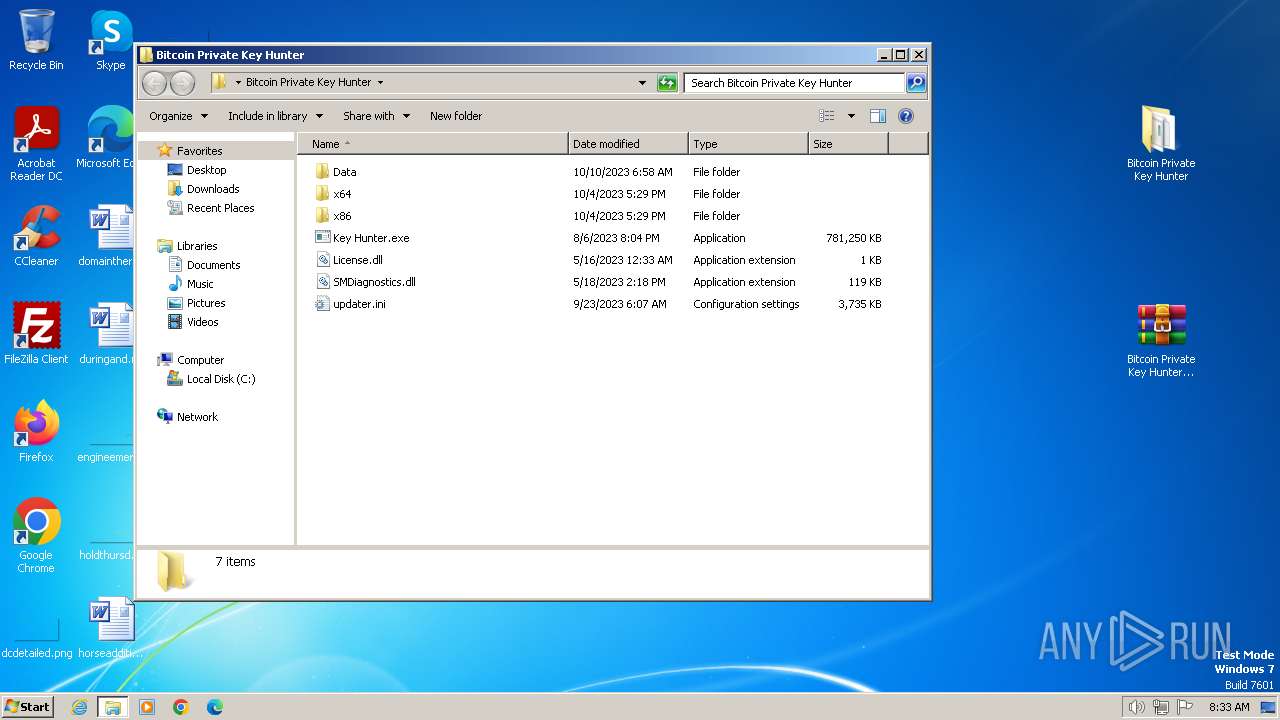
| File name: | Bitcoin_Private_Key_Hunter.rar |
| Full analysis: | https://app.any.run/tasks/15c9b19b-6147-4652-ae00-ee7af0381503 |
| Verdict: | Malicious activity |
| Analysis date: | December 20, 2023, 08:33:10 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 19493325FC93DF0D218DDA0B9E2D2ADD |
| SHA1: | 73C555A5CE779095356FAC96DE4279B50B748971 |
| SHA256: | F243CEEF18A29ECF5FB522388E2D5882B2F9917B24DEF6F134A37D037C2373AF |
| SSDEEP: | 98304:Sxq8fi8yjsBD+Gq78sEIJhTQfkxVP/bIJRSyKn3NrxYff7x3MvK1hIoeyJivlowa:bODXFa6CWwUmhi3Sy1 |
MALICIOUS
Adds path to the Windows Defender exclusion list
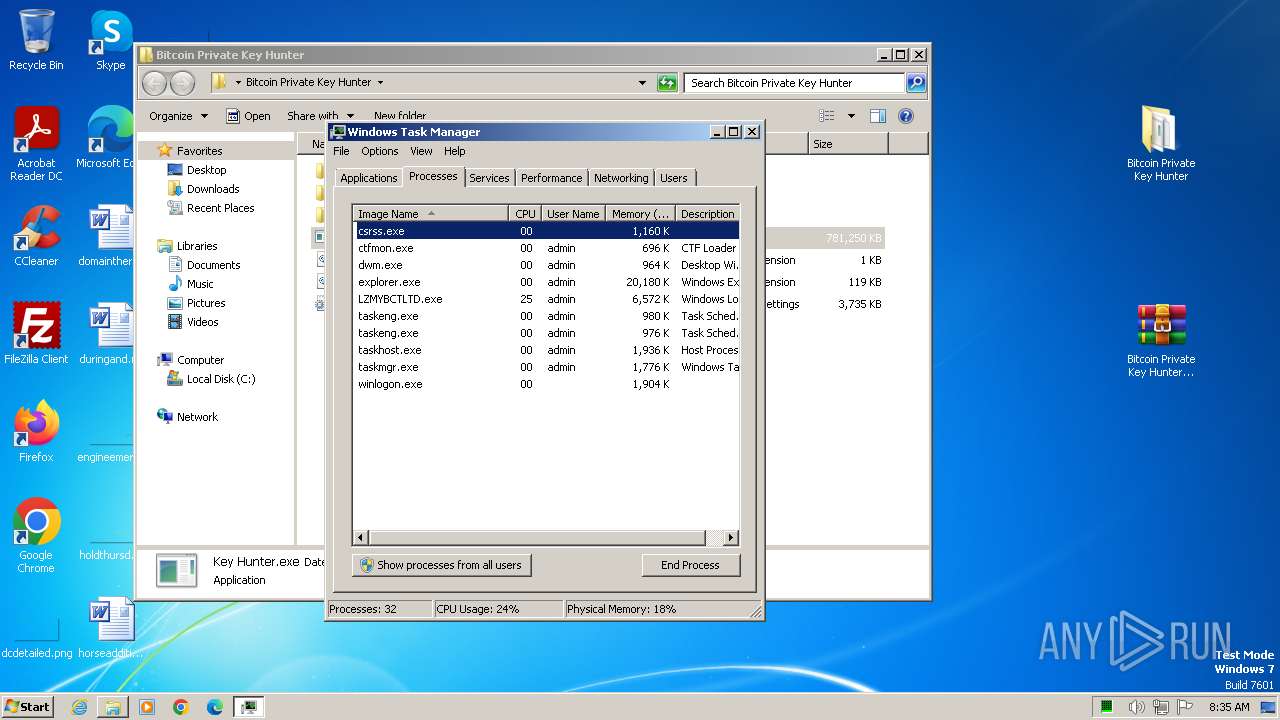
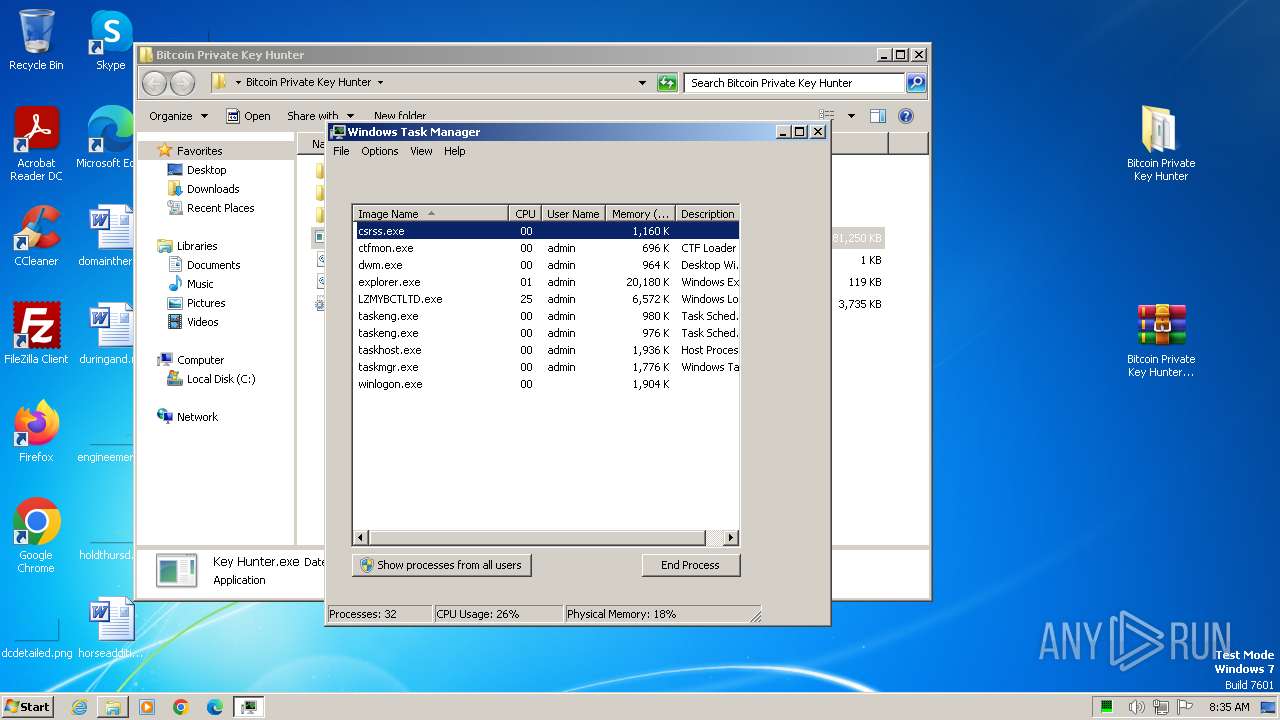
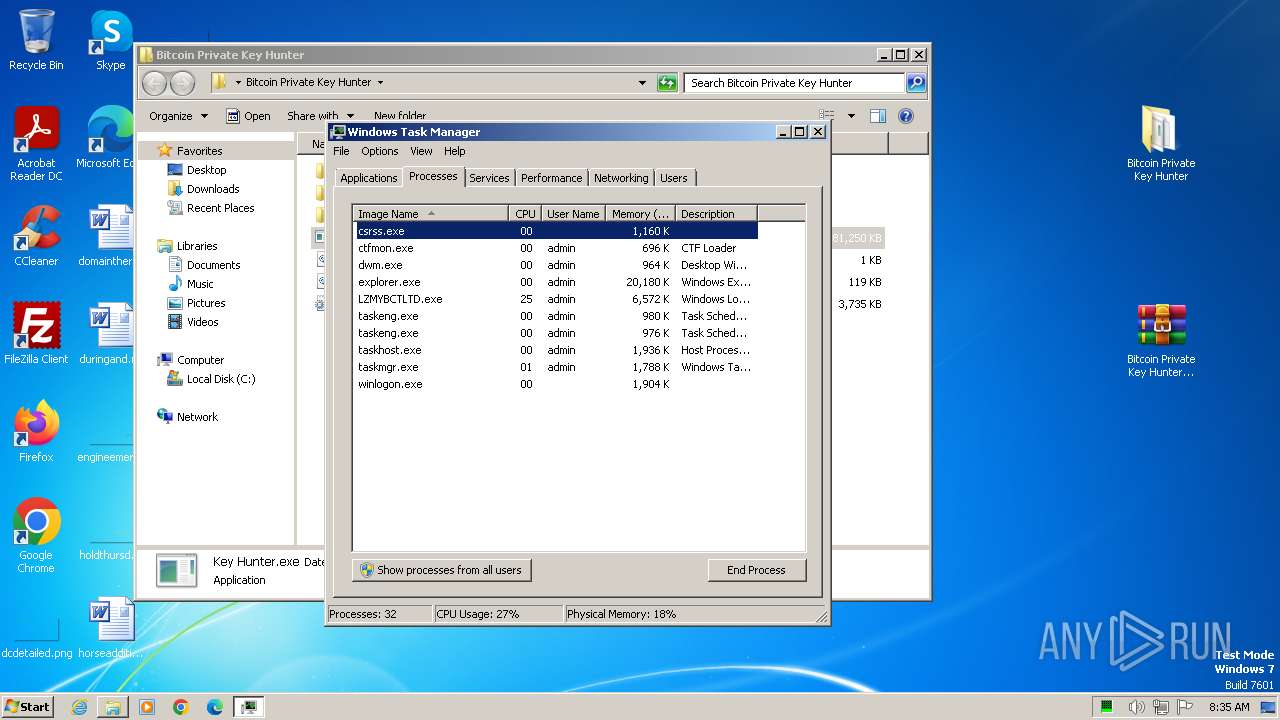
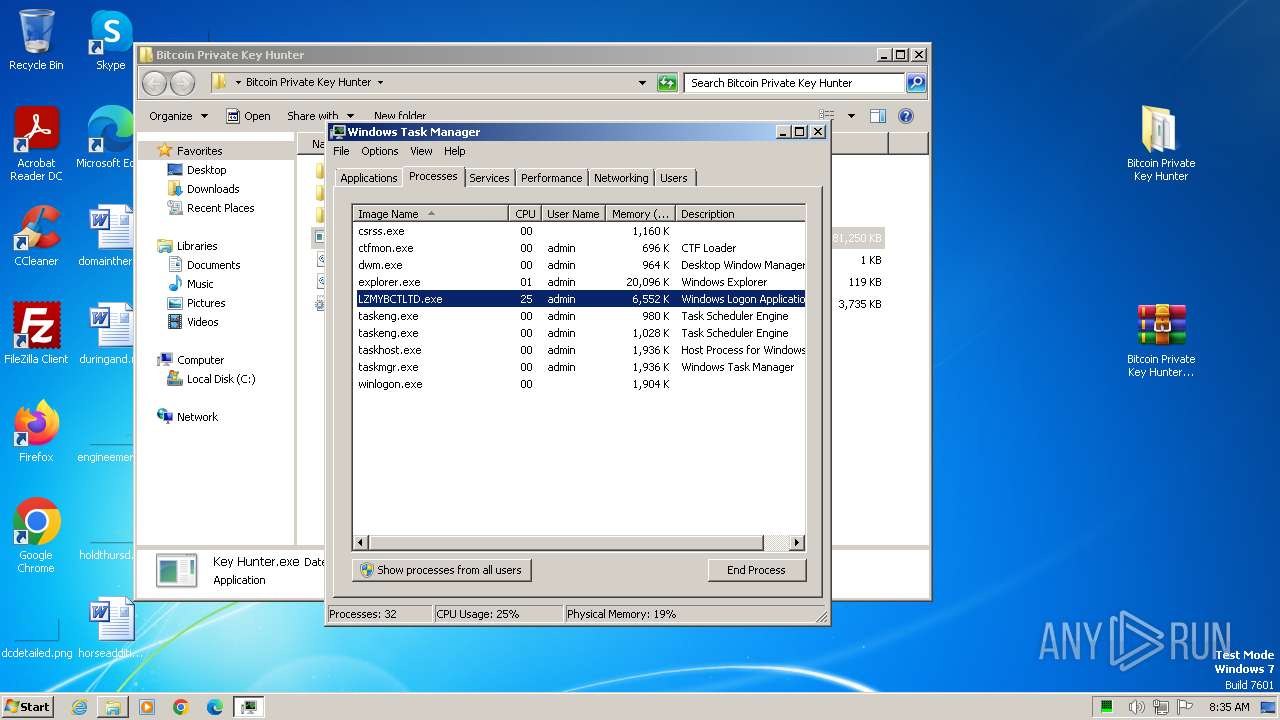
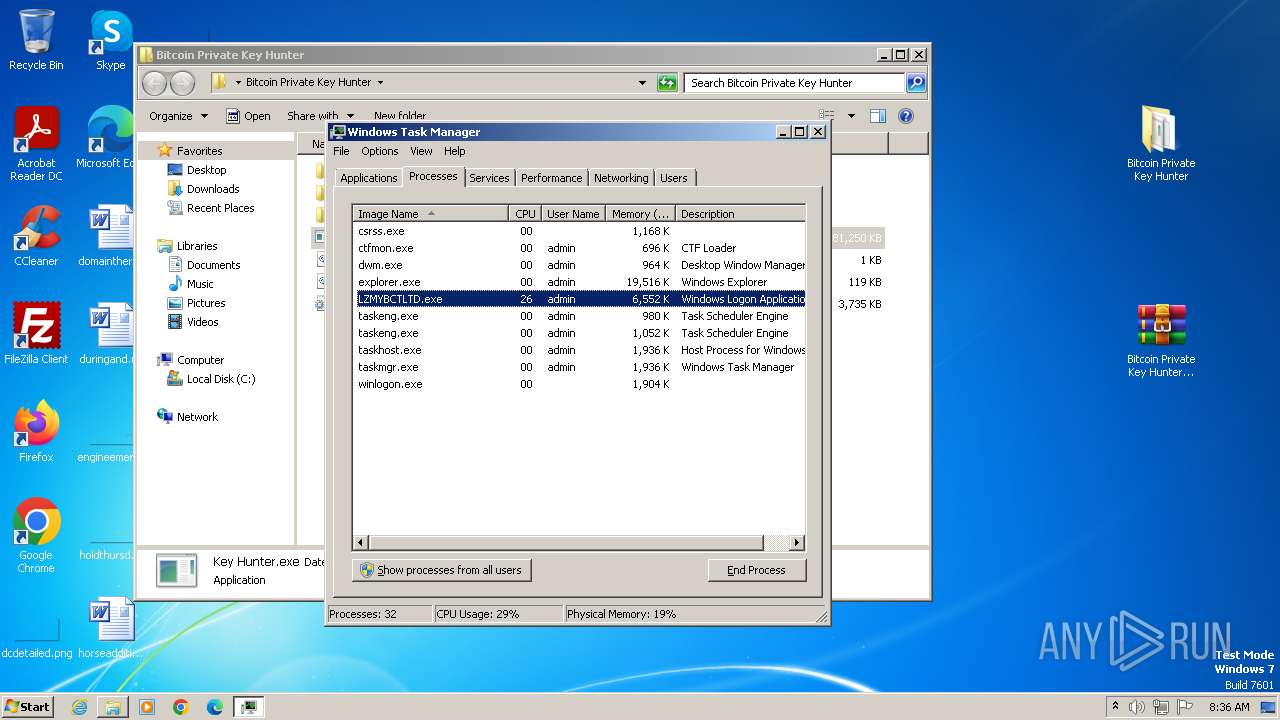
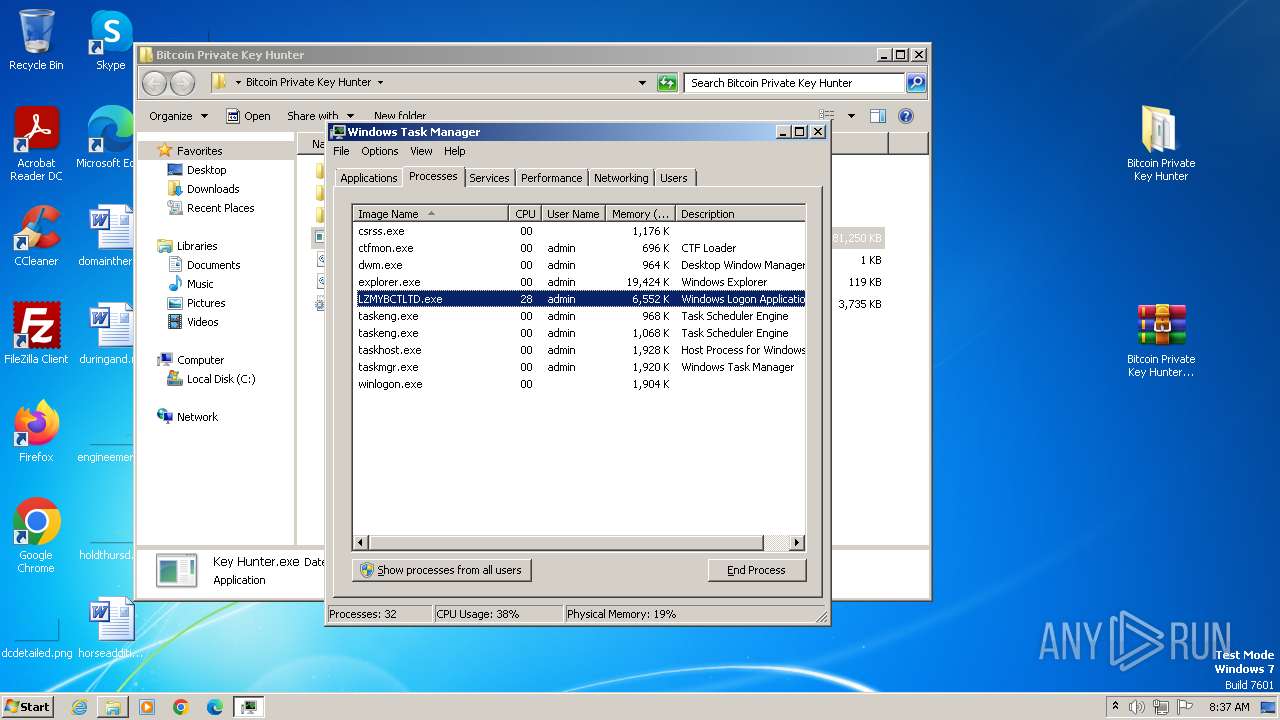
- Key Hunter.exe (PID: 2308)
- LZMYBCTLTD.exe (PID: 1036)
- LZMYBCTLTD.exe (PID: 3024)
- LZMYBCTLTD.exe (PID: 3200)
- LZMYBCTLTD.exe (PID: 3660)
Uses Task Scheduler to run other applications
- LZMYBCTLTD.exe (PID: 1036)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 2084)
Reads the BIOS version
- Key Hunter.exe (PID: 1936)
- Key Hunter.exe (PID: 2308)
- LZMYBCTLTD.exe (PID: 1036)
- LZMYBCTLTD.exe (PID: 3024)
- LZMYBCTLTD.exe (PID: 3200)
- LZMYBCTLTD.exe (PID: 3660)
Reads the Internet Settings
- Key Hunter.exe (PID: 1936)
- Key Hunter.exe (PID: 2308)
- powershell.exe (PID: 2296)
- LZMYBCTLTD.exe (PID: 1036)
- powershell.exe (PID: 2388)
- powershell.exe (PID: 2192)
- LZMYBCTLTD.exe (PID: 3024)
- powershell.exe (PID: 3040)
- powershell.exe (PID: 3056)
- powershell.exe (PID: 2828)
- LZMYBCTLTD.exe (PID: 3200)
- powershell.exe (PID: 3276)
- powershell.exe (PID: 3292)
- LZMYBCTLTD.exe (PID: 3660)
- powershell.exe (PID: 4084)
- powershell.exe (PID: 4036)
Application launched itself
- Key Hunter.exe (PID: 1936)
Script adds exclusion path to Windows Defender
- Key Hunter.exe (PID: 2308)
- LZMYBCTLTD.exe (PID: 1036)
- LZMYBCTLTD.exe (PID: 3024)
- LZMYBCTLTD.exe (PID: 3200)
- LZMYBCTLTD.exe (PID: 3660)
Starts POWERSHELL.EXE for commands execution
- Key Hunter.exe (PID: 2308)
- LZMYBCTLTD.exe (PID: 1036)
- LZMYBCTLTD.exe (PID: 3024)
- LZMYBCTLTD.exe (PID: 3200)
- LZMYBCTLTD.exe (PID: 3660)
Using PowerShell to operate with local accounts
- powershell.exe (PID: 2296)
- powershell.exe (PID: 2192)
- powershell.exe (PID: 2388)
- powershell.exe (PID: 3040)
- powershell.exe (PID: 3056)
- powershell.exe (PID: 2828)
- powershell.exe (PID: 3276)
- powershell.exe (PID: 3292)
- powershell.exe (PID: 4036)
- powershell.exe (PID: 4084)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 2588)
Starts CMD.EXE for commands execution
- Key Hunter.exe (PID: 2308)
Executing commands from a ".bat" file
- Key Hunter.exe (PID: 2308)
The process executes via Task Scheduler
- LZMYBCTLTD.exe (PID: 3024)
- LZMYBCTLTD.exe (PID: 3660)
- LZMYBCTLTD.exe (PID: 3200)
INFO
Manual execution by a user
- WinRAR.exe (PID: 2084)
- Key Hunter.exe (PID: 1936)
- taskmgr.exe (PID: 2836)
- wmpnscfg.exe (PID: 2840)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2084)
Checks supported languages
- Key Hunter.exe (PID: 1936)
- Key Hunter.exe (PID: 2308)
- LZMYBCTLTD.exe (PID: 1036)
- wmpnscfg.exe (PID: 2840)
- LZMYBCTLTD.exe (PID: 3024)
- LZMYBCTLTD.exe (PID: 3660)
- LZMYBCTLTD.exe (PID: 3200)
Reads the computer name
- Key Hunter.exe (PID: 1936)
- Key Hunter.exe (PID: 2308)
- LZMYBCTLTD.exe (PID: 1036)
- wmpnscfg.exe (PID: 2840)
- LZMYBCTLTD.exe (PID: 3024)
- LZMYBCTLTD.exe (PID: 3200)
- LZMYBCTLTD.exe (PID: 3660)
Process checks are UAC notifies on
- Key Hunter.exe (PID: 2308)
- LZMYBCTLTD.exe (PID: 1036)
- LZMYBCTLTD.exe (PID: 3024)
- LZMYBCTLTD.exe (PID: 3200)
- LZMYBCTLTD.exe (PID: 3660)
Creates files in the program directory
- Key Hunter.exe (PID: 2308)
Create files in a temporary directory
- Key Hunter.exe (PID: 2308)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
73
Monitored processes
23
Malicious processes
7
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1036 | "C:\ProgramData\active\LZMYBCTLTD.exe" | C:\ProgramData\active\LZMYBCTLTD.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Logon Application Exit code: 0 Version: 10.0.17134.1 Modules
| |||||||||||||||
| 1936 | "C:\Users\admin\Desktop\Bitcoin Private Key Hunter\Key Hunter.exe" | C:\Users\admin\Desktop\Bitcoin Private Key Hunter\Key Hunter.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Logon Application Exit code: 1 Version: 10.0.17134.1 Modules
| |||||||||||||||
| 2040 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Bitcoin_Private_Key_Hunter.rar" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2084 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\Bitcoin Private Key Hunter.rar" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2192 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" Add-MpPreference -ExclusionPath 'C:\Users\admin\AppData\Roaming' | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | Key Hunter.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 2296 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" Add-MpPreference -ExclusionPath 'C:\ProgramData' | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | Key Hunter.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 2308 | "C:\Users\admin\Desktop\Bitcoin Private Key Hunter\Key Hunter.exe" | C:\Users\admin\Desktop\Bitcoin Private Key Hunter\Key Hunter.exe | Key Hunter.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Logon Application Exit code: 0 Version: 10.0.17134.1 Modules
| |||||||||||||||
| 2388 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" Add-MpPreference -ExclusionPath 'C:\ProgramData' | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | LZMYBCTLTD.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 2588 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\s1s4.0.bat" " | C:\Windows\System32\cmd.exe | — | Key Hunter.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2724 | "C:\Windows\System32\schtasks.exe" /create /sc MINUTE /mo 1 /RL HIGHEST /tn "LZMYBCTLTD" /tr C:\ProgramData\active\LZMYBCTLTD.exe /f | C:\Windows\System32\schtasks.exe | — | LZMYBCTLTD.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
9 679
Read events
9 454
Write events
225
Delete events
0
Modification events
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
Executable files
3
Suspicious files
22
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2040 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2040.18685\Bitcoin Private Key Hunter.rar | — | |
MD5:— | SHA256:— | |||
| 2084 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2084.19917\Bitcoin Private Key Hunter\Data\Configuration.cfg | — | |
MD5:— | SHA256:— | |||
| 2084 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2084.19917\Bitcoin Private Key Hunter\Key Hunter.exe | — | |
MD5:— | SHA256:— | |||
| 2308 | Key Hunter.exe | C:\ProgramData\active\LZMYBCTLTD.exe | — | |
MD5:— | SHA256:— | |||
| 2084 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2084.19917\Bitcoin Private Key Hunter\updater.ini | binary | |
MD5:BDB71E725923415AD118571A96A58F9C | SHA256:CDFD1E0DB31EF98BE246AC26C14CBD47B24A11F85DD255FE55F93F8FB9FCAB11 | |||
| 2084 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2084.19917\Bitcoin Private Key Hunter\x64\SQLite.Interop.dll | executable | |
MD5:56A504A34D2CFBFC7EAA2B68E34AF8AD | SHA256:9309FB2A3F326D0F2CC3F2AB837CFD02E4F8CB6B923B3B2BE265591FD38F4961 | |||
| 2084 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2084.19917\Bitcoin Private Key Hunter\SMDiagnostics.dll | executable | |
MD5:F1D92AC71001BCC24B99044EE675619F | SHA256:5DF3A2E0329D7668AD0F6C426F6E4C6D1ECD45225B2C39D96B15CD7B6A1BBE53 | |||
| 2084 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2084.19917\Bitcoin Private Key Hunter\x86\SQLite.Interop.dll | executable | |
MD5:8BE215ABF1F36AA3D23555A671E7E3BE | SHA256:83F332EA9535814F18BE4EE768682ECC7720794AEDC30659EB165E46257A7CAE | |||
| 2192 | powershell.exe | C:\Users\admin\AppData\Local\Temp\ythh5ct0.bwj.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 2828 | powershell.exe | C:\Users\admin\AppData\Local\Temp\aulnz442.udj.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |