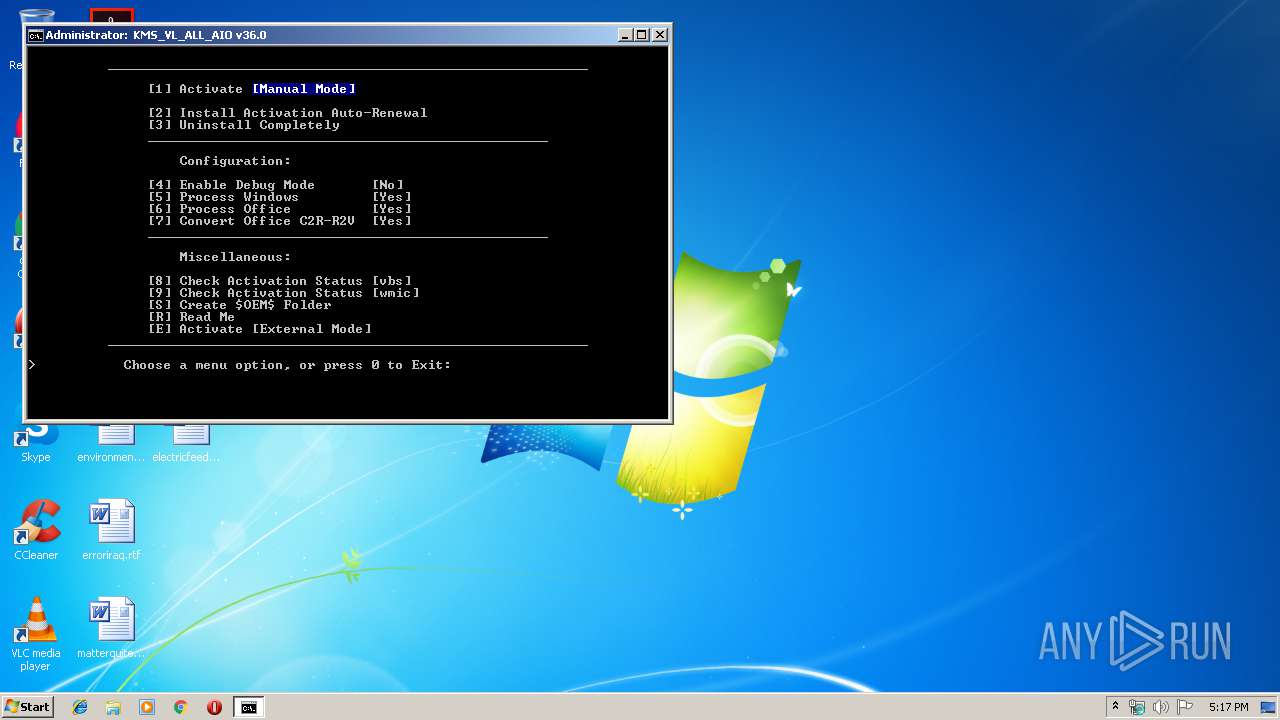
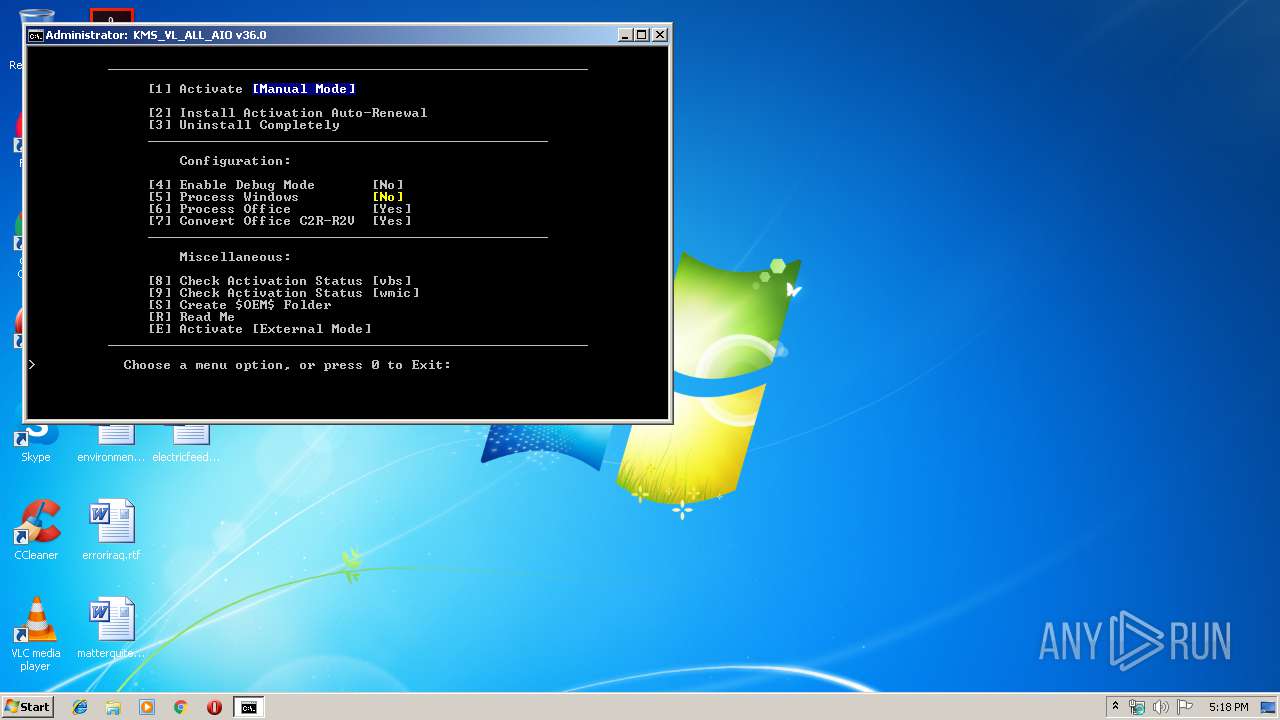
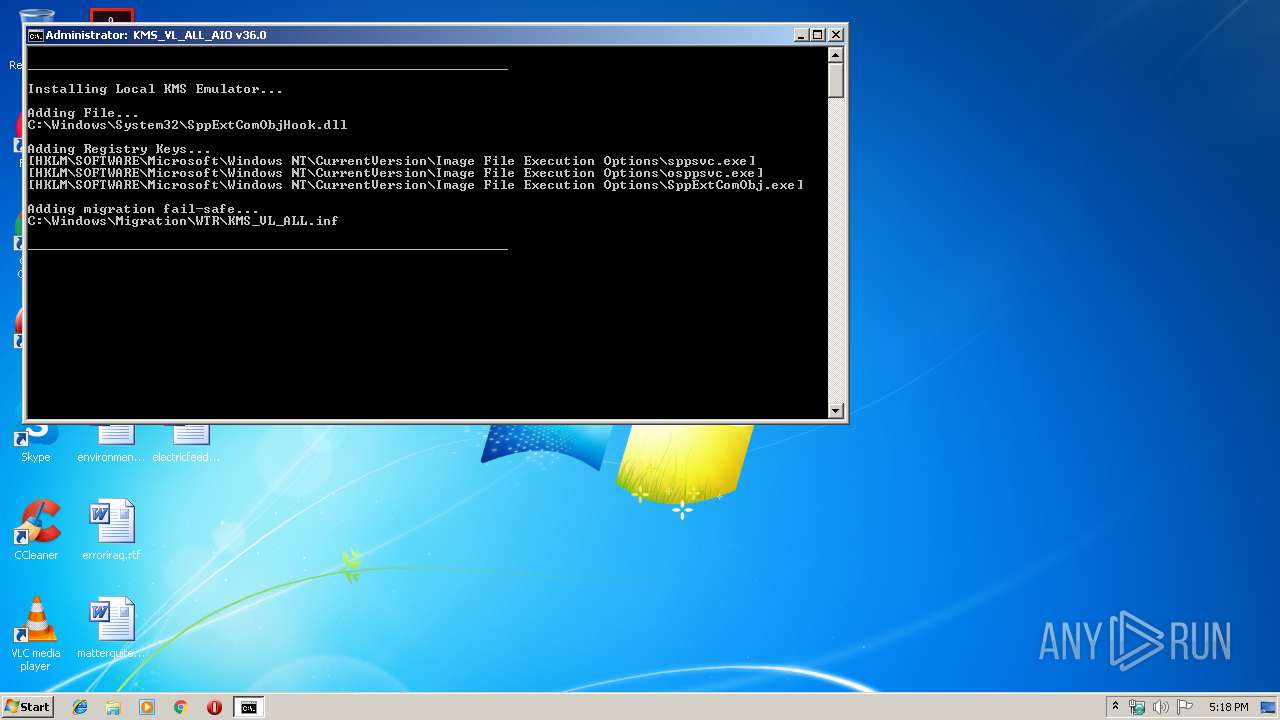
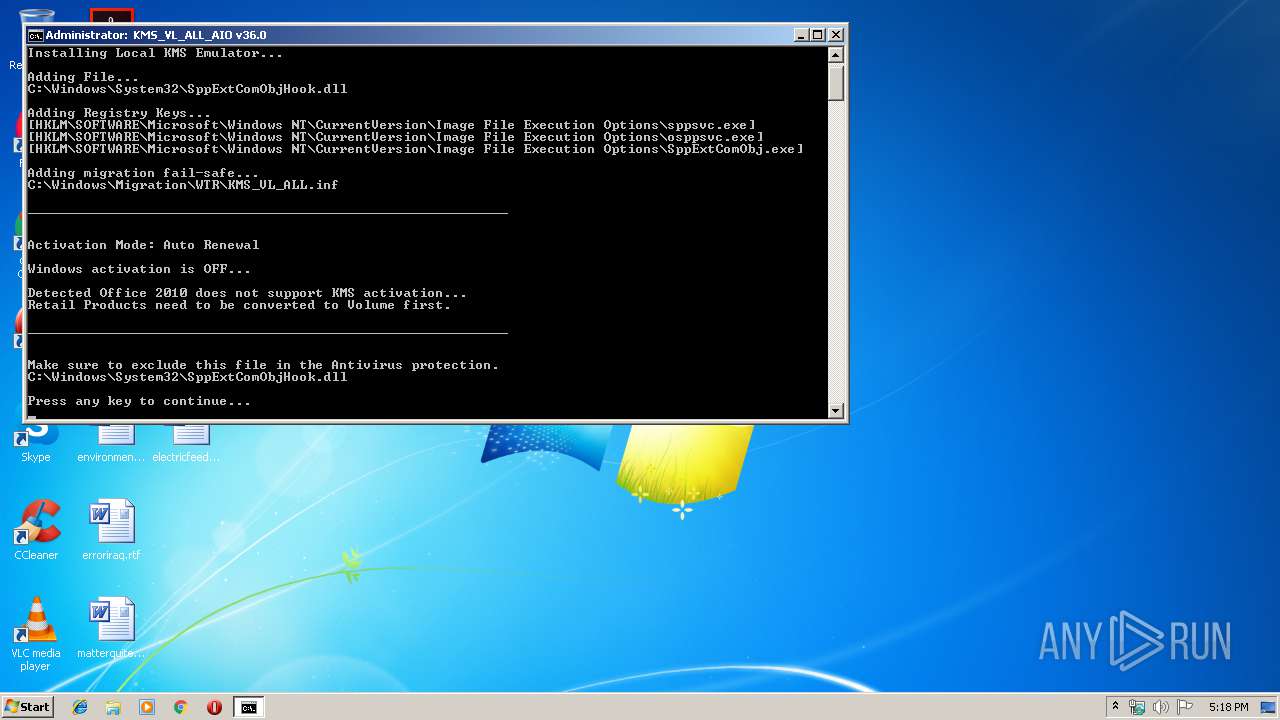
| File name: | KMS_VL_ALL_AIO.cmd |
| Full analysis: | https://app.any.run/tasks/d4b7b0d0-9013-461c-87ce-7e7d5aeb81b6 |
| Verdict: | Malicious activity |
| Analysis date: | November 24, 2019, 17:17:38 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | exported SGML document, ASCII text, with very long lines, with CRLF line terminators |
| MD5: | 7D6040331CCB44DCD9A0908496A364DB |
| SHA1: | 4627A1326BDFD8ADC7B1B769675602F76F1A4C6E |
| SHA256: | F28A363DBC572F4CE6FDE8C4B271F3D1310238F246016F0DB9ECC242D2941AE8 |
| SSDEEP: | 3072:a7J35SJzcWaaUNHRGnEAyGOwSiLtFIrzNtlsUSilMwTf8Tkdt2oR4tqm96:aJAJzdUQyGOwSirI1tlscawTf+kS/w |
MALICIOUS
Executes PowerShell scripts
- cmd.exe (PID: 1904)
Starts Visual C# compiler
- powershell.exe (PID: 3224)
Loads the Task Scheduler COM API
- OSPPSVC.EXE (PID: 2456)
- sppsvc.exe (PID: 3816)
- sppsvc.exe (PID: 3124)
Loads dropped or rewritten executable
- sppsvc.exe (PID: 3816)
- OSPPSVC.EXE (PID: 2456)
- sppsvc.exe (PID: 3124)
Starts NET.EXE for service management
- cmd.exe (PID: 1904)
SUSPICIOUS
Starts CMD.EXE for commands execution
- cscript.exe (PID: 1552)
- cmd.exe (PID: 1904)
Uses RUNDLL32.EXE to load library
- cscript.exe (PID: 1552)
Executes scripts
- cmd.exe (PID: 2828)
Uses REG.EXE to modify Windows registry
- cmd.exe (PID: 2828)
- cmd.exe (PID: 4060)
- cmd.exe (PID: 1904)
- cmd.exe (PID: 3688)
- cmd.exe (PID: 3964)
- cmd.exe (PID: 1188)
- cmd.exe (PID: 1160)
- cmd.exe (PID: 2448)
- cmd.exe (PID: 2412)
- cmd.exe (PID: 4004)
Starts SC.EXE for service management
- cmd.exe (PID: 1904)
Creates files in the Windows directory
- cmd.exe (PID: 1904)
- powershell.exe (PID: 3224)
Application launched itself
- cmd.exe (PID: 1904)
Starts CHOICE.EXE (used to create a delay)
- cmd.exe (PID: 1904)
Creates files in the user directory
- powershell.exe (PID: 2928)
- powershell.exe (PID: 3224)
- powershell.exe (PID: 3696)
Executable content was dropped or overwritten
- powershell.exe (PID: 3224)
Uses WMIC.EXE to obtain a system information
- cmd.exe (PID: 3532)
- cmd.exe (PID: 1904)
Removes files from Windows directory
- cmd.exe (PID: 1904)
INFO
Dropped object may contain Bitcoin addresses
- sppsvc.exe (PID: 3816)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .wsf | | | Windows Script File (72.7) |
|---|---|---|
| .html | | | HyperText Markup Language (27.2) |
Total processes
161
Monitored processes
121
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 184 | reg add "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\sppsvc.exe" /f /v KMS_RenewalInterval /t REG_DWORD /d 10080 | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 236 | reg add "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\sppsvc.exe" /f /v KMS_ActivationInterval /t REG_DWORD /d 120 | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 236 | C:\Windows\system32\cmd.exe /c "prompt $H&for %B in (1) do rem" | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 292 | reg add "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SppExtComObj.exe" /f /v KMS_ActivationInterval /t REG_DWORD /d 120 | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 324 | reg add "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\osppsvc.exe" /f /v KMS_Emulation /t REG_DWORD /d 1 | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 408 | reg add "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\sppsvc.exe" /f /v KMS_Emulation /t REG_DWORD /d 1 | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 504 | reg add "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\sppsvc.exe" /f /v KMS_ActivationInterval /t REG_DWORD /d 120 | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 584 | C:\Windows\system32\cmd.exe /c dir /b /ad C:\Windows\System32\spp\tokens\skus | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 688 | mode con cols=100 lines=31 | C:\Windows\System32\mode.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: DOS Device MODE Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 784 | sc query sppsvc | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: A tool to aid in developing services for WindowsNT Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 087
Read events
892
Write events
195
Delete events
0
Modification events
| (PID) Process: | (1552) cscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (1552) cscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2928) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3224) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3700) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\sppsvc.exe |
| Operation: | write | Name: | GlobalFlag |
Value: 256 | |||
| (PID) Process: | (408) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\sppsvc.exe |
| Operation: | write | Name: | KMS_Emulation |
Value: 1 | |||
| (PID) Process: | (504) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\sppsvc.exe |
| Operation: | write | Name: | KMS_ActivationInterval |
Value: 120 | |||
| (PID) Process: | (3004) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\sppsvc.exe |
| Operation: | write | Name: | KMS_RenewalInterval |
Value: 10080 | |||
| (PID) Process: | (3948) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\osppsvc.exe |
| Operation: | write | Name: | VerifierDlls |
Value: SppExtComObjHook.dll | |||
| (PID) Process: | (2468) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\sppsvc.exe |
| Operation: | write | Name: | VerifierDlls |
Value: SppExtComObjHook.dll | |||
Executable files
1
Suspicious files
9
Text files
7
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2928 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\W5M9KFJX79H8RA86OTJT.temp | — | |
MD5:— | SHA256:— | |||
| 3224 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\PYSMY8P39OXN435EFUI0.temp | — | |
MD5:— | SHA256:— | |||
| 3224 | powershell.exe | C:\Users\admin\AppData\Local\Temp\idnswogt.0.cs | — | |
MD5:— | SHA256:— | |||
| 3224 | powershell.exe | C:\Users\admin\AppData\Local\Temp\idnswogt.cmdline | — | |
MD5:— | SHA256:— | |||
| 1560 | csc.exe | C:\Users\admin\AppData\Local\Temp\CSC5A3.tmp | — | |
MD5:— | SHA256:— | |||
| 1560 | csc.exe | C:\Users\admin\AppData\Local\Temp\idnswogt.pdb | — | |
MD5:— | SHA256:— | |||
| 3876 | cvtres.exe | C:\Users\admin\AppData\Local\Temp\RES5A4.tmp | — | |
MD5:— | SHA256:— | |||
| 1560 | csc.exe | C:\Users\admin\AppData\Local\Temp\idnswogt.dll | — | |
MD5:— | SHA256:— | |||
| 1560 | csc.exe | C:\Users\admin\AppData\Local\Temp\idnswogt.out | — | |
MD5:— | SHA256:— | |||
| 3696 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\P822M37FQ5Y3OQW0W827.temp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
DNS requests
Threats
Process | Message |
|---|---|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|