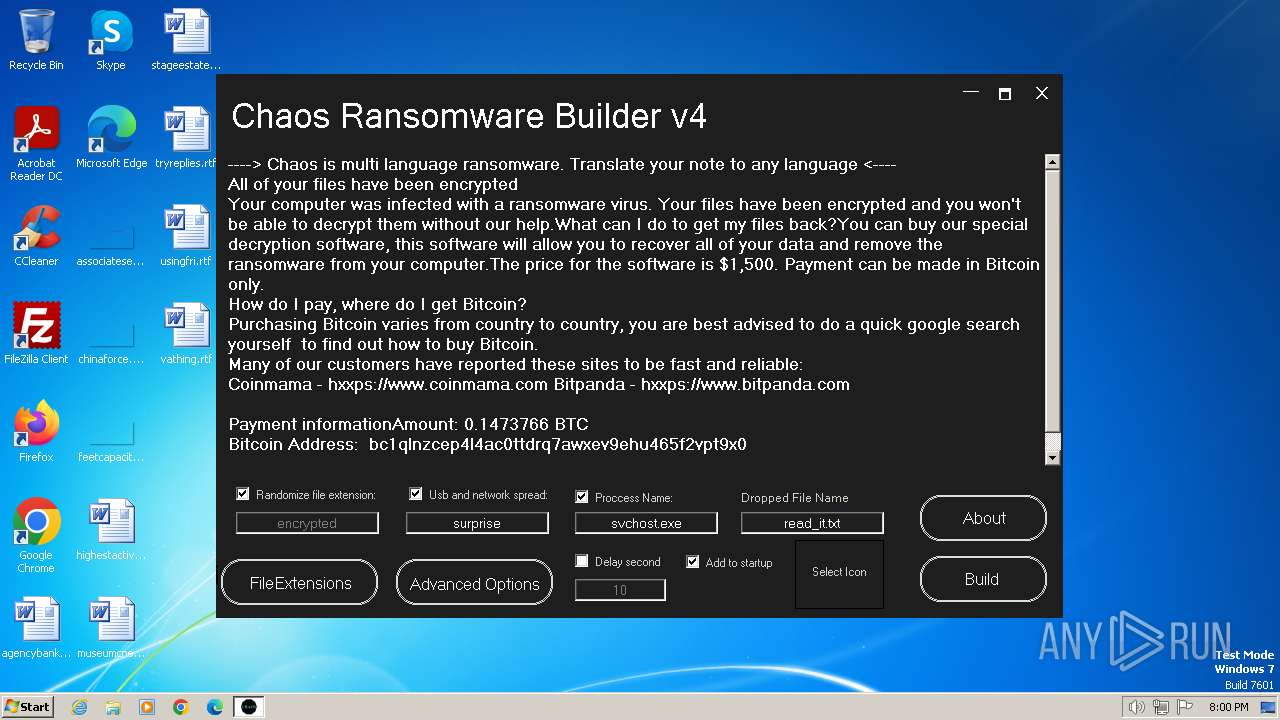
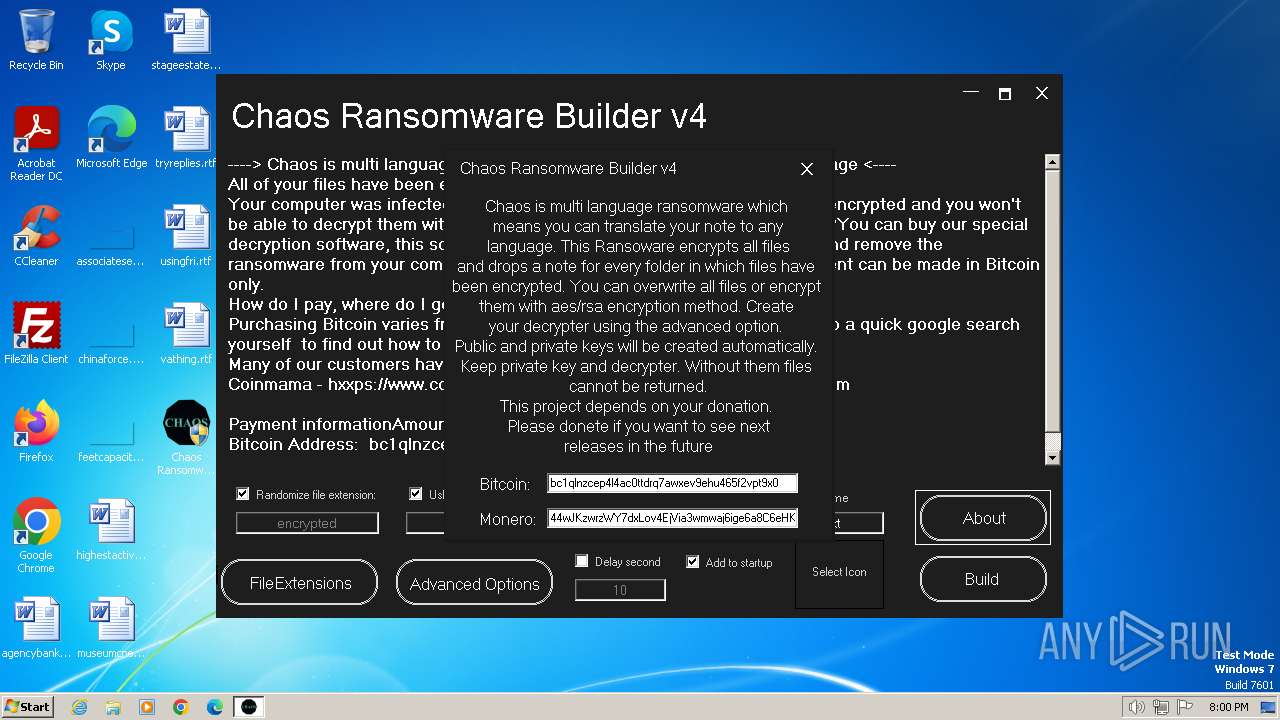
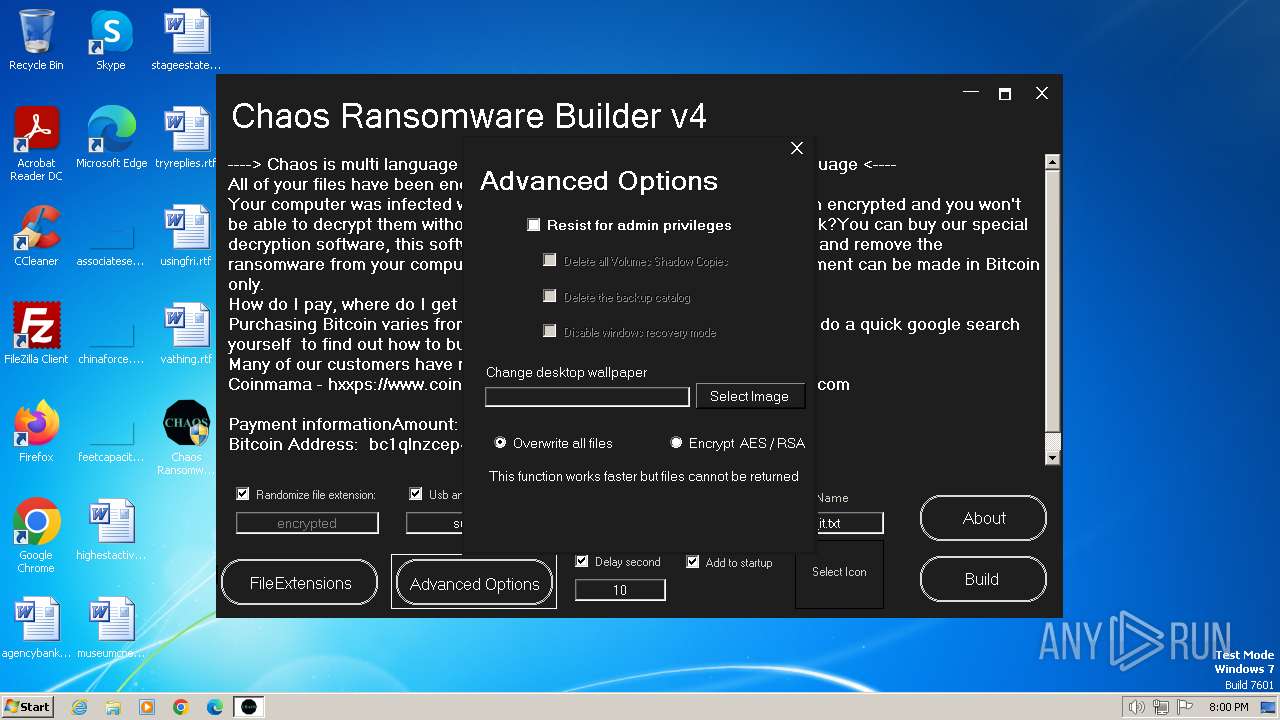
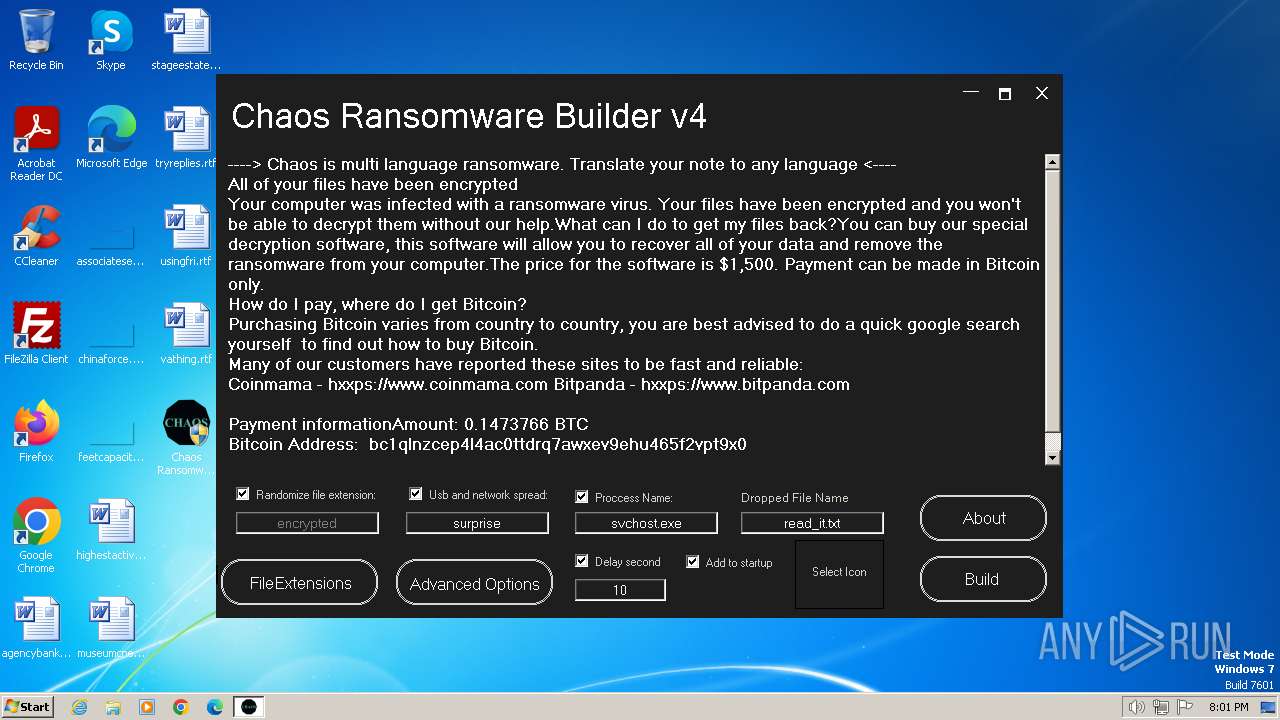
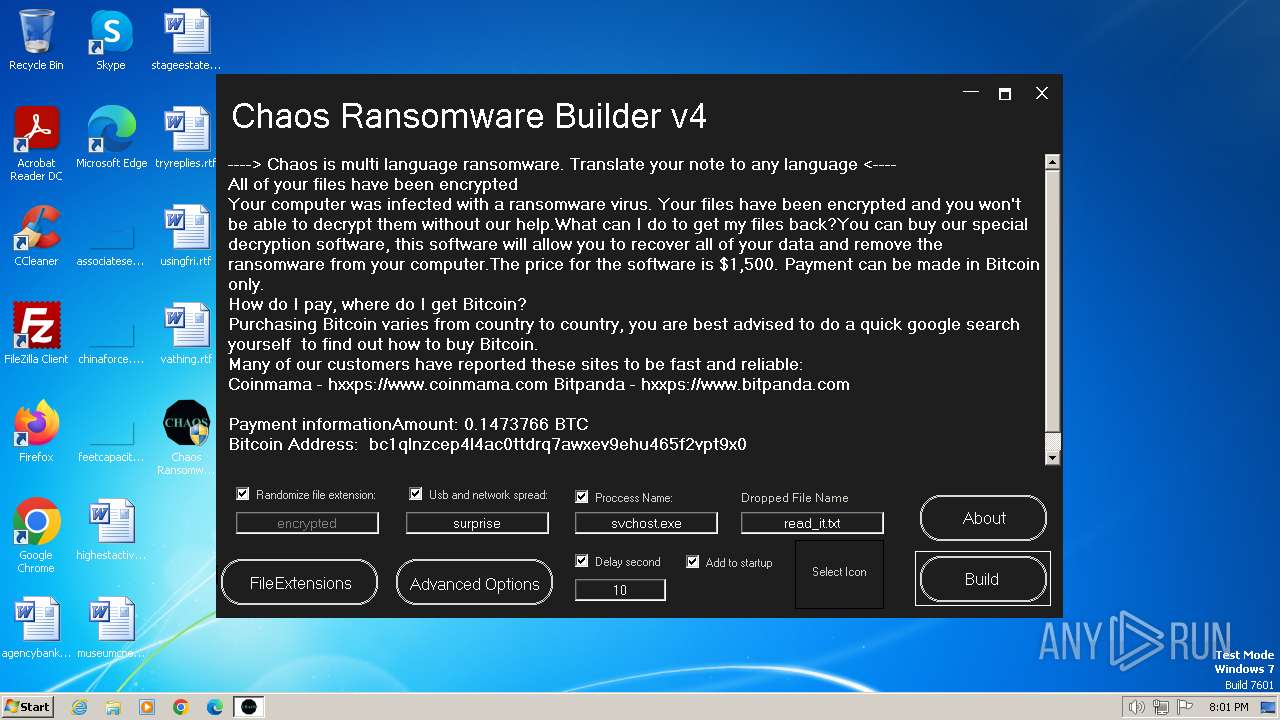
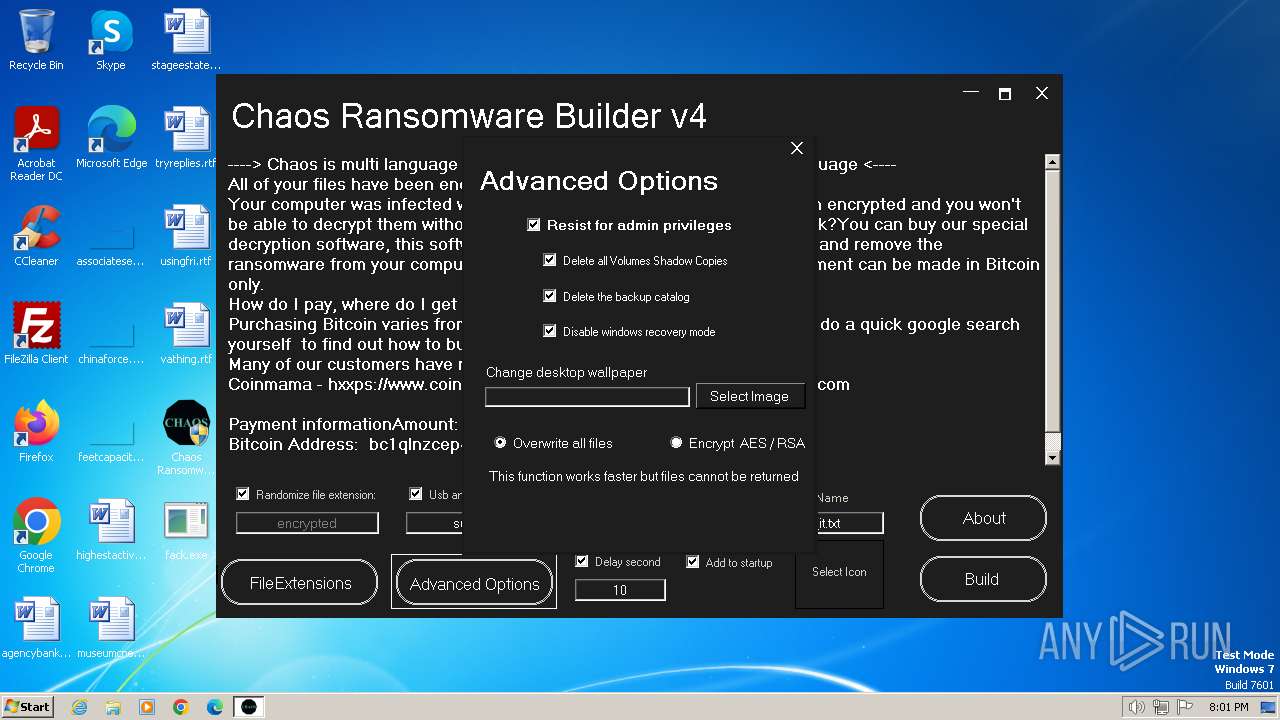
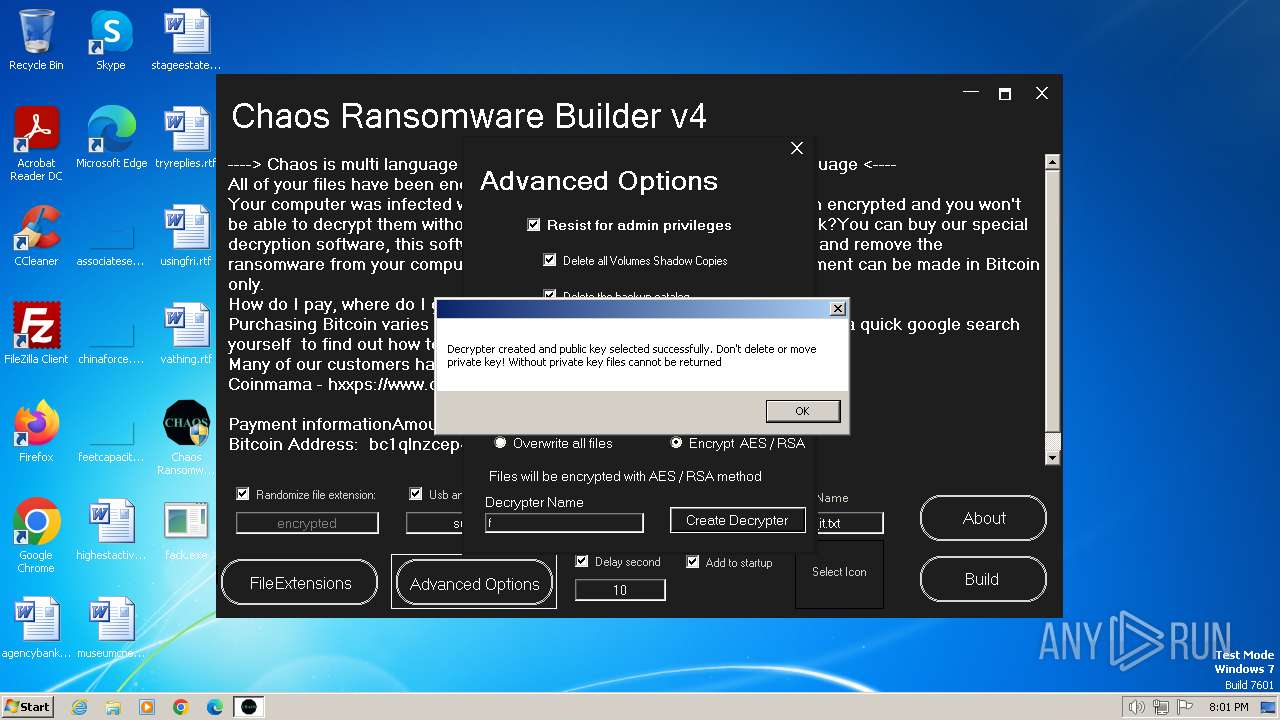
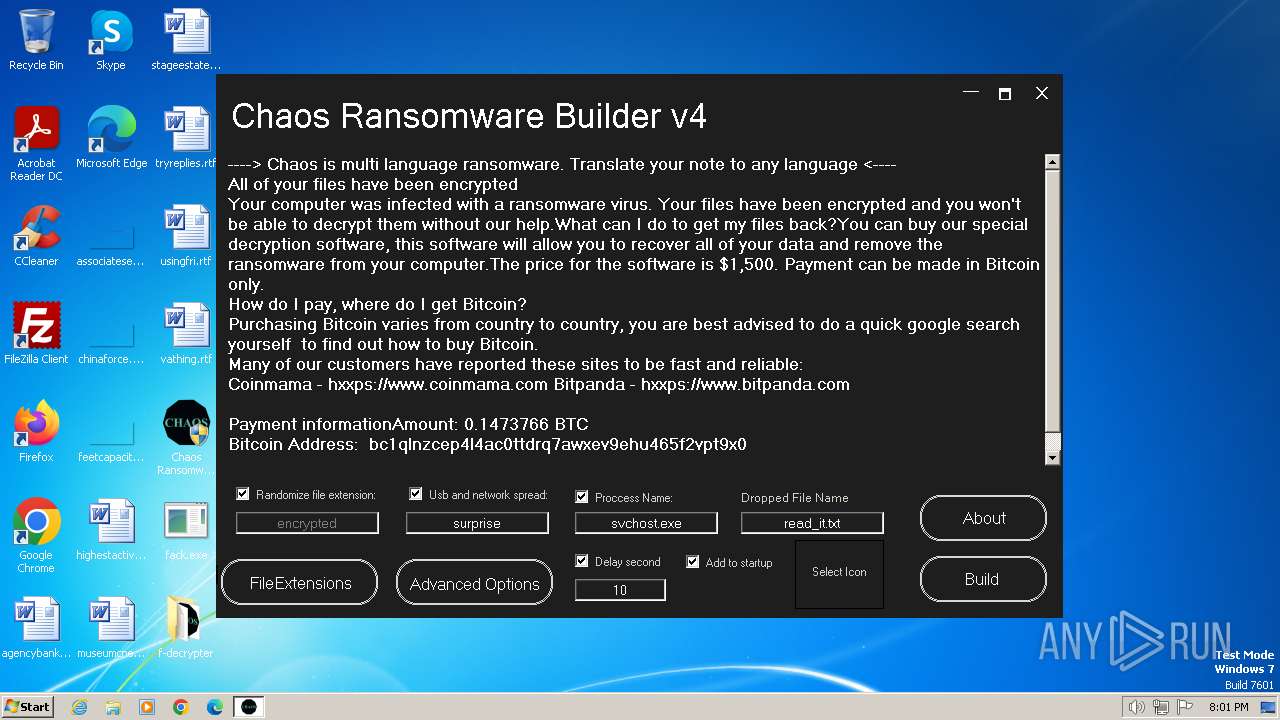
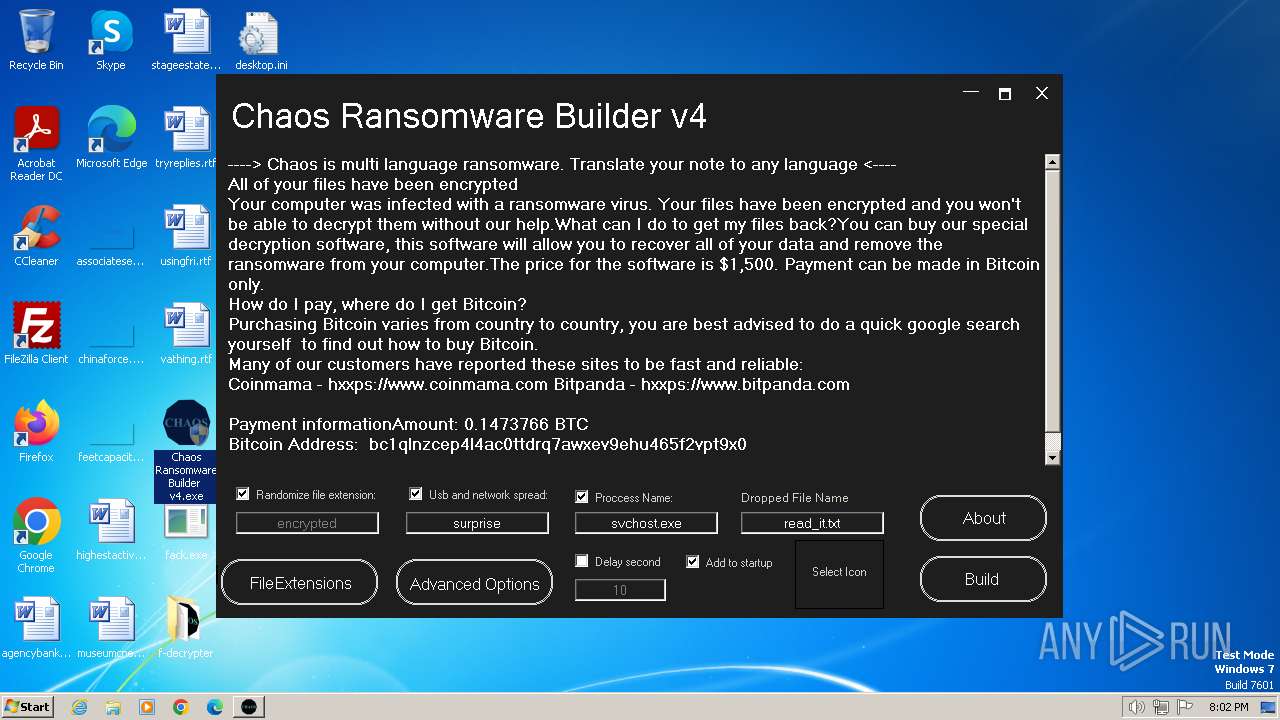
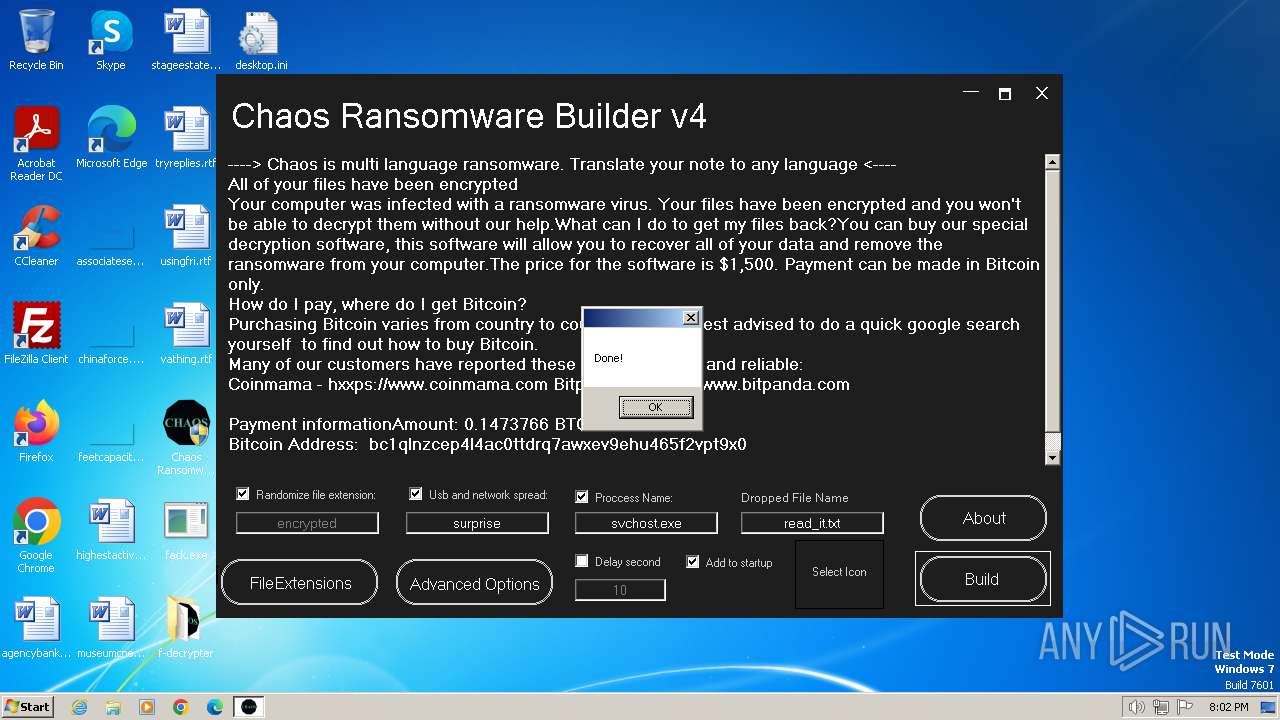
| File name: | Chaos Ransomware Builder v4.exe |
| Full analysis: | https://app.any.run/tasks/64eb3af3-2b54-408e-bf35-7b6b157aefc3 |
| Verdict: | Malicious activity |
| Analysis date: | March 04, 2024, 20:00:17 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | 8B855E56E41A6E10D28522A20C1E0341 |
| SHA1: | 17EA75272CFE3749C6727388FD444D2C970F9D01 |
| SHA256: | F2665F89BA53ABD3DEB81988C0D5194992214053E77FC89B98B64A31A7504D77 |
| SSDEEP: | 3072:9UJAYdi2YcRVm16Pn6tpzqJG/sX9i2YcRPm16Pn6ckCjSH5EyR9aKZt18rTu+i21:9aiWm162qJEsNiym16ryAiym168m |
MALICIOUS
Starts Visual C# compiler
- Chaos Ransomware Builder v4.exe (PID: 2848)
- Chaos Ransomware Builder v4.exe (PID: 3108)
Drops the executable file immediately after the start
- Chaos Ransomware Builder v4.exe (PID: 2848)
- csc.exe (PID: 2648)
- fack.exe (PID: 3164)
- csc.exe (PID: 1196)
- idfk.exe (PID: 3448)
Create files in the Startup directory
- svchost.exe (PID: 1572)
Deletes shadow copies
- cmd.exe (PID: 1368)
- cmd.exe (PID: 2020)
Actions looks like stealing of personal data
- svchost.exe (PID: 1572)
- svchost.exe (PID: 3688)
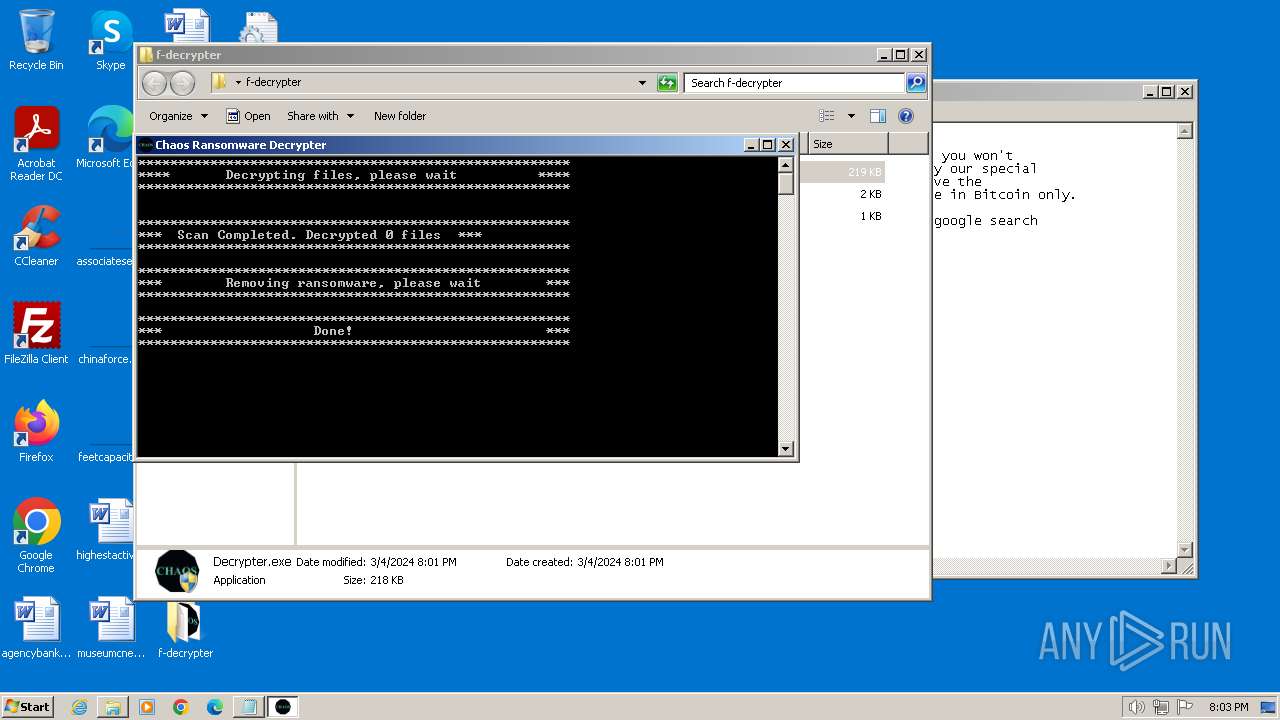
- Decrypter.exe (PID: 3084)
Using BCDEDIT.EXE to modify recovery options
- cmd.exe (PID: 480)
Steals credentials from Web Browsers
- Decrypter.exe (PID: 3084)
SUSPICIOUS
Reads security settings of Internet Explorer
- Chaos Ransomware Builder v4.exe (PID: 2848)
- fack.exe (PID: 3164)
- svchost.exe (PID: 1572)
- Chaos Ransomware Builder v4.exe (PID: 3108)
- idfk.exe (PID: 3448)
Uses .NET C# to load dll
- Chaos Ransomware Builder v4.exe (PID: 2848)
- Chaos Ransomware Builder v4.exe (PID: 3108)
Reads the Internet Settings
- Chaos Ransomware Builder v4.exe (PID: 2848)
- fack.exe (PID: 3164)
- svchost.exe (PID: 1572)
- Chaos Ransomware Builder v4.exe (PID: 3108)
- WMIC.exe (PID: 840)
- idfk.exe (PID: 3448)
Executable content was dropped or overwritten
- csc.exe (PID: 2648)
- Chaos Ransomware Builder v4.exe (PID: 2848)
- fack.exe (PID: 3164)
- csc.exe (PID: 1196)
- idfk.exe (PID: 3448)
The process creates files with name similar to system file names
- fack.exe (PID: 3164)
- idfk.exe (PID: 3448)
Starts CMD.EXE for commands execution
- svchost.exe (PID: 1572)
Starts itself from another location
- fack.exe (PID: 3164)
- idfk.exe (PID: 3448)
Executes as Windows Service
- wbengine.exe (PID: 1636)
- vds.exe (PID: 1020)
- VSSVC.exe (PID: 2484)
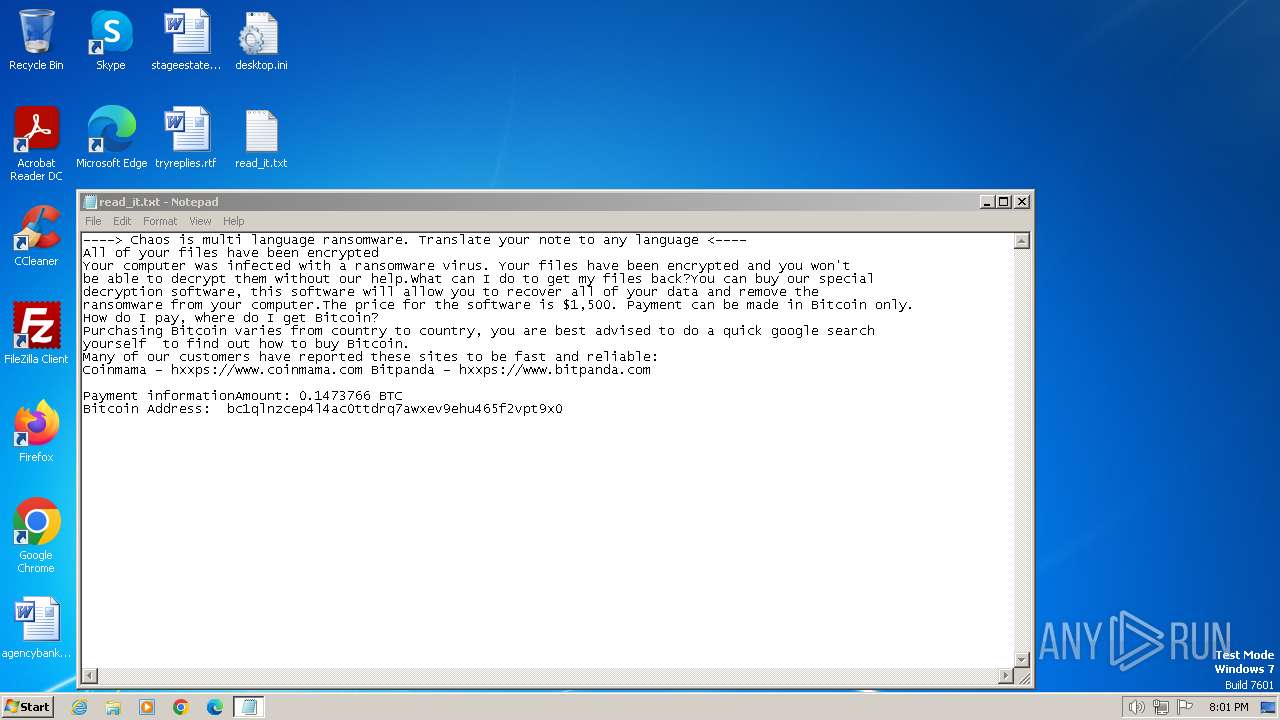
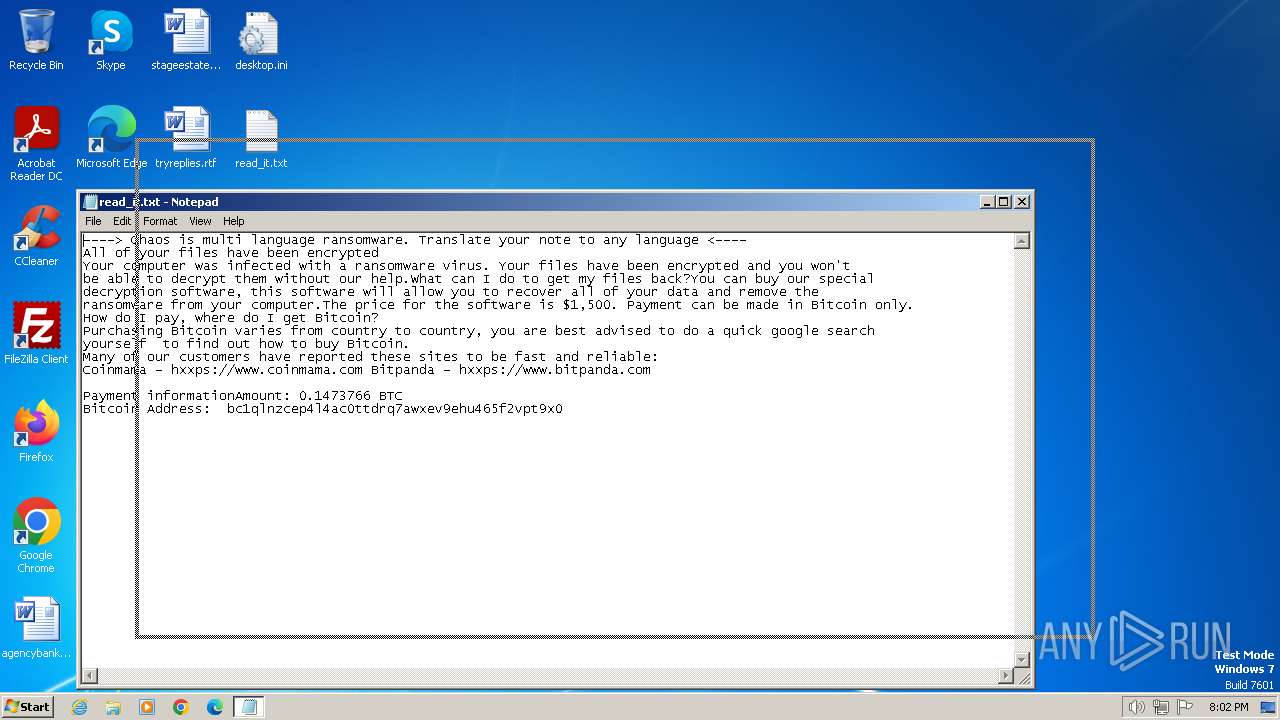
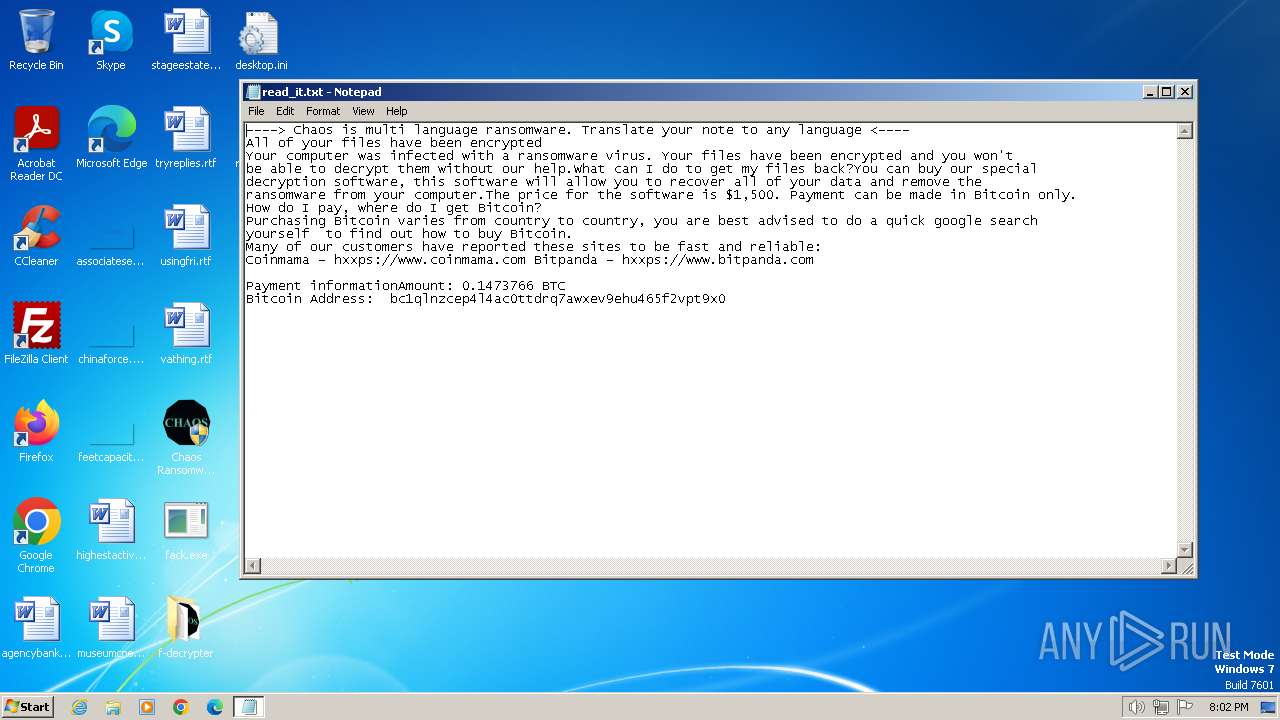
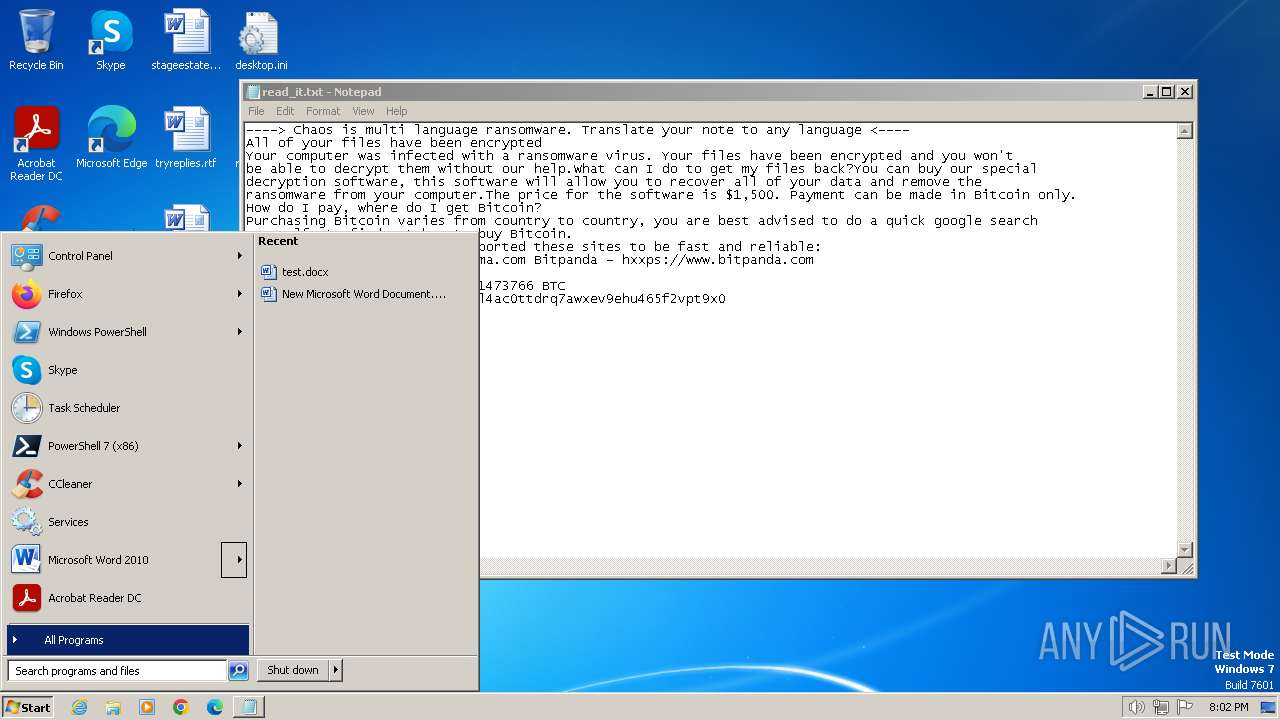
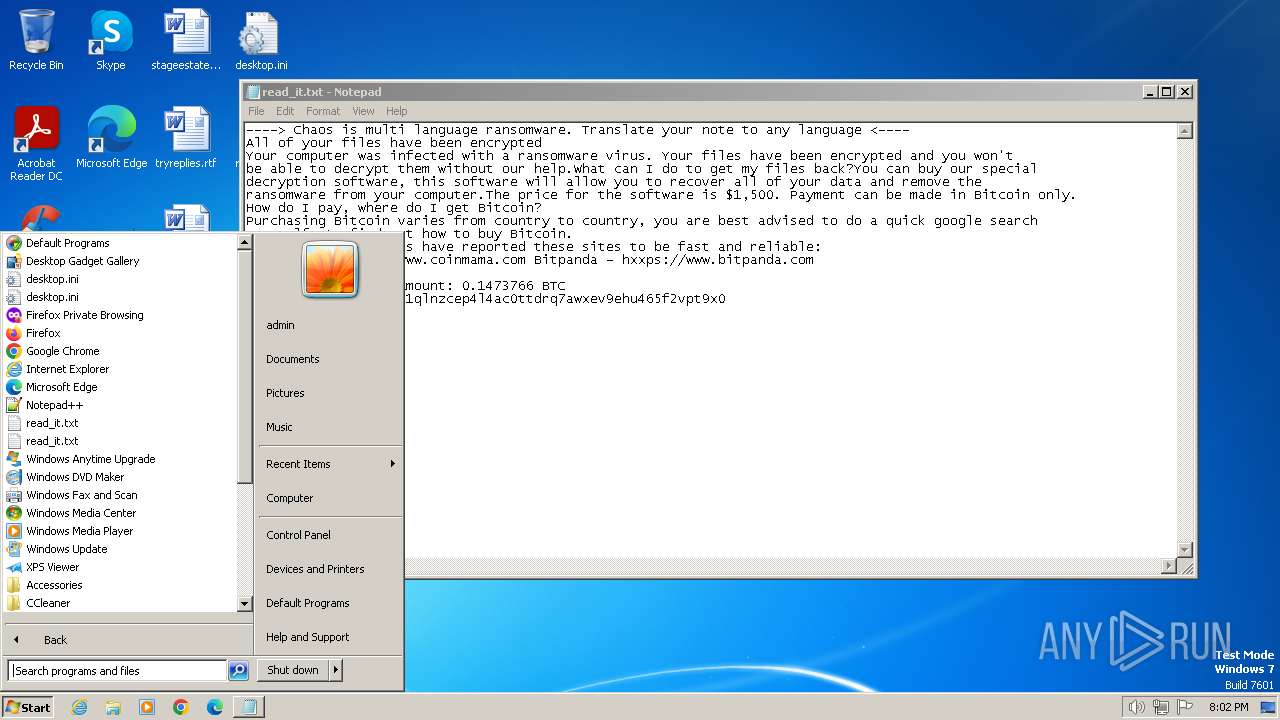
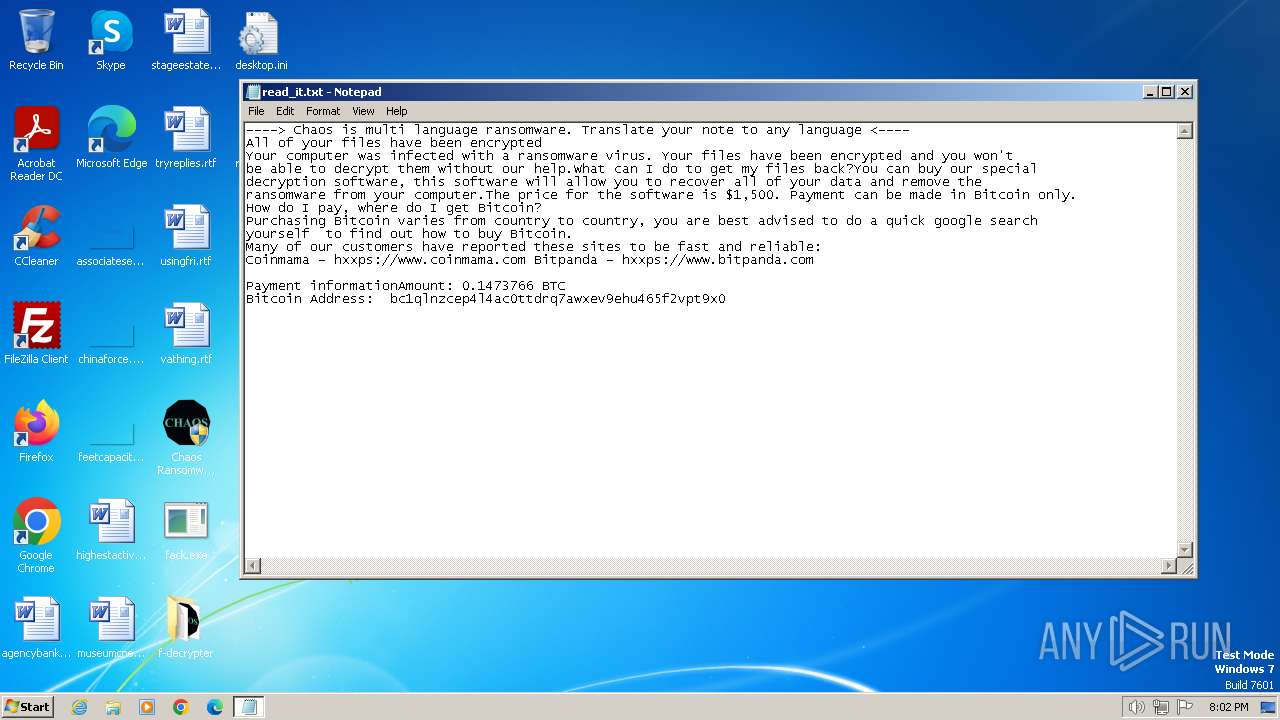
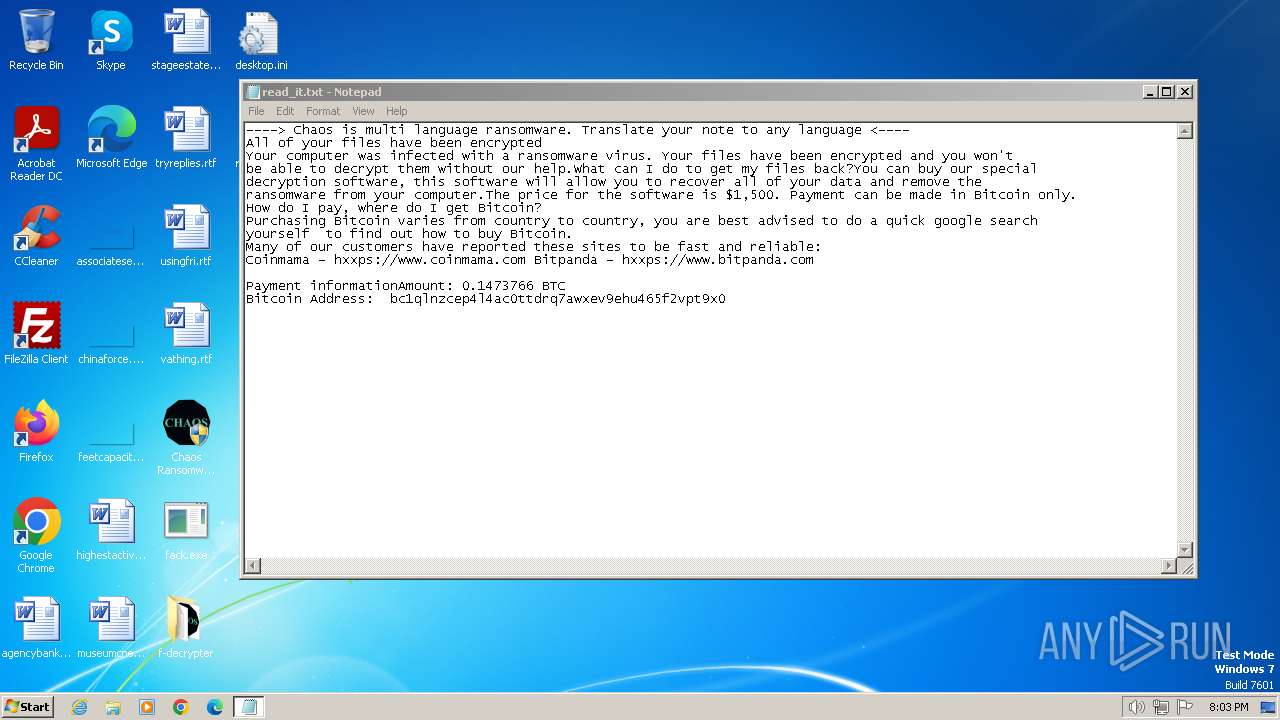
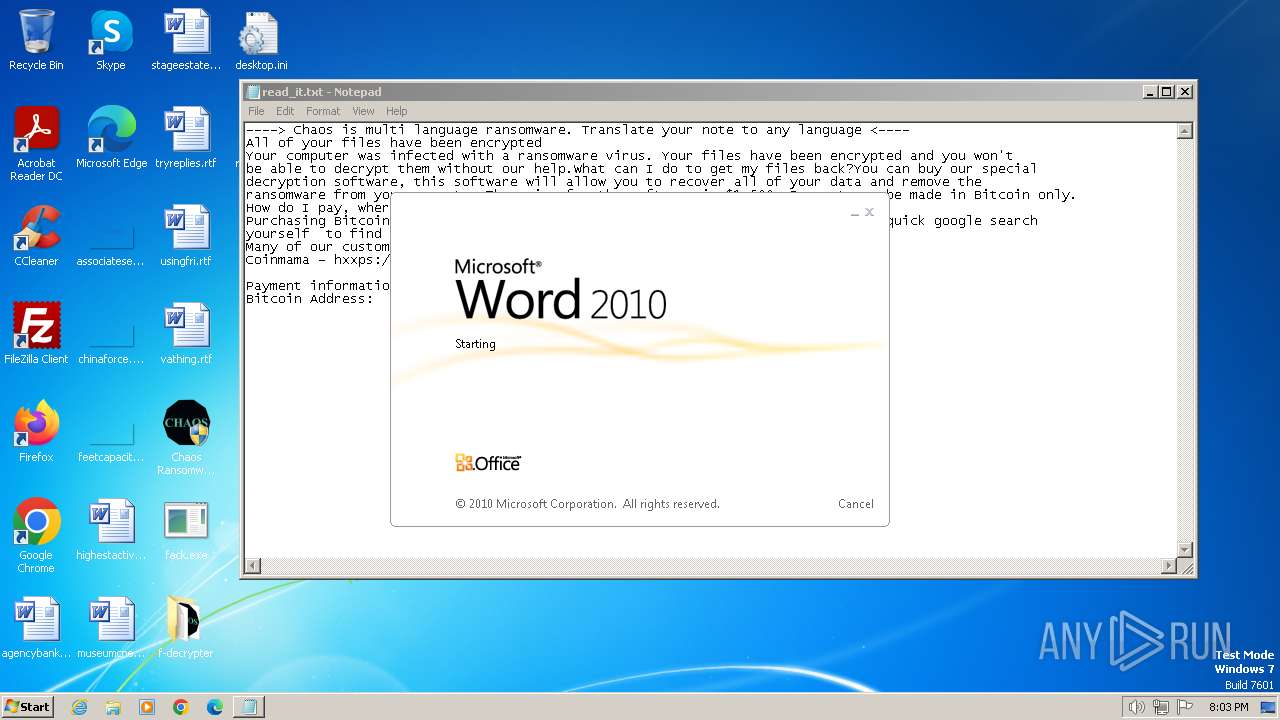
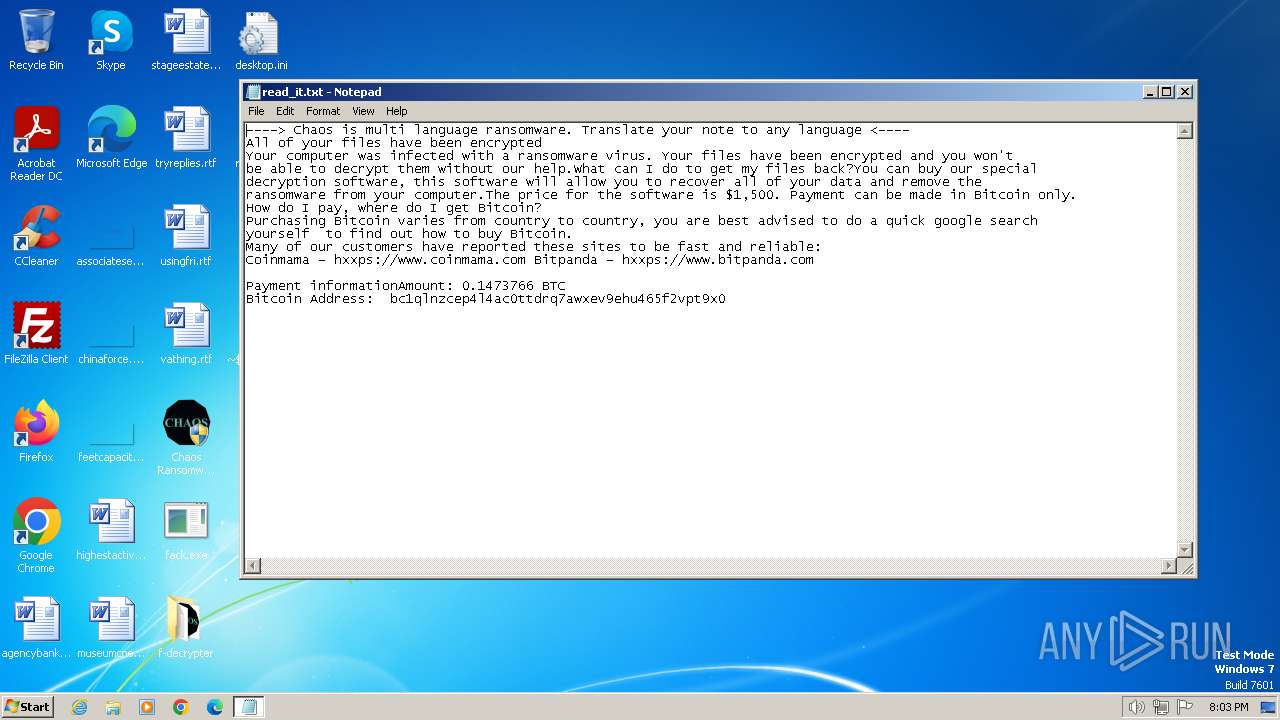
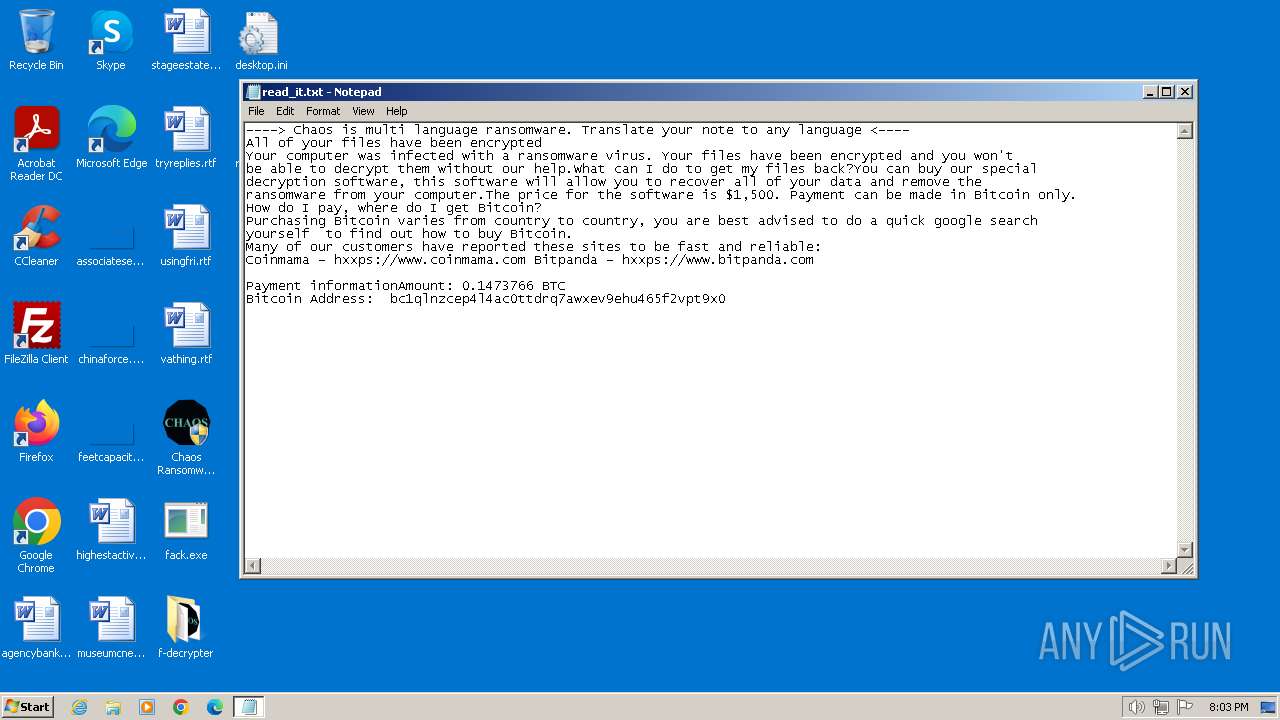
Start notepad (likely ransomware note)
- svchost.exe (PID: 1572)
- svchost.exe (PID: 3688)
Reads browser cookies
- Decrypter.exe (PID: 3084)
INFO
Reads the machine GUID from the registry
- Chaos Ransomware Builder v4.exe (PID: 2848)
- csc.exe (PID: 2648)
- cvtres.exe (PID: 2572)
- svchost.exe (PID: 1572)
- Chaos Ransomware Builder v4.exe (PID: 3108)
- csc.exe (PID: 1196)
- cvtres.exe (PID: 3600)
- svchost.exe (PID: 3688)
Checks supported languages
- Chaos Ransomware Builder v4.exe (PID: 2848)
- csc.exe (PID: 2648)
- cvtres.exe (PID: 2572)
- fack.exe (PID: 3164)
- svchost.exe (PID: 1572)
- csc.exe (PID: 1196)
- cvtres.exe (PID: 3600)
- idfk.exe (PID: 3448)
- svchost.exe (PID: 3688)
- Decrypter.exe (PID: 3084)
- Chaos Ransomware Builder v4.exe (PID: 3108)
Reads the computer name
- Chaos Ransomware Builder v4.exe (PID: 2848)
- fack.exe (PID: 3164)
- svchost.exe (PID: 1572)
- Chaos Ransomware Builder v4.exe (PID: 3108)
- idfk.exe (PID: 3448)
- svchost.exe (PID: 3688)
- Decrypter.exe (PID: 3084)
Create files in a temporary directory
- Chaos Ransomware Builder v4.exe (PID: 2848)
- cvtres.exe (PID: 2572)
- Chaos Ransomware Builder v4.exe (PID: 3108)
- cvtres.exe (PID: 3600)
- Decrypter.exe (PID: 3084)
Manual execution by a user
- fack.exe (PID: 3164)
- Chaos Ransomware Builder v4.exe (PID: 532)
- Chaos Ransomware Builder v4.exe (PID: 3108)
- idfk.exe (PID: 3448)
- Decrypter.exe (PID: 2860)
- Decrypter.exe (PID: 3084)
- WINWORD.EXE (PID: 2160)
Creates files or folders in the user directory
- fack.exe (PID: 3164)
- svchost.exe (PID: 1572)
- idfk.exe (PID: 3448)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (63.1) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (23.8) |
| .dll | | | Win32 Dynamic Link Library (generic) (5.6) |
| .exe | | | Win32 Executable (generic) (3.8) |
| .exe | | | Generic Win/DOS Executable (1.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2021:08:04 07:08:22+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 11 |
| CodeSize: | 439808 |
| InitializedDataSize: | 123392 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x6d5ae |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 3.0.0.0 |
| ProductVersionNumber: | 3.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | Chaos Ransomware v4 |
| FileVersion: | 3.0.0.0 |
| InternalName: | Chaos Ransomware Builder v4.exe |
| LegalCopyright: | Copyright © 2021 |
| OriginalFileName: | Chaos Ransomware Builder v4.exe |
| ProductName: | Chaos Ransomware Builder v4 |
| ProductVersion: | 3.0.0.0 |
| AssemblyVersion: | 3.0.0.0 |
Total processes
93
Monitored processes
29
Malicious processes
8
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 480 | "C:\Windows\System32\cmd.exe" /C bcdedit /set {default} bootstatuspolicy ignoreallfailures & bcdedit /set {default} recoveryenabled no | C:\Windows\System32\cmd.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 532 | "C:\Users\admin\Desktop\Chaos Ransomware Builder v4.exe" | C:\Users\admin\Desktop\Chaos Ransomware Builder v4.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Chaos Ransomware v4 Exit code: 3221226540 Version: 3.0.0.0 Modules
| |||||||||||||||
| 764 | wbadmin delete catalog -quiet | C:\Windows\System32\wbadmin.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Command Line Interface for Microsoft® BLB Backup Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 840 | wmic shadowcopy delete | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1020 | C:\Windows\System32\vds.exe | C:\Windows\System32\vds.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Virtual Disk Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1196 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\2i230v5p\2i230v5p.cmdline" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe | Chaos Ransomware Builder v4.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Visual C# Command Line Compiler Exit code: 0 Version: 4.8.3761.0 built by: NET48REL1 Modules
| |||||||||||||||
| 1368 | "C:\Windows\System32\cmd.exe" /C vssadmin delete shadows /all /quiet & wmic shadowcopy delete | C:\Windows\System32\cmd.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1572 | "C:\Users\admin\AppData\Roaming\svchost.exe" | C:\Users\admin\AppData\Roaming\svchost.exe | fack.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Exit code: 4294967295 Version: 0.0.0.0 Modules
| |||||||||||||||
| 1608 | bcdedit /set {default} recoveryenabled no | C:\Windows\System32\bcdedit.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Boot Configuration Data Editor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1636 | "C:\Windows\system32\wbengine.exe" | C:\Windows\System32\wbengine.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Block Level Backup Engine Service EXE Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
26 829
Read events
26 212
Write events
292
Delete events
325
Modification events
| (PID) Process: | (2848) Chaos Ransomware Builder v4.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2848) Chaos Ransomware Builder v4.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2848) Chaos Ransomware Builder v4.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2848) Chaos Ransomware Builder v4.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2848) Chaos Ransomware Builder v4.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\CIDSizeMRU |
| Operation: | write | Name: | 4 |
Value: 4300680061006F0073002000520061006E0073006F006D00770061007200650020004200750069006C0064006500720020002000760034002E00650078006500000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000100000000000000 | |||
| (PID) Process: | (2848) Chaos Ransomware Builder v4.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 0202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (2848) Chaos Ransomware Builder v4.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 07000000020000000100000006000000000000000B0000000C0000000D0000000A0000000900000008000000030000000500000004000000FFFFFFFF | |||
| (PID) Process: | (2848) Chaos Ransomware Builder v4.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2848) Chaos Ransomware Builder v4.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\LastVisitedPidlMRU |
| Operation: | write | Name: | 3 |
Value: 4300680061006F0073002000520061006E0073006F006D00770061007200650020004200750069006C0064006500720020002000760034002E0065007800650000000000 | |||
| (PID) Process: | (2848) Chaos Ransomware Builder v4.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\LastVisitedPidlMRU |
| Operation: | write | Name: | MRUListEx |
Value: 03000000000000000200000001000000FFFFFFFF | |||
Executable files
6
Suspicious files
9
Text files
119
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
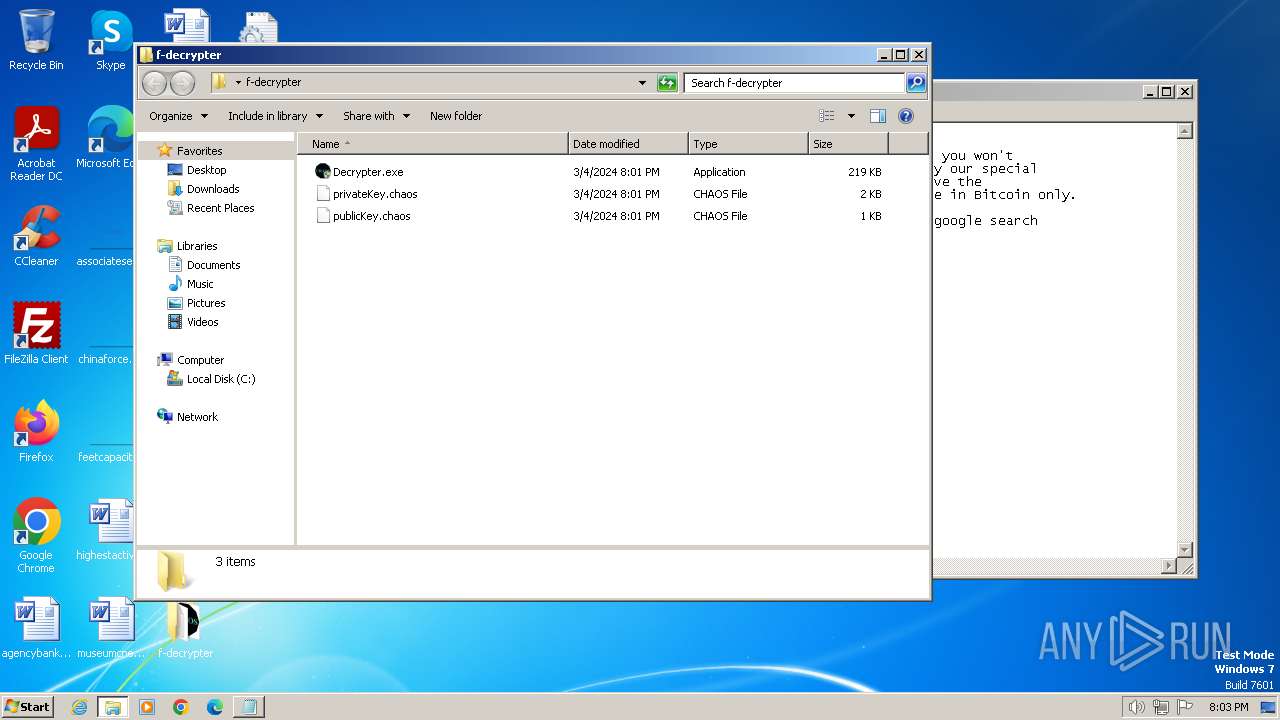
| 2848 | Chaos Ransomware Builder v4.exe | C:\Users\admin\Desktop\f-decrypter\publicKey.chaos | xml | |
MD5:4EAB6C2AD391FB6ADB8F88B712857295 | SHA256:22CBBED02B6733520E6DB5CEC18AF48981FC2679438CDBAB564DE8447A706D01 | |||
| 2648 | csc.exe | C:\Users\admin\AppData\Local\Temp\eotvzn2z\eotvzn2z.out | text | |
MD5:8B8FF5B8B766229BEA08741E0A6671BC | SHA256:5D706D4975D8ECD3E030C4AE647DDF9514F38F92448DF97B02DABF620576A950 | |||
| 2572 | cvtres.exe | C:\Users\admin\AppData\Local\Temp\RESBF44.tmp | o | |
MD5:EE7BA0BD687E020BF93317BCDB410A36 | SHA256:6508401273E53BFB3AFDB75ABA043346042B8151240189346AADCE288AA45A0D | |||
| 2848 | Chaos Ransomware Builder v4.exe | C:\Users\admin\AppData\Local\Temp\eotvzn2z\eotvzn2z.cmdline | text | |
MD5:E62B575E57736D3DF97089D322EC4479 | SHA256:2470BF38A48109FED4106BF1FB4D41E26107A226A4E56C447FC6409933BE8D2C | |||
| 2848 | Chaos Ransomware Builder v4.exe | C:\Users\admin\AppData\Local\Temp\eotvzn2z\eotvzn2z.0.cs | text | |
MD5:ADB72B9DD908446B2A980761A632360A | SHA256:07E1B8A2222EC2E1EB5E6B65F1345CEF699B800FBFAF371AB67FA78EF9982AA5 | |||
| 2648 | csc.exe | C:\Users\admin\Desktop\CSC81893520984344A7ADAF93F13BE8BE64.TMP | binary | |
MD5:1B5017CF6386C7FEF34F14D49F8B042E | SHA256:42C0B53B11A21067C1FF924A83639B97ED7DEC8650B7AA6A2397DC68FE9BB961 | |||
| 2848 | Chaos Ransomware Builder v4.exe | C:\Users\admin\Desktop\f-decrypter\privateKey.chaos | xml | |
MD5:3DB005840022B0281BC8B5AD5773E282 | SHA256:506D8440EEAF1548521BCB858C48DC2229CAB1B0C7475EAEBEA4F6E443BF056B | |||
| 2848 | Chaos Ransomware Builder v4.exe | C:\Users\admin\Desktop\f-decrypter\Decrypter.exe | executable | |
MD5:97F3854D27D9F5D8F9B15818237894D5 | SHA256:FAC94A8E02F92D63CFDF1299DB27E40410DA46C9E86D8BB2CD4B1A0D68D5F7A2 | |||
| 1572 | svchost.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\svchost.url | text | |
MD5:83660DEB1A47E0B191FDA82BDFD61827 | SHA256:87089BD6FEDDA43B5E4D738B5BF246BA1B2E5C248B9220F0D1E742B827F30B0D | |||
| 1572 | svchost.exe | C:\Users\admin\Documents\OneNote Notebooks\Personal\read_it.txt | text | |
MD5:4217B8B83CE3C3F70029A056546F8FD0 | SHA256:7D767E907BE373C680D1F7884D779588EB643BEBB3F27BF3B5ED4864AA4D8121 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
3
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |