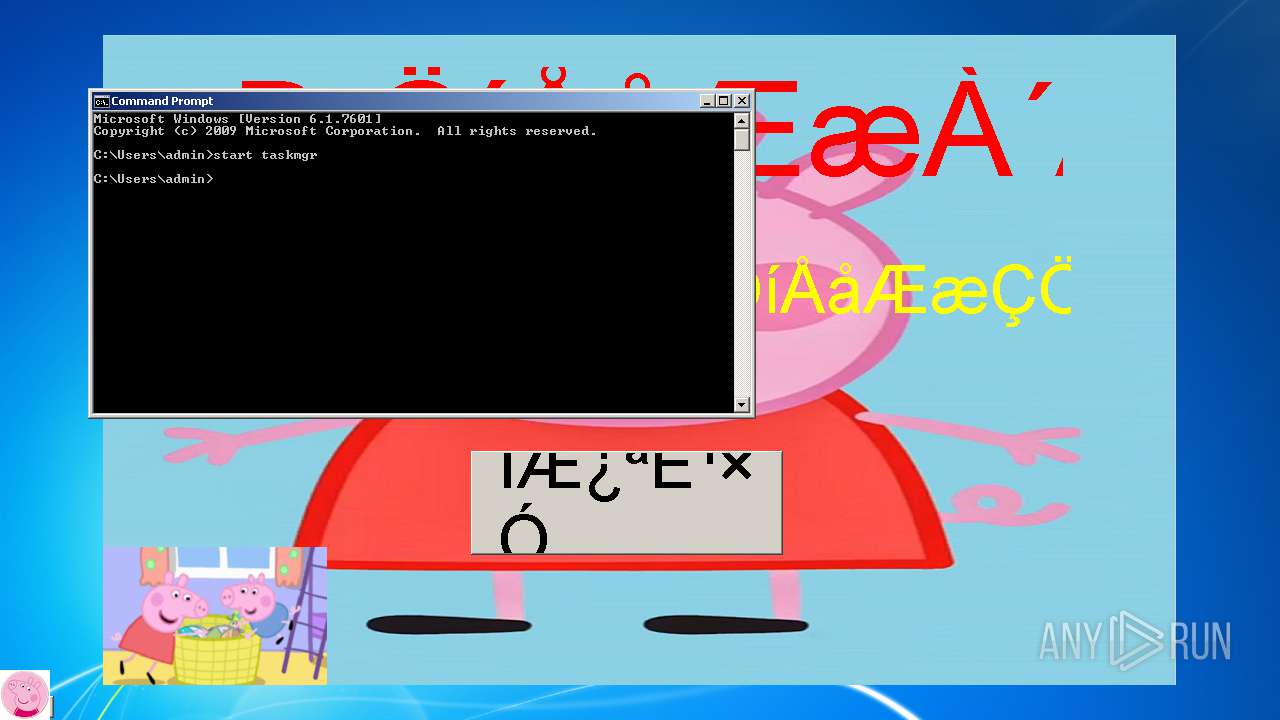
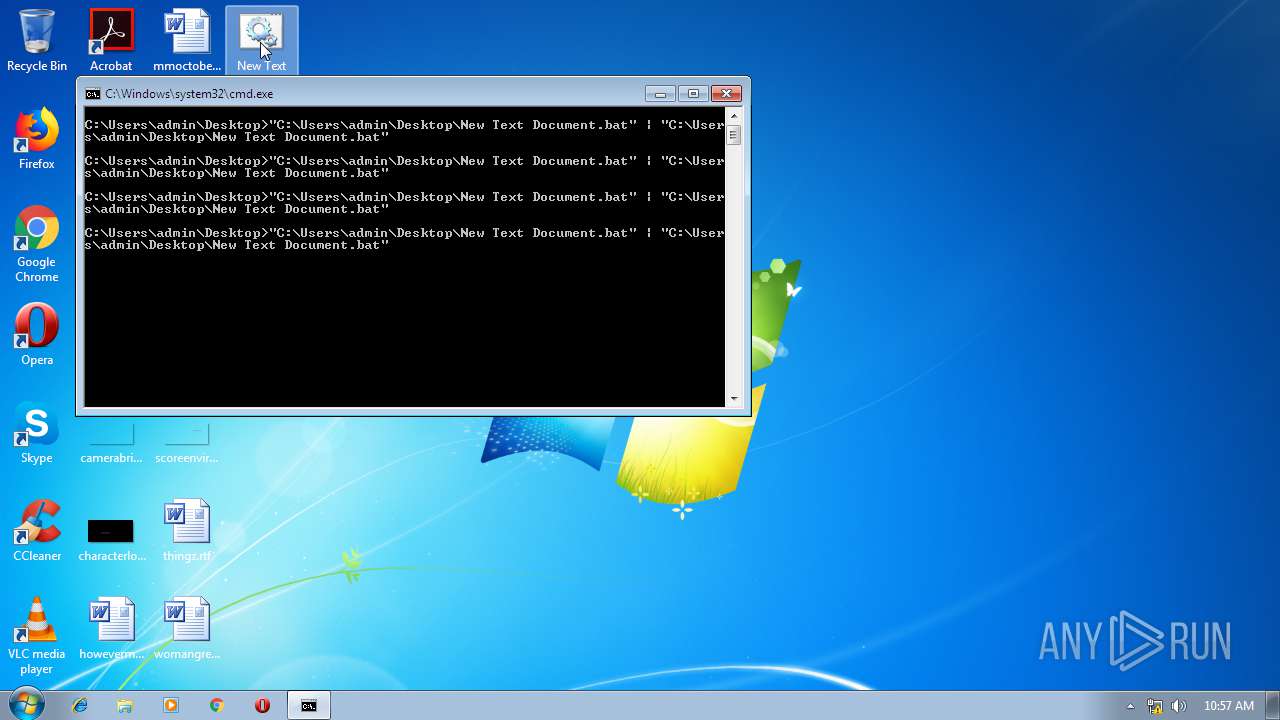
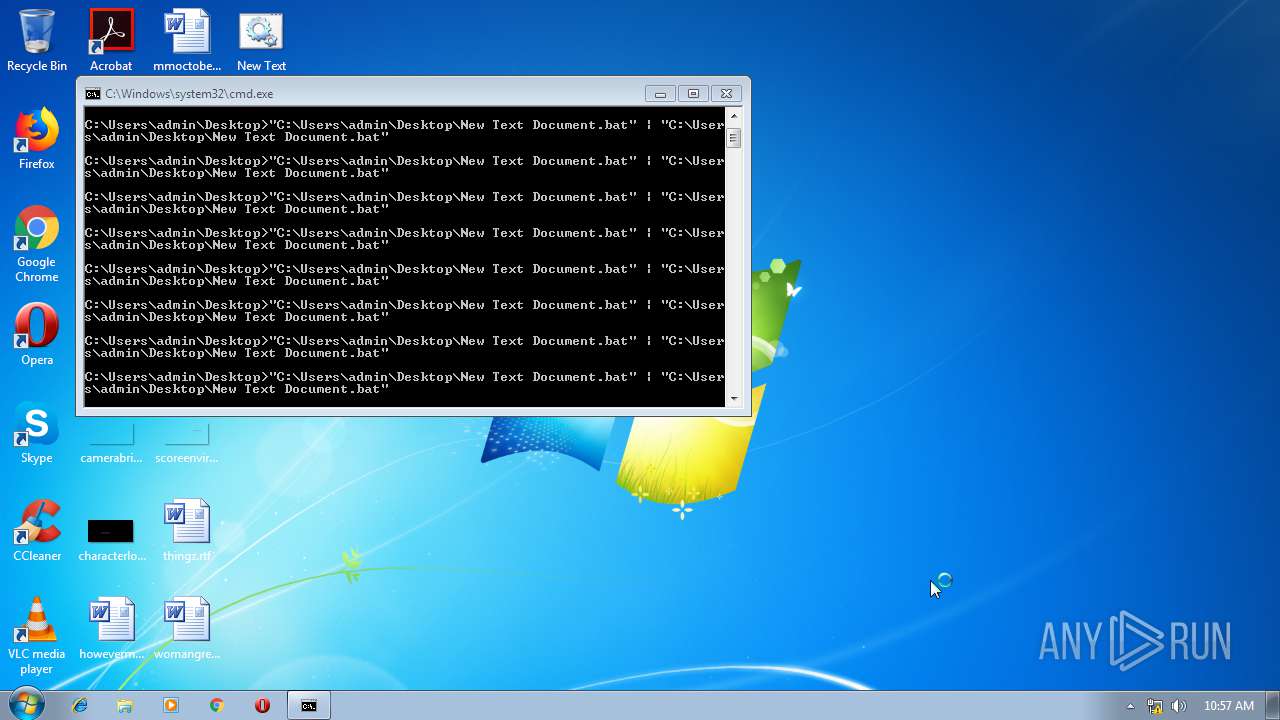
Starts CMD.EXE for commands execution
- explorer.exe (PID: 2536)
- cmd.exe (PID: 624)
- cmd.exe (PID: 3548)
- cmd.exe (PID: 2508)
- cmd.exe (PID: 940)
- cmd.exe (PID: 3992)
- cmd.exe (PID: 3412)
- cmd.exe (PID: 3604)
- cmd.exe (PID: 1928)
- cmd.exe (PID: 4080)
- cmd.exe (PID: 3172)
- cmd.exe (PID: 3140)
- cmd.exe (PID: 3852)
- cmd.exe (PID: 2272)
- cmd.exe (PID: 3484)
- cmd.exe (PID: 3216)
- cmd.exe (PID: 3540)
- cmd.exe (PID: 2168)
- cmd.exe (PID: 2408)
- cmd.exe (PID: 1904)
- cmd.exe (PID: 3000)
- cmd.exe (PID: 3024)
- cmd.exe (PID: 3424)
- cmd.exe (PID: 3376)
- cmd.exe (PID: 3796)
- cmd.exe (PID: 3280)
- cmd.exe (PID: 3632)
- cmd.exe (PID: 1440)
- cmd.exe (PID: 1832)
- cmd.exe (PID: 3308)
- cmd.exe (PID: 2948)
- cmd.exe (PID: 2704)
- cmd.exe (PID: 2424)
- cmd.exe (PID: 1704)
- cmd.exe (PID: 3948)
- cmd.exe (PID: 1828)
- cmd.exe (PID: 4092)
- cmd.exe (PID: 2896)
- cmd.exe (PID: 3532)
- cmd.exe (PID: 2472)
- cmd.exe (PID: 2248)
- cmd.exe (PID: 636)
- cmd.exe (PID: 952)
- cmd.exe (PID: 1164)
- cmd.exe (PID: 2824)
- cmd.exe (PID: 2084)
- cmd.exe (PID: 2764)
- cmd.exe (PID: 2336)
- cmd.exe (PID: 3084)
- cmd.exe (PID: 3636)
- cmd.exe (PID: 4060)
- cmd.exe (PID: 2068)
- cmd.exe (PID: 2680)
- cmd.exe (PID: 3428)
- cmd.exe (PID: 972)
- cmd.exe (PID: 296)
- cmd.exe (PID: 476)
- cmd.exe (PID: 3620)
- cmd.exe (PID: 2776)
- cmd.exe (PID: 968)
- cmd.exe (PID: 2156)
- cmd.exe (PID: 1228)
- cmd.exe (PID: 908)
- cmd.exe (PID: 1288)
- cmd.exe (PID: 3488)
- cmd.exe (PID: 1820)
- cmd.exe (PID: 920)
- cmd.exe (PID: 992)
- cmd.exe (PID: 2812)
- cmd.exe (PID: 1624)
- cmd.exe (PID: 3996)
- cmd.exe (PID: 2808)
- cmd.exe (PID: 3480)
- cmd.exe (PID: 2736)
- cmd.exe (PID: 564)
- cmd.exe (PID: 1248)
- cmd.exe (PID: 2904)
- cmd.exe (PID: 3884)
- cmd.exe (PID: 3572)
- cmd.exe (PID: 3072)
- cmd.exe (PID: 2700)
- cmd.exe (PID: 2212)
- cmd.exe (PID: 4020)
- cmd.exe (PID: 2616)
- cmd.exe (PID: 2304)
- cmd.exe (PID: 2544)
- cmd.exe (PID: 2624)
- cmd.exe (PID: 416)
- cmd.exe (PID: 3120)
- cmd.exe (PID: 2892)
- cmd.exe (PID: 3168)
- cmd.exe (PID: 3152)
- cmd.exe (PID: 3256)
- cmd.exe (PID: 3320)
- cmd.exe (PID: 2940)
- cmd.exe (PID: 3588)
- cmd.exe (PID: 3248)
- cmd.exe (PID: 2832)
- cmd.exe (PID: 3612)
- cmd.exe (PID: 3720)
- cmd.exe (PID: 2132)
- cmd.exe (PID: 3064)
- cmd.exe (PID: 2600)
- cmd.exe (PID: 284)
- cmd.exe (PID: 3984)
- cmd.exe (PID: 2264)
- cmd.exe (PID: 2332)
- cmd.exe (PID: 2692)
- cmd.exe (PID: 3552)
- cmd.exe (PID: 3224)
- cmd.exe (PID: 3724)
- cmd.exe (PID: 3092)
- cmd.exe (PID: 3456)
- cmd.exe (PID: 2552)
- cmd.exe (PID: 2580)
- cmd.exe (PID: 3260)
- cmd.exe (PID: 3304)
- cmd.exe (PID: 3580)
- cmd.exe (PID: 552)
- cmd.exe (PID: 1036)
- cmd.exe (PID: 504)
- cmd.exe (PID: 3856)
- cmd.exe (PID: 3276)
- cmd.exe (PID: 3068)
- cmd.exe (PID: 2936)
- cmd.exe (PID: 2784)
- cmd.exe (PID: 2696)
- cmd.exe (PID: 2276)
- cmd.exe (PID: 2640)
- cmd.exe (PID: 1140)
- cmd.exe (PID: 2976)
- cmd.exe (PID: 3492)
- cmd.exe (PID: 3880)
- cmd.exe (PID: 1944)
- cmd.exe (PID: 4076)
- cmd.exe (PID: 4012)
- cmd.exe (PID: 3656)
- cmd.exe (PID: 3820)
- cmd.exe (PID: 1584)
- cmd.exe (PID: 1868)
- cmd.exe (PID: 3500)
- cmd.exe (PID: 788)
Creates files in the user directory
- explorer.exe (PID: 2536)
Application launched itself
- cmd.exe (PID: 2508)
- cmd.exe (PID: 3992)
- cmd.exe (PID: 1928)
- cmd.exe (PID: 3140)
- cmd.exe (PID: 3172)
- cmd.exe (PID: 4080)
- cmd.exe (PID: 3216)
- cmd.exe (PID: 3540)
- cmd.exe (PID: 2168)
- cmd.exe (PID: 3484)
- cmd.exe (PID: 3852)
- cmd.exe (PID: 2272)
- cmd.exe (PID: 1904)
- cmd.exe (PID: 3024)
- cmd.exe (PID: 2408)
- cmd.exe (PID: 3000)
- cmd.exe (PID: 3424)
- cmd.exe (PID: 3280)
- cmd.exe (PID: 3796)
- cmd.exe (PID: 3376)
- cmd.exe (PID: 3632)
- cmd.exe (PID: 3308)
- cmd.exe (PID: 2424)
- cmd.exe (PID: 1704)
- cmd.exe (PID: 1820)
- cmd.exe (PID: 1828)
- cmd.exe (PID: 2896)
- cmd.exe (PID: 4092)
- cmd.exe (PID: 636)
- cmd.exe (PID: 3532)
- cmd.exe (PID: 2824)
- cmd.exe (PID: 1164)
- cmd.exe (PID: 908)
- cmd.exe (PID: 2336)
- cmd.exe (PID: 2764)
- cmd.exe (PID: 3428)
- cmd.exe (PID: 2680)
- cmd.exe (PID: 296)
- cmd.exe (PID: 972)
- cmd.exe (PID: 3084)
- cmd.exe (PID: 4060)
- cmd.exe (PID: 2068)
- cmd.exe (PID: 2156)
- cmd.exe (PID: 2776)
- cmd.exe (PID: 968)
- cmd.exe (PID: 3488)
- cmd.exe (PID: 1228)
- cmd.exe (PID: 1288)
- cmd.exe (PID: 2808)
- cmd.exe (PID: 476)
- cmd.exe (PID: 1440)
- cmd.exe (PID: 952)
- cmd.exe (PID: 3948)
- cmd.exe (PID: 3620)
- cmd.exe (PID: 992)
- cmd.exe (PID: 2084)
- cmd.exe (PID: 2736)
- cmd.exe (PID: 2812)
- cmd.exe (PID: 1624)
- cmd.exe (PID: 3996)
- cmd.exe (PID: 3480)
- cmd.exe (PID: 920)
- cmd.exe (PID: 2904)
- cmd.exe (PID: 3884)
- cmd.exe (PID: 3072)
- cmd.exe (PID: 2700)
- cmd.exe (PID: 2212)
- cmd.exe (PID: 1944)
- cmd.exe (PID: 564)
- cmd.exe (PID: 1248)
- cmd.exe (PID: 4020)
- cmd.exe (PID: 2304)
- cmd.exe (PID: 2544)
- cmd.exe (PID: 3120)
- cmd.exe (PID: 2624)
- cmd.exe (PID: 3588)
- cmd.exe (PID: 416)
- cmd.exe (PID: 2616)
- cmd.exe (PID: 3168)
- cmd.exe (PID: 3320)
- cmd.exe (PID: 2940)
- cmd.exe (PID: 3152)
- cmd.exe (PID: 3248)
- cmd.exe (PID: 2892)
- cmd.exe (PID: 3256)
- cmd.exe (PID: 3984)
- cmd.exe (PID: 3720)
- cmd.exe (PID: 3612)
- cmd.exe (PID: 3064)
- cmd.exe (PID: 2132)
- cmd.exe (PID: 2600)
- cmd.exe (PID: 3456)
- cmd.exe (PID: 284)
- cmd.exe (PID: 2832)
- cmd.exe (PID: 2692)
- cmd.exe (PID: 2332)
- cmd.exe (PID: 3552)
- cmd.exe (PID: 3224)
- cmd.exe (PID: 3724)
- cmd.exe (PID: 3092)
- cmd.exe (PID: 2264)
- cmd.exe (PID: 2580)
- cmd.exe (PID: 3260)
- cmd.exe (PID: 3580)
- cmd.exe (PID: 2936)
- cmd.exe (PID: 2784)
- cmd.exe (PID: 2696)
- cmd.exe (PID: 552)
- cmd.exe (PID: 2552)
- cmd.exe (PID: 3304)
- cmd.exe (PID: 1036)
- cmd.exe (PID: 504)
- cmd.exe (PID: 3856)
- cmd.exe (PID: 3068)
- cmd.exe (PID: 4076)
- cmd.exe (PID: 3572)
- cmd.exe (PID: 3276)
- cmd.exe (PID: 2976)
- cmd.exe (PID: 1140)
- cmd.exe (PID: 3492)
- cmd.exe (PID: 3880)
- cmd.exe (PID: 788)
- cmd.exe (PID: 4012)
- cmd.exe (PID: 2276)
- cmd.exe (PID: 2640)
- cmd.exe (PID: 1868)
- cmd.exe (PID: 3500)
- cmd.exe (PID: 4468)
- cmd.exe (PID: 4196)
- cmd.exe (PID: 3648)
- cmd.exe (PID: 4252)
- cmd.exe (PID: 4552)
- cmd.exe (PID: 3656)
- cmd.exe (PID: 3820)
- cmd.exe (PID: 1584)
- cmd.exe (PID: 2296)
- cmd.exe (PID: 2608)
- cmd.exe (PID: 2716)
- cmd.exe (PID: 5064)
- cmd.exe (PID: 880)
- cmd.exe (PID: 5144)
- cmd.exe (PID: 5248)
- cmd.exe (PID: 1972)
- cmd.exe (PID: 5284)
- cmd.exe (PID: 2104)
- cmd.exe (PID: 4744)
- cmd.exe (PID: 2836)
- cmd.exe (PID: 4996)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:02:21 06:48:25+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 7.1 |
| CodeSize: | 540672 |
| InitializedDataSize: | 675840 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x652e6 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Chinese (Simplified) |
| CharacterSet: | Unicode |
| FileVersion: | 1.0.0.0 |
| FileDescription: | 易语言程序 |
| ProductName: | 易语言程序 |
| ProductVersion: | 1.0.0.0 |
| LegalCopyright: | 作者版权所有 请尊重并使用正版 |
| Comments: | 本程序使用易语言编写(http://www.dywt.com.cn) |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 21-Feb-2018 05:48:25 |
| Detected languages: |
|
| FileVersion: | 1.0.0.0 |
| FileDescription: | 易语言程序 |
| ProductName: | 易语言程序 |
| ProductVersion: | 1.0.0.0 |
| LegalCopyright: | 作者版权所有 请尊重并使用正版 |
| Comments: | 本程序使用易语言编写(http://www.dywt.com.cn) |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000128 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 4 |
| Time date stamp: | 21-Feb-2018 05:48:25 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x0008312E | 0x00084000 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.53423 |
.rdata | 0x00085000 | 0x0008C106 | 0x0008D000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 7.66931 |
.data | 0x00112000 | 0x00039E6A | 0x00012000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 5.04147 |
.rsrc | 0x0014C000 | 0x00005B20 | 0x00006000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.78541 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.07695 | 461 | Latin 1 / Western European | UNKNOWN | RT_MANIFEST |
2 | 2.18858 | 296 | Latin 1 / Western European | Chinese - PRC | RT_ICON |
3 | 2.45415 | 296 | Latin 1 / Western European | UNKNOWN | RT_ICON |
4 | 2.84053 | 744 | Latin 1 / Western European | UNKNOWN | RT_ICON |
5 | 2.61843 | 1640 | Latin 1 / Western European | UNKNOWN | RT_ICON |
127 | 1.4183 | 12 | Latin 1 / Western European | Chinese - PRC | RT_MENU |
150 | 3.06278 | 152 | Latin 1 / Western European | Chinese - PRC | RT_DIALOG |
286 | 3.5561 | 378 | Latin 1 / Western European | Chinese - PRC | RT_DIALOG |
554 | 3.78697 | 250 | Latin 1 / Western European | Chinese - PRC | RT_DIALOG |
1031 | 3.67246 | 584 | Latin 1 / Western European | Chinese - PRC | RT_BITMAP |
Imports
ADVAPI32.dll |
COMCTL32.dll |
GDI32.dll |
KERNEL32.dll |
OLEAUT32.dll |
SHELL32.dll |
USER32.dll |
WINMM.dll |
WINSPOOL.DRV |
WS2_32.dll |
Total processes
351
Monitored processes
308
Malicious processes
72
Suspicious processes
65
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
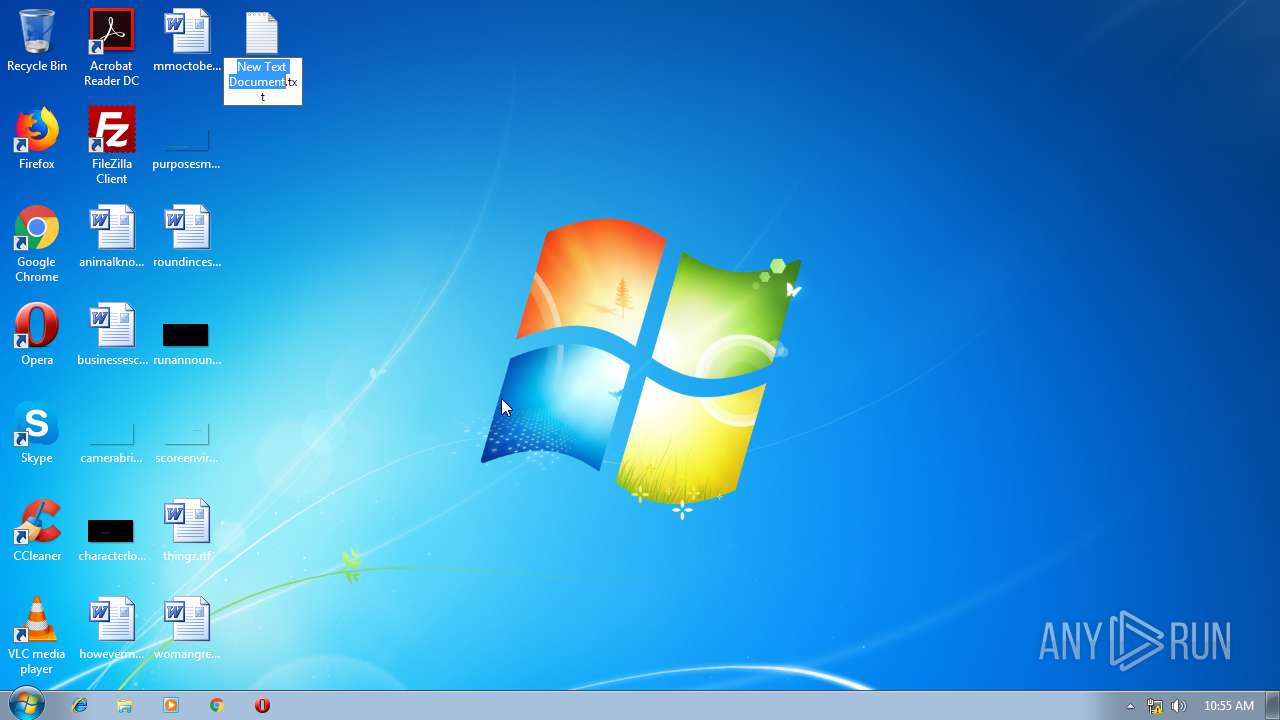
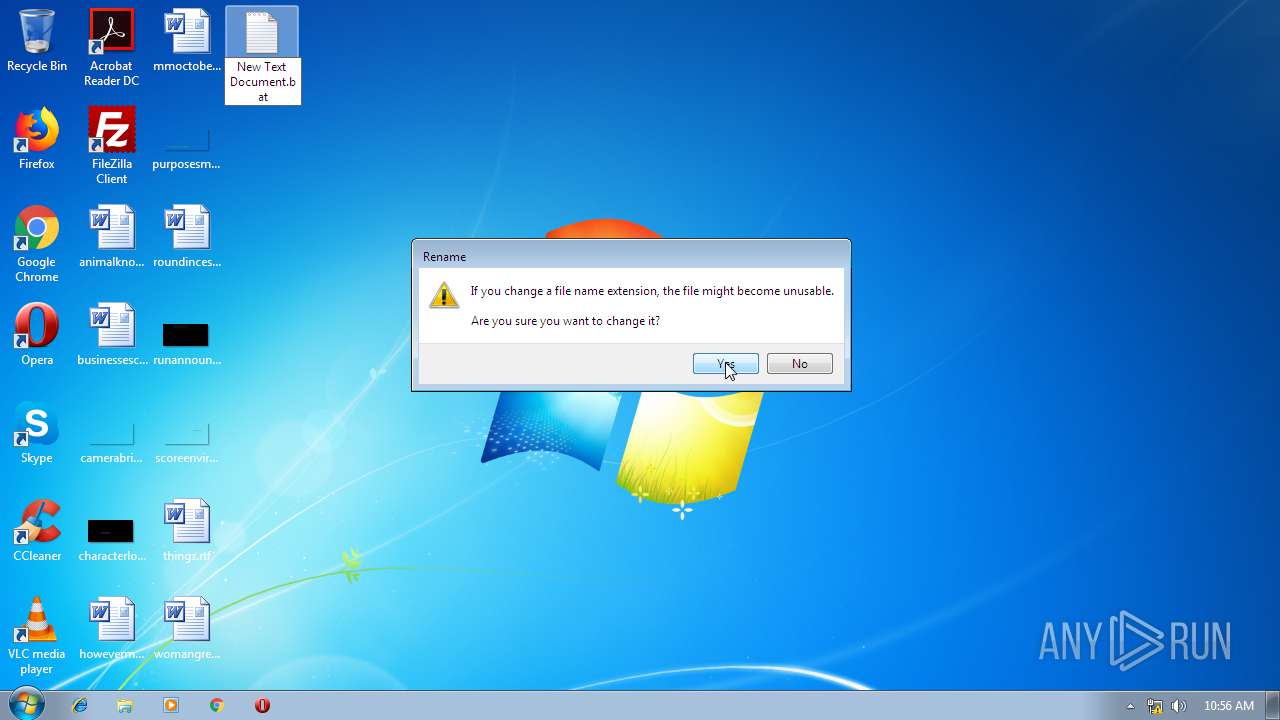
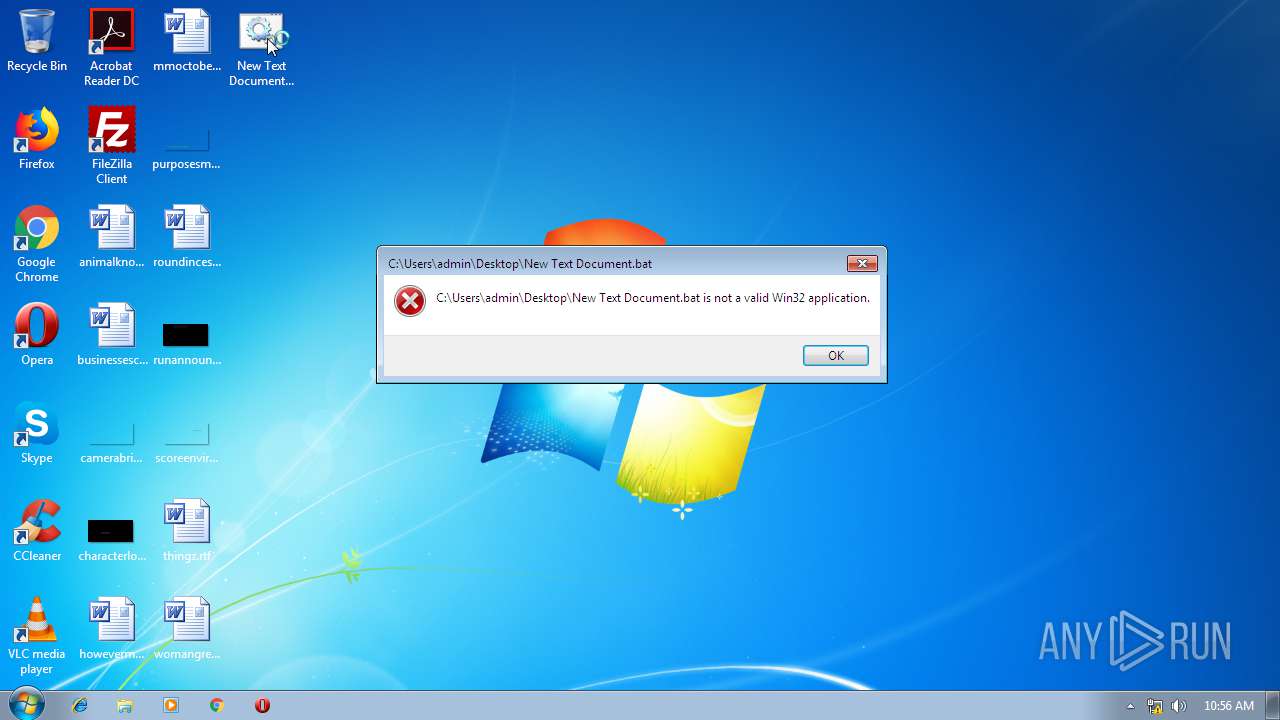
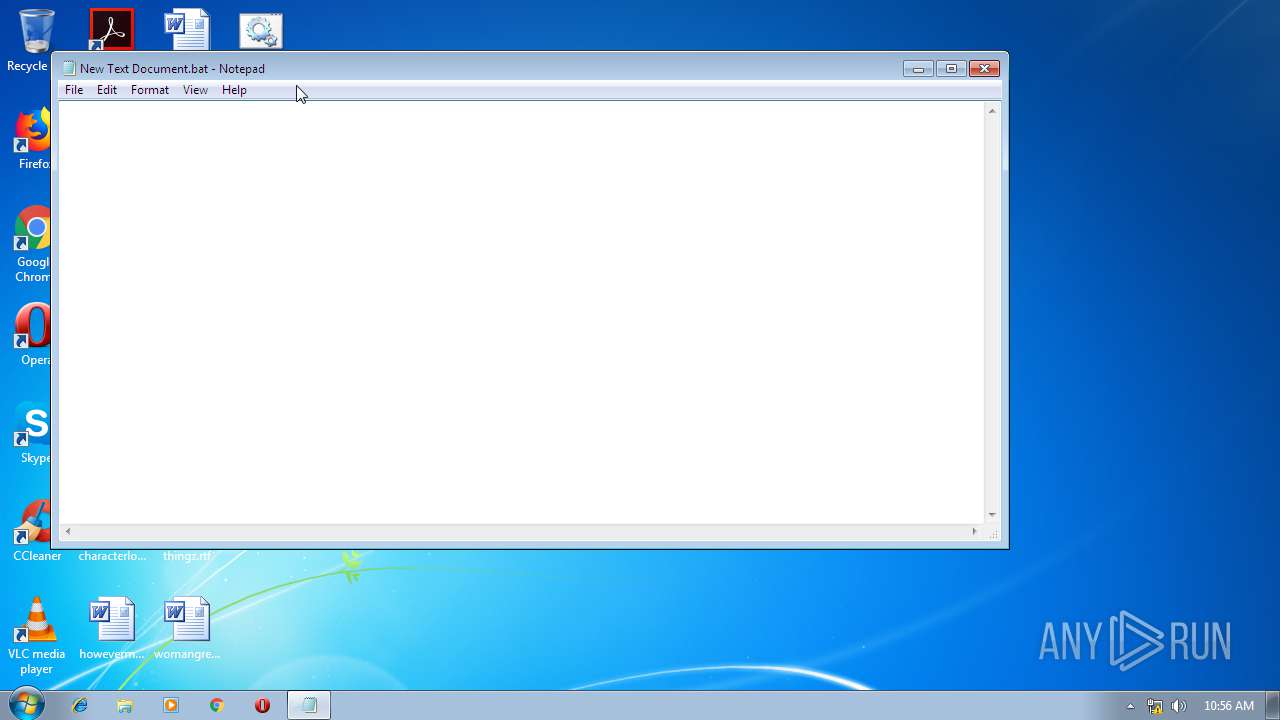
| 284 | C:\Windows\system32\cmd.exe /S /D /c" "C:\Users\admin\Desktop\New Text Document.bat"" | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 296 | C:\Windows\system32\cmd.exe /S /D /c" "C:\Users\admin\Desktop\New Text Document.bat"" | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 348 | C:\Windows\system32\cmd.exe /S /D /c" "C:\Users\admin\Desktop\New Text Document.bat"" | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 416 | C:\Windows\system32\cmd.exe /S /D /c" "C:\Users\admin\Desktop\New Text Document.bat"" | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 476 | C:\Windows\system32\cmd.exe /S /D /c" "C:\Users\admin\Desktop\New Text Document.bat"" | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 504 | C:\Windows\system32\cmd.exe /S /D /c" "C:\Users\admin\Desktop\New Text Document.bat"" | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 552 | C:\Windows\system32\cmd.exe /S /D /c" "C:\Users\admin\Desktop\New Text Document.bat"" | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 564 | C:\Windows\system32\cmd.exe /S /D /c" "C:\Users\admin\Desktop\New Text Document.bat"" | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 624 | C:\Windows\system32\cmd.exe /S /D /c" "C:\Users\admin\Desktop\New Text Document.bat"" | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 636 | C:\Windows\system32\cmd.exe /S /D /c" "C:\Users\admin\Desktop\New Text Document.bat"" | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
6 687
Read events
5 962
Write events
721
Delete events
4
Modification events
| (PID) Process: | (3508) 小猪佩奇病毒.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | ??????.exe |
Value: C:\Users\admin\AppData\Local\Temp\??????.exe | |||
| (PID) Process: | (3508) 小猪佩奇病毒.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\.exe |
| Operation: | write | Name: | |
Value: exe | |||
| (PID) Process: | (3508) 小猪佩奇病毒.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | GlobalAssocChangedCounter |
Value: 52 | |||
| (PID) Process: | (2268) taskmgr.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2268) taskmgr.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2268) taskmgr.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | {S38OS404-1Q43-42S2-9305-67QR0O28SP23}\rkcybere.rkr |
Value: 000000000700000009000000A8D90300000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BFFFFFFFFFD0AC926D9B93D40100000000 | |||
| (PID) Process: | (2268) taskmgr.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | HRZR_PGYFRFFVBA |
Value: 00000000300000004200000080E81500090000000B000000DCC402007B00370043003500410034003000450046002D0041003000460042002D0034004200460043002D0038003700340041002D004300300046003200450030004200390046004100380045007D005C00410064006F00620065005C004100630072006F0062006100740020005200650061006400650072002000440043005C005200650061006400650072005C004100630072006F0052006400330032002E0065007800650000000000D09866060000000034E82802C05D5A740200000002000000000C00940F000000E8E82802010000000400000001000000010000006B001001D098660605000000D098660602020000E20101AE2B51EA0088E7280239B58D76E20101AE24E82802130000000400000030000000120000001D000000130000001D0000000E00000012000000020000003200000014000000E387EE7A38E82802F3AE5B7400574100E20101AE010000000000000011000000F0443500E8443500A14A52740000000020E800001F51EA7AD0E728028291917520E828028CD800006B51EA7AE4E72802B69C917590D8D4035C0000000401000084F2280244F228026B4E317411000000F0443500E8443500A8EAD403FA4F31740000000074E80000AB5EEA7A24E828028291917574E8280228E8280227959175000000008CD8D40350E82802CD9491758CD8D403FCE8280200D4D403E19491750000000000D4D403FCE8280258E82802000000000F000000E21705007B00440036003500320033003100420030002D0042003200460031002D0034003800350037002D0041003400430045002D004100380045003700430036004500410037004400320037007D005C007400610073006B006D00670072002E006500780065000000370274E8370290E837026C873C750100000000000000ACE837027F873C75FF13A66B0000000014EE37020200000070005C000F5C2A73694F4759000000000000817254E8370200000000F8EC370265E13D75E77CAD1CFEFFFFFF7F873C75F36B3C7582BA3C75B04840750200000001000000A048407501000000C8E83702C5B83C75A848407501000000C810750000000000F0E837026BB93C7500000000350100C00100000010E93702973C0A779C3C0A7727B9257501000000350100C000000000E8E83702FFFFFFFF58E93702EDE00677374C1800FEFFFFFF20E937020D6B3C7500EE3702ECEE37020000000058E93702973C0A779C3C0A776FB9257500000000ECEE370200EE370230E9370201000000D0ED3702EDE00677374C1800FEFFFFFF68E937020D6B3C757E000000ECEE3702E0ED3702F36B3C75E1863C758F16A66BECEE370211000000B8457800B0457800ECEE3702FCE900002251A06BACE937028291F075FCE93702B0E937022795F075000000005459EE02D8E93702CD94F0755459EE0284EA3702C854EE02E194F07500000000C854EE0284EA3702E0E93702090000000B000000DCC402007B00370043003500410034003000450046002D0041003000460042002D0034004200460043002D0038003700340041002D004300300046003200450030004200390046004100380045007D005C00410064006F00620065005C004100630072006F0062006100740020005200650061006400650072002000440043005C005200650061006400650072005C004100630072006F0052006400330032002E0065007800650000000000D09866060000000034E82802C05D5A740200000002000000000C00940F000000E8E82802010000000400000001000000010000006B001001D098660605000000D098660602020000E20101AE2B51EA0088E7280239B58D76E20101AE24E82802130000000400000030000000120000001D000000130000001D0000000E00000012000000020000003200000014000000E387EE7A38E82802F3AE5B7400574100E20101AE010000000000000011000000F0443500E8443500A14A52740000000020E800001F51EA7AD0E728028291917520E828028CD800006B51EA7AE4E72802B69C917590D8D4035C0000000401000084F2280244F228026B4E317411000000F0443500E8443500A8EAD403FA4F31740000000074E80000AB5EEA7A24E828028291917574E8280228E8280227959175000000008CD8D40350E82802CD9491758CD8D403FCE8280200D4D403E19491750000000000D4D403FCE8280258E82802 | |||
| (PID) Process: | (2268) taskmgr.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2536) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2536) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | CleanShutdown |
Value: 0 | |||
Executable files
0
Suspicious files
1
Text files
5
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2536 | explorer.exe | C:\Users\admin\Desktop\New Text Document.bat | — | |
MD5:— | SHA256:— | |||
| 3508 | 小猪佩奇病毒.exe | C:\Users\admin\AppData\Local\VirtualStore\1.bmp | image | |
MD5:— | SHA256:— | |||
| 2536 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations\7e4dca80246863e3.automaticDestinations-ms | automaticdestinations-ms | |
MD5:— | SHA256:— | |||
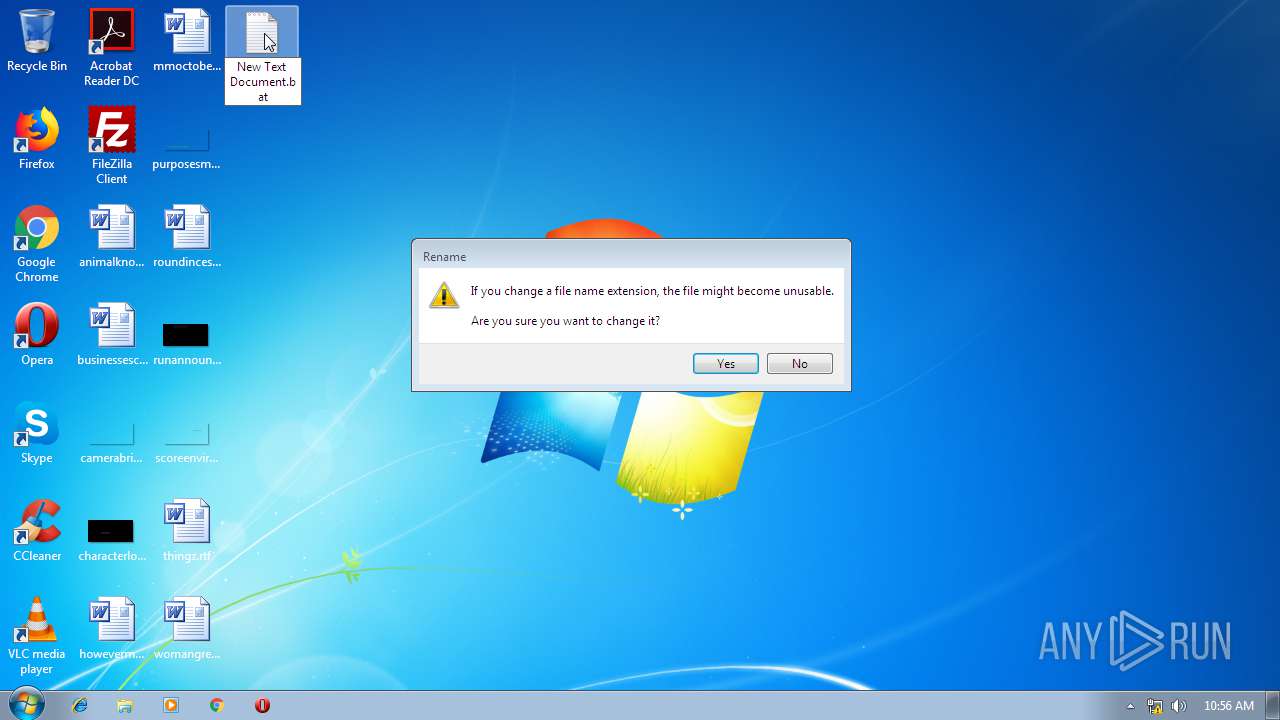
| 3100 | NOTEPAD.EXE | C:\Users\admin\Desktop\New Text Document.bat | text | |
MD5:3808D82ED52876C3DDA66FBF4CB142C8 | SHA256:11EA65B2709BB714F059CF53767F7EE5AE6DEFE5B5D548E32375E65571B66015 | |||
| 2536 | explorer.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Explorer\thumbcache_idx.db | binary | |
MD5:— | SHA256:— | |||
| 2536 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\Appearance and Personalization.lnk | lnk | |
MD5:09383AFE23B505A7BCCB775B9C1E26B9 | SHA256:77F67F1FAD901634AB4B5F0EFA51CDDA21C7F5DC6E32FA457AA6DA383335727A | |||
| 3508 | 小猪佩奇病毒.exe | C:\Users\admin\AppData\Local\VirtualStore\1.ico | image | |
MD5:— | SHA256:— | |||
| 1160 | sidebar.exe | C:\Users\admin\AppData\Local\Microsoft\Windows Sidebar\Settings.ini | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report