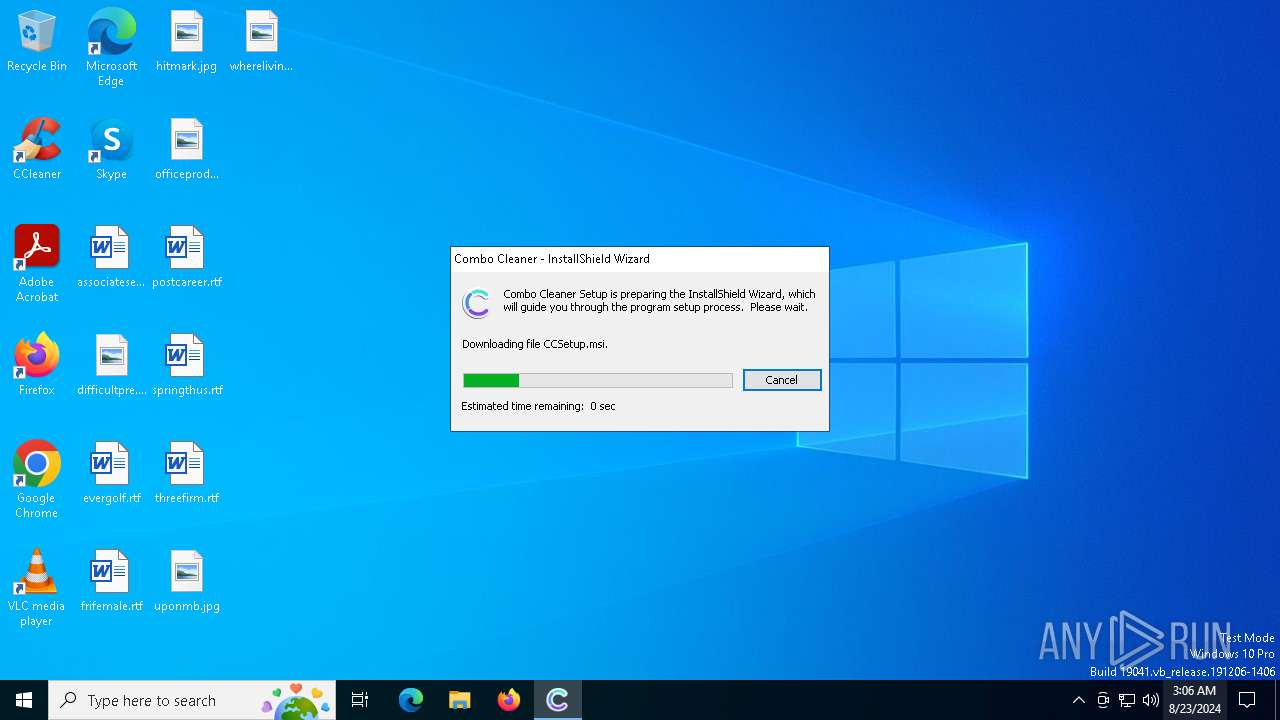
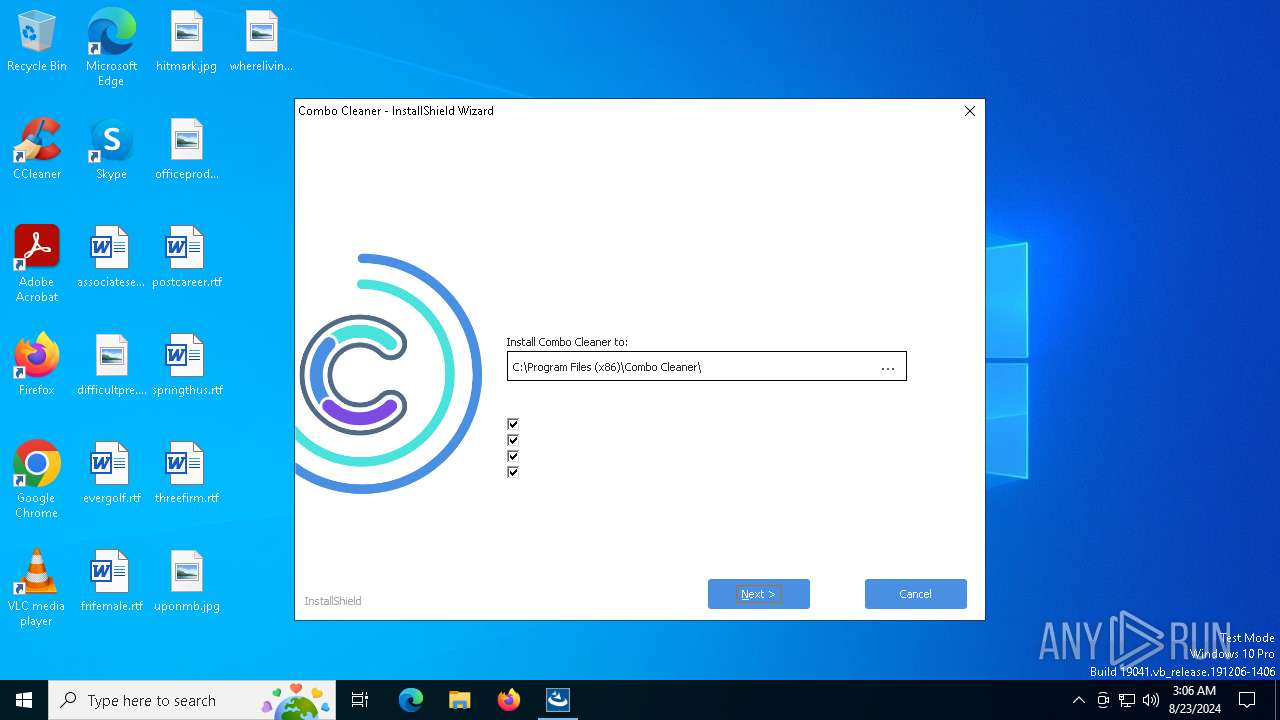
| File name: | CCSetup.exe |
| Full analysis: | https://app.any.run/tasks/f77571ee-3898-476c-96a4-b3e709064367 |
| Verdict: | Malicious activity |
| Analysis date: | August 23, 2024, 03:05:53 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | FEC08CD443DA550781BB3F12CF64439B |
| SHA1: | CE0607A0D2E1E87BC6F02DCCD8BD242FD64402E6 |
| SHA256: | F2945E170B8F97CDB773D4E271C9F8892F585372262EBB773F1AB9008BD1787A |
| SSDEEP: | 98304:P9t0taQEx5Tf+S+PqFe+Qo7LJwhYpL6Gee+kXE0ulNadVeewWOUl48f1Z4qmtMqC:CE |
MALICIOUS
Changes the autorun value in the registry
- rundll32.exe (PID: 2480)
- rundll32.exe (PID: 7000)
- rundll32.exe (PID: 6940)
- CCSetup.exe (PID: 6872)
- ComboCleaner.WinService.exe (PID: 6716)
Starts NET.EXE for service management
- cmd.exe (PID: 4592)
- cmd.exe (PID: 6112)
- net.exe (PID: 2368)
- net.exe (PID: 1076)
- net.exe (PID: 4284)
- cmd.exe (PID: 6660)
SUSPICIOUS
Drops the executable file immediately after the start
- CCSetup.exe (PID: 6848)
- CCSetup.exe (PID: 6872)
- msiexec.exe (PID: 6956)
Starts itself from another location
- CCSetup.exe (PID: 6848)
Executable content was dropped or overwritten
- CCSetup.exe (PID: 6848)
- CCSetup.exe (PID: 6872)
- rundll32.exe (PID: 2480)
- rundll32.exe (PID: 7000)
- rundll32.exe (PID: 6940)
Checks Windows Trust Settings
- CCSetup.exe (PID: 6872)
- msiexec.exe (PID: 6956)
- ComboCleaner.WinService.exe (PID: 6716)
- ComboCleaner.Guard.exe (PID: 6244)
- ComboCleaner.exe (PID: 3272)
Reads the Windows owner or organization settings
- CCSetup.exe (PID: 6872)
- msiexec.exe (PID: 6956)
Reads security settings of Internet Explorer
- CCSetup.exe (PID: 6872)
- msiexec.exe (PID: 6956)
- ComboCleaner.WinService.exe (PID: 6716)
- ComboCleaner.exe (PID: 3800)
- ComboCleaner.exe (PID: 3272)
- ComboCleaner.Guard.exe (PID: 6244)
Starts CMD.EXE for commands execution
- CCSetup.exe (PID: 6872)
- ComboCleaner.WinService.exe (PID: 6716)
Uses DRIVERQUERY.EXE to obtain a list of installed device drivers
- cmd.exe (PID: 6504)
Reads Microsoft Outlook installation path
- CCSetup.exe (PID: 6872)
Drops a system driver (possible attempt to evade defenses)
- msiexec.exe (PID: 6956)
- rundll32.exe (PID: 2480)
- rundll32.exe (PID: 7000)
- rundll32.exe (PID: 6940)
Searches for installed software
- CCSetup.exe (PID: 6872)
- ComboCleaner.WinService.exe (PID: 6716)
Creates a software uninstall entry
- CCSetup.exe (PID: 6872)
- ComboCleaner.WinService.exe (PID: 6716)
Process drops legitimate windows executable
- msiexec.exe (PID: 6956)
Reads the date of Windows installation
- CCSetup.exe (PID: 6872)
- ComboCleaner.WinService.exe (PID: 6716)
Uses RUNDLL32.EXE to load library
- CCSetup.exe (PID: 6872)
Creates or modifies Windows services
- rundll32.exe (PID: 7000)
- rundll32.exe (PID: 6940)
- ComboCleaner.WinService.exe (PID: 6716)
Executes as Windows Service
- ComboCleaner.WinService.exe (PID: 6716)
- ComboCleaner.Guard.exe (PID: 6244)
- WmiApSrv.exe (PID: 6840)
- WmiApSrv.exe (PID: 6172)
Application launched itself
- ComboCleaner.exe (PID: 3800)
Reads Internet Explorer settings
- CCSetup.exe (PID: 6872)
The process checks if it is being run in the virtual environment
- ComboCleaner.WinService.exe (PID: 6716)
The process deletes folder without confirmation
- CCSetup.exe (PID: 6872)
INFO
Reads the computer name
- CCSetup.exe (PID: 6872)
- CCSetup.exe (PID: 6848)
- msiexec.exe (PID: 6956)
- msiexec.exe (PID: 7072)
- ISBEW64.exe (PID: 7132)
- ISBEW64.exe (PID: 6724)
- ISBEW64.exe (PID: 4672)
- ISBEW64.exe (PID: 6580)
- ISBEW64.exe (PID: 2180)
- ISBEW64.exe (PID: 6240)
- ISBEW64.exe (PID: 6156)
- ISBEW64.exe (PID: 6200)
- ISBEW64.exe (PID: 6300)
- ISBEW64.exe (PID: 6332)
- msiexec.exe (PID: 6236)
- ComboCleaner.WinService.exe (PID: 6716)
- ComboCleaner.Guard.exe (PID: 6244)
- ComboCleaner.exe (PID: 3800)
- ComboCleaner.exe (PID: 3272)
Create files in a temporary directory
- CCSetup.exe (PID: 6848)
- CCSetup.exe (PID: 6872)
Checks supported languages
- CCSetup.exe (PID: 6848)
- CCSetup.exe (PID: 6872)
- msiexec.exe (PID: 6956)
- msiexec.exe (PID: 7072)
- ISBEW64.exe (PID: 4672)
- ISBEW64.exe (PID: 6580)
- ISBEW64.exe (PID: 7132)
- ISBEW64.exe (PID: 6724)
- ISBEW64.exe (PID: 2180)
- ISBEW64.exe (PID: 6200)
- ISBEW64.exe (PID: 6240)
- ISBEW64.exe (PID: 6156)
- ISBEW64.exe (PID: 6332)
- ISBEW64.exe (PID: 6300)
- msiexec.exe (PID: 6236)
- ComboCleaner.WinService.exe (PID: 6716)
- ComboCleaner.Guard.exe (PID: 6244)
- ComboCleaner.exe (PID: 3800)
- ComboCleaner.exe (PID: 3272)
Checks proxy server information
- CCSetup.exe (PID: 6872)
- ComboCleaner.exe (PID: 3272)
Reads the machine GUID from the registry
- CCSetup.exe (PID: 6872)
- msiexec.exe (PID: 6956)
- ComboCleaner.WinService.exe (PID: 6716)
- ComboCleaner.Guard.exe (PID: 6244)
- ComboCleaner.exe (PID: 3800)
- ComboCleaner.exe (PID: 3272)
Reads the software policy settings
- CCSetup.exe (PID: 6872)
- msiexec.exe (PID: 6956)
- ComboCleaner.WinService.exe (PID: 6716)
- ComboCleaner.Guard.exe (PID: 6244)
- ComboCleaner.exe (PID: 3272)
Process checks Internet Explorer phishing filters
- CCSetup.exe (PID: 6872)
Creates files or folders in the user directory
- CCSetup.exe (PID: 6872)
- ComboCleaner.exe (PID: 3272)
Executable content was dropped or overwritten
- msiexec.exe (PID: 6956)
Dropped object may contain TOR URL's
- msiexec.exe (PID: 6956)
Creates a software uninstall entry
- msiexec.exe (PID: 6956)
Process checks computer location settings
- CCSetup.exe (PID: 6872)
Creates files in the driver directory
- rundll32.exe (PID: 2480)
- rundll32.exe (PID: 7000)
- rundll32.exe (PID: 6940)
Creates files in the program directory
- CCSetup.exe (PID: 6872)
- ComboCleaner.WinService.exe (PID: 6716)
- ComboCleaner.Guard.exe (PID: 6244)
Reads the time zone
- runonce.exe (PID: 1556)
- runonce.exe (PID: 188)
- runonce.exe (PID: 6172)
- ComboCleaner.WinService.exe (PID: 6716)
Reads security settings of Internet Explorer
- runonce.exe (PID: 1556)
- runonce.exe (PID: 188)
- runonce.exe (PID: 6172)
Reads Environment values
- ComboCleaner.WinService.exe (PID: 6716)
- ComboCleaner.exe (PID: 3272)
- ComboCleaner.Guard.exe (PID: 6244)
Disables trace logs
- ComboCleaner.WinService.exe (PID: 6716)
- ComboCleaner.Guard.exe (PID: 6244)
- ComboCleaner.exe (PID: 3272)
Reads CPU info
- ComboCleaner.WinService.exe (PID: 6716)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2021:06:20 19:44:34+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 11 |
| CodeSize: | 622080 |
| InitializedDataSize: | 780288 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x59e5a |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.65.0 |
| ProductVersionNumber: | 1.0.65.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Dynamic link library |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | RCS LT |
| FileDescription: | Combo Cleaner |
| FileVersion: | 1.0.65.0 |
| InternalName: | Setup |
| LegalCopyright: | Copyright (c) 2024 RCS LT, UAB. All Rights Reserved. |
| OriginalFileName: | CCSetup.exe |
| ProductName: | Combo Cleaner |
| ProductVersion: | 1.0.65.0 |
| InternalBuildNumber: | 202227 |
| ISInternalVersion: | 26.0.720 |
| ISInternalDescription: | Setup Launcher Unicode |
Total processes
189
Monitored processes
52
Malicious processes
6
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 188 | "C:\WINDOWS\system32\runonce.exe" -r | C:\Windows\System32\runonce.exe | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Run Once Wrapper Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 188 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1064 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1076 | net start gzflt | C:\Windows\System32\net.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Net Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1124 | "C:\WINDOWS\system32\cmd.exe" /c rmdir /s /q "C:\Users\admin\AppData\Local\Temp\{20FD435F-4273-4A20-A7D3-619C3BF7F3AD}" | C:\Windows\SysWOW64\cmd.exe | — | CCSetup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1556 | "C:\WINDOWS\system32\runonce.exe" -r | C:\Windows\System32\runonce.exe | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Run Once Wrapper Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1636 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | sc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1644 | "C:\Windows\System32\grpconv.exe" -o | C:\Windows\System32\grpconv.exe | — | runonce.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Progman Group Converter Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2180 | C:\Users\admin\AppData\Local\Temp\{70320C92-2F10-4A87-B954-900468ABCA1A}\ISBEW64.exe {EFB7539B-24F3-46B6-AF6E-3B021B51EFEF}:{4097FA81-1AEE-49AC-A92D-AA5D80B39C12} | C:\Users\admin\AppData\Local\Temp\{70320C92-2F10-4A87-B954-900468ABCA1A}\ISBEW64.exe | — | CCSetup.exe | |||||||||||
User: admin Company: Flexera Integrity Level: HIGH Description: InstallShield (R) 64-bit Setup Engine Exit code: 0 Version: 26.0.720 Modules
| |||||||||||||||
| 2368 | net start trufos | C:\Windows\System32\net.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Net Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
56 731
Read events
56 283
Write events
431
Delete events
17
Modification events
| (PID) Process: | (6872) CCSetup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion |
| Operation: | delete value | Name: | %IS_PREREQ%-Combo Cleaner |
Value: | |||
| (PID) Process: | (6872) CCSetup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion |
| Operation: | delete value | Name: | %IS_PREREQF%-Combo Cleaner |
Value: | |||
| (PID) Process: | (6872) CCSetup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | delete value | Name: | ISSetupPrerequisistes |
Value: | |||
| (PID) Process: | (6872) CCSetup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6872) CCSetup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (6872) CCSetup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (6872) CCSetup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (6872) CCSetup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6872) CCSetup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6872) CCSetup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
Executable files
88
Suspicious files
118
Text files
41
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6872 | CCSetup.exe | C:\Users\admin\AppData\Local\Temp\{20FD435F-4273-4A20-A7D3-619C3BF7F3AD}\0x0409.ini | text | |
MD5:A108F0030A2CDA00405281014F897241 | SHA256:8B76DF0FFC9A226B532B60936765B852B89780C6E475C152F7C320E085E43948 | |||
| 6872 | CCSetup.exe | C:\Users\admin\AppData\Local\Temp\~DBF6.tmp | text | |
MD5:83DA0B2E6F742807321B9017D42057E0 | SHA256:2787A904EED56017DF786FFA19A13607E977685A337B40A2210A383C6A4B422B | |||
| 6872 | CCSetup.exe | C:\Users\admin\AppData\Local\Temp\{20FD435F-4273-4A20-A7D3-619C3BF7F3AD}\Microsoft .NET Framework 4.7.2 Full.prq | xml | |
MD5:742F35470542E0F3B871918C6A10ABB2 | SHA256:880DF4512FFA3353A9658C8FCF0927F9E285B2E41905864EA0A04661C0649BBA | |||
| 6872 | CCSetup.exe | C:\Users\admin\AppData\Local\Temp\~DBE6.tmp | text | |
MD5:83DA0B2E6F742807321B9017D42057E0 | SHA256:2787A904EED56017DF786FFA19A13607E977685A337B40A2210A383C6A4B422B | |||
| 6848 | CCSetup.exe | C:\Users\admin\AppData\Local\Temp\~DB2C.tmp | text | |
MD5:83DA0B2E6F742807321B9017D42057E0 | SHA256:2787A904EED56017DF786FFA19A13607E977685A337B40A2210A383C6A4B422B | |||
| 6848 | CCSetup.exe | C:\Users\admin\AppData\Local\Temp\~DB3D.tmp | text | |
MD5:83DA0B2E6F742807321B9017D42057E0 | SHA256:2787A904EED56017DF786FFA19A13607E977685A337B40A2210A383C6A4B422B | |||
| 6872 | CCSetup.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\KCV3KQBA\CCSetup[1].msi | executable | |
MD5:2F050B2E5B8CB3609BEADCD3D14883D9 | SHA256:315466D1A0BBDC23FA24548CBB191CBE67A263819F3B2D361C95951C07F3EECE | |||
| 6872 | CCSetup.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\26C212D9399727259664BDFCA073966E_C5856A5EB1E3B74AE8014850A678CDBF | der | |
MD5:926340427BC801FF886F2DFAE2CAA65E | SHA256:3457217FECC60C1550F46AB0554DF6351501FD6011F24AF5627D9AC5B799FF7A | |||
| 6872 | CCSetup.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\26C212D9399727259664BDFCA073966E_C5856A5EB1E3B74AE8014850A678CDBF | binary | |
MD5:E9CAD712EC4D18473120A8B53FF414C6 | SHA256:AFDD8730DBB18B9F015D0252A698EEE82B6CABBEB064F66F4BF75B4CE17781AA | |||
| 6872 | CCSetup.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\3EC49180A59F0C351C30F112AD97CFA5_D6347C03508EACBF491FD848B4BDF21D | binary | |
MD5:9AF41EE2D8F84102E90960EAA5497471 | SHA256:32AF5A148B47864CBAD645DDDBC9019BE82C2B728AC1FEEED107F2A404B64186 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
46
DNS requests
22
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6872 | CCSetup.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEA%2B4p0C5FY0DUUO8WdnwQCk%3D | unknown | — | — | whitelisted |
2068 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6772 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6716 | ComboCleaner.WinService.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSE67Nbq3jfQQg8yXEpbmqLTNn7XwQUm1%2BwNrqdBq4ZJ73AoCLAi4s4d%2B0CEAGtzR3ebXqHxeW3NrExxPc%3D | unknown | — | — | whitelisted |
6872 | CCSetup.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSE67Nbq3jfQQg8yXEpbmqLTNn7XwQUm1%2BwNrqdBq4ZJ73AoCLAi4s4d%2B0CEAGtzR3ebXqHxeW3NrExxPc%3D | unknown | — | — | whitelisted |
7120 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6716 | ComboCleaner.WinService.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEA%2B4p0C5FY0DUUO8WdnwQCk%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3852 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5744 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6872 | CCSetup.exe | 172.67.96.20:443 | services.combocleaner.com | CLOUDFLARENET | US | unknown |
6872 | CCSetup.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3852 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3260 | svchost.exe | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2068 | svchost.exe | 40.126.32.72:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
2068 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
services.combocleaner.com |
| unknown |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |